fa9976ad123dbdc7748a795cf28a405a.ppt
- Количество слайдов: 21
 Avaya Security Overview Andy Zmolek Senior Manager, Security Planning and Strategy © 2005 Avaya Inc. All rights reserved.
Avaya Security Overview Andy Zmolek Senior Manager, Security Planning and Strategy © 2005 Avaya Inc. All rights reserved.
 Agenda Introductions – Group Overview Security Strategy & Evolution “Secure by Default” within Avaya Products – Advisories: Staying Informed of the latest vulnerabilities – Product Security Standards © 2005 Avaya Inc. All rights reserved. Proprietary and Confidential: Do NOT distribute 2
Agenda Introductions – Group Overview Security Strategy & Evolution “Secure by Default” within Avaya Products – Advisories: Staying Informed of the latest vulnerabilities – Product Security Standards © 2005 Avaya Inc. All rights reserved. Proprietary and Confidential: Do NOT distribute 2
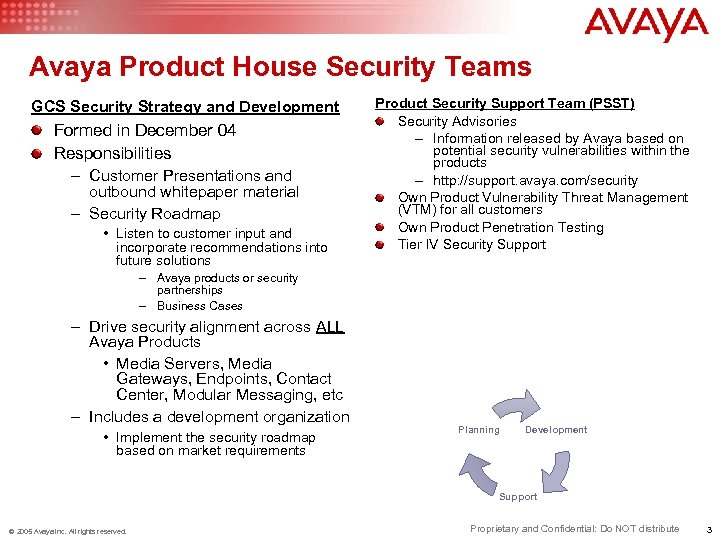 Avaya Product House Security Teams GCS Security Strategy and Development Formed in December 04 Responsibilities – Customer Presentations and outbound whitepaper material – Security Roadmap • Listen to customer input and incorporate recommendations into future solutions Product Security Support Team (PSST) Security Advisories – Information released by Avaya based on potential security vulnerabilities within the products – http: //support. avaya. com/security Own Product Vulnerability Threat Management (VTM) for all customers Own Product Penetration Testing Tier IV Security Support – Avaya products or security partnerships – Business Cases – Drive security alignment across ALL Avaya Products • Media Servers, Media Gateways, Endpoints, Contact Center, Modular Messaging, etc – Includes a development organization • Implement the security roadmap based on market requirements Planning Development Support © 2005 Avaya Inc. All rights reserved. Proprietary and Confidential: Do NOT distribute 3
Avaya Product House Security Teams GCS Security Strategy and Development Formed in December 04 Responsibilities – Customer Presentations and outbound whitepaper material – Security Roadmap • Listen to customer input and incorporate recommendations into future solutions Product Security Support Team (PSST) Security Advisories – Information released by Avaya based on potential security vulnerabilities within the products – http: //support. avaya. com/security Own Product Vulnerability Threat Management (VTM) for all customers Own Product Penetration Testing Tier IV Security Support – Avaya products or security partnerships – Business Cases – Drive security alignment across ALL Avaya Products • Media Servers, Media Gateways, Endpoints, Contact Center, Modular Messaging, etc – Includes a development organization • Implement the security roadmap based on market requirements Planning Development Support © 2005 Avaya Inc. All rights reserved. Proprietary and Confidential: Do NOT distribute 3
 Avaya Strategy © 2005 Avaya Inc. All rights reserved.
Avaya Strategy © 2005 Avaya Inc. All rights reserved.
