3404fff9703286b21f7a39106210524c.ppt
- Количество слайдов: 1
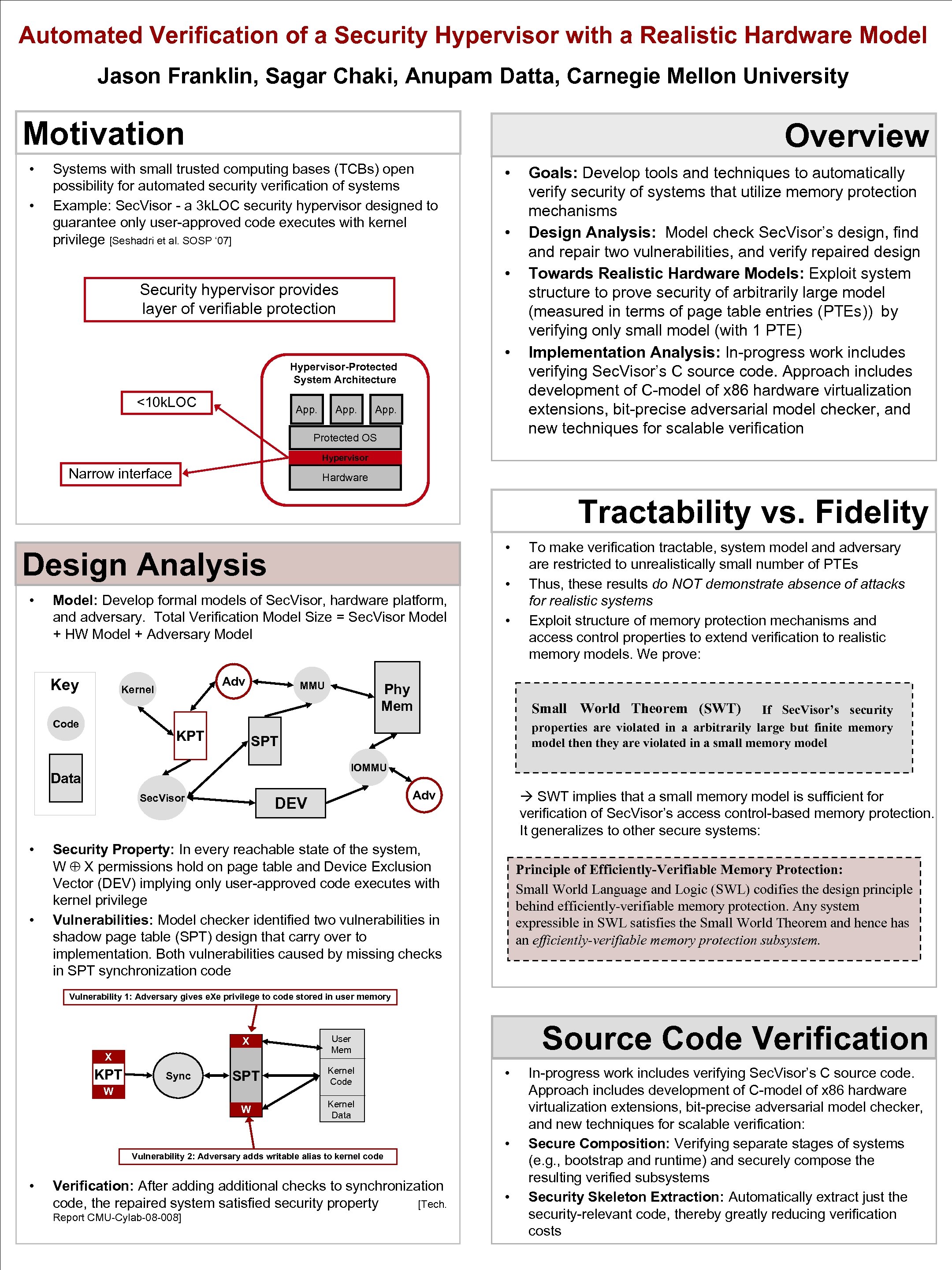 Automated Verification of a Security Hypervisor with a Realistic Hardware Model Jason Franklin, Sagar Chaki, Anupam Datta, Carnegie Mellon University Motivation • • Overview Systems with small trusted computing bases (TCBs) open possibility for automated security verification of systems Example: Sec. Visor - a 3 k. LOC security hypervisor designed to guarantee only user-approved code executes with kernel privilege [Seshadri et al. SOSP ‘ 07] • Hypervisor-Protected System Architecture App. • • Security hypervisor provides layer of verifiable protection <10 k. LOC • App. Protected OS Goals: Develop tools and techniques to automatically verify security of systems that utilize memory protection mechanisms Design Analysis: Model check Sec. Visor’s design, find and repair two vulnerabilities, and verify repaired design Towards Realistic Hardware Models: Exploit system structure to prove security of arbitrarily large model (measured in terms of page table entries (PTEs)) by verifying only small model (with 1 PTE) Implementation Analysis: In-progress work includes verifying Sec. Visor’s C source code. Approach includes development of C-model of x 86 hardware virtualization extensions, bit-precise adversarial model checker, and new techniques for scalable verification Hypervisor Narrow interface Hardware Tractability vs. Fidelity • Design Analysis • • Model: Develop formal models of Sec. Visor, hardware platform, and adversary. Total Verification Model Size = Sec. Visor Model + HW Model + Adversary Model Key Adv Kernel Code KPT MMU Small World Theorem (SWT) If Sec. Visor’s security properties are violated in a arbitrarily large but finite memory model then they are violated in a small memory model IOMMU Sec. Visor • Phy Mem SPT Data • • To make verification tractable, system model and adversary are restricted to unrealistically small number of PTEs Thus, these results do NOT demonstrate absence of attacks for realistic systems Exploit structure of memory protection mechanisms and access control properties to extend verification to realistic memory models. We prove: à SWT implies that a small memory model is sufficient for verification of Sec. Visor’s access control-based memory protection. It generalizes to other secure systems: Adv DEV Security Property: In every reachable state of the system, W X permissions hold on page table and Device Exclusion Vector (DEV) implying only user-approved code executes with kernel privilege Vulnerabilities: Model checker identified two vulnerabilities in shadow page table (SPT) design that carry over to implementation. Both vulnerabilities caused by missing checks in SPT synchronization code Principle of Efficiently-Verifiable Memory Protection: Small World Language and Logic (SWL) codifies the design principle behind efficiently-verifiable memory protection. Any system expressible in SWL satisfies the Small World Theorem and hence has an efficiently-verifiable memory protection subsystem. Vulnerability 1: Adversary gives e. Xe privilege to code stored in user memory X SPT Kernel Code W Kernel Data X KPT Sync W Vulnerability 2: Adversary adds writable alias to kernel code • Verification: After adding additional checks to synchronization code, the repaired system satisfied security property [Tech. Report CMU-Cylab-08 -008] Source Code Verification User Mem • • • In-progress work includes verifying Sec. Visor’s C source code. Approach includes development of C-model of x 86 hardware virtualization extensions, bit-precise adversarial model checker, and new techniques for scalable verification: Secure Composition: Verifying separate stages of systems (e. g. , bootstrap and runtime) and securely compose the resulting verified subsystems Security Skeleton Extraction: Automatically extract just the security-relevant code, thereby greatly reducing verification costs
