c41ad577ec545bcc2bb14b63829d2c22.ppt
- Количество слайдов: 60
 Authentication Services Grid security concepts and tools D. Cesini (INFN-CNAF) V. Ciaschini (INFN-CNAF) A. Paolini (INFN-CNAF) www. ccr. infn. it Scuola Amministratori Grid, Martina Franca (Taranto), 05/11/2007 http: //grid. infn. it/
Authentication Services Grid security concepts and tools D. Cesini (INFN-CNAF) V. Ciaschini (INFN-CNAF) A. Paolini (INFN-CNAF) www. ccr. infn. it Scuola Amministratori Grid, Martina Franca (Taranto), 05/11/2007 http: //grid. infn. it/
 Summary • Security concepts - Symmetric algorithm - PKI - Digital Signature - Digital Certificates • Grid Security: - Proxy Certificates - VOMS certificates - myproxy • Authentication and Authorization on Grid Services (CE) - The Gatekeeper - LCAS - LCMAPS - The gridmapfile and groupmafile - The gridmapdir, vomses - CA on the services, NTP www. ccr. infn. it Scuola Amministratori Grid, Martina Franca (Taranto), 05/11/2007 - 2 http: //grid. infn. it/
Summary • Security concepts - Symmetric algorithm - PKI - Digital Signature - Digital Certificates • Grid Security: - Proxy Certificates - VOMS certificates - myproxy • Authentication and Authorization on Grid Services (CE) - The Gatekeeper - LCAS - LCMAPS - The gridmapfile and groupmafile - The gridmapdir, vomses - CA on the services, NTP www. ccr. infn. it Scuola Amministratori Grid, Martina Franca (Taranto), 05/11/2007 - 2 http: //grid. infn. it/
 Glossary • Principal An entity: an user, a program, or a machine • Credentials Some data providing a proof of identity • Authentication Verify the identity of the principal • Authorization Map an entity to some set of privileges • Confidentiality Encrypt the message so that only the recipient can understand it • Integrity Ensure that the message has not been altered in the transmission • Non-repudiation Impossibility of denying the authenticity of a digital signature www. ccr. infn. it Scuola Amministratori Grid, Martina Franca (Taranto), 05/11/2007 - 3 http: //grid. infn. it/
Glossary • Principal An entity: an user, a program, or a machine • Credentials Some data providing a proof of identity • Authentication Verify the identity of the principal • Authorization Map an entity to some set of privileges • Confidentiality Encrypt the message so that only the recipient can understand it • Integrity Ensure that the message has not been altered in the transmission • Non-repudiation Impossibility of denying the authenticity of a digital signature www. ccr. infn. it Scuola Amministratori Grid, Martina Franca (Taranto), 05/11/2007 - 3 http: //grid. infn. it/
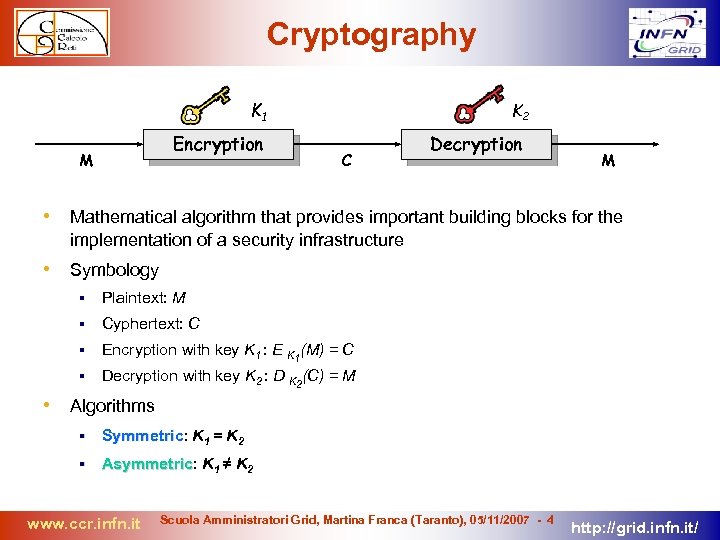 Cryptography K 1 Encryption M K 2 C Decryption M • Mathematical algorithm that provides important building blocks for the implementation of a security infrastructure • Symbology Plaintext: M Cyphertext: C Encryption with key K 1 : E K 1(M) = C Decryption with key K 2 : D K 2(C) = M • Algorithms Symmetric: K 1 = K 2 Symmetric Asymmetric: K 1 ≠ K 2 Asymmetric www. ccr. infn. it Scuola Amministratori Grid, Martina Franca (Taranto), 05/11/2007 - 4 http: //grid. infn. it/
Cryptography K 1 Encryption M K 2 C Decryption M • Mathematical algorithm that provides important building blocks for the implementation of a security infrastructure • Symbology Plaintext: M Cyphertext: C Encryption with key K 1 : E K 1(M) = C Decryption with key K 2 : D K 2(C) = M • Algorithms Symmetric: K 1 = K 2 Symmetric Asymmetric: K 1 ≠ K 2 Asymmetric www. ccr. infn. it Scuola Amministratori Grid, Martina Franca (Taranto), 05/11/2007 - 4 http: //grid. infn. it/
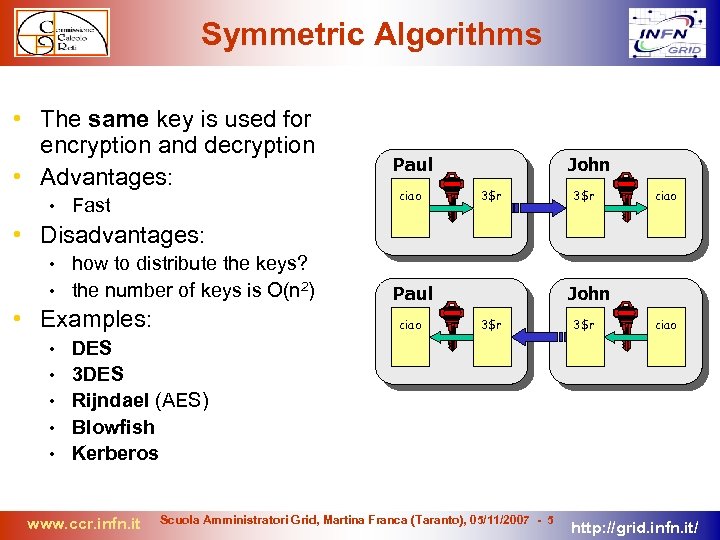 Symmetric Algorithms • The same key is used for encryption and decryption • Advantages: • Fast Paul ciao John 3$r ciao • Disadvantages: how to distribute the keys? • the number of keys is O(n 2) • • Examples: • • • Paul ciao John 3$r ciao DES 3 DES Rijndael (AES) Blowfish Kerberos www. ccr. infn. it Scuola Amministratori Grid, Martina Franca (Taranto), 05/11/2007 - 5 http: //grid. infn. it/
Symmetric Algorithms • The same key is used for encryption and decryption • Advantages: • Fast Paul ciao John 3$r ciao • Disadvantages: how to distribute the keys? • the number of keys is O(n 2) • • Examples: • • • Paul ciao John 3$r ciao DES 3 DES Rijndael (AES) Blowfish Kerberos www. ccr. infn. it Scuola Amministratori Grid, Martina Franca (Taranto), 05/11/2007 - 5 http: //grid. infn. it/
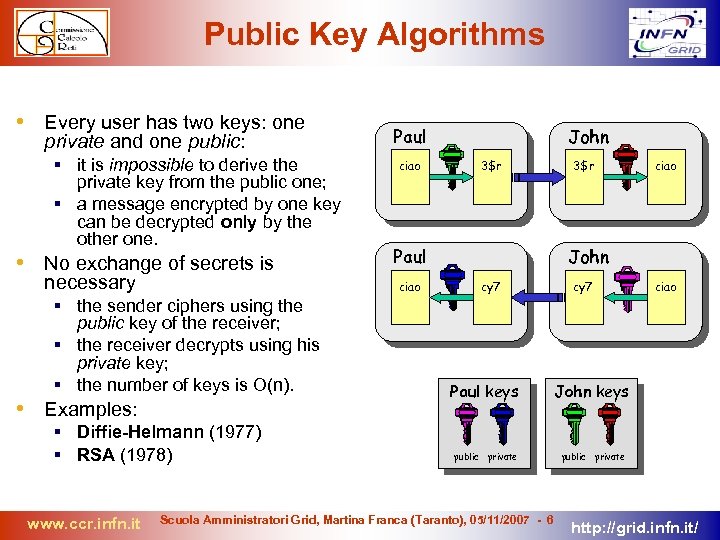 Public Key Algorithms • Every user has two keys: one private and one public: it is impossible to derive the private key from the public one; a message encrypted by one key can be decrypted only by the other one. • No exchange of secrets is necessary Paul ciao John 3$r Paul ciao 3$r ciao John cy 7 ciao the sender ciphers using the public key of the receiver; the receiver decrypts using his private key; the number of keys is O(n). • Examples: Diffie-Helmann (1977) RSA (1978) www. ccr. infn. it Paul keys John keys public private Scuola Amministratori Grid, Martina Franca (Taranto), 05/11/2007 - 6 http: //grid. infn. it/
Public Key Algorithms • Every user has two keys: one private and one public: it is impossible to derive the private key from the public one; a message encrypted by one key can be decrypted only by the other one. • No exchange of secrets is necessary Paul ciao John 3$r Paul ciao 3$r ciao John cy 7 ciao the sender ciphers using the public key of the receiver; the receiver decrypts using his private key; the number of keys is O(n). • Examples: Diffie-Helmann (1977) RSA (1978) www. ccr. infn. it Paul keys John keys public private Scuola Amministratori Grid, Martina Franca (Taranto), 05/11/2007 - 6 http: //grid. infn. it/
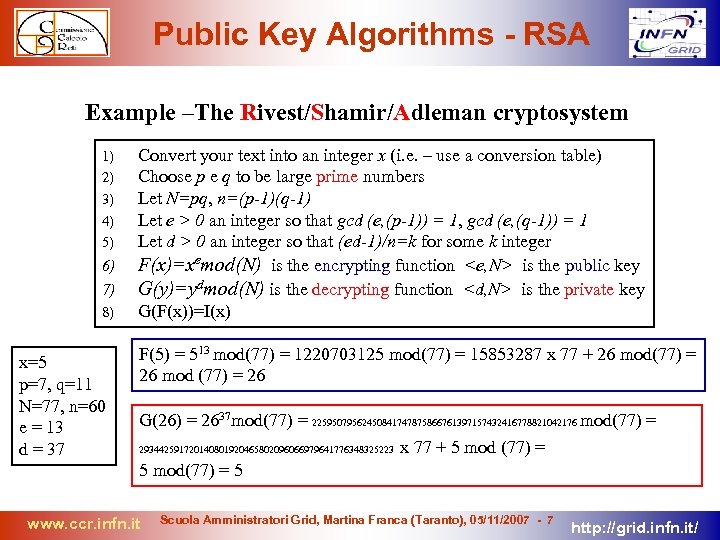 Public Key Algorithms - RSA Example –The Rivest/Shamir/Adleman cryptosystem 1) 2) 3) 4) 5) 6) 7) 8) x=5 p=7, q=11 N=77, n=60 e = 13 d = 37 Convert your text into an integer x (i. e. – use a conversion table) Choose p e q to be large prime numbers Let N=pq, n=(p-1)(q-1) Let e > 0 an integer so that gcd (e, (p-1)) = 1, gcd (e, (q-1)) = 1 Let d > 0 an integer so that (ed-1)/n=k for some k integer F(x)=xemod(N) is the encrypting function
Public Key Algorithms - RSA Example –The Rivest/Shamir/Adleman cryptosystem 1) 2) 3) 4) 5) 6) 7) 8) x=5 p=7, q=11 N=77, n=60 e = 13 d = 37 Convert your text into an integer x (i. e. – use a conversion table) Choose p e q to be large prime numbers Let N=pq, n=(p-1)(q-1) Let e > 0 an integer so that gcd (e, (p-1)) = 1, gcd (e, (q-1)) = 1 Let d > 0 an integer so that (ed-1)/n=k for some k integer F(x)=xemod(N) is the encrypting function
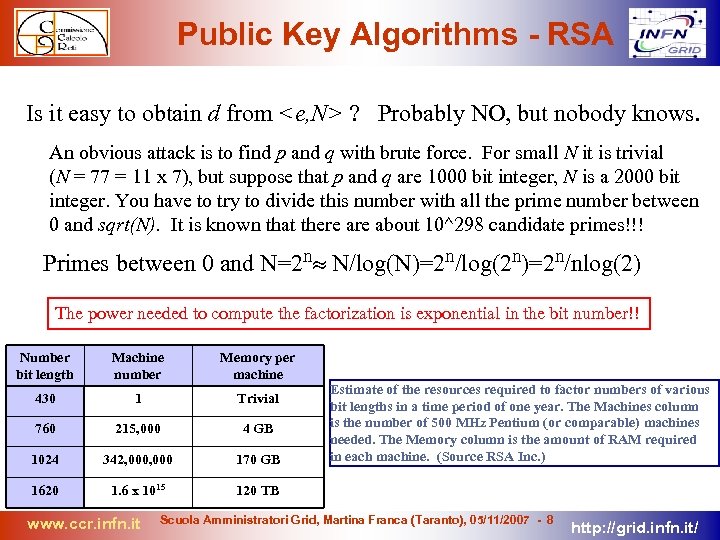 Public Key Algorithms - RSA Is it easy to obtain d from
Public Key Algorithms - RSA Is it easy to obtain d from
 One-Way Hash Functions • Functions (H) that, given as input a variable-length message (M), produce as output a string of fixed length (h) the length of h must be at least 128 bits (to avoid birthday attacks) 1. given M, it must be easy to calculate H(M) = h 2. given h, it must be difficult to calculate M = H-1(h) 3. given M, it must be difficult to find M’ such that H(M) = H(M’) • Examples: SNEFRU: hash of 128 or 256 bits; MD 4/MD 5: hash of 128 bits; SHA (Standard FIPS): hash of 160 bits. www. ccr. infn. it Scuola Amministratori Grid, Martina Franca (Taranto), 05/11/2007 - 9 http: //grid. infn. it/
