cdd48334113ada3ebc0604cec6ebb469.ppt
- Количество слайдов: 31


Beyond PCI Compliance with Net. IQ Solutions Todd Tucker, CISSP, CPA Director, Chief Security Strategist Ulrich Weigel Product Line Manager, Net. IQ

Agenda • • PCI DSS and its most challenging requirements The need to go beyond PCI DSS The vendor landscape…and Net. IQ How Net. IQ can help you address: – – – Requirement 2. 2 – security configuration standards Requirement 11. 5 – file integrity monitoring Requirement 10. 5 – secure audit trails Requirement 10. 6 – review logs Others • Final Q&A

PCI DSS Requirements 12 Requirements Spanning 6 Control Objectives Build and Maintain a Secure Network 1. Install and maintain a firewall configuration to protect cardholder data 2. Do not use vendor-supplied defaults for system passwords and other security parameters Protect Cardholder Data 3. Protect stored cardholder data 4. Encrypt transmission of cardholder data across open, public networks Maintain a Vulnerability Management Program 5. Use and regularly update anti-virus software 6. Develop and maintain secure systems and applications Implement Strong Access Control Measures 7. Restrict access to cardholder data by business need-to-know 8. Assign a unique ID to each person with computer access 9. Restrict physical access to cardholder data Regularly Monitor and Test Networks 10. Track and monitor all access to network resources and cardholder data 11. Regularly test security systems and processes Maintain an Information Security Policy 12. Maintain a policy that addresses information security
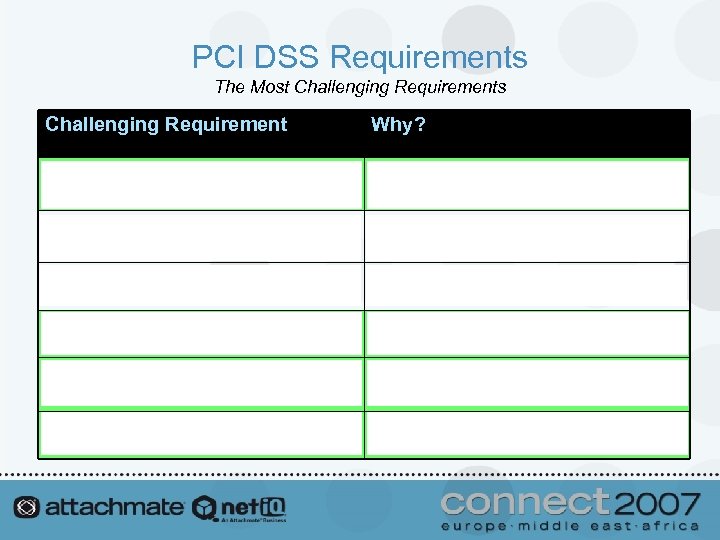
PCI DSS Requirements The Most Challenging Requirements Challenging Requirement Why? 2. Do not use vendor-supplied defaults for system passwords and other security parameters Requires the development and application of secure configuration standards, which often requires a significant amount of work. 3. Protect stored cardholder data Requires cardholder data to be encrypted wherever it is stored, including backup tapes, in logs, etc. ). 6. Develop and maintain secure systems and applications Requires the practice of secure coding guidelines. 7. Restrict access to cardholder data by business need-to-know Many organizations have too many administrators with access. 10. Track and monitor all access to network resources and cardholder data Requires auditing of user access, which is often disabled, along with the security of logs and daily reviews. 11. Regularly test security systems and processes Requires file integrity monitoring of system files and other data.

Going Beyond PCI DSS What We Hear from Our Customers “Compliance Is still king. ” “Data protection is more critical than ever. ” • Log management is still a top compliance requirement for IT, but… • IT shops are struggling to monitor server-level user activity, data access and changes. • Help us get a “C” in compliance, but no more. • We want an “A” in security! • Threat vectors are changing and less predictable and… • Quick detection, response and investigation are essential to reducing the business impact. “We want products that allow us to start fast and start simple, but supports our strategic security requirements. ” • Multi-vendor integration lengthens deployments, but… • Many simple products are too simple to support our IT organization as it matures.

