a93e1225d516ef9b95a60a73b7f8fb14.ppt
- Количество слайдов: 30

Biometrics: Challenges and Applications Department of Computer Science & Engineering Ishwar K. Sethi Department of Computer Science & Engineering Oakland University, Rochester, MI 48309 isethi@oakland. edu www. cse. secs. oakland. edu/isethi iielab-secs. oakland. edu
Biometrics – What is it? Department of Computer Science & Engineering Technology for automated recognition or verification of the identity of a person using physiological or behavioral characteristics such as fingerprints, hand geometry, iris, voice, and signatures.
Recognition vs. Verification Department of Computer Science & Engineering • Recognition or identification implies checking whether a person is in the system’s database or not. (one-tomany search) • Verification or authentication implies checking the identity claim presented by a user. (one-to-one search)
Why Biometrics? • – Department of Computer Science & Engineering – • – – Better than password/PIN No need to memorize passwords Requires physical presence of the person to be identified Better than smart cards Cannot be stolen Cannot leave it at home
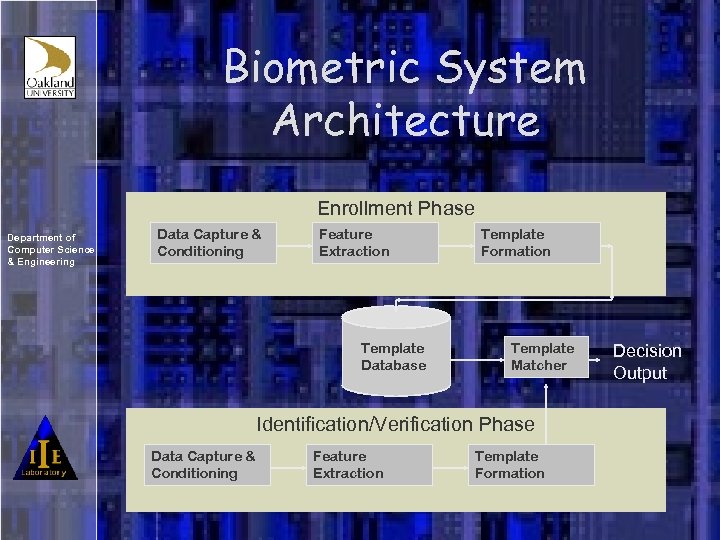
Biometric System Architecture Enrollment Phase Department of Computer Science & Engineering Data Capture & Conditioning Feature Extraction Template Database Template Formation Template Matcher Identification/Verification Phase Data Capture & Conditioning Feature Extraction Template Formation Decision Output
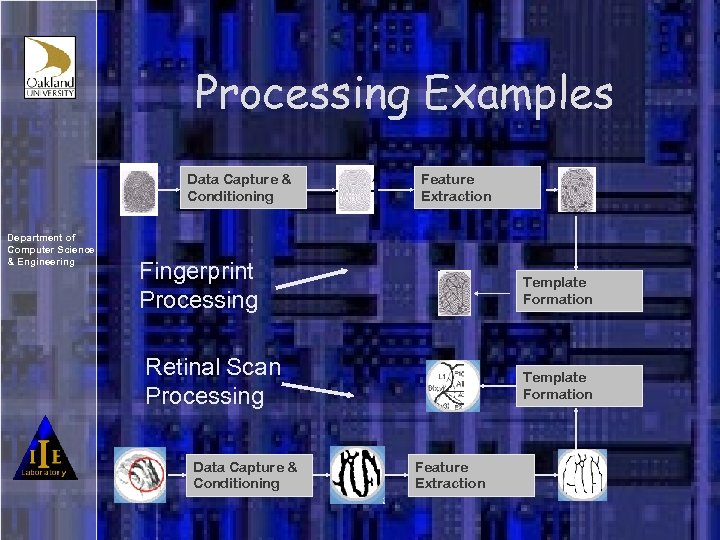
Processing Examples Data Capture & Conditioning Department of Computer Science & Engineering Feature Extraction Fingerprint Processing Template Formation Retinal Scan Processing Data Capture & Conditioning Template Formation Feature Extraction

