32c7b5a2c716ef836303de4c526be096.ppt
- Количество слайдов: 36

Bots, viruses, and spam: The converged threat and how to fight it January 27, 2005
Bots, viruses, and spam AGENDA 1. 2. 3. 4. 5. 6. 2 Introduction. What is a botnet? What are botnets used for? Who is behind this? How we can fight them. Conclusion/Q&A
Spokane Helena Seattle Green Bay Minneapolis Billings Montreal Toronto Portland Detroit Milwaukee Buffalo Eugene Casper Medford Redding Chico Oakland Salt Lake City Reno Denver Sacramento San Francisco Colorado Springs Sunnyvale San Jose Salinas San Luis Obispo Santa Barbara Los Angeles Des Moines Omaha Lincoln Anaheim San Diego Tijuana Albuquerque El Paso Akron St. Louis Bowling Green Nashville Tulsa Oklahoma City Chattanooga Dallas Fort Worth Austin San Antonio Houston Monterrey Mazatlan Cities Connected Connecting Systems IP POP Guadalajara Mexico City Global Crossing North America – 3 Dedicated Internet Access/IP Transit Rocky Mount Raleigh Mobile Jacksonville Tallahassee Orlando Newark Trenton Philadelphia Washington DC Atlanta Tampa Legend New York Pittsburgh Altoona Greensboro Charlotte Greenville New Orleans Boston Albany Columbus Dayton Baltimore Cincinnati Fredericksburg Louisville Richmond Chesapeake Macon Baton Rouge Landing Points Cities Connected (Switch Sites) Cleveland Kansas City Topeka Syracuse Erie Toledo Indianapolis Phoenix Tucson Chicago Rochester Daytona Beach Melbourne Fort Lauderdale Miami
St. Croix Ft. Amador Panama City Puerto Viejo Caracas Fortaleza Lima Lurin São Paulo Santos Legend Landing Points Cities Connected Connecting Systems IP POP Global Crossing South America – 4 Dedicated Internet Access/IP Transit Rio De Janeiro Valparaiso Santiago Buenos Aires Las Toninas
Legend Landing Points Cities Connected Connecting Systems IP POP Aberdeen Glasgow Edinburgh Carlisle Newcastle Middlesbrough Preston Dublin Liverpool Manchester Kilmore Quay Derby Bristol Bude Reading London Southampton Exeter Basingstoke Brighton Plymouth Whitesands Global Crossing UK – 5 Dedicated Internet Access/IP Transit Beverwijk Peterborough Birmingham Wexford York Leeds Sheffield Nottingham Norwich Amsterdam Southend Rotterdam Dover Antwerp Brussels
Stockholm Oslo Aberdeen Copenhagen Edinburgh Glasgow Sylt Dublin Kilmore Quay Liverpool Wexford Bristol Beverwijk London Bude Whitesands Paris Hamburg Berlin Hannover Amsterdam Dusseldorf Cologne Dresden Rotterdam Leipzig Antwerp Frankfurt Brussels Nuremberg Strasbourg Munich Stuttgart Zurich Lyon Geneva Turin Legend Landing Points Cities Connected Connecting Systems IP POP Marseilles Barcelona Madrid Global Crossing Europe – 6 Dedicated Internet Access/IP Transit Milan