Corporate Data Must Be Protected Hard Lessons Learned 8 Months Undetected | Internet-based theft Dai Nippon Printing reports client data theft Reuters | 12 March 2007 TOKYO, March 12 (Reuters) - Japan's Dai Nippon Printing Co. said on Monday a former contract worker stole nearly 9 million pieces of private data on customers from 43 clients including Toyota Motor Corp. Card. Systems' Data Left Unsecured Kim Zetter | Wired Magazine | 22 June 2005 Master. Card International announced last Friday that intruders had accessed the data from Card. Systems Solutions, a payment processing company based in Arizona, after placing a malicious script on the company's network. "Had they been following the rules and requirements, they would not have been compromised, " Jones said. These breaches occurred over a long period of time and took Dai Nippon, one of Japan's largest different threat vectors TJX thieves had |time to steal, trip up commercial printing companies, said the By Mark Jewell | AP 13 April 2007 confidential information included names, addresses and credit card numbers intended for use in direct mailing and other printing services. Dai Nippon said the employee stole client data between May 2001 and March 2006 by copying information on to floppy disks and other recording media. TJX warned in its recent regulatory filing against expecting too much from its investigation. "We believe that we may never be able to identify much of the information believed stolen" aside 17 Months Undetected | Theft via far, the filing said. from the 45. 7 million cards it knows about sowireless access The way TJX detected the breach — by finding what the company calls "suspicious software" on its computer systems — is an indication not only of the hackers' skill in avoiding detection for so long but also holes in TJX's security, experts say. 5 Years Undetected | Theft by insider
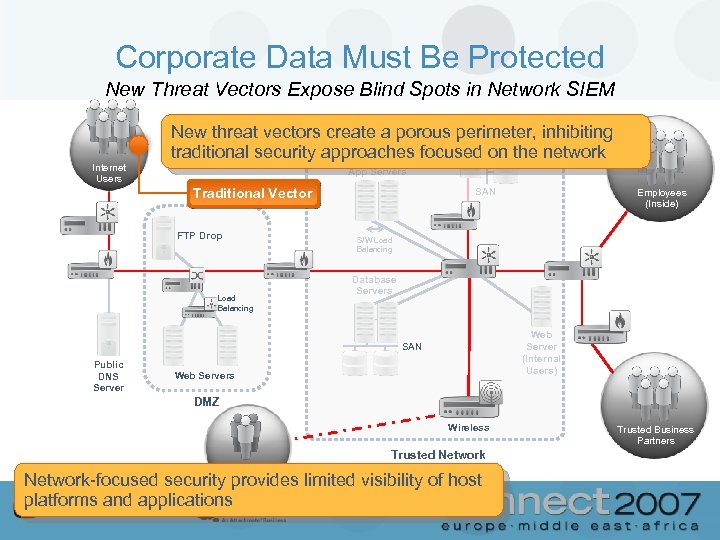
Corporate Data Must Be Protected New Threat Vectors Expose Blind Spots in Network SIEM Internet Users New threat vectors create a porous perimeter, inhibiting traditional security approaches focused on the network App Servers Traditional Vector FTP Drop SAN S/W Load Balancing Database Servers Web Server (Internal Users) SAN Public DNS Server Employees (Inside) Web Servers DMZ Wireless Organized Crime Trusted Network-focused security provides limited visibility of host platforms and applications Trusted Business Partners
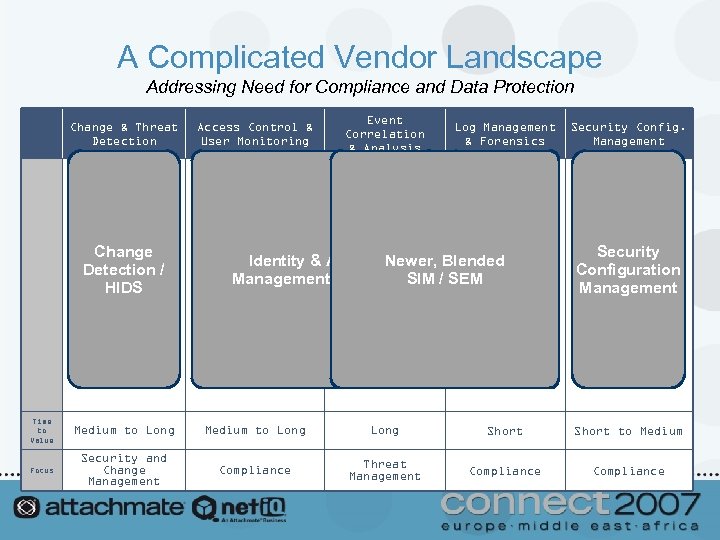
A Complicated Vendor Landscape Addressing Need for Compliance and Data Protection Change & Threat Detection Change Detection / HIDS Access Control & User Monitoring Event Correlation & Analysis Log Management & Forensics Traditional Identity & Access Newer, Blended Traditional SEM Management Vendors SIM / SEM SIM Security Config. Management Security Configuration Management Time to Value Medium to Long Short to Medium Focus Security and Change Management Compliance Threat Management Compliance

A Simpler Solution Compliance and Comprehensive Data Protection Change & Threat Detection Access Control & User Monitoring Event Correlation & Analysis Log Management & Forensics Security Config. Management Net. IQ Security Compliance Suite The industry’s only integrated solution to include: Change and Threat Detection User and Access Monitoring Security Event Correlation and Analysis Log Management and Forensics Security Configuration Management Time to Value Medium to Long Short to Medium Focus Security and Change Management Compliance Threat Management Compliance

Net. IQ Security Compliance Suite • Net. IQ Security Manager – Leading security information and event management solution • Change Guardian Modules – Change detection, classification and alerting • Net. IQ Secure Configuration Manager – Robust security assessment and reporting with baselining and delta reporting

Addressing Requirement 2. 2 Security Configuration Standards 2. 2 Develop configuration standards for all system components. Assure that these standards address all known security vulnerabilities and are consistent with industry-accepted system hardening standards as defined, for example, by Sys. Admin Audit Network Security Network (SANS), National Institute of Standards Technology (NIST), and Center for Internet Security (CIS). 2. 2. 1 Implement only one primary function per server (for example, web servers, database servers, and DNS should be implemented on separate servers) 2. 2. 2 Disable all unnecessary and insecure services and protocols (services and protocols not directly needed to perform the devices’ specified function) 2. 2. 3 Configure system security parameters to prevent misuse 2. 2. 4 Remove all unnecessary functionality, such as scripts, drivers, features, subsystems, file systems, and unnecessary web servers.