An Example of a Face Template Department of Computer Science & Engineering
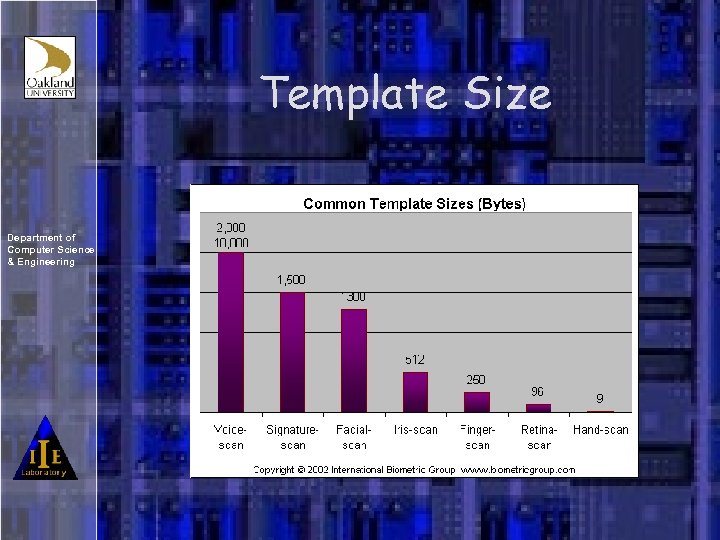
Template Size Department of Computer Science & Engineering
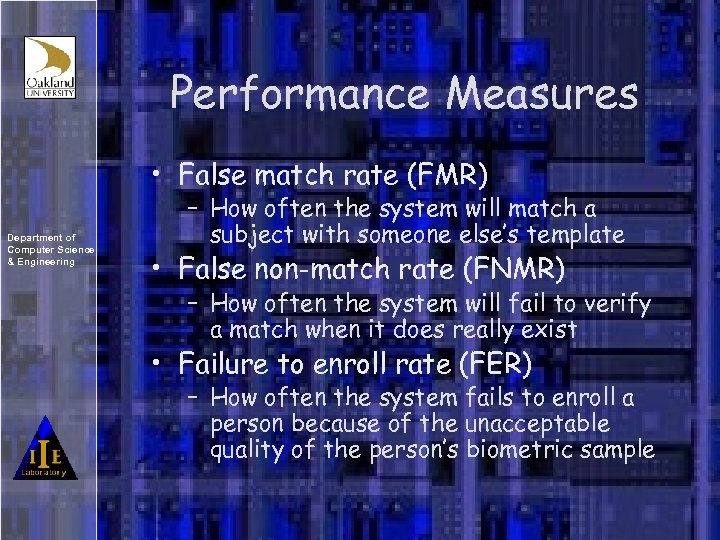
Performance Measures • False match rate (FMR) Department of Computer Science & Engineering – How often the system will match a subject with someone else’s template • False non-match rate (FNMR) – How often the system will fail to verify a match when it does really exist • Failure to enroll rate (FER) – How often the system fails to enroll a person because of the unacceptable quality of the person’s biometric sample
State of the Art Performance Metrics Department of Computer Science & Engineering • False match rates have been falling as the technology matures. Near zero rates are possible with some technologies • False non-match rates lie in single digit range • Failure to enroll rates can be as high as about 12%

Factors Affecting Performance • Data capture factors Department of Computer Science & Engineering – Lighting, background noise, pose etc. • Sensor interoperability • Temporal changes – Facial hair, eye glasses etc. • Segmentation error

