9bb6bd0cd67205c2e870dc9f359ff125.ppt
- Количество слайдов: 41

business on demand Accessing Secure e. Business Systems from NMCI © 2003 IBM Corporation
2 Accessing Secure e. Business Systems from NMCI Industry Symposium June 2003 © 2003 IBM Corporation

An enterprise whose business processes – integrated end-to-end across the company and with key partners, suppliers and customers – can respond with flexibility and speed to any customer demand, market opportunity or threat 3 Accessing Secure e. Business Systems from NMCI Industry Symposium June 2003 © 2003 IBM Corporation
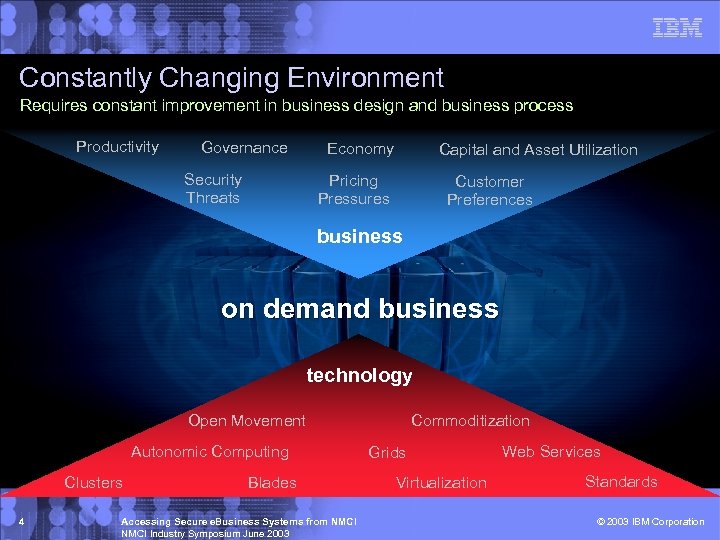
Constantly Changing Environment Requires constant improvement in business design and business process Productivity Governance Security Threats Economy Capital and Asset Utilization Pricing Pressures Customer Preferences business on demand business technology Open Movement Autonomic Computing Clusters 4 Blades Accessing Secure e. Business Systems from NMCI Industry Symposium June 2003 Commoditization Grids Virtualization Web Services Standards © 2003 IBM Corporation
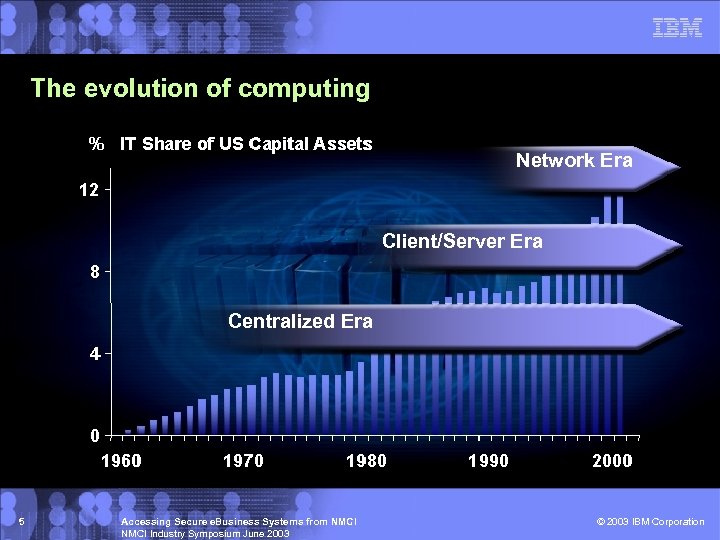
The evolution of computing Network Era Client/Server Era Centralized Era 5 Accessing Secure e. Business Systems from NMCI Industry Symposium June 2003 © 2003 IBM Corporation
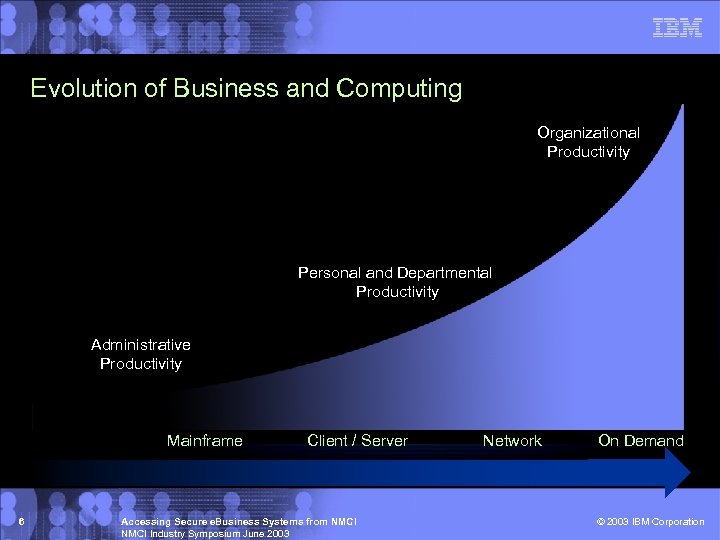
Evolution of Business and Computing Organizational Productivity Personal and Departmental Productivity Administrative Productivity Mainframe 6 Client / Server Accessing Secure e. Business Systems from NMCI Industry Symposium June 2003 Network On Demand © 2003 IBM Corporation
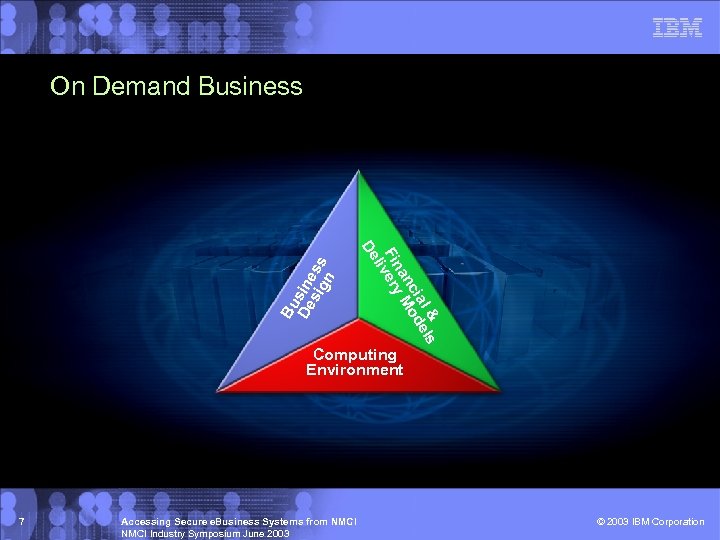
l & els cia od an M Finvery li De Bu De sine sig ss n On Demand Business Computing Environment 7 Accessing Secure e. Business Systems from NMCI Industry Symposium June 2003 © 2003 IBM Corporation
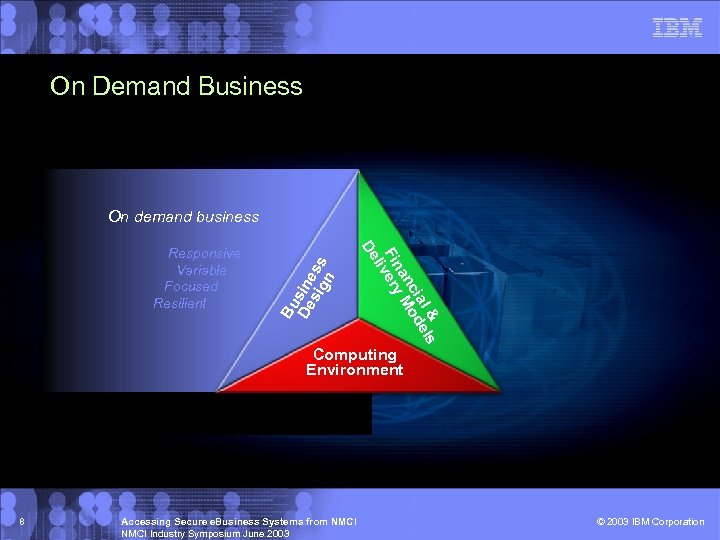
On Demand Business l & els cia od an M Finvery li De Responsive Variable Focused Resilient Bu De sine sig ss n On demand business Computing Environment 8 Accessing Secure e. Business Systems from NMCI Industry Symposium June 2003 © 2003 IBM Corporation
