c92225feb3fdd91da8eac40afa95f94a.ppt
- Количество слайдов: 56

BIM 302: Computer Networks • • Time: Thursdays 09: 15 -12: 00 Location: BLab 4 Instructor: Emre Kaçmaz – Yasin Pak Grading: – – Midterm I – 15% Midterm II – 15% 1 Final – 40% Homeworks - 30% 1
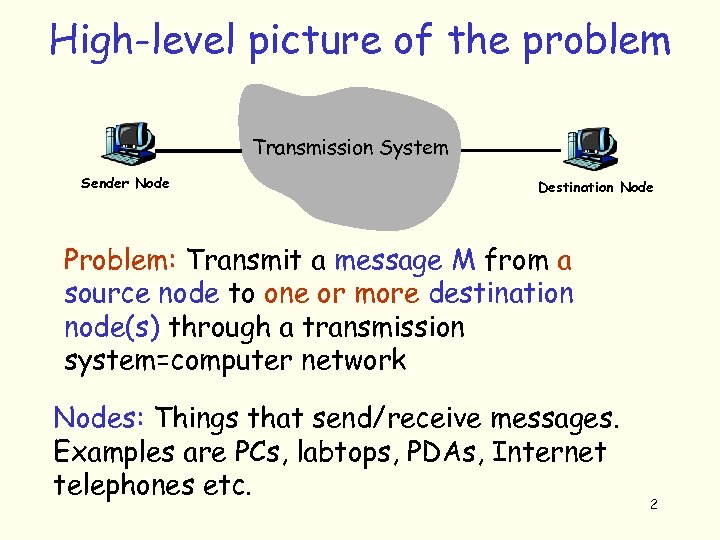
High-level picture of the problem Transmission System Sender Node Destination Node Problem: Transmit a message M from a source node to one or more destination node(s) through a transmission system=computer network Nodes: Things that send/receive messages. Examples are PCs, labtops, PDAs, Internet telephones etc. 2
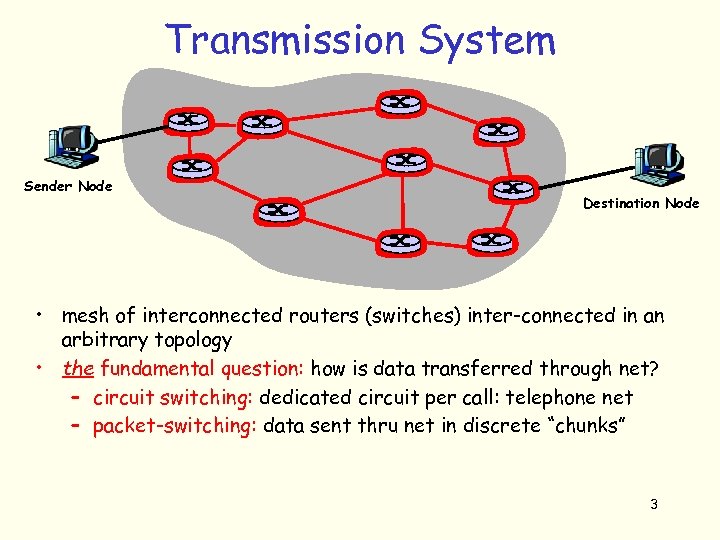
Transmission System Sender Node Destination Node • mesh of interconnected routers (switches) inter-connected in an arbitrary topology • the fundamental question: how is data transferred through net? – circuit switching: dedicated circuit per call: telephone net – packet-switching: data sent thru net in discrete “chunks” 3
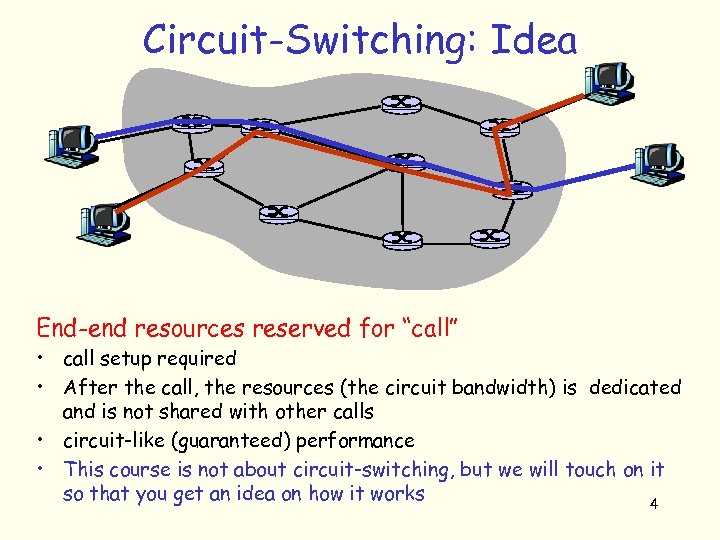
Circuit-Switching: Idea End-end resources reserved for “call” • call setup required • After the call, the resources (the circuit bandwidth) is dedicated and is not shared with other calls • circuit-like (guaranteed) performance • This course is not about circuit-switching, but we will touch on it so that you get an idea on how it works 4
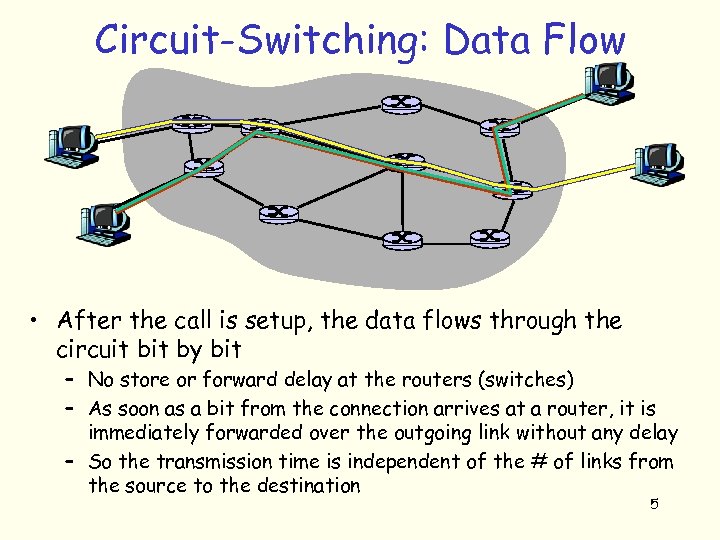
Circuit-Switching: Data Flow • After the call is setup, the data flows through the circuit by bit – No store or forward delay at the routers (switches) – As soon as a bit from the connection arrives at a router, it is immediately forwarded over the outgoing link without any delay – So the transmission time is independent of the # of links from the source to the destination 5
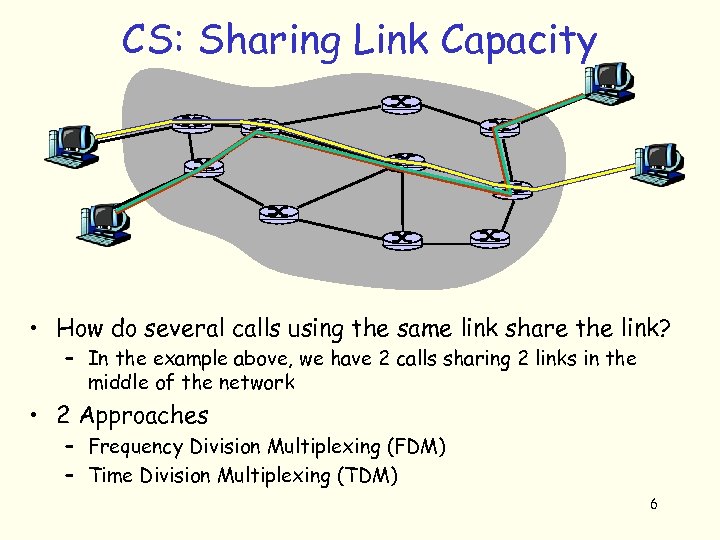
CS: Sharing Link Capacity • How do several calls using the same link share the link? – In the example above, we have 2 calls sharing 2 links in the middle of the network • 2 Approaches – Frequency Division Multiplexing (FDM) – Time Division Multiplexing (TDM) 6
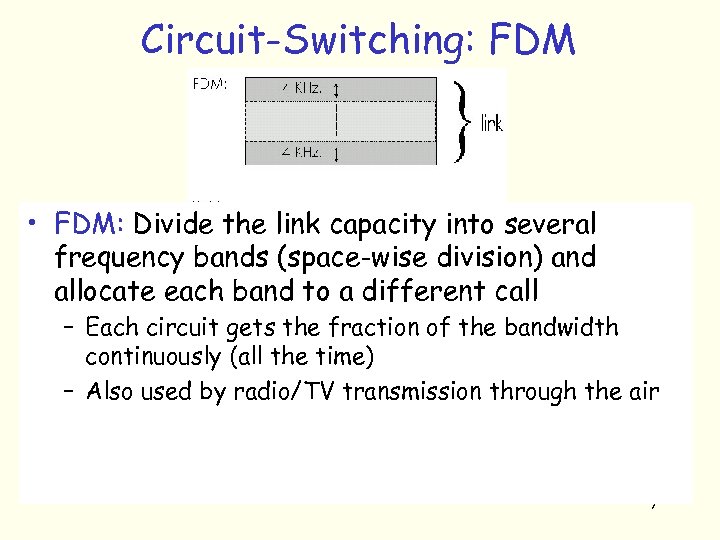
Circuit-Switching: FDM • FDM: Divide the link capacity into several frequency bands (space-wise division) and allocate each band to a different call – Each circuit gets the fraction of the bandwidth continuously (all the time) – Also used by radio/TV transmission through the air 7
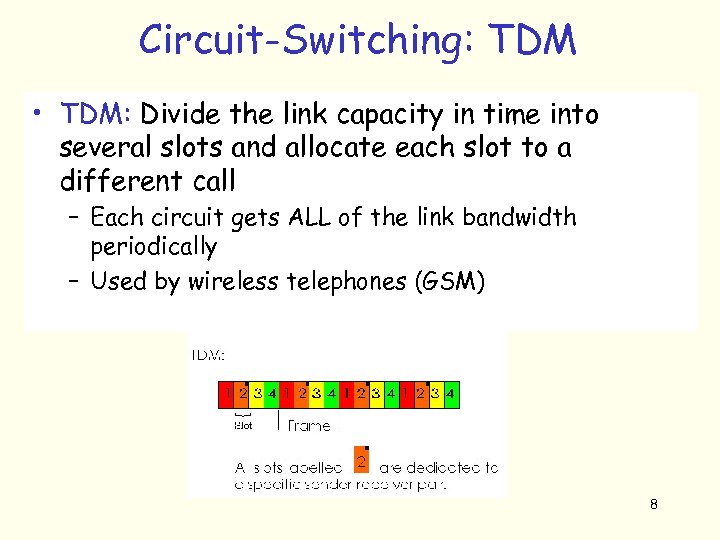
Circuit-Switching: TDM • TDM: Divide the link capacity in time into several slots and allocate each slot to a different call – Each circuit gets ALL of the link bandwidth periodically – Used by wireless telephones (GSM) 8
Circuit Switching Example • 1890 -current: Phone network – – – Fixed bit rate Mostly voice Not fault-tolerant Components extremely reliable Global application-level knowledge throughout network 9
Circuit Switching: Summary • Establish a dedicated circuit before sending data – – Dedicated resources Data flows through the circuit No store and forward at the switches (routers) Good for constant-bit-rate traffic such as voice • BUT – Dedicated resources means if no data is flowing the circuit, the allocated resources are idle • Leads to waste of network resources • Might be OK for telephone calls where two parties are typically talking all the time • But is this good if two people are exchanging a data as in a instant messaging session? – How can be let other people use unused bandwidth? • Packet Switching -- Next 10