Bots, viruses, and spam Percentage of email that is spam: 2002: 9%. 2003: 40%. 2004: 73%. Percentage of email containing viruses: 2002: 0. 5%. 2003: 3%. 2004: 6. 1%. Number of phishing emails: Total through September 2003: 273 Total through September 2004: >2 million Monthly since September 2004: 2 -5 million (Above from Message. Labs 2004 end-of-year report. ) Denial of Service Attacks: 2002: 48. 2003: 409. 2004: 482. Jan. 1 -26, 2005: 25. (Above from Global Crossing; 2002 is for Oct-Dec only. ) 7
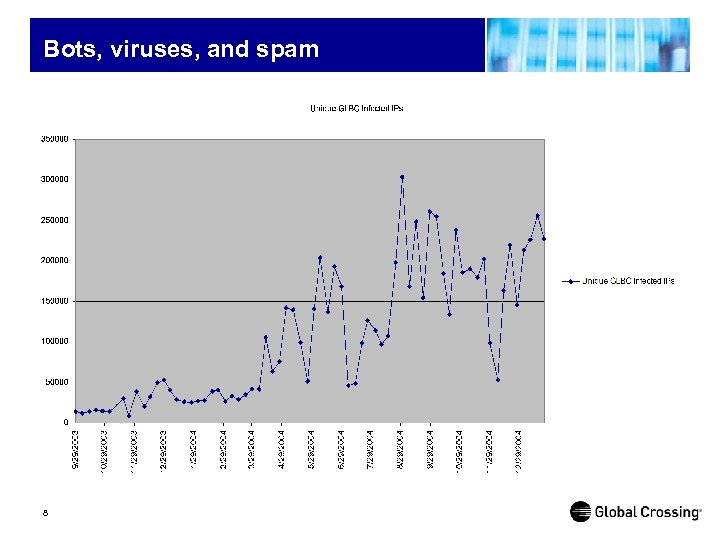
Bots, viruses, and spam 8
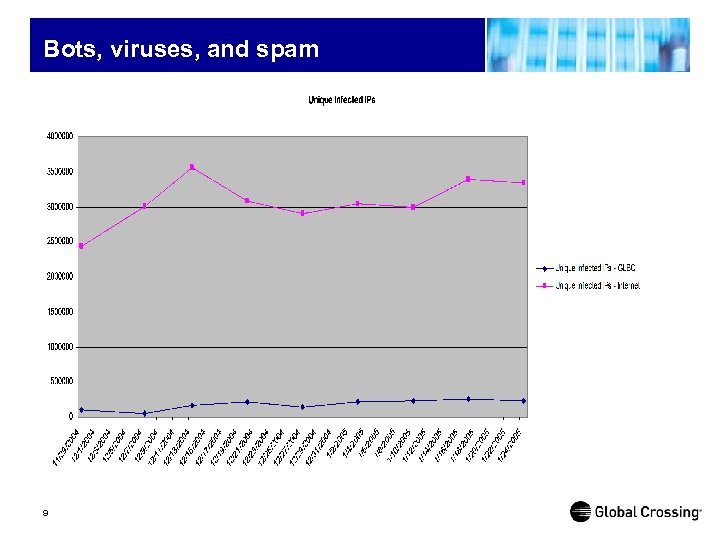
Bots, viruses, and spam 9
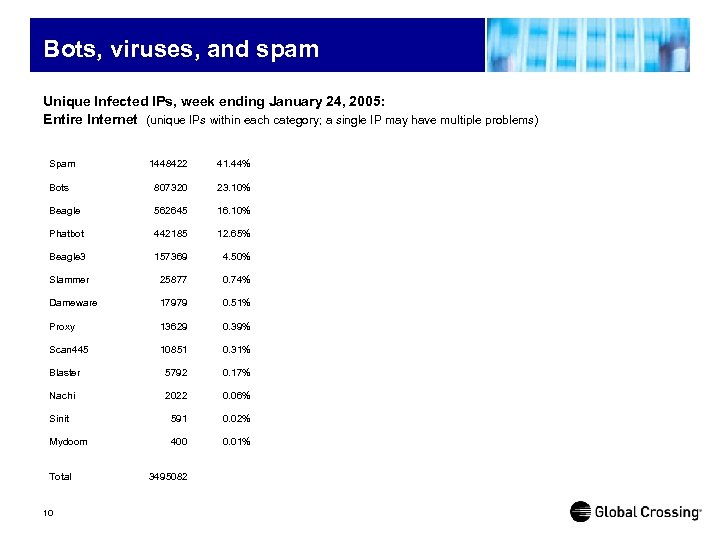
Bots, viruses, and spam Unique Infected IPs, week ending January 24, 2005: Entire Internet (unique IPs within each category; a single IP may have multiple problems) Spam 1448422 41. 44% Bots 807320 23. 10% Beagle 562645 16. 10% Phatbot 442185 12. 65% Beagle 3 157369 4. 50% Slammer 25877 0. 74% Dameware 17979 0. 51% Proxy 13629 0. 39% Scan 445 10851 0. 31% Blaster 5792 0. 17% Nachi 2022 0. 06% Sinit 591 0. 02% Mydoom 400 0. 01% Total 10 3495082

