1fe6ac4bb207667f84c6d687592a30d6.ppt
- Количество слайдов: 56

Boaz Elgar Product Manager November, 2002 1
Agenda l. Some known DDo. S attacks l. Types of DDo. S attacks l. Current measures for blocking DDo. S l. Riverhead Solution overview Confidential, © Riverhead Networks, Inc. , 2002 2
Riverhead Profile l Solution: Secure internet availability against crippling DDo. S cyber-attacks l Customers: Large enterprises, new media companies, service providers and government organizations l Investors: l HQ: Cupertino, California l Products: Riverhead Guard and Detector - infrastructure security devices Confidential, © Riverhead Networks, Inc. , 2002 3

Overview of DDo. S attacks Confidential, © Riverhead Networks, Inc. , 2002 4

DDo. S Incidents Around The Globe l Global World Economic Forum's, CERT l Europe Deutsche Bank, Lufthansa, Firenet, Tiscali, ed. NET, The. Dogma. Group, Don. Host, British telecom, Cloud 9 l US Amazon, Yahoo, CNN, e-Bay, e-Trade, Microsoft, White House NY Times, NASA, OZ. Net l ROW 200 small corporations, 30 educational organizations and 20 government systems (Korea), St George Bank (Australia) Confidential, © Riverhead Networks, Inc. , 2002 5
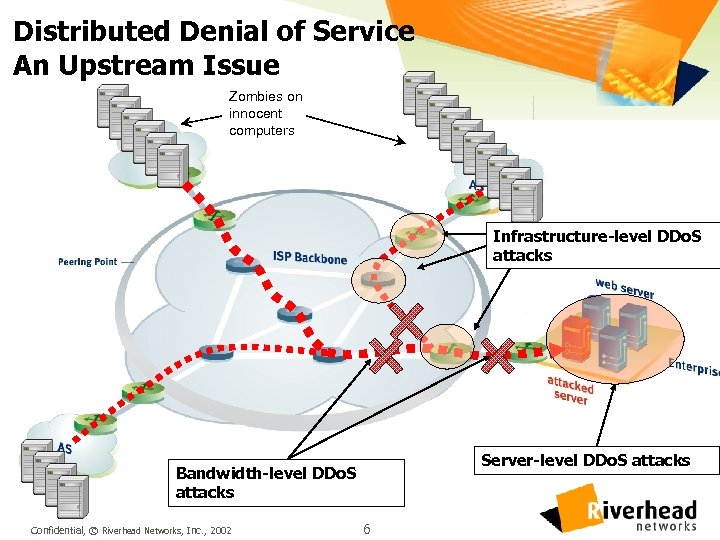
Distributed Denial of Service An Upstream Issue Zombies on innocent computers Infrastructure-level DDo. S attacks Server-level DDo. S attacks Bandwidth-level DDo. S attacks Confidential, © Riverhead Networks, Inc. , 2002 6
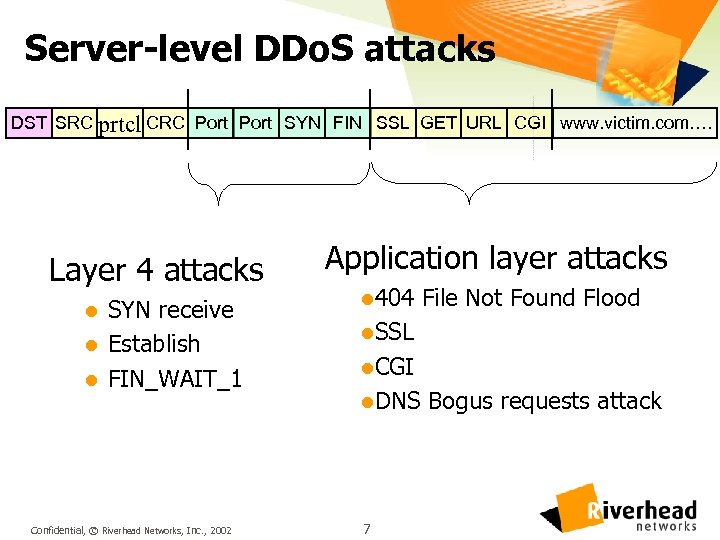
Server-level DDo. S attacks DST SRC prtcl CRC Port SYN FIN SSL GET URL CGI www. victim. com…. Layer 4 attacks l l l SYN receive Establish FIN_WAIT_1 Confidential, © Riverhead Networks, Inc. , 2002 Application layer attacks l 404 File Not Found Flood l. SSL l. CGI l. DNS 7 Bogus requests attack
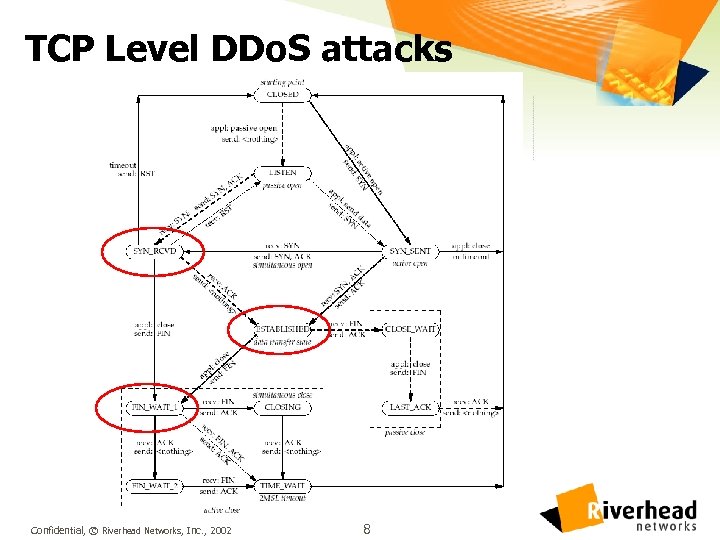
TCP Level DDo. S attacks Confidential, © Riverhead Networks, Inc. , 2002 8
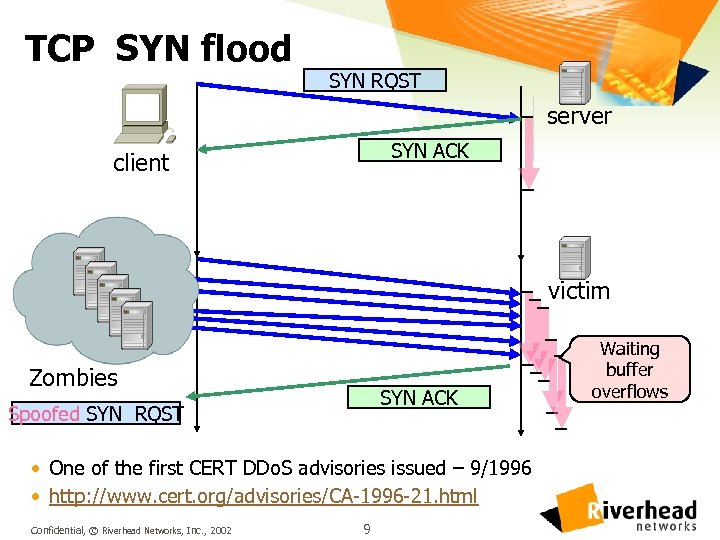