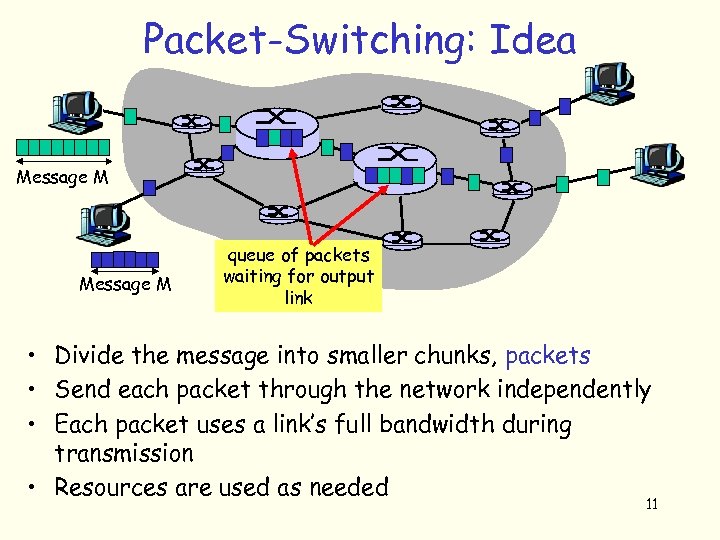
Packet-Switching: Idea Message M queue of packets waiting for output link • Divide the message into smaller chunks, packets • Send each packet through the network independently • Each packet uses a link’s full bandwidth during transmission • Resources are used as needed 11
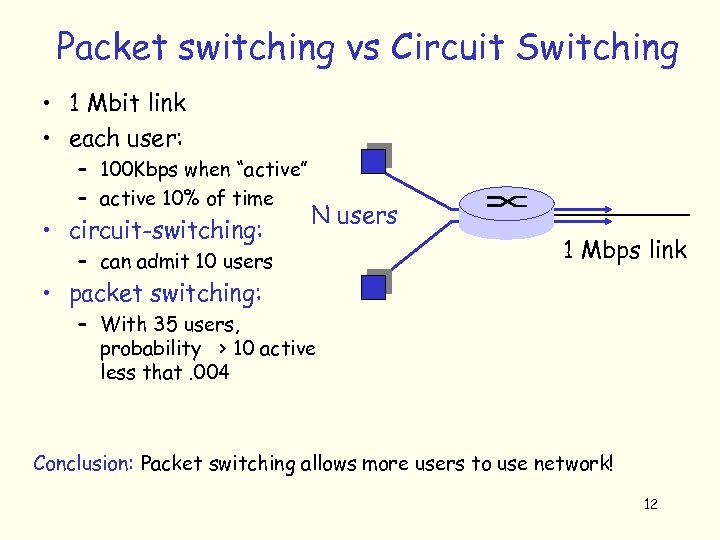
Packet switching vs Circuit Switching • 1 Mbit link • each user: – 100 Kbps when “active” – active 10% of time • circuit-switching: N users – can admit 10 users 1 Mbps link • packet switching: – With 35 users, probability > 10 active less that. 004 Conclusion: Packet switching allows more users to use network! 12
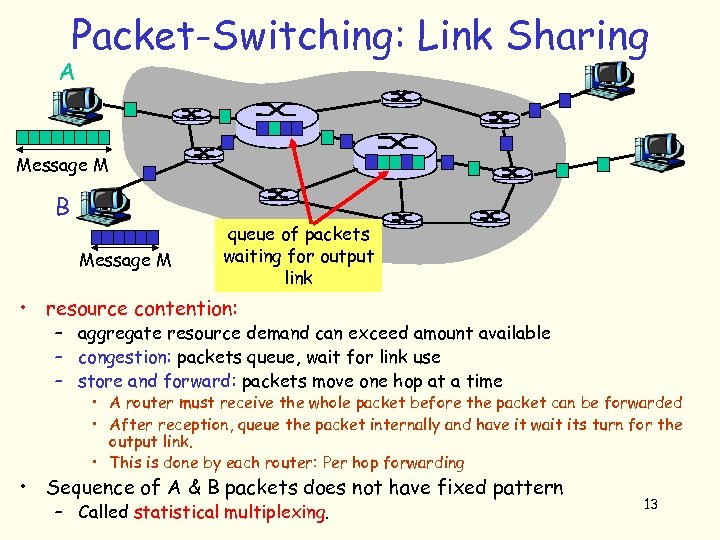
Packet-Switching: Link Sharing A Message M B Message M queue of packets waiting for output link • resource contention: – aggregate resource demand can exceed amount available – congestion: packets queue, wait for link use – store and forward: packets move one hop at a time • A router must receive the whole packet before the packet can be forwarded • After reception, queue the packet internally and have it wait its turn for the output link. • This is done by each router: Per hop forwarding • Sequence of A & B packets does not have fixed pattern – Called statistical multiplexing. 13
Packet-Switching: Issues • Two Fundamental Questions must be answered in a packet-switched network: 1. What should the packet size be? • Fixed-size or variable-sized packets? • How big? 2. Should we establish an end-to-end path through the network for the packets to flow? • Yes: Virtual-Circuit Networks (X. 25, Frame-Relay, ATM) • No: Datagram Networks (the Internet) 14
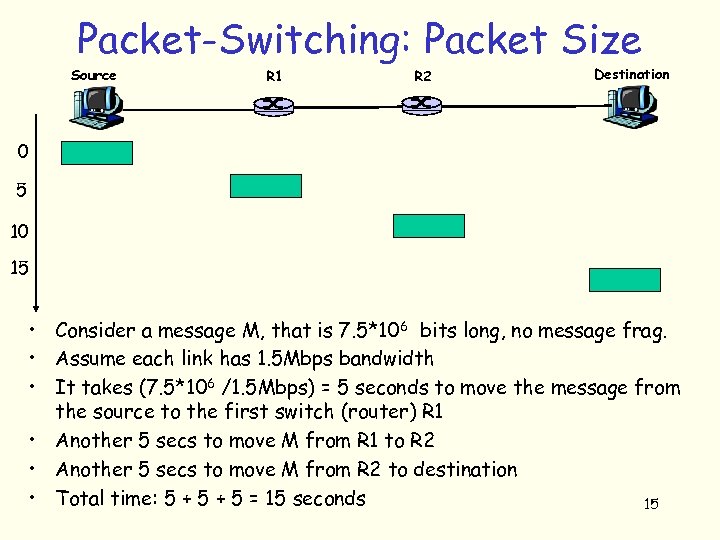
Packet-Switching: Packet Size Source R 1 R 2 Destination 0 5 10 15 • Consider a message M, that is 7. 5*106 bits long, no message frag. • Assume each link has 1. 5 Mbps bandwidth • It takes (7. 5*106 /1. 5 Mbps) = 5 seconds to move the message from the source to the first switch (router) R 1 • Another 5 secs to move M from R 1 to R 2 • Another 5 secs to move M from R 2 to destination • Total time: 5 + 5 = 15 seconds 15
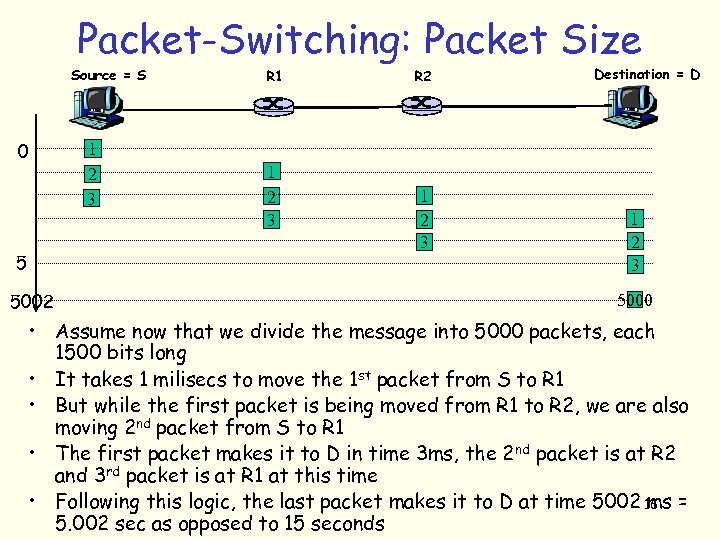
Packet-Switching: Packet Size Source = S 0 5 5002 1 2 3 R 1 1 2 3 R 2 1 2 3 Destination = D 1 2 3 5000 • Assume now that we divide the message into 5000 packets, each 1500 bits long • It takes 1 milisecs to move the 1 st packet from S to R 1 • But while the first packet is being moved from R 1 to R 2, we are also moving 2 nd packet from S to R 1 • The first packet makes it to D in time 3 ms, the 2 nd packet is at R 2 and 3 rd packet is at R 1 at this time • Following this logic, the last packet makes it to D at time 5002 16 = ms 5. 002 sec as opposed to 15 seconds
Packet-Switching: Packet Size • Small-sized packets has yet another advantage – Bit errors can be introduced as packet travels through the network. In such cases the packet is simply discarded • • The smaller the packet, the smaller the discarded info If small packets are so good, why not make them 1 byte – – – Each packet carries some headers with it Headers are used for packet forwarding, and other stuff The smaller the packet, the bigger the header to payload ratio, which translates to more waste of bandwidth – Consider 100 byte packets with 20 byte header • – 20% bandwidth waste Consider 1000 byte packets with 20 byte header • 2% bandwidth waste 17