Bots, viruses, and spam What do viruses, worms, spams, phishing, and denial of service attacks have in common? All are associated with bots and botnets. All are being used to get criminals what they want: • Your clean (not listed on blacklists) IP addresses. • Your accounts and passwords. • Your money. • Your identity. • The ability to continue getting these things without being caught. 11

Bots, viruses, and spam What is a botnet? A collection of compromised systems (“bots”) under the control of a single entity who uses a central controller (“botnet controller”) to issue commands to the bots. Bots are almost always compromised Windows machines—they may be compromised by worms, viruses, trojan horses, or automated or semi-automated attack tools exploiting common Windows vulnerabilities. Botnet controllers are almost always compromised Unix machines—most often compromised by automated or semi-automated attack tools exploiting common Unix vulnerabilities. The method of control is almost always IRC, usually on standard IRC ports (TCP 6667 -up). When the use of botnets is sold to third parties, there is often a nice, professional-looking Windows or web interface provided. 12

Bots, viruses, and spam Phatbot command list (from LURHQ) bot. command runs a command with system() bot. unsecure enable shares / enable dcom bot. secure delete shares / disable dcom bot. flushdns flushes the bots dns cache bot. quits the bot. longuptime If uptime > 7 days then bot will respond bot. sysinfo displays the system info bot. status gives status ot. rndnick makes the bot generate a new random nick bot. removeallbut removes the bot if id does not match bot. removes the bot. opens a file (whatever) bot. nick changes the nickname of the bot. id displays the id of the current code bot. execute makes the bot execute a. exe bot. dns resolves ip/hostname by dns bot. die terminates the bot. about displays the info the author wants you to see shell. disable Disable shell handler shell. enable Enable shell handler shell. handler Fall. Back handler for shell commands. list Lists all available commands plugin. unloads a plugin (not supported yet) plugin. loads a plugin cvar. saveconfig saves config to a file cvar. loadconfig loads config from a file cvar. sets the content of a cvar. gets the content of a cvar. list prints a list of all cvars inst. svcdel deletes a service from scm inst. svcadd adds a service to scm inst. asdel deletes an autostart entry inst. asadd adds an autostart entry logic. ifuptime exec command if uptime is bigger than specified mac. login logs the user in mac. logout logs the user out ftp. update executes a file from a ftp url ftp. execute updates the bot from a ftp url ftp. downloads a file from ftp http. visits an url with a specified referrer http. update executes a file from a http url http. execute updates the bot from a http url 13 http. downloads a file from http rsl. logoff logs the user off rsl. shutdown shuts the computer down rsl. reboots the computer pctrl. kills a process pctrl. lists all processes scan. stop signal stop to child threads scan. start signal start to child threads scan. disables a scanner module scan. enables a scanner module scan. clearnetranges clears all netranges registered with the scanner scan. resetnetranges resets netranges to the localhost scan. listnetranges lists all netranges registered with the scanner scan. delnetrange deletes a netrange from the scanner scan. addnetrange adds a netrange to the scanner ddos. phatwonk starts phatwonk flood ddos. phaticmp starts phaticmp flood ddos. phatsyn starts phatsyn flood ddos. stops all floods ddos. httpflood starts a HTTP flood ddos. synflood starts an SYN flood ddos. udpflood starts a UDP flood redirect. stops all redirects running redirect. socks starts a socks 4 proxy redirect. https starts a https proxy redirect. http starts a http proxy redirect. gre starts a gre redirect. tcp starts a tcp port redirect harvest. aol makes the bot get aol stuff harvest. cdkeys makes the bot get a list of cdkeys harvest. emailshttp makes the bot get a list of emails via http harvest. emails makes the bot get a list of emails waste. server changes the server the bot connects to waste. reconnects to the server waste. raw sends a raw message to the waste server waste. quit waste. privmsg sends a privmsg waste. part makes the bot part a channel waste. netinfo prints netinfo waste. mode lets the bot perform a mode change waste. join makes the bot join a channel waste. gethost prints netinfo when host matches waste. getedu prints netinfo when the bot is. edu waste. action lets the bot perform an action waste. disconnects the bot from waste

