403f436e6d92d373cd36208807628374.ppt
- Количество слайдов: 31
Biometrics Overview
Biometrics Identification or verification of an individual based on a physical characteristic or trait.
Biometric Modes Biological Characteristics Ø Fingerprint Ø Facial Recognition Ø Hand Geometry Ø Eye (Iris & Retina) Ø Vein Pattern Behavioral Traits Ø Signature Ø Voice Ø Keystroke Dynamics

Why use Biometrics? Biometrics has No Risk of: ØForgetting it ØLosing it ØGetting it stolen ØGetting it copied ØLoaning it out ØBeing used by anyone else
Biometric Uses Ø Financial Institutes • ATM, Validation of credit and debit cards Ø Law Enforcement • Automated Fingerprint Identification System • Surveillance Ø Physical Access Control • Buildings, Airports, Hospitals, Schools Ø IT Security • Network-systems of organizations – Internet/Intranet Ø E-Commerce market : User Authentication Ø Consumer Market • PC Applications(Mouse, Keyboard, Laptop, etc. ) • Time and Attendance Monitoring • Home Appliances (Door locks, Safes, etc. )
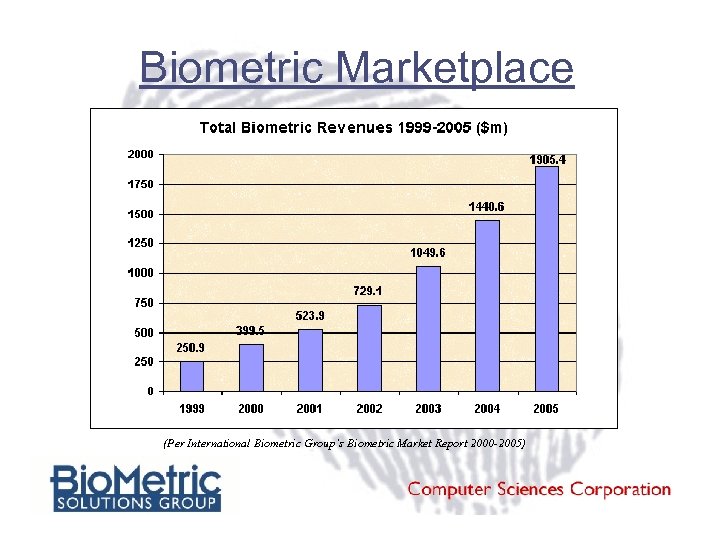
Biometric Marketplace (Per International Biometric Group’s Biometric Market Report 2000 -2005)

Market Drivers v Real need for increased security Ø Traditional methods obsolete Ø Increased identity theft and fraud v Advances in biometric technology Ø Reliability and functionality v Price factors v Weak capital markets Ø Competitive environment Ø Consolidation v Industry standardization v Current Events/Emotion

Fingerprint v. Measures ridges and minutiae (end, fusion, bifurcation of fingerprint data) ØUsed for over 100 years ØHighly accurate ØSmall devices ØLatent prints ØEnvironmental conditions

Facial Recognition v. Measures the contours and distances of the Eyes, Nose and Chin. ØMay also use Thermograph matching ØEasy to use/Non-cooperative ØInfluenced by lighting and facial angles ØSusceptible to spoofing with glasses, wigs, beards
Hand Geometry v. Measures finger length and knuckle thickness ØIntuitive Operation ØUses few minutiae points ØLarge Devices limit the installation possibilities.
Eye Recognition v. Iris: ØMeasures the shape & color of the Iris ØMinutiae rich ØInconvenient ØExpensive v. Retina: ØBlood Vessel Pattern ØHighly Accurate ØLow public acceptance (Intrusive)

Vein Recognition v. Uses an infrared camera to measure the veins on the wrist and back of the hand. ØCurrently impossible to copy ØLarge Equipment ØExpensive ØUses few minutiae points

Signature Recognition v. Measures the pressure and speed of stroke dynamics ØInexpensive ØIntuitive Operation ØSignatures may change over time ØParticipation must be voluntary ØLow Accuracy

