ac7c23e613a7c457cd1ac4561200a9c8.ppt
- Количество слайдов: 117

Better-than-best-effort: Qo. S, Int. Serv, Diff. Serv, RSVP, RTP Shivkumar Kalyanaraman Rensselaer Polytechnic Institute shivkuma@ecse. rpi. edu http: //www. ecse. rpi. edu/Homepages/shivkuma Based in part on slides of Ion Stoica, Jim Kurose, Srini Seshan, Srini Keshav Shivkumar Kalyanaraman Rensselaer Polytechnic Institute 1

Overview q q q Why better-than-best-effort (Qo. S-enabled) Internet ? Quality of Service (Qo. S) building blocks End-to-end protocols: RTP, H. 323 Network protocols: q Integrated Services(Int. Serv), RSVP. q Scalable differentiated services: Diff. Serv Control plane: Qo. S routing, traffic engineering, policy management, pricing models Shivkumar Kalyanaraman Rensselaer Polytechnic Institute 2

Why Better-than-Best-Effort (Qo. S)? q To support a wider range of applications q Real-time, Multimedia, etc q To develop sustainable economic models and new private networking services q Current flat priced models, and best-effort services do not cut it for businesses Shivkumar Kalyanaraman Rensselaer Polytechnic Institute 3
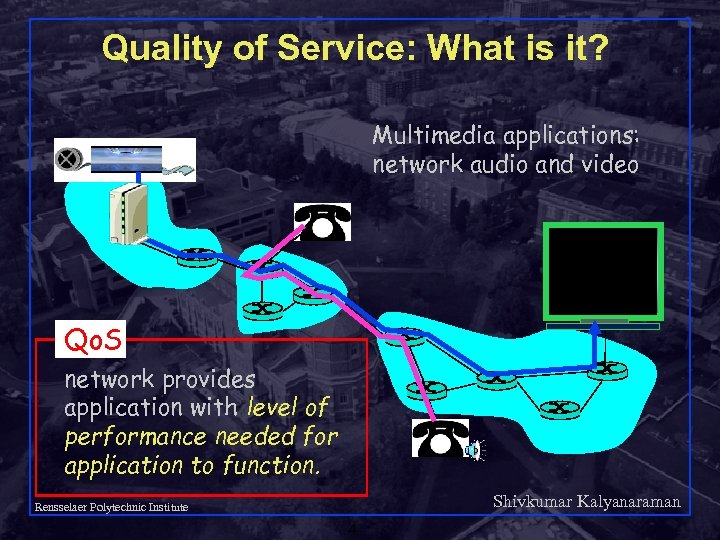
Quality of Service: What is it? Multimedia applications: network audio and video Qo. S network provides application with level of performance needed for application to function. Shivkumar Kalyanaraman Rensselaer Polytechnic Institute 4

What is Qo. S? q “Better performance” as described by a set of parameters or measured by a set of metrics. q Generic parameters: q Bandwidth q Delay, Delay-jitter q Packet loss rate (or loss probability) q Transport/Application-specific parameters: q Timeouts q Percentage of “important” packets lost Shivkumar Kalyanaraman Rensselaer Polytechnic Institute 5

What is Qo. S (contd) ? q These parameters can be measured at several granularities: q “micro” flow, aggregate flow, population. q Qo. S considered “better” if q a) more parameters can be specified q b) Qo. S can be specified at a fine-granularity. q Qo. S spectrum: Best Effort Leased Line Shivkumar Kalyanaraman Rensselaer Polytechnic Institute 6
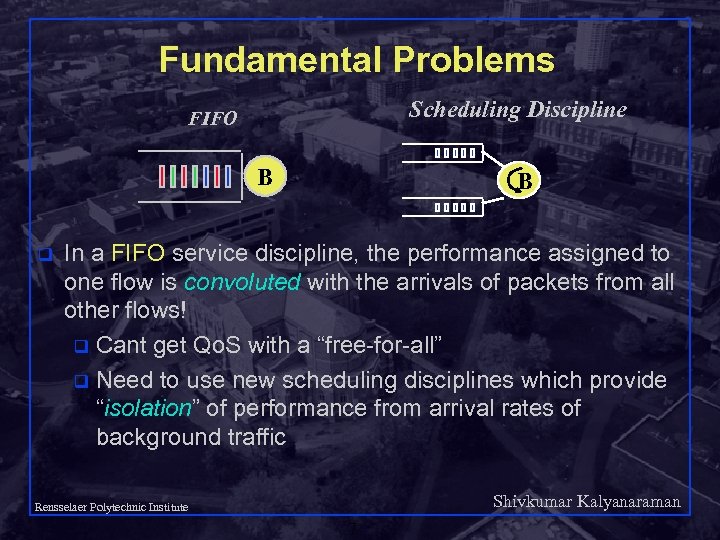
Fundamental Problems Scheduling Discipline FIFO B q B In a FIFO service discipline, the performance assigned to one flow is convoluted with the arrivals of packets from all other flows! q Cant get Qo. S with a “free-for-all” q Need to use new scheduling disciplines which provide “isolation” of performance from arrival rates of background traffic Shivkumar Kalyanaraman Rensselaer Polytechnic Institute 7
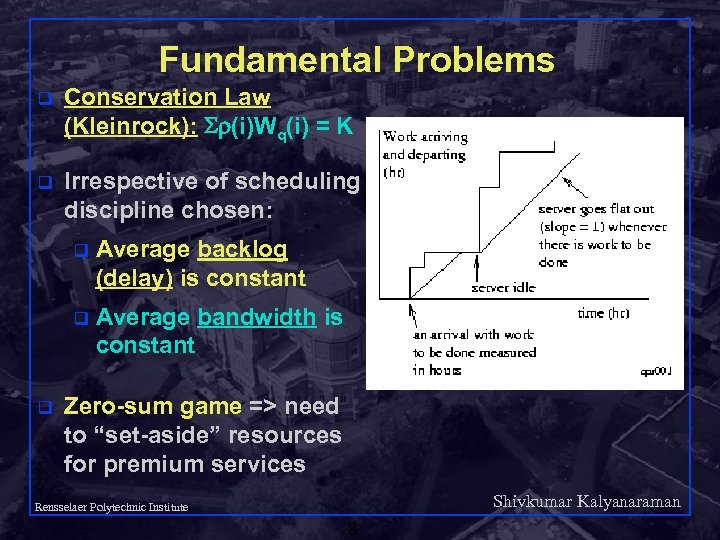
Fundamental Problems q Conservation Law (Kleinrock): (i)Wq(i) = K q Irrespective of scheduling discipline chosen: q q q Average backlog (delay) is constant Average bandwidth is constant Zero-sum game => need to “set-aside” resources for premium services Shivkumar Kalyanaraman Rensselaer Polytechnic Institute 8
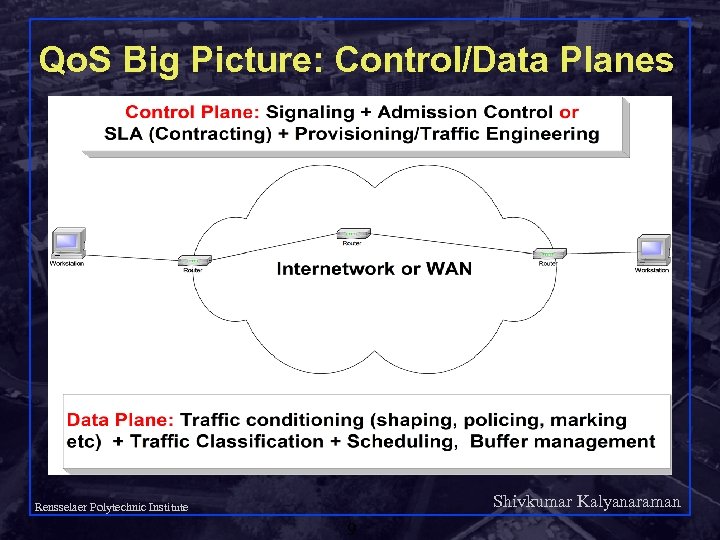
Qo. S Big Picture: Control/Data Planes Shivkumar Kalyanaraman Rensselaer Polytechnic Institute 9
Qo. S Components Qo. S => set aside resources for premium services q Qo. S components: q a) Specification of premium services: (service/service level agreement design) q b) How much resources to set aside? (admission control/provisioning) q c) How to ensure network resource utilization, do load balancing, flexibly manage traffic aggregates and paths ? (Qo. S routing, traffic engineering) q Shivkumar Kalyanaraman Rensselaer Polytechnic Institute 10

Qo. S Components (Continued) q d) How to actually set aside these resources in a distributed manner ? (signaling, provisioning, policy) q e) How to deliver the service when the traffic actually comes in (claim/police resources)? (traffic shaping, classification, scheduling) q f) How to monitor quality, account and price these services? (network mgmt, accounting, billing, pricing) Shivkumar Kalyanaraman Rensselaer Polytechnic Institute 11

How to upgrade the Internet for Qo. S? q Approach: de-couple end-system evolution from network evolution q End-to-end protocols: RTP, H. 323 etc to spur the growth of adaptive multimedia applications q Assume best-effort or better-than-best-effort clouds q Network protocols: Int. Serv, Diff. Serv, RSVP, MPLS, COPS … q To support better-than-best-effort capabilities at the network (IP) level Shivkumar Kalyanaraman Rensselaer Polytechnic Institute 12

QOS SPECIFICATION, TRAFFIC, SERVICE CHARACTERIZATION, BASIC MECHANISMS Shivkumar Kalyanaraman Rensselaer Polytechnic Institute 13

Service Specification Loss: probability that a flow’s packet is lost q Delay: time it takes a packet’s flow to get from source to destination q Delay jitter: maximum difference between the delays experienced by two packets of the flow q Bandwidth: maximum rate at which the soource can send traffic q Qo. S spectrum: q Best Effort Leased Line Shivkumar Kalyanaraman Rensselaer Polytechnic Institute 14

