8863478231c9fd17d26e8d971b3b5b2c.ppt
- Количество слайдов: 28

Bandwidth Do. S Attacks and Defenses Presented By: Ken Regis

What is a Denial of Service Attack? • Goal: make a service unusable. • How: overload a server, router, network link. • Focus: bandwidth attacks (“trinoo”, “tfn”).
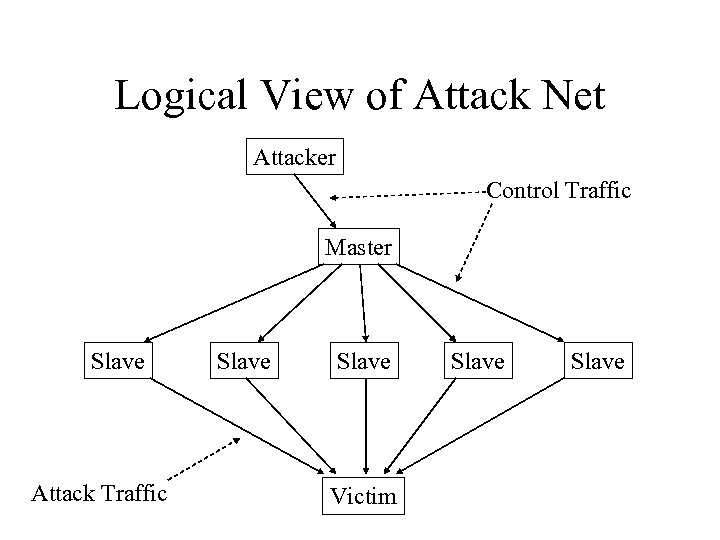
Logical View of Attack Net Attacker Control Traffic Master Slave Attack Traffic Slave Victim Slave
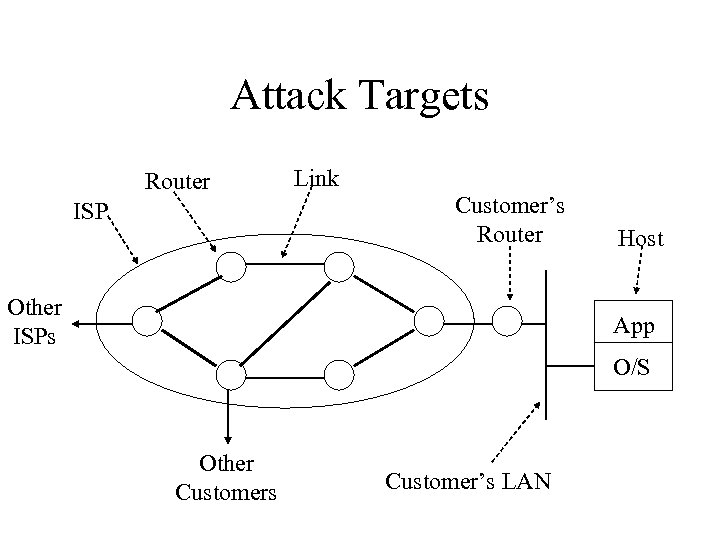
Attack Targets Router ISP Link Customer’s Router Other ISPs Host App O/S Other Customers Customer’s LAN

Attacks use IP Packets IP Header: Source Address Destination Address User Data • Routers forward each packet independently. • Routers don’t know about connections. • Complexity is in end hosts; routers are simple.

Outline • Case study: Yahoo. – What happened. – Analysis. • Our framework for defense: RON.

