fe03d0e513b91473e51d1c6d5ecbfadf.ppt
- Количество слайдов: 48

British Computer Society NORTH LONDON BRANCH Aud. IT to Benef. IT - 6 sides of the dice Wednesday 16 th January 2008, 18. 30 – 20. 30 1 topic, 2 hours, 4 sponsors 6 views, 6 expert presenters 1 great audience

British Computer Society NORTH LONDON BRANCH Are You an Auditor?

British Computer Society NORTH LONDON BRANCH 4 Sponsors: • * Gotham Digital Science www. gdssecurity. com * • * ISACA London Chapter www. isaca-london. org * • *IT Faculty of the Institute of Chartered Accountants in England Wales www. icaew. com/itfac* • * SUPINFO The International Institute of Information Technology www. supinfo. com/uk *

British Computer Society NORTH LONDON BRANCH 6 Views – plus more! • [Target start time 18. 30] • BCS NLB Intro [10 mins. ] - Dalim • Why audit? Who needs it? [15 mins. ] - Justin • What does the auditor do? [15 mins. ] - Nick • What’s audited? [20 mins. ] - Fraser • IT audit tools and techniques [15 mins. ] - Martin • How auditors use COBIT & IT Assurance Guide [15] Lynn • How to plan to get value from your audits [15] - Steven • BCS NLB end of formal event [10 mins. ] - Dalim • [Target end time 20. 30] • Informal networking (with food & drink) ALL

British Computer Society NORTH LONDON BRANCH 6 Expert Presenters • 1. 2. 3. 4. 5. 6. • [MC] Dalim Basu, BCS NLB FRASER NICOL, Ernst & Young JUSTIN CLARKE, Gotham Digital Science LYNN LAWTON, ISACA MARTIN ALLEN, Pw. C NICK FELLOWS, Barclays Plc STEVEN BABB, KPMG & ISACA [Supporting Cast: NLB team for this event] Jude Umeh, Patrick Roberts, Rebecca King

Why audit? Who needs it? Justin Clarke, Director CISA, CISM, CISSP, A. Inst. ISP © 2007 Gotham Digital Science Ltd

What is an audit? § Anyone? § A Definition § An audit is a professional, independent examination of a company's financial statements and accounting documents according to generally accepted accounting principles (Traditional) § an evaluation of a person, organization, system, process, project or product. Audits are performed to ascertain the validity and reliability of information, and also provide an assessment of a system's internal control (Wikipedia) © 2007 Gotham Digital Science Ltd 7

Understanding your auditor § Internal or External? § Assurance or Audit? § Key ideas – Independence – Reasonable assurance – Material error – Evidence – Testing/Sampling © 2007 Gotham Digital Science Ltd 8

Why audit? § Mitigate risk § Regulatory/legal - financial § Measurement/management – Conformity/Compliance – Quality – Environmental § How are we doing? © 2007 Gotham Digital Science Ltd 9

Who needs it? § Organisations – Large and small – Private, public and government § Stakeholders – Shareholders – Management – Tax payers © 2007 Gotham Digital Science Ltd 10

Types of audit § External – ITGC, ITAC, SAS 70 § Internal – Operational, Business Process, Cob. IT, COSO § Regulatory - Sarbanes Oxley, Basel II, Mi. FID § Conformity/Compliance – ISO 17799/27001 § Quality – ISO 9001 § Environmental – ISO 14001 © 2007 Gotham Digital Science Ltd 11

Contact © 2007 Gotham Digital Science Ltd 12

Exploring the world of Internal Audit What does the auditor do and why? Nick Fellows, CISA - Audit Manager 16 January 2008
Agenda • The Audit Charter • The Audit Universe and the Audit Plan • This audit

The Audit Charter This is a document that defines the Internal Audit function Its purpose, responsibility, authority and accountability. • What we are there to do • How we will maintain our independence and objectivity • How we will do it and conduct ourselves whilst doing it • The relationship between IA and its stakeholders • The KPIs, what they are and how they are measured Standard S 1 and Guideline G 5 for Audit Charter can be found on the ISACA website www. isaca. org

The Audit Universe and the Audit Plan How does the audit department work out what to do? • Populate the audit universe • Prioritise based on risk ranking • Plan • Agree with stakeholders and get sign off from the Board Audit Committee
The audit • Understanding the processes, working out the key controls. • The ‘intention to audit’. • Testing the controls. • And the consequence was… • The report and follow up actions.
Closing thoughts • Risks are mitigated by controls. Whose controls? – yours. • An audit is not something that is done to you. It is something that is done with you. • The more you prepare, the less painful the review will be.

