010335777d27513183d4a85b11f53ed1.ppt
- Количество слайдов: 21
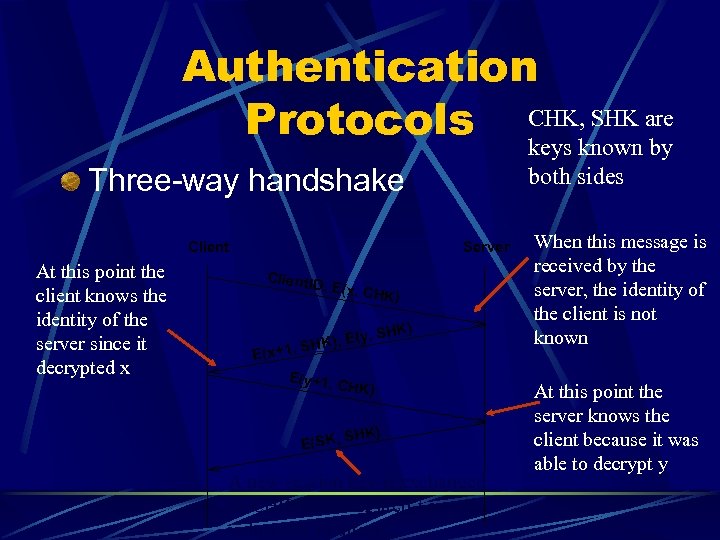
Authentication SHK Protocols CHK, known are keys by Three-way handshake Client At this point the client knows the identity of the server since it decrypted x both sides Server Client. ID , E(x, C HK) , E(y, , SHK) E(x+1 E(y+1, SHK) CHK) SHK) E(SK, A new session key is exchanged so CHK and SHK aren’t as vulnerable to attacks When this message is received by the server, the identity of the client is not known At this point the server knows the client because it was able to decrypt y

Three Way Handshake Assumes both sides know CHK and SHK This could correspond to a password We still need a way to distribute keys assuming the client and server share no keys
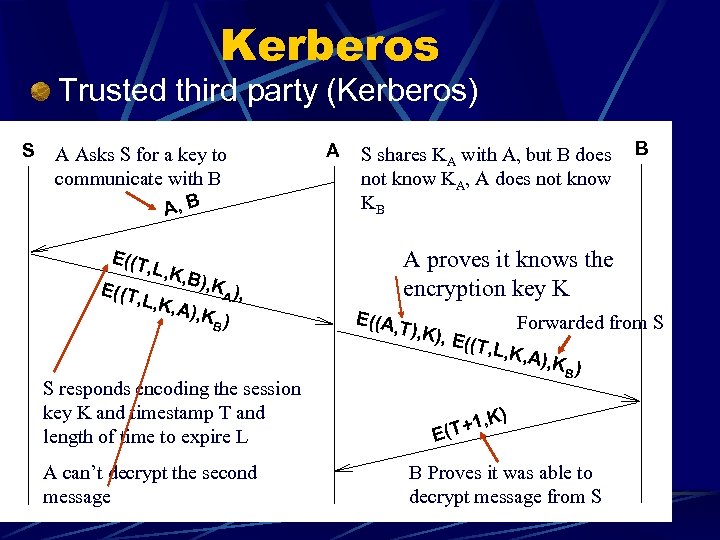
Kerberos Trusted third party (Kerberos) S A Asks S for a key to communicate with B A, B E((T , L, K , B), K E((T A ), , L, K, A), K B) S responds encoding the session key K and timestamp T and length of time to expire L A can’t decrypt the second message A S shares KA with A, but B does not know KA, A does not know KB B A proves it knows the encryption key K E((A, T ), K), E Forwarded from S ((T, L, K, A), K B) , K) 1 E(T+ B Proves it was able to decrypt message from S