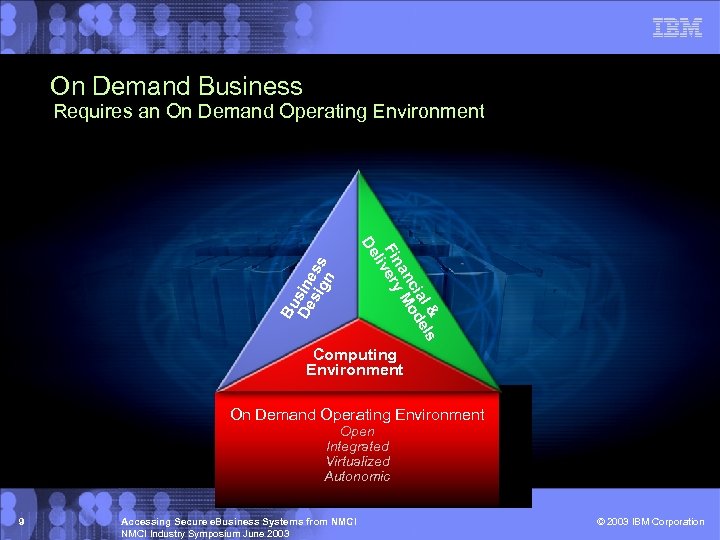
On Demand Business l & els cia od an M Finvery li De Bu De sine sig ss n Requires an On Demand Operating Environment Computing Environment On Demand Operating Environment Open Integrated Virtualized Autonomic 9 Accessing Secure e. Business Systems from NMCI Industry Symposium June 2003 © 2003 IBM Corporation
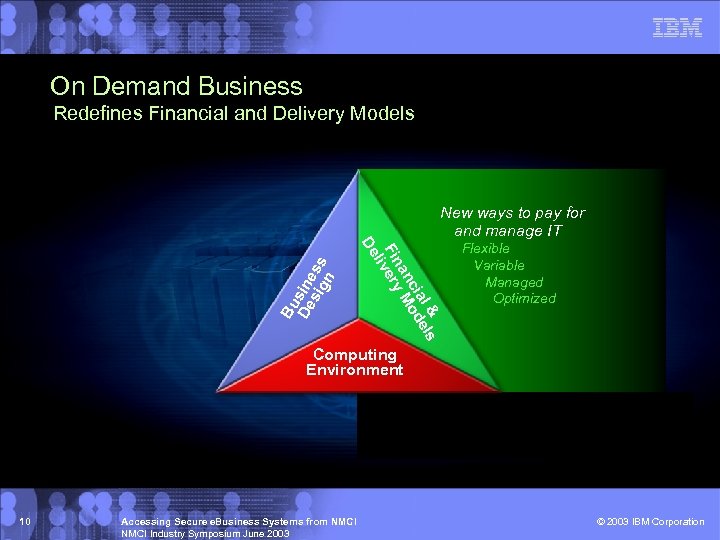
On Demand Business Redefines Financial and Delivery Models l & els cia od an M Finvery li De Bu De sine sig ss n New ways to pay for and manage IT Flexible Variable Managed Optimized Computing Environment 10 Accessing Secure e. Business Systems from NMCI Industry Symposium June 2003 © 2003 IBM Corporation
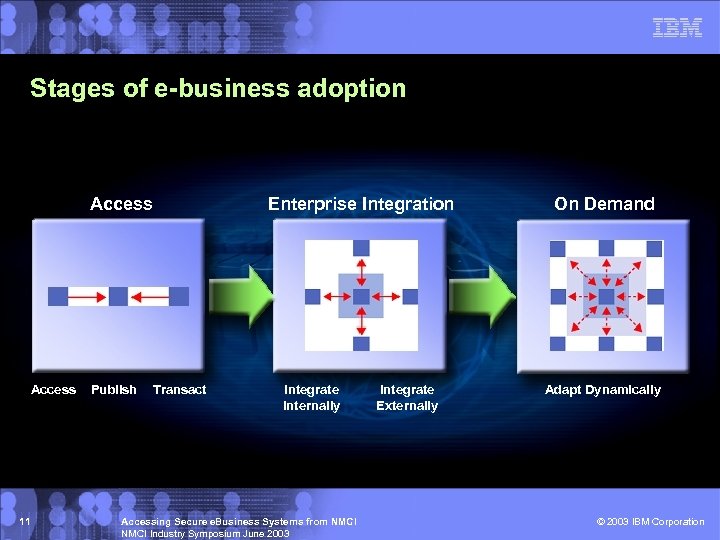
Stages of e-business adoption Access 11 Publish Transact Enterprise Integration Integrate Internally Accessing Secure e. Business Systems from NMCI Industry Symposium June 2003 Integrate Externally On Demand Adapt Dynamically © 2003 IBM Corporation

Navy One Touch Support A secure ebusiness system Accessed from NMCI 12 Accessing Secure e. Business Systems from NMCI Industry Symposium June 2003 © 2003 IBM Corporation
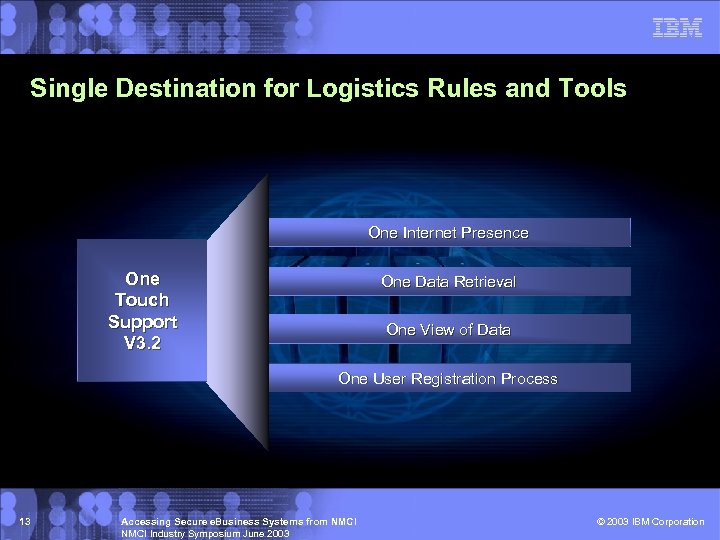
Single Destination for Logistics Rules and Tools One Internet Presence One Touch Support V 3. 2 One Data Retrieval One View of Data One User Registration Process 13 Accessing Secure e. Business Systems from NMCI Industry Symposium June 2003 © 2003 IBM Corporation

Commercially Hosted – DITSCAP Certified www. onetouch. navy. mil § A Technical Architecture that: – Is Scalable, Highly Reliable and Open – Is Flexible and Extensible to support integration and additional interfaces – Complies with Navy and Do. D Security Requirements – Is a modular based architecture – incorporating relevant Task Force Web (TFW) web enabled Navy architecture guidance as appropriate – Complies with NMCI issued guidelines 14 Accessing Secure e. Business Systems from NMCI Industry Symposium June 2003 © 2003 IBM Corporation