Voice Recognition v. Measures the vibration of phoneme, syllable, words ØEasy to use ØRemote applications ØEasy to impersonate ØInfluenced by health conditions ØSensitive to noise
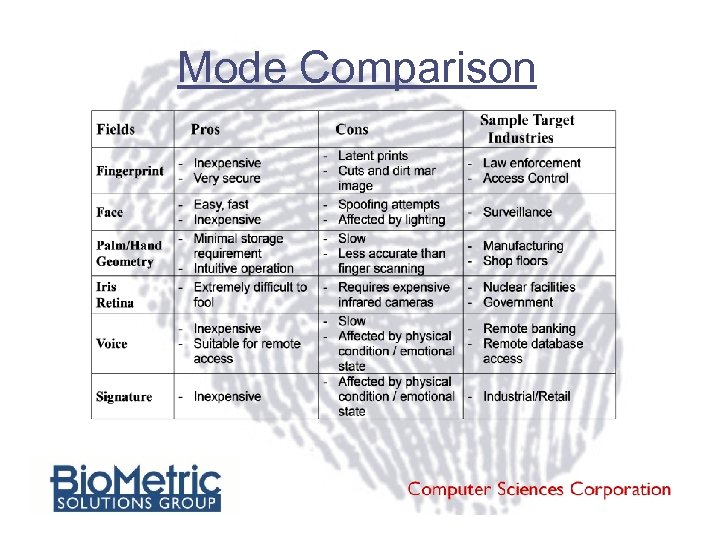
Mode Comparison
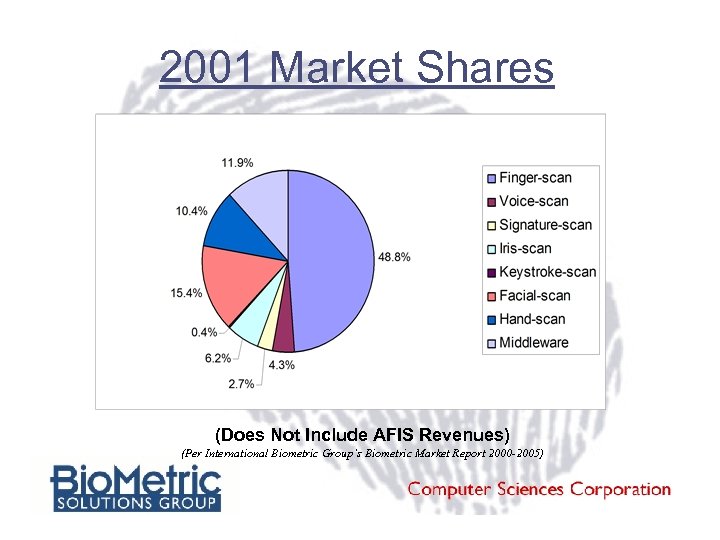
2001 Market Shares (Does Not Include AFIS Revenues) (Per International Biometric Group’s Biometric Market Report 2000 -2005)
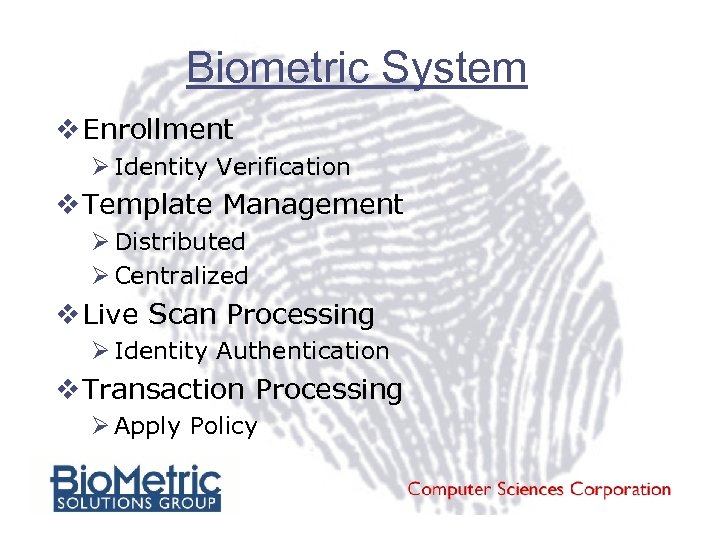
Biometric System v Enrollment Ø Identity Verification v Template Management Ø Distributed Ø Centralized v Live Scan Processing Ø Identity Authentication v Transaction Processing Ø Apply Policy
