543e0c172ca4ad8ba76983ae3a9709dc.ppt
- Количество слайдов: 42

Building Secure, Flexible and Scalable Environments using LDAP - SANS 2002 - Orlando Sacha Faust Pricewaterhouse. Coopers sacha@severus. org sacha. faust. bourque@ca. pwcglobal. com

LDAP overview l l l 2 History Historical Usage Technical specs

History l l Created by the University of Michigan Evolution – – – 3 1993 : LDAP v 1: RFC 1487: X. 500 Lightweight Directory Access Protocol 1995 : LDAP v 2: RFC 1777: Lightweight Directory Access Protocol 1997 : LDAP v 3: RFC 2251: Lightweight Directory Access Protocol (v 3)

Historical Usage l People-centric information – – l 4 Phone books Personnel Data Large white page applications

Technical specs l l 5 TCP/IP Lightweight Hierarchical structure Easy API

LDAP for a single sign-on environment? l l l 6 Why single sign-on is needed? Why LDAP is a viable solution for single-on? Requirements for an efficient and secure single signon solution Technical challenges for implementing a true singlesign on What can LDAP do to solve the problems?
Why single sign-on is needed? l l 7 Large networks Multiple operating systems Various network devices Centralizing Infrastructure
Why LDAP is a viable solution for single-on? l l 8 Lightweight TCP/IP Open standard Already used to store People-centric information
Requirements for an efficient and secure single sign-on solution l l l 9 Open standard Scalability Access controls Easy to integrate with current infrastructure Easy and reliable API Easy to manage
Technical challenges for implementing a true single-sign on l l l 10 Cross platform support Cross platform user settings Data Synchronization Proprietary authentications Security Schema and organizational structure

What can LDAP do to solve the problems? l l l 11 Open standard Support for SSL Most vendors offer ACL Customizable schema Powerful search capabilities