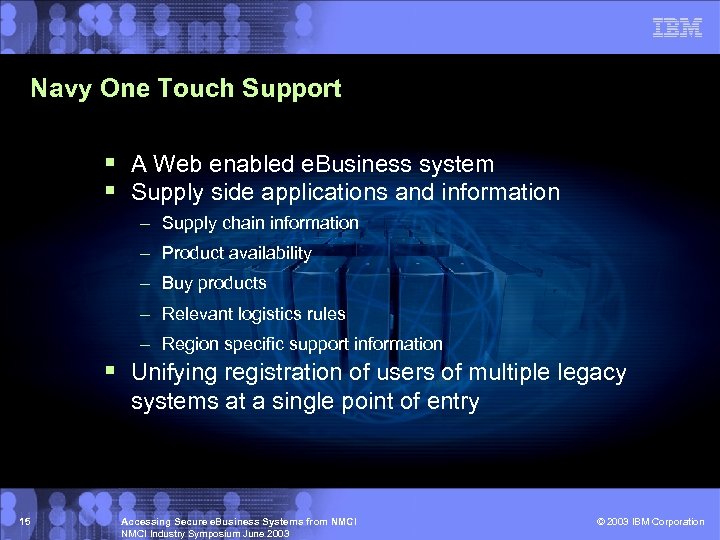
Navy One Touch Support § A Web enabled e. Business system § Supply side applications and information – Supply chain information – Product availability – Buy products – Relevant logistics rules – Region specific support information § Unifying registration of users of multiple legacy systems at a single point of entry 15 Accessing Secure e. Business Systems from NMCI Industry Symposium June 2003 © 2003 IBM Corporation

Users transition to NMCI from legacy domains such as fisc. navy. mil. They just point their enterprise approved browser to onetouch. navy. mil, enter their user ID and password, and continue to conduct ebusiness as usual. 16 Accessing Secure e. Business Systems from NMCI Industry Symposium June 2003 © 2003 IBM Corporation
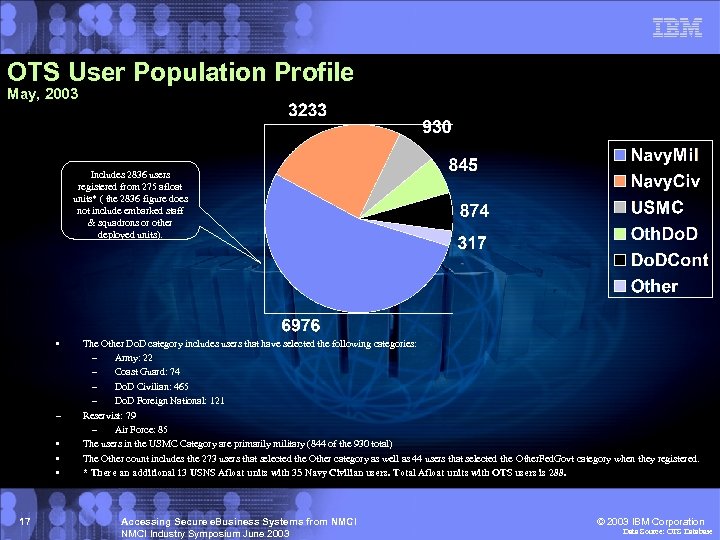
OTS User Population Profile May, 2003 Includes 2836 users registered from 275 afloat units* ( the 2836 figure does not include embarked staff & squadrons or other deployed units). • – • • • 17 The Other Do. D category includes users that have selected the following categories: – Army: 22 – Coast Guard: 74 – Do. D Civilian: 465 – Do. D Foreign National: 121 Reservist: 79 – Air Force: 85 The users in the USMC Category are primarily military (844 of the 930 total) The Other count includes the 273 users that selected the Other category as well as 44 users that selected the Other. Fed. Govt category when they registered. * There an additional 13 USNS Afloat units with 35 Navy Civilian users. Total Afloat units with OTS users is 288. Accessing Secure e. Business Systems from NMCI Industry Symposium June 2003 © 2003 IBM Corporation Data Source: OTS Database

Doing a little e. Business § First year of operations for OTS v 3. 2 – 63 million hits – 108 billion byes transferred – 920 thousand logins – 12 million page views – 2 million query transactions – 1 million MILSTRIP transactions – 13, 000 registered users 18 Accessing Secure e. Business Systems from NMCI Industry Symposium June 2003 © 2003 IBM Corporation