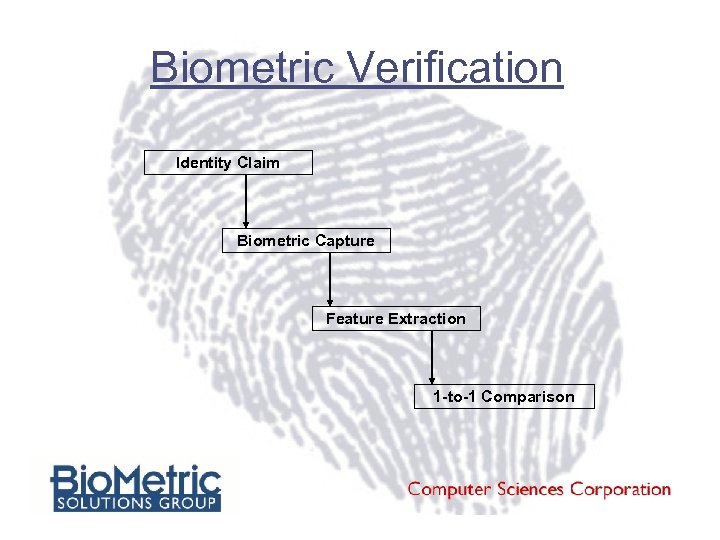
Biometric Verification Identity Claim Biometric Capture Feature Extraction 1 -to-1 Comparison
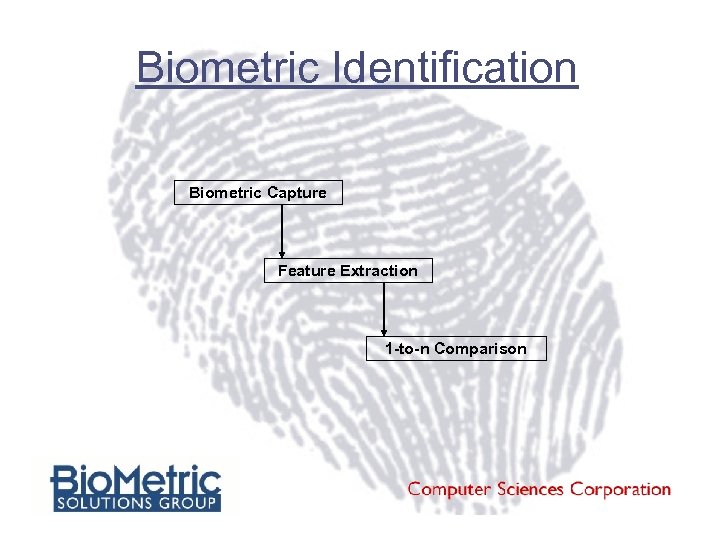
Biometric Identification Biometric Capture Feature Extraction 1 -to-n Comparison
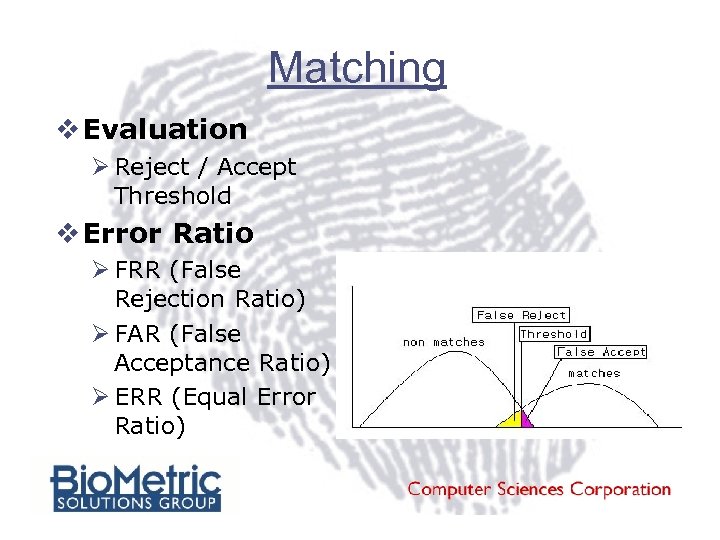
Matching v Evaluation Ø Reject / Accept Threshold v Error Ratio Ø FRR (False Rejection Ratio) Ø FAR (False Acceptance Ratio) Ø ERR (Equal Error Ratio)
Implementation v. Interoperability v. Bio. API ØANSI Fast track v. CBEFF ØCommon Biometric Exchange File Format ØUsed in Bio. API v. Multimode integration