 Security Trends and Issues Business Continuity is impacted by Security Vulnerabilities Sophistication of threats are evolving – severity of vulnerabilities are increasing – Time of infection is very fast requiring IT to react much faster – The motive and intent is changing – moving from notoriety to financial gain • Exploit (June 06): “A Miami man allegedly defrauded Internet voice providers to the tune of $1 million, with a sophisticated hacking scheme. ” 1 – Vo. IP and Telephony applications as new targets, no longer just collateral damage Mobility and always-on networks add to propagation of threats Enterprises are strengthening their security guidelines and policies – Influence from Government regulations (HIPAA, GLBA, and SOX) Security must be pervasive (End-to-End) Note 1: http: //www. networkcomputing. com/article/print. Full. Article. jhtml? article. ID=188702999 © 2005 Avaya Inc. All rights reserved. Proprietary and Confidential: Do NOT distribute 5
Security Trends and Issues Business Continuity is impacted by Security Vulnerabilities Sophistication of threats are evolving – severity of vulnerabilities are increasing – Time of infection is very fast requiring IT to react much faster – The motive and intent is changing – moving from notoriety to financial gain • Exploit (June 06): “A Miami man allegedly defrauded Internet voice providers to the tune of $1 million, with a sophisticated hacking scheme. ” 1 – Vo. IP and Telephony applications as new targets, no longer just collateral damage Mobility and always-on networks add to propagation of threats Enterprises are strengthening their security guidelines and policies – Influence from Government regulations (HIPAA, GLBA, and SOX) Security must be pervasive (End-to-End) Note 1: http: //www. networkcomputing. com/article/print. Full. Article. jhtml? article. ID=188702999 © 2005 Avaya Inc. All rights reserved. Proprietary and Confidential: Do NOT distribute 5
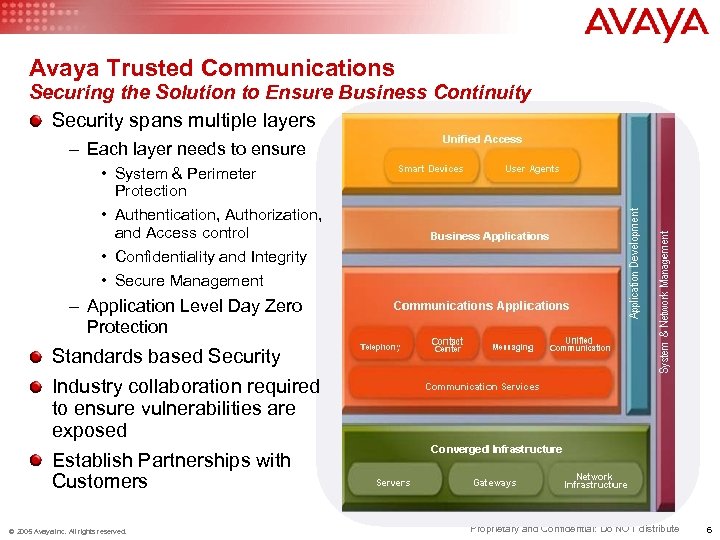 Avaya Trusted Communications Securing the Solution to Ensure Business Continuity Security spans multiple layers – Each layer needs to ensure • System & Perimeter Protection • Authentication, Authorization, and Access control • Confidentiality and Integrity • Secure Management – Application Level Day Zero Protection Standards based Security Industry collaboration required to ensure vulnerabilities are exposed Establish Partnerships with Customers © 2005 Avaya Inc. All rights reserved. Proprietary and Confidential: Do NOT distribute 6
Avaya Trusted Communications Securing the Solution to Ensure Business Continuity Security spans multiple layers – Each layer needs to ensure • System & Perimeter Protection • Authentication, Authorization, and Access control • Confidentiality and Integrity • Secure Management – Application Level Day Zero Protection Standards based Security Industry collaboration required to ensure vulnerabilities are exposed Establish Partnerships with Customers © 2005 Avaya Inc. All rights reserved. Proprietary and Confidential: Do NOT distribute 6
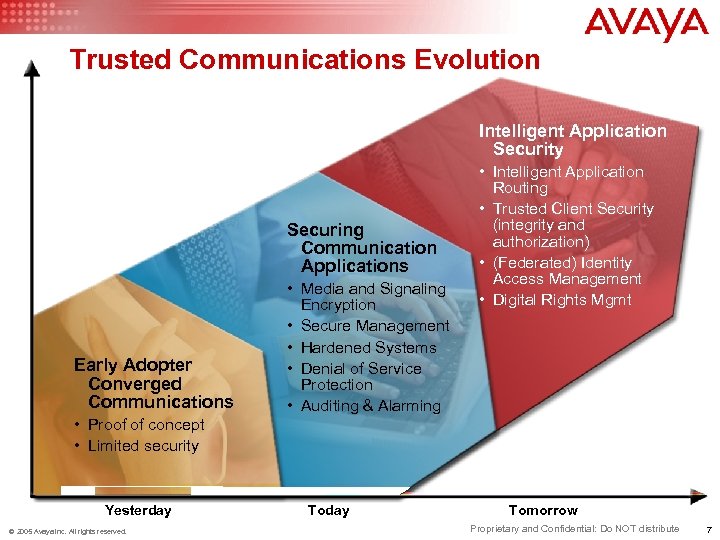 Trusted Communications Evolution Intelligent Application Security Securing Communication Applications Early Adopter Converged Communications • Media and Signaling Encryption • Secure Management • Hardened Systems • Denial of Service Protection • Auditing & Alarming • Intelligent Application Routing • Trusted Client Security (integrity and authorization) • (Federated) Identity Access Management • Digital Rights Mgmt • Proof of concept • Limited security Yesterday © 2005 Avaya Inc. All rights reserved. Today Tomorrow Proprietary and Confidential: Do NOT distribute 7
Trusted Communications Evolution Intelligent Application Security Securing Communication Applications Early Adopter Converged Communications • Media and Signaling Encryption • Secure Management • Hardened Systems • Denial of Service Protection • Auditing & Alarming • Intelligent Application Routing • Trusted Client Security (integrity and authorization) • (Federated) Identity Access Management • Digital Rights Mgmt • Proof of concept • Limited security Yesterday © 2005 Avaya Inc. All rights reserved. Today Tomorrow Proprietary and Confidential: Do NOT distribute 7
 Product Security Functionality © 2005 Avaya Inc. All rights reserved.