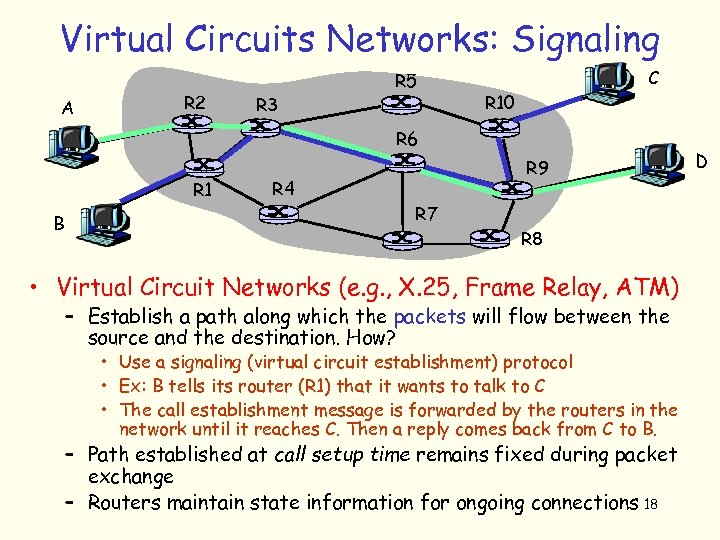
Virtual Circuits Networks: Signaling A R 2 R 3 R 5 C R 10 R 6 R 1 B R 9 R 4 R 7 R 8 • Virtual Circuit Networks (e. g. , X. 25, Frame Relay, ATM) – Establish a path along which the packets will flow between the source and the destination. How? • Use a signaling (virtual circuit establishment) protocol • Ex: B tells its router (R 1) that it wants to talk to C • The call establishment message is forwarded by the routers in the network until it reaches C. Then a reply comes back from C to B. – Path established at call setup time remains fixed during packet exchange – Routers maintain state information for ongoing connections 18 D
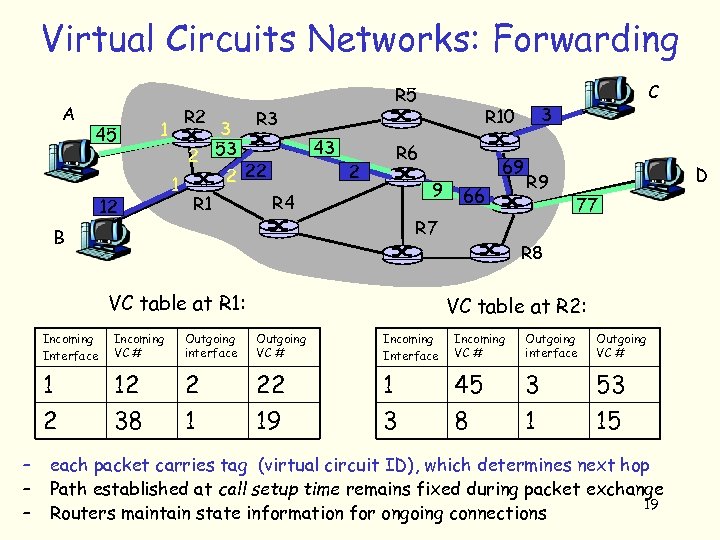
Virtual Circuits Networks: Forwarding A 45 1 12 R 5 R 2 R 3 3 2 53 2 22 1 R 4 R 1 43 2 3 R 10 R 6 9 69 66 R 9 R 7 B C D 77 R 8 VC table at R 1: VC table at R 2: Incoming Interface Outgoing interface Outgoing VC # Incoming Interface Incoming VC # Outgoing interface Outgoing VC # 1 2 – – – Incoming VC # 12 38 2 1 22 19 1 3 45 8 3 1 53 15 each packet carries tag (virtual circuit ID), which determines next hop Path established at call setup time remains fixed during packet exchange 19 Routers maintain state information for ongoing connections
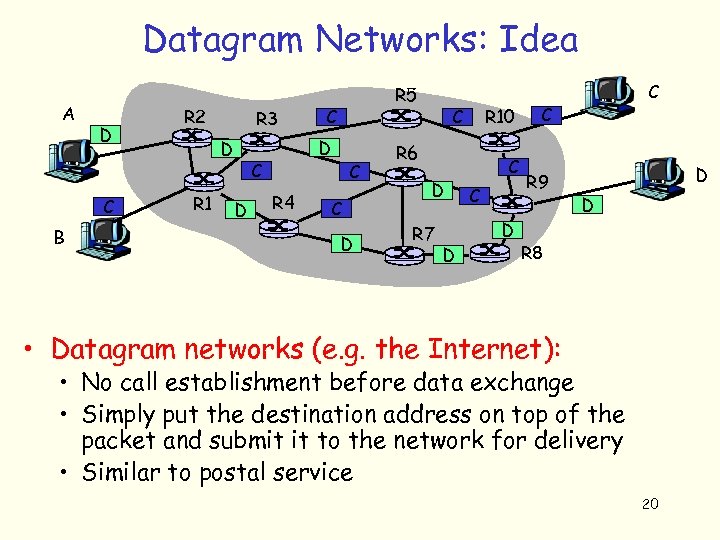
Datagram Networks: Idea A D C B R 2 R 3 D R 1 C D R 5 R 4 C C D R 10 C R 6 D R 7 D C C R 9 D D R 8 • Datagram networks (e. g. the Internet): • No call establishment before data exchange • Simply put the destination address on top of the packet and submit it to the network for delivery • Similar to postal service 20
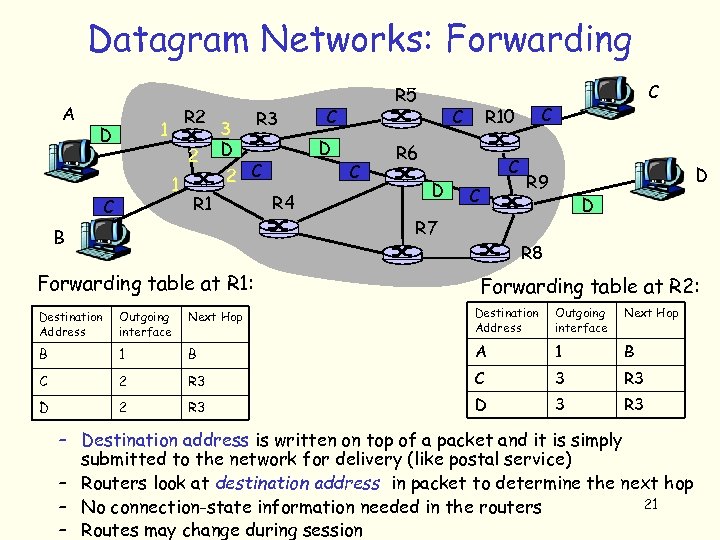
Datagram Networks: Forwarding A R 2 1 D 2 1 C 3 D R 3 R 1 B C D 2 C R 4 R 5 C R 6 D C R 10 C C D R 9 D R 7 R 8 Forwarding table at R 1: Forwarding table at R 2: Destination Address Outgoing interface Next Hop B 1 B A 1 B C 2 R 3 C 3 R 3 D 2 R 3 D 3 R 3 – Destination address is written on top of a packet and it is simply submitted to the network for delivery (like postal service) – Routers look at destination address in packet to determine the next hop 21 – No connection-state information needed in the routers – Routes may change during session
Packet switching versus circuit switching Is packet switching a “slam dunk winner? ” • Great for bursty data – resource sharing • But, excessive congestion: packet delay and loss – protocols needed for reliable data transfer, congestion control • Q: How to provide circuit-like behavior? – Bandwidth guarantees needed for audio/video apps – Active research area: IP Qo. S 22
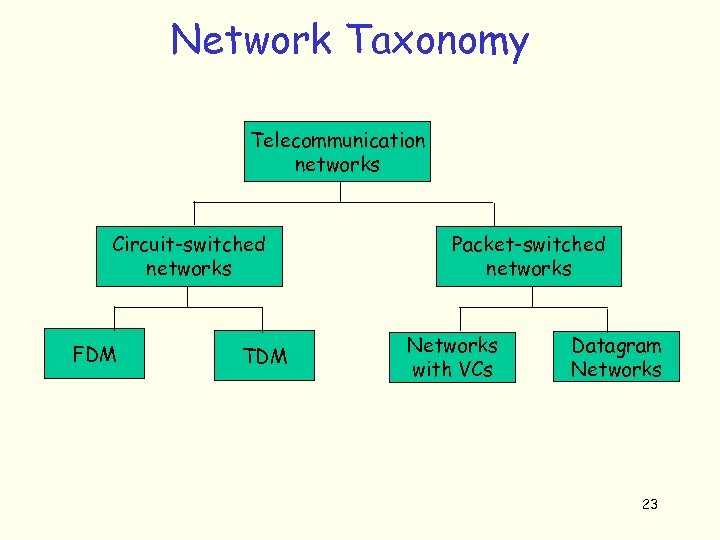
Network Taxonomy Telecommunication networks Circuit-switched networks FDM TDM Packet-switched networks Networks with VCs Datagram Networks 23
Packet Switched Networks • This course is about packet-switched networks • We will not cover circuit-switched networks • In looking at packet-switched networks, our approach will be from the view of network designer, a system engineer, who wants to build a packet switched network from the ground up – – – How do you build a packet switched network? What are the issues? How do you solve them? What are the specific solutions in existence today? We will mostly look at Internet Protocols 24
