cba3fce4a9de4776bc645f49f1543077.ppt
- Количество слайдов: 23

Automated Web Patrol with Strider Honey. Monkeys Present by Zhichun Li

Overview… • • • Problem @ hand. Proposed solution. Browser based vulnerabilities. The Honey. Monkey system. Evaluation. Questions & Discussion.

Problem @ hand… • Several attacks exploit browser vulnerabilities and install malware software. • E. g. – Download. Ject – Bofra – Xpire. info • Current state –manual analysis – Unable to scale. – Do not provide a comprehensive picture.

Proposed solution… • Active, client-side, VM – based honeypots called Strider Honey. Monkey. • Performs large-scale, systematic & automated web patrol. • Uses monkey programs of various OS level patches to mimic human browsing. • Adopts a state-management methodology. • Use of Strider Tracer.

Browser based vulnerability exploits… Code obfuscation URL redirection Vulnerability exploitation Malware installation

Code obfuscation… • Dynamic code injection – document. write() function inside a script. • Unreadable code – decoded using unescape() function. • Custom decoding routine. • Substring replacement using replace() function.

URL redirection… Secondary URL • Primary URL • Protocol redirection using HTTP 302 temporary redirect. • HTML tags. • Script functions including window. location. replace().

Vulnerability exploitation… • Exploiting of multiple browser vulnerabilities. • Owing to its popularity IE is attacked a lot. Malware installation… • Introduce some piece of arbitrary code on the victim machine in order to achieve a larger attack goal.
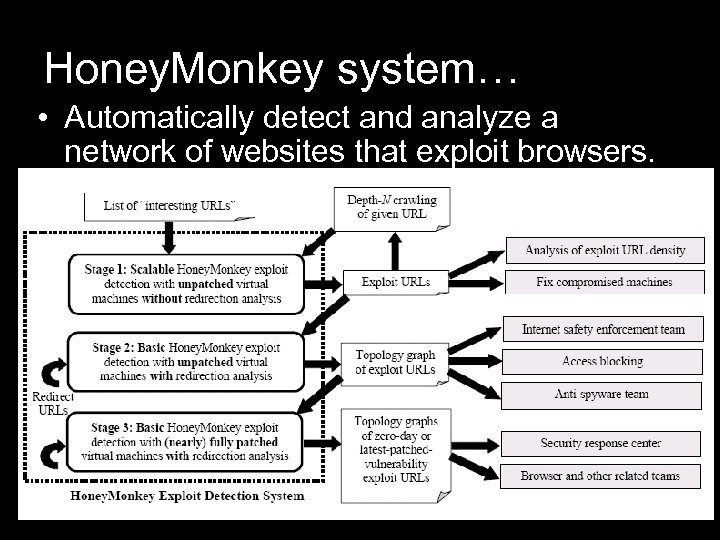
Honey. Monkey system… • Automatically detect and analyze a network of websites that exploit browsers.
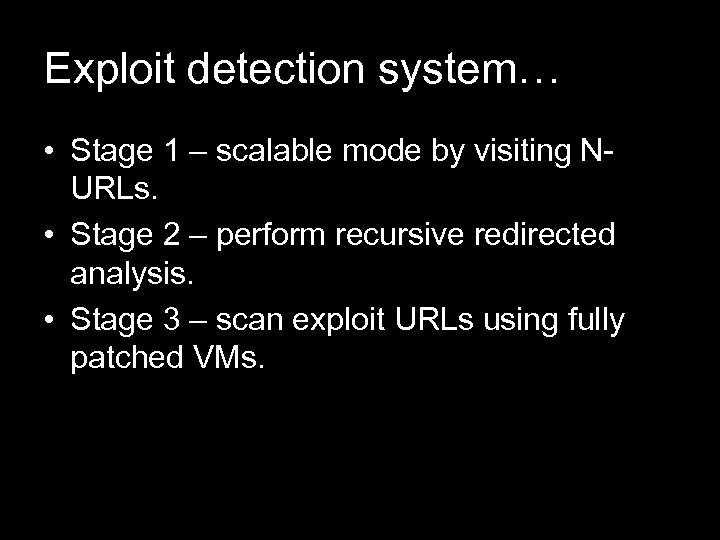
Exploit detection system… • Stage 1 – scalable mode by visiting NURLs. • Stage 2 – perform recursive redirected analysis. • Stage 3 – scan exploit URLs using fully patched VMs.
Exploit detection - XML report… • Executable files created or modified outside the browser sandbox folders. • Processes created. • Windows registry entries created or modified. • Vulnerability exploited. • Redirect-URLs visited.