One-Way Hash Functions • Functions (H) that, given as input a variable-length message (M), produce as output a string of fixed length (h) the length of h must be at least 128 bits (to avoid birthday attacks) 1. given M, it must be easy to calculate H(M) = h 2. given h, it must be difficult to calculate M = H-1(h) 3. given M, it must be difficult to find M’ such that H(M) = H(M’) • Examples: SNEFRU: hash of 128 or 256 bits; MD 4/MD 5: hash of 128 bits; SHA (Standard FIPS): hash of 160 bits. www. ccr. infn. it Scuola Amministratori Grid, Martina Franca (Taranto), 05/11/2007 - 9 http: //grid. infn. it/
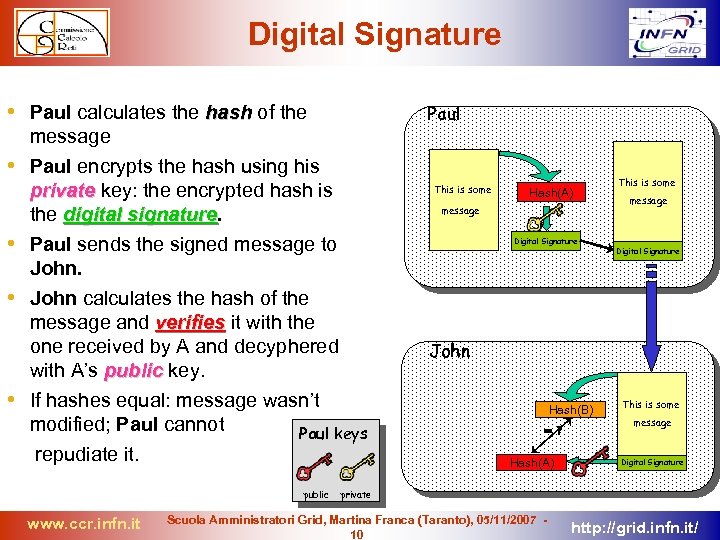 Digital Signature • Paul calculates the hash of the Paul message • Paul encrypts the hash using his private key: the encrypted hash is the digital signature • Paul sends the signed message to John. • John calculates the hash of the message and verifies it with the one received by A and decyphered with A’s public key. • If hashes equal: message wasn’t modified; Paul cannot Paul keys repudiate it. public www. ccr. infn. it This is some Hash(A) message Digital Signature This is some message Digital Signature John Hash(B) =? Hash(A) This is some message Digital Signature private Scuola Amministratori Grid, Martina Franca (Taranto), 05/11/2007 10 http: //grid. infn. it/
Digital Signature • Paul calculates the hash of the Paul message • Paul encrypts the hash using his private key: the encrypted hash is the digital signature • Paul sends the signed message to John. • John calculates the hash of the message and verifies it with the one received by A and decyphered with A’s public key. • If hashes equal: message wasn’t modified; Paul cannot Paul keys repudiate it. public www. ccr. infn. it This is some Hash(A) message Digital Signature This is some message Digital Signature John Hash(B) =? Hash(A) This is some message Digital Signature private Scuola Amministratori Grid, Martina Franca (Taranto), 05/11/2007 10 http: //grid. infn. it/
 Digital Certificates • Paul’s digital signature is safe if: 1. 2. Paul’s private key is not compromised John knows Paul’s public key • How can John be sure that Paul’s public key is really Paul’s public key and not someone else’s? A third party guarantees the correspondence between public key and owner’s identity Both A and B must trust this third party • Two models: X. 509: hierarchical organization; PGP: “web of trust”. www. ccr. infn. it Scuola Amministratori Grid, Martina Franca (Taranto), 05/11/2007 11 http: //grid. infn. it/
Digital Certificates • Paul’s digital signature is safe if: 1. 2. Paul’s private key is not compromised John knows Paul’s public key • How can John be sure that Paul’s public key is really Paul’s public key and not someone else’s? A third party guarantees the correspondence between public key and owner’s identity Both A and B must trust this third party • Two models: X. 509: hierarchical organization; PGP: “web of trust”. www. ccr. infn. it Scuola Amministratori Grid, Martina Franca (Taranto), 05/11/2007 11 http: //grid. infn. it/
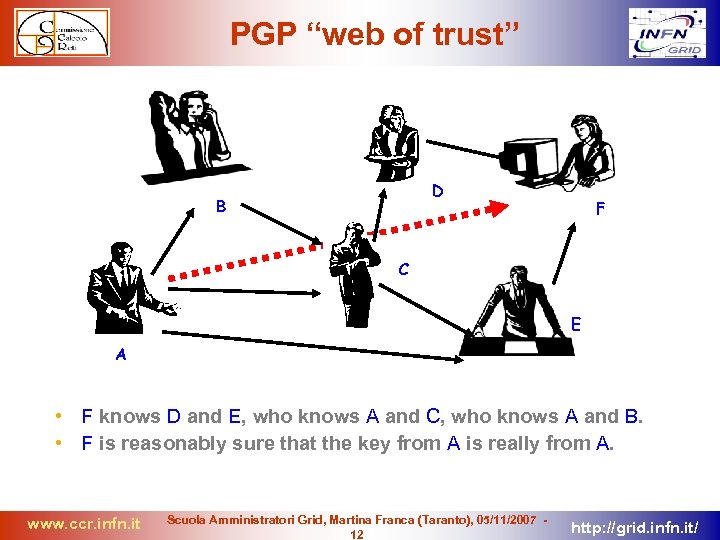 PGP “web of trust” D B F C E A • F knows D and E, who knows A and C, who knows A and B. • F is reasonably sure that the key from A is really from A. www. ccr. infn. it Scuola Amministratori Grid, Martina Franca (Taranto), 05/11/2007 12 http: //grid. infn. it/
PGP “web of trust” D B F C E A • F knows D and E, who knows A and C, who knows A and B. • F is reasonably sure that the key from A is really from A. www. ccr. infn. it Scuola Amministratori Grid, Martina Franca (Taranto), 05/11/2007 12 http: //grid. infn. it/
 X. 509 Certificates The “third party” is called Certification Authority (CA). • Issue Digital Certificates for users, programs and machines • Check the identity and the personal data of the requestor Registration Authorities (RAs) do the actual validation • CA’s periodically publish a list of compromised certificates Certificate Revocation Lists (CRL): contain all the revoked certificates yet to expire • CA certificates are self-signed www. ccr. infn. it Scuola Amministratori Grid, Martina Franca (Taranto), 05/11/2007 13 http: //grid. infn. it/
X. 509 Certificates The “third party” is called Certification Authority (CA). • Issue Digital Certificates for users, programs and machines • Check the identity and the personal data of the requestor Registration Authorities (RAs) do the actual validation • CA’s periodically publish a list of compromised certificates Certificate Revocation Lists (CRL): contain all the revoked certificates yet to expire • CA certificates are self-signed www. ccr. infn. it Scuola Amministratori Grid, Martina Franca (Taranto), 05/11/2007 13 http: //grid. infn. it/
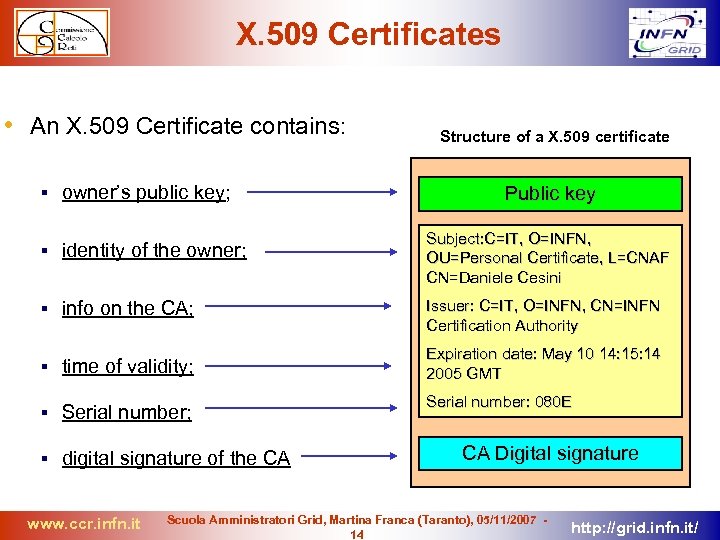 X. 509 Certificates • An X. 509 Certificate contains: owner’s public key; identity of the owner; info on the CA; time of validity; Serial number; digital signature of the CA www. ccr. infn. it Structure of a X. 509 certificate Public key Subject: C=IT, O=INFN, OU=Personal Certificate, L=CNAF CN=Daniele Cesini Issuer: C=IT, O=INFN, CN=INFN Certification Authority Expiration date: May 10 14: 15: 14 2005 GMT Serial number: 080 E CA Digital signature Scuola Amministratori Grid, Martina Franca (Taranto), 05/11/2007 14 http: //grid. infn. it/
X. 509 Certificates • An X. 509 Certificate contains: owner’s public key; identity of the owner; info on the CA; time of validity; Serial number; digital signature of the CA www. ccr. infn. it Structure of a X. 509 certificate Public key Subject: C=IT, O=INFN, OU=Personal Certificate, L=CNAF CN=Daniele Cesini Issuer: C=IT, O=INFN, CN=INFN Certification Authority Expiration date: May 10 14: 15: 14 2005 GMT Serial number: 080 E CA Digital signature Scuola Amministratori Grid, Martina Franca (Taranto), 05/11/2007 14 http: //grid. infn. it/
 Which are the trusted CA in LCG/EGEE? http: //www. eugridpma. org/ “The EUGrid. PMA is the international organization to coordinate the trust fabric for e-Science grid authentication in Europe. It collaborates with the regional peers APGrid. PMA for the Asia -Pacific and The Americas Grid PMA in the International Grid Trust Federation. The charter document defines the group's objective, scope and operation. It is the basis for the guidelines documents on the accreditation procedure, the Authentication profile for X. 509 secured "classic" certification authorities and other IGTF recognised Profiles. “ In LCG/EGEE CA are installed on machine trough rpms. The official production apt CA repository is: rpm http: //linuxsoft. cern. ch LCG-CAs/current production apt-get install lcg-CA a metapackage that install the lcg CA www. ccr. infn. it Scuola Amministratori Grid, Martina Franca (Taranto), 05/11/2007 15 http: //grid. infn. it/
Which are the trusted CA in LCG/EGEE? http: //www. eugridpma. org/ “The EUGrid. PMA is the international organization to coordinate the trust fabric for e-Science grid authentication in Europe. It collaborates with the regional peers APGrid. PMA for the Asia -Pacific and The Americas Grid PMA in the International Grid Trust Federation. The charter document defines the group's objective, scope and operation. It is the basis for the guidelines documents on the accreditation procedure, the Authentication profile for X. 509 secured "classic" certification authorities and other IGTF recognised Profiles. “ In LCG/EGEE CA are installed on machine trough rpms. The official production apt CA repository is: rpm http: //linuxsoft. cern. ch LCG-CAs/current production apt-get install lcg-CA a metapackage that install the lcg CA www. ccr. infn. it Scuola Amministratori Grid, Martina Franca (Taranto), 05/11/2007 15 http: //grid. infn. it/
