09983a10a199bfac9d4e23ed0009aae8.ppt
- Количество слайдов: 26

BGP Security Issues Seong. Ho Cho DPNM Lab. , POSTECH nology@postech. ac. kr 2008. 5. 13 Future Internet EECS 702 2008, Future Internet - /25 - DPNM Lab.
Contents v Introduction v Overview of BGP v BGP Operational Practice – – IP Address Allocation AS Business Relationship BGP Route Exporting Policy BGP Route Selection Process – – – Attack Objectives Sources of Threats Malicious Actions Falsification of NLRI Falsification of AS_PATH v BGP Security Threats v BGP Security Countermeasures – Goals – Proposals • S-BGP • so. BGP • ps. BGP EECS 702 2008, Future Internet - 2/25 - DPNM Lab.
Introduction v BGP Incidents – April 25 1997 • AS 7007 incident was caused by a misconfigured router that flooded the Internet with incorrect advertisement. – April 7 1998 • AS 8584 announced about 10, 000 prefixes it did not own. – April 6 2001 • AS 15412 announced about 5, 000 prefixes it did not own. – December 24 2004 • TTNet in Turkey hijacks the Internet – January 22 2006 • Con-Edison hijacks big chunk of the Internet – February 24 2008 • Pakistan's attempt to block You. Tube access within their country takes down You. Tube entirely EECS 702 2008, Future Internet - 3/25 - DPNM Lab.
Introduction v The Internet routing infrastructure is vulnerable to attacks. – BGP does not • protect the integrity, freshness and origin authentication of messages. • validate an AS’s authority to announce reachability information. • ensure the authenticity of the path attributes announced by an AS. v The important things that need to be monitored and controlled – – – AS Number (Authentication) BGP Speaker (Authentication) Data Integrity Prefix Origination (Verification) AS Path (Verification) EECS 702 2008, Future Internet - 4/25 - DPNM Lab.
Overview of BGP v Features – BGP is an inter-domain routing protocol based on distance vector approach. – A BGP speaker establishes a session over TCP with its direct neighbors. – A BGP route is associated with a number of attributes. • LOCAL_PREF, AS_PATH, MED, NEXT_HOP, etc. – A best route is selected among multiple routes to the same destination based on local policy. v BGP General Operation – – Learns multiple paths via Internal and external BGP speakers Picks the best path and installs in the forwarding table Best path is sent to external BGP neighbors Policies applied by influencing the best path selection EECS 702 2008, Future Internet - 5/25 - DPNM Lab.
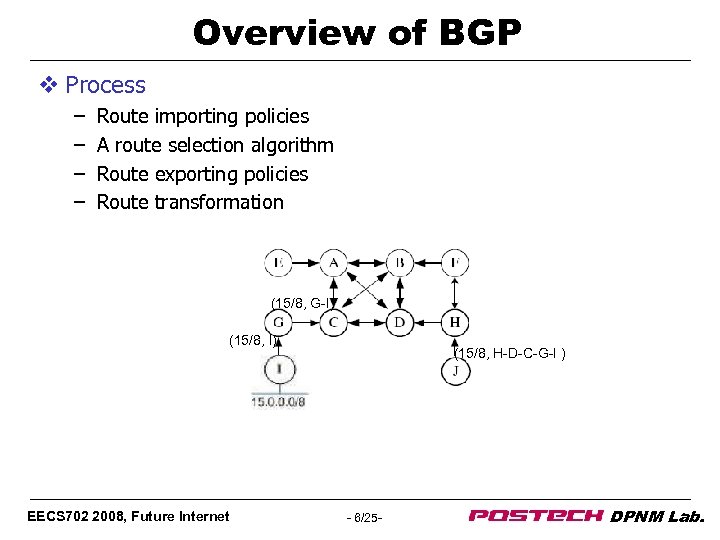
Overview of BGP v Process – – Route importing policies A route selection algorithm Route exporting policies Route transformation (15/8, G-I) (15/8, I) EECS 702 2008, Future Internet (15/8, H-D-C-G-I ) - 6/25 - DPNM Lab.
