06a561bae83df0526b0a8ea887202762.ppt
- Количество слайдов: 9

Automated Web Patrol with Strider Honey. Monkeys: Finding Web Sites That Exploit Browser Vulnerabilities Y. -M. Wang, D. Beck, X. Jiang in Proceedings of the 13 th Annual Network and Distributed Systems Security Symposium (NDSS 2006), The Internet Society, 2006. Presenter: Sangyup Lee
Summary n Introduces the concept of Automated Web Patrol ¨ Basic aim is at protecting Internet users Design and Implementation of the system n Effectiveness of the system is demonstrated through a series of experiments n
What is the Strider Honey. Monkey Exploit Detection System? n A pipeline of VM-based honeypots that run monkey programs which patrols the web automatically in an attempt to mimic human web browsing. ¨ Honeypot A trap to catch malice n Records attacker’s information n
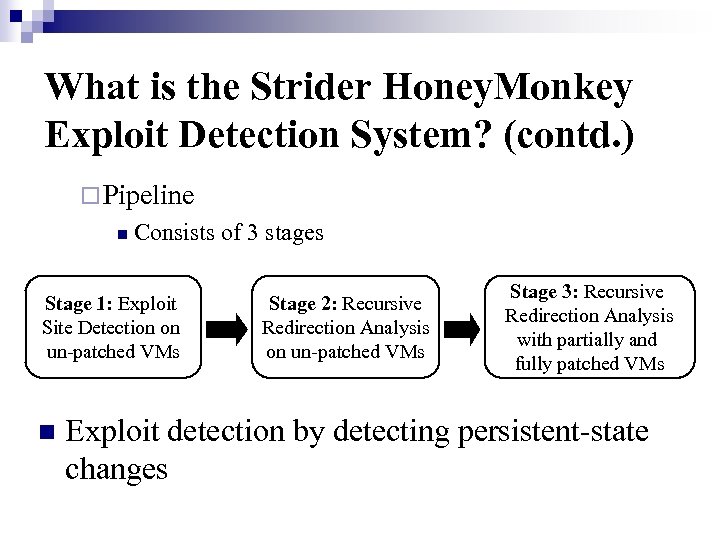
What is the Strider Honey. Monkey Exploit Detection System? (contd. ) ¨ Pipeline n Consists of 3 stages Stage 1: Exploit Site Detection on un-patched VMs n Stage 2: Recursive Redirection Analysis on un-patched VMs Stage 3: Recursive Redirection Analysis with partially and fully patched VMs Exploit detection by detecting persistent-state changes

Appreciative Comment n A good way of approaching the solution to the growing problem of browser-based attacks ¨ Concept of prevention ¨ Possible developments in future
Critical Comments #1 n Only one type of web browser used in the experiments – Internet Explorer 6. 0 ¨ Should have taken into account other popular browsers such as Firefox
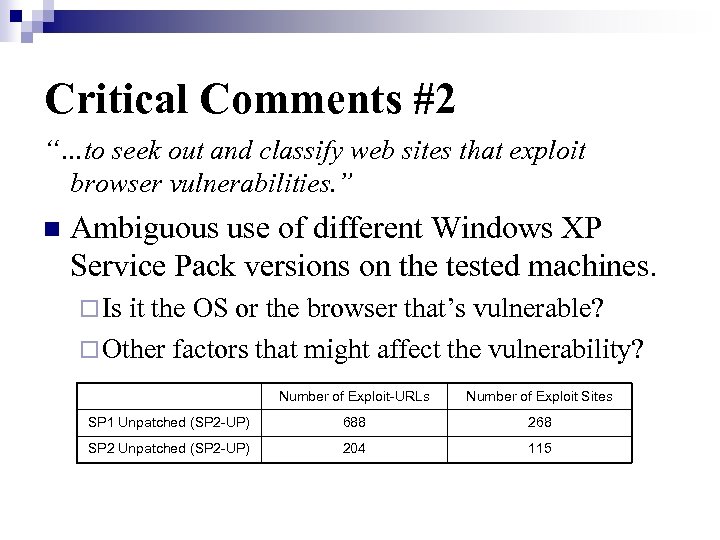
Critical Comments #2 “…to seek out and classify web sites that exploit browser vulnerabilities. ” n Ambiguous use of different Windows XP Service Pack versions on the tested machines. ¨ Is it the OS or the browser that’s vulnerable? ¨ Other factors that might affect the vulnerability? Number of Exploit-URLs Number of Exploit Sites SP 1 Unpatched (SP 2 -UP) 688 268 SP 2 Unpatched (SP 2 -UP) 204 115

Further Analysis “if I never visit those risky web sites that serve dangerous or questionable content, do I have to worry about vulnerability exploits? ” Suspicious List Popular List # URLs scanned 16, 190 1, 000 # Exploit URLs 206 (1. 28%) 710 (0. 071%) “They don’t buy it because the danger is small and because security is a pain. ” – B. Lampson
Discussion n Can you think of any other factors that might affect the vulnerability of your machine against browser-based attacks?
06a561bae83df0526b0a8ea887202762.ppt