82646067c16bce1a789e867d2e205e95.ppt
- Количество слайдов: 25
Bindings and Profiles for Attribute-based Authz in the Grid Tom Scavo trscavo@ncsa. uiuc. edu NCSA x 509 -bindings-profiles-sep 06 1

Overview • Metadata Profile for the OASIS Security Assertion Markup Language (SAML) V 1. x • Metadata Extension for SAML V 2. 0 and V 1. x Query Requesters • SAML V 1. 1 Profiles for X. 509 Subjects • SAML V 2. 0 Profiles for X. 509 Subjects • X. 509 Binding for SAML • X. 509 Attribute-based Authorization Profile for SAML • BONUS! Level of Assurance Attribute! x 509 -bindings-profiles-sep 06 2
Metadata Profile for SAML V 1. x • SAML V 2. 0 includes a Metadata Profile • The Metadata Profile for the OASIS Security Assertion Markup Language (SAML) V 1. x profiles the use of SAML V 2. 0 metadata with SAML V 1. x entities • Document is in final stages of pipeline • Shibboleth V 1. 3 (or later) supports SAML V 1. x metadata x 509 -bindings-profiles-sep 06 3
Metadata for Query Requesters • Grid. Shib use cases (e. g. ) are rife with notion of standalone attribute requesters • The Metadata Extension for SAML V 2. 0 and V 1. x Query Requesters profiles use of SAML metadata with standalone query requesters • Document is in final stages of pipeline • Shibboleth V 1. 3 (or later) supports metadata for SAML V 1. x attribute requester • It’s not clear if Shibboleth V 2. 0 will support SAML V 2. 0 attribute requester x 509 -bindings-profiles-sep 06 4

SAML Profiles for X. 509 Subjects • Two profile sets have been submitted to the OASIS Security Services TC: – SAML V 1. 1 Profiles for X. 509 Subjects http: //www. oasisopen. org/committees/document. php? document_id=19996&wg_abb rev=security – SAML V 2. 0 Profiles for X. 509 Subjects http: //www. oasisopen. org/committees/document. php? document_id=20000&wg_abb rev=security • Comments are welcome! http: //www. oasisopen. org/committees/tc_home. php? wg_abbrev=security x 509 -bindings-profiles-sep 06 5