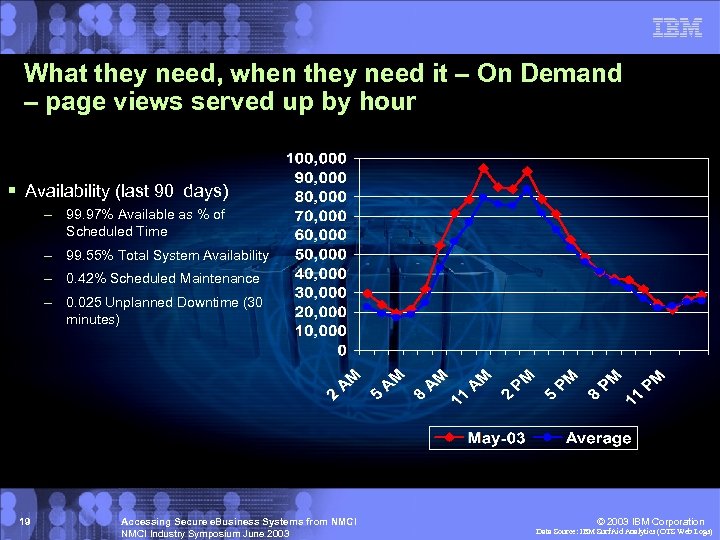
What they need, when they need it – On Demand – page views served up by hour § Availability (last 90 days) – 99. 97% Available as % of Scheduled Time – 99. 55% Total System Availability – 0. 42% Scheduled Maintenance – 0. 025 Unplanned Downtime (30 minutes) 19 Accessing Secure e. Business Systems from NMCI Industry Symposium June 2003 © 2003 IBM Corporation Data Source: IBM Surf. Aid Analytics (OTS Web Logs)
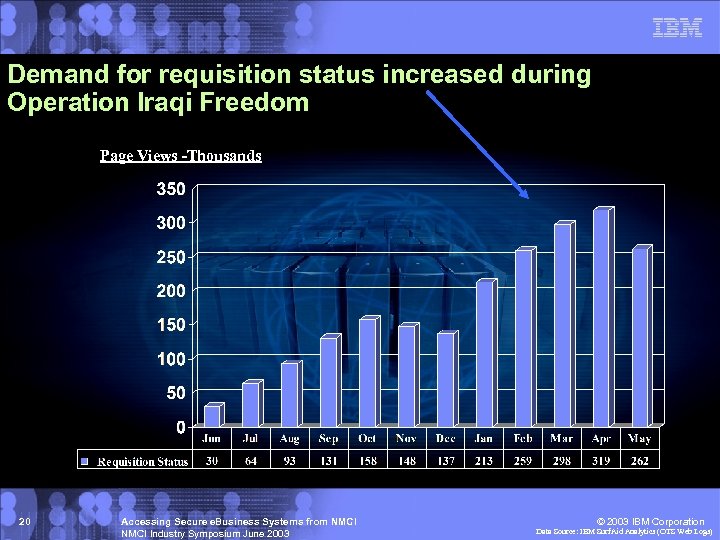
Demand for requisition status increased during Operation Iraqi Freedom Page Views -Thousands 20 Accessing Secure e. Business Systems from NMCI Industry Symposium June 2003 © 2003 IBM Corporation Data Source: IBM Surf. Aid Analytics (OTS Web Logs)

Access Management § User Registration – Do. D Employee Status Verification – If not: – Approval Authority Contact Information Request – Business Functional Approval Work Flow – Sponsor Letter Requirements § User and User Profile Management – Approving/Disapproving Requests – Request Additional Business Functions – Update Contact Information – Reset Password 21 Accessing Secure e. Business Systems from NMCI Industry Symposium June 2003 © 2003 IBM Corporation
Core Supply Chain Functions § Applications – Technical Screening, Stock Check, Requisition Input, Requisition Status, File Text Upload, Batch Query § Integrated functions where possible – Example: From Req Status Return – Detail History – Ship Status Details – Follow-up, Modify, Cancel, or Order Again – Technical Screen Item § Access over 30 data sources 22 Accessing Secure e. Business Systems from NMCI Industry Symposium June 2003 © 2003 IBM Corporation
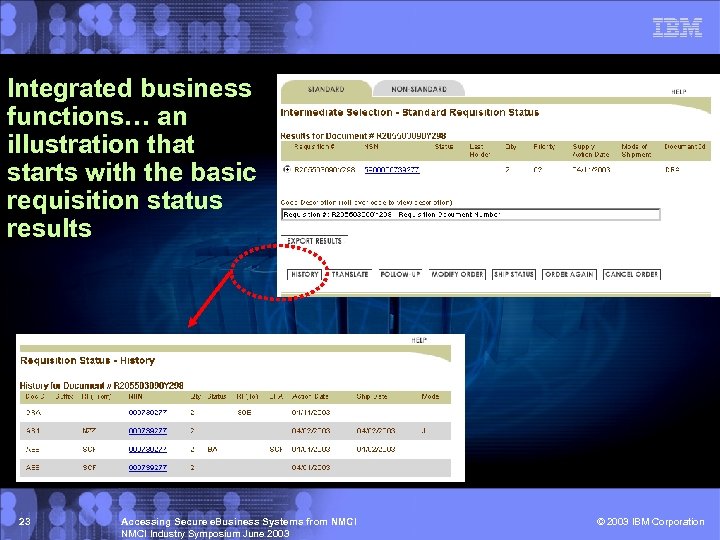
Integrated business functions… an illustration that starts with the basic requisition status results 23 Accessing Secure e. Business Systems from NMCI Industry Symposium June 2003 © 2003 IBM Corporation
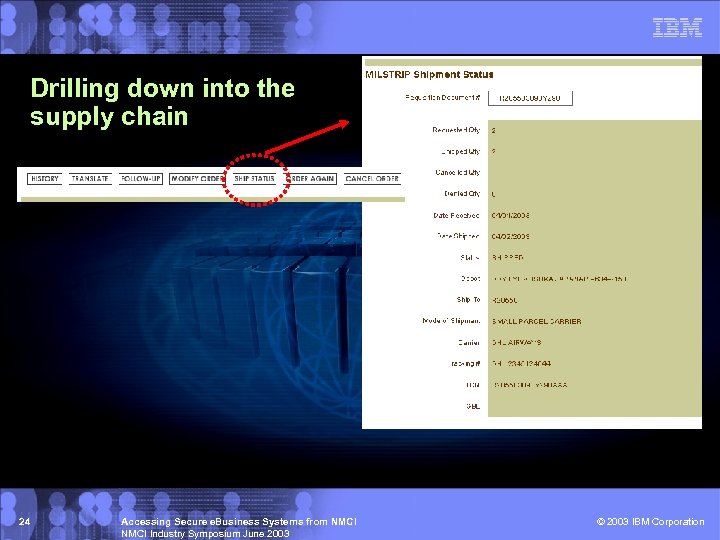