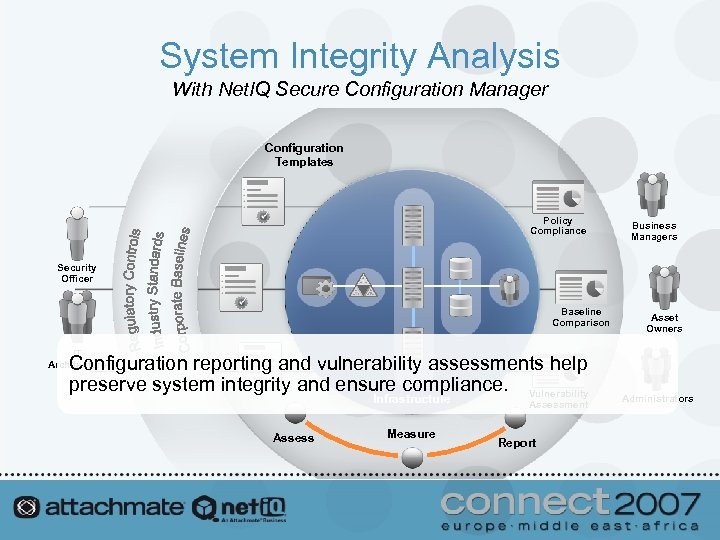
System Integrity Analysis With Net. IQ Secure Configuration Manager Configuration Templates Policy Compliance Business Managers Security Officer Baseline Comparison Asset Owners IT Architecture Configuration reporting and vulnerability assessments help preserve system integrity and ensure compliance. Vulnerability Infrastructure Assess Measure Assessment Report Administrators
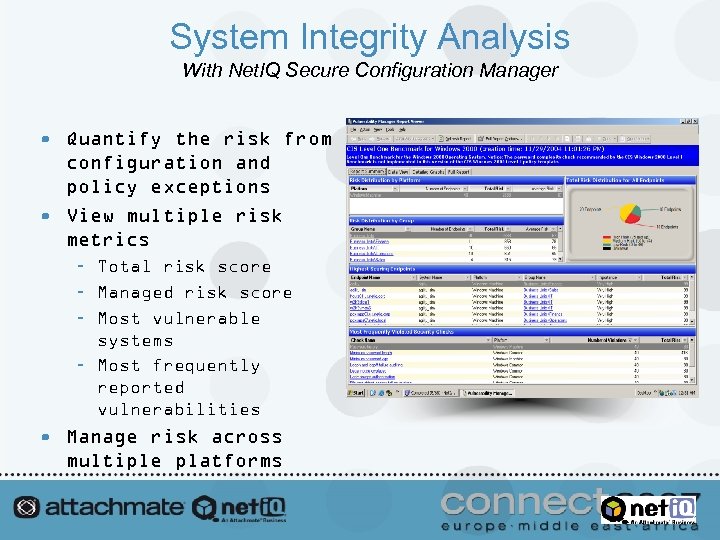
System Integrity Analysis With Net. IQ Secure Configuration Manager • Quantify the risk from configuration and policy exceptions • View multiple risk metrics – Total risk score – Managed risk score – Most vulnerable systems – Most frequently reported vulnerabilities • Manage risk across multiple platforms
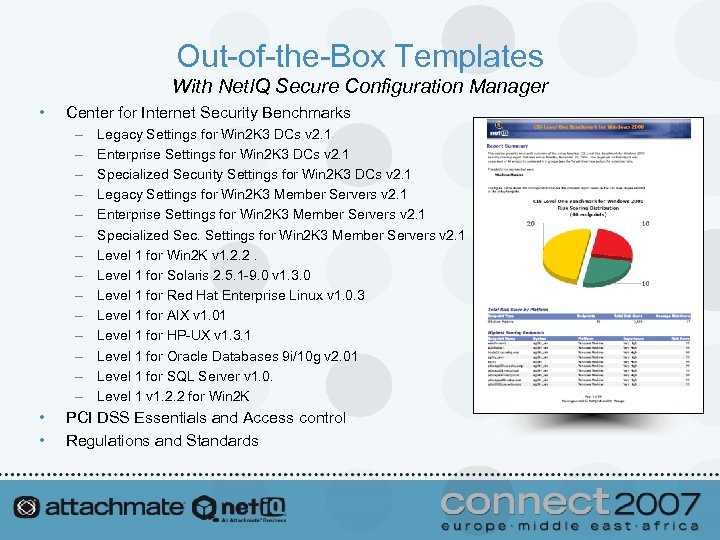
Out-of-the-Box Templates With Net. IQ Secure Configuration Manager • Center for Internet Security Benchmarks – – – – • • Legacy Settings for Win 2 K 3 DCs v 2. 1 Enterprise Settings for Win 2 K 3 DCs v 2. 1 Specialized Security Settings for Win 2 K 3 DCs v 2. 1 Legacy Settings for Win 2 K 3 Member Servers v 2. 1 Enterprise Settings for Win 2 K 3 Member Servers v 2. 1 Specialized Sec. Settings for Win 2 K 3 Member Servers v 2. 1 Level 1 for Win 2 K v 1. 2. 2. Level 1 for Solaris 2. 5. 1 -9. 0 v 1. 3. 0 Level 1 for Red Hat Enterprise Linux v 1. 0. 3 Level 1 for AIX v 1. 01 Level 1 for HP-UX v 1. 3. 1 Level 1 for Oracle Databases 9 i/10 g v 2. 01 Level 1 for SQL Server v 1. 0. Level 1 v 1. 2. 2 for Win 2 K PCI DSS Essentials and Access control Regulations and Standards
