2710e3c76a81953905277b4bee3cd306.ppt
- Количество слайдов: 48
 Awareness Program
Awareness Program
 Hack Me Now, Hack Me Then The Wonderful World of Hackers Copyright © 2011 Cyber. Security Malaysia What is All About? The awareness session is aimed to highlight the common misconception and mistake of computer and internet users on how to secure their computers. The key points include § Inside the Hackers’ Mind § Hackers’ Malicious Techniques § Secure The Human
Hack Me Now, Hack Me Then The Wonderful World of Hackers Copyright © 2011 Cyber. Security Malaysia What is All About? The awareness session is aimed to highlight the common misconception and mistake of computer and internet users on how to secure their computers. The key points include § Inside the Hackers’ Mind § Hackers’ Malicious Techniques § Secure The Human
 Jazannul Azriq Aripin Senior Executive, Outreach Dept. , Cyber. Security Malaysia Mr. Jazannul Azriq B. Aripin; Senior Executive of Outreach Department, Cyber. Security Malaysia. He has a degree in Computer Science from Universiti Malaysia Sabah. A Microsoft Certified System Engineer (MCSE) and ISMS Lead Auditor. Five years with Cyber. Security Malaysia doing Facebook Security, Facebook Forensic, Information Security Audit (ISMS/ISO 270012005) and Social Engineering
Jazannul Azriq Aripin Senior Executive, Outreach Dept. , Cyber. Security Malaysia Mr. Jazannul Azriq B. Aripin; Senior Executive of Outreach Department, Cyber. Security Malaysia. He has a degree in Computer Science from Universiti Malaysia Sabah. A Microsoft Certified System Engineer (MCSE) and ISMS Lead Auditor. Five years with Cyber. Security Malaysia doing Facebook Security, Facebook Forensic, Information Security Audit (ISMS/ISO 270012005) and Social Engineering