Automated Verification of a Security Hypervisor with a Realistic Hardware Model Jason Franklin, Sagar Chaki, Anupam Datta, Carnegie Mellon University Motivation • • Overview Systems with small trusted computing bases (TCBs) open possibility for automated security verification of systems Example: Sec. Visor - a 3 k. LOC security hypervisor designed to guarantee only user-approved code executes with kernel privilege [Seshadri et al. SOSP ‘ 07] • Hypervisor-Protected System Architecture App. • • Security hypervisor provides layer of verifiable protection <10 k. LOC • App. Protected OS Goals: Develop tools and techniques to automatically verify security of systems that utilize memory protection mechanisms Design Analysis: Model check Sec. Visor’s design, find and repair two vulnerabilities, and verify repaired design Towards Realistic Hardware Models: Exploit system structure to prove security of arbitrarily large model (measured in terms of page table entries (PTEs)) by verifying only small model (with 1 PTE) Implementation Analysis: In-progress work includes verifying Sec. Visor’s C source code. Approach includes development of C-model of x 86 hardware virtualization extensions, bit-precise adversarial model checker, and new techniques for scalable verification Hypervisor Narrow interface Hardware Tractability vs. Fidelity • Design Analysis • • Model: Develop formal models of Sec. Visor, hardware platform, and adversary. Total Verification Model Size = Sec. Visor Model + HW Model + Adversary Model Key Adv Kernel Code KPT MMU Small World Theorem (SWT) If Sec. Visor’s security properties are violated in a arbitrarily large but finite memory model then they are violated in a small memory model IOMMU Sec. Visor • Phy Mem SPT Data • • To make verification tractable, system model and adversary are restricted to unrealistically small number of PTEs Thus, these results do NOT demonstrate absence of attacks for realistic systems Exploit structure of memory protection mechanisms and access control properties to extend verification to realistic memory models. We prove: à SWT implies that a small memory model is sufficient for verification of Sec. Visor’s access control-based memory protection. It generalizes to other secure systems: Adv DEV Security Property: In every reachable state of the system, W X permissions hold on page table and Device Exclusion Vector (DEV) implying only user-approved code executes with kernel privilege Vulnerabilities: Model checker identified two vulnerabilities in shadow page table (SPT) design that carry over to implementation. Both vulnerabilities caused by missing checks in SPT synchronization code Principle of Efficiently-Verifiable Memory Protection: Small World Language and Logic (SWL) codifies the design principle behind efficiently-verifiable memory protection. Any system expressible in SWL satisfies the Small World Theorem and hence has an efficiently-verifiable memory protection subsystem. Vulnerability 1: Adversary gives e. Xe privilege to code stored in user memory X SPT Kernel Code W Kernel Data X KPT Sync W Vulnerability 2: Adversary adds writable alias to kernel code • Verification: After adding additional checks to synchronization code, the repaired system satisfied security property [Tech. Report CMU-Cylab-08 -008] Source Code Verification User Mem • • • In-progress work includes verifying Sec. Visor’s C source code. Approach includes development of C-model of x 86 hardware virtualization extensions, bit-precise adversarial model checker, and new techniques for scalable verification: Secure Composition: Verifying separate stages of systems (e. g. , bootstrap and runtime) and securely compose the resulting verified subsystems Security Skeleton Extraction: Automatically extract just the security-relevant code, thereby greatly reducing verification costs