Hard Real Time: Guaranteed Services Service contract q Network to client: guarantee a deterministic upper bound on delay for each packet in a session q Client to network: the session does not send more than it specifies q Algorithm support q Admission control based on worst-case analysis q Per flow classification/scheduling at routers q Shivkumar Kalyanaraman Rensselaer Polytechnic Institute 15
Soft Real Time: Controlled Load Service contract: q Network to client: similar performance as an unloaded best-effort network q Client to network: the session does not send more than it specifies q Algorithm Support q Admission control based on measurement of aggregates q Scheduling for aggregate possible q Shivkumar Kalyanaraman Rensselaer Polytechnic Institute 16
Traffic and Service Characterization To quantify a service one has two know q Flow’s traffic arrival q Service provided by the router, i. e. , resources reserved at each router q Examples: q Traffic characterization: token bucket q Service provided by router: fix rate and fix buffer space q Characterized by a service model (service curve framework) q Shivkumar Kalyanaraman Rensselaer Polytechnic Institute 17
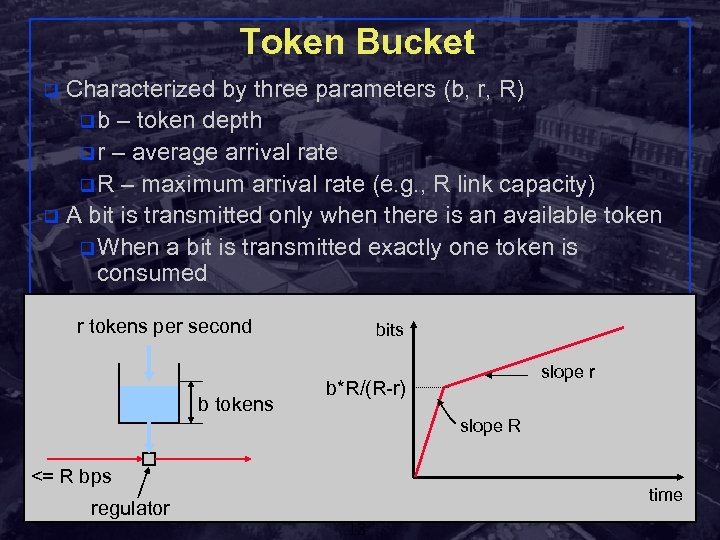
Token Bucket Characterized by three parameters (b, r, R) q b – token depth q r – average arrival rate q R – maximum arrival rate (e. g. , R link capacity) q A bit is transmitted only when there is an available token q When a bit is transmitted exactly one token is consumed q r tokens per second b tokens bits slope r b*R/(R-r) slope R <= R bps regulator time Shivkumar Kalyanaraman Rensselaer Polytechnic Institute 18
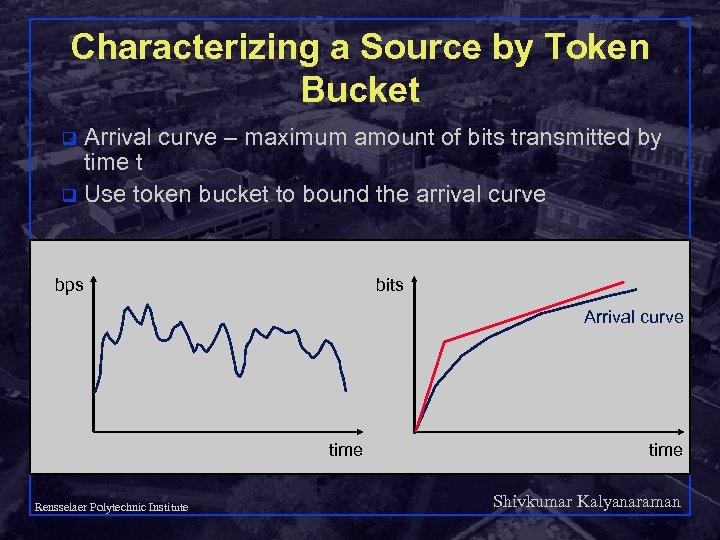
Characterizing a Source by Token Bucket Arrival curve – maximum amount of bits transmitted by time t q Use token bucket to bound the arrival curve q bps bits Arrival curve time Shivkumar Kalyanaraman Rensselaer Polytechnic Institute 19
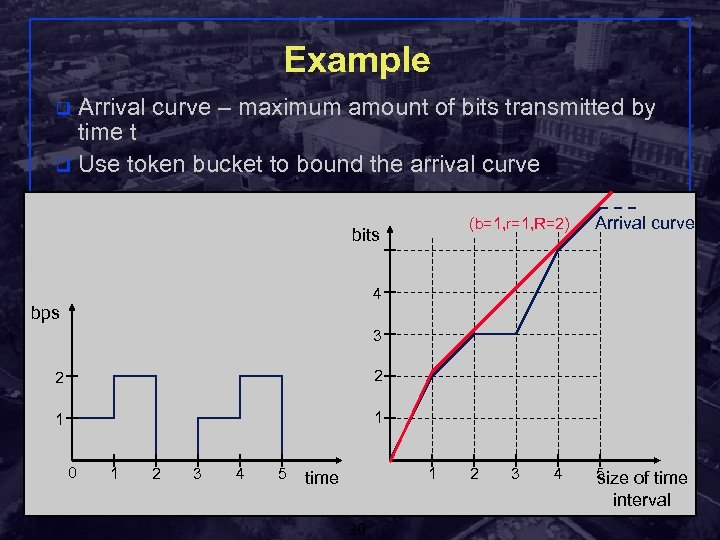
Example Arrival curve – maximum amount of bits transmitted by time t q Use token bucket to bound the arrival curve q (b=1, r=1, R=2) bits Arrival curve 2 5 size of time 4 bps 3 2 2 1 1 0 1 2 3 4 5 1 time 3 4 interval Shivkumar Kalyanaraman Rensselaer Polytechnic Institute 20
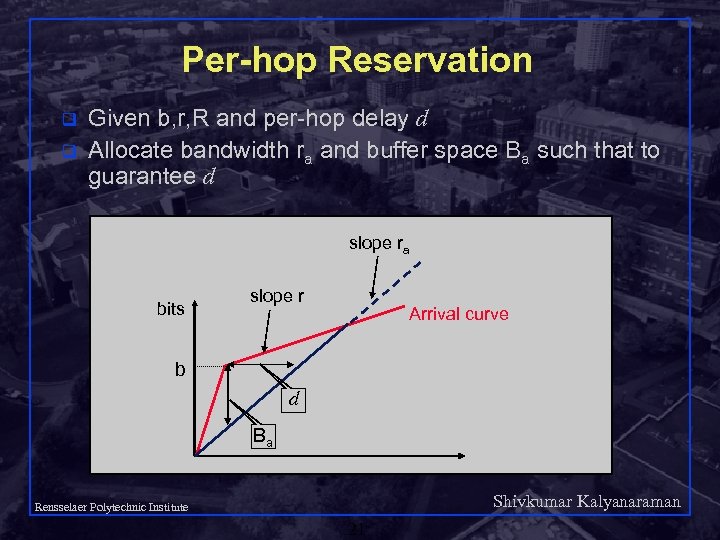
Per-hop Reservation q q Given b, r, R and per-hop delay d Allocate bandwidth ra and buffer space Ba such that to guarantee d slope ra bits slope r Arrival curve b d Ba Shivkumar Kalyanaraman Rensselaer Polytechnic Institute 21
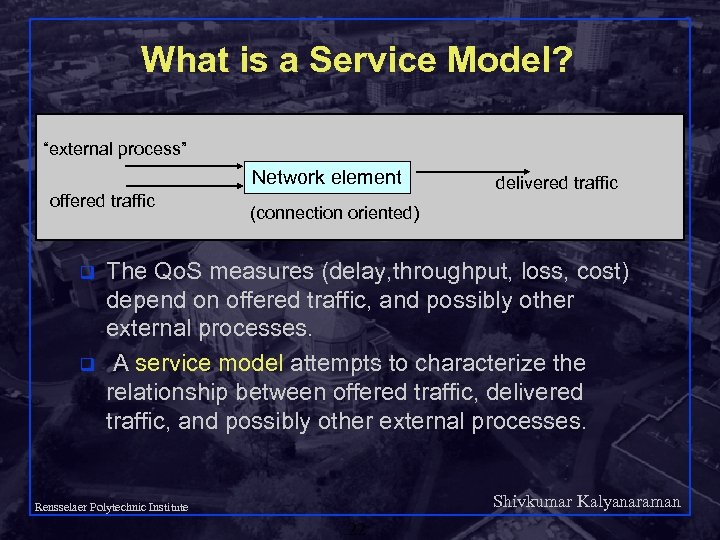
What is a Service Model? “external process” Network element offered traffic q q delivered traffic (connection oriented) The Qo. S measures (delay, throughput, loss, cost) depend on offered traffic, and possibly other external processes. A service model attempts to characterize the relationship between offered traffic, delivered traffic, and possibly other external processes. Shivkumar Kalyanaraman Rensselaer Polytechnic Institute 22
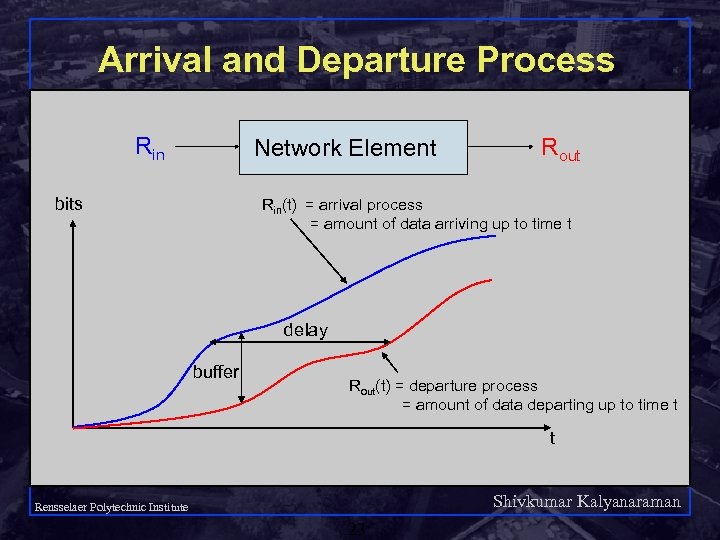
Arrival and Departure Process Rin Network Element bits Rout Rin(t) = arrival process = amount of data arriving up to time t delay buffer Rout(t) = departure process = amount of data departing up to time t t Shivkumar Kalyanaraman Rensselaer Polytechnic Institute 23
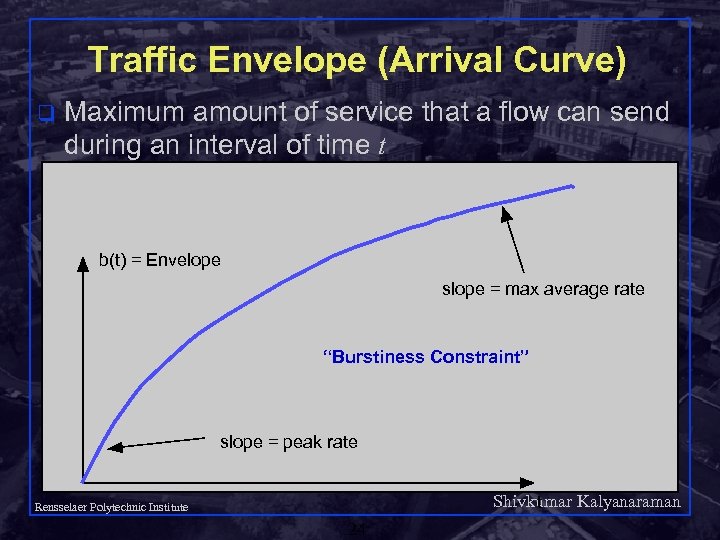
Traffic Envelope (Arrival Curve) q Maximum amount of service that a flow can send during an interval of time t b(t) = Envelope slope = max average rate “Burstiness Constraint” slope = peak rate Shivkumar Kalyanaraman t Rensselaer Polytechnic Institute 24
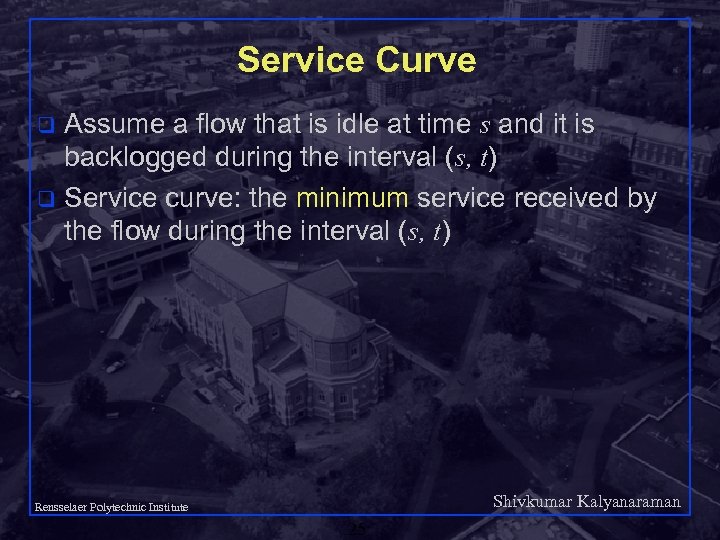
Service Curve Assume a flow that is idle at time s and it is backlogged during the interval (s, t) q Service curve: the minimum service received by the flow during the interval (s, t) q Shivkumar Kalyanaraman Rensselaer Polytechnic Institute 25
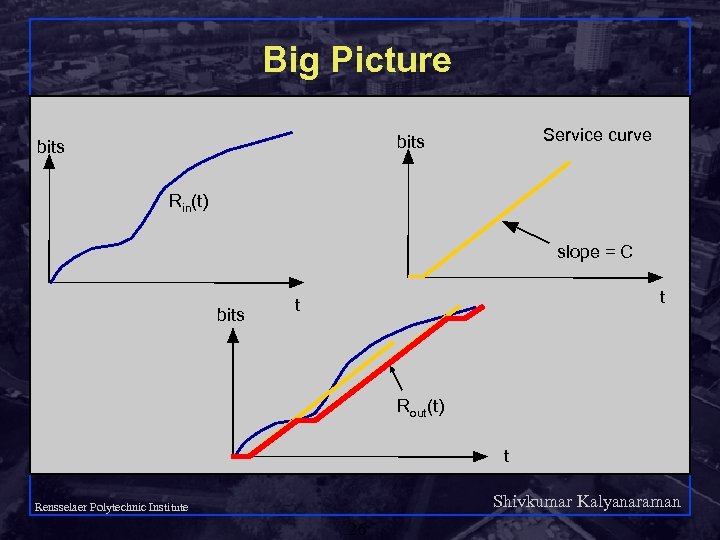
Big Picture Service curve bits Rin(t) slope = C bits t t Rout(t) t Shivkumar Kalyanaraman Rensselaer Polytechnic Institute 26
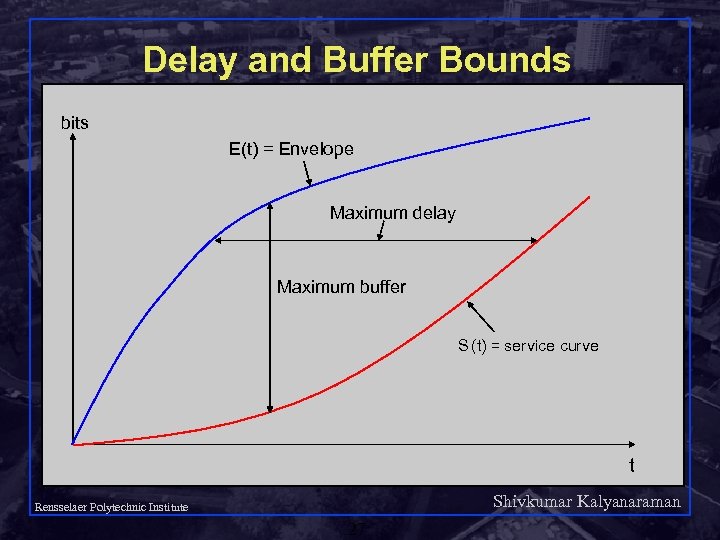
Delay and Buffer Bounds bits E(t) = Envelope Maximum delay Maximum buffer S (t) = service curve t Shivkumar Kalyanaraman Rensselaer Polytechnic Institute 27
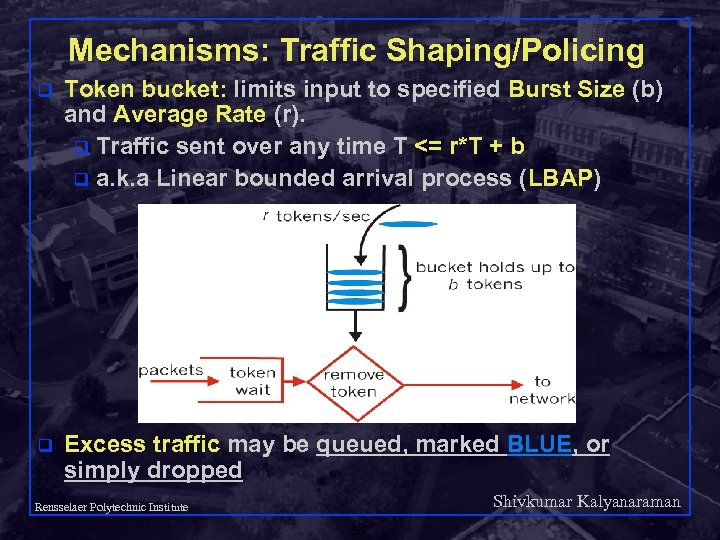
Mechanisms: Traffic Shaping/Policing q Token bucket: limits input to specified Burst Size (b) and Average Rate (r). q Traffic sent over any time T <= r*T + b q a. k. a Linear bounded arrival process (LBAP) q Excess traffic may be queued, marked BLUE, or simply dropped Shivkumar Kalyanaraman Rensselaer Polytechnic Institute 28
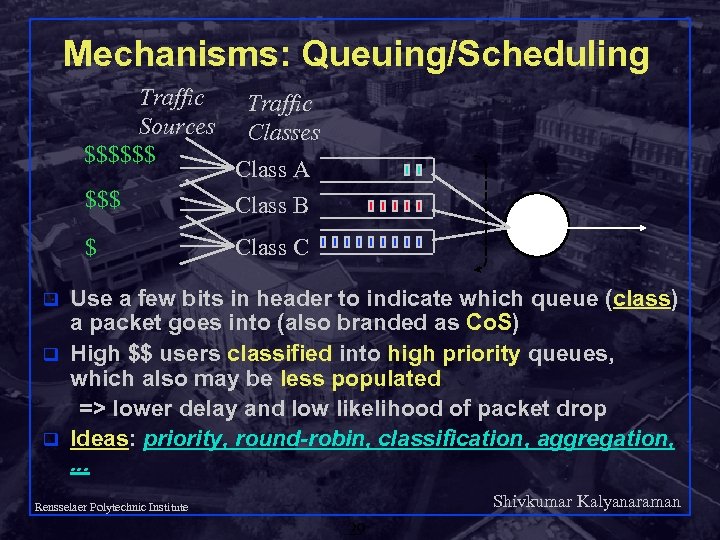
Mechanisms: Queuing/Scheduling Traffic Sources $$$$$$ Traffic Classes $$$ $ q q q Class A Class B Class C Use a few bits in header to indicate which queue (class) a packet goes into (also branded as Co. S) High $$ users classified into high priority queues, which also may be less populated => lower delay and low likelihood of packet drop Ideas: priority, round-robin, classification, aggregation, . . . Shivkumar Kalyanaraman Rensselaer Polytechnic Institute 29
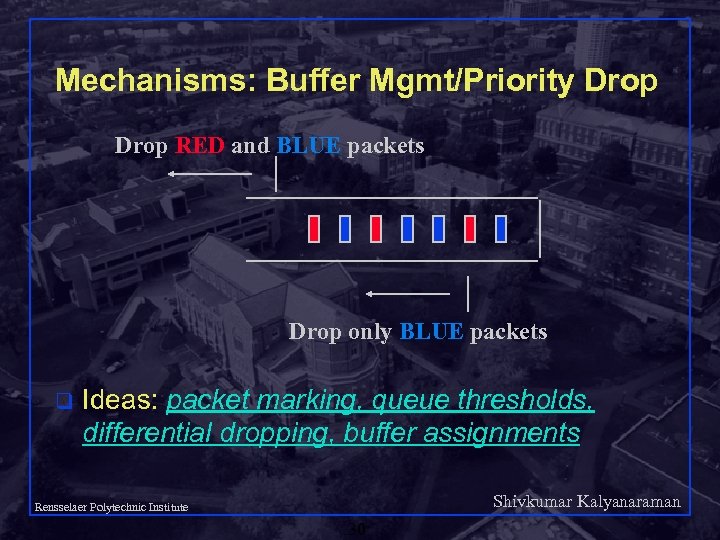
Mechanisms: Buffer Mgmt/Priority Drop RED and BLUE packets Drop only BLUE packets q Ideas: packet marking, queue thresholds, differential dropping, buffer assignments Shivkumar Kalyanaraman Rensselaer Polytechnic Institute 30

SCHEDULING Shivkumar Kalyanaraman Rensselaer Polytechnic Institute 31
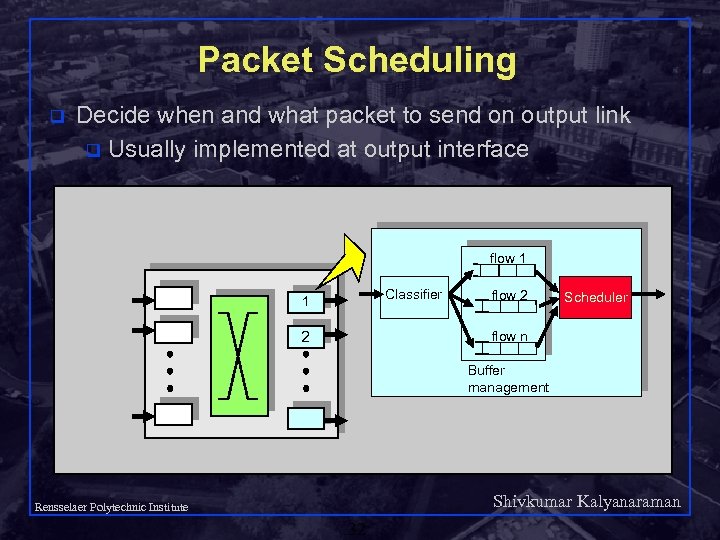
Packet Scheduling q Decide when and what packet to send on output link q Usually implemented at output interface flow 1 Classifier 1 2 flow 2 Scheduler flow n Buffer management Shivkumar Kalyanaraman Rensselaer Polytechnic Institute 32
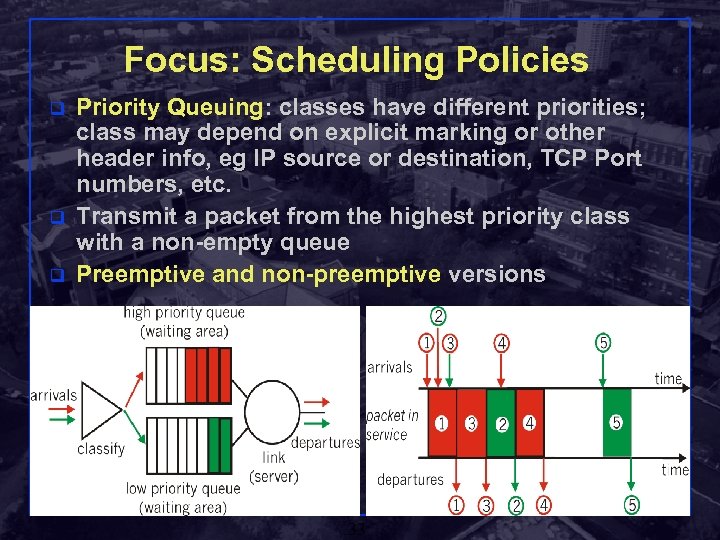
Focus: Scheduling Policies q q q Priority Queuing: classes have different priorities; class may depend on explicit marking or other header info, eg IP source or destination, TCP Port numbers, etc. Transmit a packet from the highest priority class with a non-empty queue Preemptive and non-preemptive versions Shivkumar Kalyanaraman Rensselaer Polytechnic Institute 33
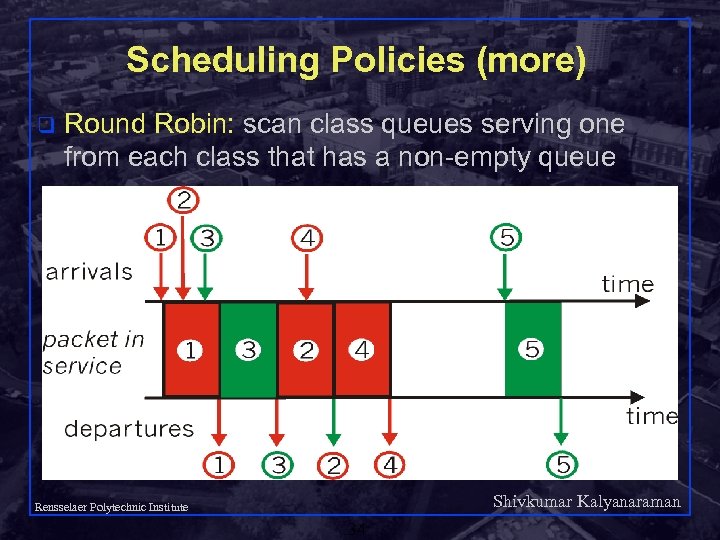
Scheduling Policies (more) q Round Robin: scan class queues serving one from each class that has a non-empty queue Shivkumar Kalyanaraman Rensselaer Polytechnic Institute 34