 Reality Check
Reality Check
 Computer Usage 101
Computer Usage 101
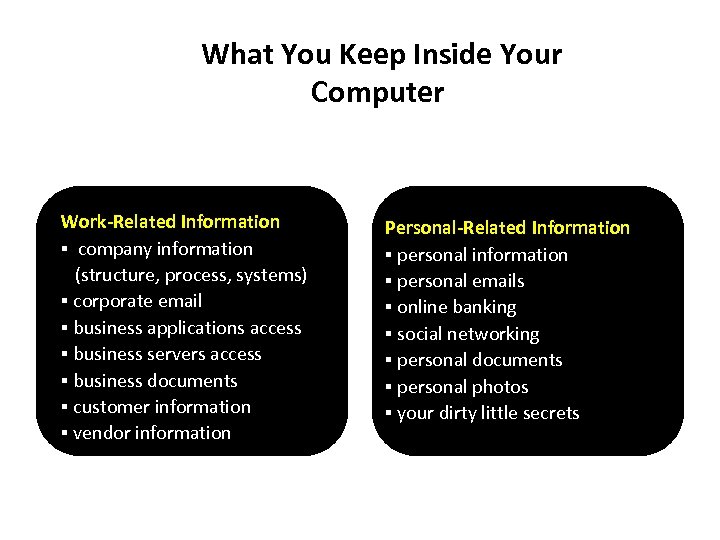 What You Keep Inside Your Computer Work-Related Information § company information (structure, process, systems) § corporate email § business applications access § business servers access § business documents § customer information § vendor information Personal-Related Information § personal information § personal emails § online banking § social networking § personal documents § personal photos § your dirty little secrets
What You Keep Inside Your Computer Work-Related Information § company information (structure, process, systems) § corporate email § business applications access § business servers access § business documents § customer information § vendor information Personal-Related Information § personal information § personal emails § online banking § social networking § personal documents § personal photos § your dirty little secrets
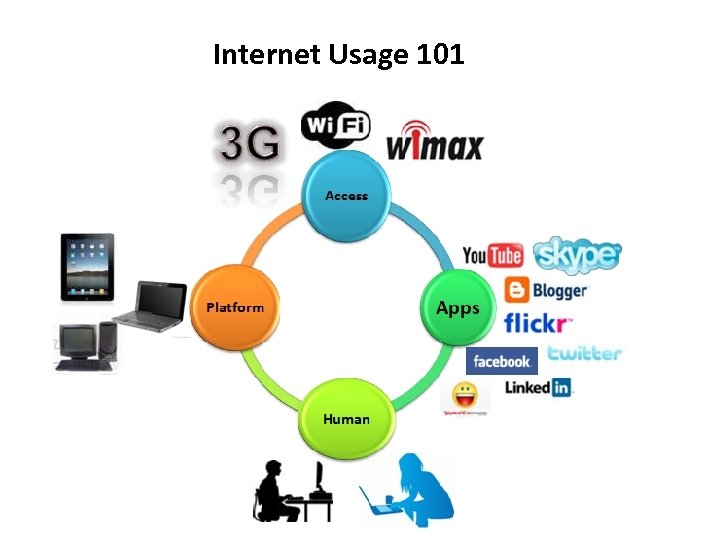 Internet Usage 101
Internet Usage 101
 Know Your Enemy Cyber Criminal Someone You Know Copyright © 2013 Cyber. Security Malaysia Someone You Don’t Know
Know Your Enemy Cyber Criminal Someone You Know Copyright © 2013 Cyber. Security Malaysia Someone You Don’t Know
 Hack Me #1 – Windows Logon
Hack Me #1 – Windows Logon

 Hack Me #2 – Password Copyright © 2013 Cyber. Security Malaysia