TCP SYN flood SYN RQST server SYN ACK client victim zombie Zombies SYN ACK Spoofed SYN RQST • One of the first CERT DDo. S advisories issued – 9/1996 • http: //www. cert. org/advisories/CA-1996 -21. html Confidential, © Riverhead Networks, Inc. , 2002 9 Waiting buffer overflows
TCP SYN Flood News - February 3, 2002 Firenet ISP Suffers Do. S Attack Firenet MD Mr Castle also stated: "The list of attacks were Syn Flood attacks, Ip Spoofing the Lan interfaces, and Total Denial of service attacks. We had taken down the servers for 4 nights in a row, from 11 oclock till 6. 00 am daily and worked all through the night with BT fighting this hacker or hackers, and had stopped the problems on Wednesday night Thursday morning". Confidential, © Riverhead Networks, Inc. , 2002 10
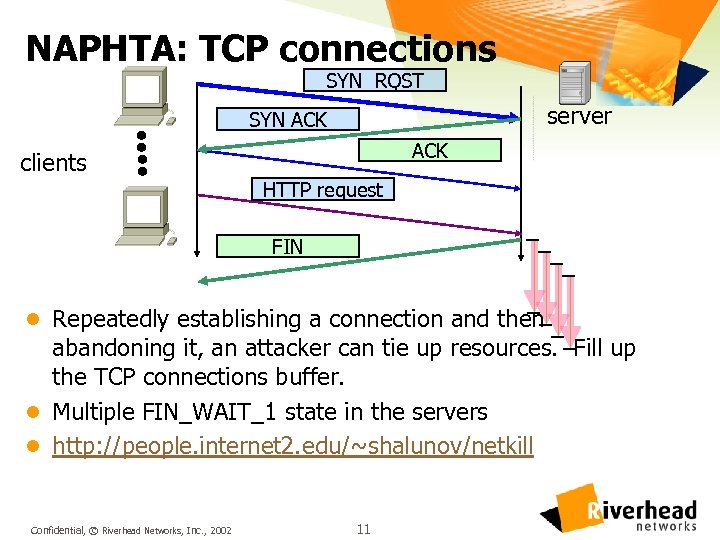
NAPHTA: TCP connections SYN RQST server SYN ACK clients HTTP request FIN l Repeatedly establishing a connection and then abandoning it, an attacker can tie up resources. Fill up the TCP connections buffer. l Multiple FIN_WAIT_1 state in the servers l http: //people. internet 2. edu/~shalunov/netkill Confidential, © Riverhead Networks, Inc. , 2002 11
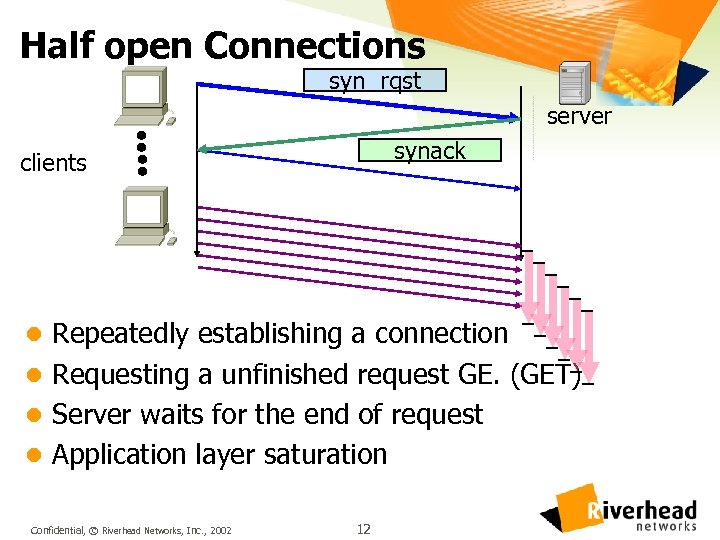
Half open Connections syn rqst server synack clients l Repeatedly establishing a connection l Requesting a unfinished request GE. (GET) l Server waits for the end of request l Application layer saturation Confidential, © Riverhead Networks, Inc. , 2002 12
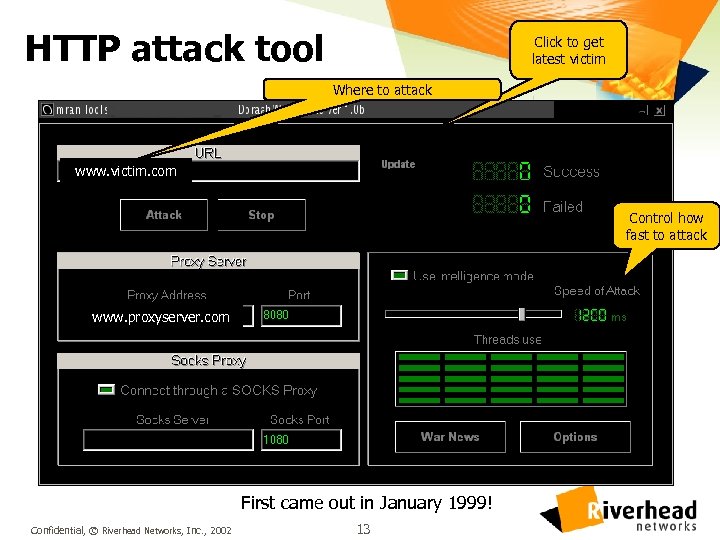
HTTP attack tool Click to get latest victim Where to attack www. victim. com Control how fast to attack www. proxyserver. com First came out in January 1999! Confidential, © Riverhead Networks, Inc. , 2002 13

Client attack l URL attacks l Repeated request l Repeated REFRESH l Random URL • Avoids proxy • Works hard • Large log file l victim cgi, long forms, heavy search requests l http: //all. net/journal/netsec/9512. html Confidential, © Riverhead Networks, Inc. , 2002 14