Drilling down into the supply chain 24 Accessing Secure e. Business Systems from NMCI Industry Symposium June 2003 © 2003 IBM Corporation
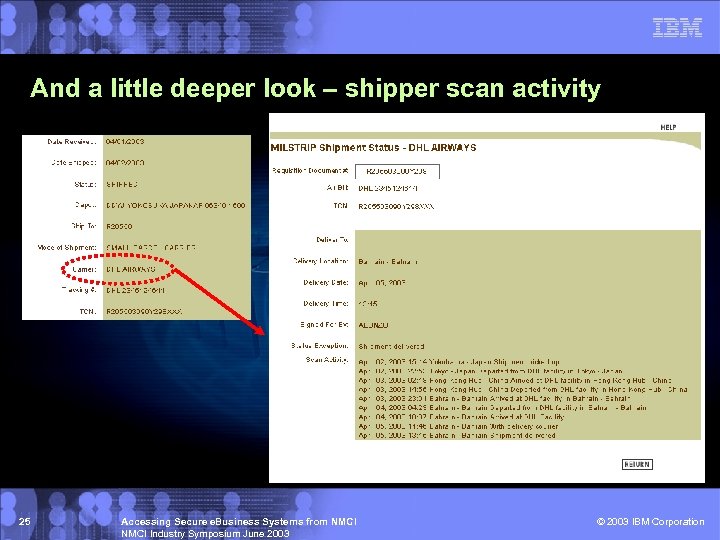
And a little deeper look – shipper scan activity 25 Accessing Secure e. Business Systems from NMCI Industry Symposium June 2003 © 2003 IBM Corporation
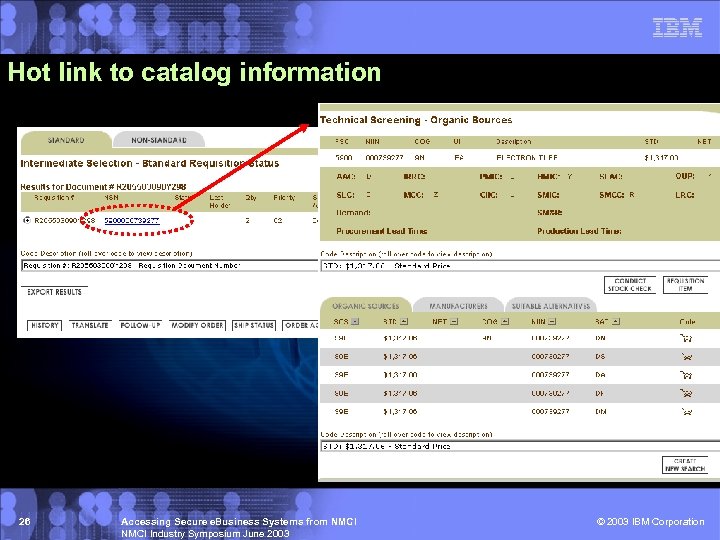
Hot link to catalog information 26 Accessing Secure e. Business Systems from NMCI Industry Symposium June 2003 © 2003 IBM Corporation
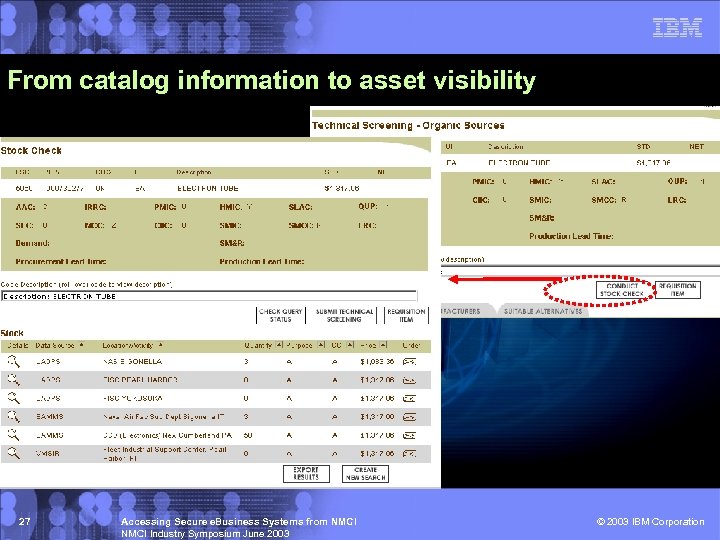
From catalog information to asset visibility 27 Accessing Secure e. Business Systems from NMCI Industry Symposium June 2003 © 2003 IBM Corporation

enterprise integration: a stop along the way to business on demand 28 Accessing Secure e. Business Systems from NMCI Industry Symposium June 2003 © 2003 IBM Corporation

Promises and Problems The Promise of I/T The Problem with I/T § Deploying new capabilities § Time to value § Cost reduction § Managing complexity and § Efficiency § Security and operational resiliency § Workforce productivity 29 Accessing Secure e. Business Systems from NMCI Industry Symposium June 2003 integration § ROI § Constrained resources § Utilization of existing infrastructure © 2003 IBM Corporation
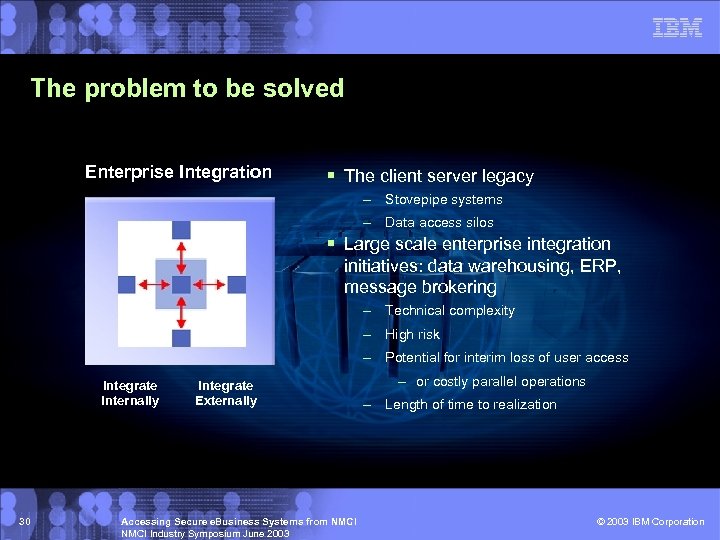
The problem to be solved Enterprise Integration § The client server legacy – Stovepipe systems – Data access silos § Large scale enterprise integration initiatives: data warehousing, ERP, message brokering – Technical complexity – High risk – Potential for interim loss of user access Integrate Internally 30 Integrate Externally Accessing Secure e. Business Systems from NMCI Industry Symposium June 2003 – or costly parallel operations – Length of time to realization © 2003 IBM Corporation
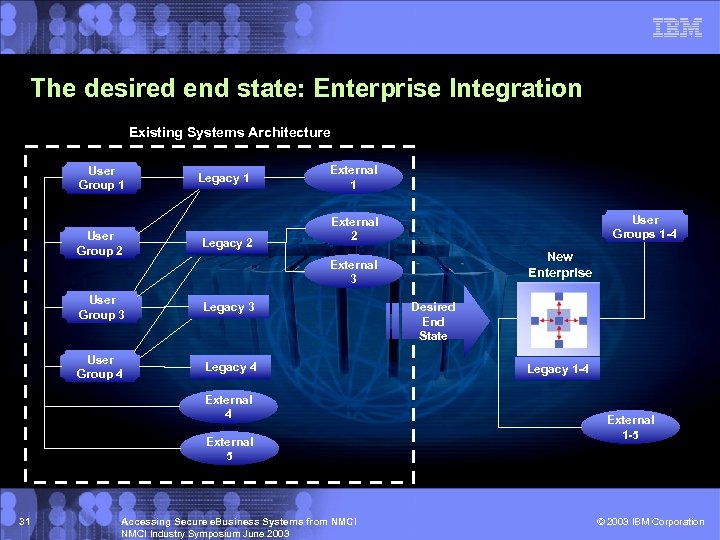
The desired end state: Enterprise Integration Existing Systems Architecture User Group 1 User Group 2 Legacy 1 Legacy 2 External 1 User Groups 1 -4 External 2 New Enterprise External 3 User Group 3 Legacy 3 User Group 4 Legacy 4 External 5 31 Accessing Secure e. Business Systems from NMCI Industry Symposium June 2003 Desired End State Legacy 1 -4 External 1 -5 © 2003 IBM Corporation