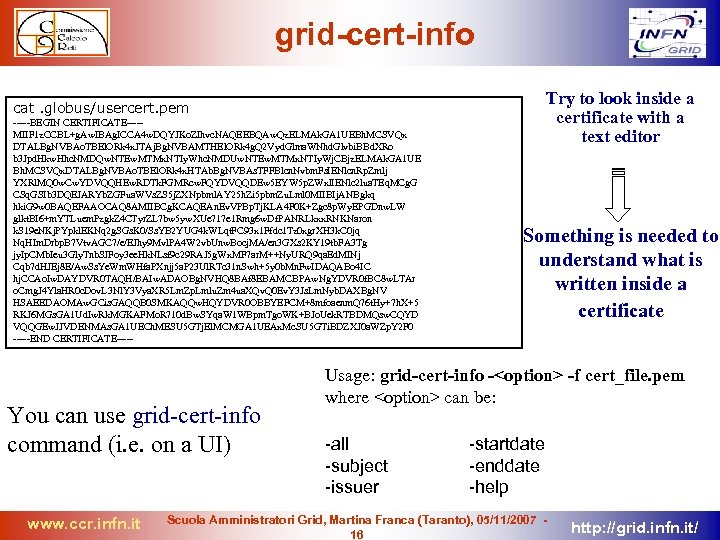 grid-cert-info Try to look inside a certificate with a text editor cat. globus/usercert. pem -----BEGIN CERTIFICATE----MIIF 1 z. CCBL+g. Aw. IBAg. ICCA 4 w. DQYJKo. ZIhvc. NAQEEBQAw. Qz. ELMAk. GA 1 UEBh. MCSVQx DTALBg. NVBAo. TBEl. ORk 4 x. JTAj. Bg. NVBAMTHEl. ORk 4 g. Q 2 Vyd. Glma. WNhd. Glvbi. BBd. XRo b 3 Jpd. Hkw. Hhc. NMDQw. NTEw. MTMx. NTIy. Whc. NMDUw. NTEw. MTMx. NTIy. Wj. CBjz. ELMAk. GA 1 UE Bh. MCSVQx. DTALBg. NVBAo. TBEl. ORk 4 x. HTAb. Bg. NVBAs. TFFBlcn. Nvbm. Fs. IENlcn. Rp. Zmlj YXRl. MQ 0 w. Cw. YDVQQHEw. RDTk. FGMRcw. FQYDVQQDEw 5 EYW 5 p. ZWxl. IENlc 2 lua. TEq. MCg. G CSq. GSIb 3 DQEJARYb. ZGFua. WVs. ZS 5 j. ZXNpbml. AY 25 h. Zi 5 pbm. Zu. Lml 0 MIIBIj. ANBgkq hki. G 9 w 0 BAQEFAAOCAQ 8 AMIIBCg. KCAQEAn. Ev. VPBp. Tj. KLA 4 F 0 K+Zgc 8 p. Wy. EPGDnw. LW glkt. BI 6+m. YTLuem. Pzgk. Z 4 CTyr. ZL 7 bw 5 yw. XUe 717 e 1 Rmg 6 w. Df. PANRLkxx. RNKNaron k. S 19 e. NKj. PYpkl. EKNq 2 g. SGs. K 0/Ss. YB 2 YUG 4 k. WLqt. FC 93 x 1 Ffdc 1 Tz 0 xgr. XH 3 k. C 0 jq Nq. HIm. Drbp. B 7 Vtv. AGC 7/e/EJhy 9 Mvl. PA 4 W 2 vb. Unw. Bocj. MA/en 3 GXs 2 KY 19 tb. FA 3 Tg jy. Ip. CMb. Ieu 3 Gly. Tnb. SJFoy 3 ee. Hk. NLsf 9 c 29 RAJ 5 g. Wx. MF 7 ar. M++Ny. URQ 9 qa. Ed. MINj Cqb 7 d. HJEj 8 E/Aw. Ss. Ye. Wm. WHfa. PXnjj 5 a. P 23 Ul. RTc 31 n. Swh+5 y 0 b. Mn. Fw. IDAQABo 4 IC hj. CCAo. Iw. DAYDVR 0 TAQH/BAIw. ADAOBg. NVHQ 8 BAf 8 EBAMCBPAw. Ng. YDVR 0 f. BC 8 w. LTAr o. Cmg. J 4 Yla. HR 0 c. Dov. L 3 Nl. Y 3 Vya. XR 5 Lm. Zp. Lmlu. Zm 4 ua. XQv. Q 0 Ev. Y 3 Js. Lm. Nyb. DAXBg. NV HSAEEDAOMAw. GCis. GAQQB 0 SMKAQQw. HQYDVR 0 OBBYEFCM+8 mfoaenm. Q 76 t. Hy+7 h. X+5 RKJ 6 MGs. GA 1 Ud. Iw. Rk. MGKAFMo. R 710 d. Bw. SYqa. W 1 WBpm. Tgo. WK+BJo. Uek. RTBDMQsw. CQYD VQQGEw. JJVDENMAs. GA 1 UECh. MESU 5 GTj. El. MCMGA 1 UEAx. Mc. SU 5 GTi. BDZXJ 0 a. WZp. Y 2 F 0 -----END CERTIFICATE----- You can use grid-cert-info command (i. e. on a UI) www. ccr. infn. it Something is needed to understand what is written inside a certificate Usage: grid-cert-info -
grid-cert-info Try to look inside a certificate with a text editor cat. globus/usercert. pem -----BEGIN CERTIFICATE----MIIF 1 z. CCBL+g. Aw. IBAg. ICCA 4 w. DQYJKo. ZIhvc. NAQEEBQAw. Qz. ELMAk. GA 1 UEBh. MCSVQx DTALBg. NVBAo. TBEl. ORk 4 x. JTAj. Bg. NVBAMTHEl. ORk 4 g. Q 2 Vyd. Glma. WNhd. Glvbi. BBd. XRo b 3 Jpd. Hkw. Hhc. NMDQw. NTEw. MTMx. NTIy. Whc. NMDUw. NTEw. MTMx. NTIy. Wj. CBjz. ELMAk. GA 1 UE Bh. MCSVQx. DTALBg. NVBAo. TBEl. ORk 4 x. HTAb. Bg. NVBAs. TFFBlcn. Nvbm. Fs. IENlcn. Rp. Zmlj YXRl. MQ 0 w. Cw. YDVQQHEw. RDTk. FGMRcw. FQYDVQQDEw 5 EYW 5 p. ZWxl. IENlc 2 lua. TEq. MCg. G CSq. GSIb 3 DQEJARYb. ZGFua. WVs. ZS 5 j. ZXNpbml. AY 25 h. Zi 5 pbm. Zu. Lml 0 MIIBIj. ANBgkq hki. G 9 w 0 BAQEFAAOCAQ 8 AMIIBCg. KCAQEAn. Ev. VPBp. Tj. KLA 4 F 0 K+Zgc 8 p. Wy. EPGDnw. LW glkt. BI 6+m. YTLuem. Pzgk. Z 4 CTyr. ZL 7 bw 5 yw. XUe 717 e 1 Rmg 6 w. Df. PANRLkxx. RNKNaron k. S 19 e. NKj. PYpkl. EKNq 2 g. SGs. K 0/Ss. YB 2 YUG 4 k. WLqt. FC 93 x 1 Ffdc 1 Tz 0 xgr. XH 3 k. C 0 jq Nq. HIm. Drbp. B 7 Vtv. AGC 7/e/EJhy 9 Mvl. PA 4 W 2 vb. Unw. Bocj. MA/en 3 GXs 2 KY 19 tb. FA 3 Tg jy. Ip. CMb. Ieu 3 Gly. Tnb. SJFoy 3 ee. Hk. NLsf 9 c 29 RAJ 5 g. Wx. MF 7 ar. M++Ny. URQ 9 qa. Ed. MINj Cqb 7 d. HJEj 8 E/Aw. Ss. Ye. Wm. WHfa. PXnjj 5 a. P 23 Ul. RTc 31 n. Swh+5 y 0 b. Mn. Fw. IDAQABo 4 IC hj. CCAo. Iw. DAYDVR 0 TAQH/BAIw. ADAOBg. NVHQ 8 BAf 8 EBAMCBPAw. Ng. YDVR 0 f. BC 8 w. LTAr o. Cmg. J 4 Yla. HR 0 c. Dov. L 3 Nl. Y 3 Vya. XR 5 Lm. Zp. Lmlu. Zm 4 ua. XQv. Q 0 Ev. Y 3 Js. Lm. Nyb. DAXBg. NV HSAEEDAOMAw. GCis. GAQQB 0 SMKAQQw. HQYDVR 0 OBBYEFCM+8 mfoaenm. Q 76 t. Hy+7 h. X+5 RKJ 6 MGs. GA 1 Ud. Iw. Rk. MGKAFMo. R 710 d. Bw. SYqa. W 1 WBpm. Tgo. WK+BJo. Uek. RTBDMQsw. CQYD VQQGEw. JJVDENMAs. GA 1 UECh. MESU 5 GTj. El. MCMGA 1 UEAx. Mc. SU 5 GTi. BDZXJ 0 a. WZp. Y 2 F 0 -----END CERTIFICATE----- You can use grid-cert-info command (i. e. on a UI) www. ccr. infn. it Something is needed to understand what is written inside a certificate Usage: grid-cert-info -
![grid-cert-info Try to run a grid-cert-info on you certificate [cesini@lcg-ui cesini]$ grid-cert-info -f. globus/usercert. grid-cert-info Try to run a grid-cert-info on you certificate [cesini@lcg-ui cesini]$ grid-cert-info -f. globus/usercert.](https://present5.com/presentation/c41ad577ec545bcc2bb14b63829d2c22/image-17.jpg) grid-cert-info Try to run a grid-cert-info on you certificate [cesini@lcg-ui cesini]$ grid-cert-info -f. globus/usercert. pem -subject -enddate -startdate -issuer /C=IT/O=INFN/OU=Personal Certificate/L=CNAF/CN=Daniele Cesini/Email=daniele. cesini@cnaf. infn. it Apr 16 17: 50: 42 2008 GMT Apr 17 17: 50: 42 2007 GMT /C=IT/O=INFN/CN=INFN CA www. ccr. infn. it Scuola Amministratori Grid, Martina Franca (Taranto), 05/11/2007 17 http: //grid. infn. it/
grid-cert-info Try to run a grid-cert-info on you certificate [cesini@lcg-ui cesini]$ grid-cert-info -f. globus/usercert. pem -subject -enddate -startdate -issuer /C=IT/O=INFN/OU=Personal Certificate/L=CNAF/CN=Daniele Cesini/Email=daniele. cesini@cnaf. infn. it Apr 16 17: 50: 42 2008 GMT Apr 17 17: 50: 42 2007 GMT /C=IT/O=INFN/CN=INFN CA www. ccr. infn. it Scuola Amministratori Grid, Martina Franca (Taranto), 05/11/2007 17 http: //grid. infn. it/
![grid-cert-info Gather info about a certificate in your CE directory /etc/grid-security/certificates/ [cesini@lcg-ui cesini]$ grid-cert-info grid-cert-info Gather info about a certificate in your CE directory /etc/grid-security/certificates/ [cesini@lcg-ui cesini]$ grid-cert-info](https://present5.com/presentation/c41ad577ec545bcc2bb14b63829d2c22/image-18.jpg) grid-cert-info Gather info about a certificate in your CE directory /etc/grid-security/certificates/ [cesini@lcg-ui cesini]$ grid-cert-info –all –f /etc/grid-security/certificates/2 f 3 fadf 6. 0 [cesini@lcg-ui cesini]$ grid-cert-info -file /etc/grid-security/certificates/2 f 3 fadf 6. 0 Certificate: Exponent: 65537 (0 x 10001) Data: X 509 v 3 extensions: Version: 3 (0 x 2) X 509 v 3 Basic Constraints: critical Serial Number: 0 (0 x 0) CA: TRUE Signature Algorithm: sha 1 With. RSAEncryption X 509 v 3 Key Usage: critical Certificate Sign, CRL Sign Validity X 509 v 3 Subject Key Identifier: Not Before: Oct 3 14: 16: 47 2006 GMT D 1: 62: F 3: B 3: 77: 72: C 8: 2 E: FB: F 2: 79: 1 A: 6 F: 37: 4 E: 27: 9 F: 13: D 5: 20 Not After : Oct 3 14: 16: 47 2016 GMT X 509 v 3 Authority Key Identifier: keyid: D 1: 62: F 3: B 3: 77: 72: C 8: 2 E: FB: F 2: 79: 1 A: 6 F: 37: 4 E: 27: 9 F: 13: D 5: 20 Dir. Name: /C=IT/O=INFN/CN=INFN CA Subject Public Key Info: serial: 00 Public Key Algorithm: rsa. Encryption RSA Public Key: (2048 bit) Signature Algorithm: sha 1 With. RSAEncryption Modulus (2048 bit): 78: d 7: d 3: 3 f: b 7: 3 f: 72: 40: 62: 01: 23: 96: 80: 5 c: e 4: b 7: 36: 00: ce: 95: 8 e: 0 e: 83: 95: 9 d: 42: a 9: ca: 29: 23: ca: b 7: e 0: c 4: 7 f: 43: 1 d: a 8: 22: c 5: 20: 6 b: 17: 8 e: db: c 8: 9 b: 69: 03: 48: 63: f 9: 0 a: 49: ba: 82: 5 e: 2 a: 4 a: 85: e 1: f 6: dd: e 8: ba: c 4: 86: 40: e 8: 39: b 9: 99: c 9: 2 d: 30: 21: 69: 3 f: a 0: 5 f: 97: 8 d: 90: ea: 79: 02: f 4: 76: a 0: 22: 96: e 5: 51: f 0: 3 e: 32: fd: 37: 73: 86: eb: 89: 12: 05: b 5: 14: f 1: 83: cb: 62: 1 f: eb: 38: 03: e 1: ……. . Issuer: C=IT, O=INFN, CN=INFN CA Subject: C=IT, O=INFN, CN=INFN CA [cesini@lch-ui cesini]$ openssl verify /etc/grid-security/certificates/2 f 3 fadf 6. 0: /C=IT/O=INFN/CN=INFN CA error 18 at 0 depth lookup: self signed certificate OK www. ccr. infn. it Scuola Amministratori Grid, Martina Franca (Taranto), 05/11/2007 18 http: //grid. infn. it/