What is Audited? Fraser Nicol – Technology Security and Risk Services, Ernst and Young Aud. IT to Benef. IT Presentation to British Computer Society

IT audit – who, why, what and how? • Internal auditing – is an independent, objective assurance and consulting activity designed to add value and improve an organisations operations • External auditing – is an independent opinion on whether or not financial statements are relevant, accurate, complete, and fairly presented • Both approaches are characterised by a systematic approach to the evaluation of risk management, control and governance processes. A common industry standard for IT auditing is: • COBIT 4. 1 – Control Objectives for Information and Related Technology. Set of leading practises (framework) for information technology (IT) management. Created and governed by Information Systems Audit and Control Association (ISACA). COBIT is organised into 4 domains: – Plan and Organise – Acquire and Implement – Delivery and Support – Monitor and Evaluate
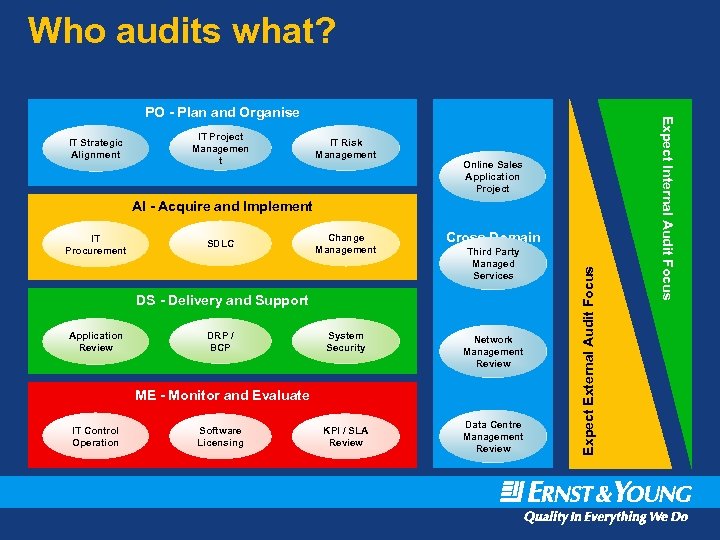
Who audits what? IT Strategic Alignment IT Project Managemen t IT Risk Management Online Sales Application Project AI - Acquire and Implement SDLC Change Management Cross Domain Third Party Reviews Managed Services DS - Delivery and Support Application Review DRP / BCP System Security Network Management Review ME - Monitor and Evaluate IT Control Operation Software Licensing KPI / SLA Review Data Centre Management Review Expect External Audit Focus IT Procurement Expect Internal Audit Focus PO - Plan and Organise