Case Study: Yahoo Attack • Early February 2000. • Took Yahoo off the net for hours.
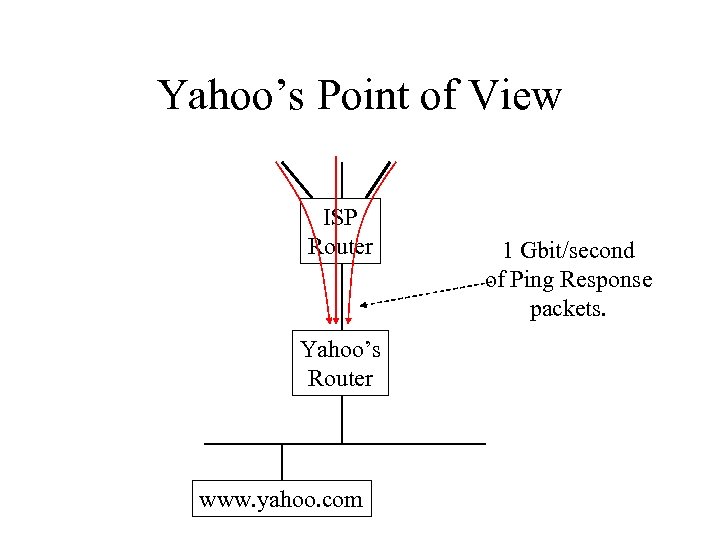
Yahoo’s Point of View ISP Router Yahoo’s Router www. yahoo. com 1 Gbit/second of Ping Response packets.
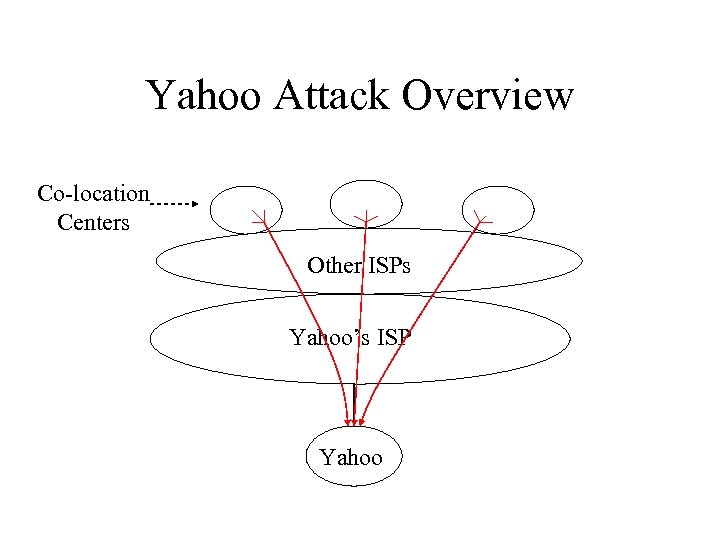
Yahoo Attack Overview Co-location Centers Other ISPs Yahoo’s ISP Yahoo
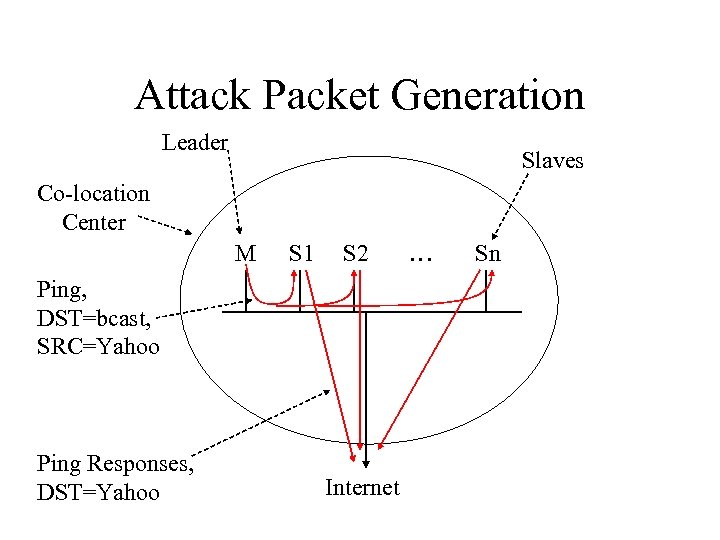
Attack Packet Generation Leader Slaves Co-location Center M S 1 S 2 Ping, DST=bcast, SRC=Yahoo Ping Responses, DST=Yahoo Internet … Sn

What did the attack depend on? • • • Pervasive insecure hosts. Fake IP source addresses. Use of hosts as amplifiers. Weak router software. Difficulty of diagnosis.

Pervasive Insecure Hosts • Required for disguise and to generate enough traffic. • How do they break in? – Buffer overruns. – Typically Solaris and Linux. – Highly automated. • Defenses? – – Better programming practices. Disable services by default. Firewalls, intrusion detection. Motivation for deployment is not strong.