grid-cert-info Gather info about a certificate in your CE directory /etc/grid-security/certificates/ [cesini@lcg-ui cesini]$ grid-cert-info –all –f /etc/grid-security/certificates/2 f 3 fadf 6. 0 [cesini@lcg-ui cesini]$ grid-cert-info -file /etc/grid-security/certificates/2 f 3 fadf 6. 0 Certificate: Exponent: 65537 (0 x 10001) Data: X 509 v 3 extensions: Version: 3 (0 x 2) X 509 v 3 Basic Constraints: critical Serial Number: 0 (0 x 0) CA: TRUE Signature Algorithm: sha 1 With. RSAEncryption X 509 v 3 Key Usage: critical Certificate Sign, CRL Sign Validity X 509 v 3 Subject Key Identifier: Not Before: Oct 3 14: 16: 47 2006 GMT D 1: 62: F 3: B 3: 77: 72: C 8: 2 E: FB: F 2: 79: 1 A: 6 F: 37: 4 E: 27: 9 F: 13: D 5: 20 Not After : Oct 3 14: 16: 47 2016 GMT X 509 v 3 Authority Key Identifier: keyid: D 1: 62: F 3: B 3: 77: 72: C 8: 2 E: FB: F 2: 79: 1 A: 6 F: 37: 4 E: 27: 9 F: 13: D 5: 20 Dir. Name: /C=IT/O=INFN/CN=INFN CA Subject Public Key Info: serial: 00 Public Key Algorithm: rsa. Encryption RSA Public Key: (2048 bit) Signature Algorithm: sha 1 With. RSAEncryption Modulus (2048 bit): 78: d 7: d 3: 3 f: b 7: 3 f: 72: 40: 62: 01: 23: 96: 80: 5 c: e 4: b 7: 36: 00: ce: 95: 8 e: 0 e: 83: 95: 9 d: 42: a 9: ca: 29: 23: ca: b 7: e 0: c 4: 7 f: 43: 1 d: a 8: 22: c 5: 20: 6 b: 17: 8 e: db: c 8: 9 b: 69: 03: 48: 63: f 9: 0 a: 49: ba: 82: 5 e: 2 a: 4 a: 85: e 1: f 6: dd: e 8: ba: c 4: 86: 40: e 8: 39: b 9: 99: c 9: 2 d: 30: 21: 69: 3 f: a 0: 5 f: 97: 8 d: 90: ea: 79: 02: f 4: 76: a 0: 22: 96: e 5: 51: f 0: 3 e: 32: fd: 37: 73: 86: eb: 89: 12: 05: b 5: 14: f 1: 83: cb: 62: 1 f: eb: 38: 03: e 1: ……. . Issuer: C=IT, O=INFN, CN=INFN CA Subject: C=IT, O=INFN, CN=INFN CA [cesini@lch-ui cesini]$ openssl verify /etc/grid-security/certificates/2 f 3 fadf 6. 0: /C=IT/O=INFN/CN=INFN CA error 18 at 0 depth lookup: self signed certificate OK www. ccr. infn. it Scuola Amministratori Grid, Martina Franca (Taranto), 05/11/2007 18 http: //grid. infn. it/
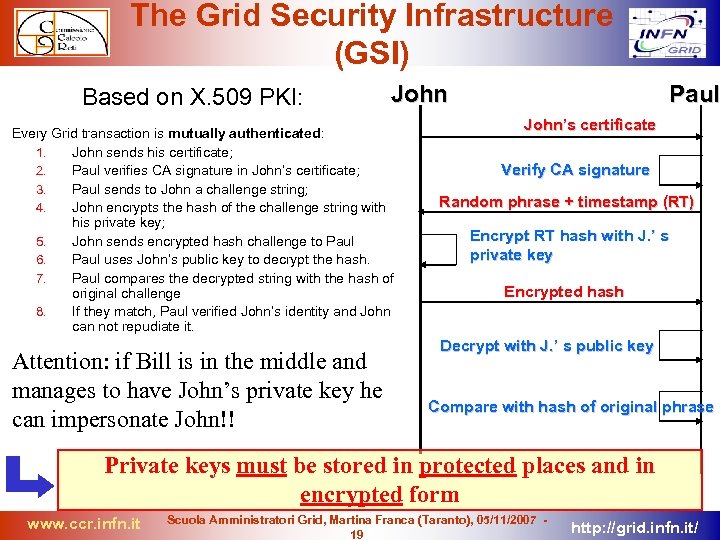 The Grid Security Infrastructure (GSI) Based on X. 509 PKI: John Every Grid transaction is mutually authenticated: 1. John sends his certificate; 2. Paul verifies CA signature in John’s certificate; 3. Paul sends to John a challenge string; 4. John encrypts the hash of the challenge string with his private key; 5. John sends encrypted hash challenge to Paul 6. Paul uses John’s public key to decrypt the hash. 7. Paul compares the decrypted string with the hash of original challenge 8. If they match, Paul verified John’s identity and John can not repudiate it. Attention: if Bill is in the middle and manages to have John’s private key he can impersonate John!! Paul John’s certificate Verify CA signature Random phrase + timestamp (RT) Encrypt RT hash with J. ’ s private key Encrypted hash Decrypt with J. ’ s public key Compare with hash of original phrase Private keys must be stored in protected places and in encrypted form www. ccr. infn. it Scuola Amministratori Grid, Martina Franca (Taranto), 05/11/2007 19 http: //grid. infn. it/
The Grid Security Infrastructure (GSI) Based on X. 509 PKI: John Every Grid transaction is mutually authenticated: 1. John sends his certificate; 2. Paul verifies CA signature in John’s certificate; 3. Paul sends to John a challenge string; 4. John encrypts the hash of the challenge string with his private key; 5. John sends encrypted hash challenge to Paul 6. Paul uses John’s public key to decrypt the hash. 7. Paul compares the decrypted string with the hash of original challenge 8. If they match, Paul verified John’s identity and John can not repudiate it. Attention: if Bill is in the middle and manages to have John’s private key he can impersonate John!! Paul John’s certificate Verify CA signature Random phrase + timestamp (RT) Encrypt RT hash with J. ’ s private key Encrypted hash Decrypt with J. ’ s public key Compare with hash of original phrase Private keys must be stored in protected places and in encrypted form www. ccr. infn. it Scuola Amministratori Grid, Martina Franca (Taranto), 05/11/2007 19 http: //grid. infn. it/
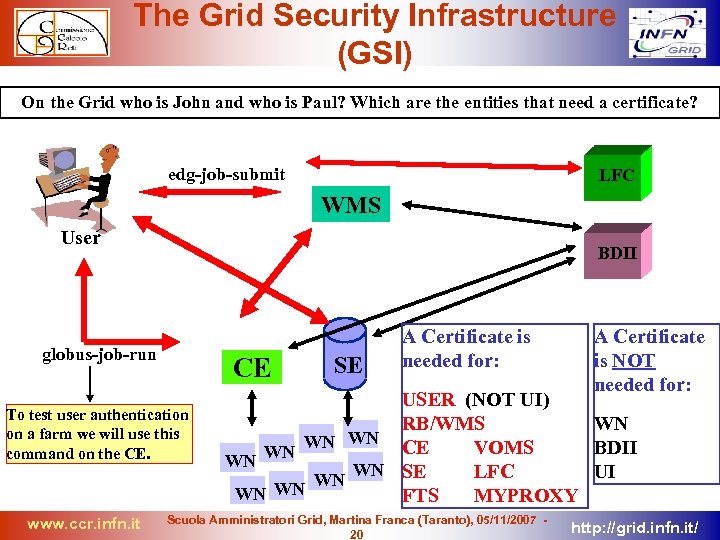 The Grid Security Infrastructure (GSI) On the Grid who is John and who is Paul? Which are the entities that need a certificate? edg-job-submit LFC WMS User BDII globus-job-run CE To test user authentication on a farm we will use this command on the CE. www. ccr. infn. it SE A Certificate is needed for: A Certificate is NOT needed for: USER (NOT UI) WN RB/WMS WN WN BDII CE VOMS WN WN WN SE UI LFC WN WN WN FTS MYPROXY Scuola Amministratori Grid, Martina Franca (Taranto), 05/11/2007 20 http: //grid. infn. it/
The Grid Security Infrastructure (GSI) On the Grid who is John and who is Paul? Which are the entities that need a certificate? edg-job-submit LFC WMS User BDII globus-job-run CE To test user authentication on a farm we will use this command on the CE. www. ccr. infn. it SE A Certificate is needed for: A Certificate is NOT needed for: USER (NOT UI) WN RB/WMS WN WN BDII CE VOMS WN WN WN SE UI LFC WN WN WN FTS MYPROXY Scuola Amministratori Grid, Martina Franca (Taranto), 05/11/2007 20 http: //grid. infn. it/
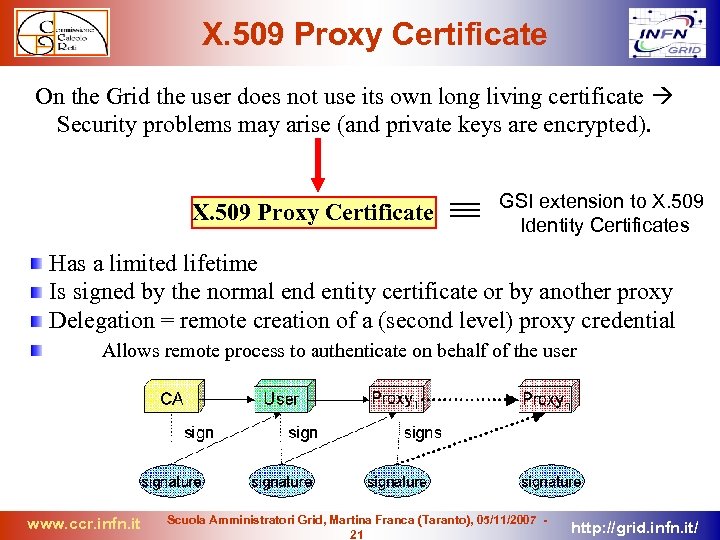 X. 509 Proxy Certificate On the Grid the user does not use its own long living certificate Security problems may arise (and private keys are encrypted). X. 509 Proxy Certificate GSI extension to X. 509 Identity Certificates Has a limited lifetime Is signed by the normal end entity certificate or by another proxy Delegation = remote creation of a (second level) proxy credential Allows remote process to authenticate on behalf of the user www. ccr. infn. it Scuola Amministratori Grid, Martina Franca (Taranto), 05/11/2007 21 http: //grid. infn. it/
X. 509 Proxy Certificate On the Grid the user does not use its own long living certificate Security problems may arise (and private keys are encrypted). X. 509 Proxy Certificate GSI extension to X. 509 Identity Certificates Has a limited lifetime Is signed by the normal end entity certificate or by another proxy Delegation = remote creation of a (second level) proxy credential Allows remote process to authenticate on behalf of the user www. ccr. infn. it Scuola Amministratori Grid, Martina Franca (Taranto), 05/11/2007 21 http: //grid. infn. it/
 grid-proxy-init Proxies can be created with the command grid-proxy-init Options for grid-proxy-init: • -hours
grid-proxy-init Proxies can be created with the command grid-proxy-init Options for grid-proxy-init: • -hours
![grid-proxy-init 1) Look inside your proxy certificate [cesini@grid 005 f]$cat /tmp/x 509. 519 -----BEGIN grid-proxy-init 1) Look inside your proxy certificate [cesini@grid 005 f]$cat /tmp/x 509. 519 -----BEGIN](https://present5.com/presentation/c41ad577ec545bcc2bb14b63829d2c22/image-23.jpg) grid-proxy-init 1) Look inside your proxy certificate [cesini@grid 005 f]$cat /tmp/x 509. 519 -----BEGIN CERTIFICATE----MIIC 9 j. CCAd 6 g. Aw. IBAg. ICCA 4 w. DQYJKo. ZIhvc. NAQ MQ 0 w. Cw. YDVQQKEw. RJTk. ZOMR 0 w. Gw. YDVQQLE 9 w 0 BCQEWG 2 Rhbmllb. GUu. Y 2 Vza. W 5 p. QGNu. YWYua NTVa. Fw 0 w. NTAy. MTgw. NDU 2 NTVa. MIGf. MQsw. CQY Tj. Ed. MBs. GA 1 UECx. MUUGVyc 29 u. YWwg. Q 2 Vyd. Glm Fz. AVBg. NVBAMTDk. Rhbmllb. GUg. Q 2 Vza. W 5 p. MSow. K -----END CERTIFICATE-----BEGIN RSA PRIVATE KEY----MIIBOw. IBAAJBALb. IP+z. Bmt 9 FDv+inwt. A/2 Bv 2 r. IZr. QQ Pri 2 Oh. Mar. WRBz. U 62 Xs 1 Cqk 6 UPKU 8 wg. Fl 8 R 8 CAwgfj Zfc. BJSx 5 a. J 0 qk. UOIPu 3+Gn. WJw. GKd. Sfj 94 Zw. QX 35 w. Vr. M 9 HECIQDzmx. MZVe. MIh 0 P 2 Dnwz. ENKs. HVOLKKqzs. S/z 7 Zc. O 00 c. Tg. CAuab. Oi. XEY 0 ci. Ow. Teaghv. Ovp. Ai. BE 0 Gyfvox. Ir aksif. Gk+z. UHVpw. Ig. LHDs 8 CSF 8 l. FOsk. AUx. KM 82 Upq. Zk a. Lxaj. QFUe 1 XJRc. Edf/nw 6 a. NFCc. Mx 2 j. DUWUp. Xvk 0+4 Q== -----END RSA PRIVATE KEY-----BEGIN CERTIFICATE----Lmlu. Zm 4 ua. XQw. PQYDVR 0 SBDYw. NIESa. W 5 mbi 1 j. YU c 2 Vjd. XJpd. Hku. Zmkua. W 5 mbi 5 pd. C 9 DQS 8 w. EQYJYIZIAY SAGG+EIBDQRKFkh. Jc 3 N 1 ZWQgd. W 5 k. ZXIg. SU 5 GTi. B IGh 0 d. HA 6 Ly 9 z. ZWN 1 cml 0 e. S 5 ma. S 5 pbm. Zu. Lml 0 L 0 NBL 0 BB 0 WG 2 h 0 d. HA 6 Ly 9 z. ZWN 1 cml 0 e. S 5 ma. S 5 pbm. Zu. Lml 0 L Y 2 dp. LWJpbi 9 ja. GVjay 1 y. ZXYuc. Gw/MCYGCWCGSAG ZWNr. LXJlbm. V 3 Ln. Bs. Pz. A 4 Bglghkg. Bhvh. CAQg. EKx. Ypa. H Lmlu. Zm 4 ua. XQv. Q 0 Evc. G 9 sa. WN 5 Lmh 0 b. Www. DQYJKo. ZI 3 o. N 9 Uepw. Lajqin. Sgl. Aadf 3 uqx. BCMgu. Isv. X 0 q. EFGk. Y 5706 mm. Sb. I+YP 4 q 4 c 9 a. Q 8 Cv 10 q 2 fi. Lbf. Go. Un 1 Pn. XKMao. DIw 5 C w. Pzjp. Mb. I 7 to. DDOmd 4 cm. BWb. C 3 uo. LZATVjcd. SJS 549 n. IEi. T EXDAup. NKu. Gjc. MIB 1 rm. RANY 2 h. A 3 Zmjdg. EYA/Wxbs. LQ id. KQ 0 h 5 DUmjd. Qj 9 jjd 2 pi. Gu. I 4 Ny. Ij. Mb. Z 9 o 0 u. OIy/1 Oq+q. FU gtkn. ZFInvkah 4 j. E= -----END CERTIFICATE----Scuola Amministratori www. ccr. infn. it grid-proxy-init + passphrase 2) Create two files with the certificates in your proxy and get information about them. Grid, Martina Franca (Taranto), 05/11/2007 23 http: //grid. infn. it/