Client attack on Lufthansa Computerworld 6/21/01 “Wednesday morning, in a planned attack, demonstrators began accessing Lufthansa's Web site. Although demonstrators claim they knocked the site off-line for about 10 minutes, Lufthansa said the claim was untrue. ” “Lufthansa's servers got 67, 004 hits per second at one point in the two-hour Web attack” “The attack was planned to protest Lufthansa's contract with the German government to fly people who are denied asylum in Germany out of the country. ” Confidential, © Riverhead Networks, Inc. , 2002 15
Client attack on WTO Confidential, © Riverhead Networks, Inc. , 2002 16
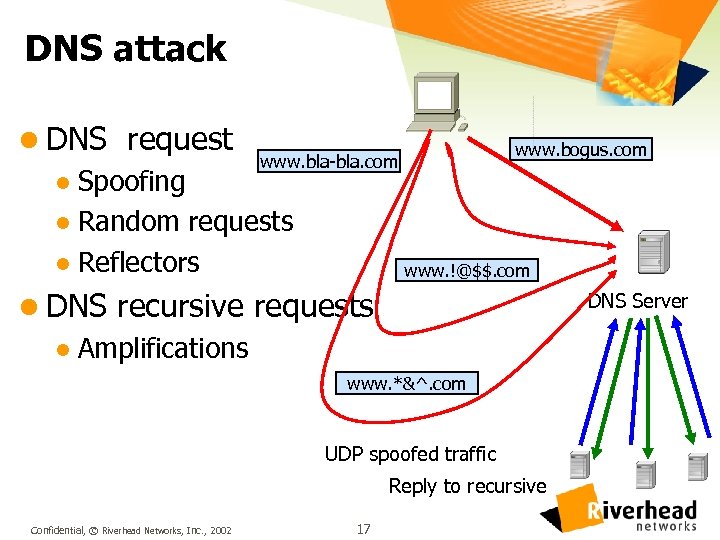
DNS attack l DNS request www. bogus. com www. bla-bla. com l Spoofing l Random requests l Reflectors www. !@$$. com l DNS recursive requests l Amplifications DNS Server www. *&^. com UDP spoofed traffic Reply to recursive Confidential, © Riverhead Networks, Inc. , 2002 17
Bandwidth-level DDo. S attacks l ICMP echo, unreachable l UDP Flood l Reflectors l Smurf Flood Bandwidth-level DDo. S attacks Confidential, © Riverhead Networks, Inc. , 2002 18
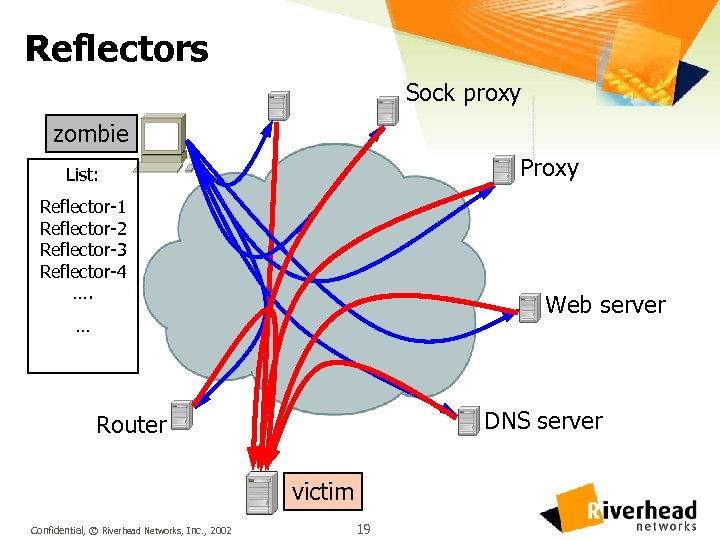
Reflectors Sock proxy zombie Proxy List: Reflector-1 Reflector-2 Reflector-3 Reflector-4 …. Web server … DNS server Router victim Confidential, © Riverhead Networks, Inc. , 2002 19
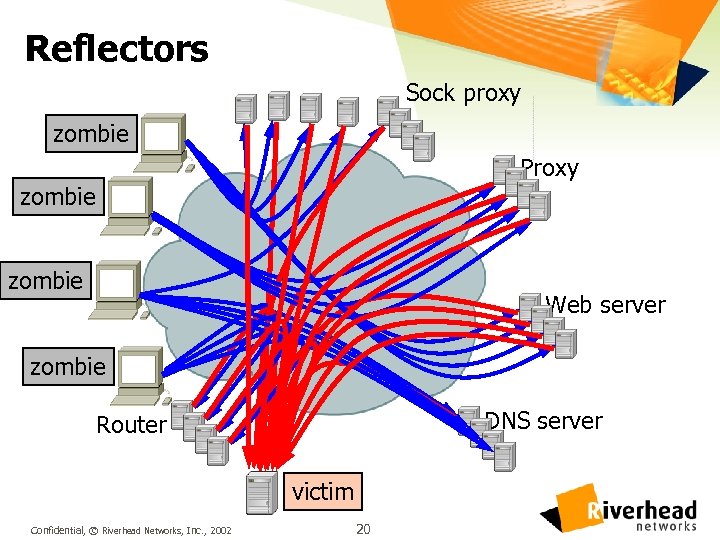
Reflectors Sock proxy zombie Proxy zombie Web server zombie DNS server Router victim Confidential, © Riverhead Networks, Inc. , 2002 20
Reflectors -> Bandwidth attack l Reflectors= returns a packet if one is sent l Web servers, DNS servers and routers • Returns SYNACK or RST in response to a SYN or other TCP packets with ACK • ICMP Time Exceeded or Host Unreachable in response to particular IP packets • Amplification if knowing the sequence number (FTP, streaming…) • DNS replies l l http: //grc. com/dos/drdos. htm http: //www. aciri. org/vern/papers/reflectors. CCR. 01. pdf Confidential, © Riverhead Networks, Inc. , 2002 21
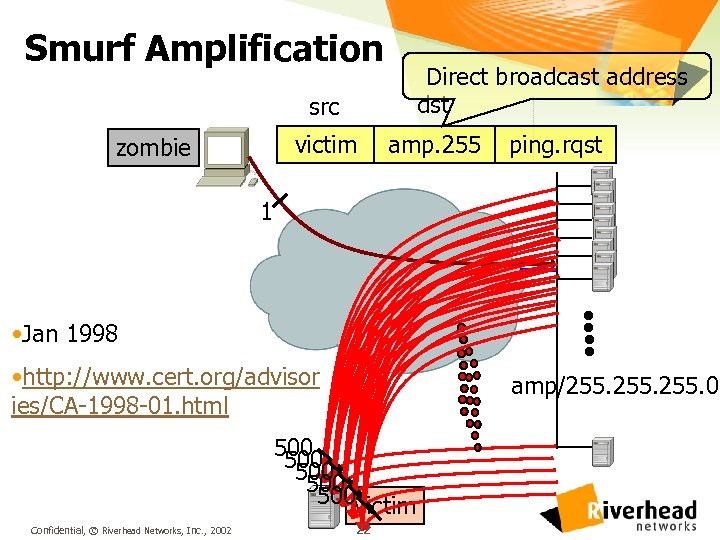
Smurf Amplification Direct broadcast address dst src victim zombie amp. 255 ping. rqst 1 • Jan 1998 • http: //www. cert. org/advisor ies/CA-1998 -01. html amp/255. 0 500 500 500 victim Confidential, © Riverhead Networks, Inc. , 2002 22