BGP Operational Practice v IP Address Allocation – A hierarchical structure was developed for IP address allocation. – IANA (Internet Assigned Number Authority) • The central authority of the whole IP address space – Five RIRs (Regional Internet Registries) • ARIN, RIPE NCC, APNIC, LACNIC and Afri. Nic – A large ISP (e. g. , tier-1) may apply for an IP address space directly from an RIR, and then delegate a portion of that address space to a downstream service provider (e. g. , tier-2) – Problem • It is not clear which IP prefixes have been delegated to which organizations via which ISPs. • “There is no single completely accurate source of truth about which organizations have the authority to advertise which address blocks” – RFC 3869 EECS 702 2008, Future Internet - 7/25 - DPNM Lab.
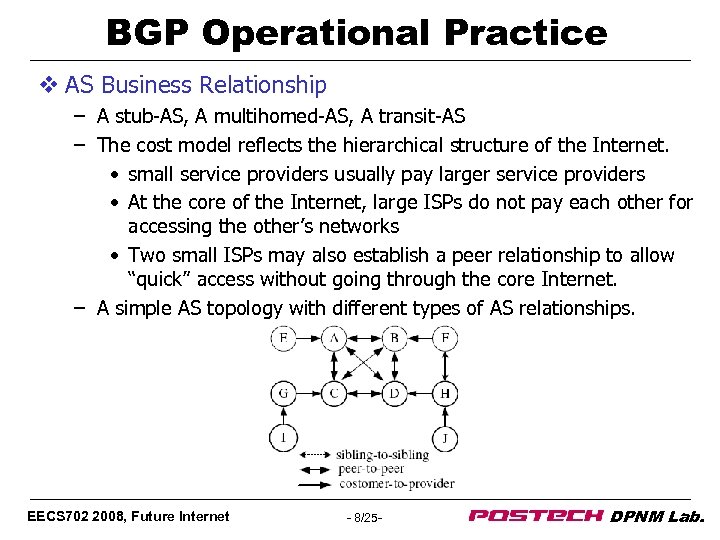
BGP Operational Practice v AS Business Relationship – A stub-AS, A multihomed-AS, A transit-AS – The cost model reflects the hierarchical structure of the Internet. • small service providers usually pay larger service providers • At the core of the Internet, large ISPs do not pay each other for accessing the other’s networks • Two small ISPs may also establish a peer relationship to allow “quick” access without going through the core Internet. – A simple AS topology with different types of AS relationships. EECS 702 2008, Future Internet - 8/25 - DPNM Lab.

BGP Operational Practice v BGP Route Exporting Policy – customer-to-provider • AS_customer exports to AS_provider its own rotues and the routes it has learned from its customers. – Provider-to-customer • AS_provider exports to AS_customer its full routing tables, including its own routes, the routes it has learned from customers, providers, peers, and siblings. – peer-to-peer • AS_peer. I exports to AS_peer. J its own routes and the routes it has learned from its customers. • Symmetric relationship. – sibling-to-sibling • AS_sibling. I exports to AS_sibling. J its full routing tables, including its own routes, the routes it has learned from customers, providers, peers, and siblings. • Symmetric relationship. EECS 702 2008, Future Internet - 9/25 - DPNM Lab.
BGP Operational Practice v BGP Route Selection Process – Selecting the most preferable route among a set of routes. – A list of route selection rules with an order of decreased preference. • LOCAL_PREF – the highest degree preference. • AS_PATH – the shortest AS_PATH among those with the same preference value • MULTI_EXIT_DISC – the lowest MED among those with the same NEXT_HOP • NEXT_HOP – the lowest cost to the NEXT_HOP of that route • The lowest BGP identifier EECS 702 2008, Future Internet - 10/25 - DPNM Lab.
BGP Security Threats v Attack Objectives – Prefix Blackholing • occurs when a prefix is unreachable from a large portion of the Internet. • Intentional blackholing is used to enforce private and nonallocated IP ranges. • Malicious blackholing refers to false route advertisements that aim to attract traffic to a particular router and then drop it. – Traffic Redirection • occurs when traffic flowing to a particular network is forced to take a different path and to reach an incorrect destination. • The compromised destination impersonates the true destination to receive confidential information. • Redirected excessive amounts of traffic to a certain link or network can cause congestion collapse. EECS 702 2008, Future Internet - 11/25 - DPNM Lab.