Hack Me #2 – Password Copyright © 2013 Cyber. Security Malaysia
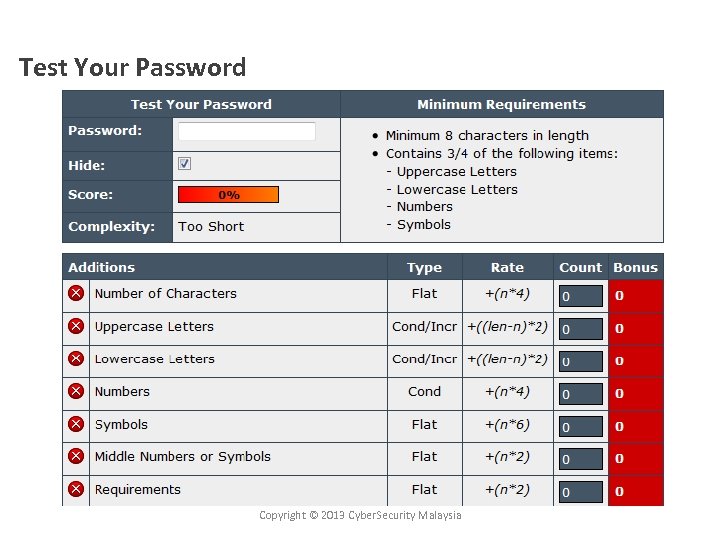 Test Your Password Copyright © 2013 Cyber. Security Malaysia
Test Your Password Copyright © 2013 Cyber. Security Malaysia
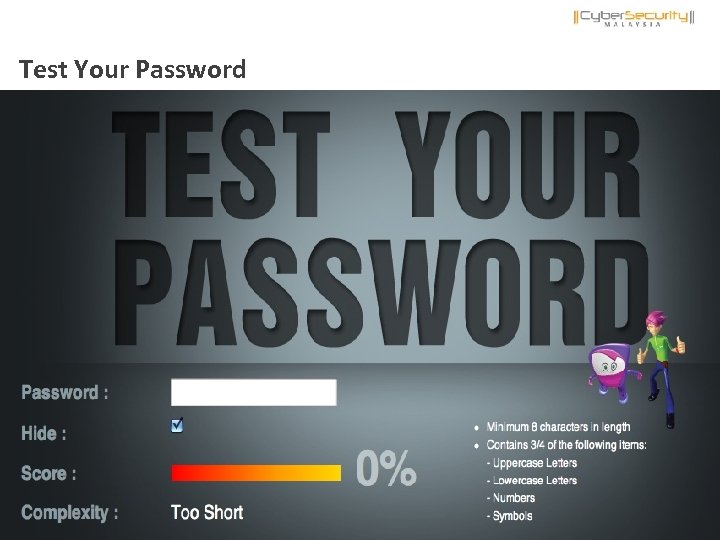 Test Your Password Copyright © 2011 Cyber. Security Malaysia
Test Your Password Copyright © 2011 Cyber. Security Malaysia
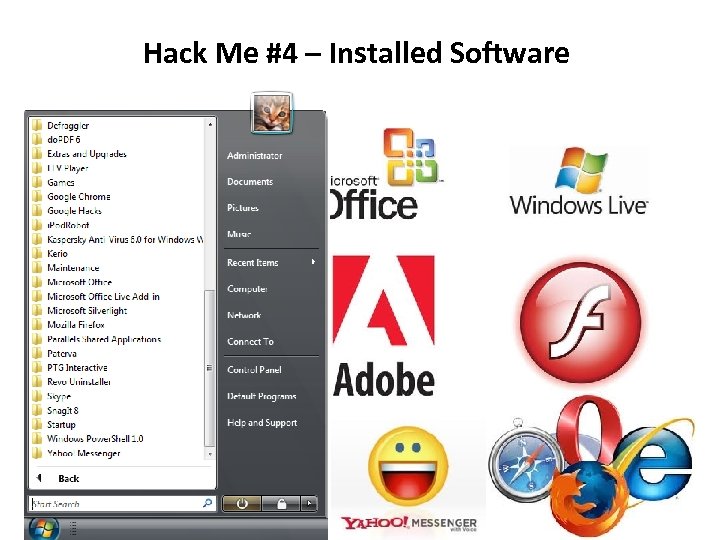 Hack Me #4 – Installed Software
Hack Me #4 – Installed Software
 Copyright © 2013 Cyber. Security Malaysia
Copyright © 2013 Cyber. Security Malaysia


 Hack Me #5 – Wireless Connection Copyright © 2013 Cyber. Security Malaysia
Hack Me #5 – Wireless Connection Copyright © 2013 Cyber. Security Malaysia
 Wi. Fi Hacking Toolkits 19 Copyright © 2010 Cyber. Security Malaysia
Wi. Fi Hacking Toolkits 19 Copyright © 2010 Cyber. Security Malaysia
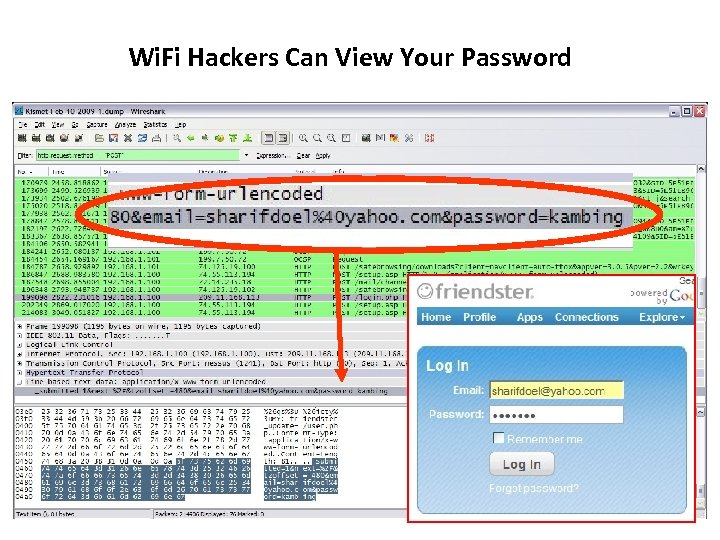 Wi. Fi Hackers Can View Your Password 20 Copyright © 2010 Cyber. Security Malaysia
Wi. Fi Hackers Can View Your Password 20 Copyright © 2010 Cyber. Security Malaysia
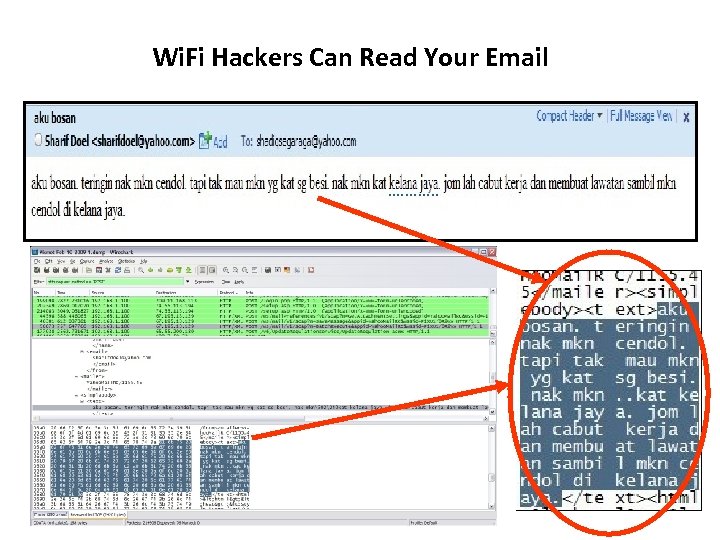 Wi. Fi Hackers Can Read Your Email 21 Copyright © 2010 Cyber. Security Malaysia
Wi. Fi Hackers Can Read Your Email 21 Copyright © 2010 Cyber. Security Malaysia
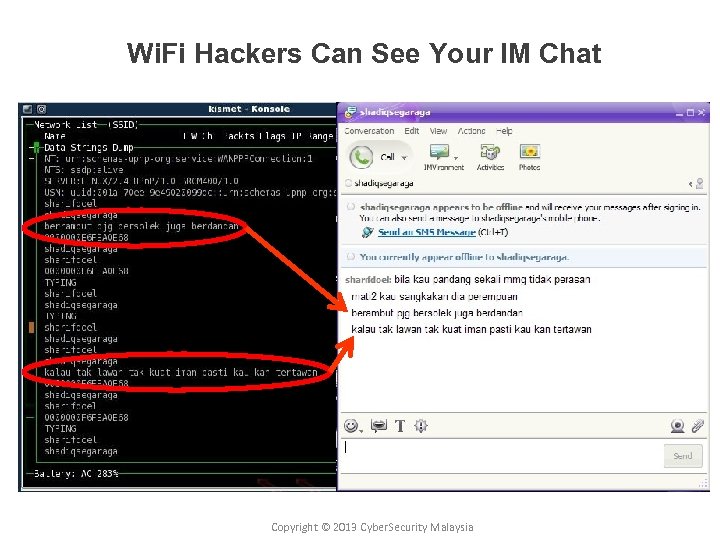 Wi. Fi Hackers Can See Your IM Chat 22 Copyright © 2010 Cyber. Security Malaysia Copyright © 2013 Cyber. Security Malaysia
Wi. Fi Hackers Can See Your IM Chat 22 Copyright © 2010 Cyber. Security Malaysia Copyright © 2013 Cyber. Security Malaysia