Product Security Functionality © 2005 Avaya Inc. All rights reserved.
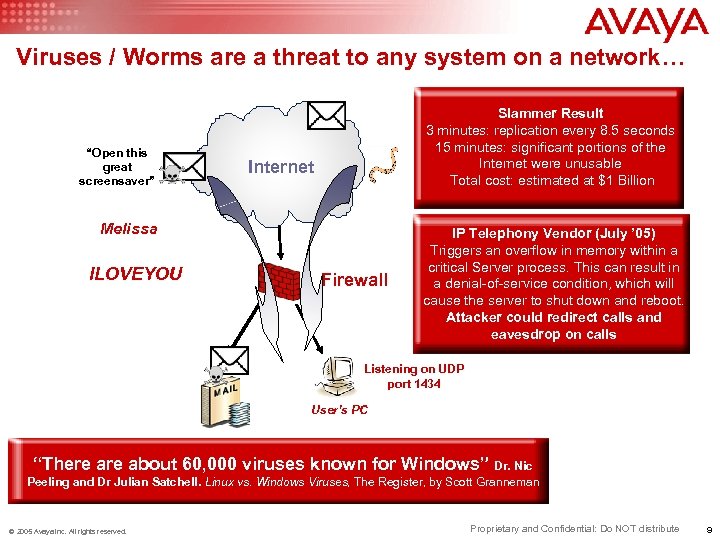 Viruses / Worms are a threat to any system on a network… “Open this great screensaver” Slammer Result 3 minutes: replication every 8. 5 seconds 15 minutes: significant portions of the Internet were unusable Total cost: estimated at $1 Billion Internet Melissa ILOVEYOU Firewall IP Telephony Vendor (July ’ 05) Triggers an overflow in memory within a critical Server process. This can result in a denial-of-service condition, which will cause the server to shut down and reboot. Attacker could redirect calls and eavesdrop on calls Listening on UDP port 1434 User’s PC “There about 60, 000 viruses known for Windows” Dr. Nic Peeling and Dr Julian Satchell. Linux vs. Windows Viruses, The Register, by Scott Granneman © 2005 Avaya Inc. All rights reserved. Proprietary and Confidential: Do NOT distribute 9
Viruses / Worms are a threat to any system on a network… “Open this great screensaver” Slammer Result 3 minutes: replication every 8. 5 seconds 15 minutes: significant portions of the Internet were unusable Total cost: estimated at $1 Billion Internet Melissa ILOVEYOU Firewall IP Telephony Vendor (July ’ 05) Triggers an overflow in memory within a critical Server process. This can result in a denial-of-service condition, which will cause the server to shut down and reboot. Attacker could redirect calls and eavesdrop on calls Listening on UDP port 1434 User’s PC “There about 60, 000 viruses known for Windows” Dr. Nic Peeling and Dr Julian Satchell. Linux vs. Windows Viruses, The Register, by Scott Granneman © 2005 Avaya Inc. All rights reserved. Proprietary and Confidential: Do NOT distribute 9
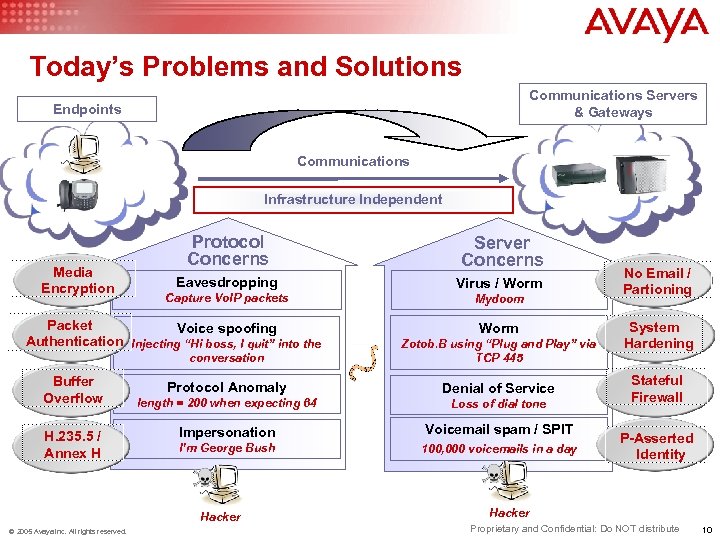 Today’s Problems and Solutions Communications Servers & Gateways Endpoints Communications Infrastructure Independent Media Encryption Protocol Concerns Server Concerns Eavesdropping Virus / Worm Capture Vo. IP packets Mydoom Packet Voice spoofing Authentication Injecting “Hi boss, I quit” into the Worm conversation Buffer Overflow H. 235. 5 / Annex H Zotob. B using “Plug and Play” via TCP 445 Protocol Anomaly Denial of Service length = 200 when expecting 64 Loss of dial tone Impersonation Voicemail spam / SPIT I’m George Bush 100, 000 voicemails in a day Hacker © 2005 Avaya Inc. All rights reserved. No Email / Partioning System Hardening Stateful Firewall P-Asserted Identity Hacker Proprietary and Confidential: Do NOT distribute 10