Redirection analysis… • Stage 1 – act as front end content providers. • Traffic redirection – tracked with a BHO – Browser Helper Objects. • Recursive scanning. • Construction of topology graphs based on traffic redirection. • Identify web pages that actually perform the exploit and stop redirection.
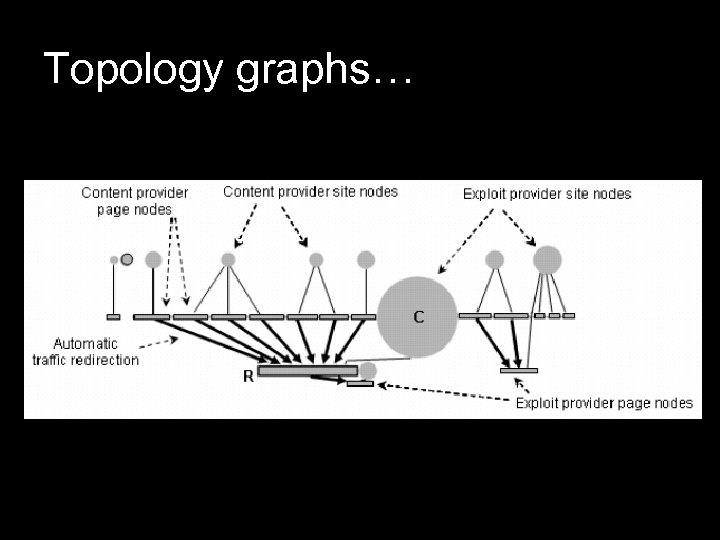
Topology graphs…
Anti-Exploit Process… • Generating Input URL Lists – source – Suspicious URLs for analysis. – Popular web sites – if attacked can potentially infect a large population. (measured search engines). – URLs of more localized scope – within organizations or based on history etc… • Acting on output exploit-URL data – Stage 1 – output-exploit-URLs. – Stage 2 – output-traffic-redirection topology graph. – Stage 3 – output-zero-day exploit URLs & topology graphs.
Overview… • • • Problem @ hand. Proposed solution. Browser based vulnerabilities. The Honey. Monkey system. Evaluation. Questions & Discussion.
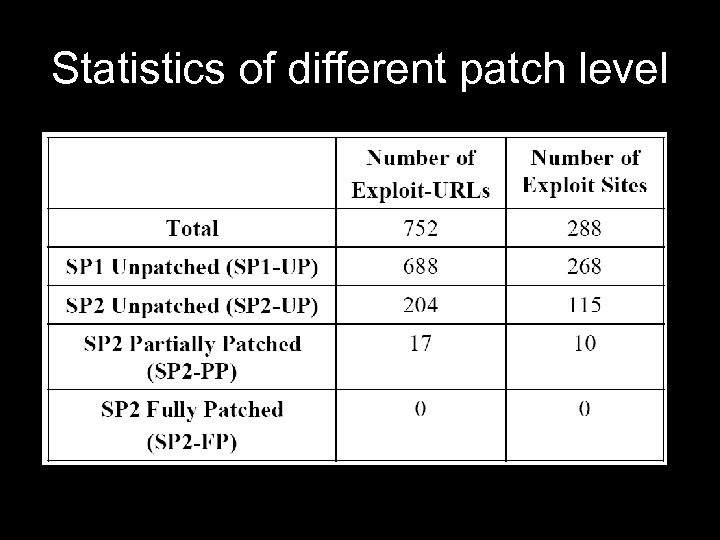
Statistics of different patch level
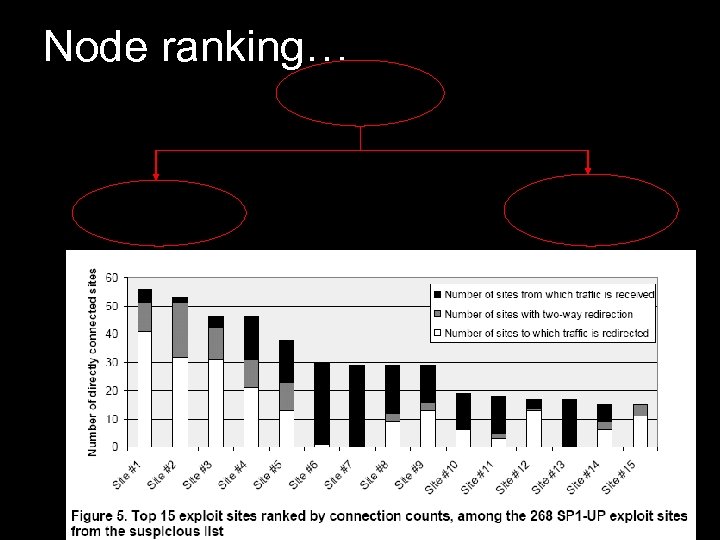
Node ranking… Node ranking Connection counts no. of exploit URLs
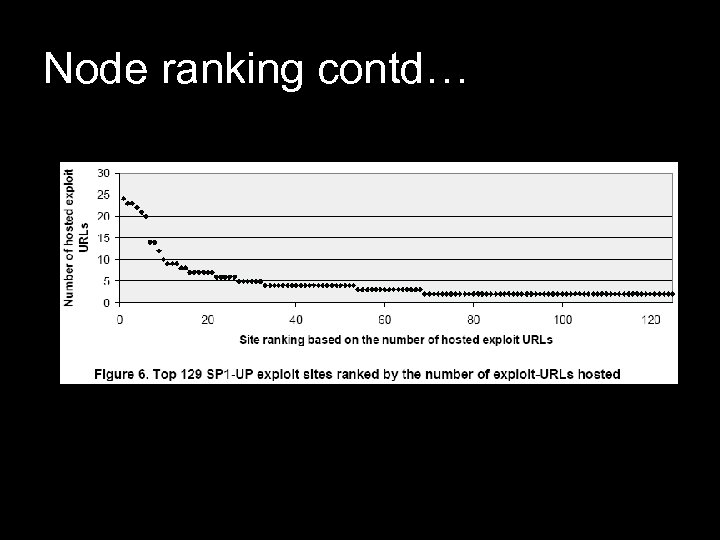
Node ranking contd…