Round-Robin Discussion q Advantages: protection among flows q Misbehaving flows will not affect the performance of well-behaving flows q Misbehaving flow – a flow that does not implement any congestion control q FIFO does not have such a property q Disadvantages: q More complex than FIFO: per flow queue/state q Biased toward large packets – a flow receives service proportional to the number of packets Shivkumar Kalyanaraman Rensselaer Polytechnic Institute 35
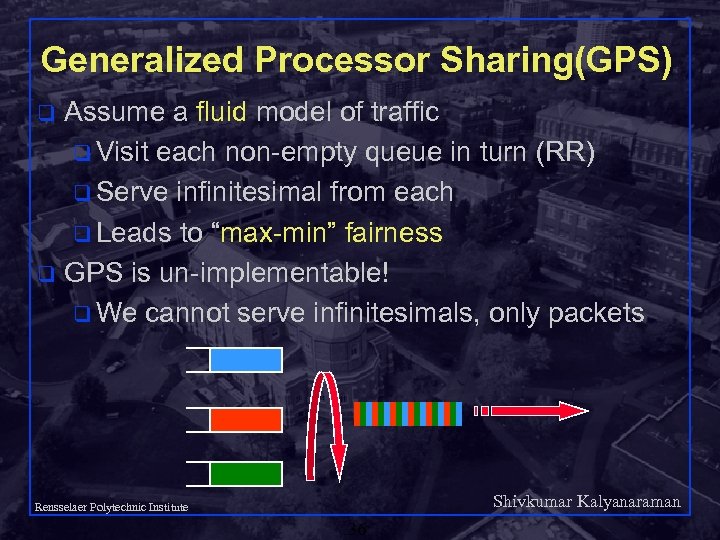
Generalized Processor Sharing(GPS) Assume a fluid model of traffic q Visit each non-empty queue in turn (RR) q Serve infinitesimal from each q Leads to “max-min” fairness q GPS is un-implementable! q We cannot serve infinitesimals, only packets q Shivkumar Kalyanaraman Rensselaer Polytechnic Institute 36
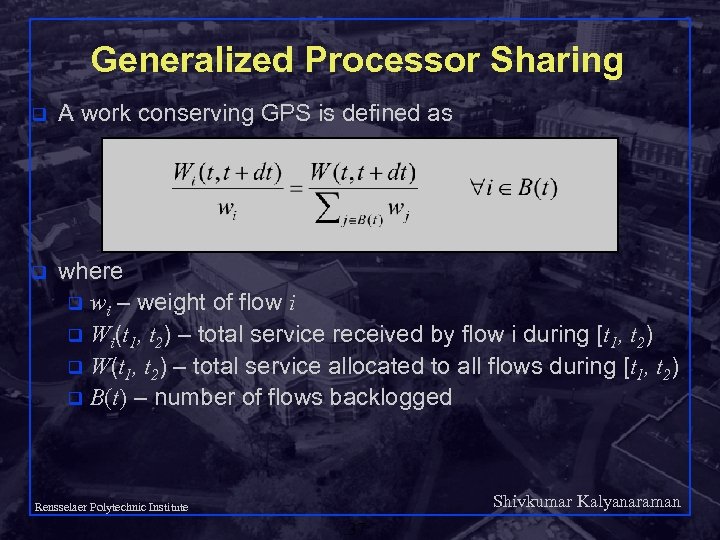
Generalized Processor Sharing q A work conserving GPS is defined as q where q wi – weight of flow i q Wi(t 1, t 2) – total service received by flow i during [t 1, t 2) q W(t 1, t 2) – total service allocated to all flows during [t 1, t 2) q B(t) – number of flows backlogged Shivkumar Kalyanaraman Rensselaer Polytechnic Institute 37
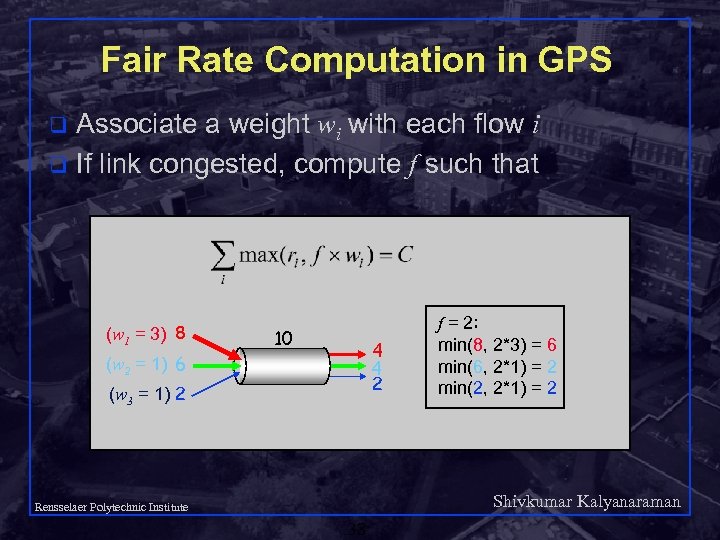
Fair Rate Computation in GPS Associate a weight wi with each flow i q If link congested, compute f such that q (w 1 = 3) 8 10 4 4 2 (w 2 = 1) 6 (w 3 = 1) 2 f = 2: min(8, 2*3) = 6 min(6, 2*1) = 2 min(2, 2*1) = 2 Shivkumar Kalyanaraman Rensselaer Polytechnic Institute 38
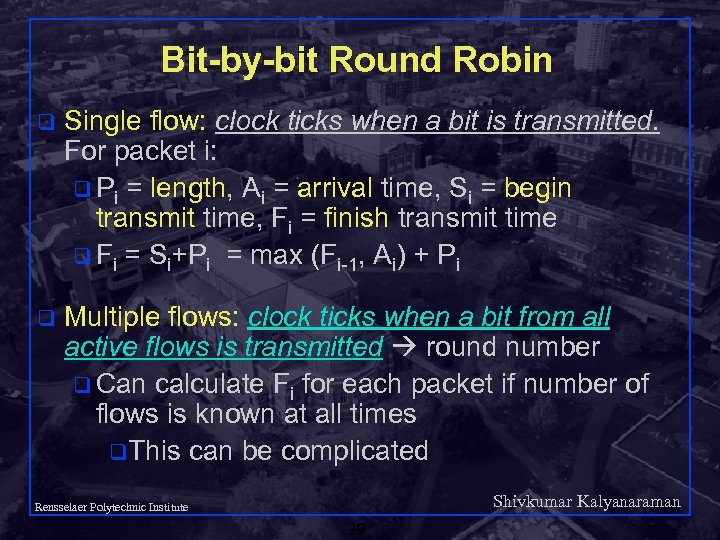
Bit-by-bit Round Robin q Single flow: clock ticks when a bit is transmitted. For packet i: q Pi = length, Ai = arrival time, Si = begin transmit time, Fi = finish transmit time q Fi = Si+Pi = max (Fi-1, Ai) + Pi q Multiple flows: clock ticks when a bit from all active flows is transmitted round number q Can calculate Fi for each packet if number of flows is known at all times q. This can be complicated Shivkumar Kalyanaraman Rensselaer Polytechnic Institute 39
Packet Approximation of Fluid System q q q Standard techniques of approximating fluid GPS q Select packet that finishes first in GPS assuming that there are no future arrivals Important properties of GPS q Finishing order of packets currently in system independent of future arrivals Implementation based on virtual time q Assign virtual finish time to each packet upon arrival q Packets served in increasing order of virtual times Shivkumar Kalyanaraman Rensselaer Polytechnic Institute 40
Fair Queuing (FQ) q q Idea: serve packets in the order in which they would have finished transmission in the fluid flow system Mapping bit-by-bit schedule onto packet transmission schedule Transmit packet with the lowest Fi at any given time Variation: Weighted Fair Queuing (WFQ) Shivkumar Kalyanaraman Rensselaer Polytechnic Institute 41
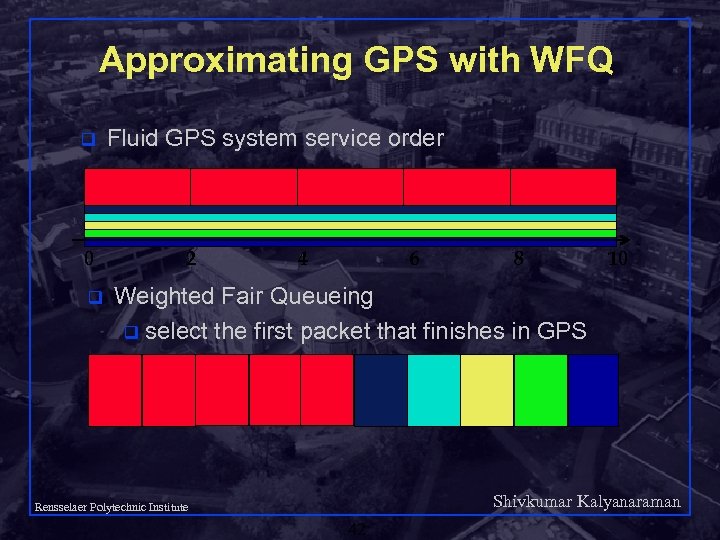
Approximating GPS with WFQ q 0 q Fluid GPS system service order 2 4 6 8 10 Weighted Fair Queueing q select the first packet that finishes in GPS Shivkumar Kalyanaraman Rensselaer Polytechnic Institute 42
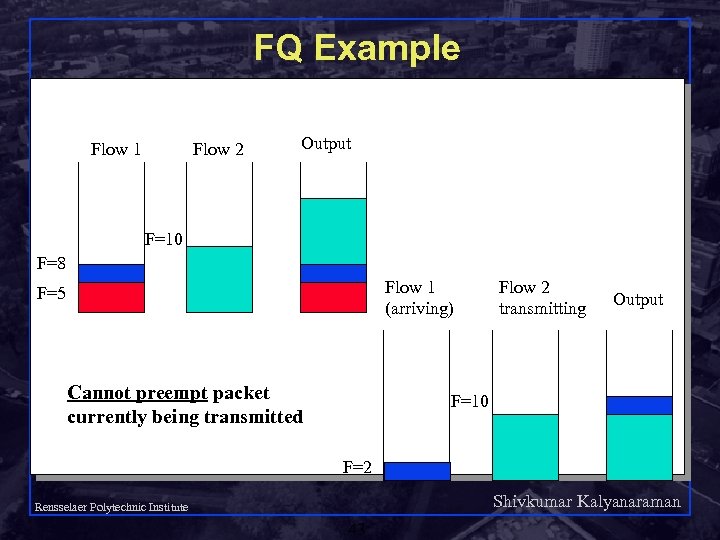
FQ Example Flow 1 Flow 2 Output F=10 F=8 Flow 1 (arriving) F=5 Cannot preempt packet currently being transmitted Flow 2 transmitting Output F=10 F=2 Shivkumar Kalyanaraman Rensselaer Polytechnic Institute 43
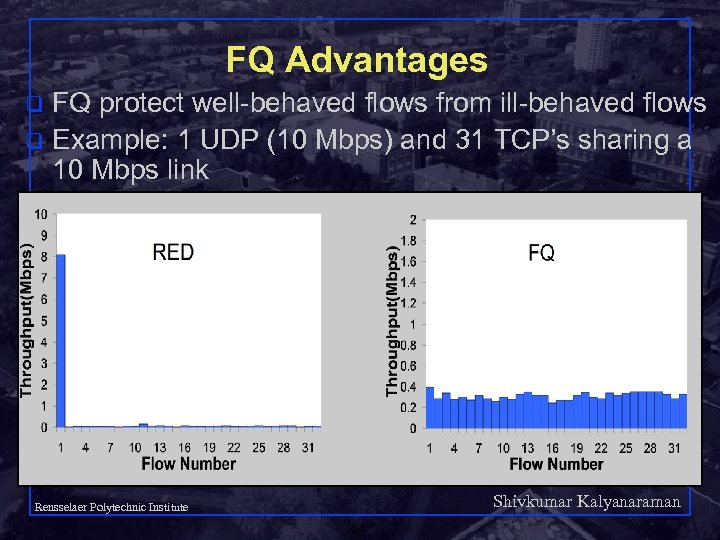
FQ Advantages FQ protect well-behaved flows from ill-behaved flows q Example: 1 UDP (10 Mbps) and 31 TCP’s sharing a 10 Mbps link q Shivkumar Kalyanaraman Rensselaer Polytechnic Institute 44
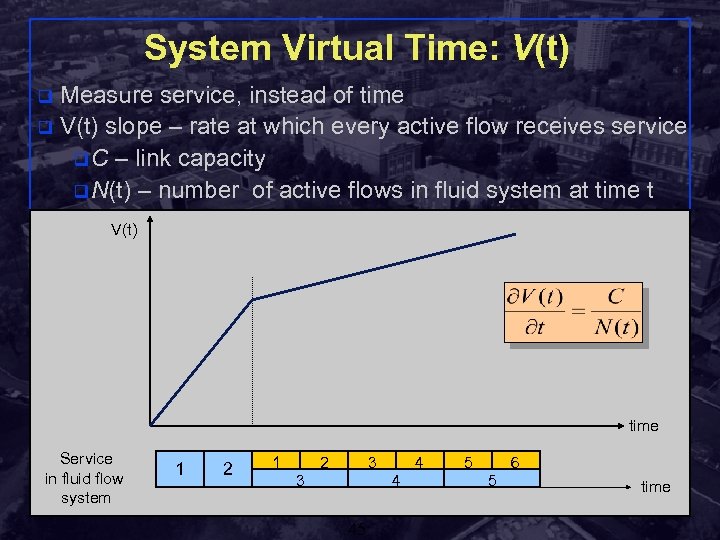
System Virtual Time: V(t) Measure service, instead of time q V(t) slope – rate at which every active flow receives service q C – link capacity q N(t) – number of active flows in fluid system at time t q V(t) time Service in fluid flow system 1 2 3 3 4 4 5 6 5 time Shivkumar Kalyanaraman Rensselaer Polytechnic Institute 45
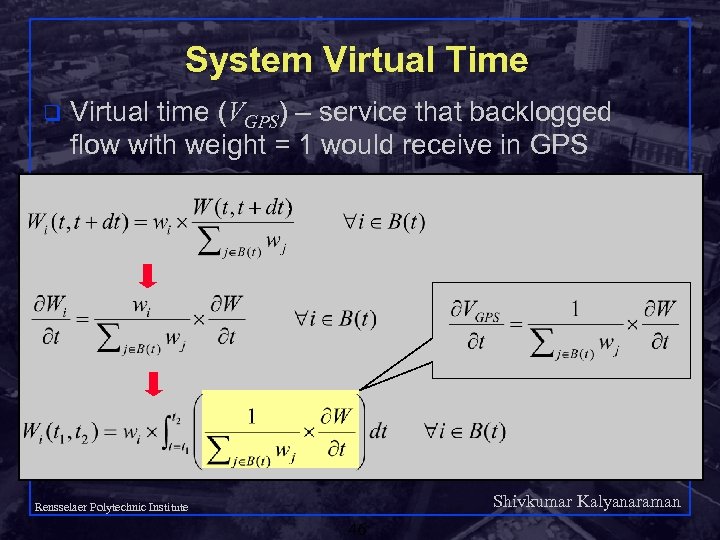
System Virtual Time q Virtual time (VGPS) – service that backlogged flow with weight = 1 would receive in GPS Shivkumar Kalyanaraman Rensselaer Polytechnic Institute 46
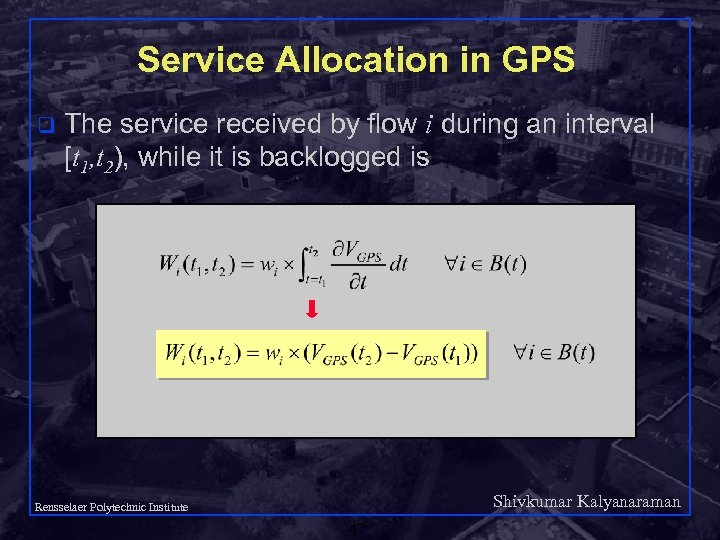
Service Allocation in GPS q The service received by flow i during an interval [t 1, t 2), while it is backlogged is Shivkumar Kalyanaraman Rensselaer Polytechnic Institute 47
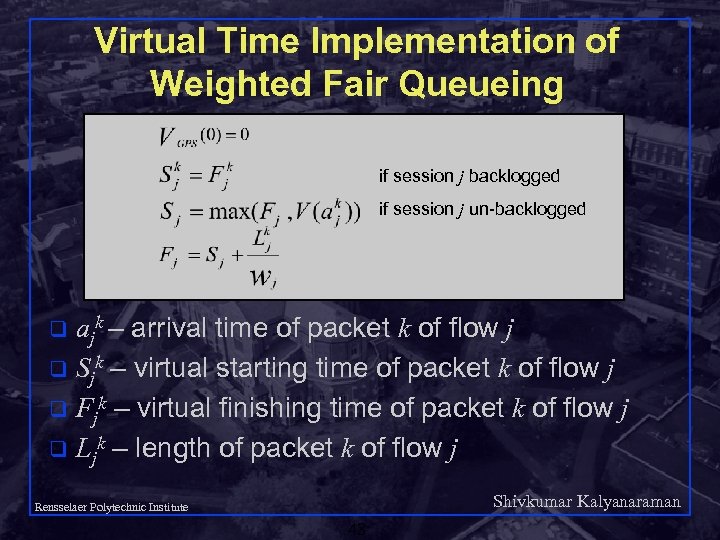
Virtual Time Implementation of Weighted Fair Queueing if session j backlogged if session j un-backlogged ajk – arrival time of packet k of flow j q Sjk – virtual starting time of packet k of flow j q Fjk – virtual finishing time of packet k of flow j q Ljk – length of packet k of flow j q Shivkumar Kalyanaraman Rensselaer Polytechnic Institute 48