 Hack Me #6 – Internet Browser Copyright © 2013 Cyber. Security Malaysia
Hack Me #6 – Internet Browser Copyright © 2013 Cyber. Security Malaysia
 Copyright © 2013 Cyber. Security Malaysia
Copyright © 2013 Cyber. Security Malaysia

 Hack Me #7 – Facebook
Hack Me #7 – Facebook
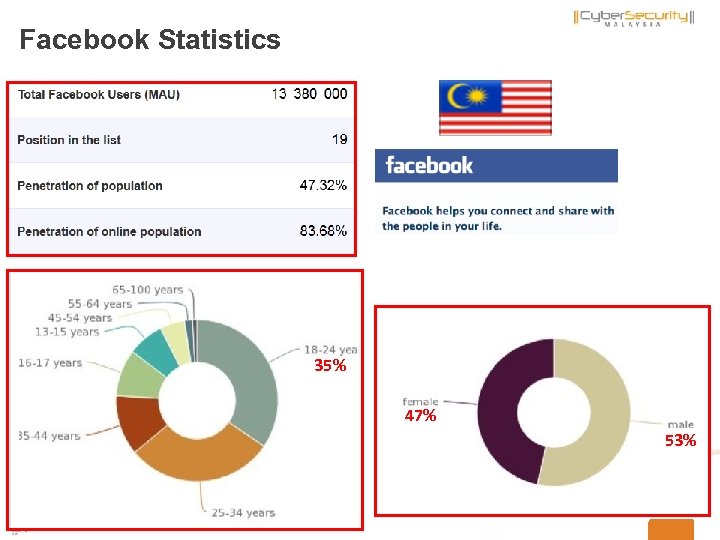 Facebook Statistics 35% 47% 53% 27
Facebook Statistics 35% 47% 53% 27
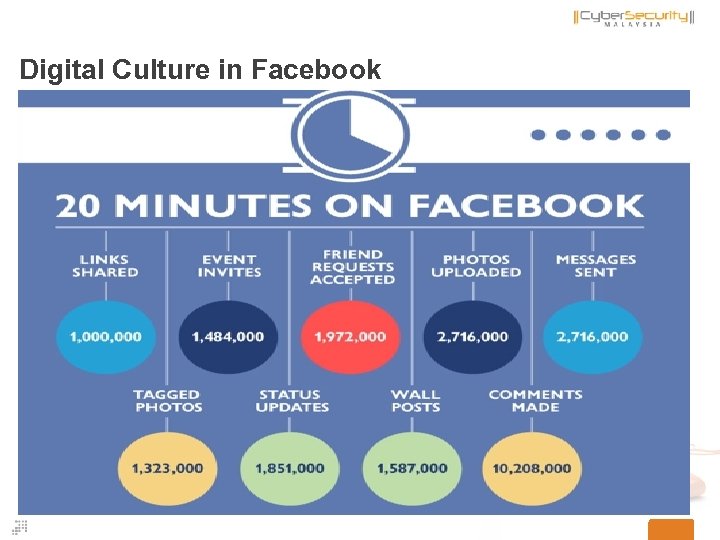 Digital Culture in Facebook
Digital Culture in Facebook
 Copyright © 2013 Cyber. Security Malaysia
Copyright © 2013 Cyber. Security Malaysia
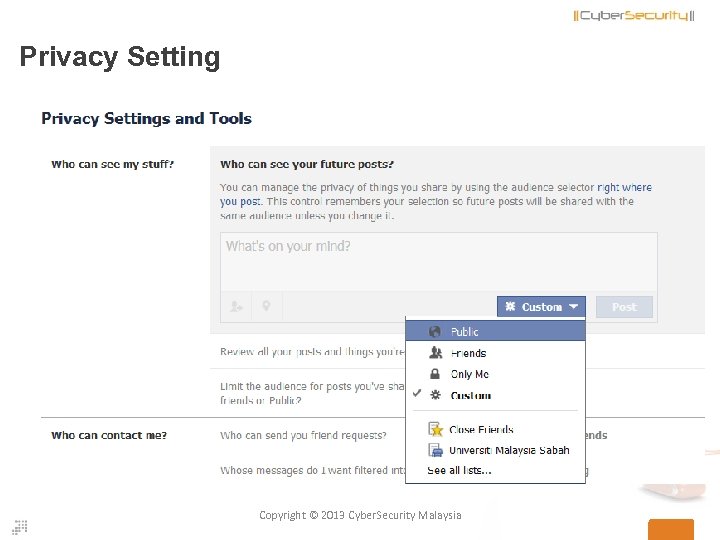 Privacy Setting Copyright © 2013 Cyber. Security Malaysia
Privacy Setting Copyright © 2013 Cyber. Security Malaysia
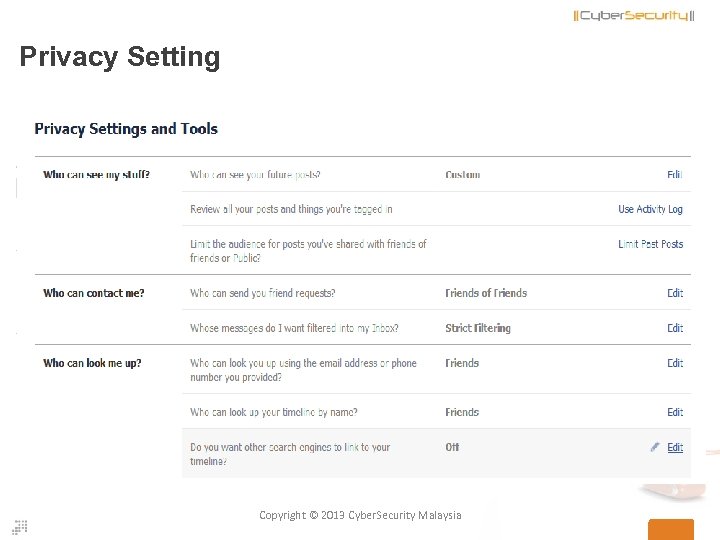 Privacy Setting Copyright © 2013 Cyber. Security Malaysia
Privacy Setting Copyright © 2013 Cyber. Security Malaysia
 Hack Me #8 – Instant Messaging & Web Cam Webcam Copyright © 2013 Cyber. Security Malaysia
Hack Me #8 – Instant Messaging & Web Cam Webcam Copyright © 2013 Cyber. Security Malaysia
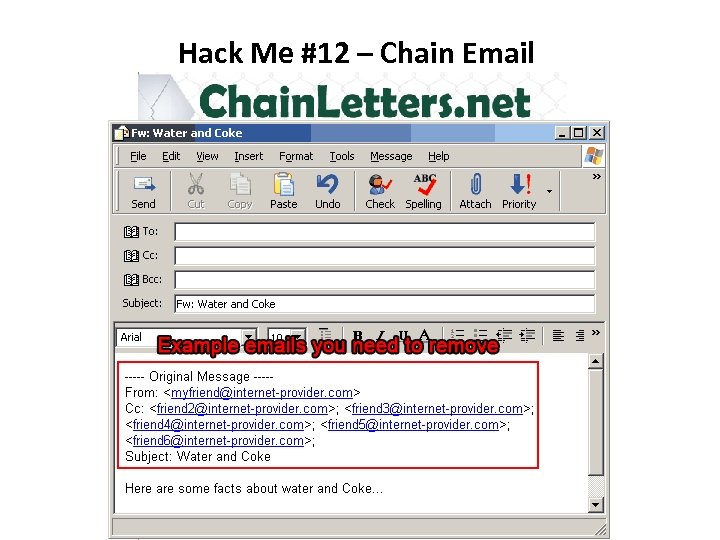 Hack Me #12 – Chain Email
Hack Me #12 – Chain Email
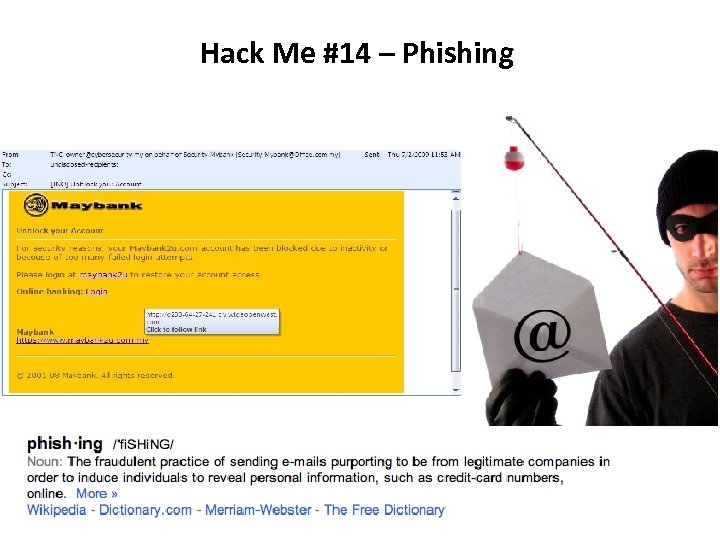 Hack Me #14 – Phishing
Hack Me #14 – Phishing
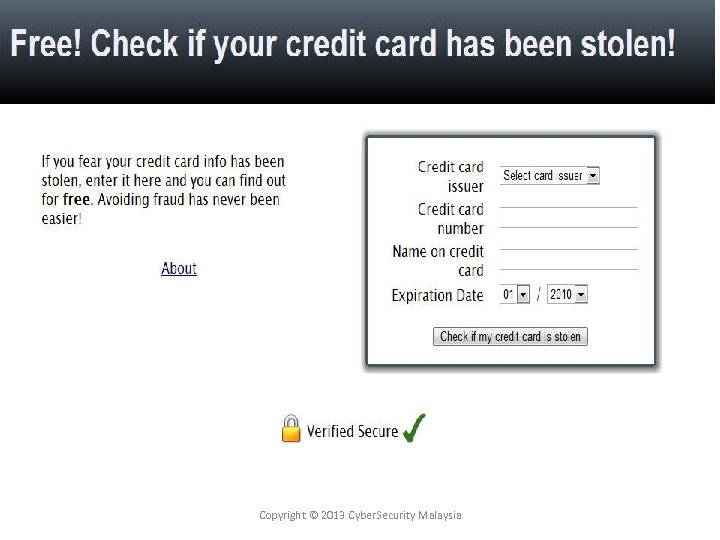 Copyright © 2013 Cyber. Security Malaysia
Copyright © 2013 Cyber. Security Malaysia
 Don’t Phish Me Copyright © 2013 Cyber. Security Malaysia
Don’t Phish Me Copyright © 2013 Cyber. Security Malaysia
 Hack Me #13 – Device Repairs Copyright © 2013 Cyber. Security Malaysia