Fake IP Source Addresses • Two uses: – Hide the source of attack. – Part of weapon. • • Example: SYN flooding. Defense: – Ingress/egress filtering. – But motivation for deployment is not strong.
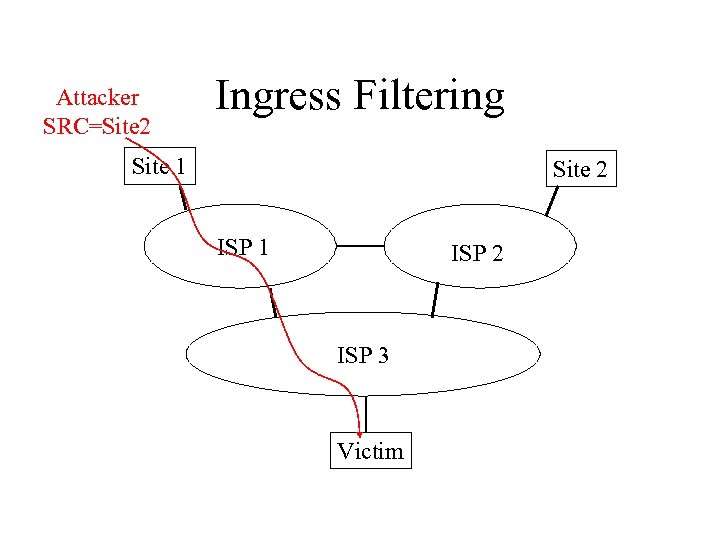
Attacker SRC=Site 2 Ingress Filtering Site 1 Site 2 ISP 1 ISP 2 ISP 3 Victim

Use of Hosts as Amplifiers • Attackers need this: – To avoid using their own machines. – To generate lots of traffic. – To avoid detection via load monitoring. • Two approaches: – Break into 1000 s of machines. – Trick legitimate machines into generating traffic.

Weak Router Software • Routers themselves are often victims. • Why? – Forwarding and management compete for CPU. – Control and data traffic compete for net b/w. • Solutions? – Simplify and partition.

Difficulty of Diagnosis • Very little automatic support for traffic analysis and correlation. – Is the high load legitimate? – What does the attack consist of? – Where does the attack come from? – How ask upstream routers to discard attack packets? • Defense: distributed analysis system.

Why are these attacks easy? • Internet built around end-to-end principle: – Most functions done by end hosts. – Examples: reliable delivery. • Advantages: – Simplifies network core. • Example: IP packet forwarding. • Example: it’s easy to start an ISP. – Anyone can introduce new services. • Result: lots of innovation.

Why is defense hard? • End-to-end principle conflicts with: – Centralized control. – Centralized monitoring. – Separation of data from control traffic. – Mandatory authentication. – Mandatory accounting.

RON Project • End-to-end framework for: – Cooperative statistics collection. – Cooperative reaction to attacks. – Fault-tolerant control and data routing. • How: resilient overlay network (RON). • Funded by DARPA/IA/FTN.
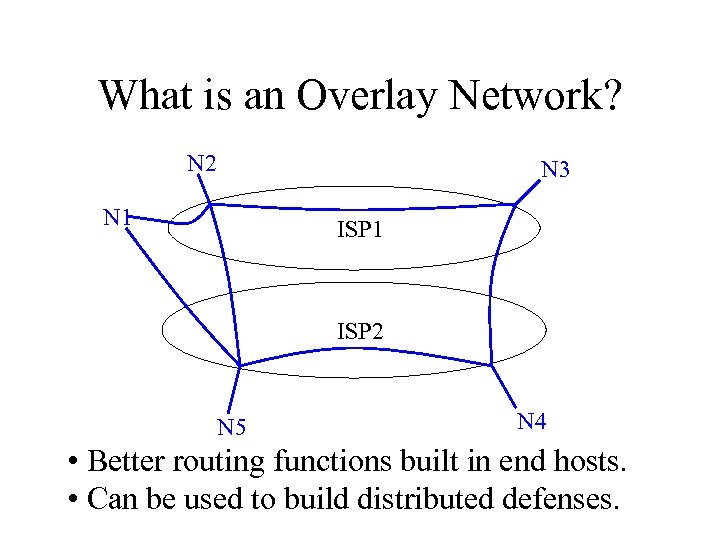
What is an Overlay Network? N 2 N 3 N 1 ISP 2 N 5 N 4 • Better routing functions built in end hosts. • Can be used to build distributed defenses.