Virtual Time Implementation of Weighted Fair Queueing Need to keep per flow instead of per packet virtual start, finish time only q System virtual time is used to reset a flow’s virtual start time when a flow becomes backlogged again after being idle q Shivkumar Kalyanaraman Rensselaer Polytechnic Institute 49
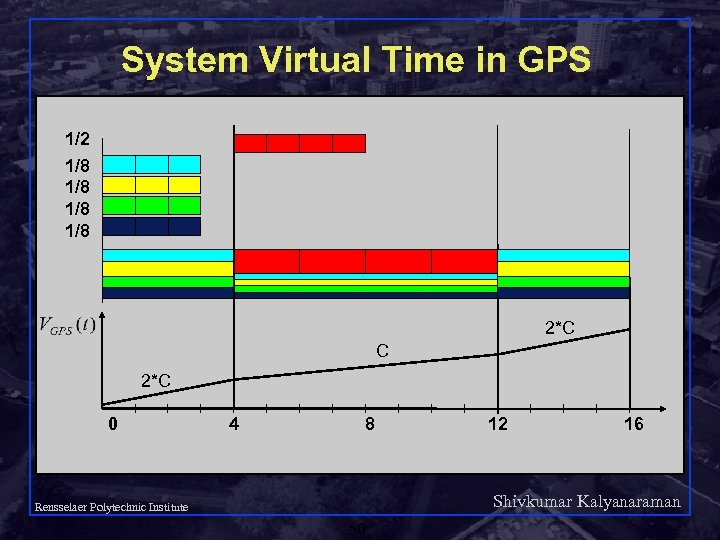
System Virtual Time in GPS 1/2 1/8 1/8 2*C C 2*C 0 4 8 12 16 Shivkumar Kalyanaraman Rensselaer Polytechnic Institute 50
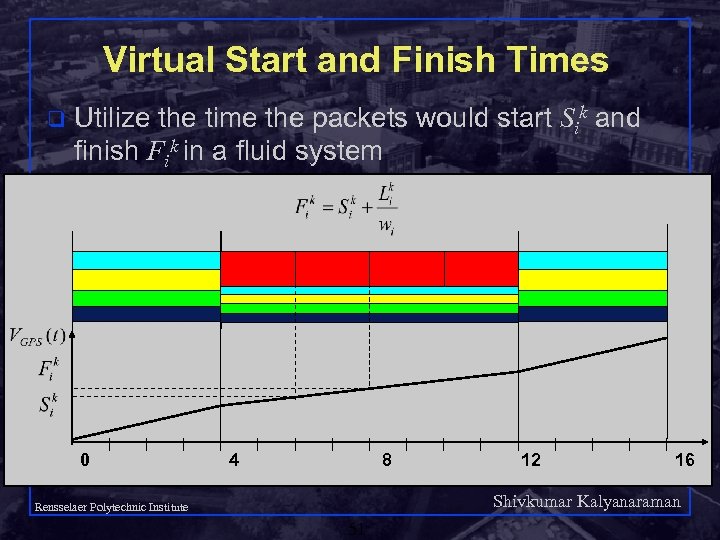
Virtual Start and Finish Times q Utilize the time the packets would start Sik and finish Fik in a fluid system 0 4 8 12 16 Shivkumar Kalyanaraman Rensselaer Polytechnic Institute 51

Big Picture FQ does not eliminate congestion it just manages the congestion q You need both end-host congestion control and router support for congestion control q end-host congestion control to adapt q router congestion control to protect/isolate q Don’t forget buffer management: you still need to drop in case of congestion. Which packet’s would you drop in FQ? q one possibility: packet from the longest queue q Shivkumar Kalyanaraman Rensselaer Polytechnic Institute 52

Qo. S ARCHITECTURES Shivkumar Kalyanaraman Rensselaer Polytechnic Institute 53
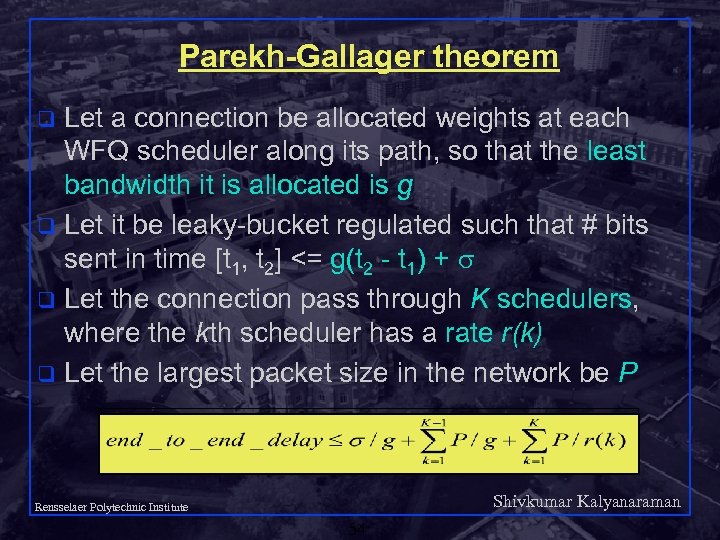
Parekh-Gallager theorem Let a connection be allocated weights at each WFQ scheduler along its path, so that the least bandwidth it is allocated is g q Let it be leaky-bucket regulated such that # bits sent in time [t 1, t 2] <= g(t 2 - t 1) + q Let the connection pass through K schedulers, where the kth scheduler has a rate r(k) q Let the largest packet size in the network be P q Shivkumar Kalyanaraman Rensselaer Polytechnic Institute 54
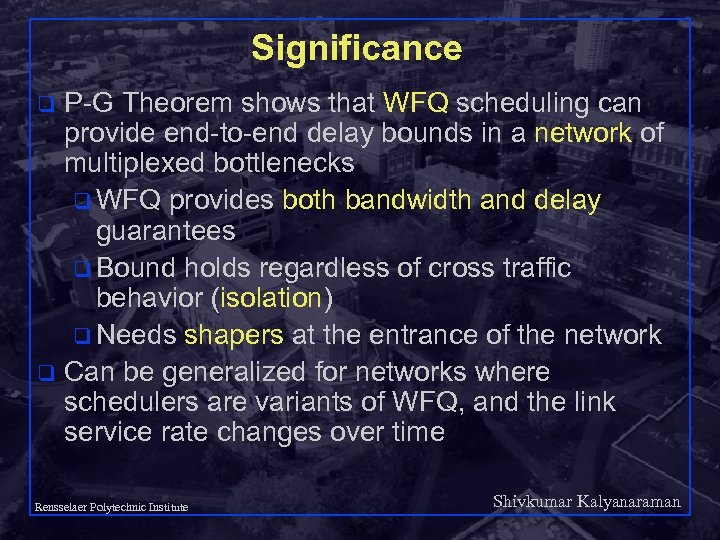
Significance P-G Theorem shows that WFQ scheduling can provide end-to-end delay bounds in a network of multiplexed bottlenecks q WFQ provides both bandwidth and delay guarantees q Bound holds regardless of cross traffic behavior (isolation) q Needs shapers at the entrance of the network q Can be generalized for networks where schedulers are variants of WFQ, and the link service rate changes over time q Shivkumar Kalyanaraman Rensselaer Polytechnic Institute 55
Stateless vs. Stateful Qo. S Solutions q q Stateless solutions – routers maintain no fine grained state about traffic £ scalable, robust ¤ weak services Stateful solutions – routers maintain per-flow state £ powerful services q guaranteed services + high resource utilization q fine grained differentiation q protection ¤ much less scalable and robust Shivkumar Kalyanaraman Rensselaer Polytechnic Institute 56
![Existing Solutions Stateful Stateless Tenet [Ferrari & q Diff. Serv Verma ’ 89] Qo. Existing Solutions Stateful Stateless Tenet [Ferrari & q Diff. Serv Verma ’ 89] Qo.](https://present5.com/presentation/ac7c23e613a7c457cd1ac4561200a9c8/image-57.jpg)
Existing Solutions Stateful Stateless Tenet [Ferrari & q Diff. Serv Verma ’ 89] Qo. S - [Clark & q Int. Serv [Clark et al Wroclawski ‘ 97] ’ 91] - [Nichols et al ’ 97] q ATM [late ’ 80 s] q Round Robin q Dec. Bit [Ramkrishnan & [Nagle ’ 85] Jain ’ 88] Network support for q Fair Queueing q Random Early Detection congestion [Demers et al ’ 89] (RED) [Floyd & Jacobson control q Flow Random Early ’ 93] Drop (FRED) [Lin & q BLUE [Feng et al ’ 99] Morris ’ 97] q REMShivkumar Kalyanaraman [Low at al ’ 00] Rensselaer Polytechnic Institute q 57
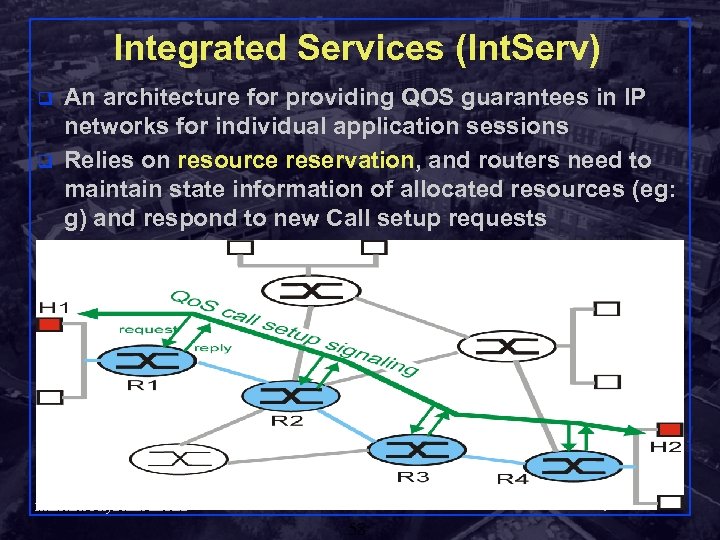
Integrated Services (Int. Serv) q q An architecture for providing QOS guarantees in IP networks for individual application sessions Relies on resource reservation, and routers need to maintain state information of allocated resources (eg: g) and respond to new Call setup requests Shivkumar Kalyanaraman Rensselaer Polytechnic Institute 58
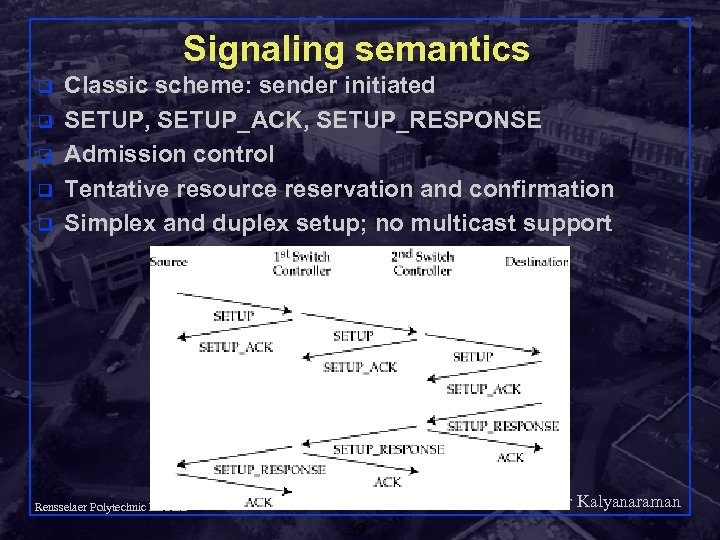
Signaling semantics q q q Classic scheme: sender initiated SETUP, SETUP_ACK, SETUP_RESPONSE Admission control Tentative resource reservation and confirmation Simplex and duplex setup; no multicast support Shivkumar Kalyanaraman Rensselaer Polytechnic Institute 59

RSVP: Internet Signaling Creates and maintains distributed reservation state q De-coupled from routing: q Multicast trees setup by routing protocols, not RSVP (unlike ATM or telephony signaling) q Receiver-initiated: scales for multicast q Soft-state: reservation times out unless refreshed q Latest paths discovered through “PATH” messages (forward direction) and used by RESV mesgs (reverse direction). q Shivkumar Kalyanaraman Rensselaer Polytechnic Institute 60

Call Admission Session must first declare its QOS requirement and characterize the traffic it will send through the network q R-spec: defines the QOS being requested q T-spec: defines the traffic characteristics q A signaling protocol is needed to carry the Rspec and T-spec to the routers where reservation is required; RSVP is a leading candidate for such signaling protocol q Shivkumar Kalyanaraman Rensselaer Polytechnic Institute 61