Template Management v. Centralized ØTemplate security ØAdministration ØCommunications Infrastructure v. Distributed ØSmartcards Ø 2 -D Barcodes ØMemory buttons ØCounterfeiting
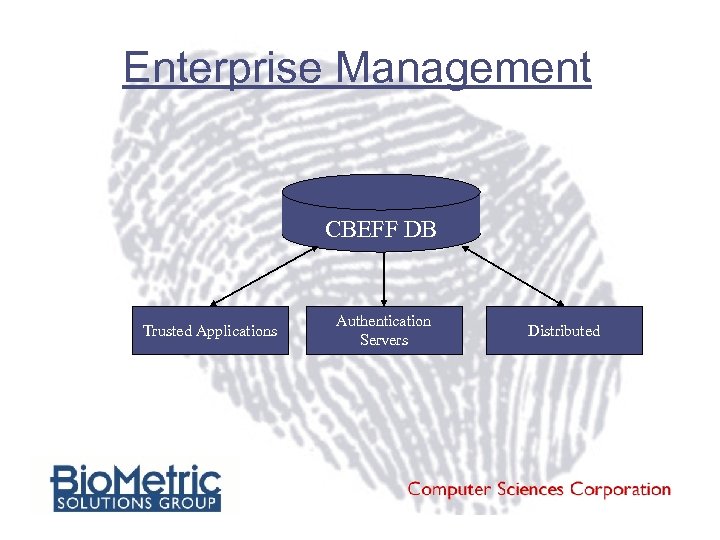
Enterprise Management CBEFF DB Trusted Applications Authentication Servers Distributed
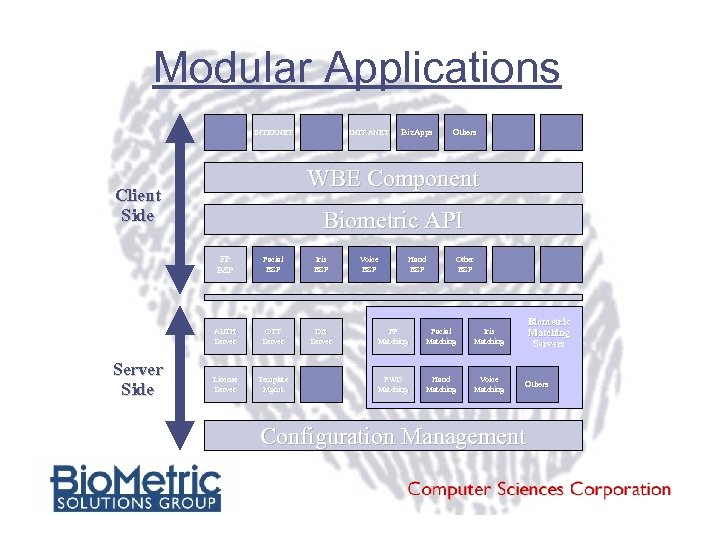
Modular Applications INTERNET INTRANET Others WBE Component Client Side Biometric API FP BSP Facial BSP Iris BSP AUTH Server Side Biz. Apps OTT Server DB Server License Server Template Mgmt Voice BSP Hand BSP Other BSP FP Matching Facial Matching PWD Matching Hand Matching Voice Matching Biometric Matching Servers Iris Matching Others Configuration Management
Fingerprint in Access Control v Lowest implementation cost v Widest availability v Matching technology Ø Correlation Ø Minutiae matching v Scanner technology Ø Optical Ø Solid-state/Capacitive Ø Ultrasonic
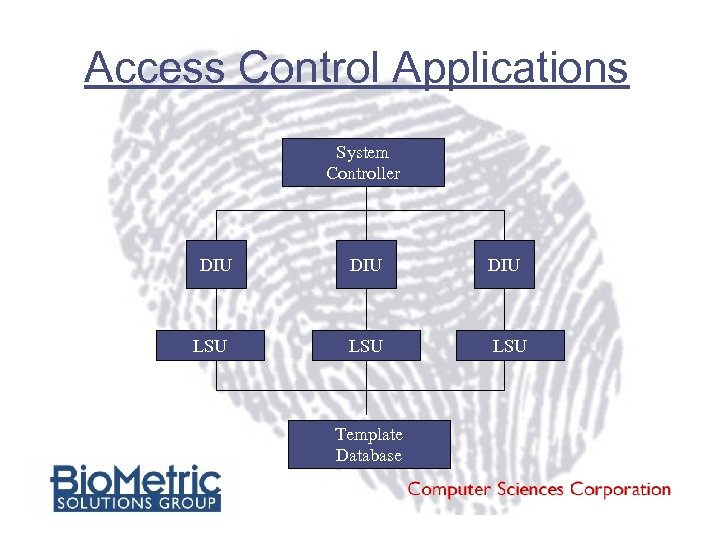
Access Control Applications System Controller DIU DIU LSU LSU Template Database
Integration Interfaces v. Legacy Systems ØWeigand ØOnly “industry standard” ØClock and Data ØProprietary v. Vendor products ØRS 485 ØTCP/IP
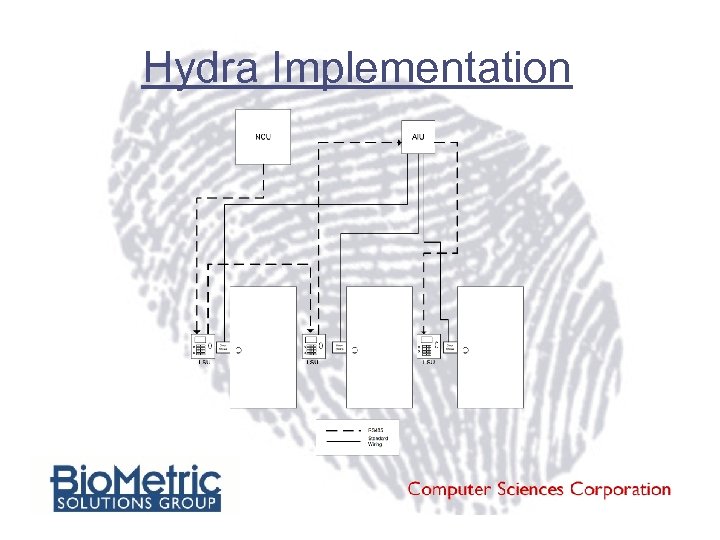
Hydra Implementation