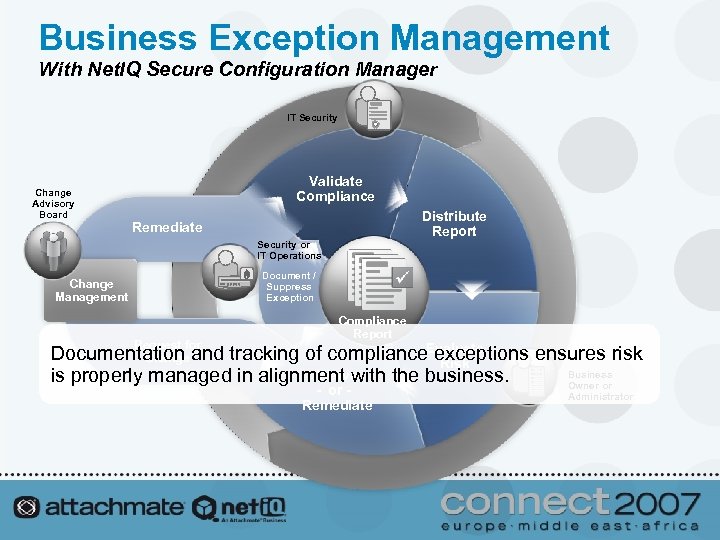
Business Exception Management With Net. IQ Secure Configuration Manager IT Security Change Advisory Board Validate Compliance Distribute Report Remediate Security or IT Operations Document / Suppress Exception Change Management Request for Compliance Report Documentation and tracking of compliance. Evaluate exceptions ensures risk Change Risk Business Waive is properly managed in alignment with the business. Owner or - or Remediate Administrator
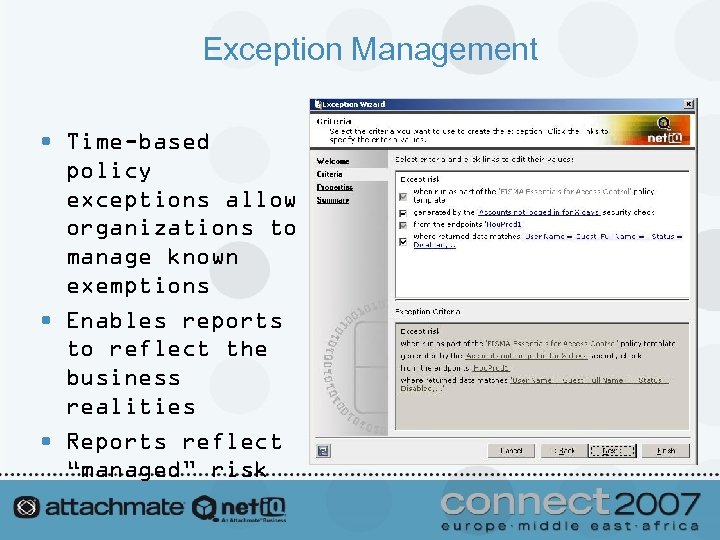
Exception Management • Time-based policy exceptions allow organizations to manage known exemptions • Enables reports to reflect the business realities • Reports reflect “managed” risk

Addressing Requirement 11. 5 File Integrity Monitoring 11. 5 Deploy file integrity monitoring software to alert personnel to unauthorized modification of critical system or content files; and configure the software to perform critical file comparisons at least weekly. Critical files are not necessarily only those containing cardholder data. For file integrity monitoring purposes, critical files are usually those that do not regularly change, but the modification of which could indicate a system compromise or risk of compromise. File integrity monitoring products usually come pre-configured with critical files for the related operating system. Other critical files, such as those for custom applications, must be evaluated and defined by the entity (that is the merchant or service provider).