Smurf Tool Set packet size from 10 to 1300 octets Came out in March 1999! Confidential, © Riverhead Networks, Inc. , 2002 23

Smurf attack Internet attack slows Web to a crawl Assault on Oz. net affects entire area Tuesday, January 18, 2000 an ISP serving 7, 000 subscribers, is known to have been targeted in the so-called smurf attack in Seattle, the assault affected many, perhaps even most, of the Internet users in the Seattle area, said experts. “… all the corporate or academic networks the smurf attacker used in the assault -- as many as 2, 000 nationwide” “The Seattle attack was most likely launched by a single person…” Confidential, © Riverhead Networks, Inc. , 2002 24
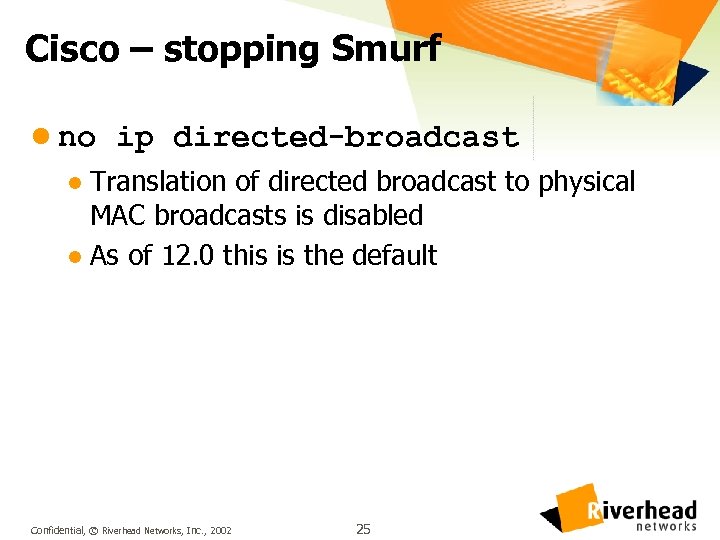
Cisco – stopping Smurf l no ip directed-broadcast Translation of directed broadcast to physical MAC broadcasts is disabled l As of 12. 0 this is the default l Confidential, © Riverhead Networks, Inc. , 2002 25
Infrastructure-level DDo. S attacks l BGP / OSPF / … attacks l SYN flood TCP 179, SSH l ICMP attack l DNS attacks Confidential, © Riverhead Networks, Inc. , 2002 Infrastructure-level DDo. S attacks 26
Attacks directly on routers l Attacks directed at routers can have broader impact than attacks directed at hosts l Packets directed at a router may be more CPU (slow path) consuming then packets transiting a router Confidential, © Riverhead Networks, Inc. , 2002 27
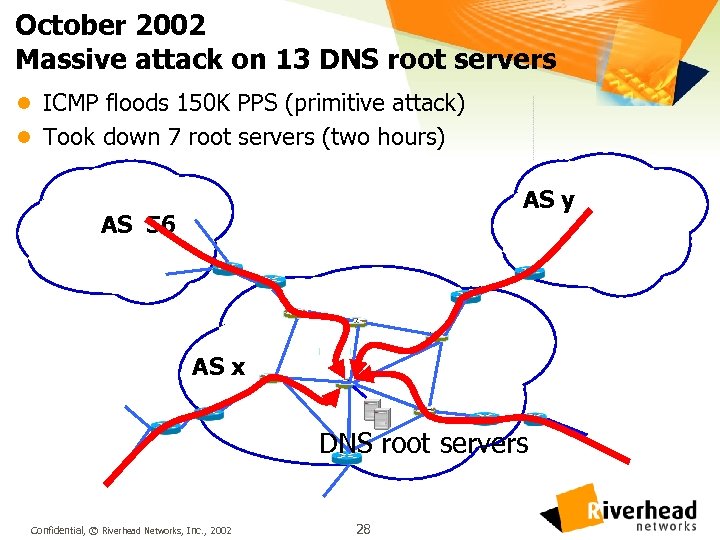
October 2002 Massive attack on 13 DNS root servers l ICMP floods 150 K PPS (primitive attack) l Took down 7 root servers (two hours) AS y AS 56 AS x DNS root servers Confidential, © Riverhead Networks, Inc. , 2002 28
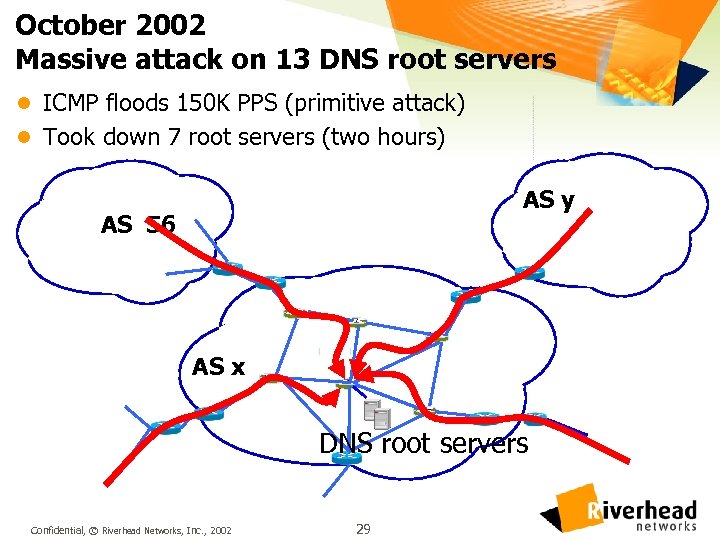
October 2002 Massive attack on 13 DNS root servers l ICMP floods 150 K PPS (primitive attack) l Took down 7 root servers (two hours) AS y AS 56 AS x DNS root servers Confidential, © Riverhead Networks, Inc. , 2002 29