Face Recognizer Challenges Department of Computer Science & Engineering

Segmentation Error Department of Computer Science & Engineering
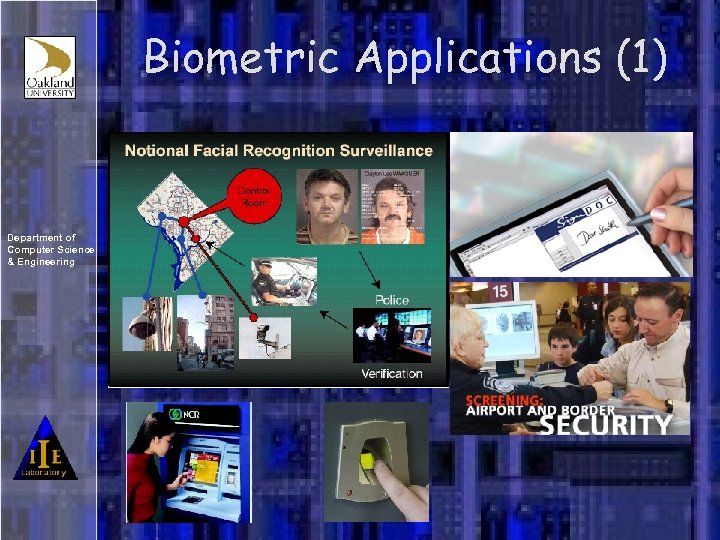
Biometric Applications (1) Department of Computer Science & Engineering
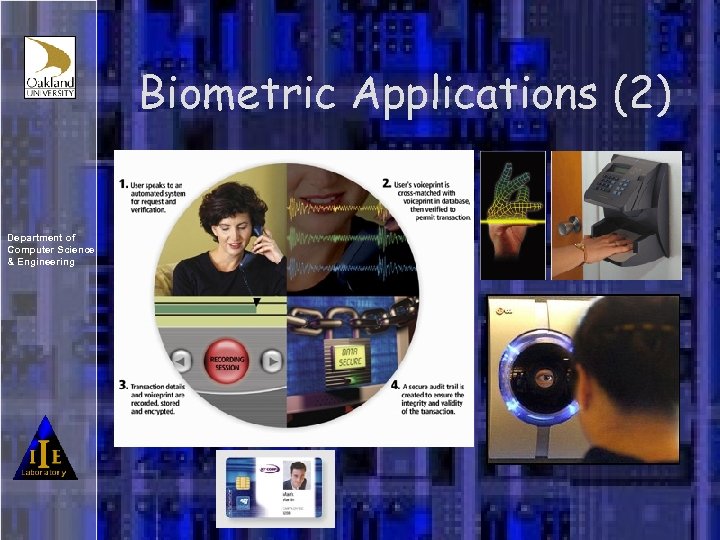
Biometric Applications (2) Department of Computer Science & Engineering
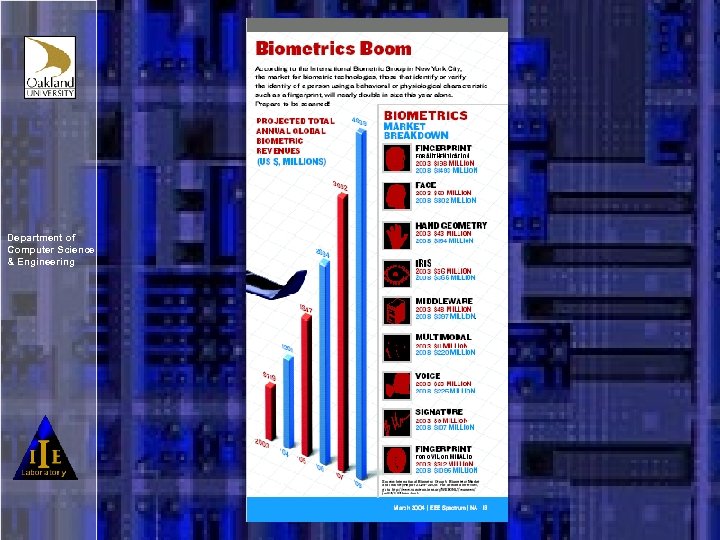
Department of Computer Science & Engineering
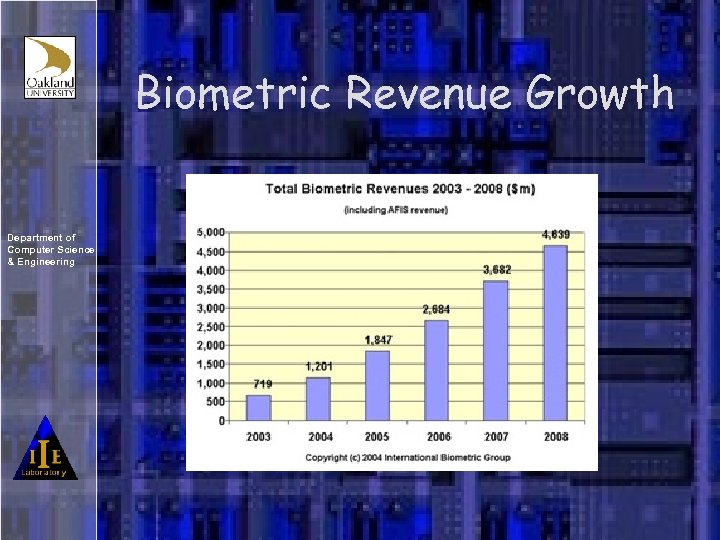
Biometric Revenue Growth Department of Computer Science & Engineering
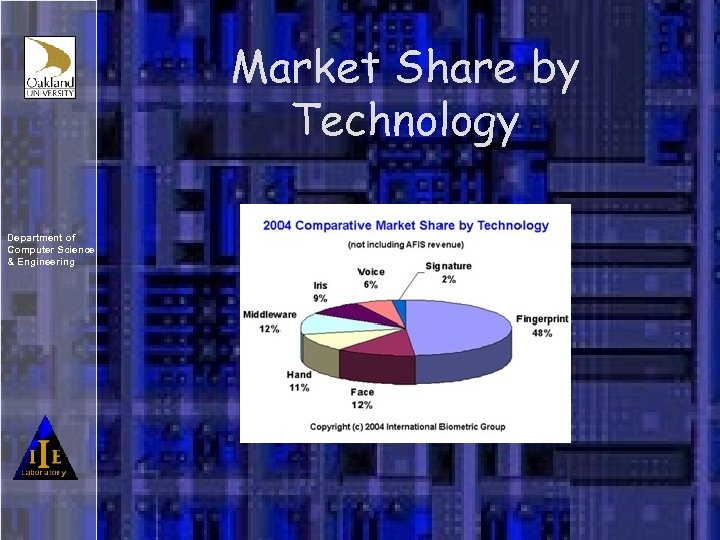
Market Share by Technology Department of Computer Science & Engineering