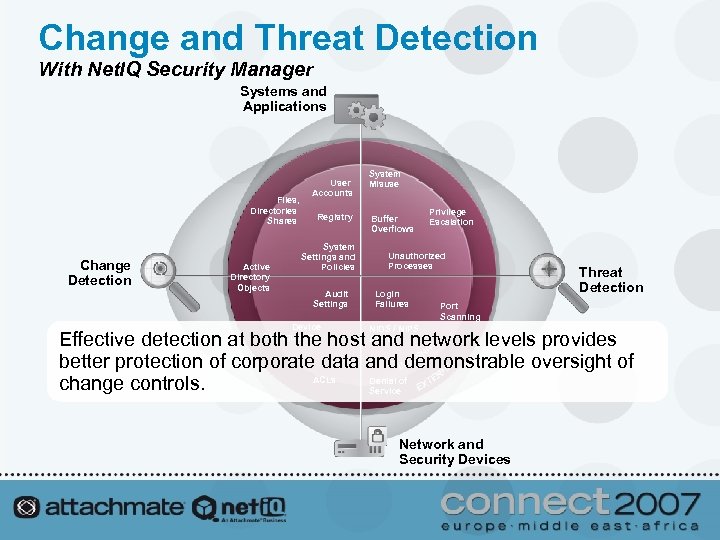
Change and Threat Detection With Net. IQ Security Manager Systems and Applications Files, Directories Shares Change Detection Active Directory Objects User Accounts Registry System Settings and Policies Audit Settings Device Configuration System Misuse Buffer Overflows Privilege Escalation Unauthorized Processes Login Failures Threat Detection Port Scanning NIDS / NIPS Alerts Effective detection at both the host and network levels provides better protection of corporate data and demonstrable oversight of ACLs Denial of change controls. Service Network and Security Devices
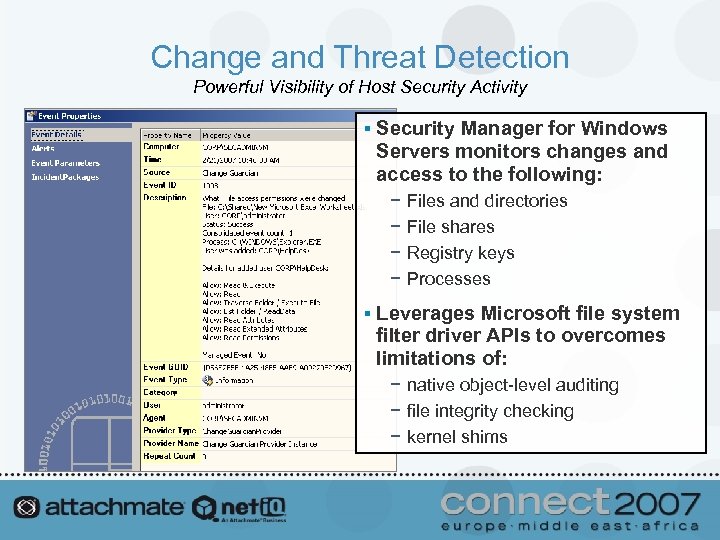
Change and Threat Detection Powerful Visibility of Host Security Activity § Security Manager for Windows Servers monitors changes and access to the following: − − Files and directories File shares Registry keys Processes § Leverages Microsoft file system filter driver APIs to overcomes limitations of: − native object-level auditing − file integrity checking − kernel shims
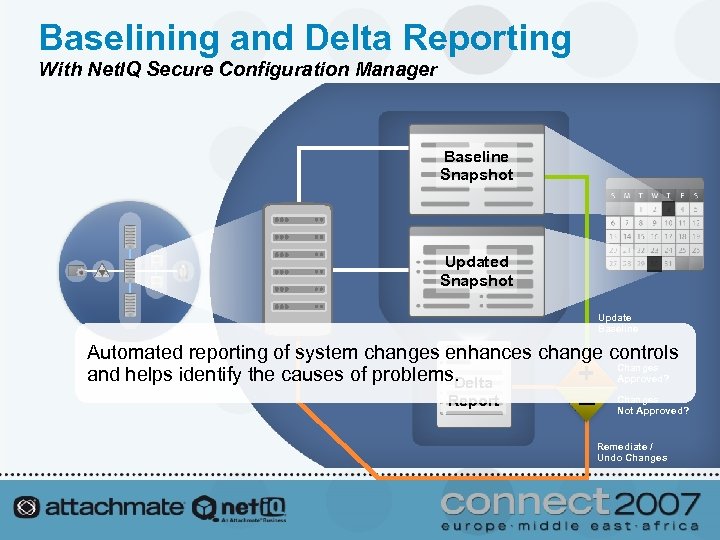
Baselining and Delta Reporting With Net. IQ Secure Configuration Manager Baseline Snapshot Updated Snapshot Update Baseline Automated reporting of system changes enhances change controls and helps identify the causes of problems. Approved? + Changes Delta Report – Changes Not Approved? Remediate / Undo Changes