Hack Me #13 – Device Repairs Copyright © 2013 Cyber. Security Malaysia
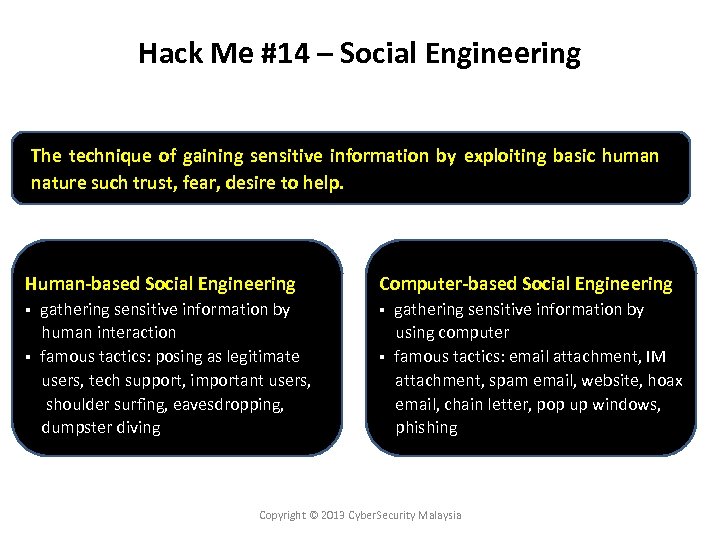 Hack Me #14 – Social Engineering The technique of gaining sensitive information by exploiting basic human nature such trust, fear, desire to help. Human-based Social Engineering Computer-based Social Engineering gathering sensitive information by human interaction § famous tactics: posing as legitimate users, tech support, important users, shoulder surfing, eavesdropping, dumpster diving § § gathering sensitive information by using computer § famous tactics: email attachment, IM attachment, spam email, website, hoax email, chain letter, pop up windows, phishing Copyright © 2013 Cyber. Security Malaysia
Hack Me #14 – Social Engineering The technique of gaining sensitive information by exploiting basic human nature such trust, fear, desire to help. Human-based Social Engineering Computer-based Social Engineering gathering sensitive information by human interaction § famous tactics: posing as legitimate users, tech support, important users, shoulder surfing, eavesdropping, dumpster diving § § gathering sensitive information by using computer § famous tactics: email attachment, IM attachment, spam email, website, hoax email, chain letter, pop up windows, phishing Copyright © 2013 Cyber. Security Malaysia
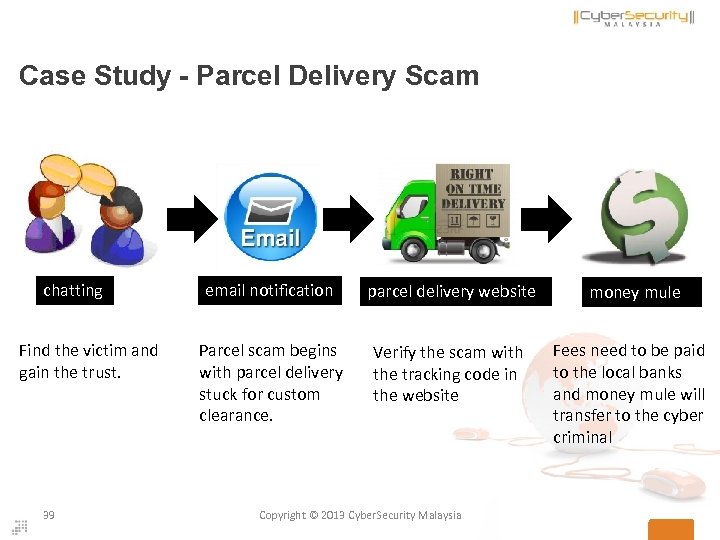 Case Study - Parcel Delivery Scam chatting Find the victim and gain the trust. 39 email notification parcel delivery website Parcel scam begins with parcel delivery stuck for custom clearance. Verify the scam with the tracking code in the website Copyright © 2013 Cyber. Security Malaysia money mule Fees need to be paid to the local banks and money mule will transfer to the cyber criminal