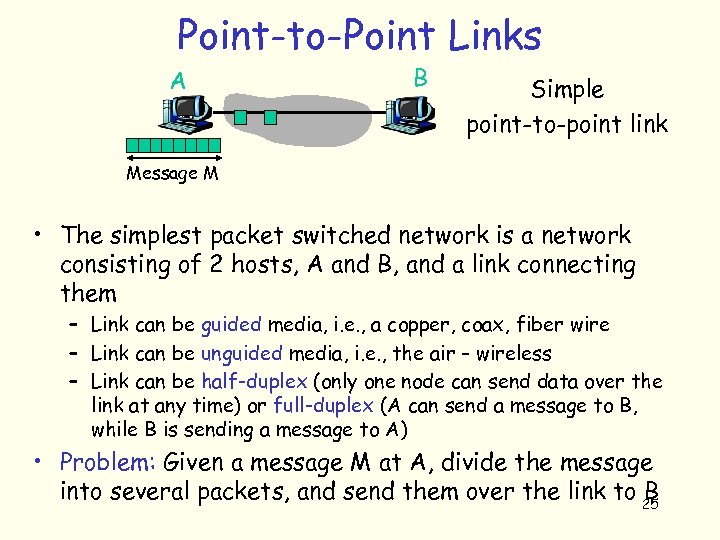
Point-to-Point Links A B Simple point-to-point link Message M • The simplest packet switched network is a network consisting of 2 hosts, A and B, and a link connecting them – Link can be guided media, i. e. , a copper, coax, fiber wire – Link can be unguided media, i. e. , the air – wireless – Link can be half-duplex (only one node can send data over the link at any time) or full-duplex (A can send a message to B, while B is sending a message to A) • Problem: Given a message M at A, divide the message into several packets, and send them over the link to 25 B
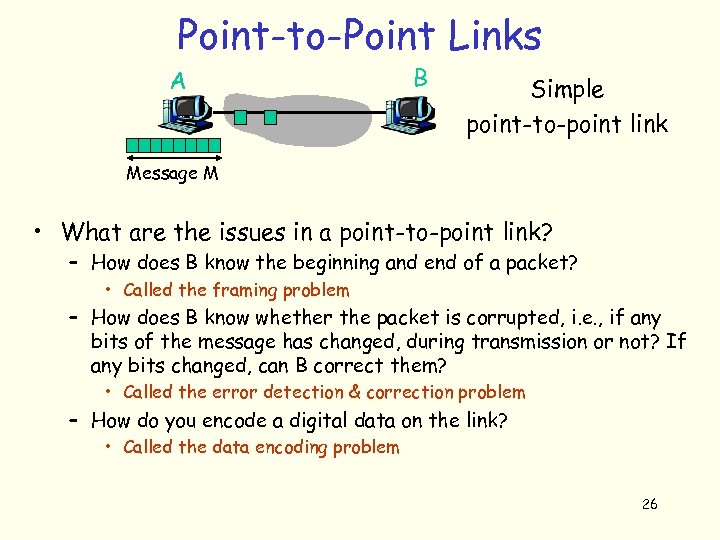
Point-to-Point Links A B Simple point-to-point link Message M • What are the issues in a point-to-point link? – How does B know the beginning and end of a packet? • Called the framing problem – How does B know whether the packet is corrupted, i. e. , if any bits of the message has changed, during transmission or not? If any bits changed, can B correct them? • Called the error detection & correction problem – How do you encode a digital data on the link? • Called the data encoding problem 26
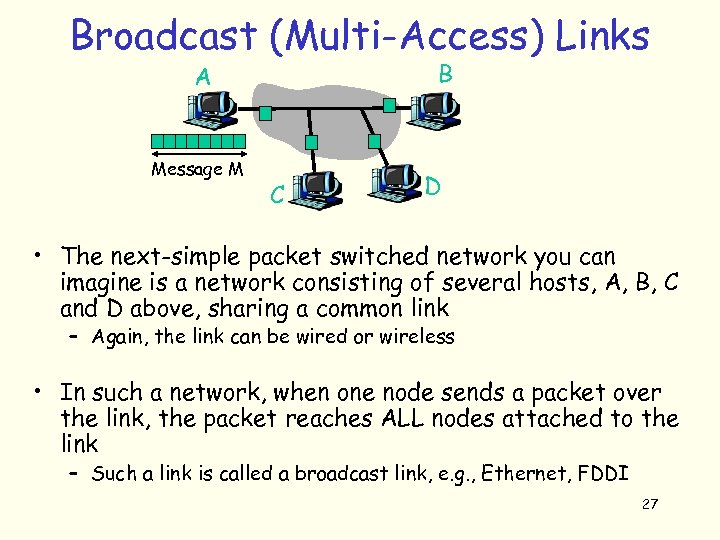
Broadcast (Multi-Access) Links B A Message M C D • The next-simple packet switched network you can imagine is a network consisting of several hosts, A, B, C and D above, sharing a common link – Again, the link can be wired or wireless • In such a network, when one node sends a packet over the link, the packet reaches ALL nodes attached to the link – Such a link is called a broadcast link, e. g. , Ethernet, FDDI 27
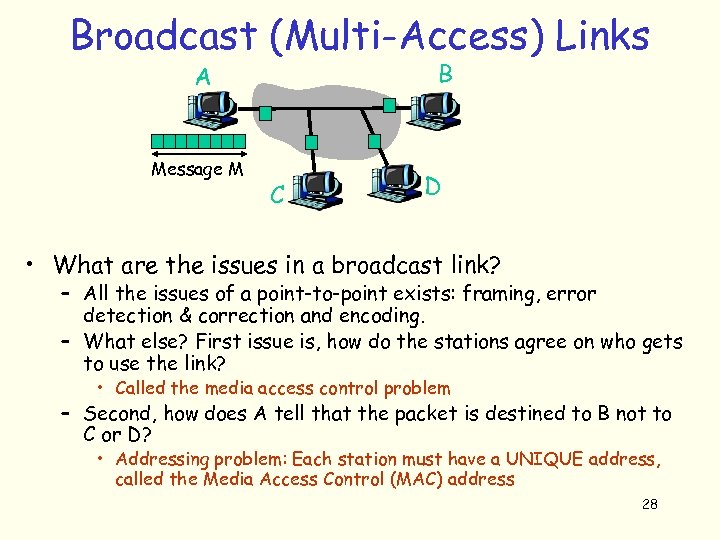
Broadcast (Multi-Access) Links B A Message M C D • What are the issues in a broadcast link? – All the issues of a point-to-point exists: framing, error detection & correction and encoding. – What else? First issue is, how do the stations agree on who gets to use the link? • Called the media access control problem – Second, how does A tell that the packet is destined to B not to C or D? • Addressing problem: Each station must have a UNIQUE address, called the Media Access Control (MAC) address 28
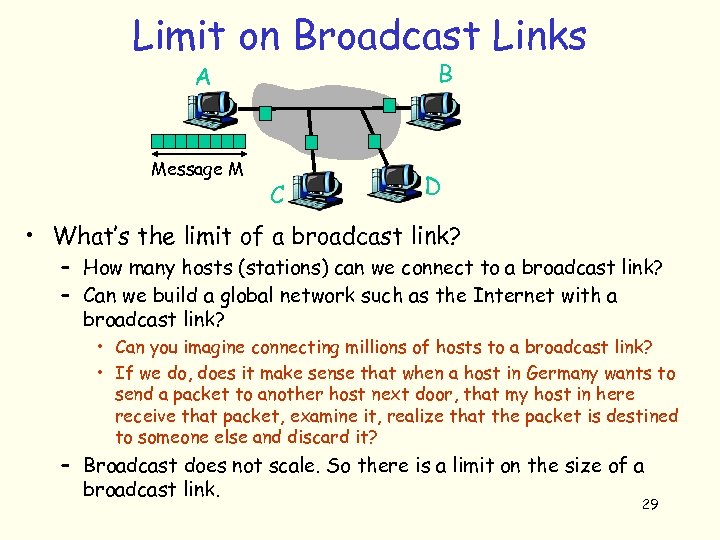
Limit on Broadcast Links B A Message M C D • What’s the limit of a broadcast link? – How many hosts (stations) can we connect to a broadcast link? – Can we build a global network such as the Internet with a broadcast link? • Can you imagine connecting millions of hosts to a broadcast link? • If we do, does it make sense that when a host in Germany wants to send a packet to another host next door, that my host in here receive that packet, examine it, realize that the packet is destined to someone else and discard it? – Broadcast does not scale. So there is a limit on the size of a broadcast link. 29
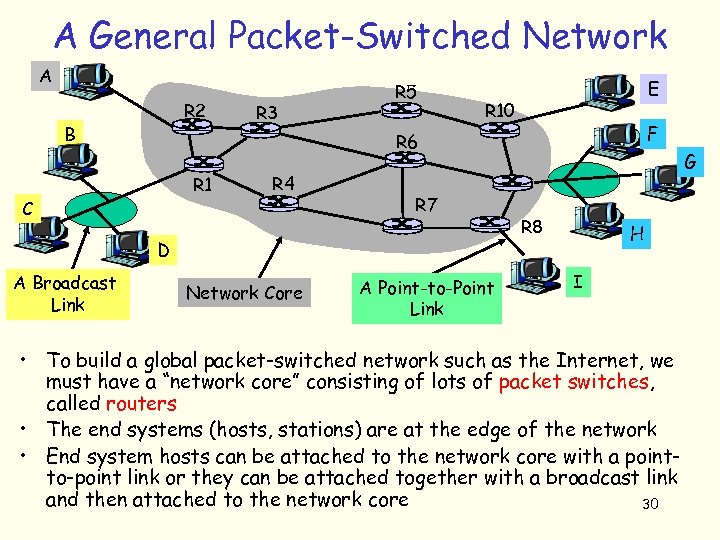
A General Packet-Switched Network A R 2 B R 3 R 5 R 10 F R 6 R 1 C R 4 R 7 D A Broadcast Link E Network Core A Point-to-Point Link G R 8 H I • To build a global packet-switched network such as the Internet, we must have a “network core” consisting of lots of packet switches, called routers • The end systems (hosts, stations) are at the edge of the network • End system hosts can be attached to the network core with a pointto-point link or they can be attached together with a broadcast link and then attached to the network core 30