Leading Biometric Applications and Vertical Markets Modality Department of Computer Science & Engineering Application Key Vertical Market Fingerprint Civil Identification Government Face Recognition Surveillance & Screening Travel & Transportation Hand Geometry PC & Network Security Financial Sector Middleware Retail/ATM/POS Healthcare Iris Recognition Remote Authentication Source: International Biometric Group Law Enforcement
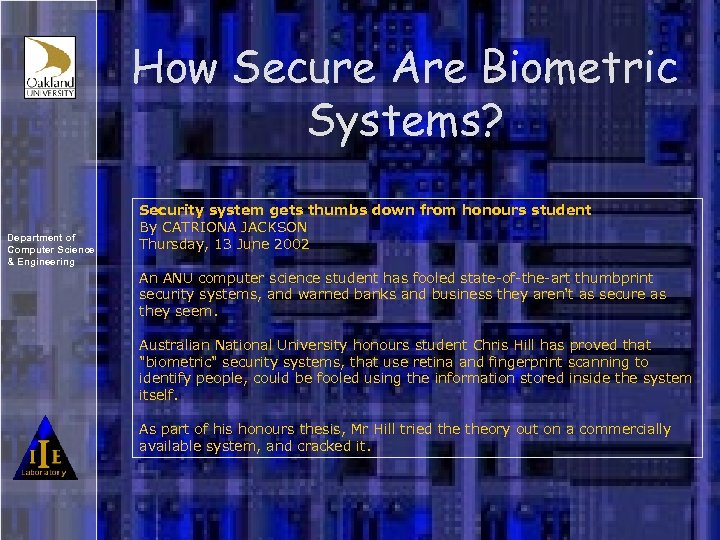
How Secure Are Biometric Systems? Department of Computer Science & Engineering Security system gets thumbs down from honours student By CATRIONA JACKSON Thursday, 13 June 2002 An ANU computer science student has fooled state-of-the-art thumbprint security systems, and warned banks and business they aren't as secure as they seem. Australian National University honours student Chris Hill has proved that "biometric" security systems, that use retina and fingerprint scanning to identify people, could be fooled using the information stored inside the system itself. As part of his honours thesis, Mr Hill tried theory out on a commercially available system, and cracked it.
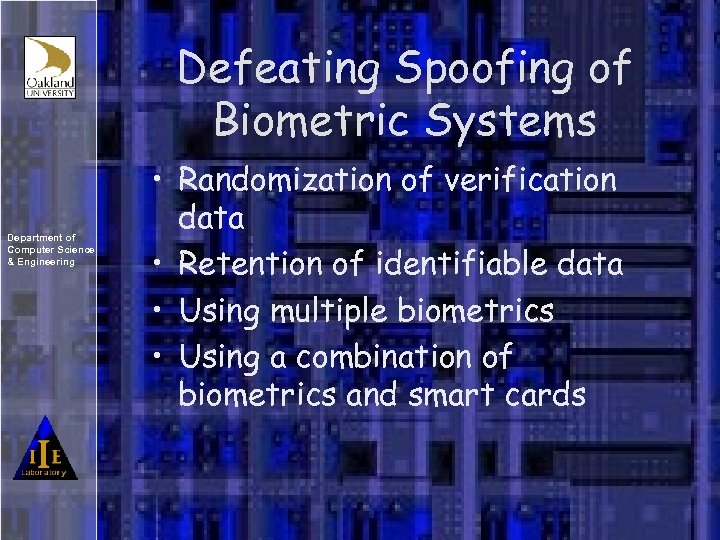
Defeating Spoofing of Biometric Systems Department of Computer Science & Engineering • Randomization of verification data • Retention of identifiable data • Using multiple biometrics • Using a combination of biometrics and smart cards