Case Study - Parcel Delivery Scam chatting Find the victim and gain the trust. 39 email notification parcel delivery website Parcel scam begins with parcel delivery stuck for custom clearance. Verify the scam with the tracking code in the website Copyright © 2013 Cyber. Security Malaysia money mule Fees need to be paid to the local banks and money mule will transfer to the cyber criminal
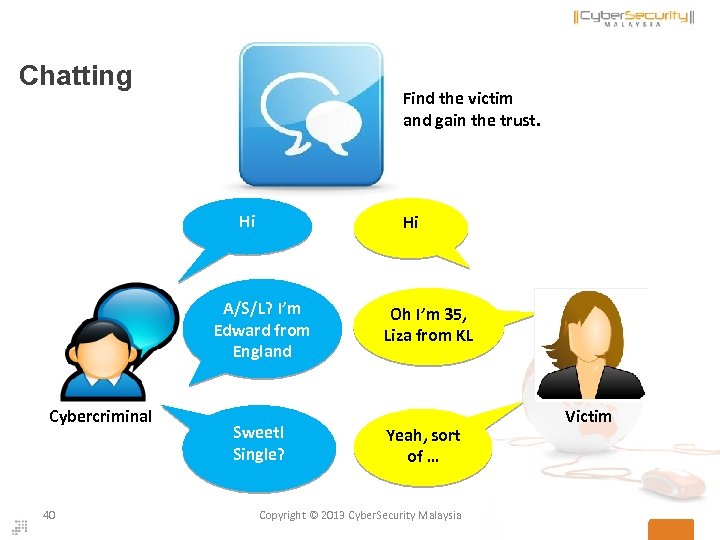 Chatting Find the victim and gain the trust. Hi Hi A/S/L? I’m Edward from England Cybercriminal 40 Sweet! Single? Oh I’m 35, Liza from KL Yeah, sort of … Copyright © 2013 Cyber. Security Malaysia Victim
Chatting Find the victim and gain the trust. Hi Hi A/S/L? I’m Edward from England Cybercriminal 40 Sweet! Single? Oh I’m 35, Liza from KL Yeah, sort of … Copyright © 2013 Cyber. Security Malaysia Victim
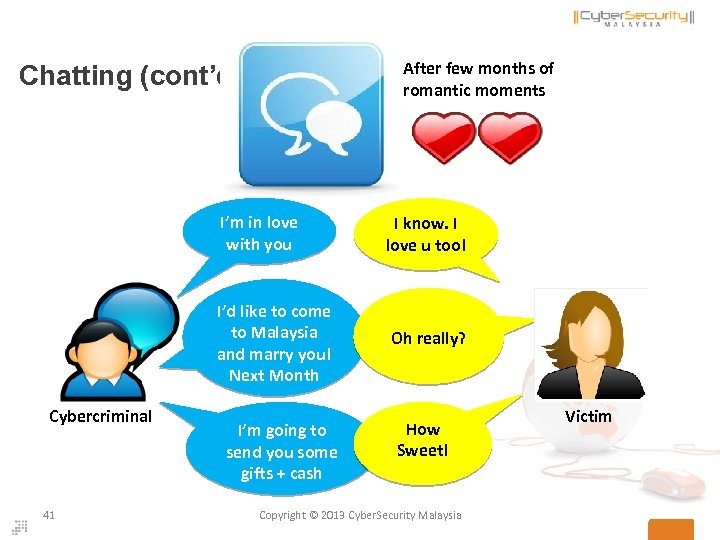 After few months of romantic moments Chatting (cont’d) I’m in love with you I’d like to come to Malaysia and marry you! Next Month Cybercriminal 41 I know. I love u too! Oh really? I’m going to send you some gifts + cash How Sweet! Copyright © 2013 Cyber. Security Malaysia Victim
After few months of romantic moments Chatting (cont’d) I’m in love with you I’d like to come to Malaysia and marry you! Next Month Cybercriminal 41 I know. I love u too! Oh really? I’m going to send you some gifts + cash How Sweet! Copyright © 2013 Cyber. Security Malaysia Victim