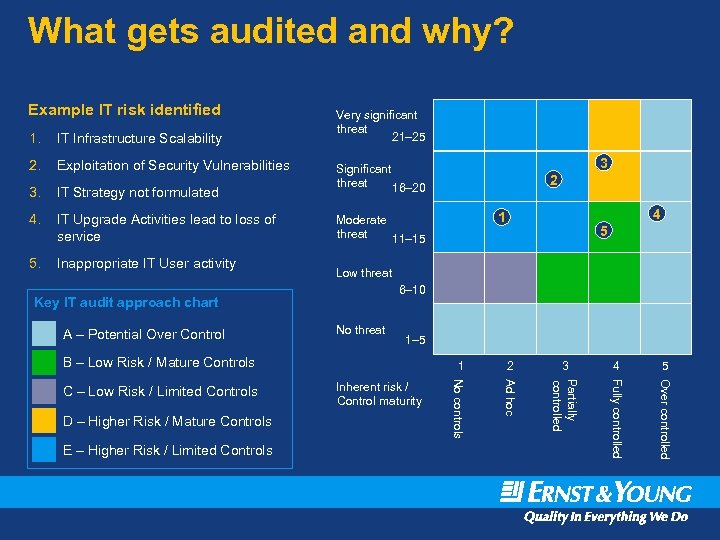
What gets audited and why? Example IT risk identified Very significant threat 21– 25 1. IT Infrastructure Scalability 2. Exploitation of Security Vulnerabilities 3. IT Strategy not formulated Significant threat 16– 20 4. IT Upgrade Activities lead to loss of service Moderate threat 11– 15 5. Inappropriate IT User activity No threat 1– 5 1 3 4 5 Partially controlled Fully controlled Over controlled Inherent risk / Control maturity 2 Ad hoc E – Higher Risk / Limited Controls 5 No controls D – Higher Risk / Mature Controls 4 1 6– 10 B – Low Risk / Mature Controls C – Low Risk / Limited Controls 2 Low threat Key IT audit approach chart A – Potential Over Control 3
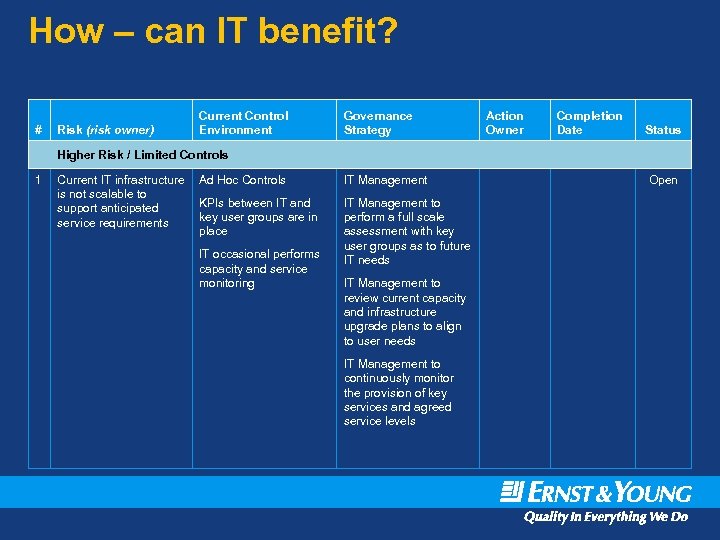
How – can IT benefit? # Risk (risk owner) Current Control Environment Governance Strategy Action Owner Completion Date Status Higher Risk / Limited Controls 1 Current IT infrastructure is not scalable to support anticipated service requirements Ad Hoc Controls IT Management KPIs between IT and key user groups are in place IT Management to perform a full scale assessment with key user groups as to future IT needs IT occasional performs capacity and service monitoring IT Management to review current capacity and infrastructure upgrade plans to align to user needs IT Management to continuously monitor the provision of key services and agreed service levels Open