Zero day exploit detection… • Two zero-day exploits discovered – Early July 2005, javaprxy. dll – Second in next hour. • Important observations: – Monitoring easy-to-find exploit-URLs is effective. – Monitoring content providers with well known URLs is effective. – Monitoring highly ranked & advanced exploit URLs is effective.
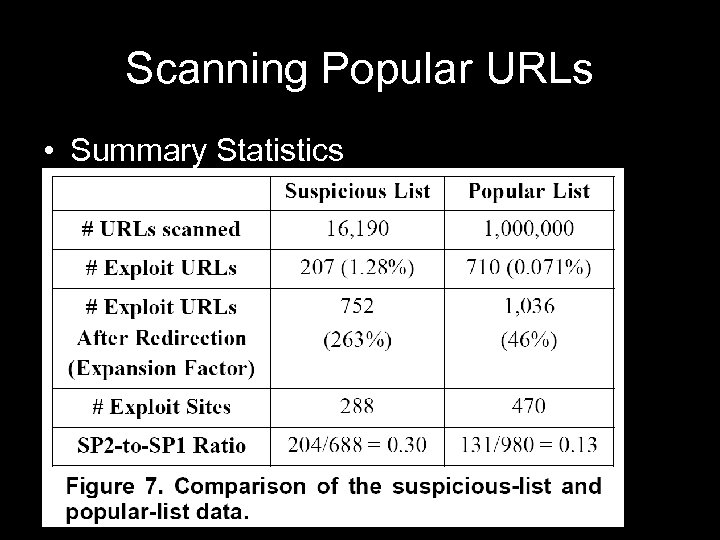
Scanning Popular URLs • Summary Statistics
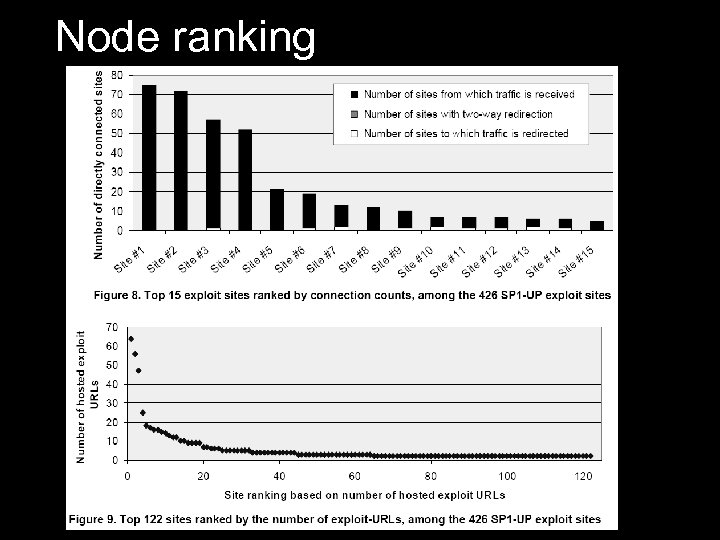
Node ranking

Discussions… • Identifying Honey. Monkeys – Targeting Honey. Monkey IP addresses. – Performing a test to determine if a human is present. – Detecting the presence of a VM or the Honey. Monkey code. • Exploiting without triggering Honey. Monkey detection – code within browser sandbox. • Randomizing the attacks. • VSED – vulnerability specific exploit detector.

Pros… • • • Automatic. Scalability. Non-signature based approach. Stage-wise. Zero-day exploits.
cba3fce4a9de4776bc645f49f1543077.ppt