565120b777cf260c769c9d0d8f61e64e.ppt
- Количество слайдов: 32

Building Better Programmers Andreas Fuchsberger OWASP App. Sec June 2004 NYC Information Security Group Royal Holloway University of London www. isg. rhul. ac. uk Copyright © 2004 - The OWASP Foundation Permission is granted to copy, distribute and/or modify this document under the terms of the GNU Free Documentation License. The OWASP Foundation http: //www. owasp. org
Royal who, where? Tony Blair The Queen Elton John Cliff Richard Royal Holloway OWASP App. Sec 2004

Royal Holloway <Royal Holloway, University of London 41 of the 6 large colleges, part of the University of London 45500 undergraduate and postgraduate students 4 International recognition for research and teaching OWASP App. Sec 2004

ISG OWASP App. Sec 2004

Information Security Group <One of the largest academic information security groups in the world with 20 staff, 5 visiting professors, 5 RAs, and 40 research students <Conducts research into areas such as design and analysis of cryptographic protocols, smart cards, electronic commerce, security management, integration of security into applications <Education and training <Maintain close links and performs contract research and consulting for leading security companies and security users OWASP App. Sec 2004

ISG Activities <Academic research <Ph. D programme <Two MSc programmes <Industrial training programmes <Sponsored research (by Government and/or Industry) <Standards/Government advisory panels <Consultancy OWASP App. Sec 2004

ISG Members <15 Full-time Academics <2 Part-time Academics <1 Senior Visiting Fellow <5 Visiting Professors <5 Consultants <5 Postdoctoral Research Assistants <30+ Research Students OWASP App. Sec 2004

ISG Recognition 1998 Queen’s Anniversary Prize for Higher and Further Education Citation “This pioneering Group provides a unique national resource for the training of information security specialists and the development of highly secure communications and computer systems. It offers world-leading independent expertise in a field of crucial importance where trust and integrity are paramount. ” OWASP App. Sec 2004

But what really put us on the map! Bestseller Gives Boost To Royal Holloway Donald Mac. Leod - Thursday August 7, 2003 A London university is basking in its reputation as a training ground for top sleuths after enthusiastic mentions in a new conspiracy thriller. Following glowing references in The Da Vinci Code, which currently tops the US bestseller lists, Royal Holloway, University of London is hoping for an increase in student applications. In the book, author Dan Brown reveals that his heroine, French cryptographer Sophie Neveu, was trained at what he calls "the Royal Holloway" - and evidently learnt her stuff, to judge by the praise she gets from her fellow spook, the impeccable Brit, Sir Leigh Teabing. OWASP App. Sec 2004

Royal Holloway Information Security Programmes <Ph. D programme <MSc Information Security <MSc Secure Electronic Commerce <Diploma Information Security <Postgraduate Certificate Information Security <Specific training OWASP App. Sec 2004

ISG: Ph. D Programme < Over 100 successful Ph. D students < About 40% had some form of industrial sponsorship < Many hold influential positions in the security industry Current position < 30+ registered students < 10+ overseas (2 Government scholarships) OWASP App. Sec 2004

ISG: Diploma in Information Security <Courses taught by industrial partners <MSc level dissertation <Introduced in 1994 <Over 60 students registered OWASP App. Sec 2004
MSc in Information Security <Started 1992 with industry support 4 Vodafone, 4 Zergo Baltimore, 4 APACS, 4 and other Fo. F OWASP App. Sec 2004
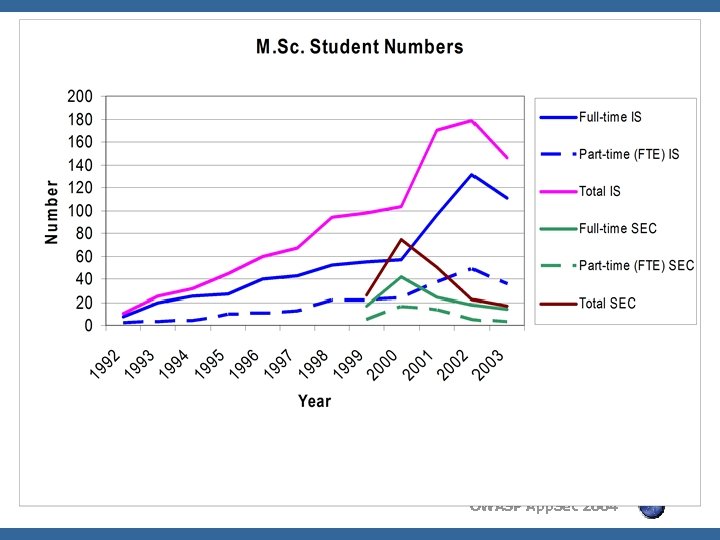
OWASP App. Sec 2004
Who are the students? <Recent graduates <Sponsored students <Career changers <25 -33% annually from outside the EU OWASP App. Sec 2004