Graterford Prison v. Barcode badge provides Guard PIN. v. Hydra performs fingerprint verification. v. Photo of verified guard displayed on touchscreen. v. Operator must visually confirm by touching photo on screen.
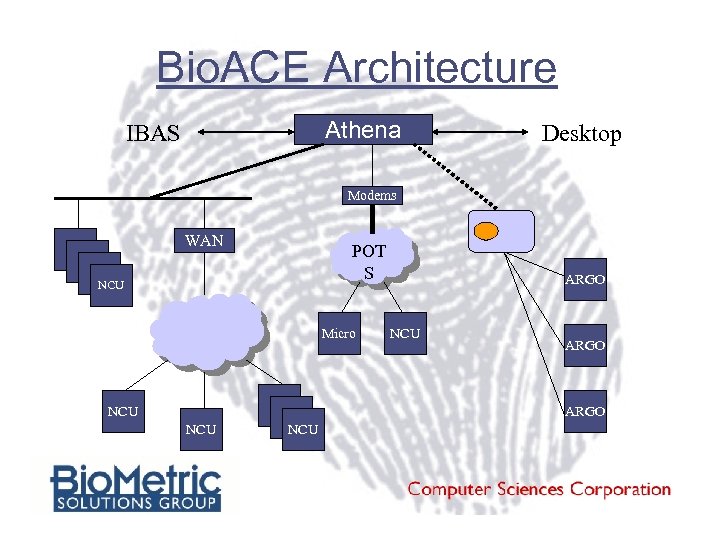
Bio. ACE Architecture Athena IBAS Desktop Modems WAN POT S NCU Micro NCU ARGO NCU

DISCUSSION
403f436e6d92d373cd36208807628374.ppt