 Email Notification From: Pro-Link International Express Courier
Email Notification From: Pro-Link International Express Courier
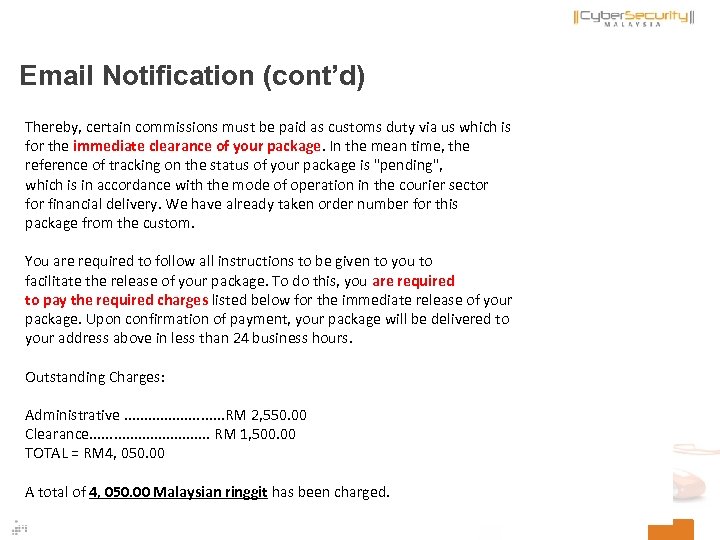 Email Notification (cont’d) Thereby, certain commissions must be paid as customs duty via us which is for the immediate clearance of your package. In the mean time, the reference of tracking on the status of your package is "pending", which is in accordance with the mode of operation in the courier sector financial delivery. We have already taken order number for this package from the custom. You are required to follow all instructions to be given to you to facilitate the release of your package. To do this, you are required to pay the required charges listed below for the immediate release of your package. Upon confirmation of payment, your package will be delivered to your address above in less than 24 business hours. Outstanding Charges: Administrative. . . RM 2, 550. 00 Clearance. . . . RM 1, 500. 00 TOTAL = RM 4, 050. 00 A total of 4, 050. 00 Malaysian ringgit has been charged. 43 Copyright © 2011 Cyber. Security Malaysia
Email Notification (cont’d) Thereby, certain commissions must be paid as customs duty via us which is for the immediate clearance of your package. In the mean time, the reference of tracking on the status of your package is "pending", which is in accordance with the mode of operation in the courier sector financial delivery. We have already taken order number for this package