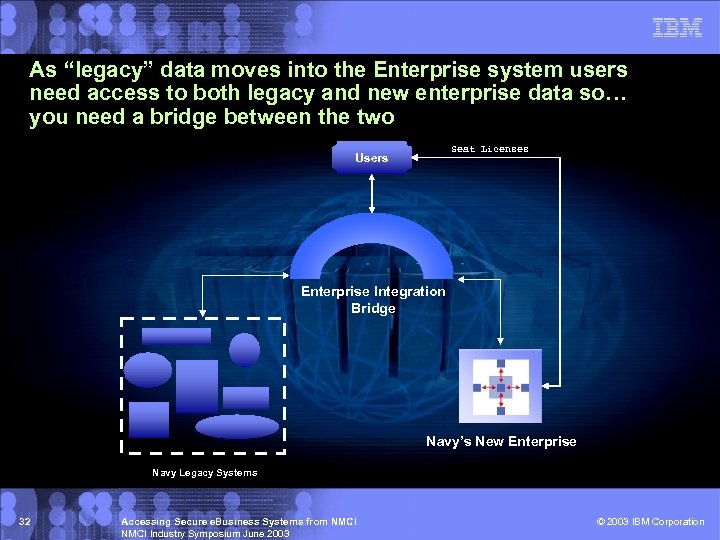
As “legacy” data moves into the Enterprise system users need access to both legacy and new enterprise data so… you need a bridge between the two Seat Licenses Users Enterprise Integration Bridge Navy’s New Enterprise Navy Legacy Systems 32 Accessing Secure e. Business Systems from NMCI Industry Symposium June 2003 © 2003 IBM Corporation
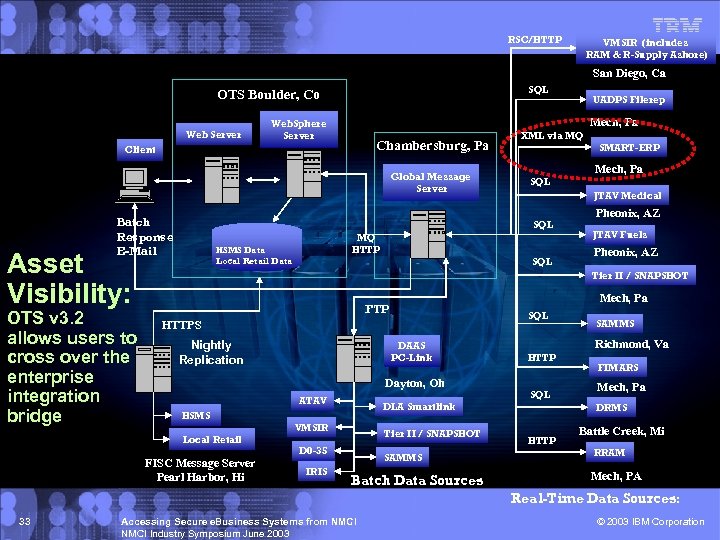
RSC/HTTP VMSIR (includes RAM & R-Supply Ashore) San Diego, Ca SQL OTS Boulder, Co Web Server Mech, Pa Web. Sphere Server Chambersburg, Pa Client Global Message Server Batch Response E-Mail Asset Visibility: OTS v 3. 2 allows users to cross over the enterprise integration bridge XML via MQ SMART-ERP Mech, Pa SQL JTAV Medical SQL MQ HTTP HSMS Data Local Retail Data UADPS Filerep SQL Pheonix, AZ JTAV Fuels Pheonix, AZ Tier II / SNAPSHOT Mech, Pa FTP SQL HTTPS Nightly Replication DAAS PC-Link Dayton, Oh ATAV VMSIR Local Retail FISC Message Server Pearl Harbor, Hi Tier II / SNAPSHOT D 0 -35 IRIS Richmond, Va HTTP SQL DLA Smartlink HSMS SAMMS Batch Data Sources SAMMS FIMARS Mech, Pa DRMS HTTP Battle Creek, Mi RRAM Mech, PA Real-Time Data Sources: 33 Accessing Secure e. Business Systems from NMCI Industry Symposium June 2003 © 2003 IBM Corporation

Security, Web Services and Enterprise Integration 34 Accessing Secure e. Business Systems from NMCI Industry Symposium June 2003 © 2003 IBM Corporation
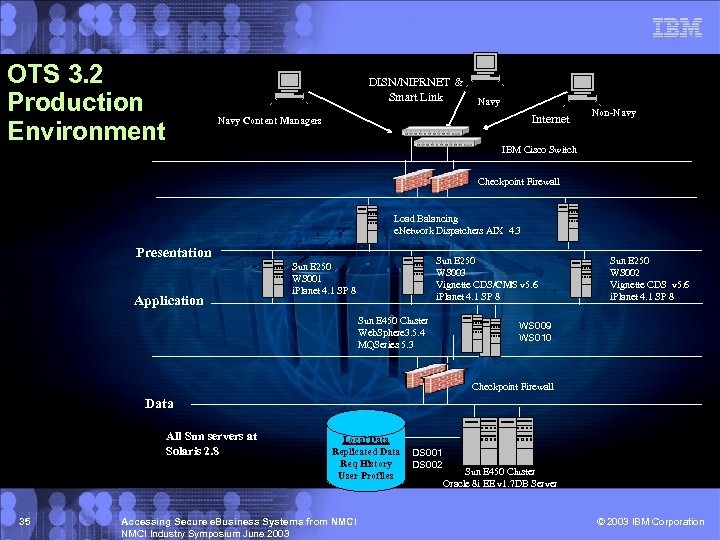
OTS 3. 2 Production Environment DISN/NIPRNET & Smart Link Navy Internet Navy Content Managers Non-Navy IBM Cisco Switch Checkpoint Firewall Load Balancing e. Network Dispatchers AIX 4. 3 Presentation Application Sun E 250 WS 003 Vignette CDS/CMS v 5. 6 i. Planet 4. 1 SP 8 Sun E 250 WS 001 i. Planet 4. 1 SP 8 Sun E 450 Cluster Web. Sphere 3. 5. 4 MQSeries 5. 3 Sun E 250 WS 002 Vignette CDS v 5. 6 i. Planet 4. 1 SP 8 WS 009 WS 010 Checkpoint Firewall Data All Sun servers at Solaris 2. 8 35 Local Data Replicated Data Req History User Profiles Accessing Secure e. Business Systems from NMCI Industry Symposium June 2003 DS 001 DS 002 Sun E 450 Cluster Oracle 8 i EE v 1. 7 DB Server © 2003 IBM Corporation
