637a661c98e6a5f2cb849c1c003eadc8.ppt
- Количество слайдов: 13

Bell Labs - Internet Research Department Mission • Investigate latent vulnerabilities and pathological deficiencies in network infrastructure, network services, and network user equipment. • Provide technologies to protect and promote the security of IP networks like the Internet. • Expand our technologies to protect and promote the security of distributed systems. Lloyd Greenwald lgreenwald@lucent. com (973) 386 -6797 1 © Lucent Technologies Proprietary 2005 - All Rights Reserved

Enabling Application Communities • Infrastructure for monitoring and securing a distributed community of applications • Algorithms and tools for understanding and addressing potential faults and attacks within the community • Formal analysis tools for generating code variations without loss of manageability lgreenwald@lucent. com 2 © Lucent Technologies Proprietary 2005 - All Rights Reserved

Internet Research Department Capabilities • Network Reconnaissance • Cyber Situational Awareness • Penetration Testing • Protecting Application Communities • High Speed, Distributed IPS/VDS • Polymorphic Programs lgreenwald@lucent. com 3 © Lucent Technologies Proprietary 2005 - All Rights Reserved
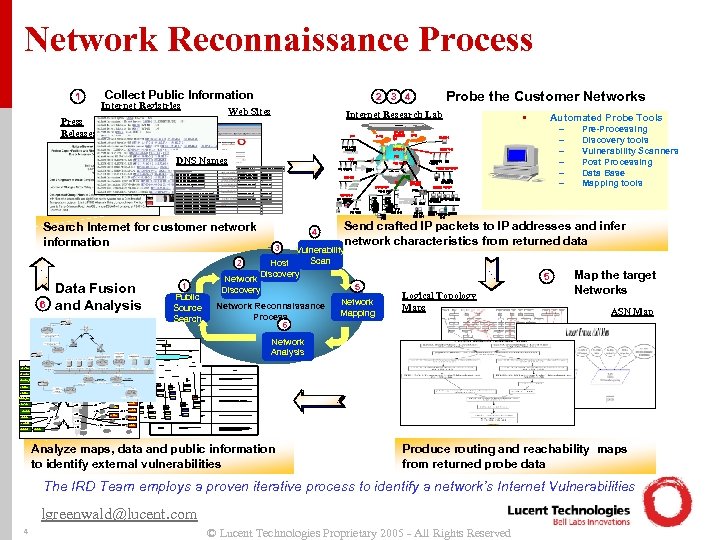
Network Reconnaissance Process • 1 Collect Public Information Internet Registries Press Releases Probe the Customer Networks 2 3 4 Web Sites Internet Research Lab DMZ SAVVIS T 1 UUNet ISP Network Security Zone OSPF NOC SMS DNS Name IP Address DNS Resolution iocecweb 1. spco. com iocecweb 2. spco. com iocecweb 3. spco. com iocecweb 4. spco. com 123. 22. 68. 248 123. 22. 68. 249 123. 22. 68. 74 worked connectandcreate. spco. com connectandcreate 1. spco. com connectandcreate 2. spco. com connectandcreate 3. spco. com connectandcreate 4. spco. com connectandcreate 5. spco. com connectandcreate 6. spco. com 123. 22. 64. 4 worked - 123. 22. 64. 29 Search Internet for customer network information 2 Data Fusion and Analysis xxx. vvv. 127. 68 xxx. uuu. 74. 169 xxx. www. 2. 174 IPv 6 xxx. www. 122. 69 SP 2 xxx. yyy. 12. 9 SP 1 ISP 1 Cisco xxx. yyy. 12. 1 Cat 1900 Cisco xxx. yyy. 12. 20 Cat 1900 xxx. yyy. 12. 2 AAGK 1 SP 1 Loc 3 -R 1 ISP 2 SP 3 SP 2 Cisco ISP 3 sp 2 xxx. yyy. 12. 24 BILLING xxx. yyy. 12. 4 BILLING 2 xxx. yyy. 12. 26 VTVG 1 xxx. yyy. 12. 6 DBCLIENT Loc 10 -R 1 ISP 4 Loc 13 -R 2 SP 9 AAVNM 1 sp 6 Loc 6 -R 1 sp 7 Loc 3 -R 6 ISP 5 ISP 7 Loc 3 -R 2 City 7 Cisco xxx. yyy. 12. 82 Cat 1900 GGGW 2 SP 12 Loc 6 -R 1 City 2 Cisco BBGW 2 xxx. yyy. 12. 225 Cisco xxx. yyy. 12. 146 Cat 1900 xxx. yyy. 12. 