Kerberos K is used like a DES session Key exchange depends on a trusted 3 rd party
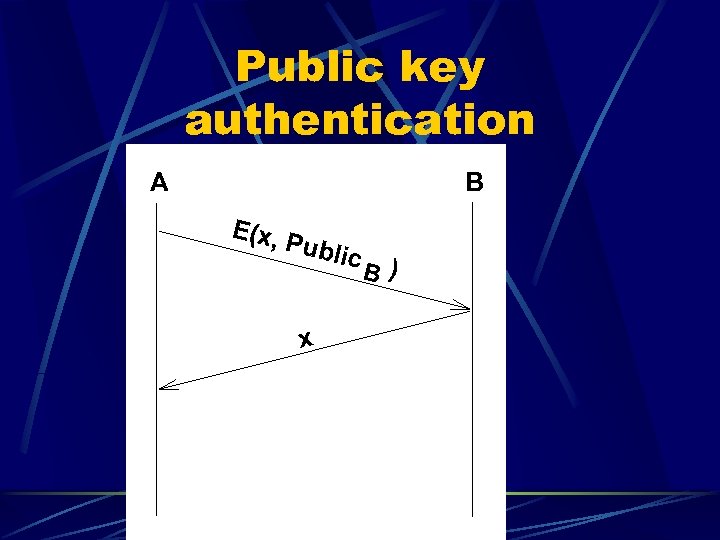
Public key authentication A B E(x, P ublic x B )

Message Integrity Protocols Digital signature using RSA special case of a message integrity where the code can only have been generated by one participant l compute signature with private key and verify with public key l

Don’t send same text to several destinations Suppose that RSA is used to send a message m to three recipients, who have relatively prime encryption moduli n 1, n 2, n 3. All three recipients use the same encryption exponent e=3, a once-popular choice as it makes encryption very fast. Show that someone who intercepts all three messages c 1=m 3 mod n 1, c 2=m 3 mod n 2, c 3=m 3 mod n 3 can efficiently decipher m. The Chinese remainder theorem implies that you can efficiently find a c such that c= c 1 mod n 1, c= c 2 mod n 2, c= c 3 mod n 3. Assume this and show that it implies c= m 3 mod n 1 n 2 n 3.

Keyed MD 5 Sender and receiver share key k sender m + MD 5(m + k) receiver l l applies MD 5 to the concatenation of random key message compares result with checksum sent with message Man-in-the middle can not recompute MD 5 because he doesn’t have secret key k

Keyed MD 5 sender m + MD 5(m + k) + E(k, private) receiver l l l recovers random key using the sender's public key applies MD 5 to the concatenation of this random key message compares result with checksum sent with message Man-in-the middle can intercept k, change message, change checksum, and the receiver wont know

Fixed Keyed MD 5 Sender m + MD 5(m + k) + E(E(k, r-public), s-private) receiver l l recovers random key using the sender's public key and receivers private key applies MD 5 to the concatenation of this random key message compares result with checksum sent with message Authenticates sender Man-in-the middle can not intercept k because it is encrypted with the public key of the receiver Only works for one receiver