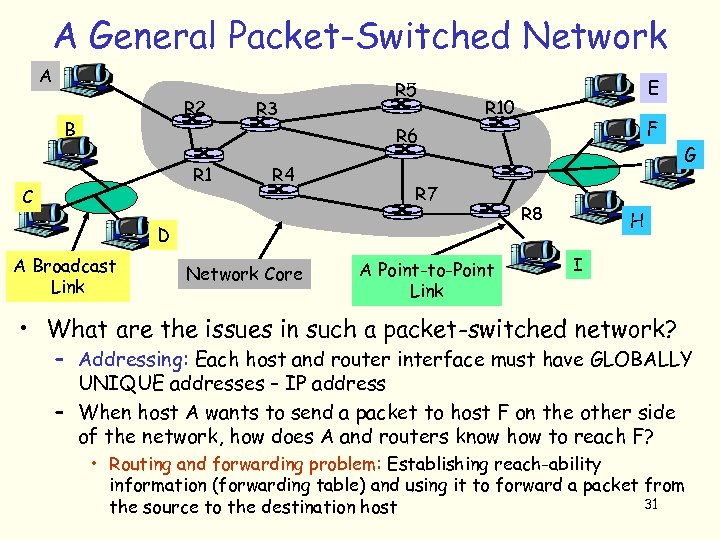
A General Packet-Switched Network A R 2 B R 3 R 5 E R 10 F R 6 R 1 C R 4 R 7 D A Broadcast Link Network Core A Point-to-Point Link G R 8 H I • What are the issues in such a packet-switched network? – Addressing: Each host and router interface must have GLOBALLY UNIQUE addresses – IP address – When host A wants to send a packet to host F on the other side of the network, how does A and routers know how to reach F? • Routing and forwarding problem: Establishing reach-ability information (forwarding table) and using it to forward a packet from 31 the source to the destination host
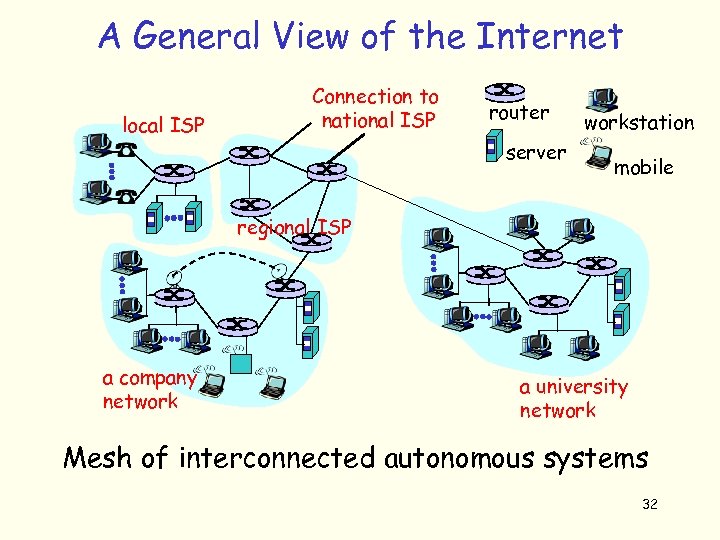
A General View of the Internet local ISP Connection to national ISP router server workstation mobile regional ISP a company network a university network Mesh of interconnected autonomous systems 32
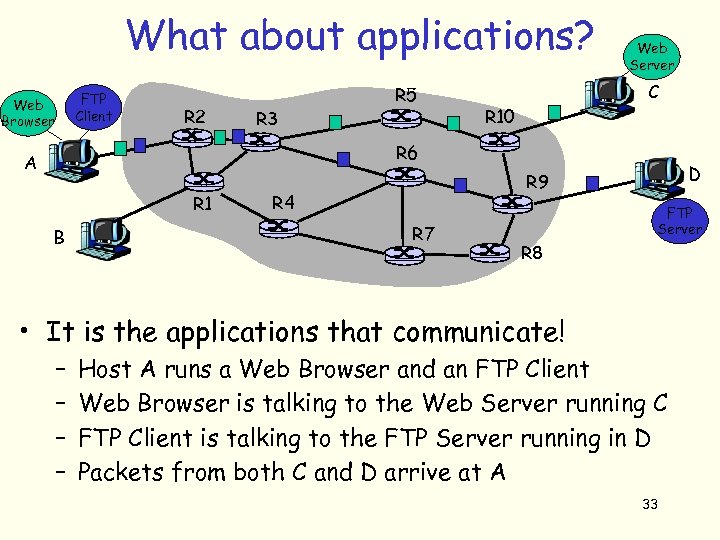
What about applications? FTP Client Web Browser R 2 R 3 R 5 Web Server C R 10 R 6 A R 1 B D R 9 R 4 R 7 FTP Server R 8 • It is the applications that communicate! – – Host A runs a Web Browser and an FTP Client Web Browser is talking to the Web Server running C FTP Client is talking to the FTP Server running in D Packets from both C and D arrive at A 33
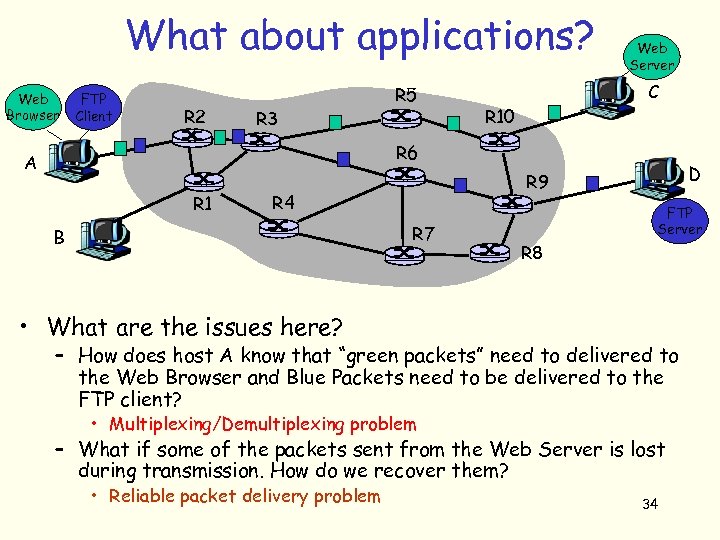
What about applications? Web Browser FTP Client R 2 R 3 R 5 Web Server C R 10 R 6 A R 1 R 4 R 7 B D R 9 FTP Server R 8 • What are the issues here? – How does host A know that “green packets” need to delivered to the Web Browser and Blue Packets need to be delivered to the FTP client? • Multiplexing/Demultiplexing problem – What if some of the packets sent from the Web Server is lost during transmission. How do we recover them? • Reliable packet delivery problem 34

How do two network entities talk to each other: PROTOCOLS • For two entities to communicate, they must “speak the same language” – What is communicated? • Message format – How is it communicated and what it means? • Order of messages and their meaning – When is it communicated? • Timing of the messages – The above must conform to mutually acceptable conventions between the entities involved – In networking, these conventions are referred to as a “protocol” 35
Protocols • A protocol is a set of rules governing the exchange of data between the two entities • Key elements of a protocol are – Syntax: Message format – Semantics: The meaning of messages • order of messages sent and received • actions taken on message transmission, receipt – Timing: Includes speed matching and sequencing • When to send a message 36
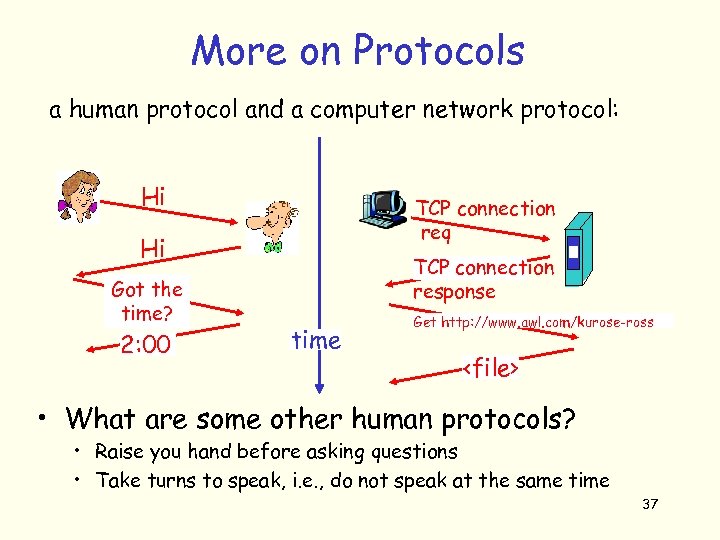
More on Protocols a human protocol and a computer network protocol: Hi TCP connection req Hi Got the time? 2: 00 TCP connection response time Get http: //www. awl. com/kurose-ross <file> • What are some other human protocols? • Raise you hand before asking questions • Take turns to speak, i. e. , do not speak at the same time 37
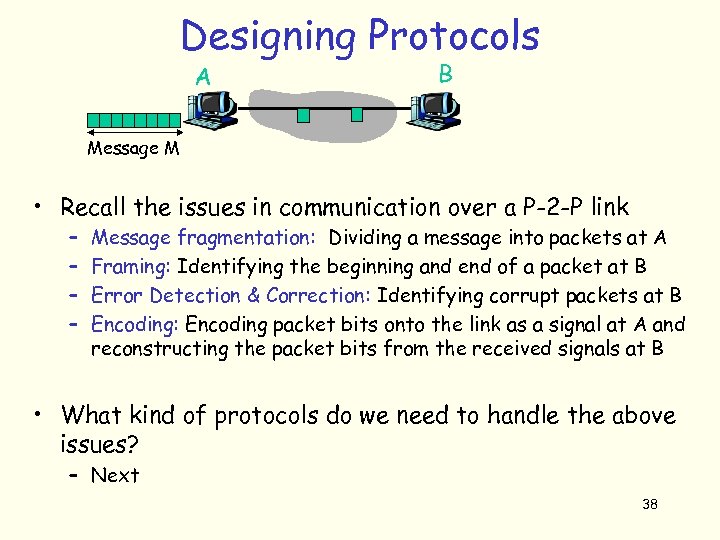
Designing Protocols A B Message M • Recall the issues in communication over a P-2 -P link – – Message fragmentation: Dividing a message into packets at A Framing: Identifying the beginning and end of a packet at B Error Detection & Correction: Identifying corrupt packets at B Encoding: Encoding packet bits onto the link as a signal at A and reconstructing the packet bits from the received signals at B • What kind of protocols do we need to handle the above issues? – Next 38