116 RRGW 1 Loc 8 -R 2 DDGW 1 SP 10 xxx. yyy. 1284 City 4 SP 16 SP 15 Network Mapping • 5 Logical Topology Maps Map the target Networks ASN Map Vulnerability Solution If Private Addressing is being used to conceal the connection then an Access Control List needs to be implemented on the router. xxx. yyy. 12. 228 LLGW 1 It is believed that this is a 3640 or 4500 M Cisco router that LLGW 2 will respond to NTP and ICMP Time Stamp Requests. City 14 The router needs to be configured to not respond to either type of request. xxx. yyy. 12. 196 KKGW 1 JJGW 2 informationsystems. atlanta. n et Cisco xxx. yyy. 12. 178 Cat 1900 Cisco xxx. yyy. 12. 242 Cat 1900 KKGW 2 It is believed that this is a 3640 or 4500 M Cisco router. In addition, it seems that the router is configured as a TACAS xxx. yyy. 12. 244 server. MMGW 1 Cisco xxx. yyy. 12. 210 Cat 1900 City 13 There are vulnerabilities with TACAS servers. To mitigate this vulnerability, verify that all updates have been implemented on this device. MMGW 2 xxx. yyy. 12. 212 PPGW 1 xxx. yyy. 12. 148 EEGW 1 RRGW 2 DDGW 2 Loc 13 -R 1 Loc 8 -R 4 xxx. yyy. 12. 241 Private Addressing is being used to connect the xxx. 76. 70. 0 Cisco network to UUNet. xxx. yyy. 12. 226 Cat 1900 xxx. 76. 70. 66 xxx. 76. 70. 12 yyy. 172. 70. 138 Cisco xxx. yyy. 12. 114 Cat 1900 City 6 SP 14 5 Cisco xxx. yyy. 12. 194 Cat 1900 City 9 xxx. yyy. 12. 53 BBGW 1 SP 13 Vulnerability Scan Host Discovery Cisco City 11 City 3 Loc 14 -R 2 Send crafted IP packets to IP addresses and infer network characteristics from returned data xxx. yyy. 12. 209 172. 25. 50 xxx. yyy. 12. 164 JJGW 1 xxx. 76. 70. 65 xxx. 76. 70. 11 HHGW 2 Loc 9 -R 1 xxx. yyy. 12. 69 GGGW 1 Cisco xxx. yyy. 12. 50 Cat 1900 ISP 5 Network Probe Tools Workstations Network Database Storage Visualization Tools Cisco xxx. yyy. 10. 81 xxx. yyy. 12. 177 172. 25. 50 xxx. 76. 70. 65 xxx. 76. 70. 11 Cisco xxx. yyy. 12. 162 Cat 1900 FFGW 2 Loc 4 -R 1 Loc 15 -R 1 Loc 2 -R 1 SP 8 SP 11 sp 5 Cisco xxx. yyy. 12. 130 Cat 1900 xxx. yyy. 12. 132 HHGW 1 Cisco xxx. yyy. 12. 66 Cat 1900 xxx. yyy. 12. 7 BILLINGDB sp 3 xxx. yyy. 12. 145 Loc 8 -R 3 SP 7 SP 6 3 Linux www 6. iplab. org Home ns 6. iplab. org Plotter Printer Agent Solaris Content Server IPv 6 Access Point Probe Tools Dial-Out Mobile Probe Tools Unit Cisco xxx. yyy. 12. 193 Cisco xxx. yyy. 12. 113 xxx. yyy. 12. 98 Cat 1900 AAGW 2 SP 3 VTVG 2 City 1 xxx. yyy. 10. 50 Cisco xxx. yyy. 12. 161 Address IP Cisco xxx. yyy. 12. 100 FFGW 1 xxx. yyy. 12. 81 xxx. yyy. 12. 3 AAGK 2 4 Agent Linux Content Server Access Point xxx. yyy. 10. 86 xxx. yyy. 106 Cisco xxx. yyy. 129 Cisco xxx. yyy. 12. 22 AAGW 1 SP 1 VTVGK 1 xxx. yyy. 12. 37 Backbone W 2 K Home MVAM Gatekeeper xxx. yyy. 18. 