c6b8a8621f933278dcf2f25a4eb072b4.ppt
- Количество слайдов: 19

BGP Security Jennifer Rexford Fall 2014 (TTh 3: 00 -4: 20 in CS 105) COS 561: Advanced Computer Networks http: //www. cs. princeton. edu/courses/archive/fall 14/cos 561/
Example “Prefix Hijacking” Attack You. Tube Outage of February 24, 2008 2
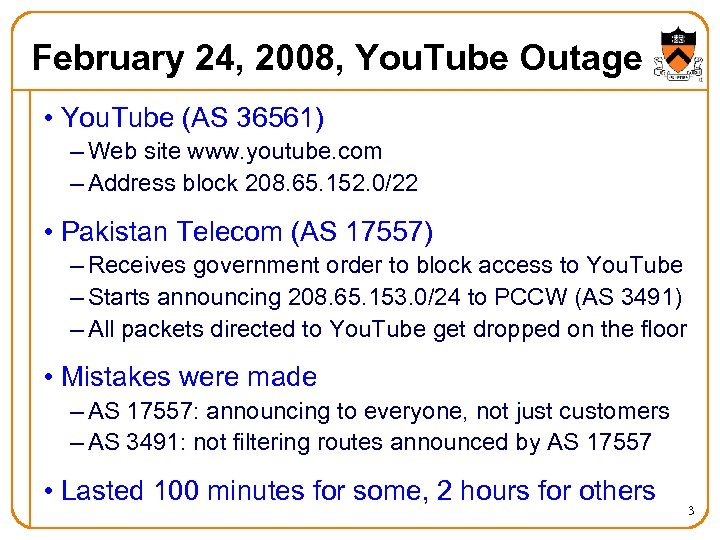
February 24, 2008, You. Tube Outage • You. Tube (AS 36561) – Web site www. youtube. com – Address block 208. 65. 152. 0/22 • Pakistan Telecom (AS 17557) – Receives government order to block access to You. Tube – Starts announcing 208. 65. 153. 0/24 to PCCW (AS 3491) – All packets directed to You. Tube get dropped on the floor • Mistakes were made – AS 17557: announcing to everyone, not just customers – AS 3491: not filtering routes announced by AS 17557 • Lasted 100 minutes for some, 2 hours for others 3

Timeline (UTC Time) • 18: 47: 45 – First evidence of hijacked /24 route propagating in Asia • 18: 48: 00 – Several big trans-Pacific providers carrying the route • 18: 49: 30 – Bogus route fully propagated • 20: 07: 25 – You. Tube starts advertising the /24 to attract traffic back • 20: 08: 30 – Many (but not all) providers are using the valid route http: //research. dyn. com/2008/02/pakistan-hijacks-youtube-1/ 4

Timeline (UTC Time) • 20: 18: 43 – You. Tube starts announcing two more-specific /25 routes • 20: 19: 37 – Some more providers start using the /25 routes • 20: 59 – AS 17557 starts prepending (“ 3491 17557”) • 20: 59: 39 – AS 3491 disconnects AS 17557 • 21: 00 – All is well, videos of cats flushing toilets are available 5

Lessons From the Example • BGP is incredibly vulnerable – Local actions have serious global consequences – Propagating misinformation is surprisingly easy • Fixing the problem required vigilance – Monitoring to detect and diagnose the problem – Immediate action to (try to) attract the traffic back – Longer-term cooperation to block/disable the attack • Preventing these problems is even harder – Require all ASes to perform defensive filtering? – Automatically detect and stop bogus route? – Require proof of ownership of the address block? 6