Attacks & Attack Tools examples l TFN l Spoofed SYN Flood l non-Spoofed SYN Flood l UDP Flood l FIN, SYNACK Flood (Spoofed and non-spoofed) l Ping Flood l Smurf Flood l Combined UDP/TCP/ICMP l Fragmentation Attack l IP/UDP (jolt 2) l IP/ICMP (trash, and fawx) l IP/TCP l HTTP l l l Targa 3 Attack l Connection Flood (Client attack) http errors 404 etc. http half connections l DNS attacks l BGP attacks on routers Partial list of covered tools: JOLT, WINNUKE, TRINOO, TFN, Targa 3, Naphta, Trash… Confidential, © Riverhead Networks, Inc. , 2002 30

How are DDo. S handled? Confidential, © Riverhead Networks, Inc. , 2002 31
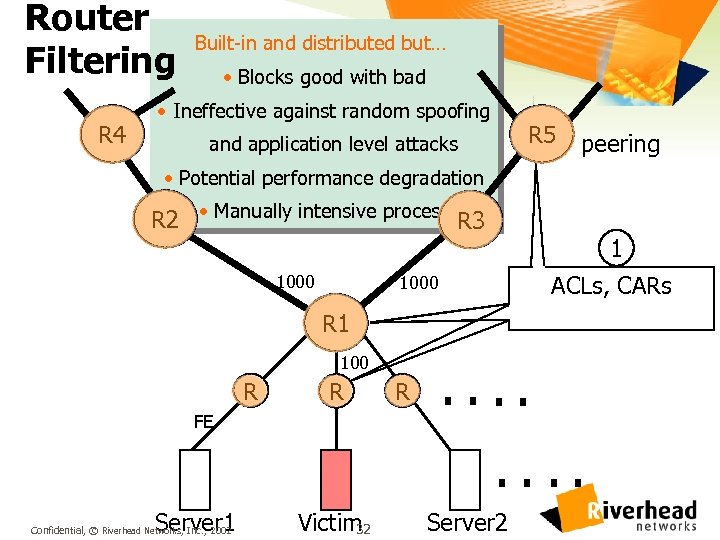
Router Filtering R 4 Built-in and distributed but… • Blocks good with bad • Ineffective against random spoofing R 5 and application level attacks peering • Potential performance degradation R 2 • Manually intensive process R 3 1000 1 ACLs, CARs 1000 R 1 100 R R FE R . . . . Server 1 Confidential, © Riverhead Networks, Inc. , 2002 Victim 32 Server 2
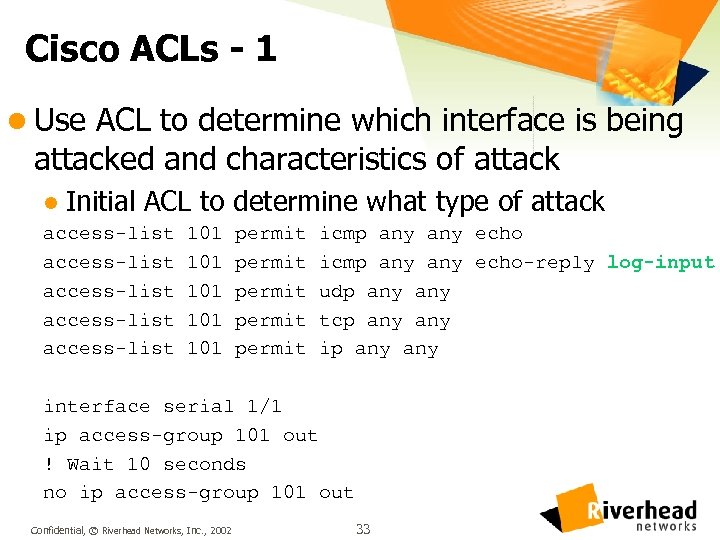
Cisco ACLs - 1 l Use ACL to determine which interface is being attacked and characteristics of attack l Initial ACL to determine what type of attack access-list access-list 101 101 101 permit permit icmp any any echo-reply log-input udp any tcp any any interface serial 1/1 ip access-group 101 out ! Wait 10 seconds no ip access-group 101 out Confidential, © Riverhead Networks, Inc. , 2002 33

Cisco ACLs - 2 l sh access-l 101 Extended permit permit IP access list 101 icmp any echo (2 matches) icmp any echo-reply (21374 matches) udp any (18 matches) tcp any (123 matches) ip any (5 matches) • Indications are that there is some sort of ICMP attack • Need to place ACL on each successive router in upstream path Confidential, © Riverhead Networks, Inc. , 2002 34
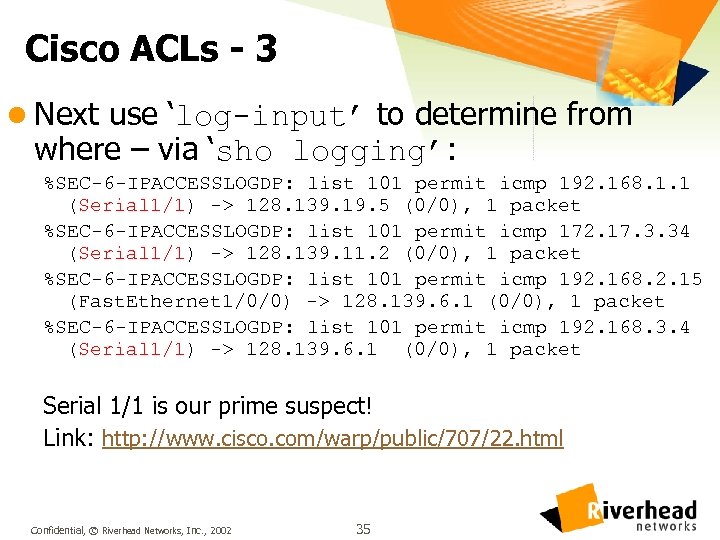