Call Admission q Call Admission: routers will admit calls based on their R-spec and T-spec and base on the current resource allocated at the routers to other calls. Shivkumar Kalyanaraman Rensselaer Polytechnic Institute 62
Stateful Solution: Guaranteed Services q Achieve per-flow bandwidth and delay guarantees q Example: guarantee 1 MBps and < 100 ms delay to a flow Receiver Sender Shivkumar Kalyanaraman Rensselaer Polytechnic Institute 63
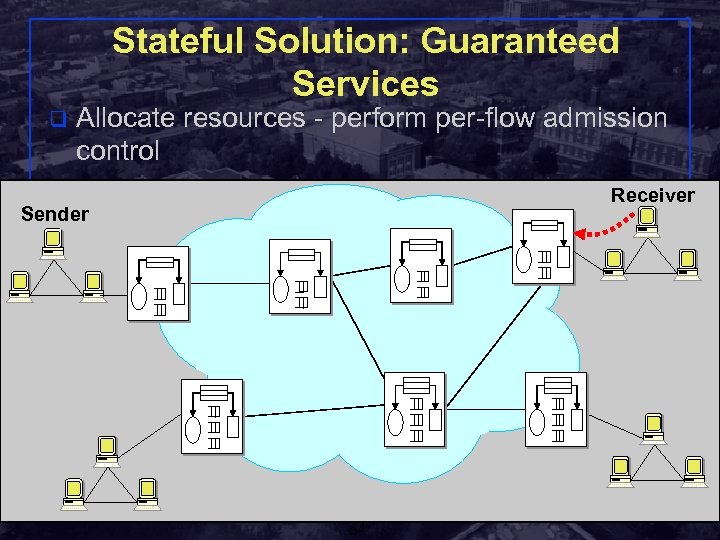
Stateful Solution: Guaranteed Services q Allocate resources - perform per-flow admission control Receiver Sender Shivkumar Kalyanaraman Rensselaer Polytechnic Institute 64
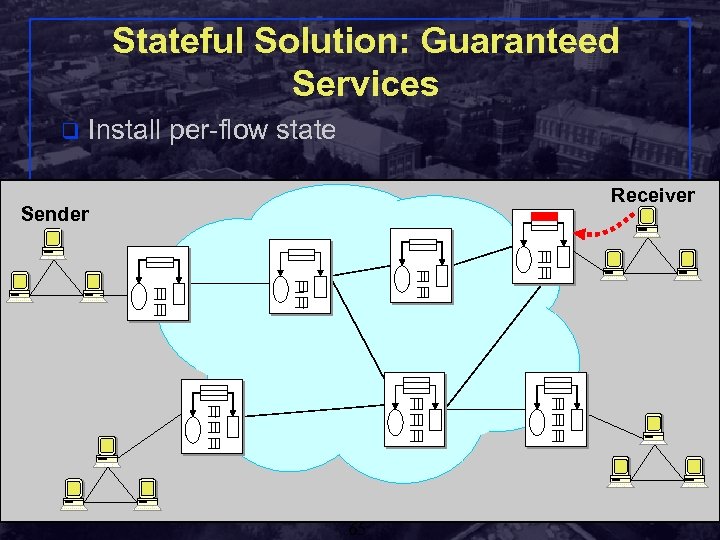
Stateful Solution: Guaranteed Services q Install per-flow state Receiver Sender Shivkumar Kalyanaraman Rensselaer Polytechnic Institute 65
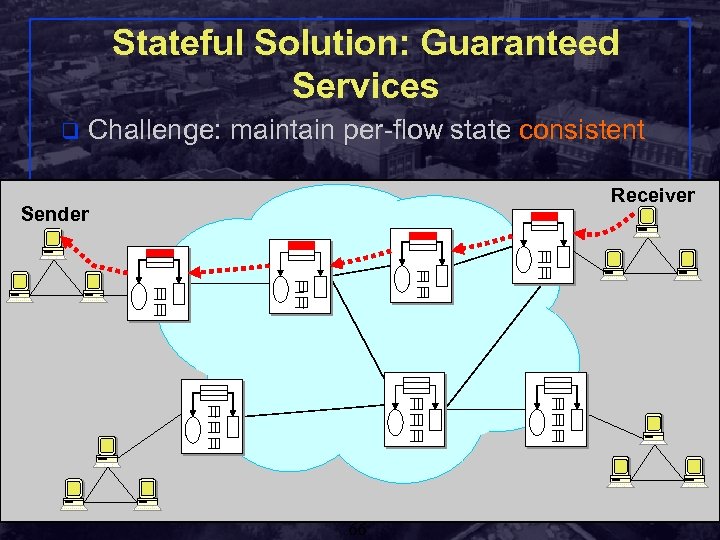
Stateful Solution: Guaranteed Services q Challenge: maintain per-flow state consistent Receiver Sender Shivkumar Kalyanaraman Rensselaer Polytechnic Institute 66
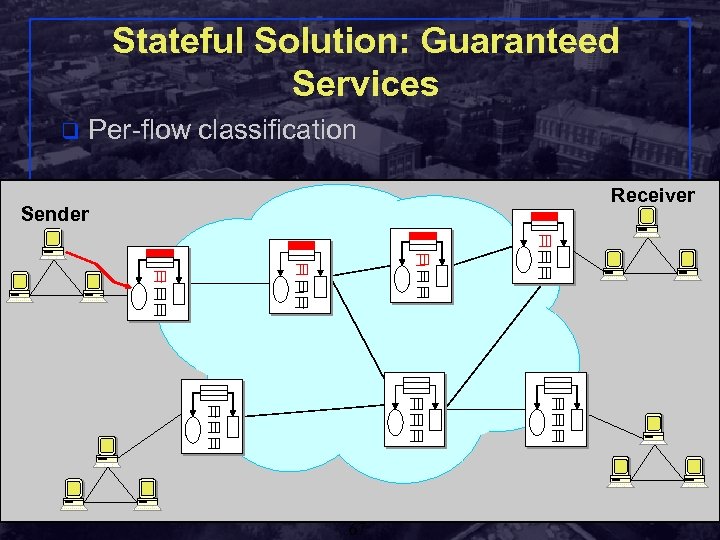
Stateful Solution: Guaranteed Services q Per-flow classification Receiver Sender Shivkumar Kalyanaraman Rensselaer Polytechnic Institute 67
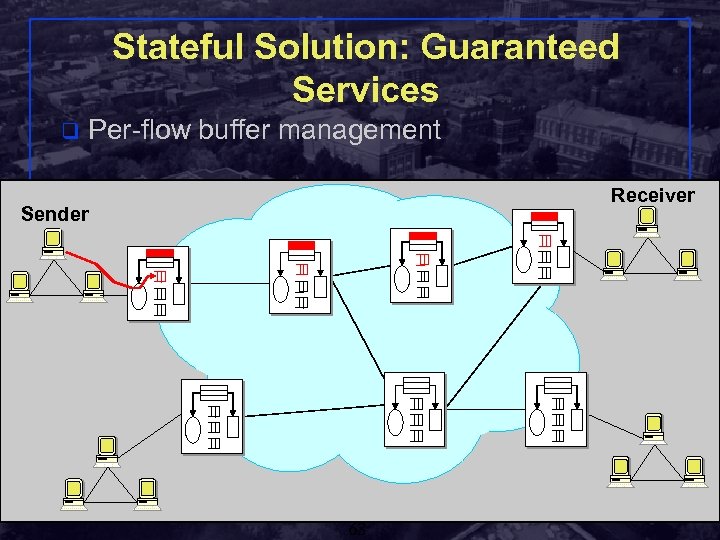
Stateful Solution: Guaranteed Services q Per-flow buffer management Receiver Sender Shivkumar Kalyanaraman Rensselaer Polytechnic Institute 68
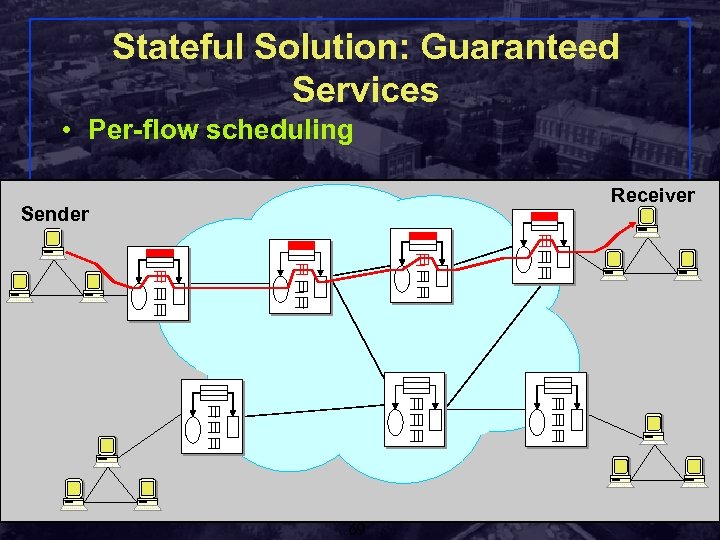
Stateful Solution: Guaranteed Services • Per-flow scheduling Receiver Sender Shivkumar Kalyanaraman Rensselaer Polytechnic Institute 69
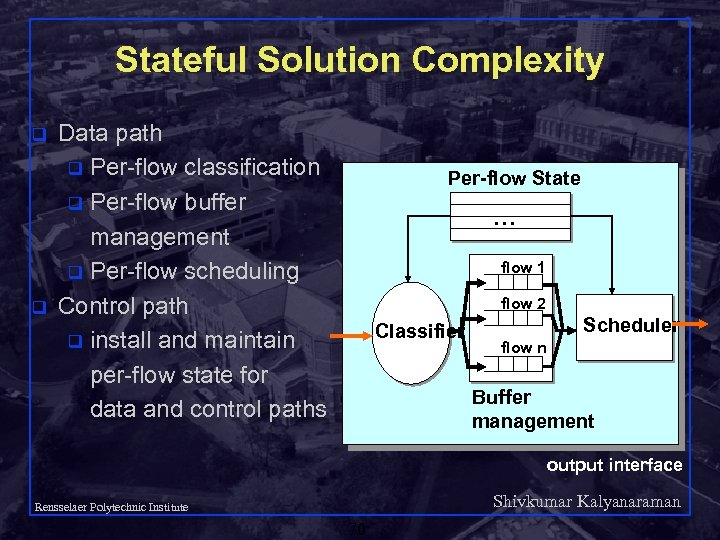
Stateful Solution Complexity q q Data path q Per-flow classification q Per-flow buffer management q Per-flow scheduling Control path q install and maintain per-flow state for data and control paths Per-flow State … flow 1 flow 2 Classifier Scheduler flow n Buffer management output interface Shivkumar Kalyanaraman Rensselaer Polytechnic Institute 70

Stateless vs. Stateful Stateless solutions are more q scalable q robust q Stateful solutions provide more powerful and flexible services q guaranteed services + high resource utilization q fine grained differentiation q protection q Shivkumar Kalyanaraman Rensselaer Polytechnic Institute 71

Question q Can we achieve the best of two worlds, i. e. , provide services implemented by stateful networks while maintaining advantages of stateless architectures? q Yes, in some interesting cases. DPS, CSFQ. q Can we provide reduced state services, I. e. , maintain state only for larger granular flows rather than end-to-end flows? q Yes: Diff-serv Shivkumar Kalyanaraman Rensselaer Polytechnic Institute 72
Differentiated Services (Diff. Serv) q q Intended to address the following difficulties with Intserv and RSVP; Scalability: maintaining states by routers in high speed networks is difficult sue to the very large number of flows Flexible Service Models: Intserv has only two classes, want to provide more qualitative service classes; want to provide ‘relative’ service distinction (Platinum, Gold, Silver, …) Simpler signaling: (than RSVP) many applications and users may only w ant to specify a more qualitative notion of service Shivkumar Kalyanaraman Rensselaer Polytechnic Institute 73
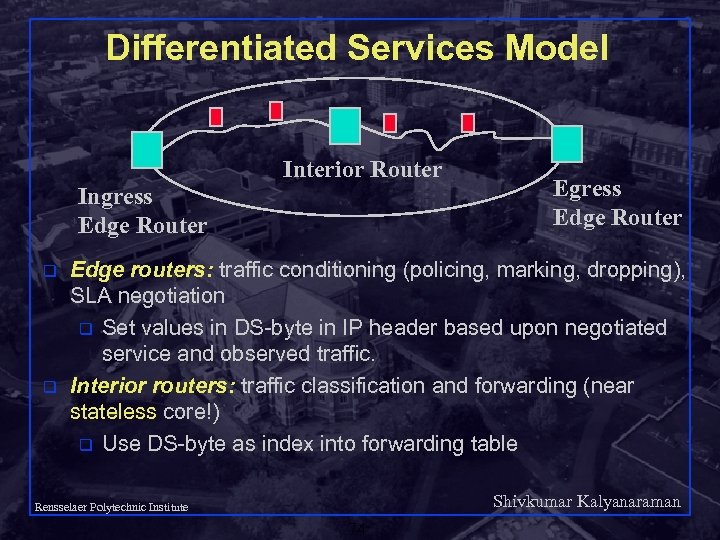
Differentiated Services Model Interior Router Ingress Edge Router q q Egress Edge Router Edge routers: traffic conditioning (policing, marking, dropping), SLA negotiation q Set values in DS-byte in IP header based upon negotiated service and observed traffic. Interior routers: traffic classification and forwarding (near stateless core!) q Use DS-byte as index into forwarding table Shivkumar Kalyanaraman Rensselaer Polytechnic Institute 74
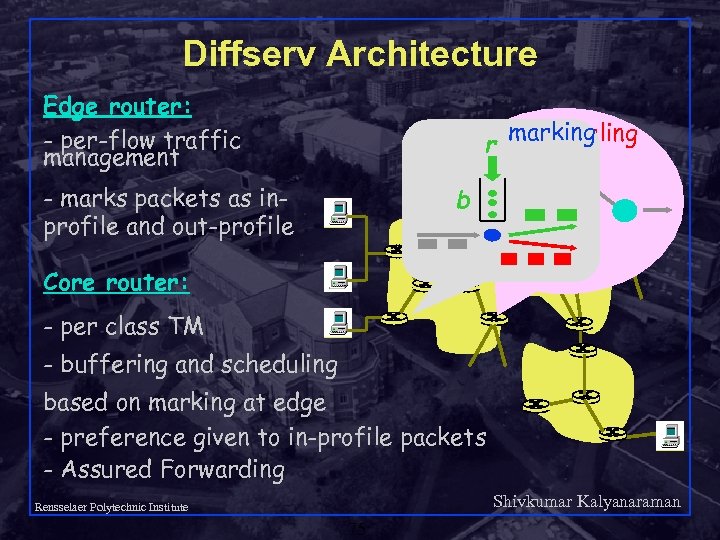
Diffserv Architecture Edge router: - per-flow traffic management scheduling r marking - marks packets as inprofile and out-profile b . . . Core router: - per class TM - buffering and scheduling based on marking at edge - preference given to in-profile packets - Assured Forwarding Shivkumar Kalyanaraman Rensselaer Polytechnic Institute 75
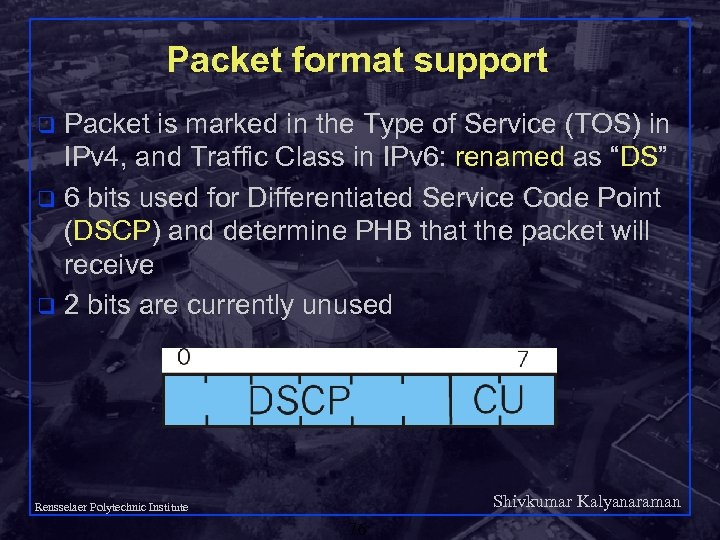
Packet format support Packet is marked in the Type of Service (TOS) in IPv 4, and Traffic Class in IPv 6: renamed as “DS” q 6 bits used for Differentiated Service Code Point (DSCP) and determine PHB that the packet will receive q 2 bits are currently unused q Shivkumar Kalyanaraman Rensselaer Polytechnic Institute 76
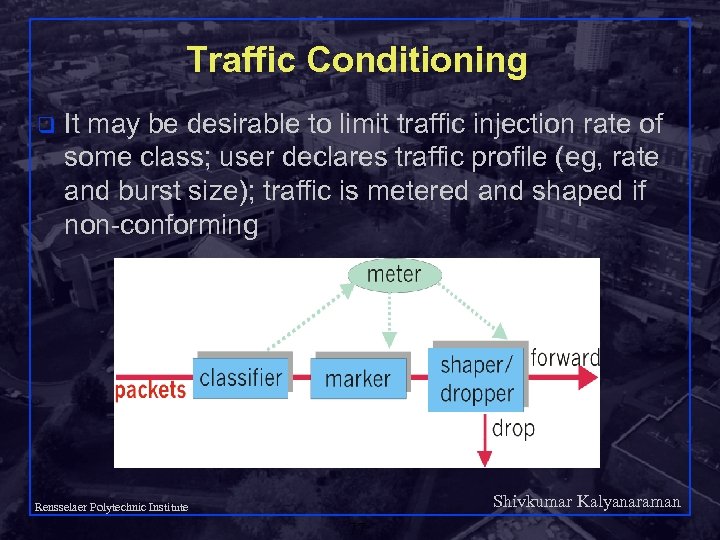
Traffic Conditioning q It may be desirable to limit traffic injection rate of some class; user declares traffic profile (eg, rate and burst size); traffic is metered and shaped if non-conforming Shivkumar Kalyanaraman Rensselaer Polytechnic Institute 77

Per-hop Behavior (PHB) q PHB: name for interior router data-plane functions q Includes scheduling, buff. mgmt, shaping etc q Logical spec: PHB does not specify mechanisms to use to ensure performance behavior q Examples: q Class A gets x% of outgoing link bandwidth over time intervals of a specified length q Class A packets leave first before packets from class B Shivkumar Kalyanaraman Rensselaer Polytechnic Institute 78
PHB (contd) q PHBs under consideration: q Expedited Forwarding: departure rate of packets from a class equals or exceeds a specified rate (logical link with a minimum guaranteed rate) q. Emulates leased-line behavior q Assured Forwarding: 4 classes, each guaranteed a minimum amount of bandwidth and buffering; each with three drop preference partitions q Emulates frame-relay behavior Shivkumar Kalyanaraman Rensselaer Polytechnic Institute 79