BGP Attacks 7
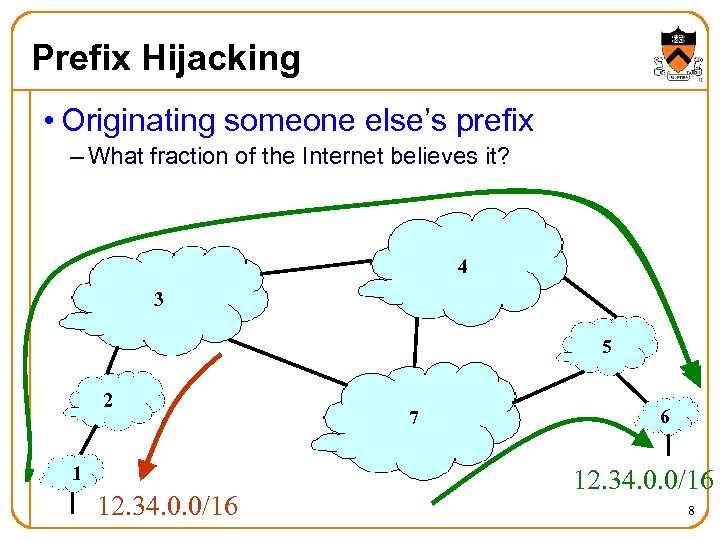
Prefix Hijacking • Originating someone else’s prefix – What fraction of the Internet believes it? 4 3 5 2 1 12. 34. 0. 0/16 7 6 12. 34. 0. 0/16 8
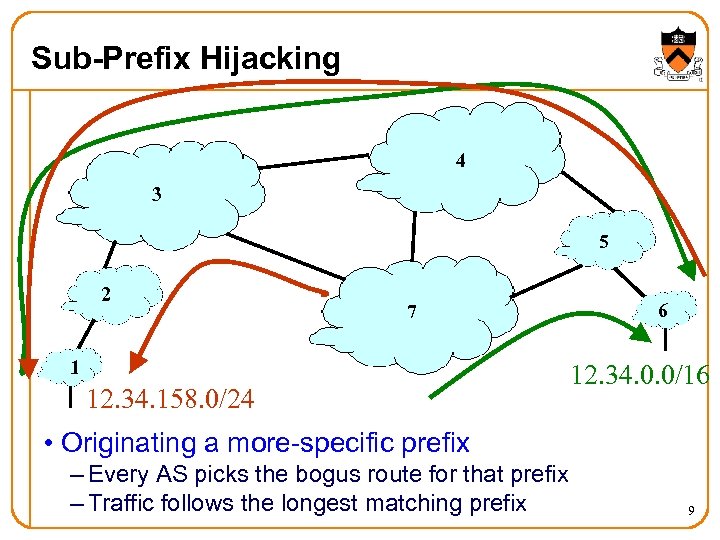
Sub-Prefix Hijacking 4 3 5 2 7 1 12. 34. 158. 0/24 6 12. 34. 0. 0/16 • Originating a more-specific prefix – Every AS picks the bogus route for that prefix – Traffic follows the longest matching prefix 9
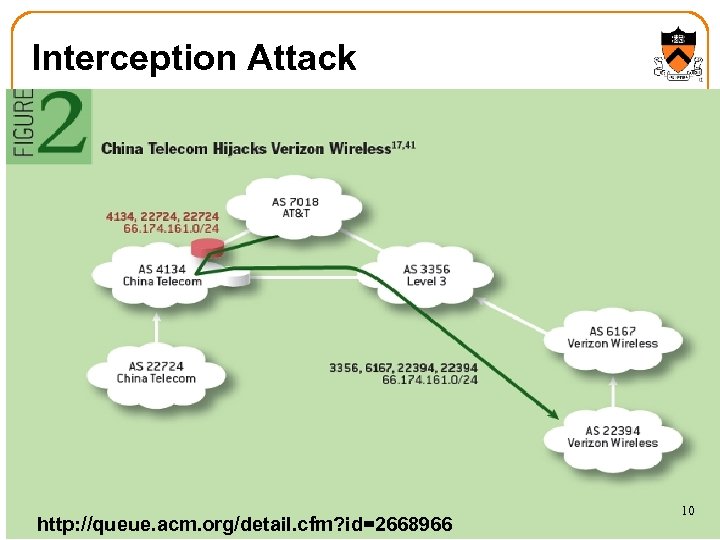
Interception Attack http: //queue. acm. org/detail. cfm? id=2668966 10
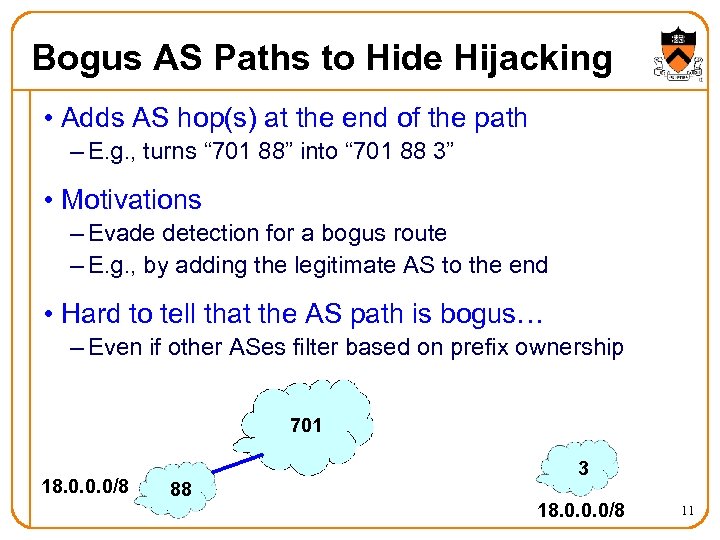
Bogus AS Paths to Hide Hijacking • Adds AS hop(s) at the end of the path – E. g. , turns “ 701 88” into “ 701 88 3” • Motivations – Evade detection for a bogus route – E. g. , by adding the legitimate AS to the end • Hard to tell that the AS path is bogus… – Even if other ASes filter based on prefix ownership 701 18. 0. 0. 0/8 88 3 18. 0. 0. 0/8 11
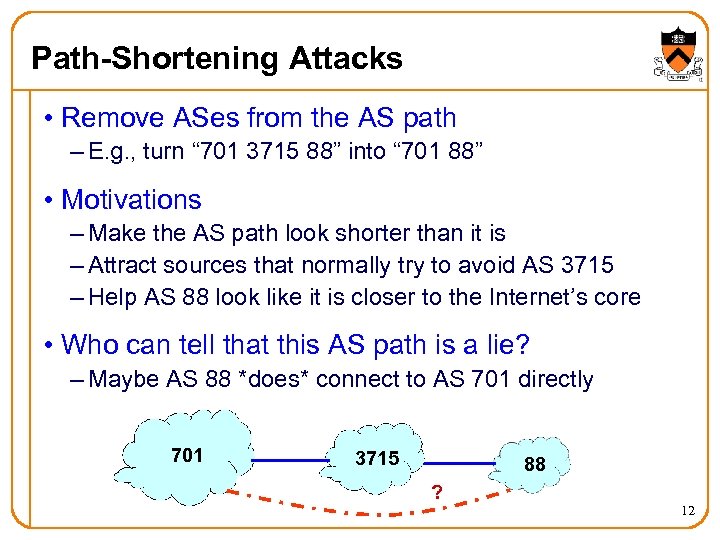