Today’s Problems and Solutions Communications Servers & Gateways Endpoints Communications Infrastructure Independent Media Encryption Protocol Concerns Server Concerns Eavesdropping Virus / Worm Capture Vo. IP packets Mydoom Packet Voice spoofing Authentication Injecting “Hi boss, I quit” into the Worm conversation Buffer Overflow H. 235. 5 / Annex H Zotob. B using “Plug and Play” via TCP 445 Protocol Anomaly Denial of Service length = 200 when expecting 64 Loss of dial tone Impersonation Voicemail spam / SPIT I’m George Bush 100, 000 voicemails in a day Hacker © 2005 Avaya Inc. All rights reserved. No Email / Partioning System Hardening Stateful Firewall P-Asserted Identity Hacker Proprietary and Confidential: Do NOT distribute 10
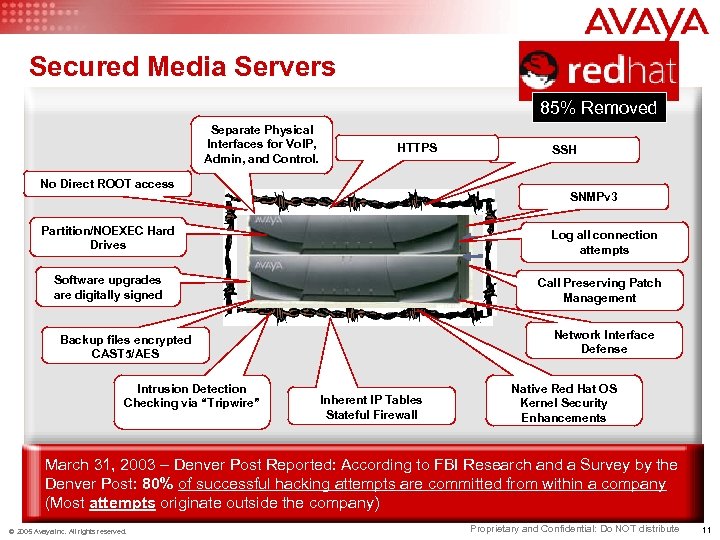 Secured Media Servers 85% Removed Separate Physical Interfaces for Vo. IP, Admin, and Control. HTTPS No Direct ROOT access SNMPv 3 Partition/NOEXEC Hard Drives Log all connection attempts Software upgrades are digitally signed Call Preserving Patch Management Network Interface Defense Backup files encrypted CAST 5/AES Intrusion Detection Checking via “Tripwire” SSH Inherent IP Tables Stateful Firewall Native Red Hat OS Kernel Security Enhancements March 31, 2003 – Denver Post Reported: According to FBI Research and a Survey by the Denver Post: 80% of successful hacking attempts are committed from within a company (Most attempts originate outside the company) © 2005 Avaya Inc. All rights reserved. Proprietary and Confidential: Do NOT distribute 11
Secured Media Servers 85% Removed Separate Physical Interfaces for Vo. IP, Admin, and Control. HTTPS No Direct ROOT access SNMPv 3 Partition/NOEXEC Hard Drives Log all connection attempts Software upgrades are digitally signed Call Preserving Patch Management Network Interface Defense Backup files encrypted CAST 5/AES Intrusion Detection Checking via “Tripwire” SSH Inherent IP Tables Stateful Firewall Native Red Hat OS Kernel Security Enhancements March 31, 2003 – Denver Post Reported: According to FBI Research and a Survey by the Denver Post: 80% of successful hacking attempts are committed from within a company (Most attempts originate outside the company) © 2005 Avaya Inc. All rights reserved. Proprietary and Confidential: Do NOT distribute 11
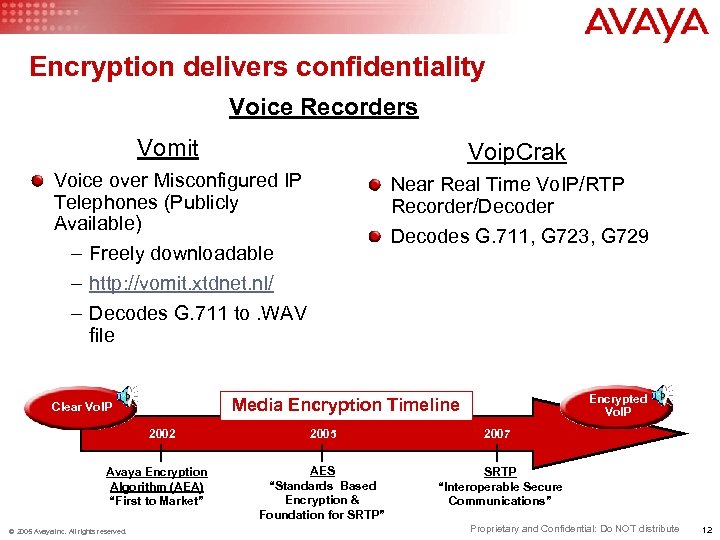 Encryption delivers confidentiality Voice Recorders Vomit Voip. Crak Voice over Misconfigured IP Telephones (Publicly Available) – Freely downloadable – http: //vomit. xtdnet. nl/ – Decodes G. 711 to. WAV file Encrypted Vo. IP Media Encryption Timeline Clear Vo. IP 2002 Avaya Encryption Algorithm (AEA) “First to Market” © 2005 Avaya Inc. All rights reserved. Near Real Time Vo. IP/RTP Recorder/Decoder Decodes G. 711, G 723, G 729 2005 2007 AES “Standards Based Encryption & Foundation for SRTP” SRTP “Interoperable Secure Communications” Proprietary and Confidential: Do NOT distribute 12