98 xxx. yyy. 10. 118 A xxx. yyy. 10. 122 Loc 5 -R 1 r e a Loc 1 -R 2 2 City 5 sp 2 xxx. yyy. 10 Cisco xxx. yyy. 12. 34 Cat 1900 Web Media Server xxx. yyy. 18. 102 xxx. yyy. 12. yyy xxx. yyy. 12. 49 Loc 8 -R 1, R 2 Loc 3 -R 3 Cisco xxx. yyy. 12. 65 SP 2 Loc 4 -R 1, R 2 Loc 3 -R 4 xxx. yyy. 12. 33 Cisco xxx. yyy. 12. 18 GPS Enterprise Network Switch Network Analysis Area 1 xxx. yyy. 10. 74 xxx. yyy. 10. 110 xxx. yyy. 10. 114 xxx. yyy. 10. 42 xxx. yyy. 10. 6 IPv 6 Tunnel To MH, HO Pre-Processing Discovery tools Vulnerability Scanners Post Processing Data Base Mapping tools Vo. IP Network PBX MAX TNT Gateway Network Reconnaissance Process 6 SP 2 Gateway Network xxx. yyy. 17. 18 Mobile IPv 6 Log Mobility Test Network MPLS Core Customers Network Discovery xxx. www. 164. 51 xxx. zzz. 216. 145 SP 1 Network IDS Analyzer MPLS Network Firewall LAN NMS MPLS DNS IPv 6 Network 1 Public Source Search – – – Honey Pot T 1 www. iplab. org A r Loc 6 -R 2 e a Loc 11 -R 1 1 Automated Probe Tools ASN 8158 DNS Web Mail Server DNS Names 6 • Internet IPv 4, IPv 6, IP Multicast BGP 4 VPN City 8 EEGW 2 xxx. yyy. 12. 180 NNGW 1 xxx. 76. 70. 66 xxx. 76. 70. 12 yyy. 172. 70. 138 City 10 xxx. 76. 70. 5 8 xxx. 76. 70. 0 1 It. City 12 PPGW 2 is a 3640 or 4500 M Cisco router that is believed that this will respond to NTP and ICMP Time Stamp Requests. The router needs to be configured to not respond to either type of request. Responds with and ICMP Filtered or ICMP ADMIN Prohibited message When implementing firewalls or access lists the device should not give away its position or the fact it is a security device. The device should have an access list to filter any ICMP message. The idea is to make the networks behind this device seem like a black hole. NNGW 2 Analyze maps, data and public information to identify external vulnerabilities Produce routing and reachability maps from returned probe data The IRD Team employs a proven iterative process to identify a network’s Internet Vulnerabilities lgreenwald@lucent. com 4 © Lucent Technologies Proprietary 2005 - All Rights Reserved

Extension to Application Reconnaissance 1. Search local and global networks for published application and community data 2. Probe community computer systems for system configuration and component information and vulnerabilities 3. Produce composite system and community views from probe data 4. Fuse and analyze data to locate and address potential faults and attacks 5. Iterate lgreenwald@lucent. com 5 © Lucent Technologies Proprietary 2005 - All Rights Reserved
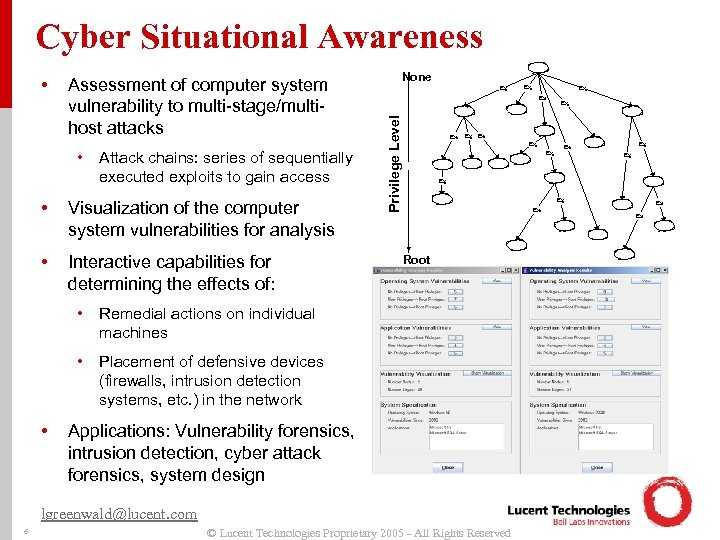