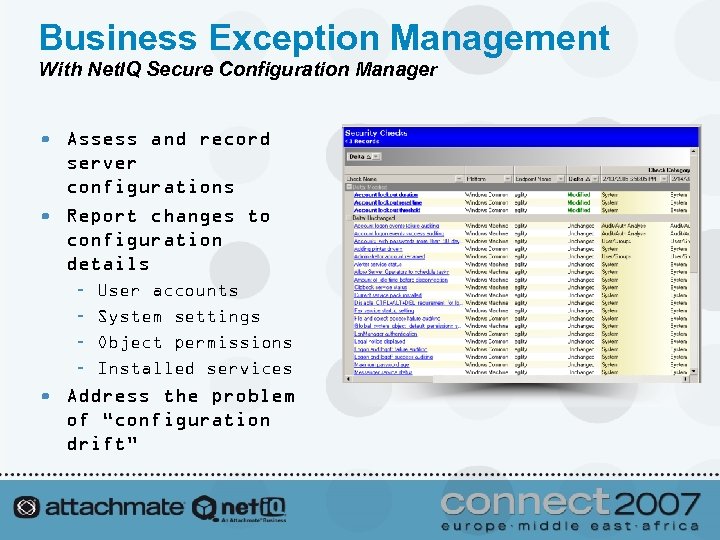
Business Exception Management With Net. IQ Secure Configuration Manager • Assess and record server configurations • Report changes to configuration details – – User accounts System settings Object permissions Installed services • Address the problem of “configuration drift”

Addressing Requirements 10. 5 / 10. 6 Secure Audit Trails and Review Them 10. 5 Secure audit trails so they cannot be altered. 10. 5. 1 Limit viewing of audit trails to those with a job-related need 10. 5. 2 Protect audit trail files from unauthorized modifications 10. 5. 3 Promptly back-up audit trail files to a centralized log server or media that is difficult to alter 10. 5. 4 Copy logs for wireless networks onto a log server on the internal LAN. 10. 5. 5 Use file integrity monitoring and change detection software on logs to ensure that existing log data cannot be changed without generating alerts (although new data being added should not cause an alert). 10. 6 Review logs for all system components at least daily. Log reviews must include those servers that perform security functions like intrusion detection system (IDS) and authentication, authorization, and accounting protocol (AAA) servers (for example, RADIUS). Note: Log harvesting, parsing, and alerting tools may be used to achieve compliance with Requirement 10. 6.