Cisco ACLs - 3 l Next use ‘log-input’ to determine from where – via ‘sho logging’: %SEC-6 -IPACCESSLOGDP: list 101 permit icmp 192. 168. 1. 1 (Serial 1/1) -> 128. 139. 19. 5 (0/0), 1 packet %SEC-6 -IPACCESSLOGDP: list 101 permit icmp 172. 17. 3. 34 (Serial 1/1) -> 128. 139. 11. 2 (0/0), 1 packet %SEC-6 -IPACCESSLOGDP: list 101 permit icmp 192. 168. 2. 15 (Fast. Ethernet 1/0/0) -> 128. 139. 6. 1 (0/0), 1 packet %SEC-6 -IPACCESSLOGDP: list 101 permit icmp 192. 168. 3. 4 (Serial 1/1) -> 128. 139. 6. 1 (0/0), 1 packet Serial 1/1 is our prime suspect! Link: http: //www. cisco. com/warp/public/707/22. html Confidential, © Riverhead Networks, Inc. , 2002 35

Cisco CAR l CAR – Committed Access Rate b/w Normal Burst in bytes Max Burst in bytes interface ATM 1/1/0. 21 point-to-point rate-limit input access-group 180 96000 24000 32000 conform-action continue exceed-action drop rate-limit input access-group 190 128000 30000 conform-action transmit exceed-action drop ! access-list 180 deny icmp 128. 139. 252. 0 0. 0. 0. 255 any access-list 180 permit icmp any access-list 190 deny tcp any established access-list 190 permit tcp any No one really understands “burst” – best to read: http: //www. nanog. org/mtg-9811/ppt/witt/index. htm Confidential, © Riverhead Networks, Inc. , 2002 36
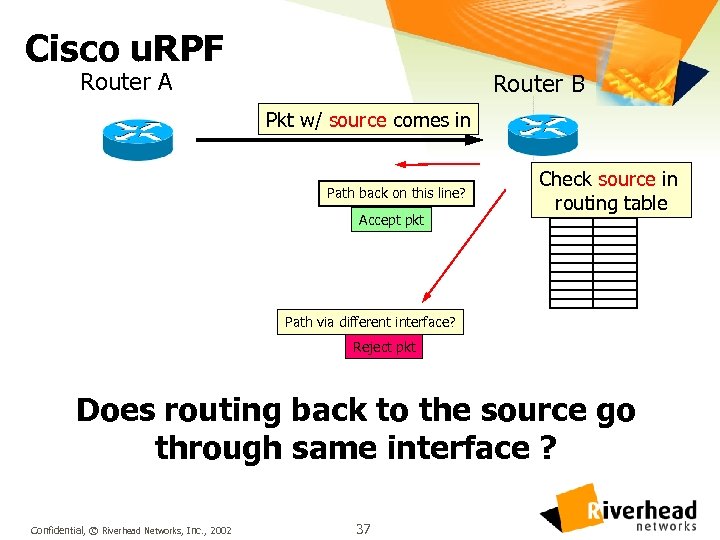
Cisco u. RPF Router A Router B Pkt w/ source comes in Path back on this line? Accept pkt Check source in routing table Path via different interface? Reject pkt Does routing back to the source go through same interface ? Confidential, © Riverhead Networks, Inc. , 2002 37

Cisco u. RPF - 1 l Unicast Reverse Path Forwarding l Requires CEF l Available starting in 11. 1(17)CC, and 12. 0 • Not available in 11. 2 or 11. 3 images l Cisco interface command: ip verify unicast rpf Confidential, © Riverhead Networks, Inc. , 2002 38
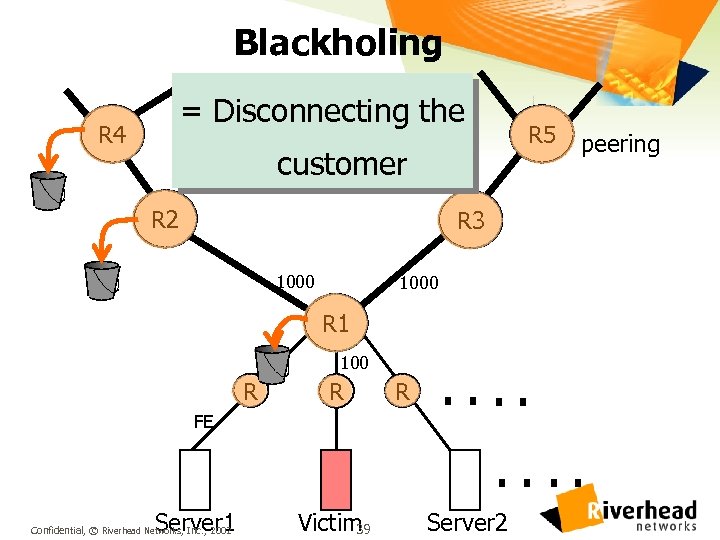
Blackholing = Disconnecting the R 4 R 5 customer R 2 peering R 3 1000 R 1 100 R R FE R . . . . Server 1 Confidential, © Riverhead Networks, Inc. , 2002 Victim 39 Server 2

Null 0 routing l Works only on destination addresses l Simple blackhole: ip route 191. 1 255 null 0 Caveat: routers can forward faster than they can drop packets l Blackholes good packets with bad packets l Confidential, © Riverhead Networks, Inc. , 2002 40