Question q Can we achieve the best of two worlds, i. e. , provide services implemented by stateful networks while maintaining advantages of stateless architectures? q Yes, in some interesting cases. DPS, CSFQ. q Can we provide reduced state services, I. e. , maintain state only for larger granular flows rather than end-to-end flows? q Yes: Diff-serv Shivkumar Kalyanaraman Rensselaer Polytechnic Institute 80
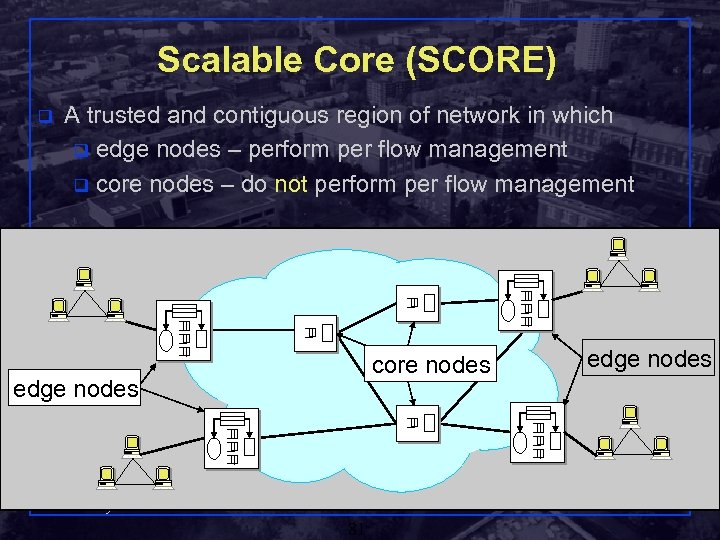
Scalable Core (SCORE) q A trusted and contiguous region of network in which q edge nodes – perform per flow management q core nodes – do not perform per flow management core nodes edge nodes Shivkumar Kalyanaraman Rensselaer Polytechnic Institute 81
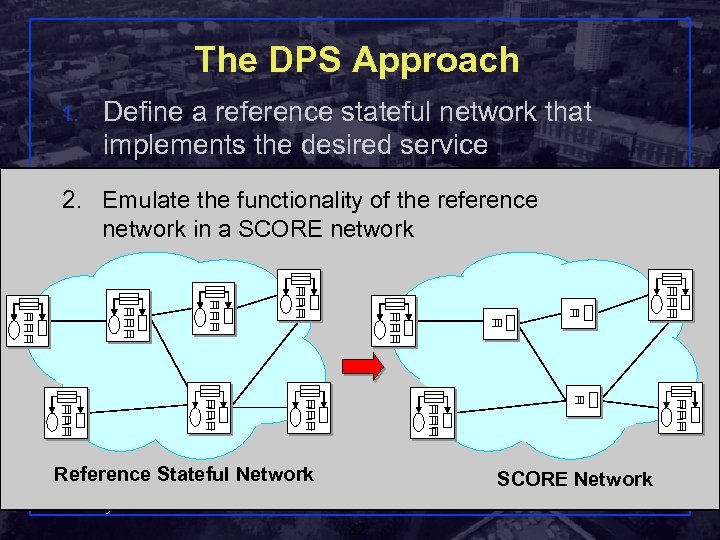
The DPS Approach 1. Define a reference stateful network that implements the desired service 2. Emulate the functionality of the reference network in a SCORE network Reference Stateful Network SCORE Network Shivkumar Kalyanaraman Rensselaer Polytechnic Institute 82
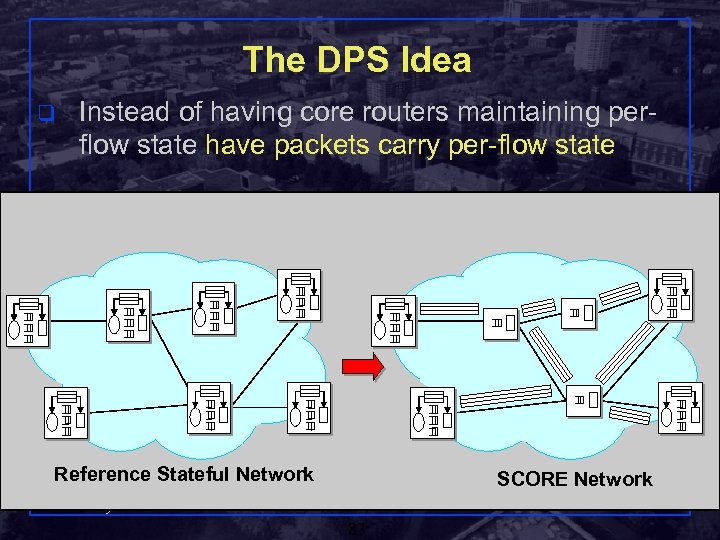
The DPS Idea q Instead of having core routers maintaining perflow state have packets carry per-flow state Reference Stateful Network SCORE Network Shivkumar Kalyanaraman Rensselaer Polytechnic Institute 83
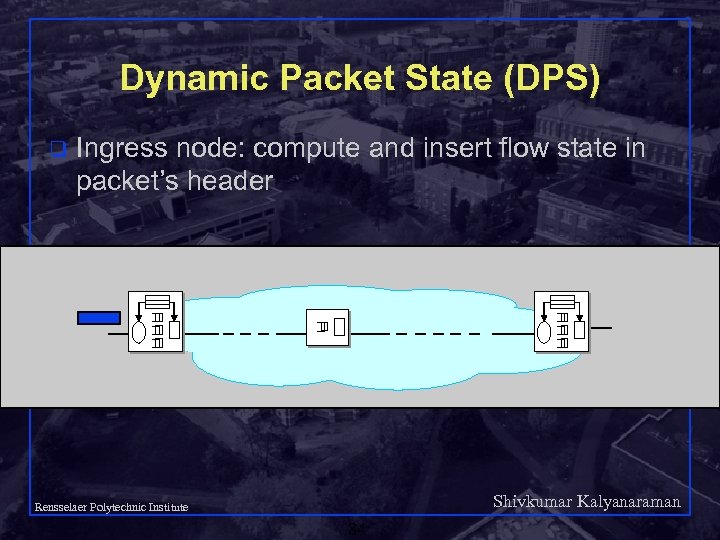
Dynamic Packet State (DPS) q Ingress node: compute and insert flow state in packet’s header Shivkumar Kalyanaraman Rensselaer Polytechnic Institute 84
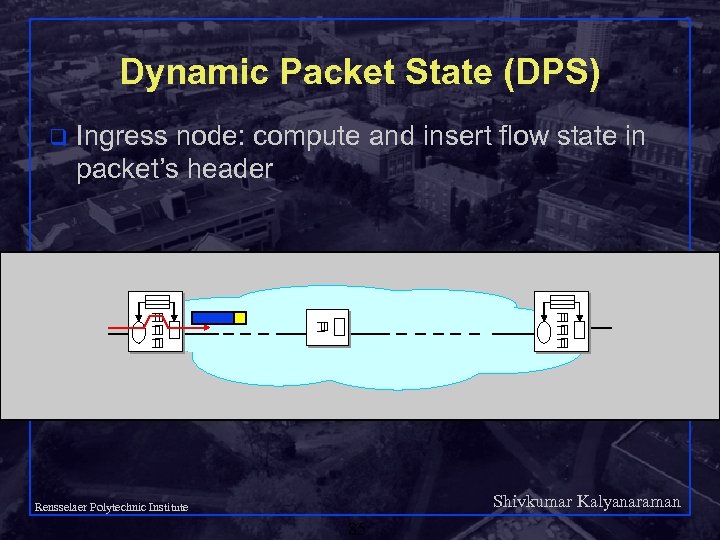
Dynamic Packet State (DPS) q Ingress node: compute and insert flow state in packet’s header Shivkumar Kalyanaraman Rensselaer Polytechnic Institute 85
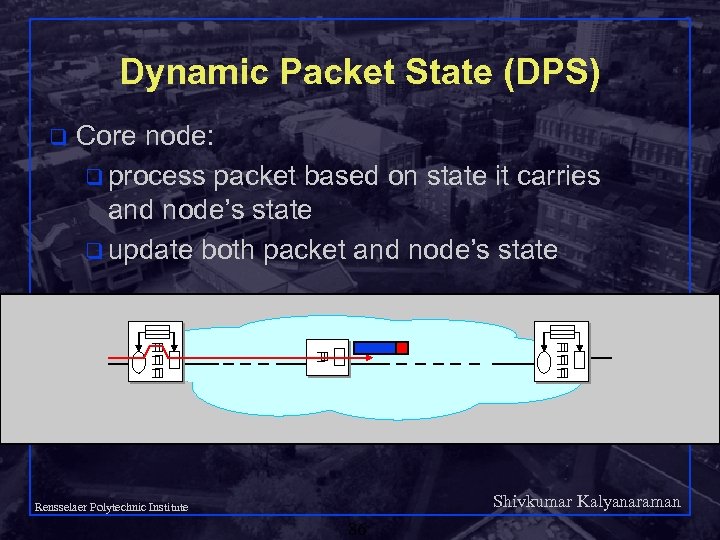
Dynamic Packet State (DPS) q Core node: q process packet based on state it carries and node’s state q update both packet and node’s state Shivkumar Kalyanaraman Rensselaer Polytechnic Institute 86
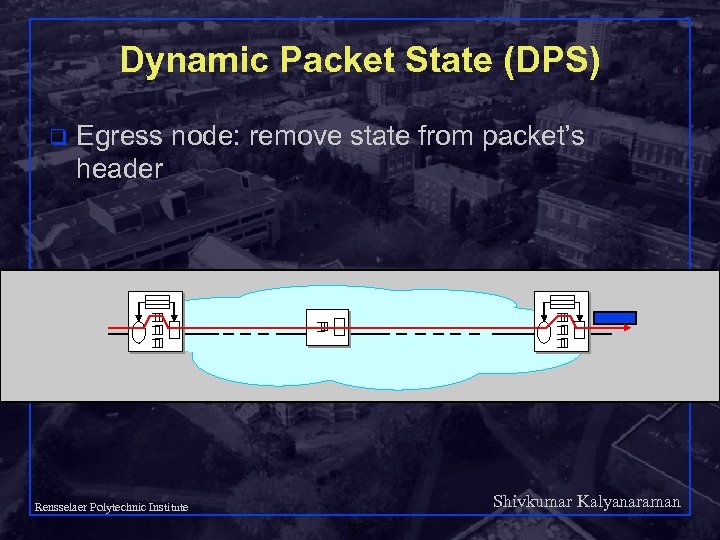
Dynamic Packet State (DPS) q Egress node: remove state from packet’s header Shivkumar Kalyanaraman Rensselaer Polytechnic Institute 87
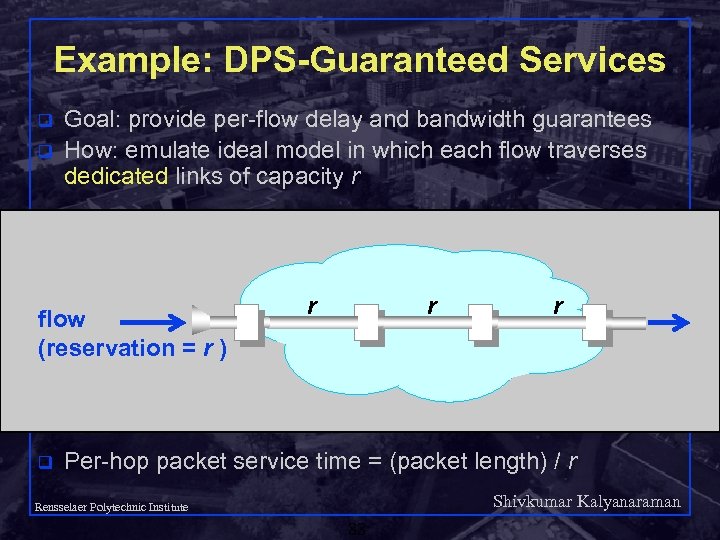
Example: DPS-Guaranteed Services q q Goal: provide per-flow delay and bandwidth guarantees How: emulate ideal model in which each flow traverses dedicated links of capacity r flow (reservation = r ) q r r r Per-hop packet service time = (packet length) / r Shivkumar Kalyanaraman Rensselaer Polytechnic Institute 88
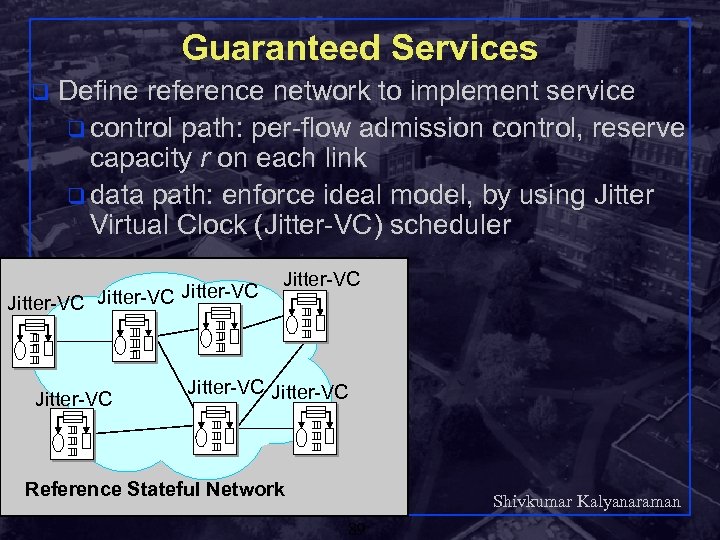
Guaranteed Services q Define reference network to implement service q control path: per-flow admission control, reserve capacity r on each link q data path: enforce ideal model, by using Jitter Virtual Clock (Jitter-VC) scheduler Jitter-VC Jitter-VC Reference Stateful Network Shivkumar Kalyanaraman Rensselaer Polytechnic Institute 89
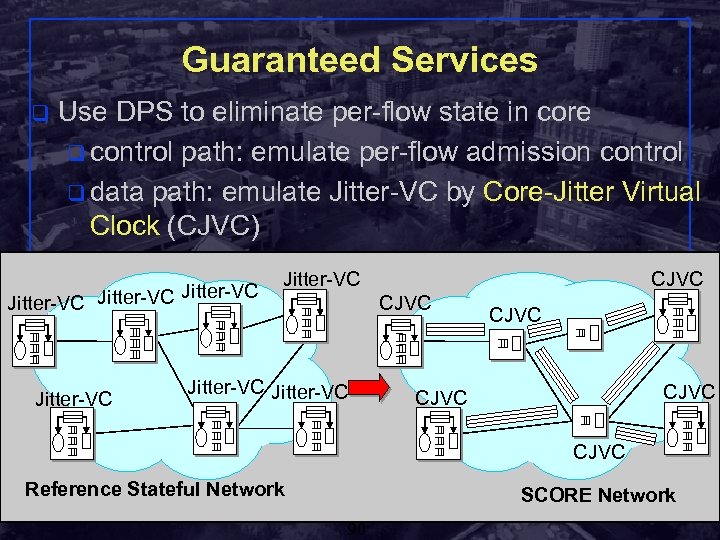
Guaranteed Services q Use DPS to eliminate per-flow state in core q control path: emulate per-flow admission control q data path: emulate Jitter-VC by Core-Jitter Virtual Clock (CJVC) Jitter-VC Jitter-VC CJVC CJVC Reference Stateful Network SCORE Network Shivkumar Kalyanaraman Rensselaer Polytechnic Institute 90
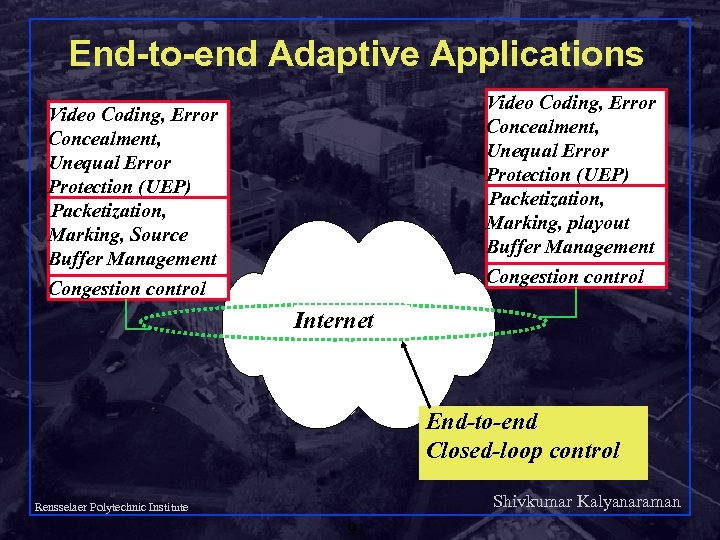
End-to-end Adaptive Applications Video Coding, Error Concealment, Unequal Error Protection (UEP) Packetization, Marking, playout Buffer Management Video Coding, Error Concealment, Unequal Error Protection (UEP) Packetization, Marking, Source Buffer Management Congestion control Internet End-to-end Closed-loop control Shivkumar Kalyanaraman Rensselaer Polytechnic Institute 91
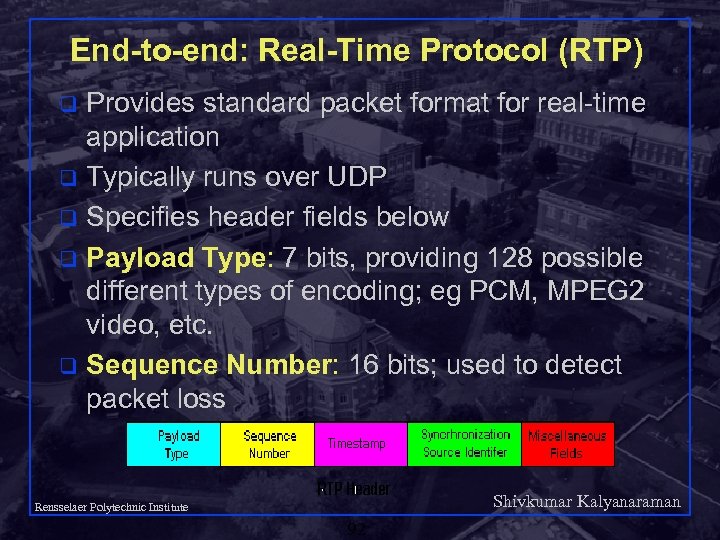
End-to-end: Real-Time Protocol (RTP) Provides standard packet format for real-time application q Typically runs over UDP q Specifies header fields below q Payload Type: 7 bits, providing 128 possible different types of encoding; eg PCM, MPEG 2 video, etc. q Sequence Number: 16 bits; used to detect packet loss q Shivkumar Kalyanaraman Rensselaer Polytechnic Institute 92
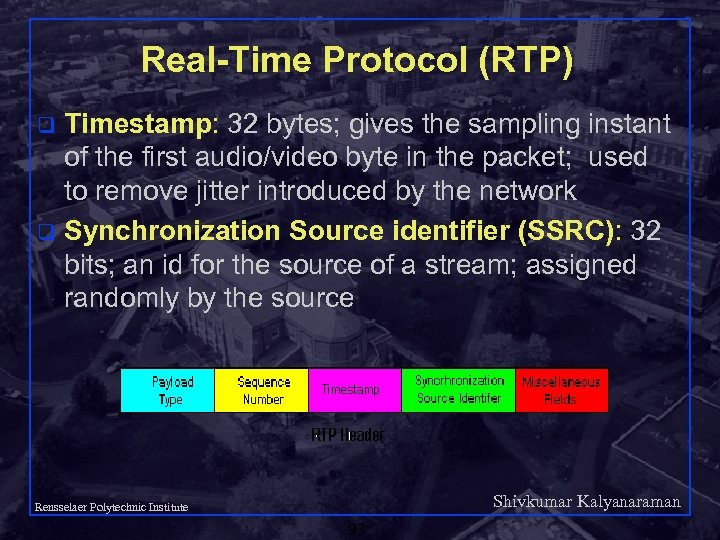
Real-Time Protocol (RTP) Timestamp: 32 bytes; gives the sampling instant of the first audio/video byte in the packet; used to remove jitter introduced by the network q Synchronization Source identifier (SSRC): 32 bits; an id for the source of a stream; assigned randomly by the source q Shivkumar Kalyanaraman Rensselaer Polytechnic Institute 93
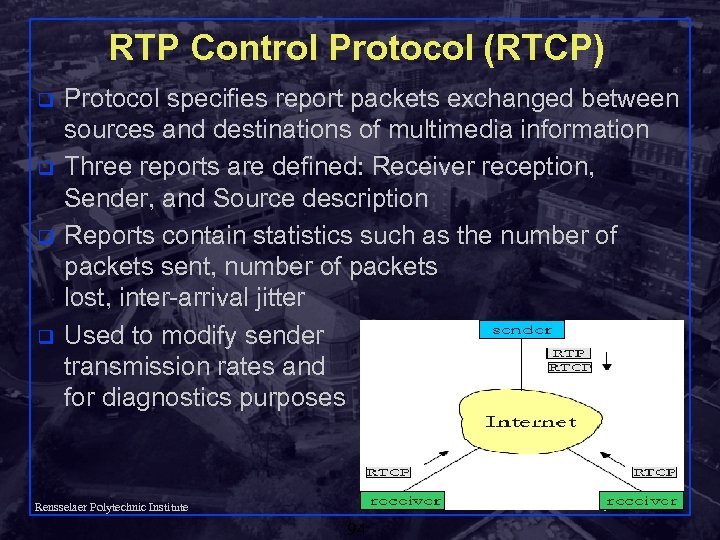
RTP Control Protocol (RTCP) q q Protocol specifies report packets exchanged between sources and destinations of multimedia information Three reports are defined: Receiver reception, Sender, and Source description Reports contain statistics such as the number of packets sent, number of packets lost, inter-arrival jitter Used to modify sender transmission rates and for diagnostics purposes Shivkumar Kalyanaraman Rensselaer Polytechnic Institute 94
Eg: Streaming & RTSP User interactive control is provided, e. g. the public protocol Real Time Streaming Protocol (RTSP) q Helper Application: displays content, which is typically requested via a Web browser; e. g. Real. Player; typical functions: q Decompression q Jitter removal q Error correction: use redundant packets to be used for reconstruction of original stream q GUI for user control q Shivkumar Kalyanaraman Rensselaer Polytechnic Institute 95
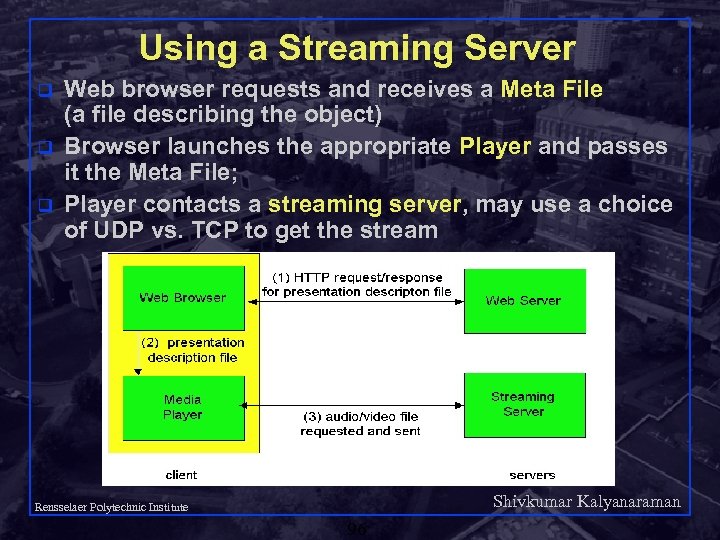
Using a Streaming Server q q q Web browser requests and receives a Meta File (a file describing the object) Browser launches the appropriate Player and passes it the Meta File; Player contacts a streaming server, may use a choice of UDP vs. TCP to get the stream Shivkumar Kalyanaraman Rensselaer Polytechnic Institute 96
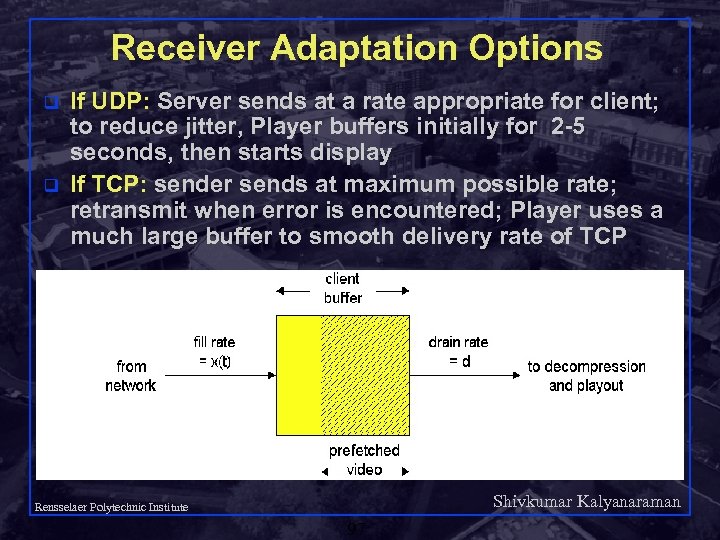
Receiver Adaptation Options q q If UDP: Server sends at a rate appropriate for client; to reduce jitter, Player buffers initially for 2 -5 seconds, then starts display If TCP: sender sends at maximum possible rate; retransmit when error is encountered; Player uses a much large buffer to smooth delivery rate of TCP Shivkumar Kalyanaraman Rensselaer Polytechnic Institute 97