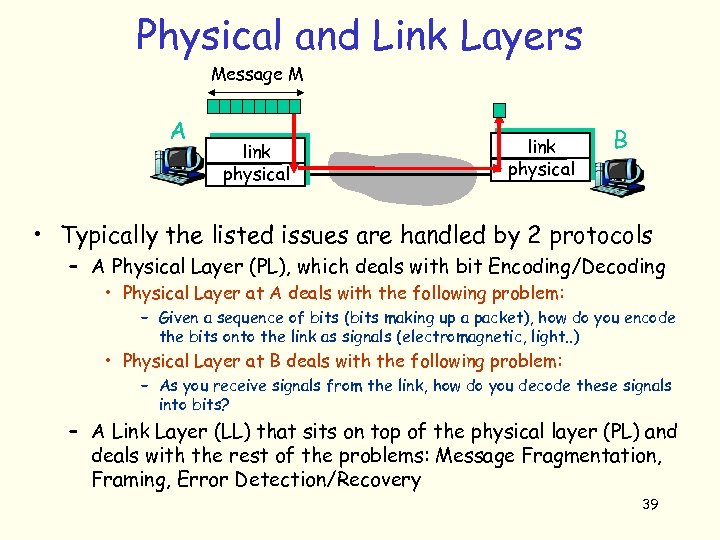
Physical and Link Layers Message M A link physical B • Typically the listed issues are handled by 2 protocols – A Physical Layer (PL), which deals with bit Encoding/Decoding • Physical Layer at A deals with the following problem: – Given a sequence of bits (bits making up a packet), how do you encode the bits onto the link as signals (electromagnetic, light. . ) • Physical Layer at B deals with the following problem: – As you receive signals from the link, how do you decode these signals into bits? – A Link Layer (LL) that sits on top of the physical layer (PL) and deals with the rest of the problems: Message Fragmentation, Framing, Error Detection/Recovery 39
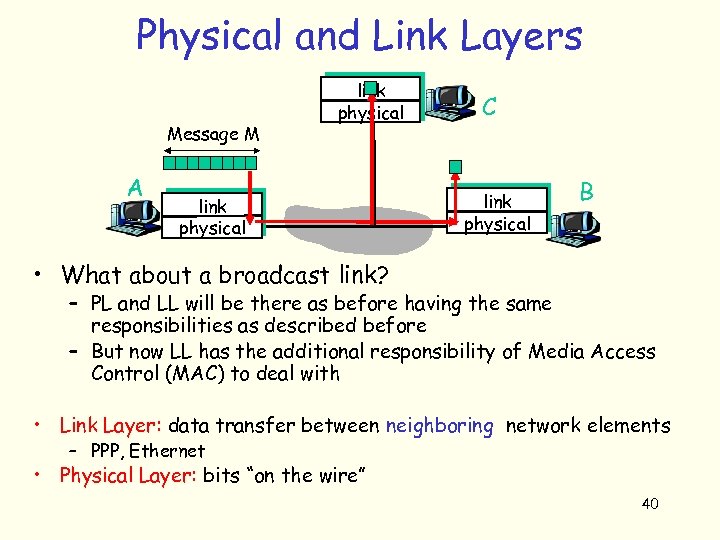
Physical and Link Layers Message M A link physical C link physical B • What about a broadcast link? – PL and LL will be there as before having the same responsibilities as described before – But now LL has the additional responsibility of Media Access Control (MAC) to deal with • Link Layer: data transfer between neighboring network elements – PPP, Ethernet • Physical Layer: bits “on the wire” 40
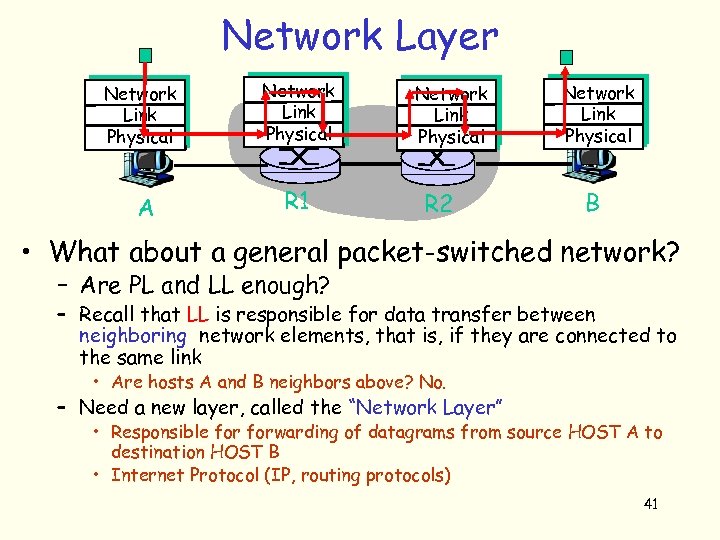
Network Layer Network link Link physical Physical A Network Link link Physical physical R 1 Network Link link Physical physical R 2 Network link Link physical Physical B • What about a general packet-switched network? – Are PL and LL enough? – Recall that LL is responsible for data transfer between neighboring network elements, that is, if they are connected to the same link • Are hosts A and B neighbors above? No. – Need a new layer, called the “Network Layer” • Responsible forwarding of datagrams from source HOST A to destination HOST B • Internet Protocol (IP, routing protocols) 41
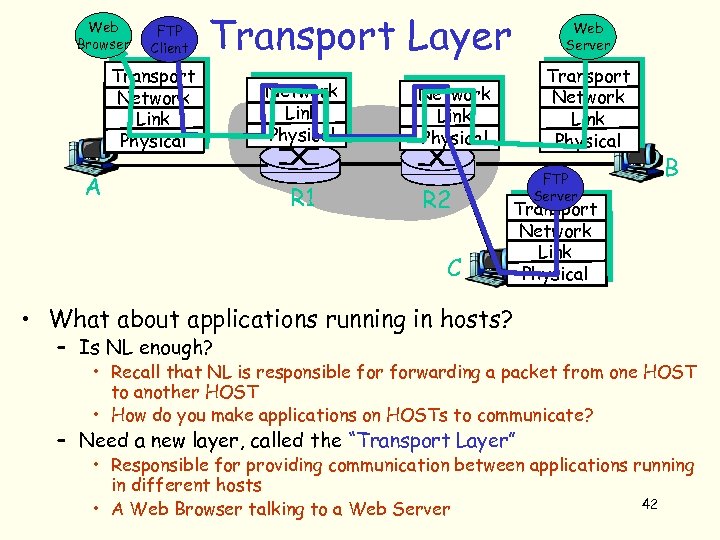
Web Browser FTP Client Transport Layer Transport Network Link Physical A Network Link Physical R 1 Web Server Transport Network Link Physical R 2 C FTP Server B Transport Network Link Physical • What about applications running in hosts? – Is NL enough? • Recall that NL is responsible forwarding a packet from one HOST to another HOST • How do you make applications on HOSTs to communicate? – Need a new layer, called the “Transport Layer” • Responsible for providing communication between applications running in different hosts 42 • A Web Browser talking to a Web Server
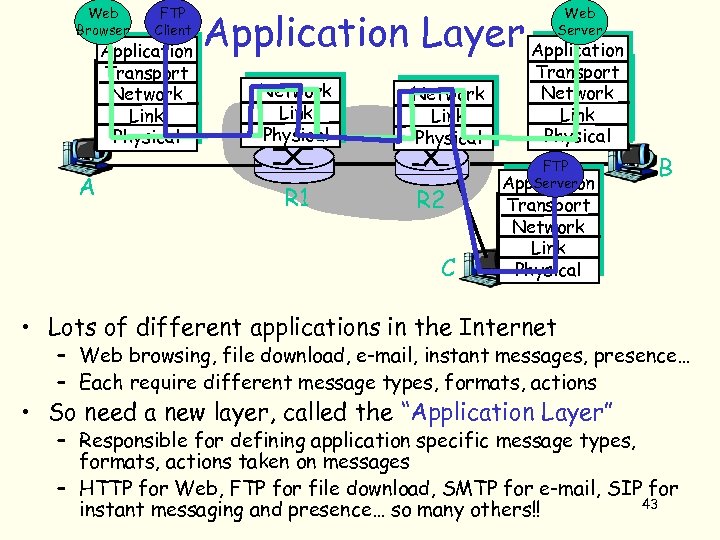
Web Browser FTP Client Application Transport Network Link Physical A Application Layer Application Web Server Network Link Physical R 1 Network Link Physical R 2 C Transport Network Link Physical FTP Server Application B Transport Network Link Physical • Lots of different applications in the Internet – Web browsing, file download, e-mail, instant messages, presence… – Each require different message types, formats, actions • So need a new layer, called the “Application Layer” – Responsible for defining application specific message types, formats, actions taken on messages – HTTP for Web, FTP for file download, SMTP for e-mail, SIP for 43 instant messaging and presence… so many others!!