Cyber Situational Awareness Assessment of computer system vulnerability to multi-stage/multihost attacks • Attack chains: series of sequentially executed exploits to gain access • Visualization of the computer system vulnerabilities for analysis • Interactive capabilities for determining the effects of: • • Ex n Ex Ex n n Ex n Ex n Root Placement of defensive devices (firewalls, intrusion detection systems, etc. ) in the network Applications: Vulnerability forensics, intrusion detection, cyber attack forensics, system design lgreenwald@lucent. com 6 Ex n Remedial actions on individual machines • None Privilege Level • © Lucent Technologies Proprietary 2005 - All Rights Reserved Ex n
Penetration Testing: Find and Address Weaknesses • Find: services, system info, users, file shares • Address: buffer overflows, misconfigurations, weak password protection, poor input validation • Access: user accounts, SQL injection, remote command execution, privilege escalation, backdoors, port redirection • Custom tools • Expertise with: – Telephony – Data networks – Wireless technologies lgreenwald@lucent. com 7 © Lucent Technologies Proprietary 2005 - All Rights Reserved

Protecting Application Communities Solution Issue 1. Ensuring that the distributed application code is authentic and authorized 1. Hash functions, application generator, resident helper agent 2. Preventing unauthorized modification of the application 2. Time-to-live timeouts, code shuffling and obfuscation 3. Resolved by addressing #1 and 2 effectively. 3. Application communities must be able to counter new threats (protected from malicious hosts and applications) lgreenwald@lucent. com 8 © Lucent Technologies Proprietary 2005 - All Rights Reserved

Other Protection Mechanisms • Applications communicate via encrypted messaging – Encryption keys are based on generation of applications – If an application can’t understand (i. e. decrypt) a message it receives, it reports a problem (unless suspected Do. S is underway) • Applications utilize helper agents – Helper agents contain only the hash algorithm – very small – If a helper agent returns with an incorrect value (or doesn’t return at all due to malicious host), a problem is indicated • Intelligent application regeneration: detect and regenerate failed community members lgreenwald@lucent. com 9 © Lucent Technologies Proprietary 2005 - All Rights Reserved
High Speed, Distributed IPS/VDS • Real-time intrusion prevention, virus/worm detection • Monitor and analyze traffic patterns in real-time • Detect anomalies or signatures of impending or actual attacks – Adaptive statistical threshold anomaly detection – Multi-character multi-pattern string matching – Sequential change-point and persistence filter detection • Filter the offending traffic at the ingress point • Conduct post-attack analysis • Detection at 40 Gb/s line speeds lgreenwald@lucent. com 10 © Lucent Technologies Proprietary 2005 - All Rights Reserved