BGP Security Threats v Attack Objectives – Traffic Subversion • is a special case of redirection in which the attackers forces the traffic to pass through a certain link with the objectives of eavesdropping or modifying the data. • The traffic is still forwarded to the correct destination. – Routing Instability • can be caused by successive advertisements and withdrawals for the same network. • An objective of such attacks can be to trigger route dampening in upstream routers, and thus cause connectivity outages. • Another objective can be to create large increases in the volume of BGP traffic, and consequently long convergence delays. EECS 702 2008, Future Internet - 12/25 - DPNM Lab.
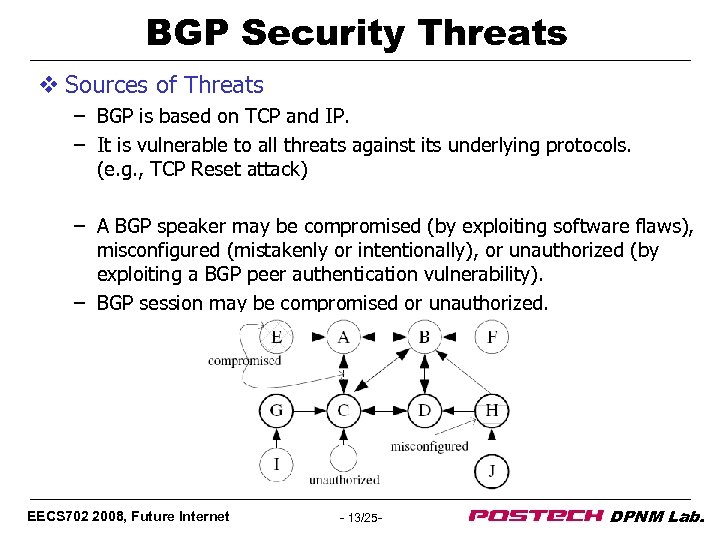
BGP Security Threats v Sources of Threats – BGP is based on TCP and IP. – It is vulnerable to all threats against its underlying protocols. (e. g. , TCP Reset attack) – A BGP speaker may be compromised (by exploiting software flaws), misconfigured (mistakenly or intentionally), or unauthorized (by exploiting a BGP peer authentication vulnerability). – BGP session may be compromised or unauthorized. EECS 702 2008, Future Internet - 13/25 - DPNM Lab.

BGP Security Threats v Malicious Actions – Four types of BGP control messages: OPEN, KEEPALIVE, NOTIFICATION, and UPDATE – The first three can be protected by a point-to-point authentication protocol, e. g. , IPsec. – A BGP update message consist of three parts: • withdrawn routes, NLRI (Network Layer Reachability Information), and path attributes (e. g. , AS_PATH, LOCAL_PREFERENCE, etc. ) – A route should be withdrawn by a party which had previously announced that routes. • Digitally signing BGP update message allows one to verify if a party has the right to withdrawn a route. – Falsification of NLRI – Falsification of AS_PATH EECS 702 2008, Future Internet - 14/25 - DPNM Lab.
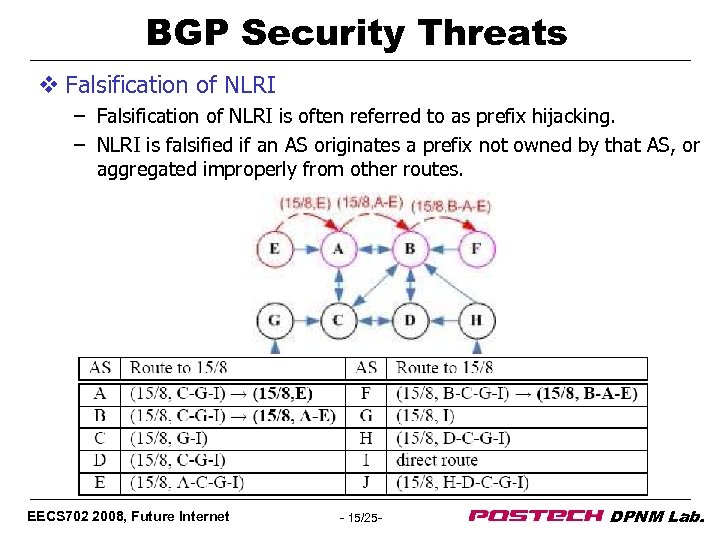
BGP Security Threats v Falsification of NLRI – Falsification of NLRI is often referred to as prefix hijacking. – NLRI is falsified if an AS originates a prefix not owned by that AS, or aggregated improperly from other routes. EECS 702 2008, Future Internet - 15/25 - DPNM Lab.