MSc – International presence Students from over 30 countries have taken one of the MSc degrees. The largest numbers (outside the UK) are from: < Greece < Hong Kong < Japan < South Korea < Malaysia < Singapore < South Africa < Taiwan < USA OWASP App. Sec 2004
MSc in Information Security – Syllabus <12 month programme <4 core modules 4 Information Security Management 4 Cryptography and Security Mechanisms 4 Computer Security 4 Network Security <Master’s Thesis 43 month research project or documentation of practical aspects of Information Security OWASP App. Sec 2004
Optional Modules – 2 of <Standards and Evaluation Criteria <Advanced Cryptography <Database Security <Computer Crime <Secure Electronic Commerce and other Applications <Smart Card Security <Application/Programming Security OWASP App. Sec 2004
New Optional Module – Application/Programming Security <The aims of the course are: 4 examine the vulnerabilities that exist in computer programs. 4 explore how the development of type-safe and object oriented languages have contributed to the improvement of program security. 4 in particular it will consider the security features of Java 2 Platform and the. NET Framework. OWASP App. Sec 2004

Application/Programming Security < The course will 4 identify the vulnerabilities that can be introduced into programs through language features and poor programming practice; 4 discuss the generic techniques that can be applied to improve the security of programs and applications; 4 consider the specific support provided for developing secure applications in the. NET Framework and Java. < At the end of the course students will be able to 4 explain the importance of security in the development of applications, particularly in the context of distributed software and web services; 4 be able to identify poor programming practice; 4 appreciate the support for secure software development that has been made available to programmers in the. NET Framework and Java. OWASP App. Sec 2004
Background < Review of Program Execution 4 Instruction pointer 4 Memory fetch 4 Process stack 4 Process heap 4 Context switch 4 Memory management 4 User and supervisor mode < The Representation of Data in a Computer < Focus on ambiguities of data representation 4 Bits and bytes 4 Integers 4 Characters < Difference between ASCII and Unicode OWASP App. Sec 2004

Background <Short introduction into compiler theory 4 Lexical analysis 4 Grammar 4 Types 4 Calling conventions 4 Code generation OWASP App. Sec 2004
Vulnerabilities and Attacks < Buffer Overflows < Heap Overflows < Array Bounds Errors < Data Representation Errors < Covert Channels < TOCTOU (Time Of Check to Time Of Use) < SQL Injection < Worms < Viruses < Trojan Horses < Logic Bombs OWASP App. Sec 2004
Countermeasures <Code Analysis <Type-Safe Languages <Object Oriented Languages OWASP App. Sec 2004

Mobile Code <Untrusted and partially trusted code <Sandboxing <Stack inspection <Stack walking <Permissions <Applets <Active. X OWASP App. Sec 2004
Case Study: Java Programming Environment <Features <Java Security Model OWASP App. Sec 2004
Case Study: . NET Framework <. NET Framework Fundamentals < Assemblies < Application Domains < Lifetime of a Secure Application < Runtime Security < Evidence and Code Identity < Permissions < Security Policy < Code-Access Security < Role-Based Security < Isolated Storage OWASP App. Sec 2004

Designing Secure Web Applications < Architecture and Design Issues for Web Applications < Deployment Considerations < Input Validation < Cross Site Scripting < Authentication < Authorisation < Sensitive Data < Session Management < Parameter Manipulation < Exception Management < Auditing and Logging OWASP App. Sec 2004
Building Secure Web Services <Protocols and Standards <Web Services & Security <Security Activities <Threats <XML Security Standards <XML DIGSIG <Web Services Security Requirements <WS-Standards <Web Services Security Architecture OWASP App. Sec 2004

Deployment and Configuration OWASP App. Sec 2004
Programming Cryptography <Implementing Algorithms <Java Cryptography Extension (JCE) 1. 2. 1 API <Microsoft Cryptographic API <. NET Framework Cryptography OWASP App. Sec 2004
Summary OWASP App. Sec 2004
565120b777cf260c769c9d0d8f61e64e.ppt