Encryption delivers confidentiality Voice Recorders Vomit Voip. Crak Voice over Misconfigured IP Telephones (Publicly Available) – Freely downloadable – http: //vomit. xtdnet. nl/ – Decodes G. 711 to. WAV file Encrypted Vo. IP Media Encryption Timeline Clear Vo. IP 2002 Avaya Encryption Algorithm (AEA) “First to Market” © 2005 Avaya Inc. All rights reserved. Near Real Time Vo. IP/RTP Recorder/Decoder Decodes G. 711, G 723, G 729 2005 2007 AES “Standards Based Encryption & Foundation for SRTP” SRTP “Interoperable Secure Communications” Proprietary and Confidential: Do NOT distribute 12
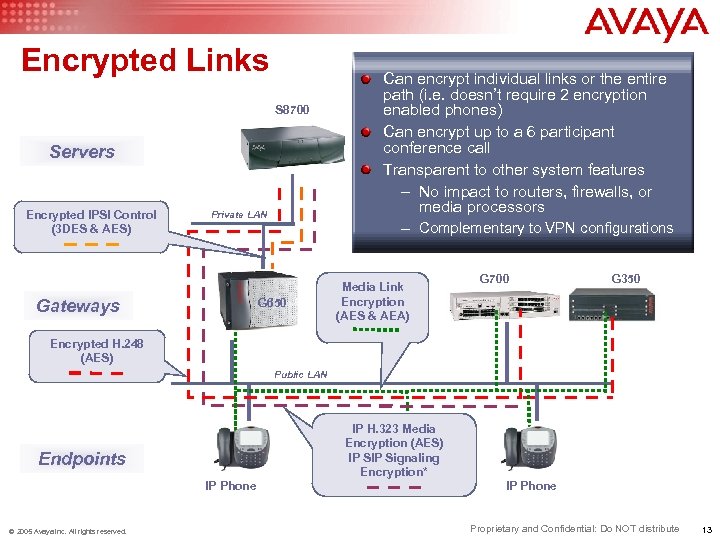 Encrypted Links S 8700 Servers Encrypted IPSI Control (3 DES & AES) Private LAN Gateways G 650 Can encrypt individual links or the entire path (i. e. doesn’t require 2 encryption enabled phones) Can encrypt up to a 6 participant conference call Transparent to other system features – No impact to routers, firewalls, or media processors – Complementary to VPN configurations Media Link Encryption (AES & AEA) G 700 G 350 Encrypted H. 248 (AES) Public LAN IP H. 323 Media Encryption (AES) IP Signaling Encryption* Endpoints IP Phone © 2005 Avaya Inc. All rights reserved. IP Phone Proprietary and Confidential: Do NOT distribute 13
Encrypted Links S 8700 Servers Encrypted IPSI Control (3 DES & AES) Private LAN Gateways G 650 Can encrypt individual links or the entire path (i. e. doesn’t require 2 encryption enabled phones) Can encrypt up to a 6 participant conference call Transparent to other system features – No impact to routers, firewalls, or media processors – Complementary to VPN configurations Media Link Encryption (AES & AEA) G 700 G 350 Encrypted H. 248 (AES) Public LAN IP H. 323 Media Encryption (AES) IP Signaling Encryption* Endpoints IP Phone © 2005 Avaya Inc. All rights reserved. IP Phone Proprietary and Confidential: Do NOT distribute 13
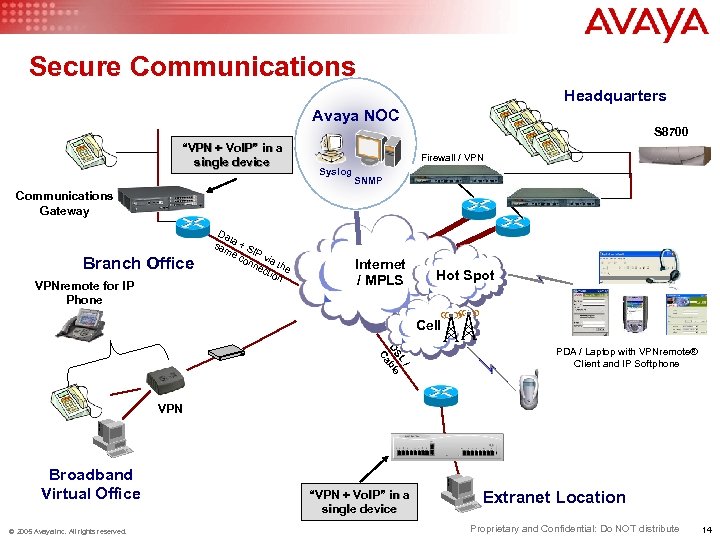 Secure Communications Headquarters Avaya NOC S 8700 “VPN + Vo. IP” in a single device Firewall / VPN Syslog SNMP Communications Gateway Branch Office VPNremote for IP Phone Da t sam a + S e c IP v on ia t ne ctio he n Internet / MPLS Hot Spot Cell / L DS ble Ca PDA / Laptop with VPNremote® Client and IP Softphone VPN Broadband Virtual Office © 2005 Avaya Inc. All rights reserved. “VPN + Vo. IP” in a single device Extranet Location Proprietary and Confidential: Do NOT distribute 14