Summary • Understand who the auditors are, what they are looking for, and what the output of the audit is going to be • Understand the risks to your own areas, be proactive in engaging with the auditors to explain your area and align their understanding of key risks with yours • Early planning is always performed at a high level, sometimes the principle actions sit with IT or the business. You need to be involved as closely as possible in audit planning to
Contact Fraser Nicol, Senior Manager Tel: 020 7951 0748 Mob: 07776047344 fnicol@uk. ey. com

Tools and Techniques Martin Allen FIIA, Qi. CA, CISA 16 January 2008 Pricewaterhouse. Coopers LLP Pw. C
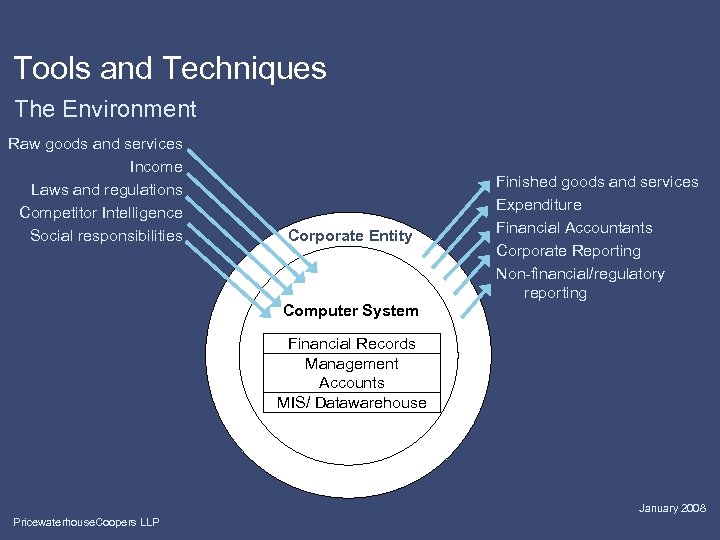
Tools and Techniques The Environment Raw goods and services Income Laws and regulations Competitor Intelligence Social responsibilities Corporate Entity Finished goods and services Expenditure Financial Accountants Corporate Reporting Non-financial/regulatory reporting Computer System Financial Records Management Accounts MIS/ Datawarehouse January 2008 Pricewaterhouse. Coopers LLP
Tools and Techniques Indicators that computer tools and techniques would help audit process: • Requirement to analyse large volumes of data or complex calculations • Reliance upon reports generated from computer systems • ‘Black box’ style systems where complex processing of data is not transparent • Key reconciliation reports regularly highlight differences • New or modified systems • Interfaces between computer systems poorly controlled January 2008 Pricewaterhouse. Coopers LLP

Tools and Techniques Tools available on the desktop: • Spreadsheets • Databases • MS Query January 2008 Pricewaterhouse. Coopers LLP

Tools and Techniques Tools that can be acquired: • • IDEA ACL OAK Datanomic January 2008 Pricewaterhouse. Coopers LLP

Tools and Techniques Risks: • Can allow the auditor to reach the wrong conclusion • Easy for inexperienced auditors to be caught out • Data interrogation does not test controls Benefits: • Allows 100% sample size • Allows quick identification of unusual or required data • Allows auditor to use the power of the computer to improve the efficiency and effectiveness of the audit January 2008 Pricewaterhouse. Coopers LLP
This publication has been prepared for general guidance on matters of interest only, and does not constitute professional advice. You should not act upon the information contained in this publication without obtaining specific professional advice. No representation or warranty (express or implied) is given as to the accuracy or completeness of the information contained in this publication, and, to the extent permitted by law, Pricewaterhouse. Coopers LLP, its members, employees and agents accept no liability, and disclaim all responsibility, for the consequences of you or anyone else acting, or refraining to act, in reliance on the information contained in this publication or for any decision based on it. © 2008 Pricewaterhouse. Coopers LLP. All rights reserved. 'Pricewaterhouse. Coopers' refers to Pricewaterhouse. Coopers LLP (a limited liability partnership in the United Kingdom) or, as the context requires, other member firms of Pricewaterhouse. Coopers International Limited, each of Pricewaterhouse. Coopers LLPwhich is a separate and independent legal entity. Pw. C

How Auditors use COBIT and the IT Assurance Guide ® Lynn Lawton, International President ISACA, Inc, and The IT Governance Institute, Inc. © 2008 IT Governance Institute. All rights reserved. 33