SAML V 1. 1 Profiles • The SAML V 1. 1 profile set consists of four layered profiles for X. 509 subjects: 1. X. 509 SAML Subject Profile 2. SAML Assertion Profile for X. 509 Subjects 3. SAML Attribute Query Profile for X. 509 Subjects 4. SAML Attribute Self-Query Profile for X. 509 Subjects • Document is brand new and not vetted x 509 -bindings-profiles-sep 06 6
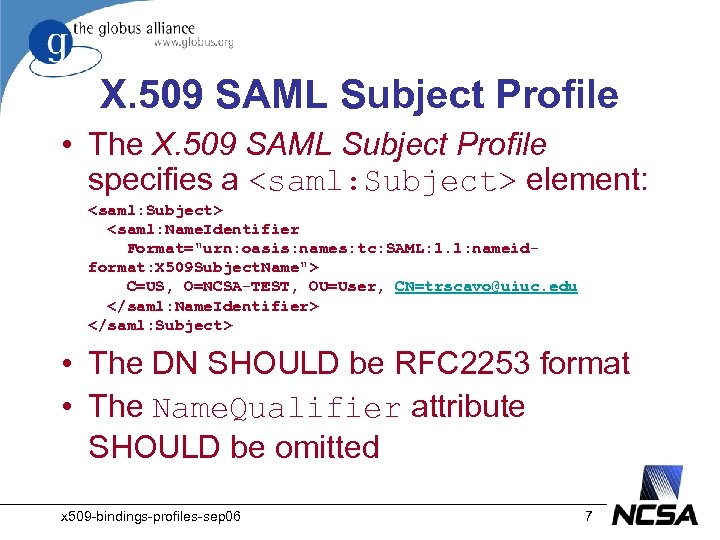
X. 509 SAML Subject Profile • The X. 509 SAML Subject Profile specifies a <saml: Subject> element: <saml: Subject> <saml: Name. Identifier Format="urn: oasis: names: tc: SAML: 1. 1: nameidformat: X 509 Subject. Name"> C=US, O=NCSA-TEST, OU=User, CN=trscavo@uiuc. edu </saml: Name. Identifier> </saml: Subject> • The DN SHOULD be RFC 2253 format • The Name. Qualifier attribute SHOULD be omitted x 509 -bindings-profiles-sep 06 7
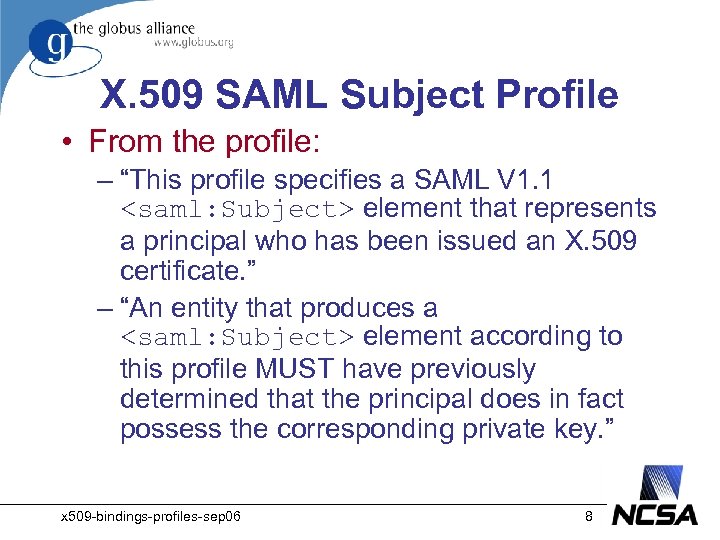
X. 509 SAML Subject Profile • From the profile: – “This profile specifies a SAML V 1. 1 <saml: Subject> element that represents a principal who has been issued an X. 509 certificate. ” – “An entity that produces a <saml: Subject> element according to this profile MUST have previously determined that the principal does in fact possess the corresponding private key. ” x 509 -bindings-profiles-sep 06 8
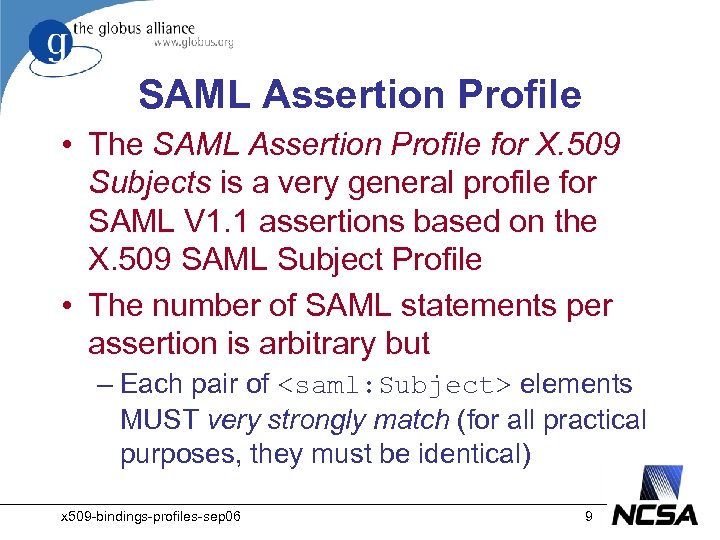
SAML Assertion Profile • The SAML Assertion Profile for X. 509 Subjects is a very general profile for SAML V 1. 1 assertions based on the X. 509 SAML Subject Profile • The number of SAML statements per assertion is arbitrary but – Each pair of <saml: Subject> elements MUST very strongly match (for all practical purposes, they must be identical) x 509 -bindings-profiles-sep 06 9