Secure Communications Headquarters Avaya NOC S 8700 “VPN + Vo. IP” in a single device Firewall / VPN Syslog SNMP Communications Gateway Branch Office VPNremote for IP Phone Da t sam a + S e c IP v on ia t ne ctio he n Internet / MPLS Hot Spot Cell / L DS ble Ca PDA / Laptop with VPNremote® Client and IP Softphone VPN Broadband Virtual Office © 2005 Avaya Inc. All rights reserved. “VPN + Vo. IP” in a single device Extranet Location Proprietary and Confidential: Do NOT distribute 14
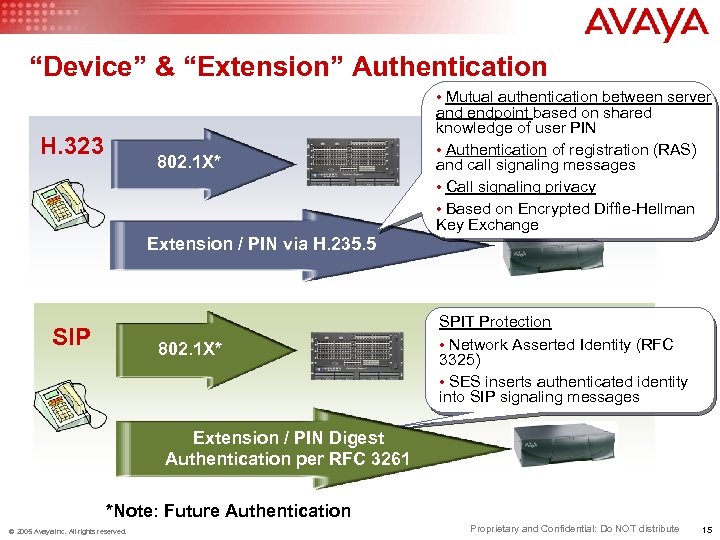 “Device” & “Extension” Authentication • Mutual authentication between server H. 323 802. 1 X* and endpoint based on shared knowledge of user PIN • Authentication of registration (RAS) and call signaling messages • Call signaling privacy • Based on Encrypted Diffie-Hellman Key Exchange Extension / PIN via H. 235. 5 SIP 802. 1 X* SPIT Protection • Network Asserted Identity (RFC 3325) • SES inserts authenticated identity into SIP signaling messages Extension / PIN Digest Authentication per RFC 3261 *Note: Future Authentication © 2005 Avaya Inc. All rights reserved. Proprietary and Confidential: Do NOT distribute 15
“Device” & “Extension” Authentication • Mutual authentication between server H. 323 802. 1 X* and endpoint based on shared knowledge of user PIN • Authentication of registration (RAS) and call signaling messages • Call signaling privacy • Based on Encrypted Diffie-Hellman Key Exchange Extension / PIN via H. 235. 5 SIP 802. 1 X* SPIT Protection • Network Asserted Identity (RFC 3325) • SES inserts authenticated identity into SIP signaling messages Extension / PIN Digest Authentication per RFC 3261 *Note: Future Authentication © 2005 Avaya Inc. All rights reserved. Proprietary and Confidential: Do NOT distribute 15
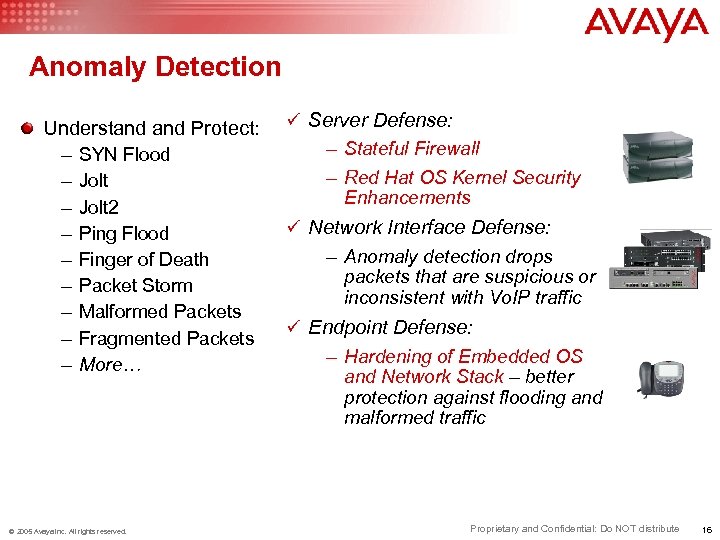 Anomaly Detection Understand Protect: – SYN Flood – Jolt 2 – Ping Flood – Finger of Death – Packet Storm – Malformed Packets – Fragmented Packets – More… © 2005 Avaya Inc. All rights reserved. ü Server Defense: – Stateful Firewall – Red Hat OS Kernel Security Enhancements ü Network Interface Defense: – Anomaly detection drops packets that are suspicious or inconsistent with Vo. IP traffic ü Endpoint Defense: – Hardening of Embedded OS and Network Stack – better protection against flooding and malformed traffic Proprietary and Confidential: Do NOT distribute 16
Anomaly Detection Understand Protect: – SYN Flood – Jolt 2 – Ping Flood – Finger of Death – Packet Storm – Malformed Packets – Fragmented Packets – More… © 2005 Avaya Inc. All rights reserved. ü Server Defense: – Stateful Firewall – Red Hat OS Kernel Security Enhancements ü Network Interface Defense: – Anomaly detection drops packets that are suspicious or inconsistent with Vo. IP traffic ü Endpoint Defense: – Hardening of Embedded OS and Network Stack – better protection against flooding and malformed traffic Proprietary and Confidential: Do NOT distribute 16