What about this? Sender m + MD 5(m + k) + E(k, r-public) receiver l l l recovers random key using the receivers private key applies MD 5 to the concatenation of this random key message compares result with checksum sent with message Man-in-the middle can make up a new key and send it using the receivers public key
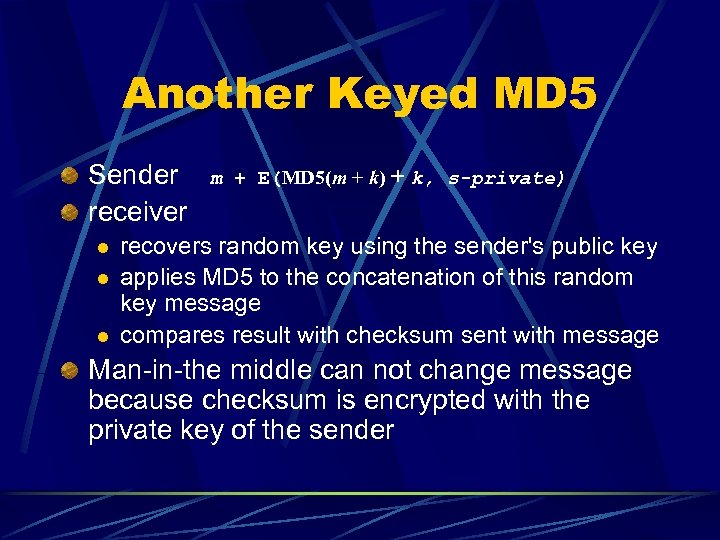
Another Keyed MD 5 Sender receiver l l l m + E(MD 5(m + k) + k, s-private) recovers random key using the sender's public key applies MD 5 to the concatenation of this random key message compares result with checksum sent with message Man-in-the middle can not change message because checksum is encrypted with the private key of the sender
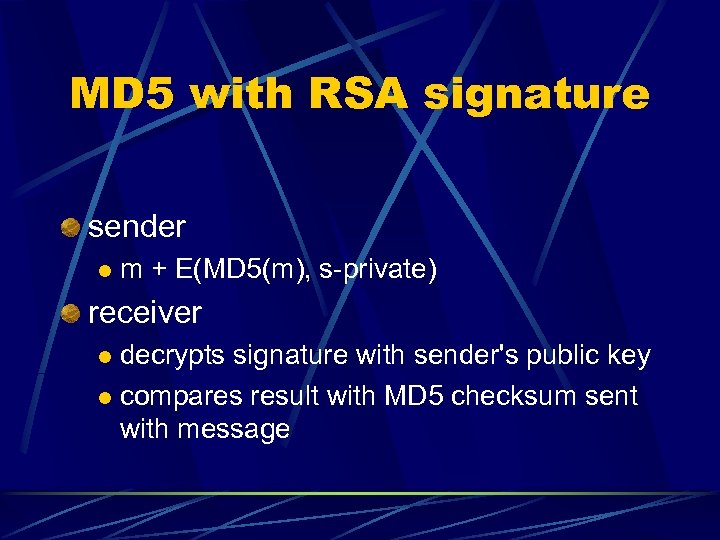
MD 5 with RSA signature sender l m + E(MD 5(m), s-private) receiver decrypts signature with sender's public key l compares result with MD 5 checksum sent with message l
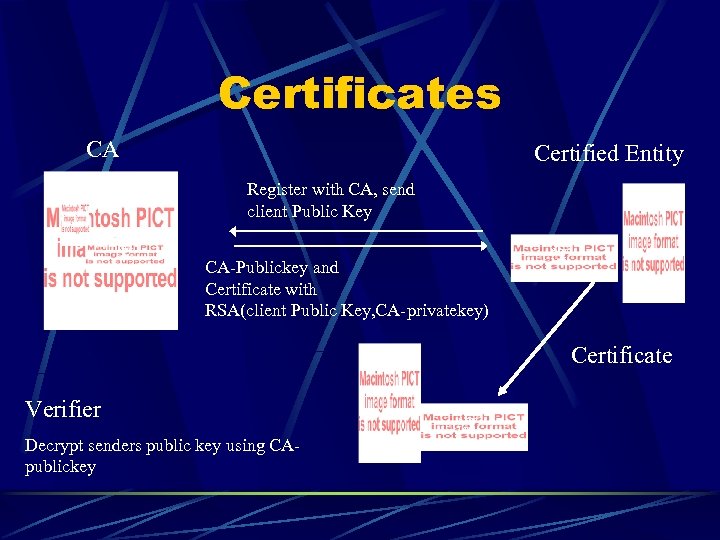
Certificates CA Certified Entity Register with CA, send client Public Key Albert Levi CA-Publickey and Certificate with RSA(client Public Key, CA-privatekey) Albert Levi Certificate Verifier Decrypt senders public key using CApublickey Albert Levi