Why Distributed Defenses? • Presence of attack obvious near victim. – Not obvious near sources of attack. – But control is easier near sources. • Identifying attackers requires cooperation. – Asymmetric routing. – Fake source addresses.

Why Distribution is Hard • RON itself is a target. • Authorized communication between RON nodes. • Bandwidth attacks on RON nodes. • Application-level Do. S attacks. • Political / deployment problems. – Needs cooperation? Or single-organization?
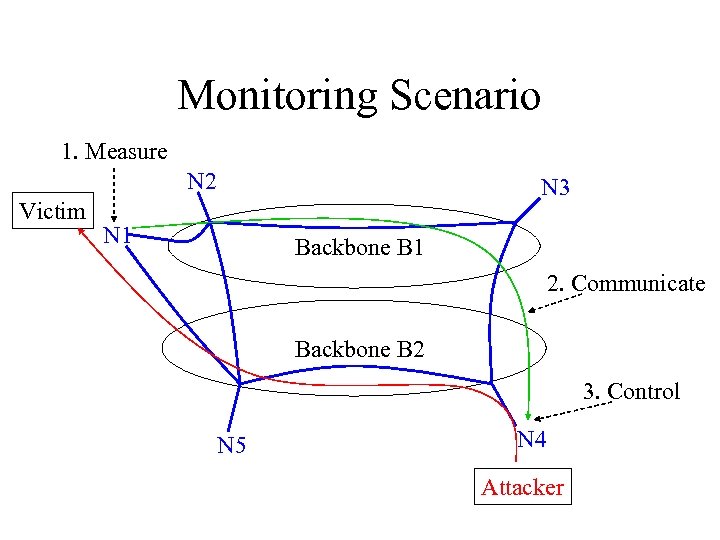
Monitoring Scenario 1. Measure N 2 Victim N 3 N 1 Backbone B 1 2. Communicate Backbone B 2 3. Control N 5 N 4 Attacker
Fault-Tolerant Routing • Use Internet to connect multiple sites. • Inter-ISP routing: – Ignores link quality. – Ignores many available paths due to policy. – Chooses only one path. – Reacts slowly. • RON allows end-system control of routing.
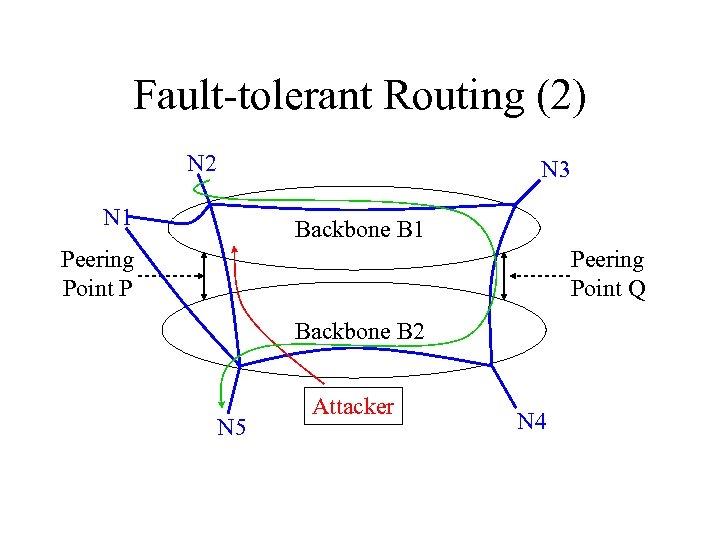
Fault-tolerant Routing (2) N 2 N 3 N 1 Backbone B 1 Peering Point P Peering Point Q Backbone B 2 N 5 Attacker N 4

Peer-to-Peer Networking • Multi-organization overlays. • Early work: Gnutella and Free. Net. – Data replicated at many sites. – Queries traverse reliable overlay. – Explicit protection of virtual infrastructure.

Summary • Raise the bar: – Improve host security. – Make it hard to fake IP addresses. • Experiment with RON-like and peer-to-peer architectures.
8863478231c9fd17d26e8d971b3b5b2c.ppt