grid-proxy-init 1) Look inside your proxy certificate [cesini@grid 005 f]$cat /tmp/x 509. 519 -----BEGIN CERTIFICATE----MIIC 9 j. CCAd 6 g. Aw. IBAg. ICCA 4 w. DQYJKo. ZIhvc. NAQ MQ 0 w. Cw. YDVQQKEw. RJTk. ZOMR 0 w. Gw. YDVQQLE 9 w 0 BCQEWG 2 Rhbmllb. GUu. Y 2 Vza. W 5 p. QGNu. YWYua NTVa. Fw 0 w. NTAy. MTgw. NDU 2 NTVa. MIGf. MQsw. CQY Tj. Ed. MBs. GA 1 UECx. MUUGVyc 29 u. YWwg. Q 2 Vyd. Glm Fz. AVBg. NVBAMTDk. Rhbmllb. GUg. Q 2 Vza. W 5 p. MSow. K -----END CERTIFICATE-----BEGIN RSA PRIVATE KEY----MIIBOw. IBAAJBALb. IP+z. Bmt 9 FDv+inwt. A/2 Bv 2 r. IZr. QQ Pri 2 Oh. Mar. WRBz. U 62 Xs 1 Cqk 6 UPKU 8 wg. Fl 8 R 8 CAwgfj Zfc. BJSx 5 a. J 0 qk. UOIPu 3+Gn. WJw. GKd. Sfj 94 Zw. QX 35 w. Vr. M 9 HECIQDzmx. MZVe. MIh 0 P 2 Dnwz. ENKs. HVOLKKqzs. S/z 7 Zc. O 00 c. Tg. CAuab. Oi. XEY 0 ci. Ow. Teaghv. Ovp. Ai. BE 0 Gyfvox. Ir aksif. Gk+z. UHVpw. Ig. LHDs 8 CSF 8 l. FOsk. AUx. KM 82 Upq. Zk a. Lxaj. QFUe 1 XJRc. Edf/nw 6 a. NFCc. Mx 2 j. DUWUp. Xvk 0+4 Q== -----END RSA PRIVATE KEY-----BEGIN CERTIFICATE----Lmlu. Zm 4 ua. XQw. PQYDVR 0 SBDYw. NIESa. W 5 mbi 1 j. YU c 2 Vjd. XJpd. Hku. Zmkua. W 5 mbi 5 pd. C 9 DQS 8 w. EQYJYIZIAY SAGG+EIBDQRKFkh. Jc 3 N 1 ZWQgd. W 5 k. ZXIg. SU 5 GTi. B IGh 0 d. HA 6 Ly 9 z. ZWN 1 cml 0 e. S 5 ma. S 5 pbm. Zu. Lml 0 L 0 NBL 0 BB 0 WG 2 h 0 d. HA 6 Ly 9 z. ZWN 1 cml 0 e. S 5 ma. S 5 pbm. Zu. Lml 0 L Y 2 dp. LWJpbi 9 ja. GVjay 1 y. ZXYuc. Gw/MCYGCWCGSAG ZWNr. LXJlbm. V 3 Ln. Bs. Pz. A 4 Bglghkg. Bhvh. CAQg. EKx. Ypa. H Lmlu. Zm 4 ua. XQv. Q 0 Evc. G 9 sa. WN 5 Lmh 0 b. Www. DQYJKo. ZI 3 o. N 9 Uepw. Lajqin. Sgl. Aadf 3 uqx. BCMgu. Isv. X 0 q. EFGk. Y 5706 mm. Sb. I+YP 4 q 4 c 9 a. Q 8 Cv 10 q 2 fi. Lbf. Go. Un 1 Pn. XKMao. DIw 5 C w. Pzjp. Mb. I 7 to. DDOmd 4 cm. BWb. C 3 uo. LZATVjcd. SJS 549 n. IEi. T EXDAup. NKu. Gjc. MIB 1 rm. RANY 2 h. A 3 Zmjdg. EYA/Wxbs. LQ id. KQ 0 h 5 DUmjd. Qj 9 jjd 2 pi. Gu. I 4 Ny. Ij. Mb. Z 9 o 0 u. OIy/1 Oq+q. FU gtkn. ZFInvkah 4 j. E= -----END CERTIFICATE----Scuola Amministratori www. ccr. infn. it grid-proxy-init + passphrase 2) Create two files with the certificates in your proxy and get information about them. Grid, Martina Franca (Taranto), 05/11/2007 23 http: //grid. infn. it/
![grid-proxy-init [cesini@grid 005 f cesini]$ grid-cert-info -all -f. /proxycert. pem Certificate: Data: Version: 3 grid-proxy-init [cesini@grid 005 f cesini]$ grid-cert-info -all -f. /proxycert. pem Certificate: Data: Version: 3](https://present5.com/presentation/c41ad577ec545bcc2bb14b63829d2c22/image-24.jpg) grid-proxy-init [cesini@grid 005 f cesini]$ grid-cert-info -all -f. /proxycert. pem Certificate: Data: Version: 3 (0 x 2) Serial Number: 2062 (0 x 80 e) Signature Algorithm: md 5 With. RSAEncryption Issuer: C=IT, O=INFN, OU=Personal Certificate, L=CNAF, CN=Daniele Cesini/Email=daniele. cesini@cnaf. infn. it Validity Not Before: Feb 17 16: 51: 55 2005 GMT Not After : Feb 18 04: 56: 55 2005 GMT Subject: C=IT, O=INFN, OU=Personal Certificate, L=CNAF, CN=Daniele Cesini/Email=daniele. cesini@cnaf. infn. it, CN=proxy Subject Public Key Info: Public Key Algorithm: rsa. Encryption RSA Public Key: (512 bit) Modulus (512 bit): …. . [cesini@grid 005 f cesini]$ grid-cert-info -all -f. /ucert. pem Certificate: Data: Version: 3 (0 x 2) Serial Number: 2062 (0 x 80 e) Signature Algorithm: md 5 With. RSAEncryption Issuer: C=IT, O=INFN, CN=INFN Certification Authority Validity Not Before: May 10 13: 15: 22 2004 GMT Not After : May 10 13: 15: 22 2005 GMT Subject: C=IT, O=INFN, OU=Personal Certificate, L=CNAF, CN=Daniele Cesini/Email=daniele. cesini@cnaf. infn. it Subject Public Key Info: Public Key Algorithm: rsa. Encryption RSA Public Key: (2048 bit) …. www. ccr. infn. it Scuola Amministratori Grid, Martina Franca (Taranto), 05/11/2007 24 http: //grid. infn. it/
grid-proxy-init [cesini@grid 005 f cesini]$ grid-cert-info -all -f. /proxycert. pem Certificate: Data: Version: 3 (0 x 2) Serial Number: 2062 (0 x 80 e) Signature Algorithm: md 5 With. RSAEncryption Issuer: C=IT, O=INFN, OU=Personal Certificate, L=CNAF, CN=Daniele Cesini/Email=daniele. cesini@cnaf. infn. it Validity Not Before: Feb 17 16: 51: 55 2005 GMT Not After : Feb 18 04: 56: 55 2005 GMT Subject: C=IT, O=INFN, OU=Personal Certificate, L=CNAF, CN=Daniele Cesini/Email=daniele. cesini@cnaf. infn. it, CN=proxy Subject Public Key Info: Public Key Algorithm: rsa. Encryption RSA Public Key: (512 bit) Modulus (512 bit): …. . [cesini@grid 005 f cesini]$ grid-cert-info -all -f. /ucert. pem Certificate: Data: Version: 3 (0 x 2) Serial Number: 2062 (0 x 80 e) Signature Algorithm: md 5 With. RSAEncryption Issuer: C=IT, O=INFN, CN=INFN Certification Authority Validity Not Before: May 10 13: 15: 22 2004 GMT Not After : May 10 13: 15: 22 2005 GMT Subject: C=IT, O=INFN, OU=Personal Certificate, L=CNAF, CN=Daniele Cesini/Email=daniele. cesini@cnaf. infn. it Subject Public Key Info: Public Key Algorithm: rsa. Encryption RSA Public Key: (2048 bit) …. www. ccr. infn. it Scuola Amministratori Grid, Martina Franca (Taranto), 05/11/2007 24 http: //grid. infn. it/
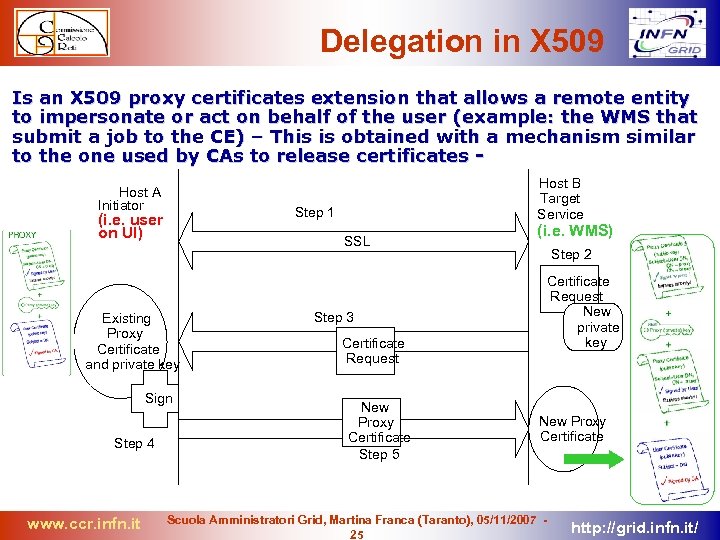 Delegation in X 509 Is an X 509 proxy certificates extension that allows a remote entity to impersonate or act on behalf of the user (example: the WMS that submit a job to the CE) – This is obtained with a mechanism similar to the one used by CAs to release certificates Host A Initiator Step 1 (i. e. user on UI) SSL Existing Proxy Certificate and private key Sign Step 4 www. ccr. infn. it Host B Target Service Step 3 Certificate Request New Proxy Certificate Step 5 (i. e. WMS) Step 2 Certificate Request New private key New Proxy Certificate Scuola Amministratori Grid, Martina Franca (Taranto), 05/11/2007 25 http: //grid. infn. it/
Delegation in X 509 Is an X 509 proxy certificates extension that allows a remote entity to impersonate or act on behalf of the user (example: the WMS that submit a job to the CE) – This is obtained with a mechanism similar to the one used by CAs to release certificates Host A Initiator Step 1 (i. e. user on UI) SSL Existing Proxy Certificate and private key Sign Step 4 www. ccr. infn. it Host B Target Service Step 3 Certificate Request New Proxy Certificate Step 5 (i. e. WMS) Step 2 Certificate Request New private key New Proxy Certificate Scuola Amministratori Grid, Martina Franca (Taranto), 05/11/2007 25 http: //grid. infn. it/
 grid-proxy-info grid-proxy-destroy • To gather information about your proxy: • grid-proxy-info • Options for printing proxy information -subject -type -strength -issuer -timeleft -help Compare the output of grid-proxy-info with the output of grid-cert-info on the file containing the first certificate of your proxy • To destroy your proxy: • grid-proxy-destroy • This does NOT destroy any proxies that were delegated from this proxy. • You cannot revoke a remote proxy CREATE SHORT LIVING PROXIES www. ccr. infn. it Scuola Amministratori Grid, Martina Franca (Taranto), 05/11/2007 26 http: //grid. infn. it/