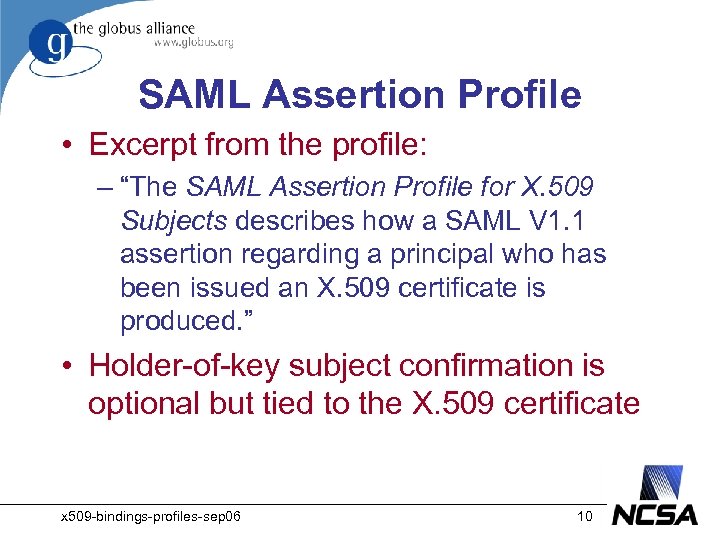
SAML Assertion Profile • Excerpt from the profile: – “The SAML Assertion Profile for X. 509 Subjects describes how a SAML V 1. 1 assertion regarding a principal who has been issued an X. 509 certificate is produced. ” • Holder-of-key subject confirmation is optional but tied to the X. 509 certificate x 509 -bindings-profiles-sep 06 10
SAML Attribute Query Profile • The SAML Attribute Query Profile for X. 509 Subjects specifies how a service provider and an identity provider exchange attributes about a principal who has been issued an X. 509 certificate • This profile relies on the X. 509 SAML Subject Profile and the SAML Assertion Profile for X. 509 Subjects x 509 -bindings-profiles-sep 06 11
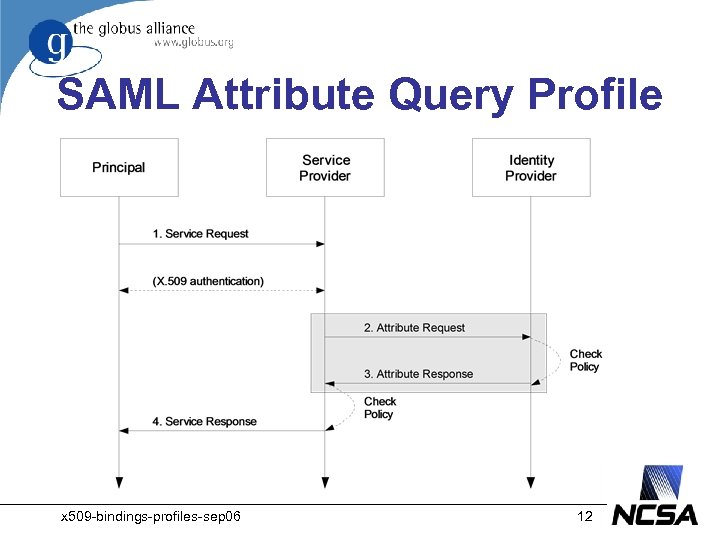
SAML Attribute Query Profile x 509 -bindings-profiles-sep 06 12
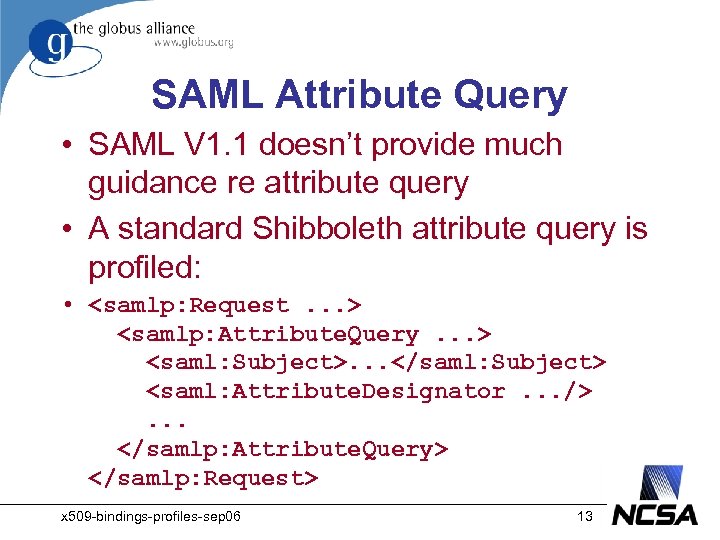
SAML Attribute Query • SAML V 1. 1 doesn’t provide much guidance re attribute query • A standard Shibboleth attribute query is profiled: • <samlp: Request. . . > <samlp: Attribute. Query. . . > <saml: Subject>. . . </saml: Subject> <saml: Attribute. Designator. . . />. . . </samlp: Attribute. Query> </samlp: Request> x 509 -bindings-profiles-sep 06 13

Attribute Query Response • <samlp: Response. . . > <samlp: Status>. . . </samlp: Status> <saml: Assertion. . . > <saml: Conditions Not. Before="2006 -07 -17 T 22: 21: 41 Z" Not. On. Or. After="2006 -07 -17 T 22: 51: 41 Z"> <saml: Audience. Restriction. Condition> <saml: Audience>. . . </saml: Audience> </saml: Audience. Restriction. Condition> </saml: Conditions> <saml: Attribute. Statement> <saml: Subject>. . . </saml: Subject> <saml: Attribute. . . > <saml: Attribute. Value. . . >. . . </saml: Attribute. Value> </saml: Attribute>. . . </saml: Attribute. Statement> </saml: Assertion> </samlp: Response> x 509 -bindings-profiles-sep 06 14
SAML Attribute Self-Query Profile • The SAML Attribute Self-Query Profile for X. 509 Subjects specifies how a principal who has been issued an X. 509 certificate self-queries an identity provider for attributes • This profile extends the SAML Attribute Query Profile for X. 509 Subjects • A driving use case for self-query is ca. BIG Dorian x 509 -bindings-profiles-sep 06 15
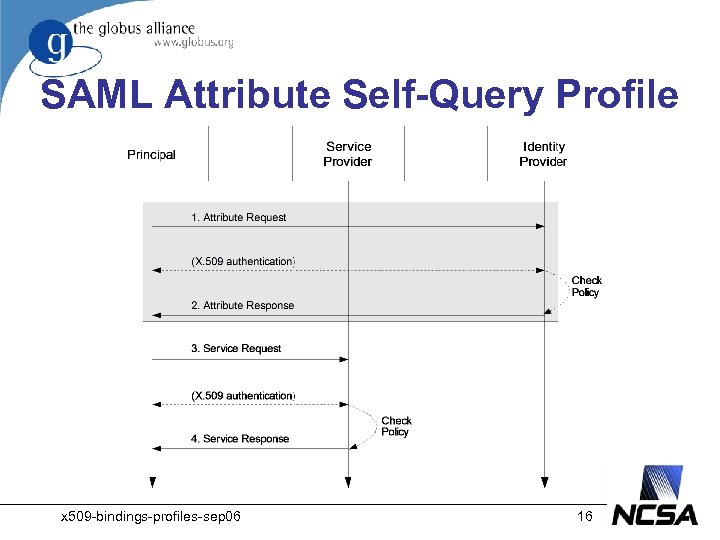
SAML Attribute Self-Query Profile x 509 -bindings-profiles-sep 06 16
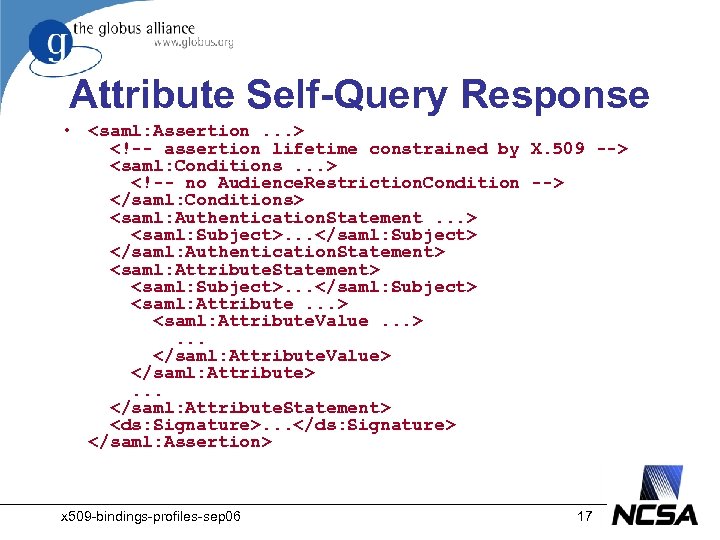
Attribute Self-Query Response • <saml: Assertion. . . > <!-- assertion lifetime constrained by X. 509 --> <saml: Conditions. . . > <!-- no Audience. Restriction. Condition --> </saml: Conditions> <saml: Authentication. Statement. . . > <saml: Subject>. . . </saml: Subject> </saml: Authentication. Statement> <saml: Attribute. Statement> <saml: Subject>. . . </saml: Subject> <saml: Attribute. . . > <saml: Attribute. Value. . . >. . . </saml: Attribute. Value> </saml: Attribute>. . . </saml: Attribute. Statement> <ds: Signature>. . . </ds: Signature> </saml: Assertion> x 509 -bindings-profiles-sep 06 17
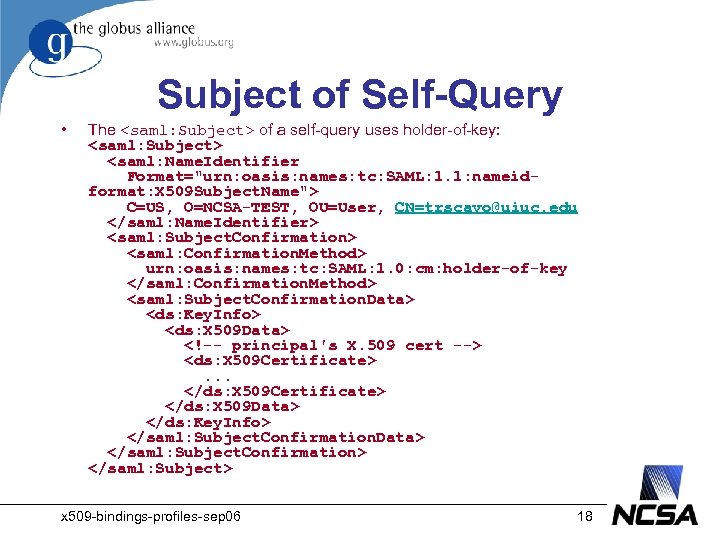
Subject of Self-Query • The <saml: Subject> of a self-query uses holder-of-key: <saml: Subject> <saml: Name. Identifier Format="urn: oasis: names: tc: SAML: 1. 1: nameidformat: X 509 Subject. Name"> C=US, O=NCSA-TEST, OU=User, CN=trscavo@uiuc. edu </saml: Name. Identifier> <saml: Subject. Confirmation> <saml: Confirmation. Method> urn: oasis: names: tc: SAML: 1. 