from the custom. You are required to follow all instructions to be given to you to facilitate the release of your package. To do this, you are required to pay the required charges listed below for the immediate release of your package. Upon confirmation of payment, your package will be delivered to your address above in less than 24 business hours. Outstanding Charges: Administrative. . . RM 2, 550. 00 Clearance. . . . RM 1, 500. 00 TOTAL = RM 4, 050. 00 A total of 4, 050. 00 Malaysian ringgit has been charged. 43 Copyright © 2011 Cyber. Security Malaysia
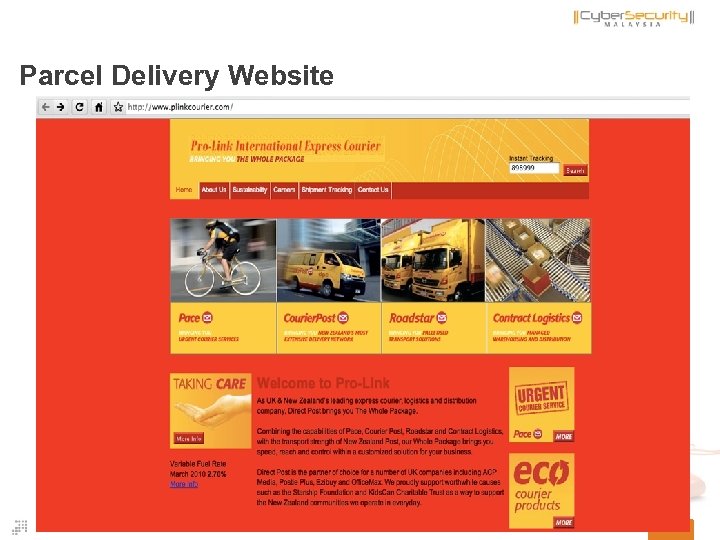 Parcel Delivery Website 44 Copyright © 2011 Cyber. Security Malaysia
Parcel Delivery Website 44 Copyright © 2011 Cyber. Security Malaysia
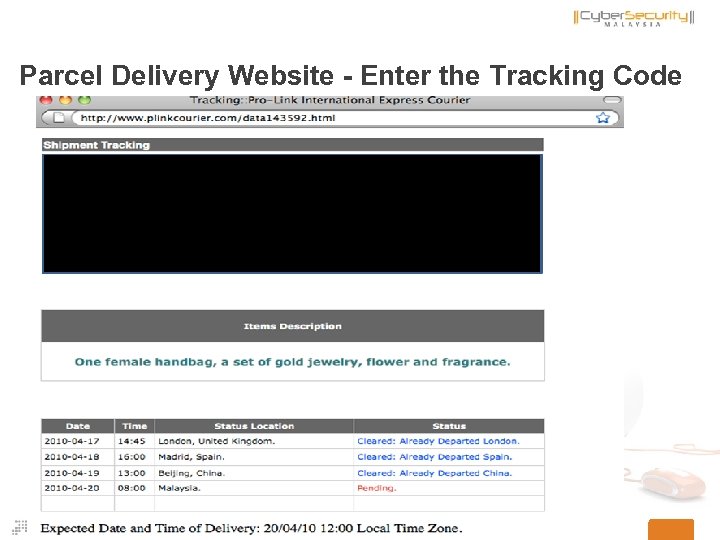 Parcel Delivery Website - Enter the Tracking Code 45 Copyright © 2011 Cyber. Security Malaysia
Parcel Delivery Website - Enter the Tracking Code 45 Copyright © 2011 Cyber. Security Malaysia
 End Message
End Message
 THANK YOU for listening Jazannul Azriq Aripin Senior Executive Outreach, Cyber. Security Malaysia Email : azriq@cybersecurity. my website : www. cybersafe. my inquiry : cybersafe@cybersecurity. my reporting : cyber 999@cybersecurity. my 47 Copyright © 2010 Cyber. Security Malaysia
THANK YOU for listening Jazannul Azriq Aripin Senior Executive Outreach, Cyber. Security Malaysia Email : azriq@cybersecurity. my website : www. cybersafe. my inquiry : cybersafe@cybersecurity. my reporting : cyber 999@cybersecurity. my 47 Copyright © 2010 Cyber. Security Malaysia
 48
48