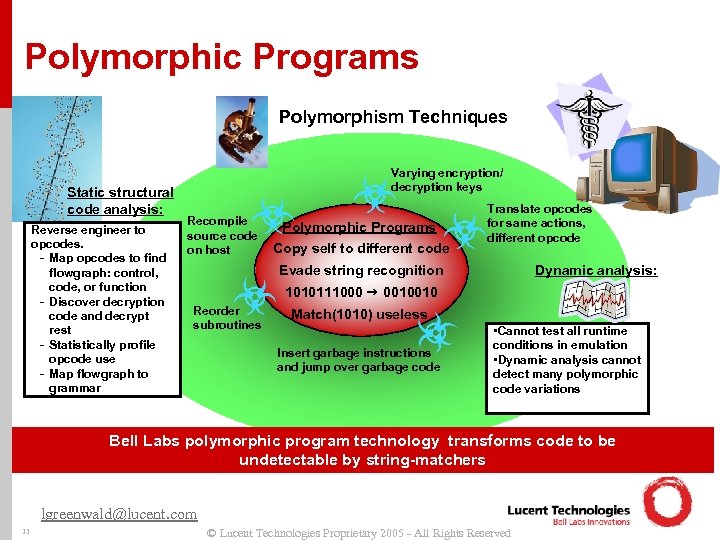
Polymorphic Programs Polymorphism Techniques Static structural code analysis: Reverse engineer to opcodes. - Map opcodes to find flowgraph: control, code, or function - Discover decryption code and decrypt rest - Statistically profile opcode use - Map flowgraph to grammar Varying encryption/ decryption keys Recompile source code on host Polymorphic Programs Copy self to different code Translate opcodes for same actions, different opcode Evade string recognition Dynamic analysis: 1010111000 0010010 Reorder subroutines Match(1010) useless Insert garbage instructions and jump over garbage code • Cannot test all runtime conditions in emulation • Dynamic analysis cannot detect many polymorphic code variations Bell Labs polymorphic program technology transforms code to be undetectable by string-matchers lgreenwald@lucent. com 11 © Lucent Technologies Proprietary 2005 - All Rights Reserved
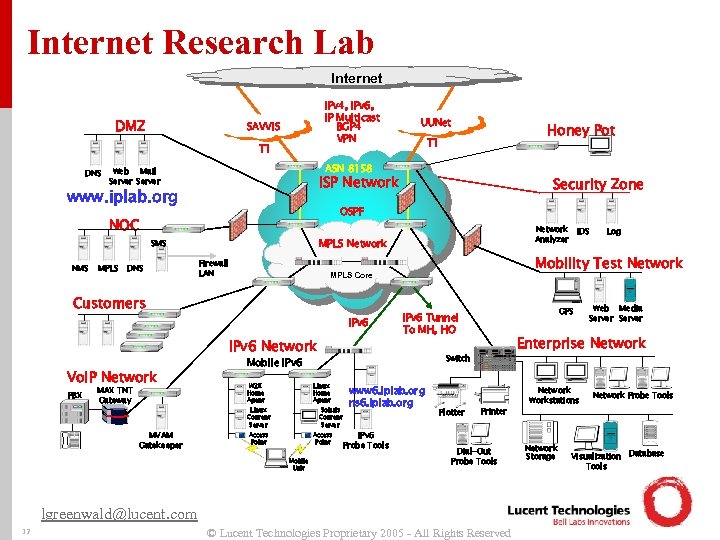
Internet Research Lab Internet DMZ IPv 4, IPv 6, IP Multicast BGP 4 VPN SAVVIS T 1 DNS ISP Network Firewall LAN IPv 6 Network PBX MAX TNT Gateway MVAM Gatekeeper Solaris Content Server Access Point Mobile Unit www 6. iplab. org ns 6. iplab. org IPv 6 Probe Tools Plotter Printer Dial-Out Probe Tools lgreenwald@lucent. com 12 Log Web Media Server Enterprise Network Switch Linux Home Agent Linux Content Server GPS IPv 6 Tunnel To MH, HO Mobile IPv 6 W 2 K Home Agent IDS Mobility Test Network MPLS Core Customers Vo. IP Network Analyzer MPLS Network SMS DNS Security Zone OSPF NOC MPLS Honey Pot T 1 ASN 8158 Web Mail Server www. iplab. org NMS UUNet © Lucent Technologies Proprietary 2005 - All Rights Reserved Network Workstations Network Storage Network Probe Tools Visualization Database Tools

Enabling Application Communities • Infrastructure for monitoring and securing a distributed community of applications • Algorithms and tools for understanding and addressing potential faults and attacks within the community • Formal analysis tools for generating code variations without loss of manageability Bell Labs Internet Research Department has years of commercial, government, and internal R&D experience in enabling technologies for application communities Lloyd Greenwald lgreenwald@lucent. com (973) 386 -6797 13 © Lucent Technologies Proprietary 2005 - All Rights Reserved
637a661c98e6a5f2cb849c1c003eadc8.ppt