Path-Shortening Attacks • Remove ASes from the AS path – E. g. , turn “ 701 3715 88” into “ 701 88” • Motivations – Make the AS path look shorter than it is – Attract sources that normally try to avoid AS 3715 – Help AS 88 look like it is closer to the Internet’s core • Who can tell that this AS path is a lie? – Maybe AS 88 *does* connect to AS 701 directly 701 3715 88 ? 12
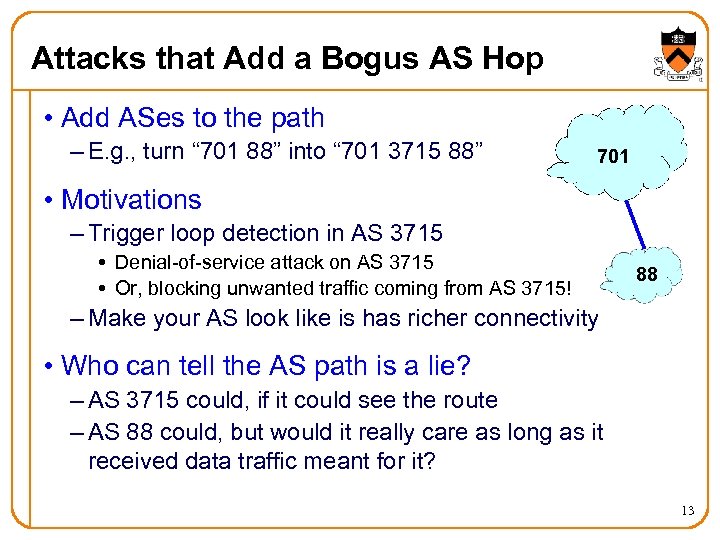
Attacks that Add a Bogus AS Hop • Add ASes to the path – E. g. , turn “ 701 88” into “ 701 3715 88” 701 • Motivations – Trigger loop detection in AS 3715 Denial-of-service attack on AS 3715 Or, blocking unwanted traffic coming from AS 3715! 88 – Make your AS look like is has richer connectivity • Who can tell the AS path is a lie? – AS 3715 could, if it could see the route – AS 88 could, but would it really care as long as it received data traffic meant for it? 13
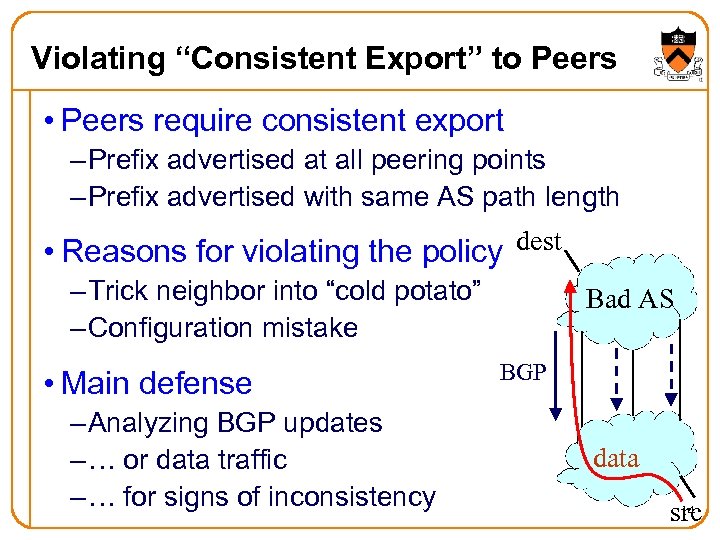
Violating “Consistent Export” to Peers • Peers require consistent export – Prefix advertised at all peering points – Prefix advertised with same AS path length • Reasons for violating the policy dest – Trick neighbor into “cold potato” – Configuration mistake • Main defense – Analyzing BGP updates – … or data traffic – … for signs of inconsistency Bad AS BGP data 14 src