Bots, viruses, and spam What are bots used for? They are a disposable platform of computing power, usable for: • Scanning for other vulnerable systems to create more bots. • Collecting information from the compromised system (accounts, passwords). • Operating as proxies for sending spam (including phishing attacks), or launching new worms or viruses. • Launching denial of service attacks (to attack competition or commit extortion). • Distribution of pirated or illegal material. They can be used for anything the controlling entity wants to use them for— and the activity will be attributed to the bot rather than the controlling entity. They refute the argument that “There’s nothing on my computer that anyone would want” (usually given as an excuse not to secure a home computer). 14

Bots, viruses, and spam Who is behind this? • Criminal hackers: They write the worms, viruses, and trojan horses, and act as “botnet wranglers. ” • Criminal spammers: They pay criminal hackers to obtain mailing lists and for the use of botnets to use as proxies (or “peas”) for sending spam. • Organized crime: They hire or have their own criminal hackers to engage in online protection rackets, credit card fraud, and identity theft. The underground economy is fueled by money, derived from sale of spammed products, direct theft from online bank accounts, credit card fraud, and denial of service attack extortion. The main tool used to commit the crime and create a buffer between the criminal and his actions is the bot. 15

Bots, viruses, worms What are the direct connections between the criminal and the Internet? • Purchase of colo space, often in carrier hotels. • Sometimes, in interactions with others in the underground economy (e. g. , spammer/hacker interactions). • Sometimes, in telephone conversations with Internet providers. • Sometimes, when signing contracts or working on hosted equipment in a colo facility. • Sometimes, when collecting the money (credit card processors, banks, Paypal and similar services like e. Passporte). • When arranging sale or delivery or receiving payment for merchandise sold through spam (dubious nutritional supplements, pharmaceuticals, mortgage leads, porn site memberships). 16
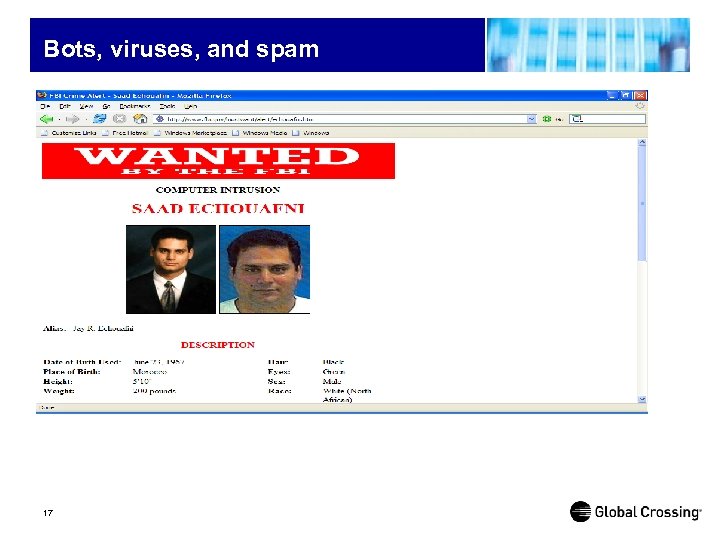
Bots, viruses, and spam 17
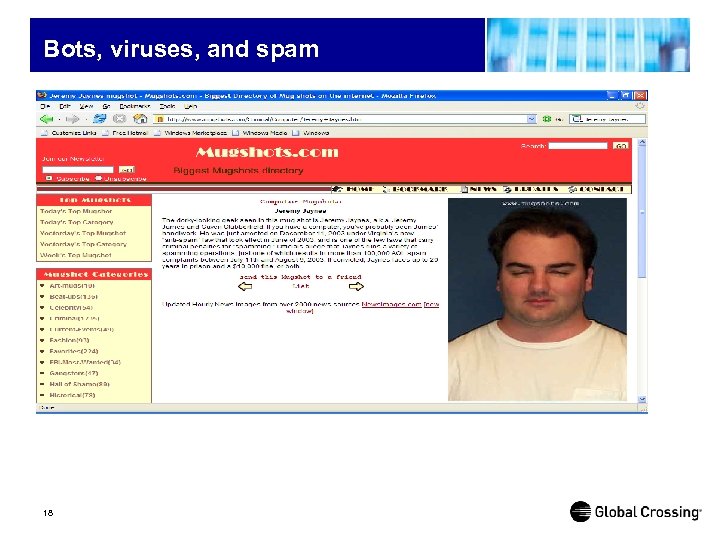
Bots, viruses, and spam 18
Bots, viruses, and spam Others: • Howard Carmack, the Buffalo spammer: $16 million judgment for Earthlink, 3. 5 -7 years on criminal charges from NY AG. • Jennifer Murray, Ft. Worth spamming grandmother, arrested and extradited to VA. • Ryan Pitylak, UT Austin philosophy student, sued by Texas AG. • 200+ spam lawsuits filed in 2004 by Microsoft (Glenn Hannifin, etc. ) • Robert Kramer/CIS Internet lawsuit in Iowa: $1 billion judgment. • Long list of names at the Registry of Known Spam Operations (ROKSO): http: //www. spamhaus. org 19
Bots, viruses, and spam 20
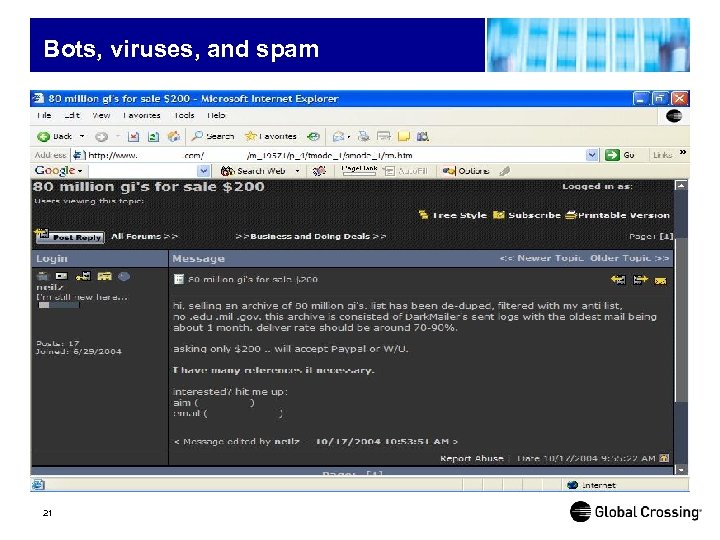
Bots, viruses, and spam 21
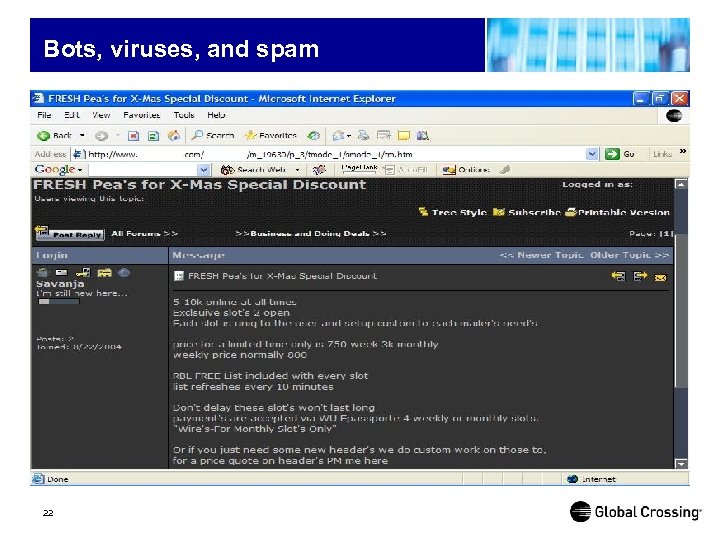
Bots, viruses, and spam 22
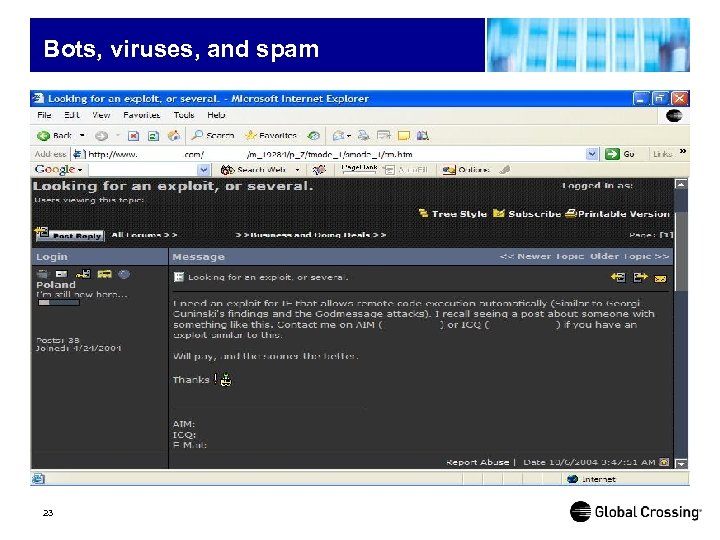
Bots, viruses, and spam 23
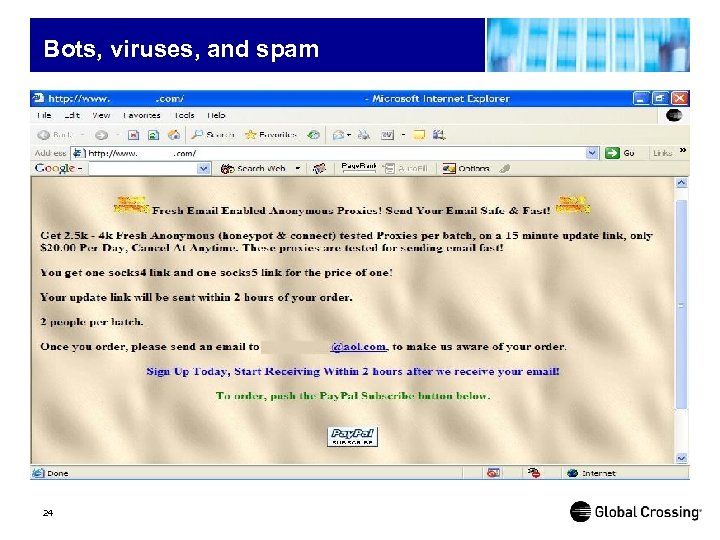
Bots, viruses, and spam 24
Bots, viruses, and spam 25