Test case - ASP environment
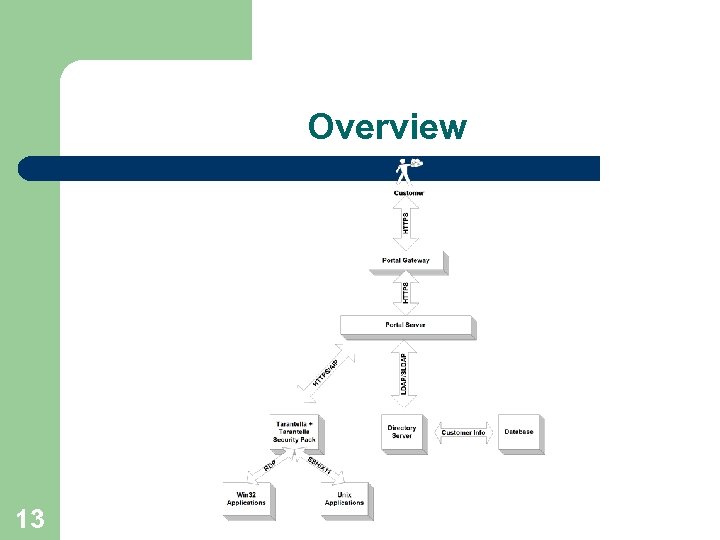
Overview 13
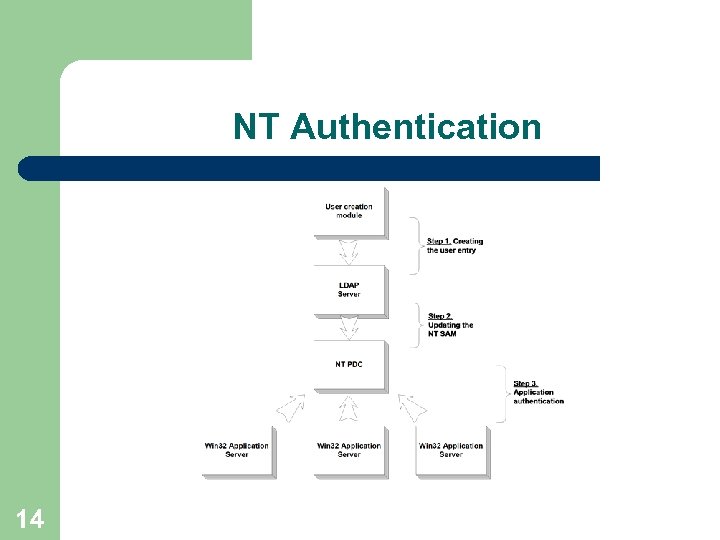
NT Authentication 14
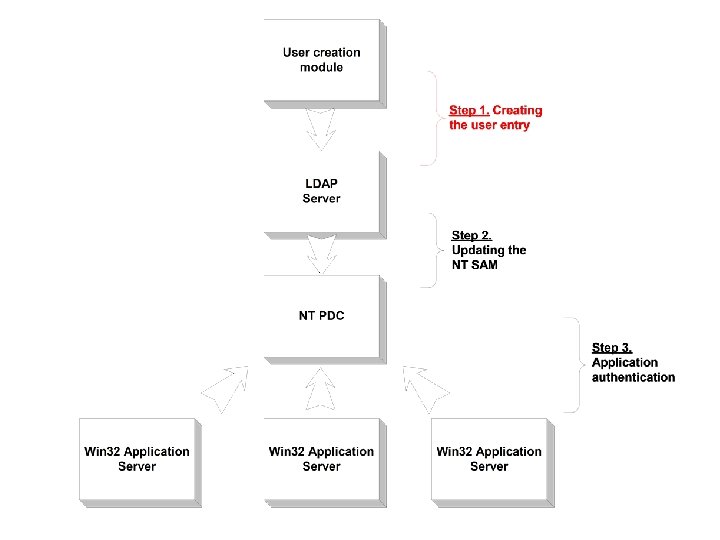
15
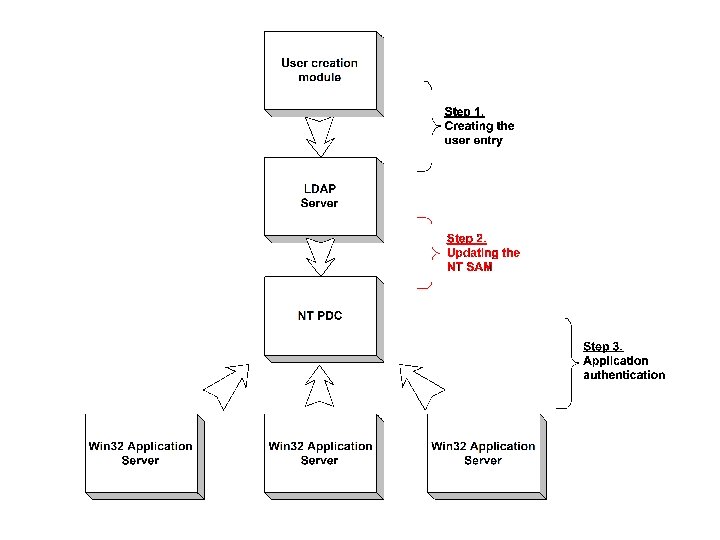
16
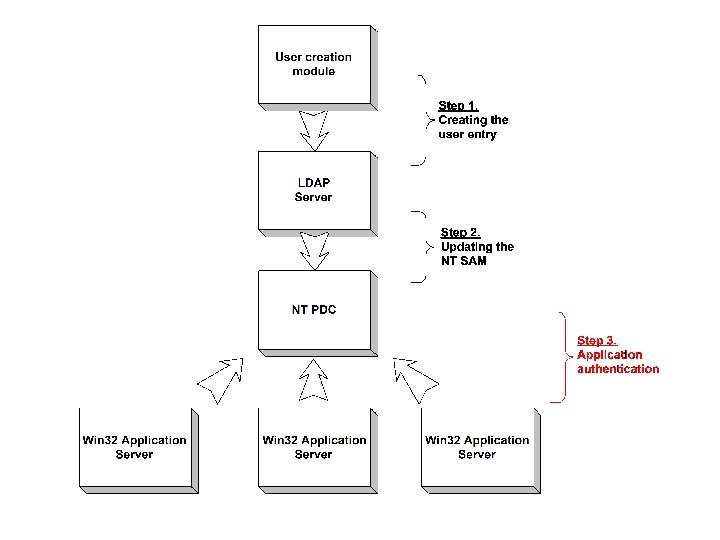
17
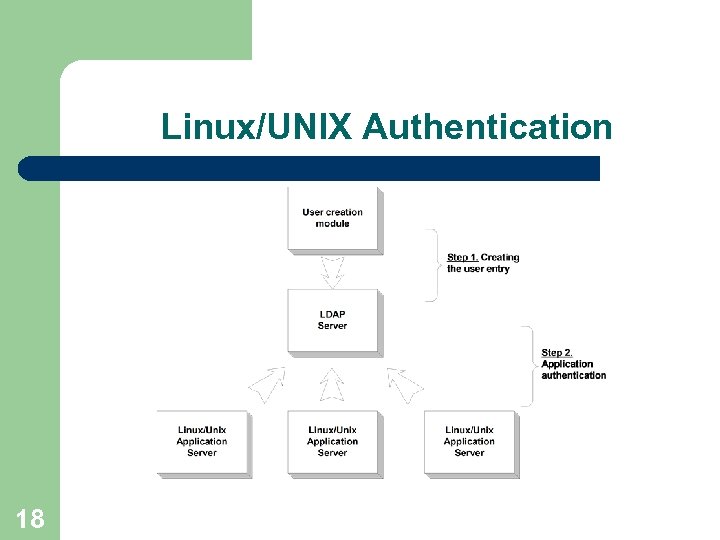
Linux/UNIX Authentication 18
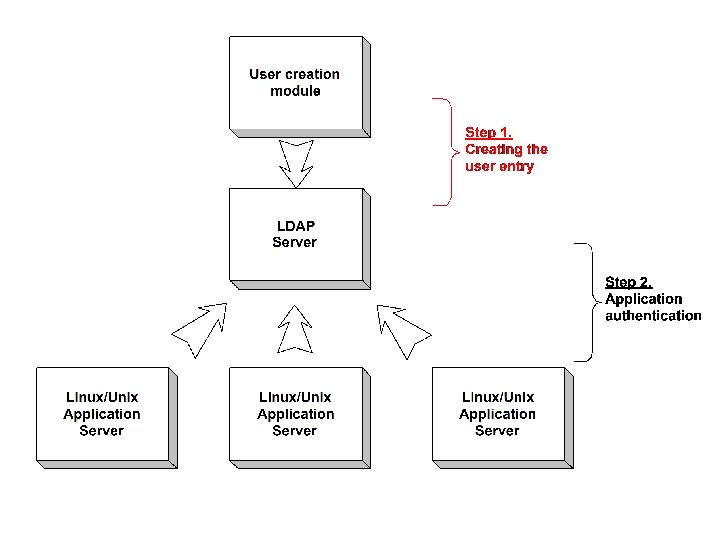
19
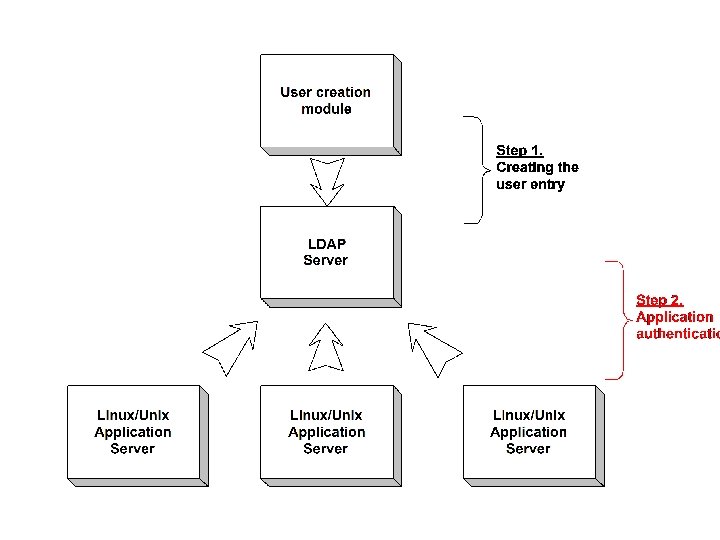
20