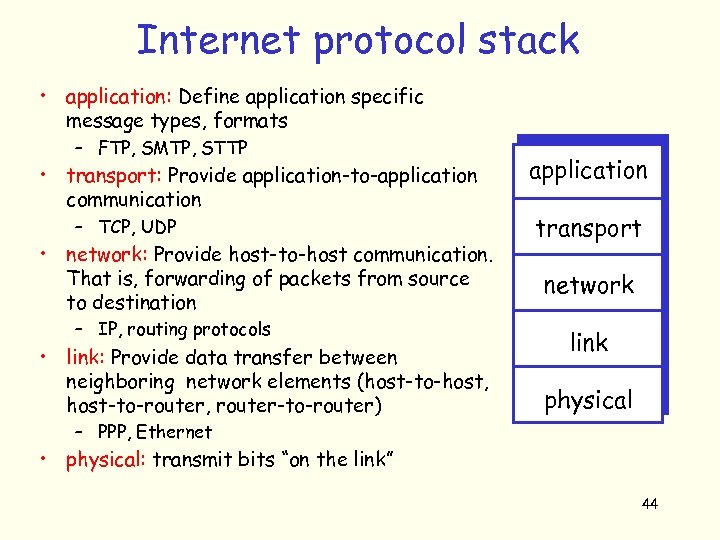
Internet protocol stack • application: Define application specific message types, formats – FTP, SMTP, STTP • transport: Provide application-to-application communication – TCP, UDP • network: Provide host-to-host communication. That is, forwarding of packets from source to destination – IP, routing protocols • link: Provide data transfer between neighboring network elements (host-to-host, host-to-router, router-to-router) application transport network link physical – PPP, Ethernet • physical: transmit bits “on the link” 44
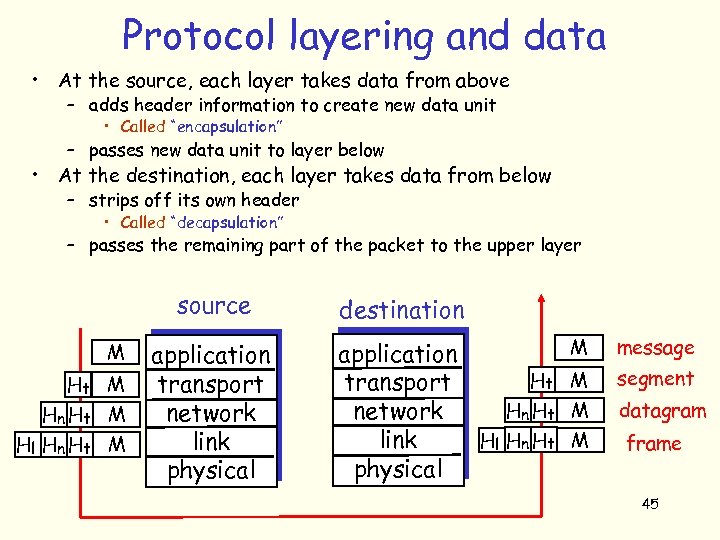
Protocol layering and data • At the source, each layer takes data from above – adds header information to create new data unit • Called “encapsulation” – passes new data unit to layer below • At the destination, each layer takes data from below – strips off its own header • Called “decapsulation” – passes the remaining part of the packet to the upper layer source M Ht M Hn Ht M Hl Hn Ht M application transport network link physical destination application Ht transport Hn Ht network Hl Hn Ht link physical M message M segment M datagram M frame 45
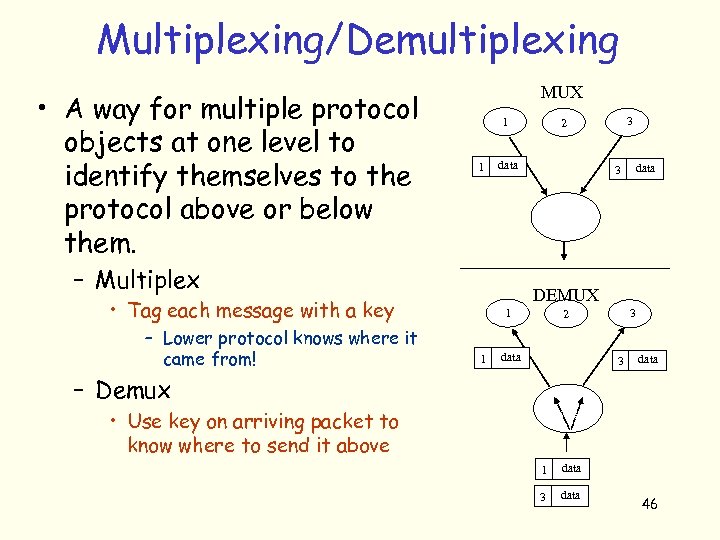
Multiplexing/Demultiplexing • A way for multiple protocol objects at one level to identify themselves to the protocol above or below them. MUX 1 1 data – Multiplex 3 data DEMUX • Tag each message with a key – Lower protocol knows where it came from! 3 2 1 1 3 2 data 3 data – Demux • Use key on arriving packet to know where to send it above 1 data 3 data 46
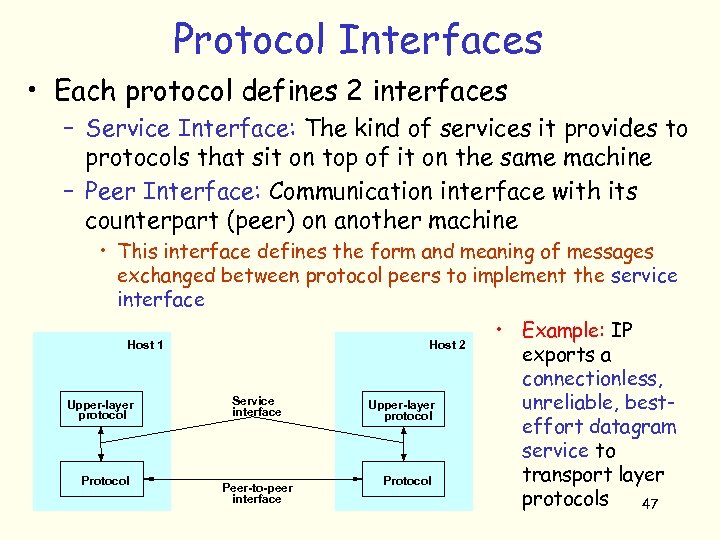
Protocol Interfaces • Each protocol defines 2 interfaces – Service Interface: The kind of services it provides to protocols that sit on top of it on the same machine – Peer Interface: Communication interface with its counterpart (peer) on another machine • This interface defines the form and meaning of messages exchanged between protocol peers to implement the service interface Host 1 Upper-layer protocol Protocol Host 2 Service interface Peer-to-peer interface Upper-layer protocol Protocol • Example: IP exports a connectionless, unreliable, besteffort datagram service to transport layer protocols 47
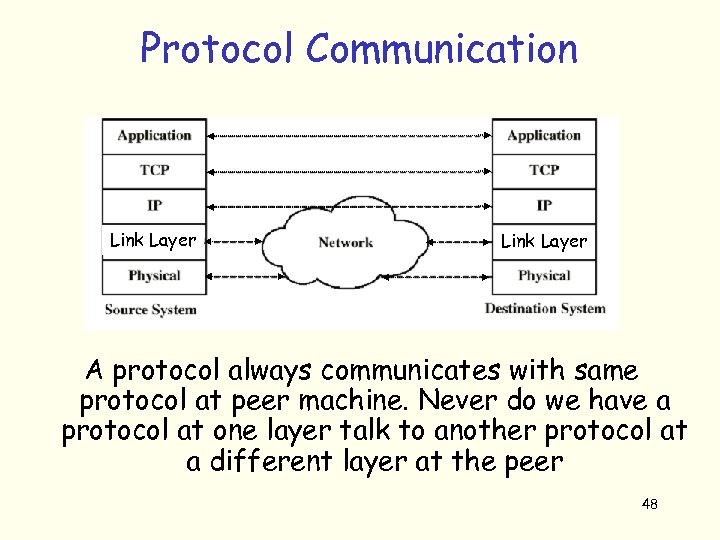
Protocol Communication Link Layer A protocol always communicates with same protocol at peer machine. Never do we have a protocol at one layer talk to another protocol at a different layer at the peer 48
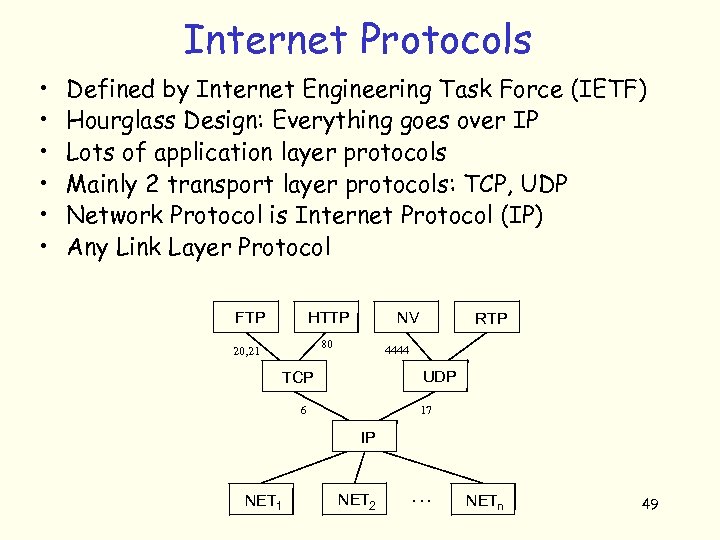
Internet Protocols • • • Defined by Internet Engineering Task Force (IETF) Hourglass Design: Everything goes over IP Lots of application layer protocols Mainly 2 transport layer protocols: TCP, UDP Network Protocol is Internet Protocol (IP) Any Link Layer Protocol FTP HTTP NV 80 20, 21 RTP 4444 UDP TCP 6 17 IP NET 1 NET 2 … NETn 49