BGP Security Threats v Falsification of NLRI – Prefix hijacking can be used to facilitate many types of attacks, including denial of service, main-in-the-middle, service hijacking. – Three types of attacks using service hijacking • Spamming – Falsification of NLRI might have been used by spammers to facilitate advanced spamming. • Intercepting of password reset message – One possible attack using prefix hijacking is to intercept password reset messages for gaining illegitimate access to other people’s email accounts. • Phishing – To use the legitimate domain or URL of a claimed organization in a phishing email without poisoning a DNS record, a phisher can hijack the IP address space of that organization and set up a fraudulent website using the IP address of the legitimate website. EECS 702 2008, Future Internet - 16/25 - DPNM Lab.
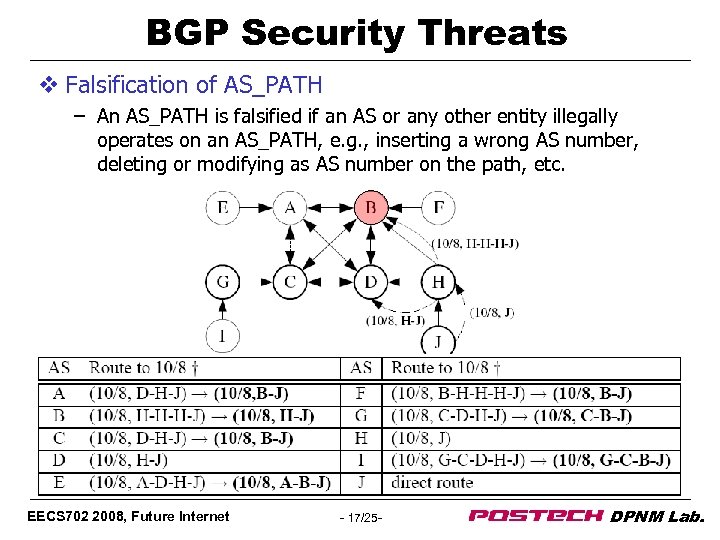
BGP Security Threats v Falsification of AS_PATH – An AS_PATH is falsified if an AS or any other entity illegally operates on an AS_PATH, e. g. , inserting a wrong AS number, deleting or modifying as AS number on the path, etc. EECS 702 2008, Future Internet - 17/25 - DPNM Lab.
BGP Security Countermeasures v BGP Security Goals – G 1: AS Number Authentication • It must be verifiable that an entity using an AS number si is an authorized representative of the AS to which a recognized AS number authority assigned si. – G 2: BGP Speaker Authentication • It must be verifiable that a BGP speaker has been authorized by the AS to which si was assigned by a recognized AS number authority. – G 3: Data Integrity • It must be verifiable that a BGP message has not been illegally modified. – G 4: Prefix Origination Verification • It must be verifiable that it is proper for an AS to originate an IP prefix. – G 5: AS Path Verification • It must be verifiable that an AS_PATH of a BGP route is originated by s 1, and has traversed through s 2, . . . , sk in order. EECS 702 2008, Future Internet - 18/25 - DPNM Lab.
BGP Security Countermeasures v Secure BGP (S-BGP) – Strict hierarchical PKIs and other mechanisms (e. g. , IPsec) – The PKIs are parallel to the existing allocation and delegation systems for AS numbers and IP address space. – A single CA rooted at IANA/ICANN was initially proposed for S-BGP, but it evolved to multiple CAs rooted at five RIRs. EECS 702 2008, Future Internet - 19/25 - DPNM Lab.