grid-proxy-info grid-proxy-destroy • To gather information about your proxy: • grid-proxy-info • Options for printing proxy information -subject -type -strength -issuer -timeleft -help Compare the output of grid-proxy-info with the output of grid-cert-info on the file containing the first certificate of your proxy • To destroy your proxy: • grid-proxy-destroy • This does NOT destroy any proxies that were delegated from this proxy. • You cannot revoke a remote proxy CREATE SHORT LIVING PROXIES www. ccr. infn. it Scuola Amministratori Grid, Martina Franca (Taranto), 05/11/2007 26 http: //grid. infn. it/
 Virtual Organizations voms-proxy-init To submit to the Grid, personal certificates are not the end of the story. Users MUST joinat least one of the group allowed to use the Grid resources = Virtual Organization (VO) The proxy obtained with grid-proxy-init does not contain information about your VO The VOMS (Virtual Organization Membership Service) extends the proxy info with VO membership, group, role and capabilities. Related commands: voms-proxy-init voms-proxy-destroy voms-proxy-info www. ccr. infn. it Scuola Amministratori Grid, Martina Franca (Taranto), 05/11/2007 27 http: //grid. infn. it/
Virtual Organizations voms-proxy-init To submit to the Grid, personal certificates are not the end of the story. Users MUST joinat least one of the group allowed to use the Grid resources = Virtual Organization (VO) The proxy obtained with grid-proxy-init does not contain information about your VO The VOMS (Virtual Organization Membership Service) extends the proxy info with VO membership, group, role and capabilities. Related commands: voms-proxy-init voms-proxy-destroy voms-proxy-info www. ccr. infn. it Scuola Amministratori Grid, Martina Franca (Taranto), 05/11/2007 27 http: //grid. infn. it/
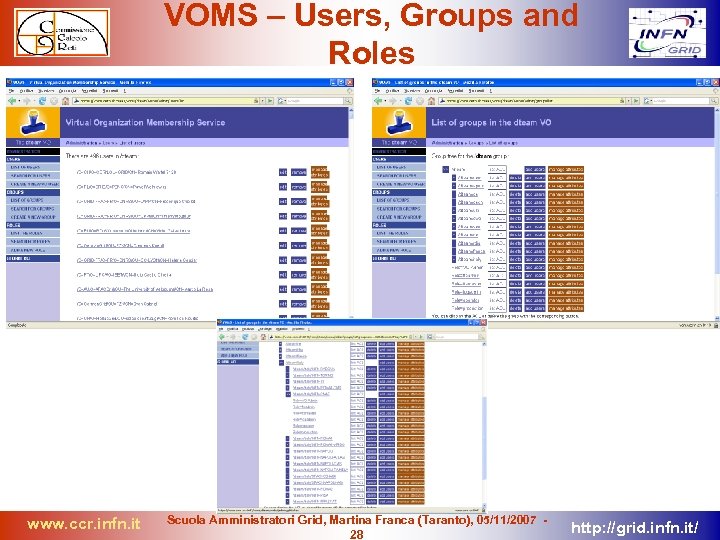 VOMS – Users, Groups and Roles www. ccr. infn. it Scuola Amministratori Grid, Martina Franca (Taranto), 05/11/2007 28 http: //grid. infn. it/
VOMS – Users, Groups and Roles www. ccr. infn. it Scuola Amministratori Grid, Martina Franca (Taranto), 05/11/2007 28 http: //grid. infn. it/
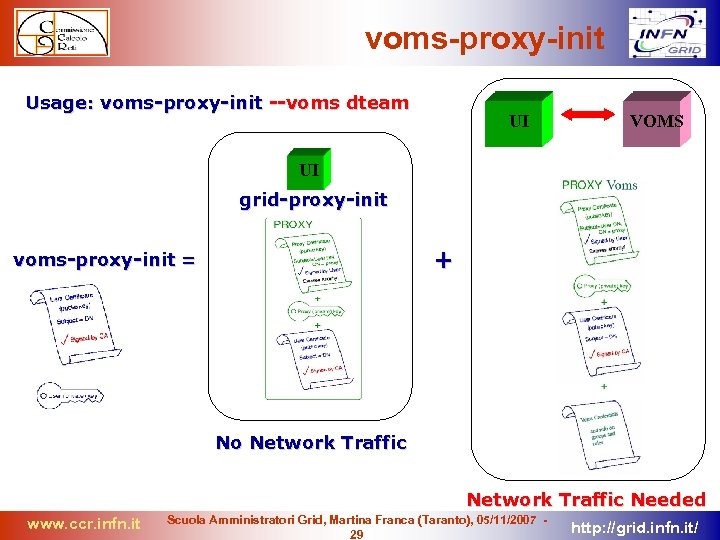 voms-proxy-init Usage: voms-proxy-init --voms dteam UI VOMS UI grid-proxy-init + voms-proxy-init = No Network Traffic Needed www. ccr. infn. it Scuola Amministratori Grid, Martina Franca (Taranto), 05/11/2007 29 http: //grid. infn. it/
voms-proxy-init Usage: voms-proxy-init --voms dteam UI VOMS UI grid-proxy-init + voms-proxy-init = No Network Traffic Needed www. ccr. infn. it Scuola Amministratori Grid, Martina Franca (Taranto), 05/11/2007 29 http: //grid. infn. it/
![voms-proxy-info [cesini@lcg-ui cesini]$ voms-proxy-init --voms dteam VO information [cesini@lcg-ui cesini]$ voms-proxy-info --all subject : voms-proxy-info [cesini@lcg-ui cesini]$ voms-proxy-init --voms dteam VO information [cesini@lcg-ui cesini]$ voms-proxy-info --all subject :](https://present5.com/presentation/c41ad577ec545bcc2bb14b63829d2c22/image-30.jpg) voms-proxy-info [cesini@lcg-ui cesini]$ voms-proxy-init --voms dteam VO information [cesini@lcg-ui cesini]$ voms-proxy-info --all subject : /C=IT/O=INFN/OU=Personal Certificate/L=CNAF/CN=Daniele Cesini/Email=daniele. cesini@cnaf. infn. it/CN=proxy issuer : /C=IT/O=INFN/OU=Personal Certificate/L=CNAF/CN=Daniele Cesini/Email=daniele. cesini@cnaf. infn. it identity : /C=IT/O=INFN/OU=Personal Certificate/L=CNAF/CN=Daniele Cesini/Email=daniele. cesini@cnaf. infn. it type : proxy strength : 512 bits path : /tmp/x 509 up_u 519 timeleft : 11: 59: 53 VO : dteam subject : /C=IT/O=INFN/OU=Personal Certificate/L=CNAF/CN=Daniele Cesini/Email=daniele. cesini@cnaf. infn. it issuer : /DC=ch/DC=cern/OU=computers/CN=voms. cern. ch attribute : /dteam/Role=NULL/Capability=NULL attribute : /dteam/italy/INFN-CNAF/Role=NULL/Capability=NULLe attribute : /dteam/italy/INFN-PADOVA/Role=NULL/Capability=NULL attribute : /dteam/italy/INFN-TORINO/Role=NULL/Capability=NULL attribute : /dteam/italy/SPACI-NAPOLI-IA 64/Role=NULL/Capability=NULL attribute : /dteam/italy/INFN-T 1/Role=NULL/Capability=NULL attribute : /dteam/italy/INFN-ROMA 1/Role=NULL/Capability=NULL Note there are 2 “timeleft”: attribute : /dteam/italy/INFN-ROMA 1 -CMS/Role=NULL/Capability=NULL attribute : /dteam/italy/INFN-ROMA 1 -VIRGO/Role=NULL/Capability=NULL - For the plain grid proxy – timeleft : 11: 59: 52 depends on UI configuration For the VOMS extension – dependes on VOMS server configuration --voms
voms-proxy-info [cesini@lcg-ui cesini]$ voms-proxy-init --voms dteam VO information [cesini@lcg-ui cesini]$ voms-proxy-info --all subject : /C=IT/O=INFN/OU=Personal Certificate/L=CNAF/CN=Daniele Cesini/Email=daniele. cesini@cnaf. infn. it/CN=proxy issuer : /C=IT/O=INFN/OU=Personal Certificate/L=CNAF/CN=Daniele Cesini/Email=daniele. cesini@cnaf. infn. it identity : /C=IT/O=INFN/OU=Personal Certificate/L=CNAF/CN=Daniele Cesini/Email=daniele. cesini@cnaf. infn. it type : proxy strength : 512 bits path : /tmp/x 509 up_u 519 timeleft : 11: 59: 53 VO : dteam subject : /C=IT/O=INFN/OU=Personal Certificate/L=CNAF/CN=Daniele Cesini/Email=daniele. cesini@cnaf. infn. it issuer : /DC=ch/DC=cern/OU=computers/CN=voms. cern. ch attribute : /dteam/Role=NULL/Capability=NULL attribute : /dteam/italy/INFN-CNAF/Role=NULL/Capability=NULLe attribute : /dteam/italy/INFN-PADOVA/Role=NULL/Capability=NULL attribute : /dteam/italy/INFN-TORINO/Role=NULL/Capability=NULL attribute : /dteam/italy/SPACI-NAPOLI-IA 64/Role=NULL/Capability=NULL attribute : /dteam/italy/INFN-T 1/Role=NULL/Capability=NULL attribute : /dteam/italy/INFN-ROMA 1/Role=NULL/Capability=NULL Note there are 2 “timeleft”: attribute : /dteam/italy/INFN-ROMA 1 -CMS/Role=NULL/Capability=NULL attribute : /dteam/italy/INFN-ROMA 1 -VIRGO/Role=NULL/Capability=NULL - For the plain grid proxy – timeleft : 11: 59: 52 depends on UI configuration For the VOMS extension – dependes on VOMS server configuration --voms
 Long term proxy - myproxy Grid tasks may need a time longer than the proxy lifetime (short for security reasons) A myproxy server is used to create and store a long term proxy which is used to renew short term proxies when they are going to expire. Related commands: myproxy-init myproxy-get-delegation myproxy-destroy • A dedicated service on the RB/WMS can renew automatically the proxy on behalf of you contacting the myproxy server (the myproxy server should by indicated in the job jdl) www. ccr. infn. it Scuola Amministratori Grid, Martina Franca (Taranto), 05/11/2007 31 http: //grid. infn. it/
Long term proxy - myproxy Grid tasks may need a time longer than the proxy lifetime (short for security reasons) A myproxy server is used to create and store a long term proxy which is used to renew short term proxies when they are going to expire. Related commands: myproxy-init myproxy-get-delegation myproxy-destroy • A dedicated service on the RB/WMS can renew automatically the proxy on behalf of you contacting the myproxy server (the myproxy server should by indicated in the job jdl) www. ccr. infn. it Scuola Amministratori Grid, Martina Franca (Taranto), 05/11/2007 31 http: //grid. infn. it/
 Authorization, Authentication and Mapping Authentication = the user is who is claiming to be. Authorization = the remote user can access local resources. Can be based on local policies. Mapping =local resources don’t know anything about the remote user identity a mapping from Grid credential to local credential (i. e. UNIX uid/gid) is needed POOL ACCOUNTS www. ccr. infn. it Scuola Amministratori Grid, Martina Franca (Taranto), 05/11/2007 32 http: //grid. infn. it/