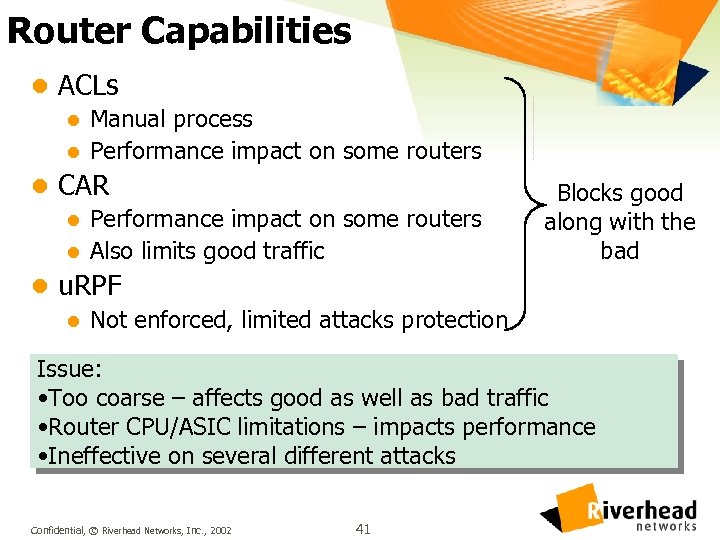
Router Capabilities l ACLs l Manual process l Performance impact on some routers l CAR l Performance impact on some routers l Also limits good traffic l u. RPF l Not enforced, limited attacks protection Blocks good along with the bad Issue: • Too coarse – affects good as well as bad traffic • Router CPU/ASIC limitations – impacts performance • Ineffective on several different attacks Confidential, © Riverhead Networks, Inc. , 2002 41
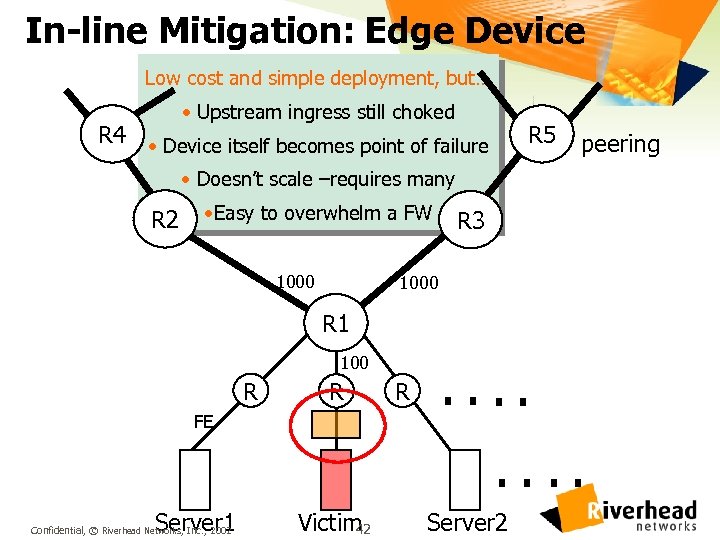
In-line Mitigation: Edge Device Low cost and simple deployment, but… • Upstream ingress still choked R 4 • Device itself becomes point of failure R 5 peering • Doesn’t scale –requires many R 2 • Easy to overwhelm a FW 1000 R 3 1000 R 1 100 R R FE R . . . . Server 1 Confidential, © Riverhead Networks, Inc. , 2002 Victim 42 Server 2
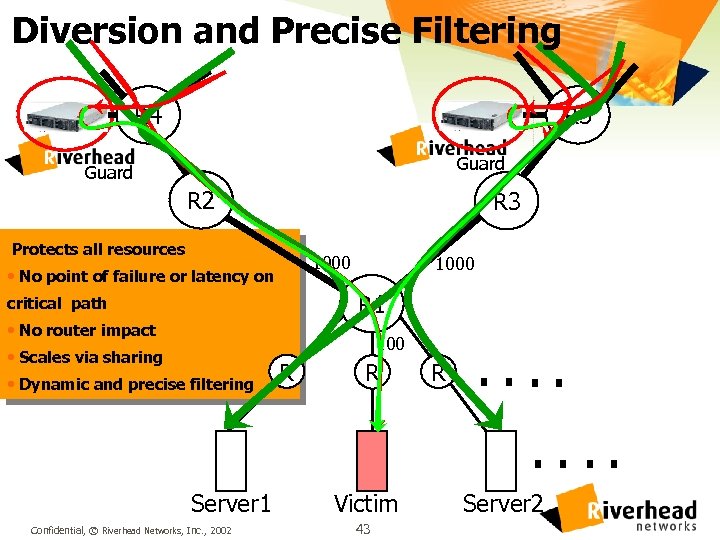
Diversion and Precise Filtering R 4 R 5 Guard R 2 R 3 Protects all resources 1000 • No point of failure or latency on 1000 R 1 critical path • No router impact 100 • Scales via sharing • Dynamic and precise filtering R R R . . . . Server 1 Confidential, © Riverhead Networks, Inc. , 2002 Victim 43 Server 2
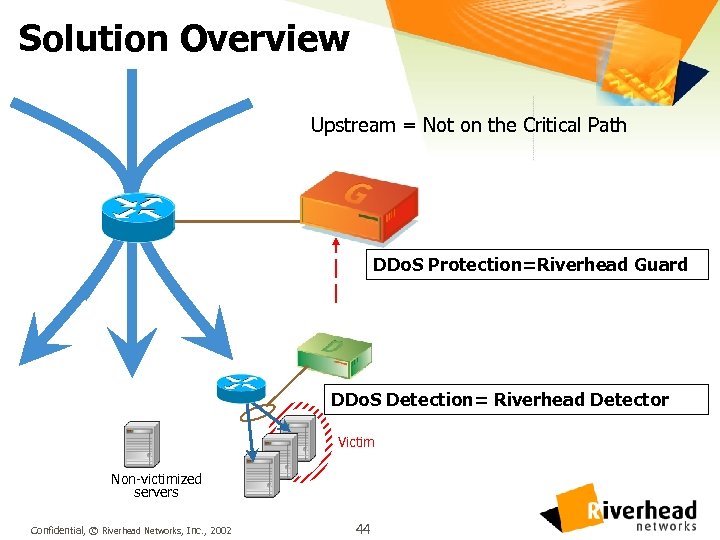
Solution Overview Upstream = Not on the Critical Path DDo. S Protection=Riverhead Guard DDo. S Detection= Riverhead Detector Victim Non-victimized servers Confidential, © Riverhead Networks, Inc. , 2002 44
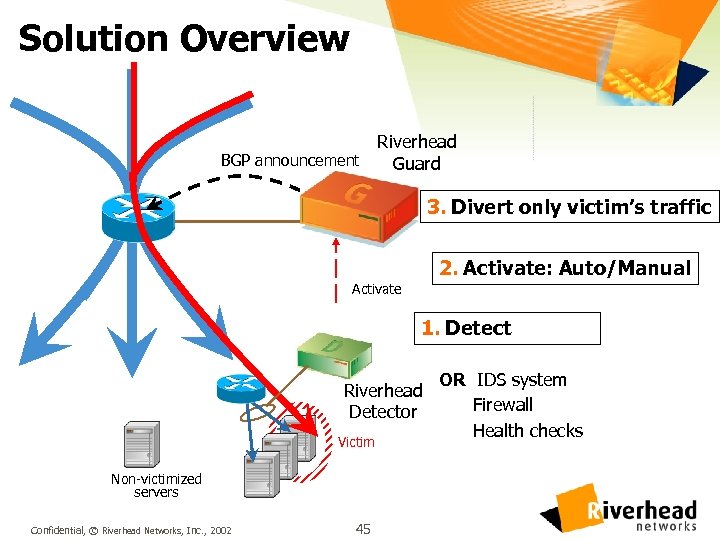
Solution Overview Riverhead BGP announcement Guard 3. Divert only victim’s traffic 2. Activate: Auto/Manual Activate 1. Detect Riverhead Detector Victim Non-victimized servers Confidential, © Riverhead Networks, Inc. , 2002 45 OR IDS system Firewall Health checks
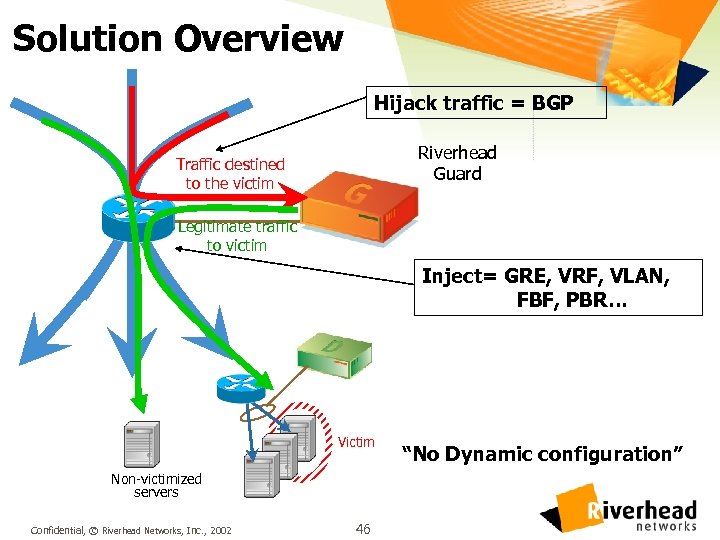
Solution Overview Hijack traffic = BGP Riverhead Guard Traffic destined to the victim Legitimate traffic to victim Inject= GRE, VRF, VLAN, FBF, PBR… Victim Non-victimized servers Confidential, © Riverhead Networks, Inc. , 2002 46 “No Dynamic configuration”