Bots, viruses, and spam This slide intentionally left blank – not to be distributed. 26
Bots, viruses, and spam 27
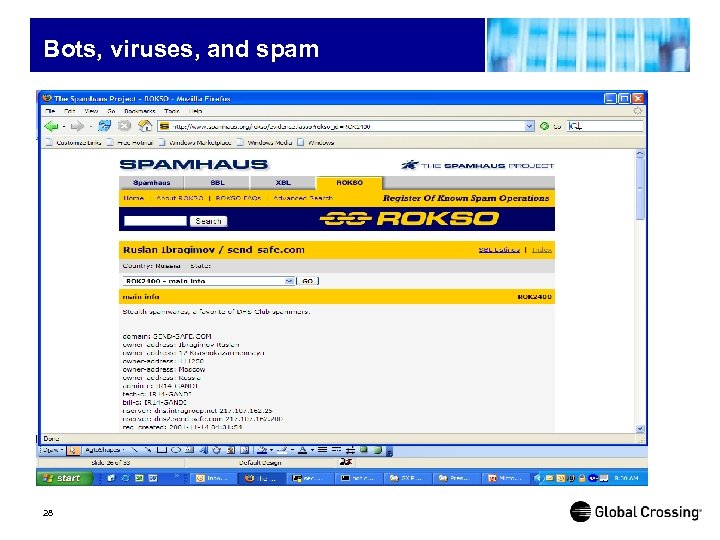
Bots, viruses, and spam 28

Bots, viruses, and spam How can we fight them? Any solution that requires all or most end users to become power users or system administrators to secure their systems will fail. The vast majority of bots are end user systems belonging to home users, sitting behind a cable or DSL modem. Effective reduction of bots, viruses, spam, and denial of service attacks will require actions from multiple parties— software and OS vendors, organizations with an Internet presence, online service providers, and law enforcement. 29

Bots, viruses, and spam Things software and OS vendors should do. • Start providing software without major well-known, detectible defects— there is no excuse for software with buffer overflows being released as a product. • Software defaults should be the most secure settings, not the least secure. 30