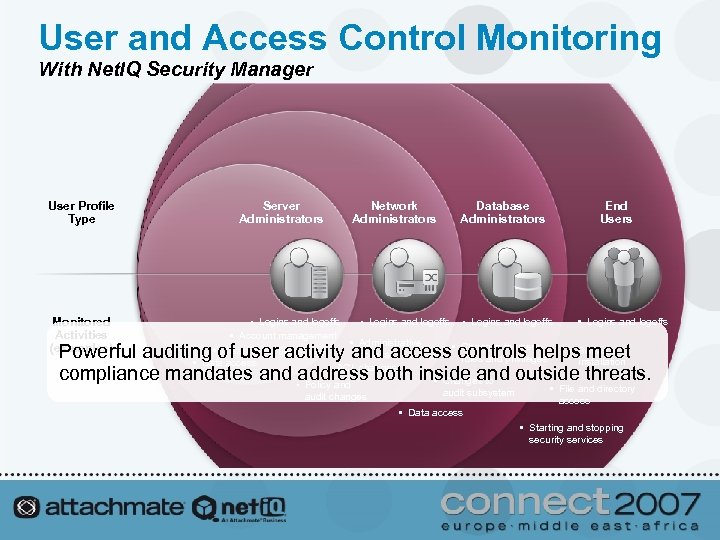
User and Access Control Monitoring With Net. IQ Security Manager User Profile Type Monitored Activities (examples) Server Administrators Network Administrators Database Administrators End Users • Logins and logoffs • Account management • Administrative • Changes to users, • Clearing log files access roles and privileges • Data access • ACL changes • Logins and logoffs • meet Powerful auditing of user activity and access controls helps. Software installation compliance mandates and • address both inside and outside threats. • Changes to Policy and audit changes audit subsystem • File and directory access • Data access • Starting and stopping security services
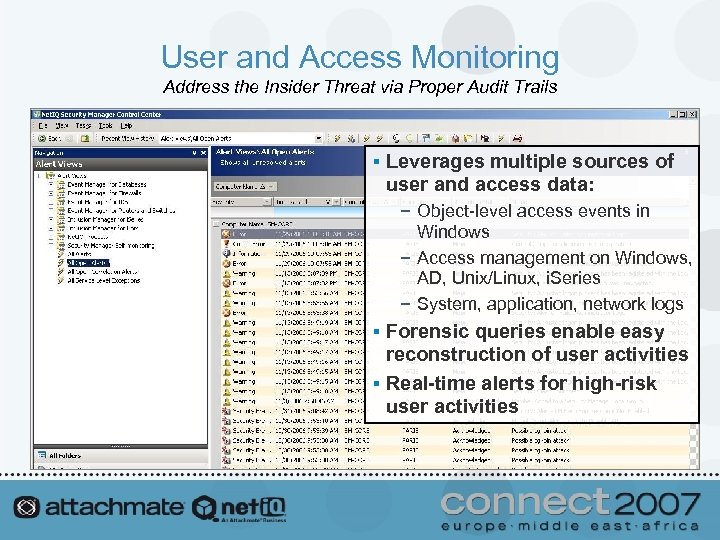
User and Access Monitoring Address the Insider Threat via Proper Audit Trails § Leverages multiple sources of user and access data: − Object-level access events in Windows − Access management on Windows, AD, Unix/Linux, i. Series − System, application, network logs § Forensic queries enable easy reconstruction of user activities § Real-time alerts for high-risk user activities
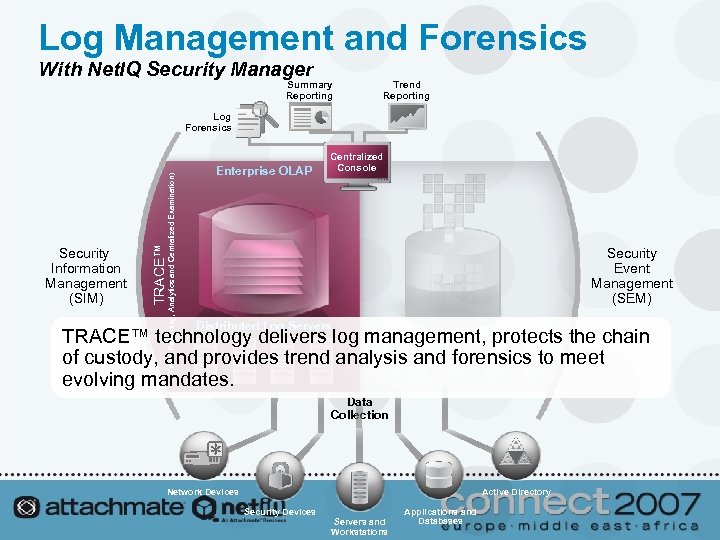
Log Management and Forensics With Net. IQ Security Manager Summary Reporting Trend Reporting Enterprise OLAP Centralized Console TRACE™ Security Information Management (SIM) (Trend Reporting, Analytics and Centralized Examination) Log Forensics Security Event Management (SEM) Distributed Log Servers TRACE™ technology delivers log management, protects the chain of custody, and provides trend analysis and forensics to meet evolving mandates. Data Collection Network Devices Active Directory Security Devices Servers and Workstations Applications and Databases
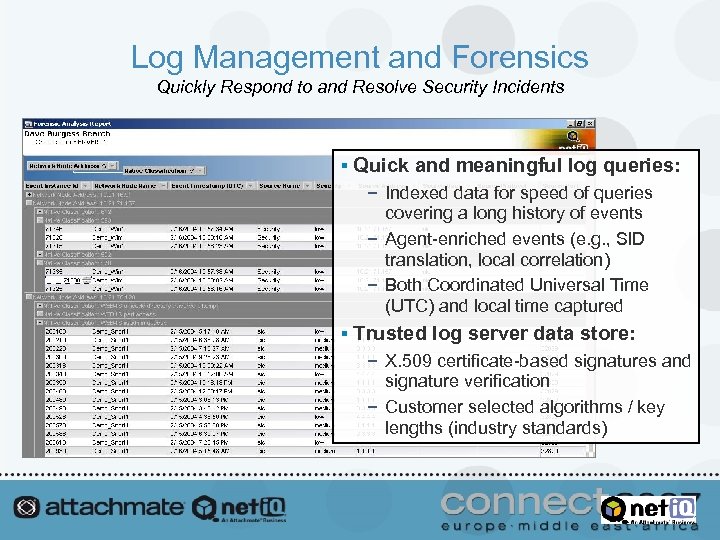