H. 323 is an ITU standard for multimedia communications over best-effort LANs. q Part of larger set of standards (H. 32 X) for videoconferencing over data networks. q H. 323 includes both stand-alone devices and embedded personal computer technology as well as point-to-point and multipoint conferences. q H. 323 addresses call control, multimedia management, and bandwidth management as well as interfaces between LANs and other networks. q Shivkumar Kalyanaraman Rensselaer Polytechnic Institute 98
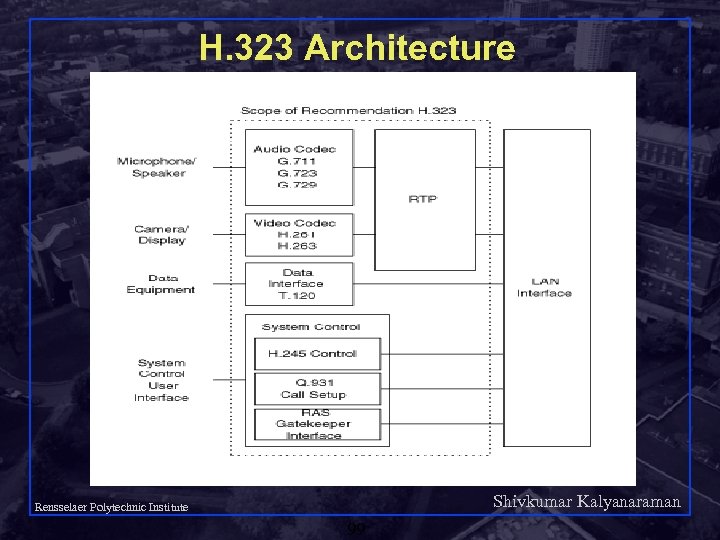
H. 323 Architecture Shivkumar Kalyanaraman Rensselaer Polytechnic Institute 99
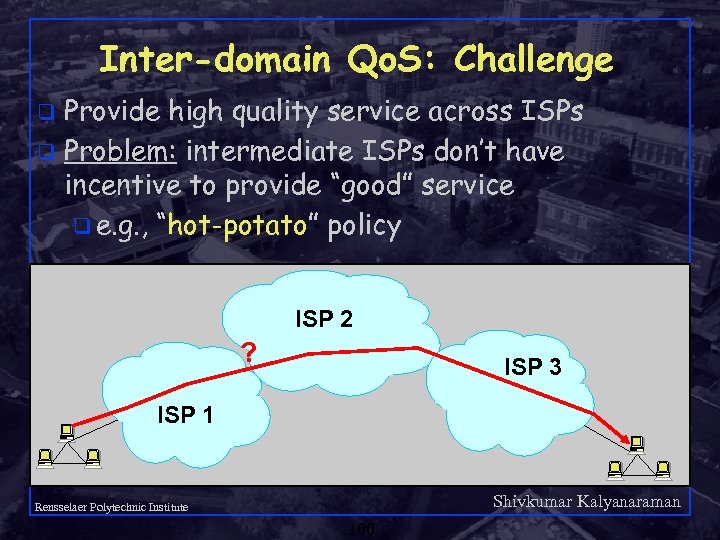
Inter-domain Qo. S: Challenge Provide high quality service across ISPs q Problem: intermediate ISPs don’t have incentive to provide “good” service q e. g. , “hot-potato” policy q ISP 2 ? ISP 3 ISP 1 Shivkumar Kalyanaraman Rensselaer Polytechnic Institute 100
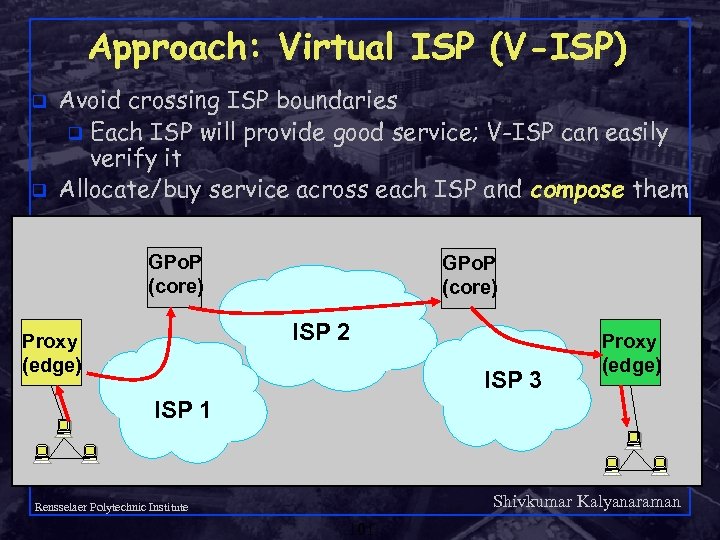
Approach: Virtual ISP (V-ISP) q q Avoid crossing ISP boundaries q Each ISP will provide good service; V-ISP can easily verify it Allocate/buy service across each ISP and compose them GPo. P (core) ISP 2 Proxy (edge) ISP 3 Proxy (edge) ISP 1 Shivkumar Kalyanaraman Rensselaer Polytechnic Institute 101
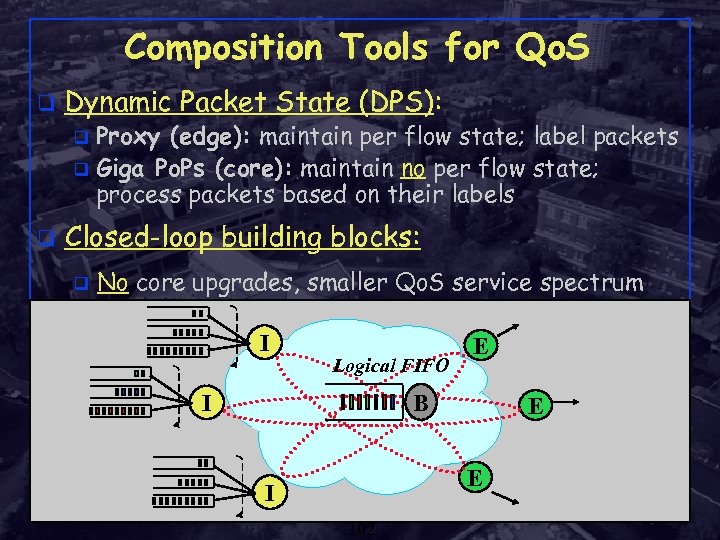
Composition Tools for Qo. S q Dynamic Packet State (DPS): Proxy (edge): maintain per flow state; label packets q Giga Po. Ps (core): maintain no per flow state; process packets based on their labels q q Closed-loop building blocks: q No core upgrades, smaller Qo. S service spectrum I Logical FIFO B I Rensselaer Polytechnic Institute E E E I 102 Shivkumar Kalyanaraman
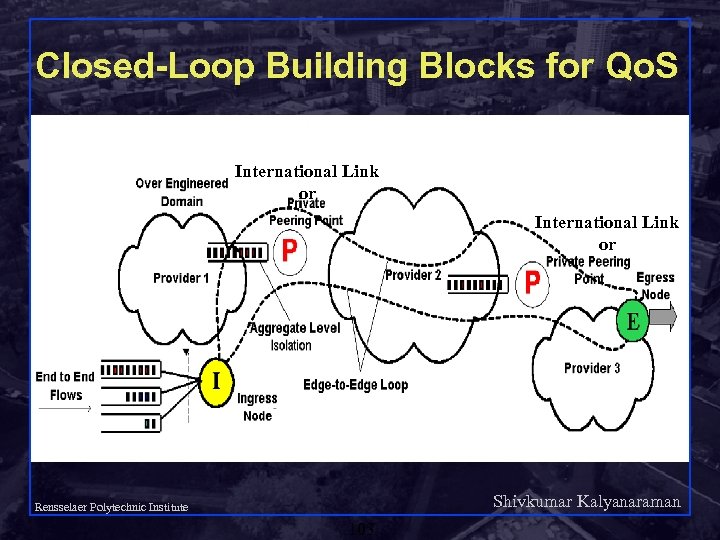
Closed-Loop Building Blocks for Qo. S International Link or Shivkumar Kalyanaraman Rensselaer Polytechnic Institute 103
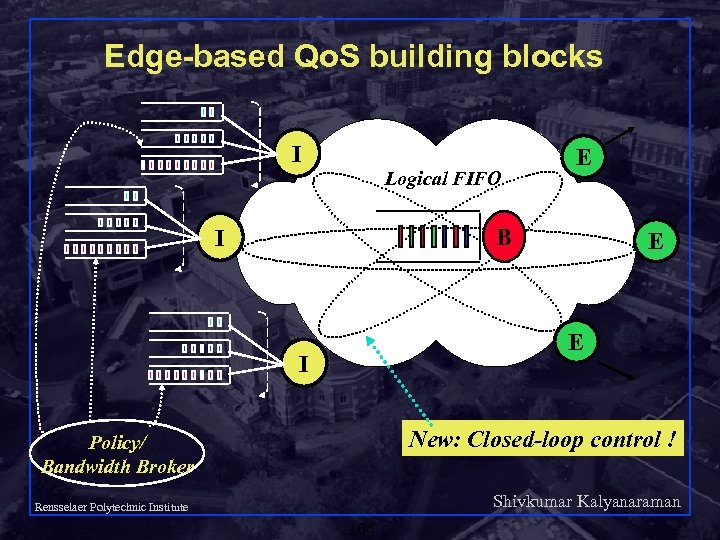
Edge-based Qo. S building blocks I Logical FIFO E B I E E I New: Closed-loop control ! Policy/ Bandwidth Broker Shivkumar Kalyanaraman Rensselaer Polytechnic Institute 104
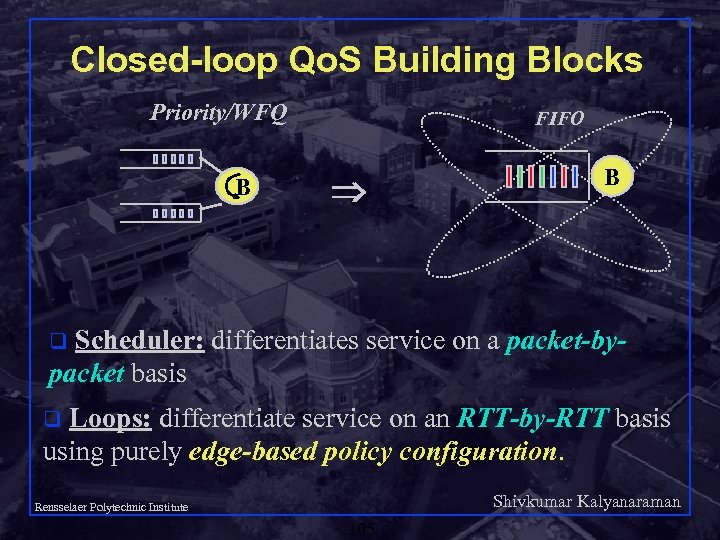
Closed-loop Qo. S Building Blocks Priority/WFQ B FIFO B Scheduler: differentiates service on a packet-bypacket basis q Loops: differentiate service on an RTT-by-RTT basis using purely edge-based policy configuration. q Shivkumar Kalyanaraman Rensselaer Polytechnic Institute 105
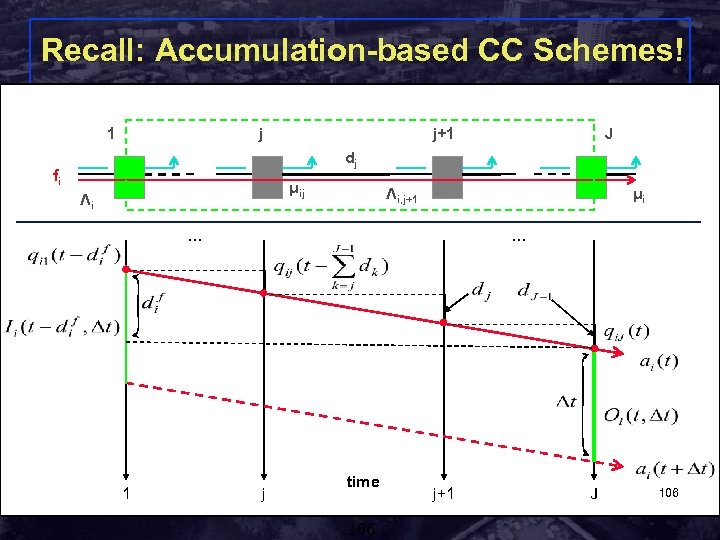
Recall: Accumulation-based CC Schemes! 1 j j+1 J dj fi μij Λi Λi, j+1 μi … 1 Rensselaer Polytechnic Institute … j time 106 j+1 J Shivkumar Kalyanaraman 106
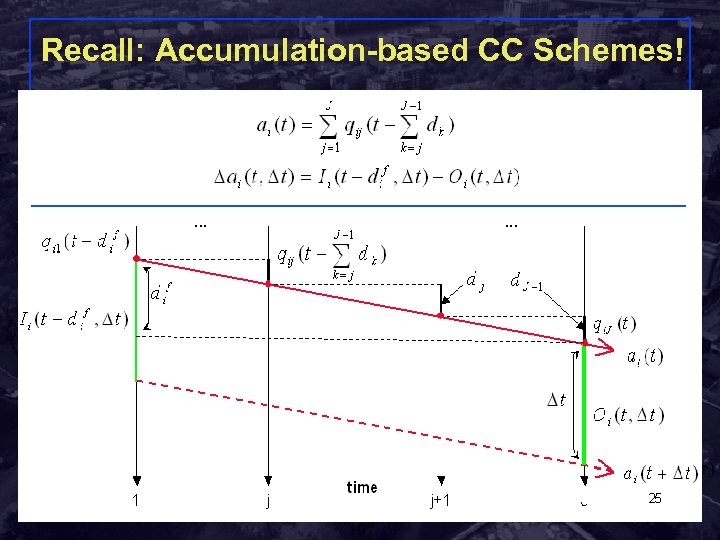
Recall: Accumulation-based CC Schemes! 1 j j+1 J dj fi μij Λi Λi, j+1 μi … 1 Rensselaer Polytechnic Institute … j time 107 j+1 J Shivkumar Kalyanaraman 107