Bots, viruses, and spam Things organizations should do. • Implement organizational firewalls (with default deny on outbound as well as inbound) and content filtering. • Implement spam filtering (w/CBL) and antivirus. • Implement endpoint security on client machines to enforce organizational standards for antivirus, patch levels, host firewall rules, file integrity—hosts out of compliance don’t get connectivity. • Switch to thin clients where a desktop computer is overkill. • Implement intrusion prevention systems. • Segment large networks to allow segregation of traffic by criticality/quarantining of infected hosts. 31

Bots, viruses, and worms Things online service providers should do. • Put the right provisions in contracts/AUPs. • Implement screening mechanisms as part of pre-sales (or pre-provisioning) process. • Implement detection and filtering mechanisms where/when feasible (ISPs with end users have more options). • Participate in intelligence sharing with security researchers, anti-spammers, and other providers. • Work with law enforcement to assist in prosecutions (e. g. , FBI’s Operation Slam Spam). • File lawsuits against criminal abusers (AOL, Earthlink, Microsoft are good at this). • Act aggressively to get known abusers off networks and keep them from getting on in the first place (e. g. , Spamhaus Blackhole List, or SBL). • Provide 24/7 incident response capability. ISPs (with end users as direct customers): • Quarantine infected end user systems. • Demand regular notifications of detected issues from upstream providers. NSPs (with ISPs, colo, webhosting, etc. as direct customers): • Blackhole botnet controllers and phishing websites upon verification. • Send regular notifications to downstream customers of detected issues. 32

Bots, viruses, and worms Things law enforcement should do. • Work with online providers and security researchers to collect intelligence (e. g. , Operation Slam Spam). • Go undercover to engage in deals with criminal hackers, criminal spammers, and organized criminals to “follow the money” and connect online identities to real identities, pursuing the common contact points. • Follow up on civil litigation from online providers with criminal prosecutions. 33

Bots, viruses, and worms Conclusion • 2004 was the year major law enforcement investigations began— 2005 will be the year of major prosecutions. • There’s a lot more to be done, and online providers play a key role, especially those with bot-infected end users as direct customers and those with spam operations as direct customers. • A combination of technology and aggressive enforcement (criminal, civil, and AUP) are essential. 34
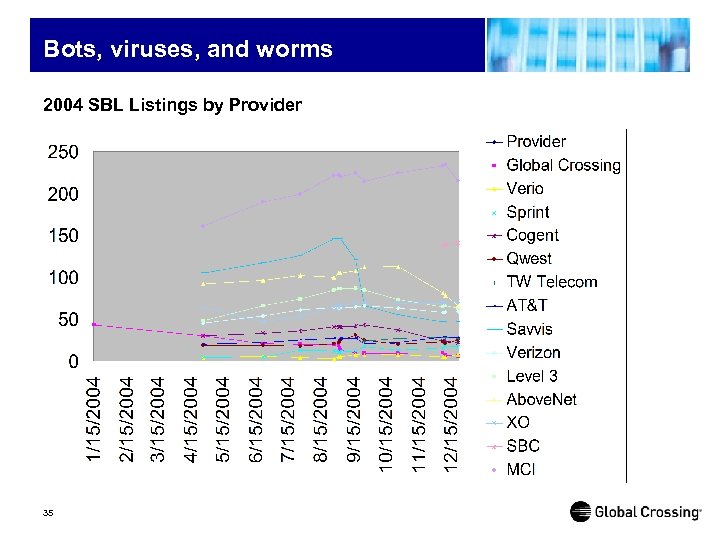
Bots, viruses, and worms 2004 SBL Listings by Provider 35

Bots, viruses, and spam Further Information Composite Blocking List: http: //cbl. abuseat. org Registry Of Known Spam Operations (ROKSO): http: //www. spamhaus. org Bot information: http: //www. lurhq. com/research. html Message Labs 2004 end-of-year report: http: //www. messagelabs. com/binaries/LAB 480_endofyear_v 2. pdf CAIDA Network Telescope: http: //www. caida. org/analysis/security/telescope/ Team Cymru Dark. Net: http: //www. cymru. com/Darknet/ Internet Motion Sensor: http: //ims. eecs. umich. edu/ Brian Mc. Williams, Spam Kings, 2004, O’Reilly and Associates. Spammer-X, Inside the Spam Cartel, 2004, Syngress. (Read but don’t buy. ) Jim Lippard james. lippard@globalcrossing. com 36
32c7b5a2c716ef836303de4c526be096.ppt