Why is this solution better? Advantages l Security – – l l l Flexibility Scalability Financially – – 21 Central control of all users Central point of revocation – Most of the components are available for free use Low management cost Doesn't requirement a lot of administration
Security l l 22 Central control of all users Central point of revocation

Advance topics l LDAP Security – – 23 Steps to secure your LDAP server Special consideration for single sign on

Steps to secure your LDAP server l l 24 1. Identifying requirements 2. Securing the Directory 2. LDAP server host security 3. Network security
1. Identifying requirements l l 25 Network access Types of users and groups Defining data access requirements LDAP schema

Network access l l l 26 Network architecture Identifying member servers and their requirements Identifying Clients and their requirements

Types of users and groups l l l Administration users Read users Write users Member servers Groups – – 27 Static Dynamic
Defining data access requirements l l What can each member server do and see Types of information can users see What attributes the user can change on themselves Data risk level – – – 28 Is the data public? Is the data restricted per organizational units? Is the data used for the infrastructure?

Data risk level l 29 Is the data public? Is the data restricted per organizational units? Is the data used for the infrastructure?

2. Securing the Directory l l 30 Implementing ACL Strong password management
2. LDAP server host security l File system – – – l l l 31 File system ACL Identifying critical data Integrity Non-privilege user Registry (Win 32 only) Limiting services
File system l l l 32 File system ACL Identifying critical data Integrity
3. Network security l Encrypting data – l Authentication – – – 33 SLDAP Basic? Certificate? Anonymous?

Special consideration for single sign on l Security of the object class attributes 1. 2. l 34 NT Authentication using i. Planet Directory Server PAM authentication via LDAP Security of the authentication module

NT Authentication using i. Planet Directory Server

PAM authentication via LDAP

Quick Links l l l 37 Further readings Tools Implementations

Further readings l l l 38 LDAP Overview by Bruce Greenblatt Why LDAP & Security Are Critical to Your Success Solaris 8 LDAP Setup and Configuration Guide IBM Understanding LDAP Securing Netscape Directory Server paper (work in progress)
Tools l l 39 LDAP Browser/Editor LDAPMiner Netscape. Get. ACL LDAPRoot. DSE
Implementations l l 40 Open. LDAP i. Planet Novell e. Directory Tivoli(IBM)

Questions?

Building Secure, Flexible and Scalable Environments using LDAP - SANS 2002 - Orlando Sacha Faust Pricewaterhouse. Coopers sacha@severus. org sacha. faust. bourque@ca. pwcglobal. com
543e0c172ca4ad8ba76983ae3a9709dc.ppt