ISACA and The IT Governance Institute • Over 70, 000 members in 140 countries • Develop and maintain tools for IT and business management, e. g. COBIT and Val. IT • Develop and administer certifications, e. g. CISA, CISM, and, coming soon, CGEIT • Deliver conferences and educational events around the world • Deliver research and thought leadership on topical issues • www. isaca. org and www. itgi. org © 2008 IT Governance Institute. All rights reserved. 34
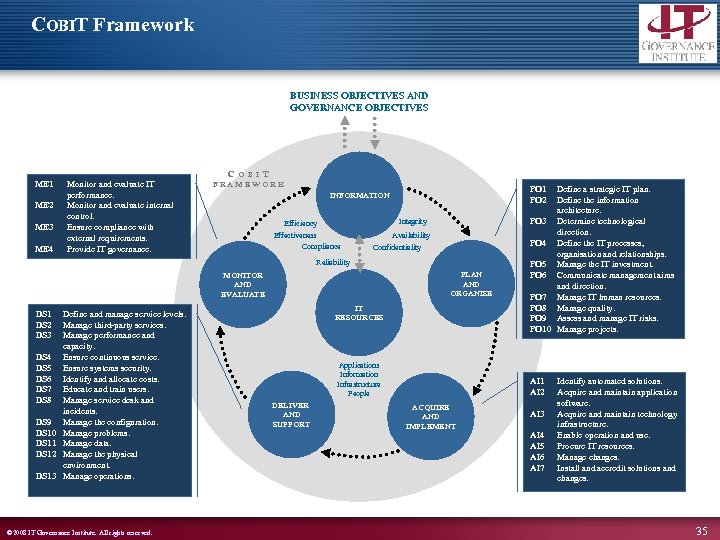
COBIT Framework BUSINESS OBJECTIVES AND GOVERNANCE OBJECTIVES C ME 1 ME 2 ME 3 ME 4 Monitor and evaluate IT performance. Monitor and evaluate internal control. Ensure compliance with external requirements. Provide IT governance. O B I T FRAMEWORK PO 1 PO 2 INFORMATION Integrity Efficiency Effectiveness Compliance Availability Confidentiality Reliability PLAN AND ORGANISE MONITOR AND EVALUATE DS 1 DS 2 DS 3 DS 4 DS 5 DS 6 DS 7 DS 8 DS 9 DS 10 DS 11 DS 12 DS 13 Define and manage service levels. Manage third-party services. Manage performance and capacity. Ensure continuous service. Ensure systems security. Identify and allocate costs. Educate and train users. Manage service desk and incidents. Manage the configuration. Manage problems. Manage data. Manage the physical environment. Manage operations. © 2008 IT Governance Institute. All rights reserved. IT RESOURCES Applications Information Infrastructure People DELIVER AND SUPPORT Define a strategic IT plan. Define the information architecture. PO 3 Determine technological direction. PO 4 Define the IT processes, organisation and relationships. PO 5 Manage