Log Management and Forensics Quickly Respond to and Resolve Security Incidents § Quick and meaningful log queries: − Indexed data for speed of queries covering a long history of events − Agent-enriched events (e. g. , SID translation, local correlation) − Both Coordinated Universal Time (UTC) and local time captured § Trusted log server data store: − X. 509 certificate-based signatures and signature verification − Customer selected algorithms / key lengths (industry standards)
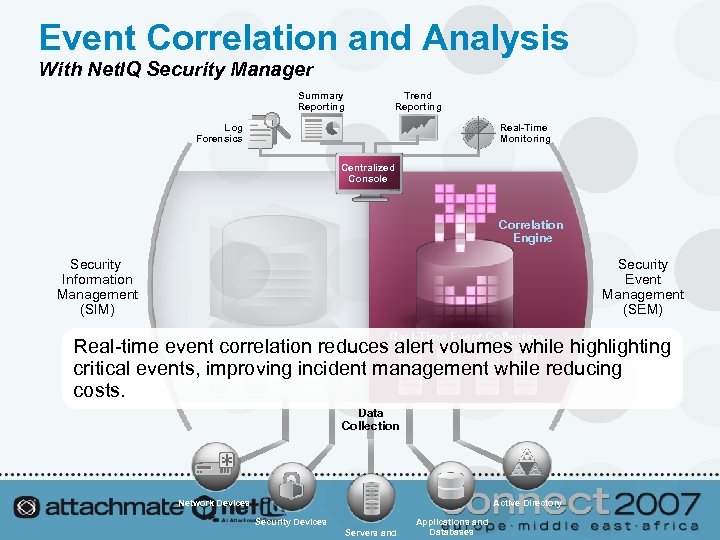
Event Correlation and Analysis With Net. IQ Security Manager Summary Reporting Trend Reporting Real-Time Monitoring Log Forensics Centralized Console Correlation Engine Security Information Management (SIM) Security Event Management (SEM) Real-Time Event Collection Real-time event correlation reduces alert volumes while highlighting critical events, improving incident management while reducing costs. Data Collection Network Devices Active Directory Security Devices Servers and Applications and Databases
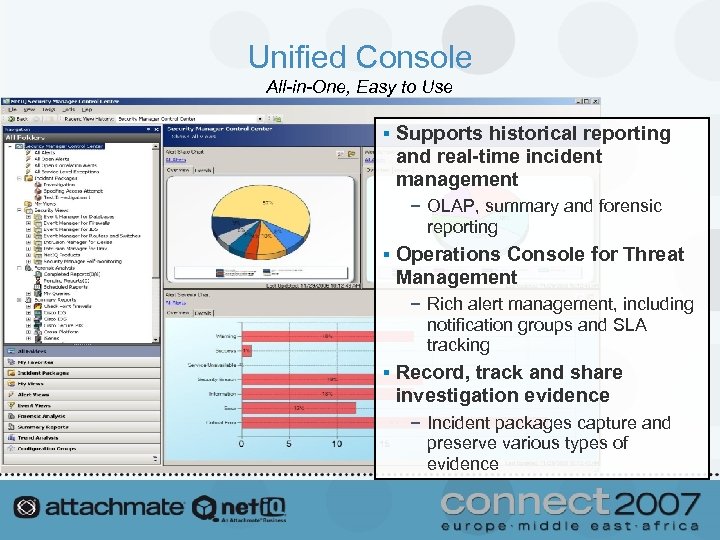
Unified Console All-in-One, Easy to Use § Supports historical reporting and real-time incident management − OLAP, summary and forensic reporting § Operations Console for Threat Management − Rich alert management, including notification groups and SLA tracking § Record, track and share investigation evidence − Incident packages capture and preserve various types of evidence

Other Ways Net. IQ Can Help • Requirement 7: Restrict access to cardholder data by business need-to-know – Entitlement reporting with Net. IQ Secure Configuration Manager – Delegated administration to reduce full administrative privileges with Net. IQ Change Administrator for Windows, Net. IQ Directory & Resource Administrator, Net. IQ Group Policy Administrator, and Net. IQ access management features on Unix, Linux and i. Series • Requirement 12: Maintain a policy that addresses information security for employees and contractors – Policy lifecycle management and security awareness with Net. IQ Vigil. Ent Policy Center

Final Q&A Todd Tucker, CISSP, CPA Director, Chief Security Strategist Ulrich Weigel Product Line Manager, Net. IQ
cdd48334113ada3ebc0604cec6ebb469.ppt