Authorization, Authentication and Mapping Authentication = the user is who is claiming to be. Authorization = the remote user can access local resources. Can be based on local policies. Mapping =local resources don’t know anything about the remote user identity a mapping from Grid credential to local credential (i. e. UNIX uid/gid) is needed POOL ACCOUNTS www. ccr. infn. it Scuola Amministratori Grid, Martina Franca (Taranto), 05/11/2007 32 http: //grid. infn. it/
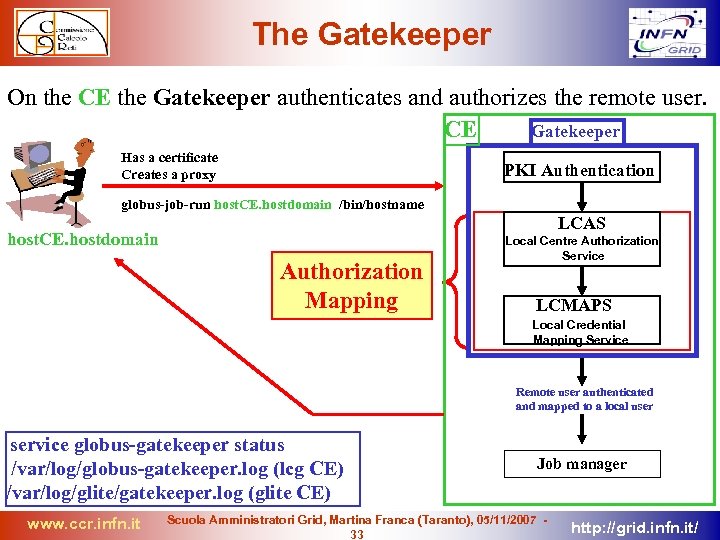 The Gatekeeper On the CE the Gatekeeper authenticates and authorizes the remote user. CE Gatekeeper Has a certificate Creates a proxy PKI Authentication globus-job-run host. CE. hostdomain /bin/hostname LCAS host. CE. hostdomain Authorization Mapping Local Centre Authorization Service LCMAPS Local Credential Mapping Service Remote user authenticated and mapped to a local user service globus-gatekeeper status /var/log/globus-gatekeeper. log (lcg CE) /var/log/glite/gatekeeper. log (glite CE) www. ccr. infn. it Job manager Scuola Amministratori Grid, Martina Franca (Taranto), 05/11/2007 33 http: //grid. infn. it/
The Gatekeeper On the CE the Gatekeeper authenticates and authorizes the remote user. CE Gatekeeper Has a certificate Creates a proxy PKI Authentication globus-job-run host. CE. hostdomain /bin/hostname LCAS host. CE. hostdomain Authorization Mapping Local Centre Authorization Service LCMAPS Local Credential Mapping Service Remote user authenticated and mapped to a local user service globus-gatekeeper status /var/log/globus-gatekeeper. log (lcg CE) /var/log/glite/gatekeeper. log (glite CE) www. ccr. infn. it Job manager Scuola Amministratori Grid, Martina Franca (Taranto), 05/11/2007 33 http: //grid. infn. it/
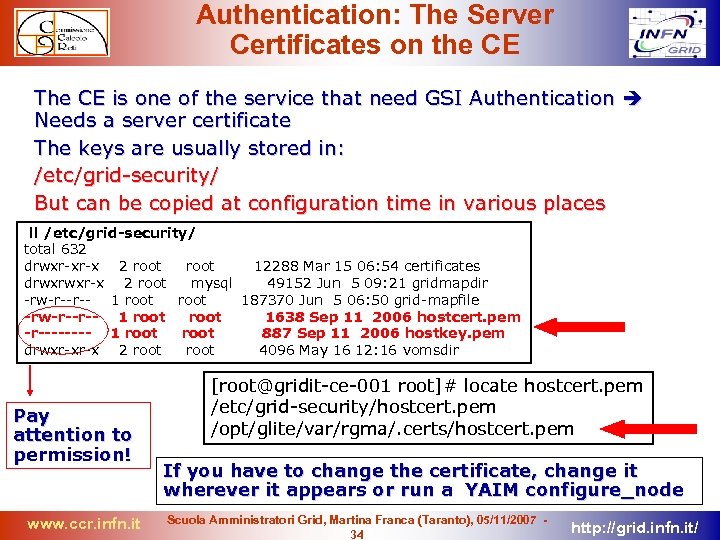 Authentication: The Server Certificates on the CE The CE is one of the service that need GSI Authentication Needs a server certificate The keys are usually stored in: /etc/grid-security/ But can be copied at configuration time in various places ll /etc/grid-security/ total 632 drwxr-xr-x 2 root 12288 Mar 15 06: 54 certificates drwxrwxr-x 2 root mysql 49152 Jun 5 09: 21 gridmapdir -rw-r--r-- 1 root 187370 Jun 5 06: 50 grid-mapfile -rw-r--r-- 1 root 1638 Sep 11 2006 hostcert. pem -r---- 1 root 887 Sep 11 2006 hostkey. pem drwxr-xr-x 2 root 4096 May 16 12: 16 vomsdir Pay attention to permission! www. ccr. infn. it [root@gridit-ce-001 root]# locate hostcert. pem /etc/grid-security/hostcert. pem /opt/glite/var/rgma/. certs/hostcert. pem If you have to change the certificate, change it wherever it appears or run a YAIM configure_node Scuola Amministratori Grid, Martina Franca (Taranto), 05/11/2007 34 http: //grid. infn. it/
Authentication: The Server Certificates on the CE The CE is one of the service that need GSI Authentication Needs a server certificate The keys are usually stored in: /etc/grid-security/ But can be copied at configuration time in various places ll /etc/grid-security/ total 632 drwxr-xr-x 2 root 12288 Mar 15 06: 54 certificates drwxrwxr-x 2 root mysql 49152 Jun 5 09: 21 gridmapdir -rw-r--r-- 1 root 187370 Jun 5 06: 50 grid-mapfile -rw-r--r-- 1 root 1638 Sep 11 2006 hostcert. pem -r---- 1 root 887 Sep 11 2006 hostkey. pem drwxr-xr-x 2 root 4096 May 16 12: 16 vomsdir Pay attention to permission! www. ccr. infn. it [root@gridit-ce-001 root]# locate hostcert. pem /etc/grid-security/hostcert. pem /opt/glite/var/rgma/. certs/hostcert. pem If you have to change the certificate, change it wherever it appears or run a YAIM configure_node Scuola Amministratori Grid, Martina Franca (Taranto), 05/11/2007 34 http: //grid. infn. it/
 Authentication: The CA on the Computing Element To accept the remote user’s job the CE must trust the CA that signs the usercert. A CA is trusted if its certificate is in /etc/grid-security/certificates They are normally installed through rpms (one per CA): [root@gridit-ce-001 root]# rpm -ql ca_INFN-CA-2006 -1. 17 -1 /etc/grid-security/certificates/2 f 3 fadf 6. 0 /etc/grid-security/certificates/2 f 3 fadf 6. crl_url /etc/grid-security/certificates/2 f 3 fadf 6. info /etc/grid-security/certificates/2 f 3 fadf 6. signing_policy /etc/grid-security/certificates/2 f 3 fadf 6. namespaces CA certificate crl contact string info about CA How CA creates the DN PAY ATTENTION: CRL are downloaded trough a cron job. CRLs has name of the kind: -rw-r--r-- 1 root 35377 Oct 29 10: 28 /etc/grid-security/certificates/2 f 3 fadf 6. r 0 CRLs have an expire time If a CRL expires ALL the corresponding CA certificates are considered expired. cat /etc/cron. d/fetch-crl PATH=/sbin: /usr/sbin: /usr/bin 38 14, 20, 2, 8 * * * root /opt/glite/libexec/fetch-crl. sh >> /var/log/fetch-crl-cron. log 2>&1 www. ccr. infn. it Scuola Amministratori Grid, Martina Franca (Taranto), 05/11/2007 35 http: //grid. infn. it/
Authentication: The CA on the Computing Element To accept the remote user’s job the CE must trust the CA that signs the usercert. A CA is trusted if its certificate is in /etc/grid-security/certificates They are normally installed through rpms (one per CA): [root@gridit-ce-001 root]# rpm -ql ca_INFN-CA-2006 -1. 17 -1 /etc/grid-security/certificates/2 f 3 fadf 6. 0 /etc/grid-security/certificates/2 f 3 fadf 6. crl_url /etc/grid-security/certificates/2 f 3 fadf 6. info /etc/grid-security/certificates/2 f 3 fadf 6. signing_policy /etc/grid-security/certificates/2 f 3 fadf 6. namespaces CA certificate crl contact string info about CA How CA creates the DN PAY ATTENTION: CRL are downloaded trough a cron job. CRLs has name of the kind: -rw-r--r-- 1 root 35377 Oct 29 10: 28 /etc/grid-security/certificates/2 f 3 fadf 6. r 0 CRLs have an expire time If a CRL expires ALL the corresponding CA certificates are considered expired. cat /etc/cron. d/fetch-crl PATH=/sbin: /usr/sbin: /usr/bin 38 14, 20, 2, 8 * * * root /opt/glite/libexec/fetch-crl. sh >> /var/log/fetch-crl-cron. log 2>&1 www. ccr. infn. it Scuola Amministratori Grid, Martina Franca (Taranto), 05/11/2007 35 http: //grid. infn. it/
 Authorization/Mapping on the CE Two files are vital for authentication/mapping on the CE: • GRIDMAPFILE • GROUPMAPFILE The first one lists the allowed VO(Users) and sets the UID on which the user is mapped, the second one sets the GID Attention: There can be more than one gridmafile and more than one groupmapfile in your system (see later). Typical locations are: /opt/edg/etc/lcmaps/ /etc/grid-security/ www. ccr. infn. it Scuola Amministratori Grid, Martina Franca (Taranto), 05/11/2007 36 http: //grid. infn. it/
Authorization/Mapping on the CE Two files are vital for authentication/mapping on the CE: • GRIDMAPFILE • GROUPMAPFILE The first one lists the allowed VO(Users) and sets the UID on which the user is mapped, the second one sets the GID Attention: There can be more than one gridmafile and more than one groupmapfile in your system (see later). Typical locations are: /opt/edg/etc/lcmaps/ /etc/grid-security/ www. ccr. infn. it Scuola Amministratori Grid, Martina Franca (Taranto), 05/11/2007 36 http: //grid. infn. it/
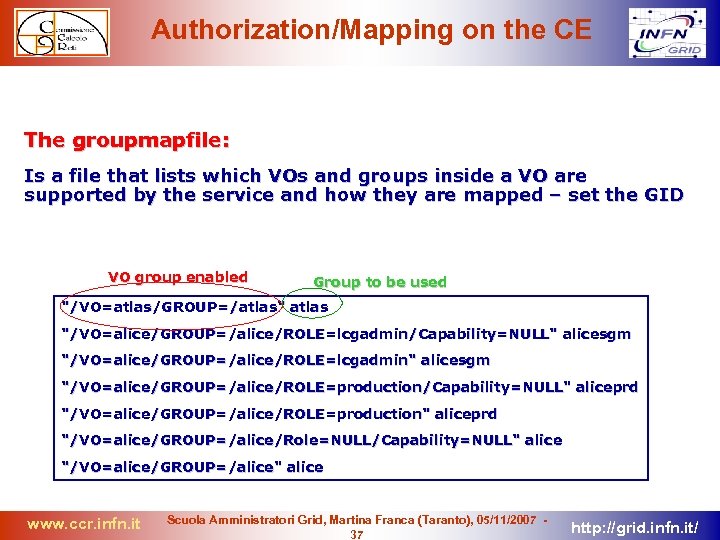 Authorization/Mapping on the CE The groupmapfile: Is a file that lists which VOs and groups inside a VO are supported by the service and how they are mapped – set the GID VO group enabled Group to be used "/VO=atlas/GROUP=/atlas" atlas "/VO=alice/GROUP=/alice/ROLE=lcgadmin/Capability=NULL" alicesgm "/VO=alice/GROUP=/alice/ROLE=lcgadmin" alicesgm "/VO=alice/GROUP=/alice/ROLE=production/Capability=NULL" aliceprd "/VO=alice/GROUP=/alice/ROLE=production" aliceprd "/VO=alice/GROUP=/alice/Role=NULL/Capability=NULL" alice "/VO=alice/GROUP=/alice" alice www. ccr. infn. it Scuola Amministratori Grid, Martina Franca (Taranto), 05/11/2007 37 http: //grid. infn. it/