the IT investment. PO 6 Communicate management aims and direction. PO 7 Manage IT human resources. PO 8 Manage quality. PO 9 Assess and manage IT risks. PO 10 Manage projects. AI 1 AI 2 ACQUIRE AND IMPLEMENT AI 3 AI 4 AI 5 AI 6 AI 7 Identify automated solutions. Acquire and maintain application software. Acquire and maintain technology infrastructure. Enable operation and use. Procure IT resources. Manage changes. Install and accredit solutions and changes. 35
© 2008 IT Governance Institute. All rights reserved. 36
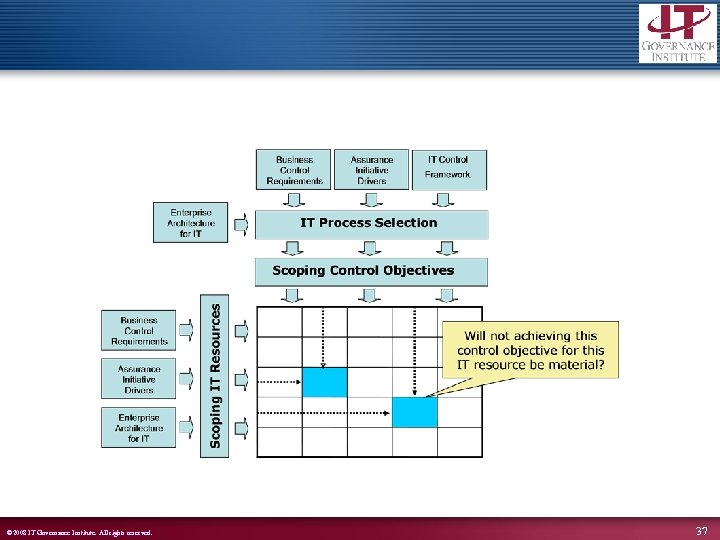
© 2008 IT Governance Institute. All rights reserved. 37
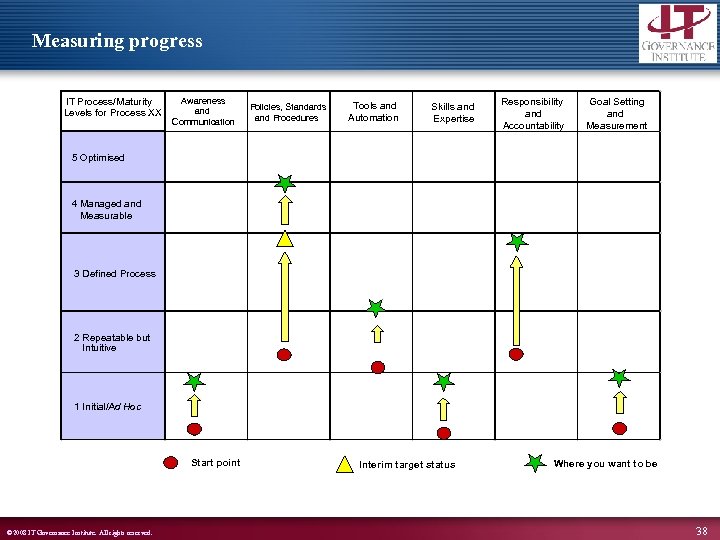
Measuring progress IT Process/Maturity Levels for Process XX Awareness and Communication Policies, Standards and Procedures Tools and Automation Skills and Expertise Responsibility and Accountability Goal Setting and Measurement 5 Optimised 4 Managed and Measurable 3 Defined Process 2 Repeatable but Intuitive 1 Initial/Ad Hoc Start point © 2008 IT Governance Institute. All rights reserved. Interim target status Where you want to be 38
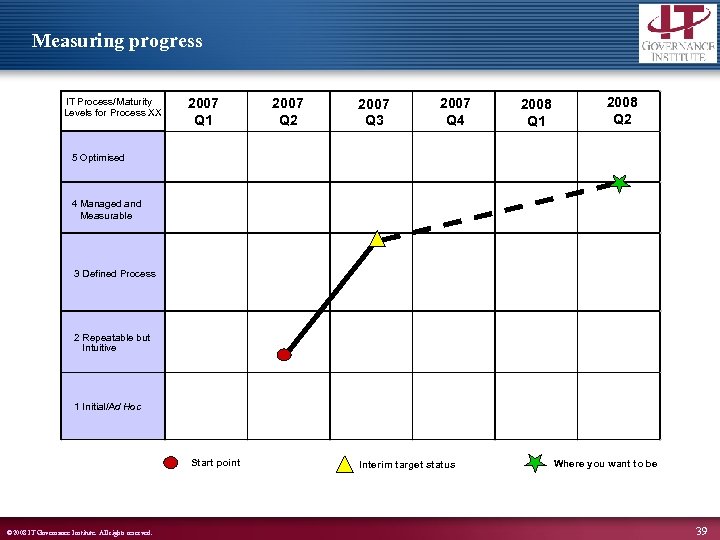
Measuring progress IT Process/Maturity Levels for Process XX 2007 Q 1 2007 Q 2 2007 Q 3 2007 Q 4 2008 Q 1 2008 Q 2 5 Optimised 4 Managed and Measurable 3 Defined Process 2 Repeatable but Intuitive 1 Initial/Ad Hoc Start point © 2008 IT Governance Institute. All rights reserved. Interim target status Where you want to be 39
ISACA and The IT Governance Institute For more information, visit: www. isaca. org www. itgi. org © 2008 IT Governance Institute. All rights reserved. 40