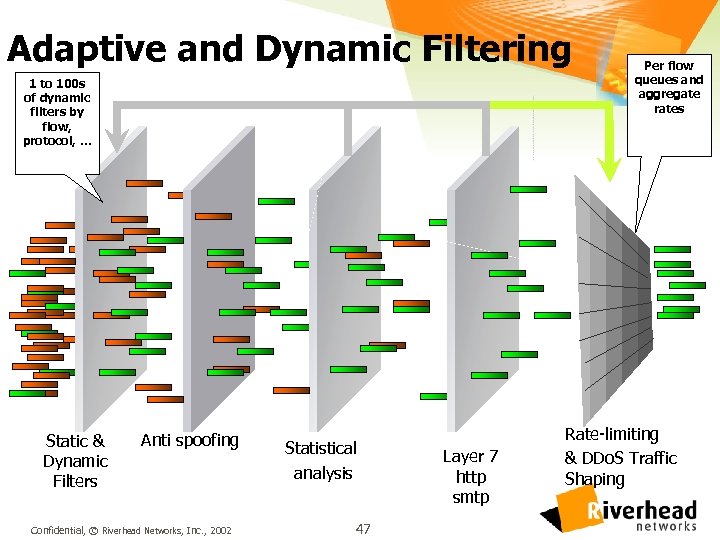
Adaptive and Dynamic Filtering 1 to 100 s of dynamic filters by flow, protocol, … Static & Dynamic Filters Anti spoofing Confidential, © Riverhead Networks, Inc. , 2002 Statistical analysis 47 Layer 7 http smtp Per flow queues and aggregate rates Rate-limiting & DDo. S Traffic Shaping
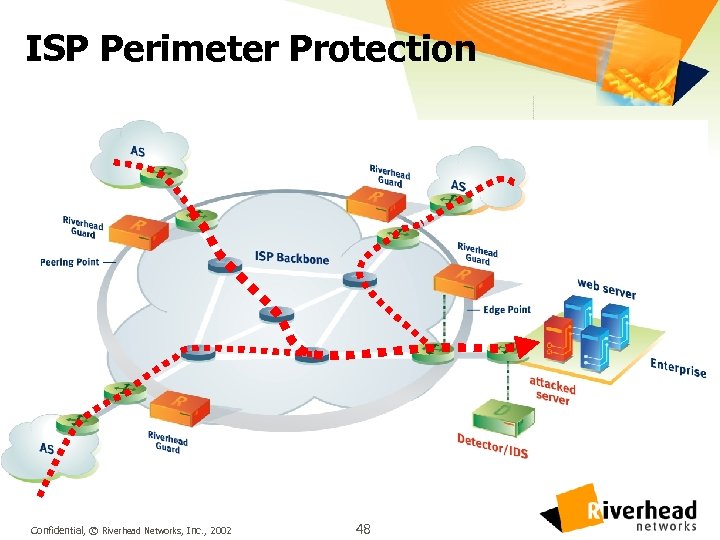
ISP Perimeter Protection Confidential, © Riverhead Networks, Inc. , 2002 48
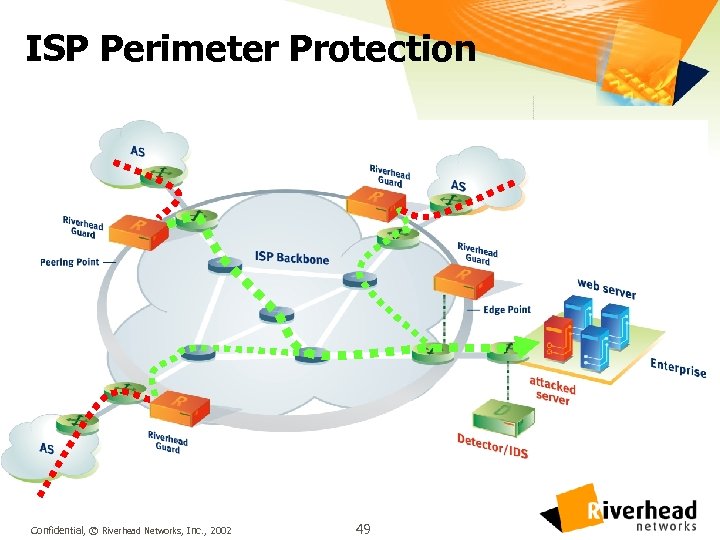
ISP Perimeter Protection Confidential, © Riverhead Networks, Inc. , 2002 49
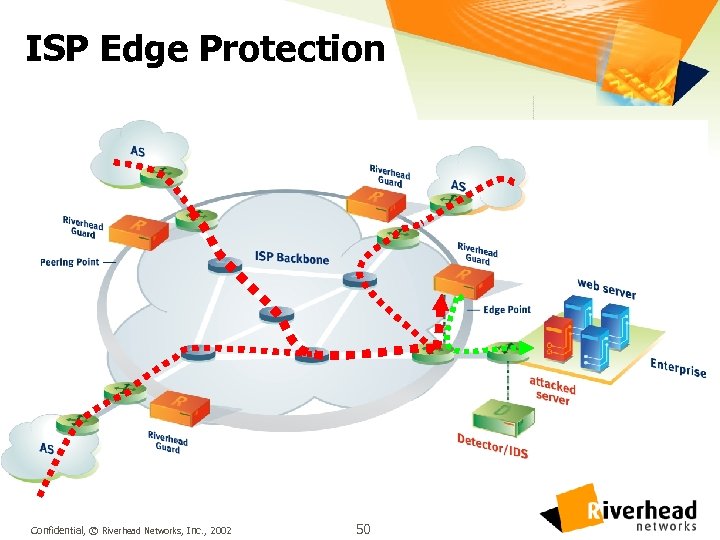
ISP Edge Protection Confidential, © Riverhead Networks, Inc. , 2002 50
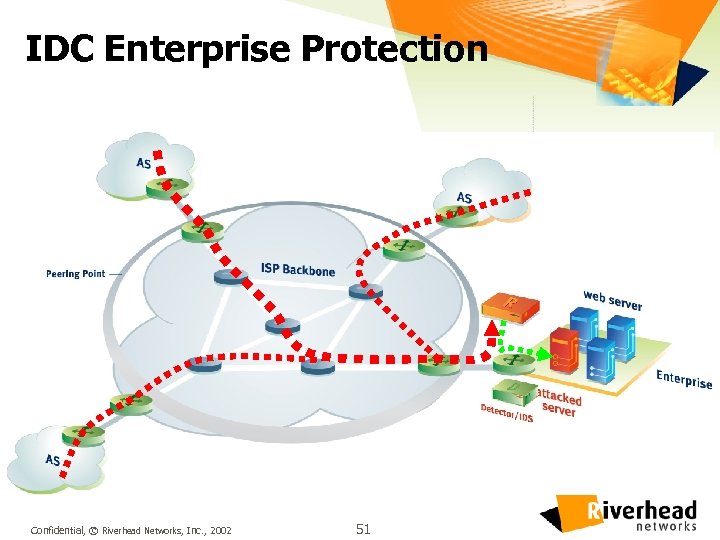
IDC Enterprise Protection Confidential, © Riverhead Networks, Inc. , 2002 51
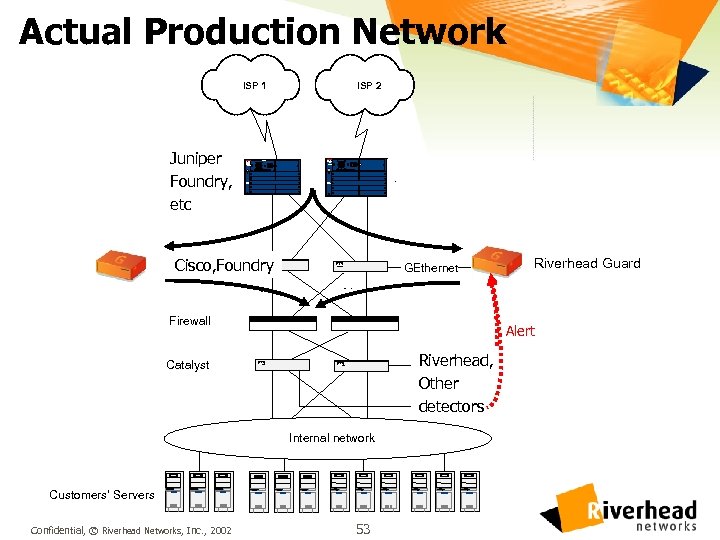
Actual Production Network ISP 1 Juniper GSR 12000 Foundry, etc C C SY T S IS O SEM ISP 2 Po e S l y 0 wr upp Po er. S ly 1 w upp S D C OSY T ISC EM o e Su p 0 w l D o er. S p 1 u ly a l t 80 SE E S Catalyst 8500 SRE ES Sw itch Processor Sw ch i P o e so S C ta y s 5 0 I P S r py Pw p S R I t r c s r Cisco, Foundry Catalyst I CO S EM YS GEthernet I CO S TEM YS CS CS T S S Firewall Catalyst Alert I CO S EM YS Riverhead, IDS Other detectors IDS I CO S TEM YS Internal network Customers’ Servers Confidential, © Riverhead Networks, Inc. , 2002 Riverhead Guard 53
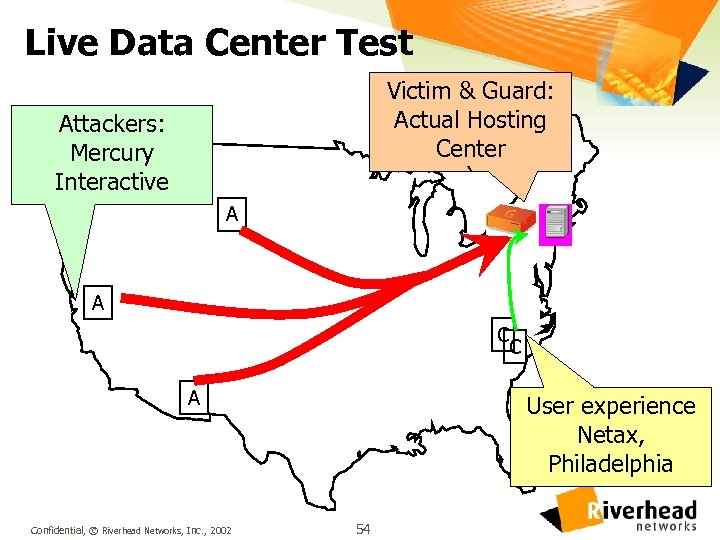
Live Data Center Test Victim & Guard: Actual Hosting Center ` Attackers: Mercury Interactive A A C C A Confidential, © Riverhead Networks, Inc. , 2002 User experience Netax, Philadelphia 54
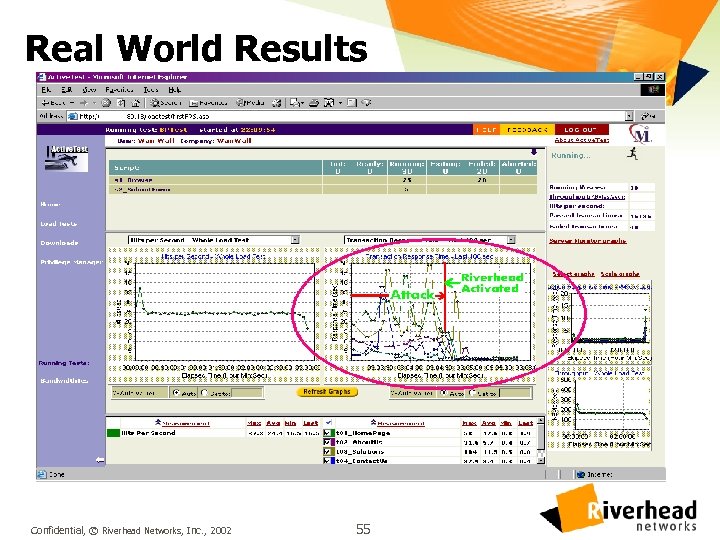
Real World Results Confidential, © Riverhead Networks, Inc. , 2002 55
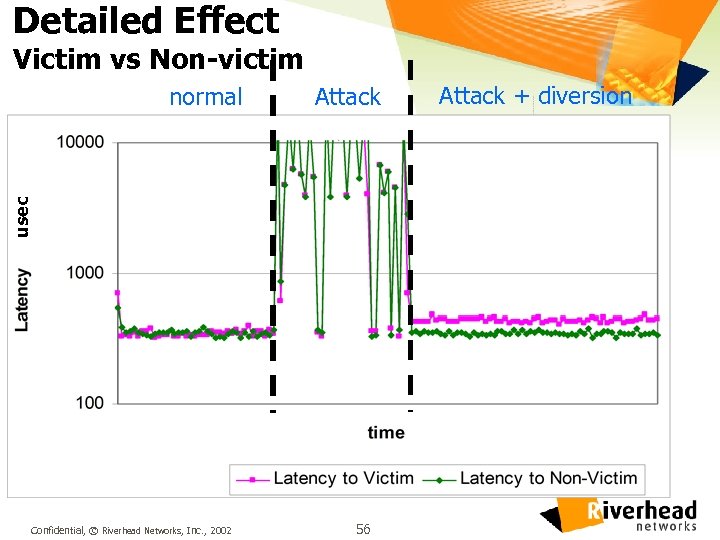
Detailed Effect Victim vs Non-victim Attack usec normal Confidential, © Riverhead Networks, Inc. , 2002 56 Attack + diversion

Thank you! Comments: boaz@riverhead. com Confidential, © Riverhead Networks, Inc. , 2002 57
1fe6ac4bb207667f84c6d687592a30d6.ppt