0: cm: holder-of-key </saml: Confirmation. Method> <saml: Subject. Confirmation. Data> <ds: Key. Info> <ds: X 509 Data> <!-- principal's X. 509 cert --> <ds: X 509 Certificate>. . . </ds: X 509 Certificate> </ds: X 509 Data> </ds: Key. Info> </saml: Subject. Confirmation. Data> </saml: Subject. Confirmation> </saml: Subject> x 509 -bindings-profiles-sep 06 18
SAML V 2. 0 Profiles • Likewise the SAML V 2. 0 profile set consists of four sub-profiles: 1. X. 509 SAML Subject Profile 2. SAML Assertion Profile for X. 509 Subjects 3. SAML Attribute Query Profile for X. 509 Subjects 4. SAML Attribute Self-Query Profile for X. 509 Subjects • Significant difference is encryption x 509 -bindings-profiles-sep 06 19

Revision History • SAML V 2. 0 profiles have a long history: – Draft-01, 22 Jun 2004 – Draft-02, 03 Feb 2005 – Draft-07, 23 May 2005 – CD-01, 01 Jun 2005 – Draft-08, 14 Mar 2006 – CD-02, 28 Mar 2006 – Draft-09, 26 Jun 2006 – Draft-10, 05 Jul 2006 – Draft-11, 24 Aug 2006 x 509 -bindings-profiles-sep 06 20
X. 509 Binding for SAML <Assertion> … </Assertion> An ASN. 1 SEQUENCE of <saml: Assertion> elements at a wellknown, non-critical X. 509 v 3 certificate extension This profile is a work in progress (but it won’t be an OASIS profile) x 509 -bindings-profiles-sep 06 21

X. 509 Attribute-based Authz • Goal: Use SAML Assertion Profile and X. 509 Binding to profile attribute push • Distinguish between two types of bound attribute assertions: – Self-issued assertions – Third-party assertions (e. g. , Shib-issued) • https: //authdev. it. ohiostate. edu/twiki/bin/view/Grid. Shib/X 509 B inding. SAML x 509 -bindings-profiles-sep 06 22