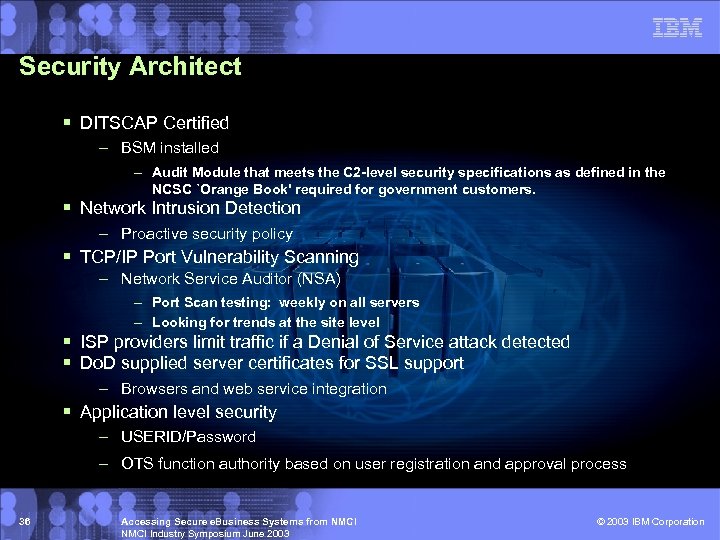
Security Architect § DITSCAP Certified – BSM installed – Audit Module that meets the C 2 -level security specifications as defined in the NCSC `Orange Book' required for government customers. § Network Intrusion Detection – Proactive security policy § TCP/IP Port Vulnerability Scanning – Network Service Auditor (NSA) – Port Scan testing: weekly on all servers – Looking for trends at the site level § ISP providers limit traffic if a Denial of Service attack detected § Do. D supplied server certificates for SSL support – Browsers and web service integration § Application level security – USERID/Password – OTS function authority based on user registration and approval process 36 Accessing Secure e. Business Systems from NMCI Industry Symposium June 2003 © 2003 IBM Corporation
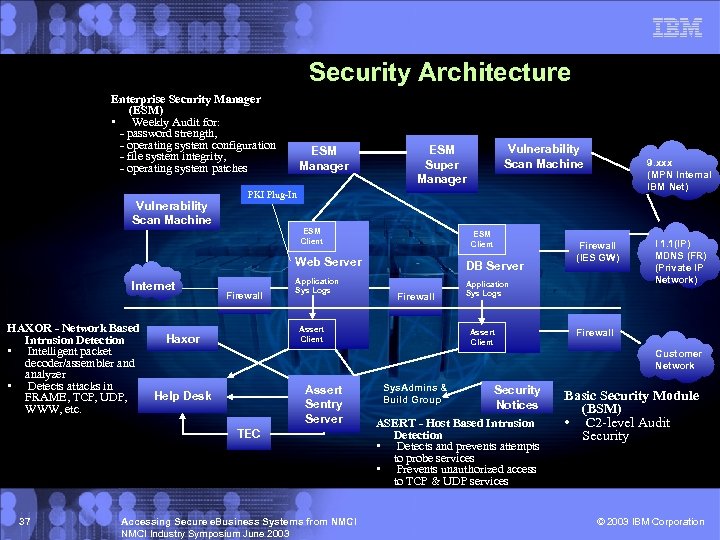
Security Architecture Enterprise Security Manager (ESM) • Weekly Audit for: - password strength, - operating system configuration - file system integrity, - operating system patches Vulnerability Scan Machine ESM Manager Vulnerability Scan Machine ESM Super Manager PKI Plug-In ESM Client Web Server Internet HAXOR - Network Based Intrusion Detection • Intelligent packet decoder/assembler and analyzer • Detects attacks in FRAME, TCP, UDP, WWW, etc. Firewall DB Server Application Sys Logs Firewall Assert Client Haxor Firewall (IES GW) Application Sys Logs Assert Client I 1. 1(IP) MDNS (FR) (Private IP Network) Firewall Customer Network Assert Sentry Server Help Desk TEC 37 9. xxx (MPN Internal IBM Net) Accessing Secure e. Business Systems from NMCI Industry Symposium June 2003 Sys. Admins & Build Group Security Notices ASERT - Host Based Intrusion Detection • Detects and prevents attempts to probe services • Prevents unauthorized access to TCP & UDP services Basic Security Module (BSM) • C 2 -level Audit Security © 2003 IBM Corporation