Other Attacks • Attacks on BGP sessions – Confidentiality of BGP messages – Denial-of-service on BGP session – Inserting, deleting, modifying, or replaying messages • Resource exhaustion attacks – Too many IP prefixes (e. g. , BGP “ 512 K Day”) – Too many BGP update messages • Data-plane attacks – Announce one BGP routes, but use another 15

Improving BGP Security 16

Solution Techniques • Protective filtering – Know your neighbors • Anomaly detection – Suspect the unexpected • Checking against registries – Establish ground truth for prefix origination • Signing and verifying – Prevent bogus AS PATHs • Data-plane verification – Ensure the path is actually followed 17
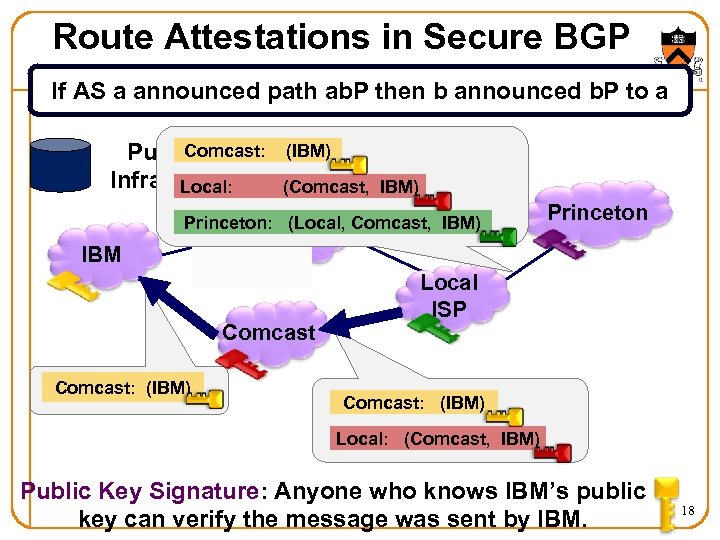
Route Attestations in Secure BGP If AS a announced path ab. P then b announced b. P to a Comcast: Public Key Infrastructure Local: (IBM) (Comcast, IBM) Princeton: (Local, Comcast, IBM) IBM AT&T Comcast: (IBM) Princeton Local ISP Comcast: (IBM) Local: (Comcast, IBM) Public Key Signature: Anyone who knows IBM’s public key can verify the message was sent by IBM. 18

Discussion of the Paper BGP Security in Partial Deployment 19
c6b8a8621f933278dcf2f25a4eb072b4.ppt