Bound Assertion Example • <!-- shib-enabled community portal --> <saml: Assertion. . . > <saml: Conditions. . . >. . . </saml: Conditions> <saml: Advice> <!-- attribute assertion obtained from campus Shib AA --> <saml: Assertion. . . >. . . </saml: Assertion> <!-- authn assertion obtained from campus Shib Id. P (if available) --> <saml: Assertion. . . >. . . </saml: Assertion> </saml: Advice> <!-- community attributes --> <saml: Attribute. Statement. . . > <!-- the subject of this proxy --> <saml: Subject>. . . </saml: Attribute. Statement> </saml: Assertion> x 509 -bindings-profiles-sep 06 23
MACE-Dir Lo. A Attribute • MACE-Dir is profiling use of authn. Loa attribute in conjunction with us. Person • Proposed SAML binding: <saml: Attribute xmlns: saml="urn: oasis: names: tc: SAML: 2. 0: assertion“ xmlns: x 500="urn: oasis: names: tc: SAML: 2. 0: profiles: attribute: X 500" x 500: Encoding="LDAP" Name. Format="urn: oasis: names: tc: SAML: 2. 0: attrname-format: uri" Name="urn: oid: . . . " Friendly. Name="authn. LOA"> <saml: Attribute. Value xsi: type="xs: any. URI">. . . </saml: Attribute. Value> </saml: Attribute> • Legal attribute values are per federation x 509 -bindings-profiles-sep 06 24

E-Auth Lo. A Values • For the E-Authentication Program, the recommended initial set of values is: – http: //www. cio. gov/eauthentication/us person/authnloa#nist-sp-800 -63 -1 – http: //www. cio. gov/eauthentication/us person/authnloa#nist-sp-800 -63 -2 – http: //www. cio. gov/eauthentication/us person/authnloa#nist-sp-800 -63 -3 – http: //www. cio. gov/eauthentication/us person/authnloa#nist-sp-800 -63 -4 – http: //www. cio. gov/eauthentication/us person/authnloa#test • In. Common values have not been proposed x 509 -bindings-profiles-sep 06 25
82646067c16bce1a789e867d2e205e95.ppt