Web Service Architecture for OTS Services § Based on Industry Standards § Platform and implementation neutral to provide true § § § 38 interoperability in a heterogeneous environment Reduces complexity by encapsulation Enables Interoperability by providing the ability to act as a wrapper for the supply side process to legacy applications Optimized for Flexibility in order to adapt to Industry and Navy Standards Reuse of current validation / definition, application, and data access components Well Defined Component-based Architecture separates SOAP middleware, service interface, business logic, and transaction semantics Implementation based on SOAP kernel adapting to new SOAP features Accessing Secure e. Business Systems from NMCI Industry Symposium June 2003 © 2003 IBM Corporation
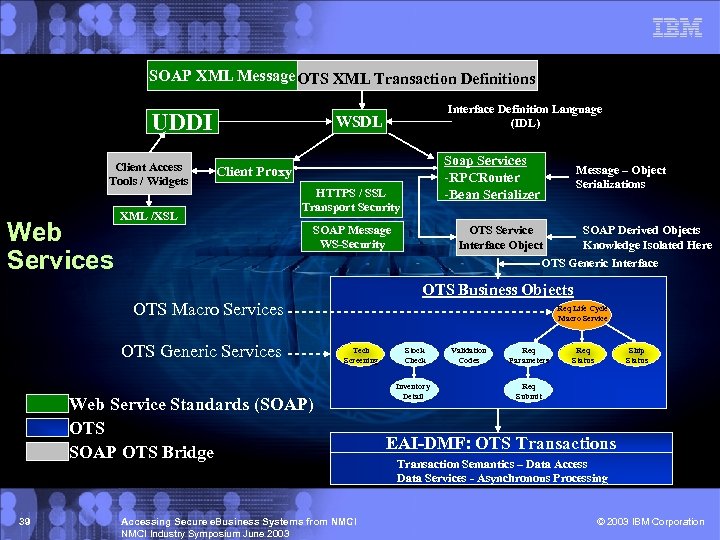
SOAP XML Message OTS XML Transaction Definitions UDDI Client Access Tools / Widgets Web Services Interface Definition Language (IDL) WSDL Soap Services -RPCRouter -Bean Serializer Client Proxy XML /XSL HTTPS / SSL Transport Security SOAP Message WS-Security Message – Object Serializations OTS Service Interface Object SOAP Derived Objects Knowledge Isolated Here OTS Generic Interface OTS Business Objects OTS Macro Services OTS Generic Services Req Life Cycle Macro Service Tech Screening Web Service Standards (SOAP) OTS SOAP OTS Bridge 39 Accessing Secure e. Business Systems from NMCI Industry Symposium June 2003 Stock Check Inventory Detail Validation Codes Req Parameters Req Status Ship Status Req Submit EAI-DMF: OTS Transactions Transaction Semantics – Data Access Data Services - Asynchronous Processing © 2003 IBM Corporation

40 Accessing Secure e. Business Systems from NMCI Industry Symposium June 2003 © 2003 IBM Corporation

business on demand 41 Accessing Secure e. Business Systems from NMCI Industry Symposium June 2003 © 2003 IBM Corporation
9bb6bd0cd67205c2e870dc9f359ff125.ppt