BGP Security Countermeasures v Secure BGP (S-BGP) – An organization X which obtains IP address and AS number directly from an RIR, will be issued the following certificates. • Organization Public Key Certificates - binding a public key Kx to X signed by T, denoted by (Kx, X)T • Address Delegation Certificates - binding IP prefixes fx to X signed by T, denoted by (fx, X)T • AS Number Delegation Certificates - binding an AS number sx to X signed by T, denoted by (sx, X)T – To participate in the inter-domain routing, X issues the following certificates or attestations • Router Public Key Certificate - binding a public key Ky to a BGP speaker y and an AS number sx signed by X using KX, denoted by (Ky, sx, y)Kx • Address Attestation - binding IP prefixes fx or a subset of fx to an AS number sx signed by X, denoted by (fx, sx)Kx • Route Attestation - binding IP prefixes fi to an AS_PATH pi signed by a BGP speaker y, denoted by (fi , pi)Ky EECS 702 2008, Future Internet - 20/25 - DPNM Lab.
BGP Security Countermeasures v Secure BGP (S-BGP) – How a BGP speaker announces and verifies a route in S-BGP? • Route Announcement – rx originates and signs a route (fx, sx)rx – rx forwards it to its neighboring BGP speaker ry representing AS sy – ry verifies the received route – If the route verification succeeds, ry forwards the route to its neighboring speaker rz. • Route Verification – Upon receiving (fx, sx-sy )ry , rz performs the following verifications: – (Kx, X)T , (fx, X)T , (sx, X)T , (fx, sx)Kx prefix origin verification succeeds – sy is authorized by sx to further propagate the route – (fx, sx)Kx AS_PATH sx-sy verification succeeds EECS 702 2008, Future Internet - 21/25 - DPNM Lab.
BGP Security Countermeasures v Secure BGP (S-BGP) – It provides a strong guarantee of prefix origin verification and AS_PATH integrity. – It has following drawbacks: • The proposed S-BGP PKIs are complex and unscalable, thus impractical. • AS_PATH verifications is computational expensive. • AS_PATH verification cannot detect violation of route exporting policy. • “the S-BGP proposal has significant unresolved deployment challenges” – RFC 3869 EECS 702 2008, Future Internet - 22/25 - DPNM Lab.

BGP Security Countermeasures v Secure Origin BGP (so. BGP) – Uses web-of-trust model for authenticating AS public keys. – Uses a hierarchical structure for verifying IP prefix ownership. – Each AS has a public key certificate, binding an AS number with a public key, signed by a “trusted” public key. – An AS with a trusted AS public key certificate (e. g. , signed by a trusted CA) may further sign a public key certificate for another AS, thus naturally forming a web-of-trust model. – Prefix delegation structures might be simplified in so. BGP by using ASes instead of organizations. – It is not clear if it is practical to do so since IP addresses are usually delegated to organizations not to Ases. – so. BGP also faces difficulty in tracing changes of IP address ownership in a strict hierarchical way. EECS 702 2008, Future Internet - 23/25 - DPNM Lab.
BGP Security Countermeasures v Pretty Secure BGP (ps. BGP) – One advantage of ps. BGP is that apparently it can successfully defend against threats from uncoordinated, misconfigured or malicious BGP speakers in a practical way. – A centralized trust model for authenticating AS numbers. • Each AS obtains a public key certificate from one of a number of the trusted certificate authorities, e. g. , RIRs, binding an AS number to a public key. – A decentralized trust model for verifying IP prefix ownership. • Each AS creates a prefix assertion list (PAL) consisting of a number of bindings of an AS number and prefixes which are asserted to be originated by that AS. EECS 702 2008, Future Internet - 24/25 - DPNM Lab.
Conclusions v It is vulnerable to a variety of attacks, and it must be secured to protect the Internet routing infrastructure. – There are several proposals for securing BGP. However none of them has been deployed. v Securing BGP and doing so in such a way that it will actually be both deployable and deployed requires collaboration among many parties, e. g. , router vendors and ISPs. – While many stake holders are aware of the problem, none of them has taken initiative to push it forward. – One operational obstacle is that extra costs will incur from developing and deploying BGP security solutions. – Router vendors are not motivated either to develop BGP security solutions due to the lack of interest from ISP. v BGP Security Alert System – PHAS: A Prefix Hijack Alert System – Pretty Good BGP and the Internet Alert Registry EECS 702 2008, Future Internet - 25/25 - DPNM Lab.
Questions ? EECS 702 2008, Future Internet - 26/25 - DPNM Lab.
09983a10a199bfac9d4e23ed0009aae8.ppt