How to plan to get value from your audits 16 January 2008 AUDIT

Disclaimer The information contained herein is of a general nature and is not intended to address the circumstances of any particular individual or entity. Although we endeavour to provide accurate and timely information, there can be no guarantee that such information is accurate as of the date it is received or that it will continue to be accurate in the future. No one should act on such information without appropriate professional advice after a thorough examination of the particular situation. © 2008 KPMG LLP, a UK limited liability partnership, is a subsidiary of KPMG Europe LLP and a member firm of the KPMG network of independent member firms affiliated with KPMG International, a Swiss cooperative. All rights reserved. This document is confidential and its circulation and use are restricted. KPMG and the KPMG logo are registered trademarks of KPMG International, a Swiss cooperative. 42

Agenda l Recap – What is audit? l Pre-audit activities l During the audit l What happens next? © 2008 KPMG LLP, a UK limited liability partnership, is a subsidiary of KPMG Europe LLP and a member firm of the KPMG network of independent member firms affiliated with KPMG International, a Swiss cooperative. All rights reserved. This document is confidential and its circulation and use are restricted. KPMG and the KPMG logo are registered trademarks of KPMG International, a Swiss cooperative. 43

Recap – What is audit? l Internal auditing - Internal, yet independent assurance over internal controls - Designed to add value and improve an organisations operations l External auditing - External, independent opinion over financial statements l Audit should be viewed as a critical friend rather than a hindrance l It can add value to your organisation – so treat it this way l An audit is not something that is done to you; It is something that is done with you © 2008 KPMG LLP, a UK limited liability partnership, is a subsidiary of KPMG Europe LLP and a member firm of the KPMG network of independent member firms affiliated with KPMG International, a Swiss cooperative. All rights reserved. This document is confidential and its circulation and use are restricted. KPMG and the KPMG logo are registered trademarks of KPMG International, a Swiss cooperative. 44

Pre-audit activities What to do before the audit takes place l Understand who the auditors are, their scope, objectives and deliverables - Get involved in audit planning – understand the risks and issues in your own areas - You can influence – are there any areas you want covered? l Plan – The more you prepare, the less painful the review will be l Have a central point of contact l Confirm logistical arrangements © 2008 KPMG LLP, a UK limited liability partnership, is a subsidiary of KPMG Europe LLP and a member firm of the KPMG network of independent member firms affiliated with KPMG International, a Swiss cooperative. All rights reserved. This document is confidential and its circulation and use are restricted. KPMG and the KPMG logo are registered trademarks of KPMG International, a Swiss cooperative. 45

During the audit Maintain contact with your auditors l The central point of contact will be key in ensuring a smooth audit l Arrange regular catch-up meetings l Understand what the key findings are - Have the auditors got a clear handle on the risks? - Are the key findings valid? l Is the audit on track? l What are the next steps? © 2008 KPMG LLP, a UK limited liability partnership, is a subsidiary of KPMG Europe LLP and a member firm of the KPMG network of independent member firms affiliated with KPMG International, a Swiss cooperative. All rights reserved. This document is confidential and its circulation and use are restricted. KPMG and the KPMG logo are registered trademarks of KPMG International, a Swiss cooperative. 46

What happens next? How to reap the benefits for your organisation l Ensure that you get to review findings - Draft report stage l Be positive about the findings – Don’t take the outcome as personal criticism l Prepare a plan to address any issues identified and publish it – make sure the plan is implemented! l Roll-out learning points across your organisation, wherever possible l Prepare for your next audit! © 2008 KPMG LLP, a UK limited liability partnership, is a subsidiary of KPMG Europe LLP and a member firm of the KPMG network of independent member firms affiliated with KPMG International, a Swiss cooperative. All rights reserved. This document is confidential and its circulation and use are restricted. KPMG and the KPMG logo are registered trademarks of KPMG International, a Swiss cooperative. 47

Presenter’s contact details Steven Babb KPMG LLP (UK) +44 (0)7717 511 554 steven. babb@kpmg. co. uk www. kpmg. co. uk © 2008 KPMG LLP, a UK limited liability partnership, is a subsidiary of KPMG Europe LLP and a member firm of the KPMG network of independent member firms affiliated with KPMG International, a Swiss cooperative. All rights reserved. This document is confidential and its circulation and use are restricted. KPMG and the KPMG logo are registered trademarks of KPMG International, a Swiss cooperative.
fe03d0e513b91473e51d1c6d5ecbfadf.ppt