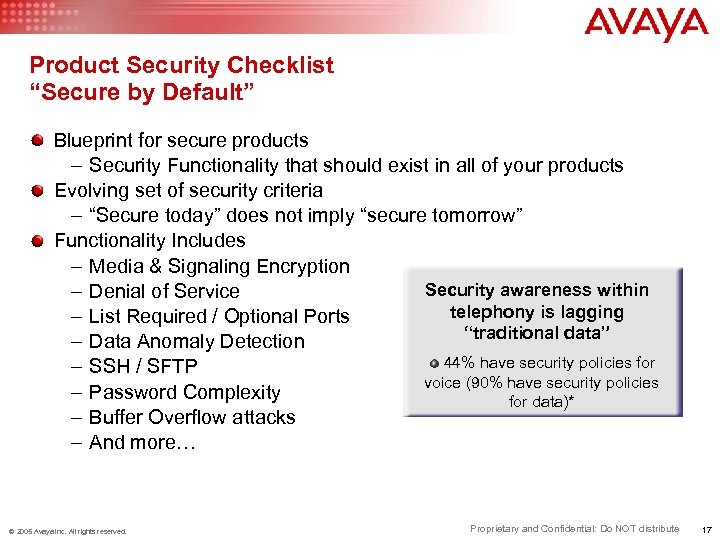 Product Security Checklist “Secure by Default” Blueprint for secure products – Security Functionality that should exist in all of your products Evolving set of security criteria – “Secure today” does not imply “secure tomorrow” Functionality Includes – Media & Signaling Encryption Security awareness within – Denial of Service telephony is lagging – List Required / Optional Ports “traditional data” – Data Anomaly Detection 44% have security policies for – SSH / SFTP voice (90% have security policies – Password Complexity for data)* – Buffer Overflow attacks – And more… © 2005 Avaya Inc. All rights reserved. Proprietary and Confidential: Do NOT distribute 17
Product Security Checklist “Secure by Default” Blueprint for secure products – Security Functionality that should exist in all of your products Evolving set of security criteria – “Secure today” does not imply “secure tomorrow” Functionality Includes – Media & Signaling Encryption Security awareness within – Denial of Service telephony is lagging – List Required / Optional Ports “traditional data” – Data Anomaly Detection 44% have security policies for – SSH / SFTP voice (90% have security policies – Password Complexity for data)* – Buffer Overflow attacks – And more… © 2005 Avaya Inc. All rights reserved. Proprietary and Confidential: Do NOT distribute 17
 Security Partnerships © 2005 Avaya Inc. All rights reserved. Proprietary and Confidential: Do NOT distribute 18
Security Partnerships © 2005 Avaya Inc. All rights reserved. Proprietary and Confidential: Do NOT distribute 18
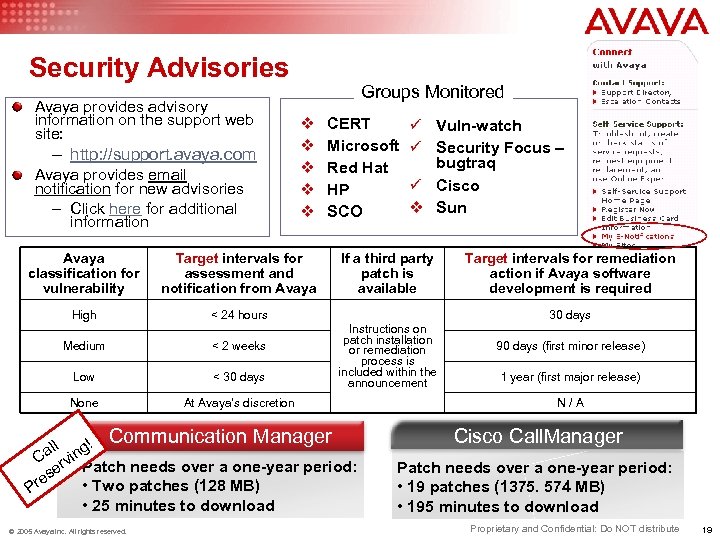 Security Advisories Avaya provides advisory information on the support web site: – http: //support. avaya. com Avaya provides email notification for new advisories – Click here for additional information Groups Monitored v v v Avaya classification for vulnerability Target intervals for assessment and notification from Avaya High CERT Microsoft Red Hat HP SCO ü Vuln-watch ü Security Focus – bugtraq ü Cisco v Sun < 24 hours Medium < 2 weeks Low < 30 days None If a third party patch is available 30 days Instructions on patch installation or remediation process is included within the announcement At Avaya’s discretion Communication Manager ll ng! Ca rvi se Patch needs over a one-year period: re • Two patches (128 MB) P • 25 minutes to download © 2005 Avaya Inc. All rights reserved. Target intervals for remediation action if Avaya software development is required 90 days (first minor release) 1 year (first major release) N/A Cisco Call. Manager Patch needs over a one-year period: • 19 patches (1375. 574 MB) • 195 minutes to download Proprietary and Confidential: Do NOT distribute 19