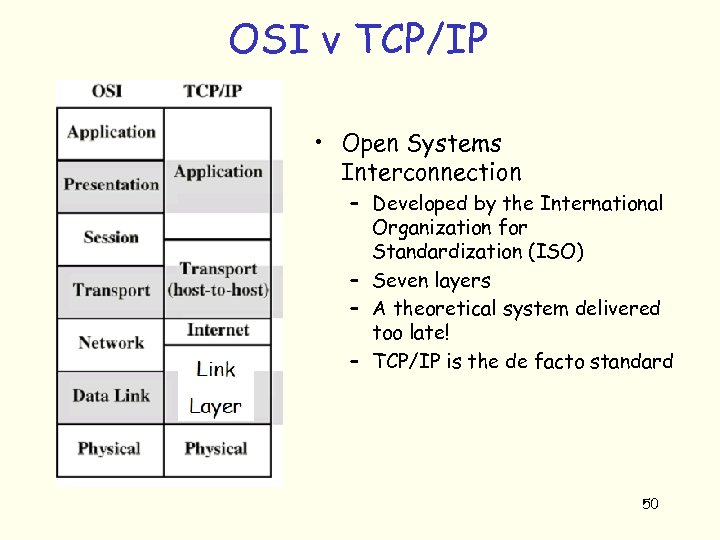
OSI v TCP/IP • Open Systems Interconnection – Developed by the International Organization for Standardization (ISO) – Seven layers – A theoretical system delivered too late! – TCP/IP is the de facto standard 50
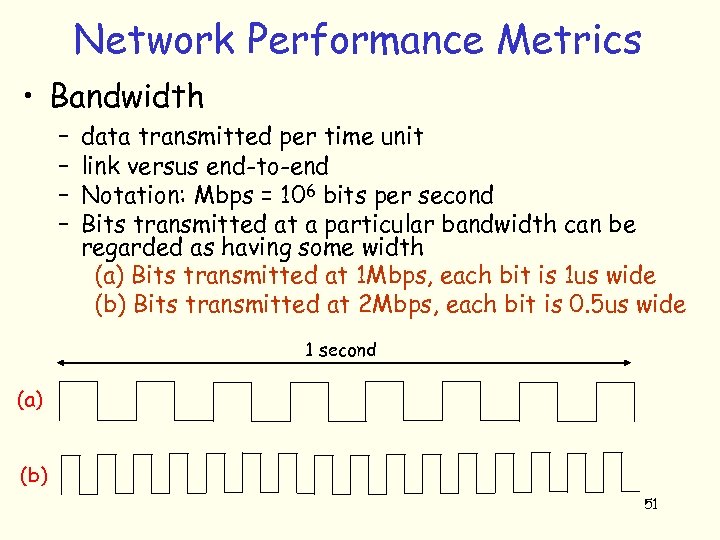
Network Performance Metrics • Bandwidth – – data transmitted per time unit link versus end-to-end Notation: Mbps = 106 bits per second Bits transmitted at a particular bandwidth can be regarded as having some width (a) Bits transmitted at 1 Mbps, each bit is 1 us wide (b) Bits transmitted at 2 Mbps, each bit is 0. 5 us wide 1 second (a) (b) 51
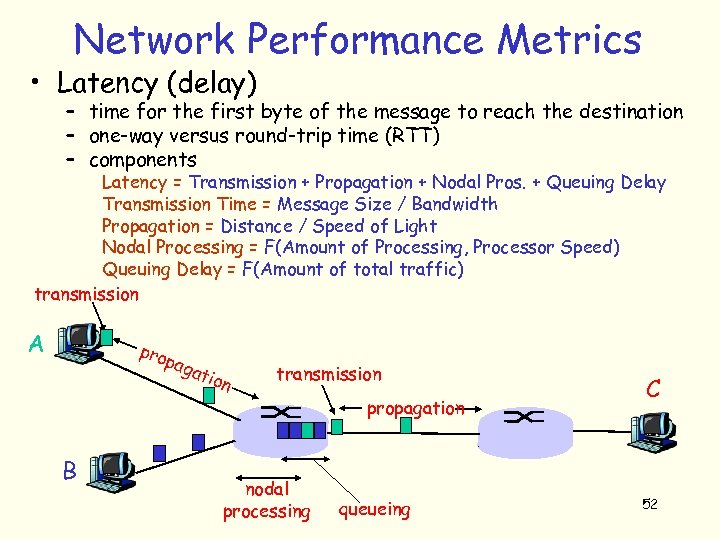
Network Performance Metrics • Latency (delay) – time for the first byte of the message to reach the destination – one-way versus round-trip time (RTT) – components Latency = Transmission + Propagation + Nodal Pros. + Queuing Delay Transmission Time = Message Size / Bandwidth Propagation = Distance / Speed of Light Nodal Processing = F(Amount of Processing, Processor Speed) Queuing Delay = F(Amount of total traffic) transmission A pro pag atio n transmission propagation B nodal processing queueing C 52
Latency or Delay • dtrans = transmission delay – = L/R, L: Message size, R: Link Bandwidth – significant for low-speed links • dprop = propagation delay – a few microsecs to hundreds of msecs • dproc = processing delay – typically a few microsecs or less • dqueue = queuing delay – depends on congestion (the amount of total traffic) 53
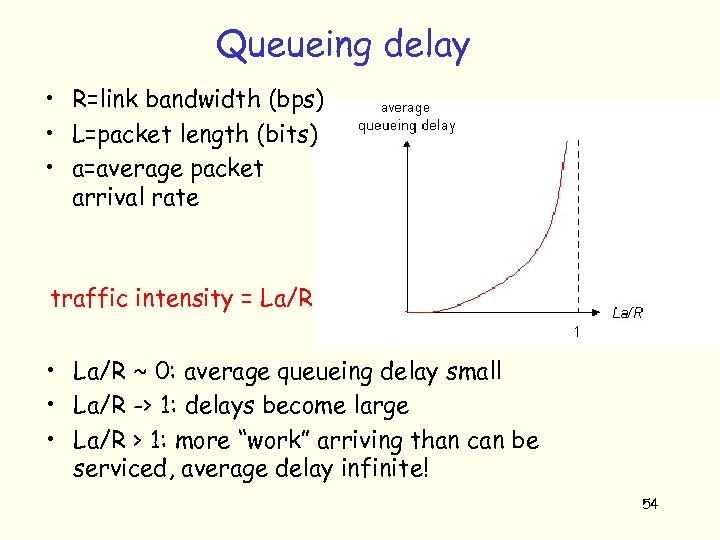
Queueing delay • R=link bandwidth (bps) • L=packet length (bits) • a=average packet arrival rate traffic intensity = La/R • La/R ~ 0: average queueing delay small • La/R -> 1: delays become large • La/R > 1: more “work” arriving than can be serviced, average delay infinite! 54
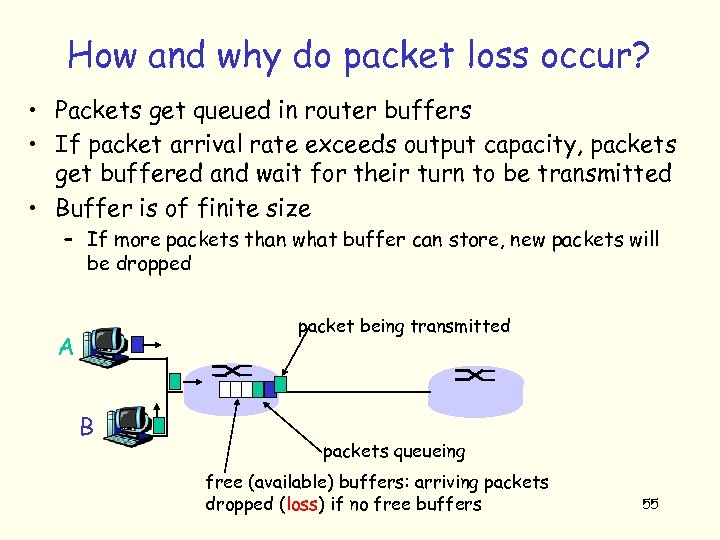
How and why do packet loss occur? • Packets get queued in router buffers • If packet arrival rate exceeds output capacity, packets get buffered and wait for their turn to be transmitted • Buffer is of finite size – If more packets than what buffer can store, new packets will be dropped packet being transmitted A B packets queueing free (available) buffers: arriving packets dropped (loss) if no free buffers 55
Introduction: Summary Covered a “ton” of material! • Internet overview • what’s a protocol? • network edge, core – packet-switching versus circuit-switching • performance: loss, delay • layering and service models You now have: • context, overview, “feel” of networking • The rest of the course will be to learn the details of these protocols in the context of IP protocol stack 56
c92225feb3fdd91da8eac40afa95f94a.ppt