Societal Issues (1) • Are some people left out because of physiological considerations Department of Computer Science & Engineering – For example, about 3% of the population has poor fingerprint quality • Religious objections – “Mark of the Beast” objection. • Pat Robertson, host of “The 700 Club” and founder of The Christian Broadcasting Network, Inc. , observes that the “Bible says the time is going to come when you cannot buy or sell except when a mark is placed on your hand or forehead. ”

Societal Issues (2) • Informational privacy Department of Computer Science & Engineering – Function creep – Tracking – Identity theft • Physical Privacy – Stigmatization – Hygiene

Function Creep Department of Computer Science & Engineering • Function creep, or mission creep, is the process by which the original purpose for obtaining the information is widened to include purposes other than the one originally stated. Function creep can occur with or without the knowledge or agreement of the person providing the data. • Examples – The use of SSN for purposes it was never intended to is the best example of function creep. – South Carolina sold photographs of the state’s drivers to Image Data LLC, a New Hampshire company.

Tracking Department of Computer Science & Engineering • Possibility of linking different transactions to build a profile • Use of face recognition to covertly monitor individuals – Super Bowl in Tampa, Florida to identify would be criminals and terrorists

Identity Theft Department of Computer Science & Engineering • Although the biometrics provide a greater protection against the identity theft, the remote authentication does open up the possibility of identity theft. • Liveness/Spoofing

Privacy Risk Factors (1) • Overt/Covert Department of Computer Science & Engineering – Whether biometric signatures can be acquired without users knowledge or not. Covert systems are highly privacy invasive • Optional/Mandatory – Mandatory systems are considered more prone to privacy risks • Verification/Identification – Systems with identification capabilities are considered more risky • Ownership of biometric data – Systems where the biometric data resides with the owner are less susceptible to privacy abuse

Privacy Risk Factors (2) • Behavioral/Physiological Department of Computer Science & Engineering – Behavioral biometric systems are less likely to be employed in a privacy invasive manner • Templates/Identifiable Data – Systems that maintain identifiable data in addition to templates are more risky • Public/Private Sector – Public sector use is more open to abuse due to lax controls while private sector may be tempted to share/link with others
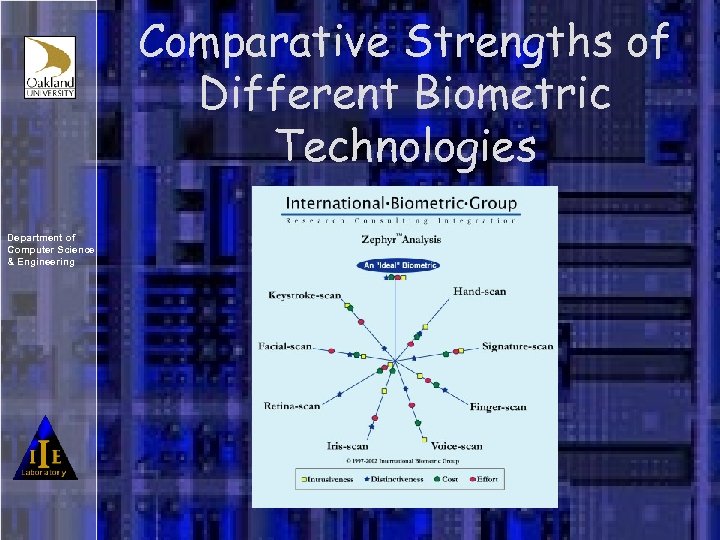
Comparative Strengths of Different Biometric Technologies Department of Computer Science & Engineering

Summary Department of Computer Science & Engineering • Biometrics is at the threshold of tremendous growth. Numerous applications are emerging. The war on terror hastened the deployment of biometrics • Much hype in performance. Lots of improvements are needed • Template protection and methods against spoofing are needed • Privacy concerns need better addressing
a93e1225d516ef9b95a60a73b7f8fb14.ppt