Security Advisories Avaya provides advisory information on the support web site: – http: //support. avaya. com Avaya provides email notification for new advisories – Click here for additional information Groups Monitored v v v Avaya classification for vulnerability Target intervals for assessment and notification from Avaya High CERT Microsoft Red Hat HP SCO ü Vuln-watch ü Security Focus – bugtraq ü Cisco v Sun < 24 hours Medium < 2 weeks Low < 30 days None If a third party patch is available 30 days Instructions on patch installation or remediation process is included within the announcement At Avaya’s discretion Communication Manager ll ng! Ca rvi se Patch needs over a one-year period: re • Two patches (128 MB) P • 25 minutes to download © 2005 Avaya Inc. All rights reserved. Target intervals for remediation action if Avaya software development is required 90 days (first minor release) 1 year (first major release) N/A Cisco Call. Manager Patch needs over a one-year period: • 19 patches (1375. 574 MB) • 195 minutes to download Proprietary and Confidential: Do NOT distribute 19
 Summary Security Evolution Security is evolving – Security Focus needs to expand beyond Infrastructure Security – Application Security is required Secure by Design Security is “built in” instead of “bolted on” – Includes standards based Encryption, Authentication, Denial of Service Partnerships 24 x 7 Ownership Deliver best of breed technology to enable secure communications Security is a 24 x 7 responsibility – Short Term Advisories To – Long Term Roadmaps End Goal © 2005 Avaya Inc. All rights reserved. Ensuring that disruption of service and / or theft are eliminated as vulnerabilities for IP Communications Proprietary and Confidential: Do NOT distribute 20
Summary Security Evolution Security is evolving – Security Focus needs to expand beyond Infrastructure Security – Application Security is required Secure by Design Security is “built in” instead of “bolted on” – Includes standards based Encryption, Authentication, Denial of Service Partnerships 24 x 7 Ownership Deliver best of breed technology to enable secure communications Security is a 24 x 7 responsibility – Short Term Advisories To – Long Term Roadmaps End Goal © 2005 Avaya Inc. All rights reserved. Ensuring that disruption of service and / or theft are eliminated as vulnerabilities for IP Communications Proprietary and Confidential: Do NOT distribute 20
 Thank You! © 2005 Avaya Inc. All rights reserved.
Thank You! © 2005 Avaya Inc. All rights reserved.