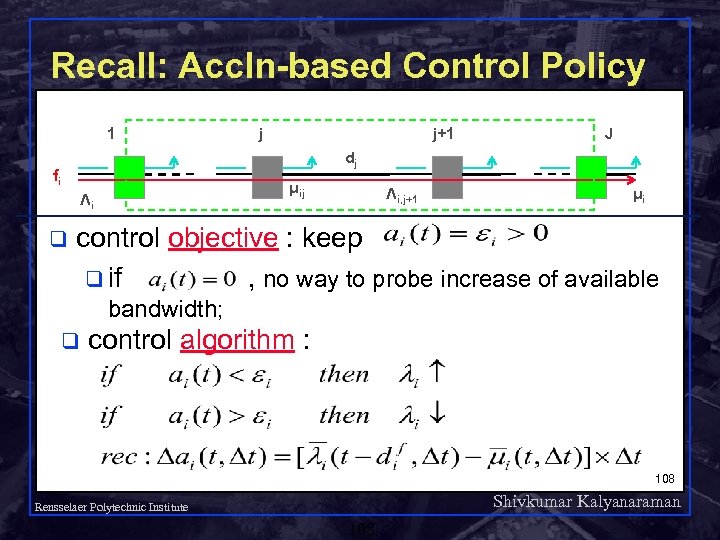
Recall: Accln-based Control Policy 1 j+1 J dj fi μij Λi q j Λi, j+1 μi control objective : keep q if , no way to probe increase of available bandwidth; q control algorithm : 108 Shivkumar Kalyanaraman Rensselaer Polytechnic Institute 108
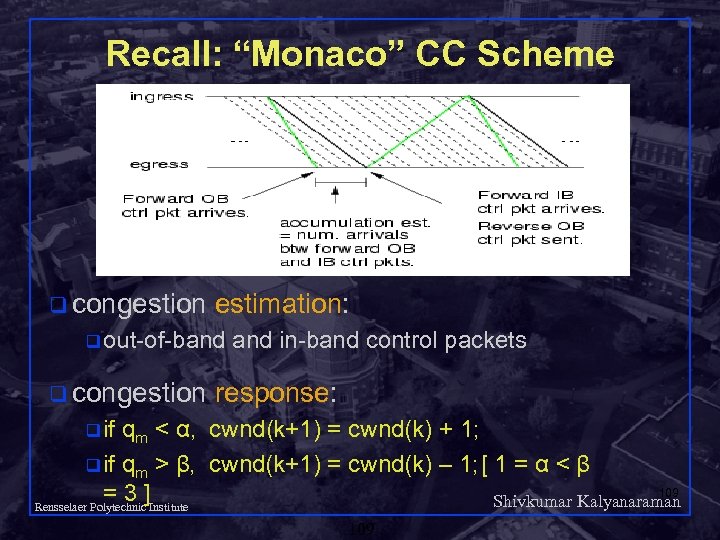
Recall: “Monaco” CC Scheme q congestion estimation: q out-of-band q congestion and in-band control packets response: q if qm < α, cwnd(k+1) = cwnd(k) + 1; q if qm > β, cwnd(k+1) = cwnd(k) – 1; [ 1 = α < β 109 =3] Shivkumar Kalyanaraman Rensselaer Polytechnic Institute 109
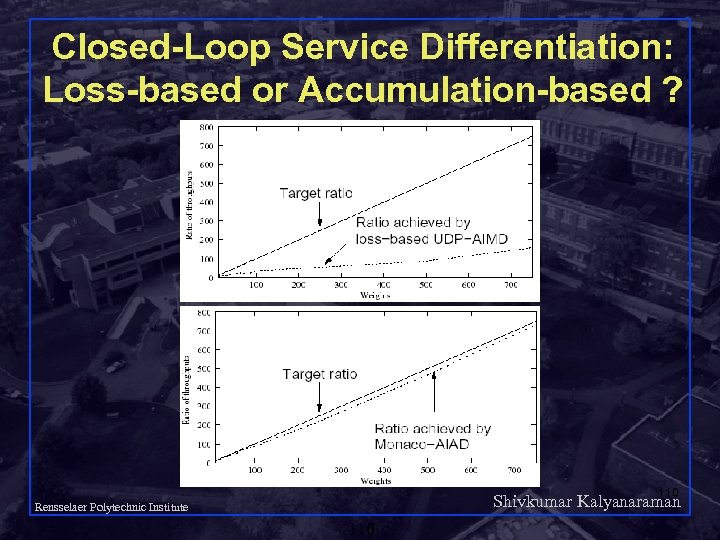
Closed-Loop Service Differentiation: Loss-based or Accumulation-based ? 110 Shivkumar Kalyanaraman Rensselaer Polytechnic Institute 110
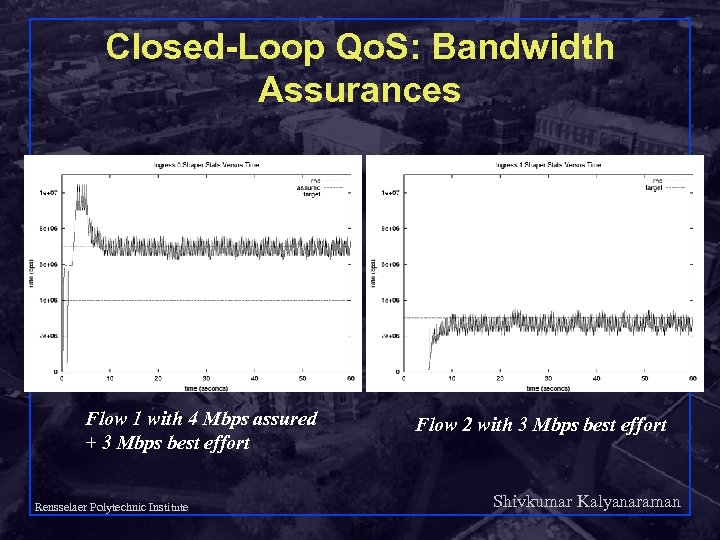
Closed-Loop Qo. S: Bandwidth Assurances Flow 1 with 4 Mbps assured + 3 Mbps best effort Flow 2 with 3 Mbps best effort Shivkumar Kalyanaraman Rensselaer Polytechnic Institute 111
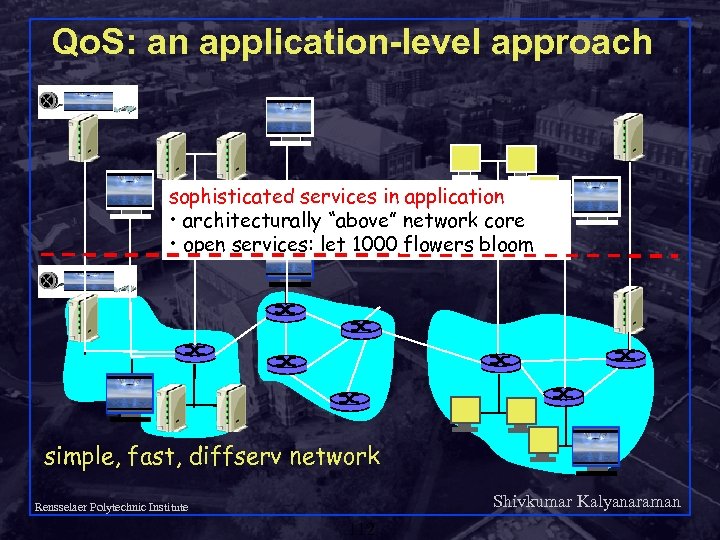
Qo. S: an application-level approach sophisticated services in application • architecturally “above” network core • open services: let 1000 flowers bloom simple, fast, diffserv network Shivkumar Kalyanaraman Rensselaer Polytechnic Institute 112
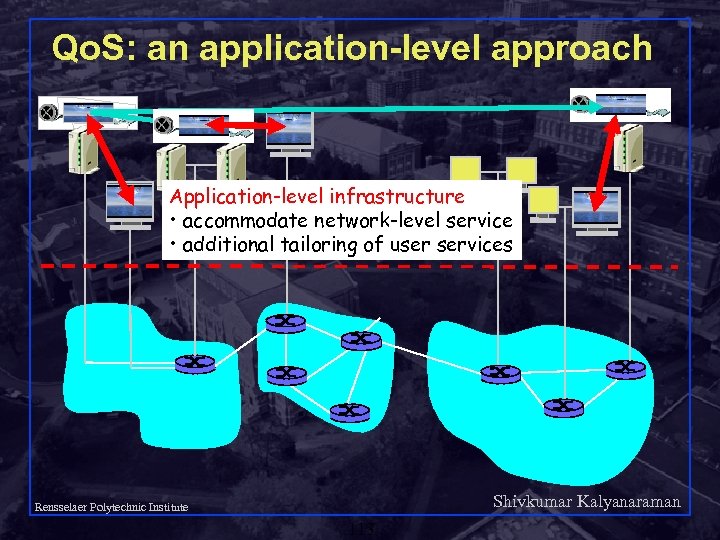
Qo. S: an application-level approach Application-level infrastructure • accommodate network-level service • additional tailoring of user services Shivkumar Kalyanaraman Rensselaer Polytechnic Institute 113
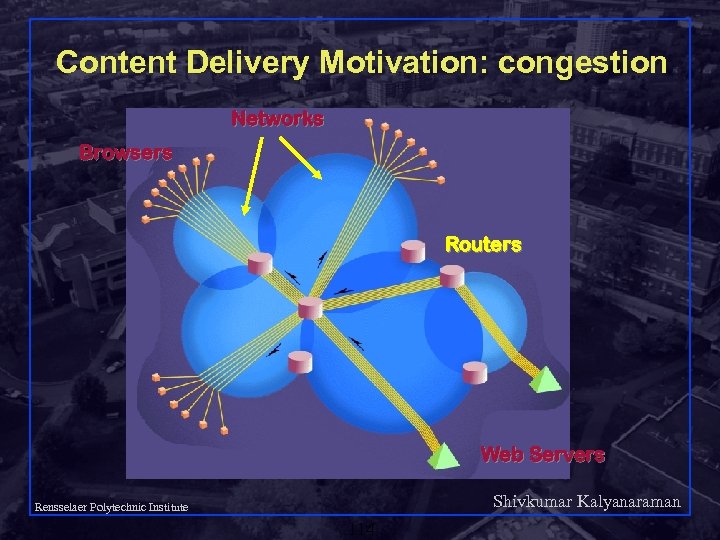
Content Delivery Motivation: congestion Networks Browsers Routers Web Servers Shivkumar Kalyanaraman Rensselaer Polytechnic Institute 114
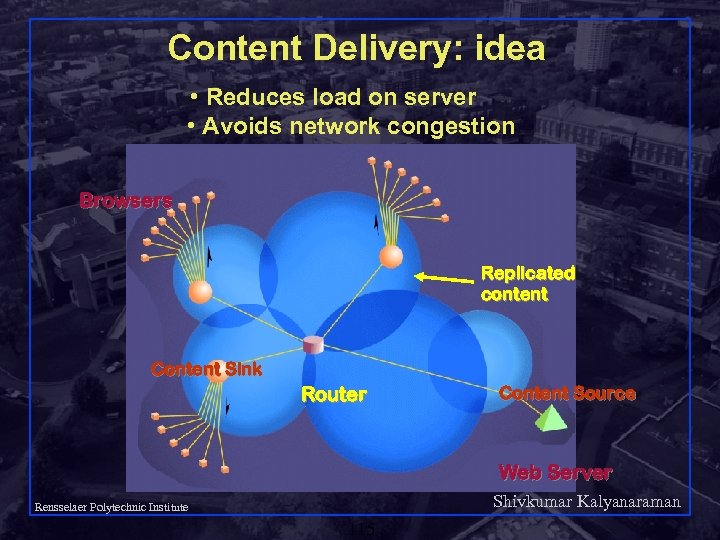
Content Delivery: idea • Reduces load on server • Avoids network congestion Browsers Replicated content Content Sink Router Content Source Web Server Shivkumar Kalyanaraman Rensselaer Polytechnic Institute 115
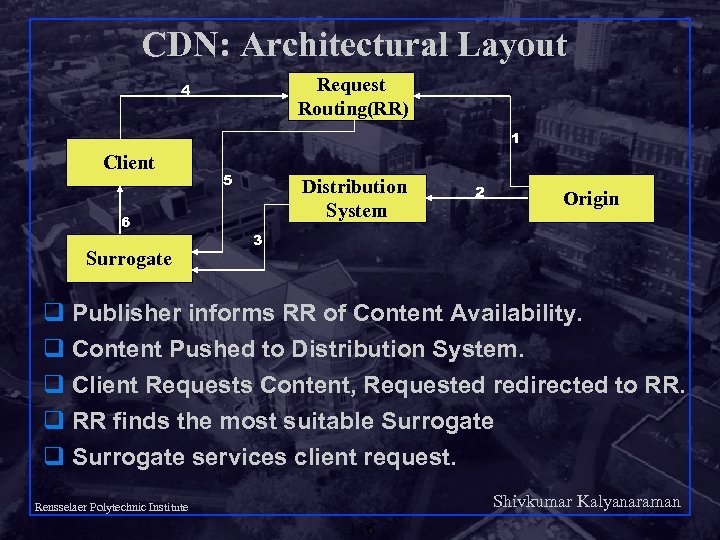
CDN: Architectural Layout Request Routing(RR) 4 1 Client 6 Surrogate 5 Distribution System 2 Origin 3 q Publisher informs RR of Content Availability. q Content Pushed to Distribution System. q Client Requests Content, Requested redirected to RR. q RR finds the most suitable Surrogate q Surrogate services client request. Shivkumar Kalyanaraman Rensselaer Polytechnic Institute 116
Summary q q q Qo. S big picture, building blocks Integrated services: RSVP, 2 services, scheduling, admission control etc Diff-serv: edge-routers, core routers; DS byte marking and PHBs Real-time transport/middleware: RTP, H. 323 New problems: inter-domain Qo. S, Application-level Qo. S, Content delivery/web caching Shivkumar Kalyanaraman Rensselaer Polytechnic Institute 117
ac7c23e613a7c457cd1ac4561200a9c8.ppt