Hierarchical PKI Example RSA(User. Pub. K, CAPri. K) RSA(CAPub. K. UCAPri. K) RSA(UCAPub. K, Root. CAPri. K)
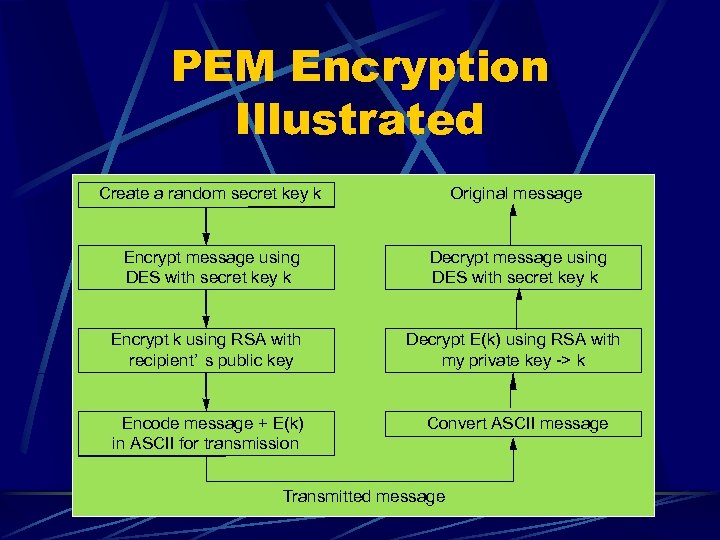
PEM Encryption Illustrated Create a random secret key k Original message Encrypt message using DES with secret key k Decrypt message using DES with secret key k Encrypt k using RSA with recipient’ s public key Decrypt E(k) using RSA with my private key -> k Encode message + E(k) in ASCII for transmission Convert ASCII message Transmitted message
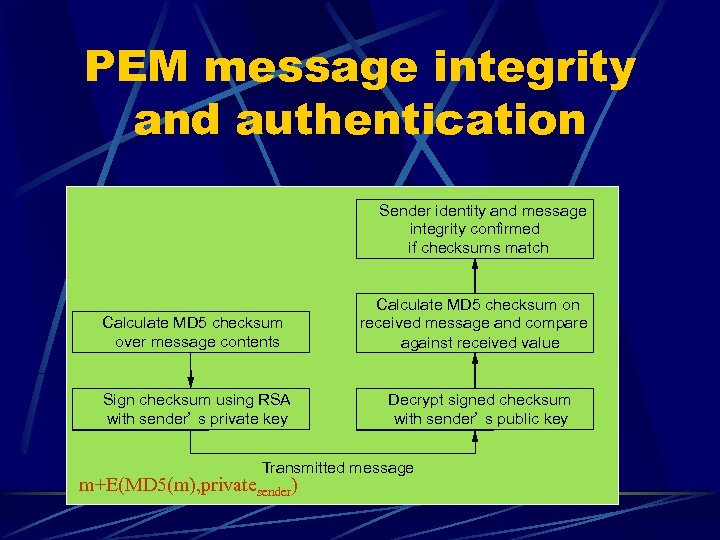
PEM message integrity and authentication Sender identity and message integrity confirmed if checksums match Calculate MD 5 checksum over message contents Sign checksum using RSA with sender’ s private key Calculate MD 5 checksum on received message and compare against received value Decrypt signed checksum with sender’ s public key Transmitted message m+E(MD 5(m), privatesender)
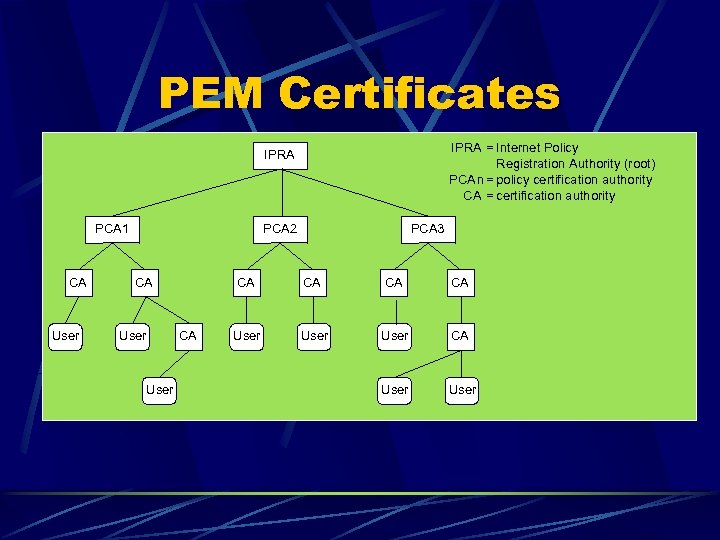
PEM Certificates IPRA = Internet Policy Registration Authority (root) PCA n= policy certification authority CA = certification authority IPRA PCA 1 CA User PCA 2 CA User PCA 3 CA CA CA User CA User

TLS, SSL, HTTPS Transport Layer Security, Secure Socket Layer

SSL Each browser is configured with a root CA When a session is initiated, server and client agree on security capabilities. (most clients are 40 bit encryption, but 128 bit encryption is available on many strong servers The server is authenticated by the certificate authority Using the server public key from the CA, the client sends a DES key to the server The DES key is used to encrypt the session

IPSEC Optional in IPv 4, mandatory in IPv 6 Data Confidentiality---The IPSec sender can encrypt packets before transmitting them across a network. Data Integrity---The IPSec receiver can authenticate packets sent by the IPSec sender to ensure that the data has not been altered during transmission. Data Origin Authentication---The IPSec receiver can authenticate the source of the IPSec packets sent. This service is dependent upon the data integrity service. Anti-Replay---The IPSec receiver can detect and reject replayed packets.
010335777d27513183d4a85b11f53ed1.ppt