Authorization/Mapping on the CE The groupmapfile: Is a file that lists which VOs and groups inside a VO are supported by the service and how they are mapped – set the GID VO group enabled Group to be used "/VO=atlas/GROUP=/atlas" atlas "/VO=alice/GROUP=/alice/ROLE=lcgadmin/Capability=NULL" alicesgm "/VO=alice/GROUP=/alice/ROLE=lcgadmin" alicesgm "/VO=alice/GROUP=/alice/ROLE=production/Capability=NULL" aliceprd "/VO=alice/GROUP=/alice/ROLE=production" aliceprd "/VO=alice/GROUP=/alice/Role=NULL/Capability=NULL" alice "/VO=alice/GROUP=/alice" alice www. ccr. infn. it Scuola Amministratori Grid, Martina Franca (Taranto), 05/11/2007 37 http: //grid. infn. it/
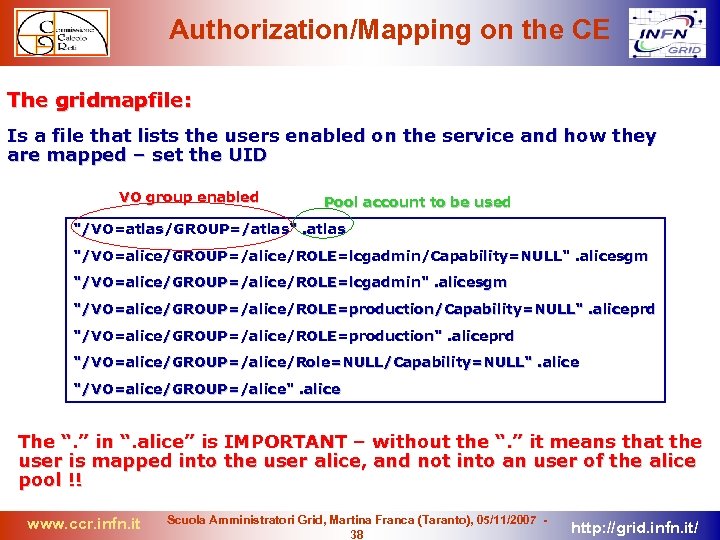 Authorization/Mapping on the CE The gridmapfile: Is a file that lists the users enabled on the service and how they are mapped – set the UID VO group enabled Pool account to be used "/VO=atlas/GROUP=/atlas". atlas "/VO=alice/GROUP=/alice/ROLE=lcgadmin/Capability=NULL". alicesgm "/VO=alice/GROUP=/alice/ROLE=lcgadmin". alicesgm "/VO=alice/GROUP=/alice/ROLE=production/Capability=NULL". aliceprd "/VO=alice/GROUP=/alice/ROLE=production". aliceprd "/VO=alice/GROUP=/alice/Role=NULL/Capability=NULL". alice "/VO=alice/GROUP=/alice". alice The “. ” in “. alice” is IMPORTANT – without the “. ” it means that the user is mapped into the user alice, and not into an user of the alice pool !! www. ccr. infn. it Scuola Amministratori Grid, Martina Franca (Taranto), 05/11/2007 38 http: //grid. infn. it/
Authorization/Mapping on the CE The gridmapfile: Is a file that lists the users enabled on the service and how they are mapped – set the UID VO group enabled Pool account to be used "/VO=atlas/GROUP=/atlas". atlas "/VO=alice/GROUP=/alice/ROLE=lcgadmin/Capability=NULL". alicesgm "/VO=alice/GROUP=/alice/ROLE=lcgadmin". alicesgm "/VO=alice/GROUP=/alice/ROLE=production/Capability=NULL". aliceprd "/VO=alice/GROUP=/alice/ROLE=production". aliceprd "/VO=alice/GROUP=/alice/Role=NULL/Capability=NULL". alice "/VO=alice/GROUP=/alice". alice The “. ” in “. alice” is IMPORTANT – without the “. ” it means that the user is mapped into the user alice, and not into an user of the alice pool !! www. ccr. infn. it Scuola Amministratori Grid, Martina Franca (Taranto), 05/11/2007 38 http: //grid. infn. it/
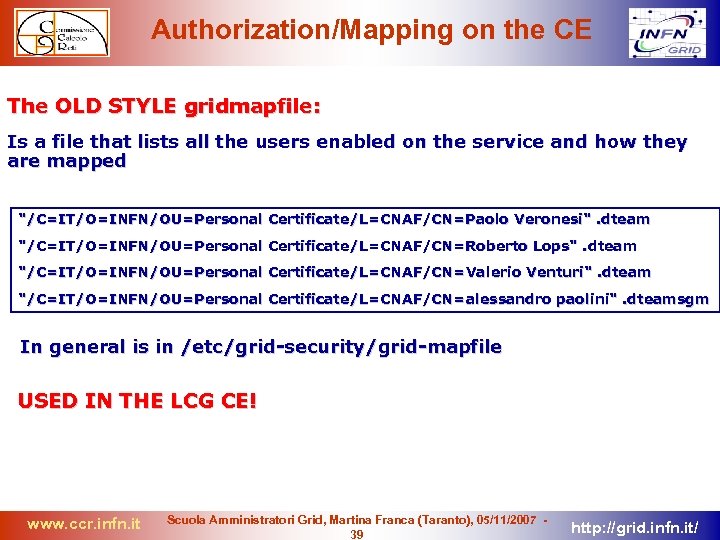 Authorization/Mapping on the CE The OLD STYLE gridmapfile: Is a file that lists all the users enabled on the service and how they are mapped "/C=IT/O=INFN/OU=Personal Certificate/L=CNAF/CN=Paolo Veronesi". dteam "/C=IT/O=INFN/OU=Personal Certificate/L=CNAF/CN=Roberto Lops". dteam "/C=IT/O=INFN/OU=Personal Certificate/L=CNAF/CN=Valerio Venturi". dteam "/C=IT/O=INFN/OU=Personal Certificate/L=CNAF/CN=alessandro paolini". dteamsgm In general is in /etc/grid-security/grid-mapfile USED IN THE LCG CE! www. ccr. infn. it Scuola Amministratori Grid, Martina Franca (Taranto), 05/11/2007 39 http: //grid. infn. it/
Authorization/Mapping on the CE The OLD STYLE gridmapfile: Is a file that lists all the users enabled on the service and how they are mapped "/C=IT/O=INFN/OU=Personal Certificate/L=CNAF/CN=Paolo Veronesi". dteam "/C=IT/O=INFN/OU=Personal Certificate/L=CNAF/CN=Roberto Lops". dteam "/C=IT/O=INFN/OU=Personal Certificate/L=CNAF/CN=Valerio Venturi". dteam "/C=IT/O=INFN/OU=Personal Certificate/L=CNAF/CN=alessandro paolini". dteamsgm In general is in /etc/grid-security/grid-mapfile USED IN THE LCG CE! www. ccr. infn. it Scuola Amministratori Grid, Martina Franca (Taranto), 05/11/2007 39 http: //grid. infn. it/
 Authorization on the CE: LCAS: • Authorizes the users. If LCAS fails for any reason no more actions are taken. The user is not allowed. • LCAS logs on the gatekeeper log file. • Based on a plugin scheme to support multiple auth. Policies – Timeslot, userban, userallow, VOMS • Configuration on the lcas. db file (Location of the lcas. db file in use is in the gatekeeper conf file: /opt/globus/etc/globus-gatekeeper. conf for the lcg CE) [root@gridit-ce-001 root]# cat /opt/edg/etc/lcas. db pluginname=lcas_userban. mod, pluginargs=ban_users. db pluginname=lcas_timeslots. mod, pluginargs=timeslots. db pluginname=lcas_plugin_example. mod, pluginargs=arguments CE LCG [root@glite-ce-01 root]# cat /opt/glite/etc/lcas. db CE g. Lite pluginname=lcas_userban. mod, pluginargs=ban_users. db pluginname=lcas_voms. mod, pluginargs="-vomsdir /etc/grid-security/vomsdir -certdir /etc/gridsecurity/certificates -authfile /etc/grid-security/grid-mapfile -authformat simple use_user_dn" www. ccr. infn. it Scuola Amministratori Grid, Martina Franca (Taranto), 05/11/2007 40 http: //grid. infn. it/
Authorization on the CE: LCAS: • Authorizes the users. If LCAS fails for any reason no more actions are taken. The user is not allowed. • LCAS logs on the gatekeeper log file. • Based on a plugin scheme to support multiple auth. Policies – Timeslot, userban, userallow, VOMS • Configuration on the lcas. db file (Location of the lcas. db file in use is in the gatekeeper conf file: /opt/globus/etc/globus-gatekeeper. conf for the lcg CE) [root@gridit-ce-001 root]# cat /opt/edg/etc/lcas. db pluginname=lcas_userban. mod, pluginargs=ban_users. db pluginname=lcas_timeslots. mod, pluginargs=timeslots. db pluginname=lcas_plugin_example. mod, pluginargs=arguments CE LCG [root@glite-ce-01 root]# cat /opt/glite/etc/lcas. db CE g. Lite pluginname=lcas_userban. mod, pluginargs=ban_users. db pluginname=lcas_voms. mod, pluginargs="-vomsdir /etc/grid-security/vomsdir -certdir /etc/gridsecurity/certificates -authfile /etc/grid-security/grid-mapfile -authformat simple use_user_dn" www. ccr. infn. it Scuola Amministratori Grid, Martina Franca (Taranto), 05/11/2007 40 http: //grid. infn. it/
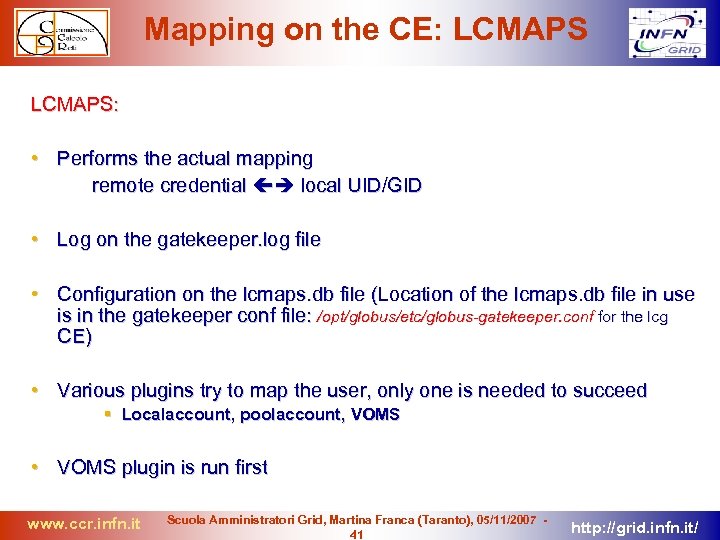 Mapping on the CE: LCMAPS: • Performs the actual mapping remote credential local UID/GID • Log on the gatekeeper. log file • Configuration on the lcmaps. db file (Location of the lcmaps. db file in use is in the gatekeeper conf file: /opt/globus/etc/globus-gatekeeper. conf for the lcg CE) • Various plugins try to map the user, only one is needed to succeed Localaccount, poolaccount, VOMS • VOMS plugin is run first www. ccr. infn. it Scuola Amministratori Grid, Martina Franca (Taranto), 05/11/2007 41 http: //grid. infn. it/
Mapping on the CE: LCMAPS: • Performs the actual mapping remote credential local UID/GID • Log on the gatekeeper. log file • Configuration on the lcmaps. db file (Location of the lcmaps. db file in use is in the gatekeeper conf file: /opt/globus/etc/globus-gatekeeper. conf for the lcg CE) • Various plugins try to map the user, only one is needed to succeed Localaccount, poolaccount, VOMS • VOMS plugin is run first www. ccr. infn. it Scuola Amministratori Grid, Martina Franca (Taranto), 05/11/2007 41 http: //grid. infn. it/
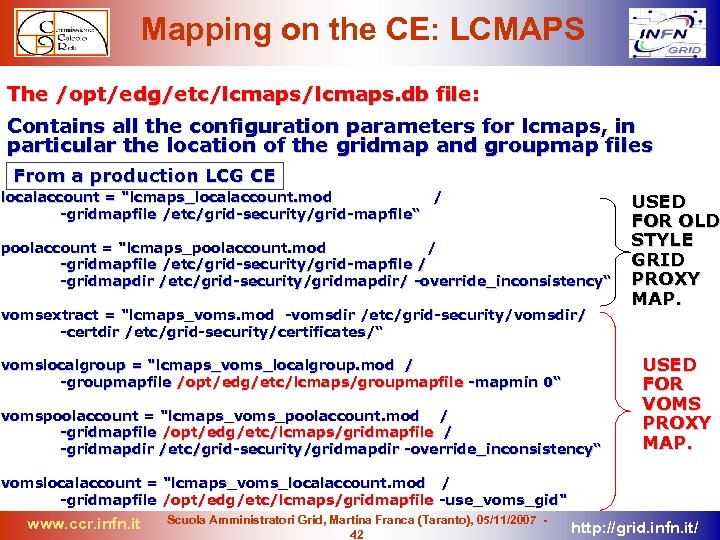 Mapping on the CE: LCMAPS The /opt/edg/etc/lcmaps. db file: Contains all the configuration parameters for lcmaps, in particular the location of the gridmap and groupmap files From a production LCG CE localaccount = "lcmaps_localaccount. mod / -gridmapfile /etc/grid-security/grid-mapfile“ poolaccount = "lcmaps_poolaccount. mod / -gridmapfile /etc/grid-security/grid-mapfile / -gridmapdir /etc/grid-security/gridmapdir/ -override_inconsistency“ vomsextract = "lcmaps_voms. mod -vomsdir /etc/grid-security/vomsdir/ -certdir /etc/grid-security/certificates/“ vomslocalgroup = "lcmaps_voms_localgroup. mod / -groupmapfile /opt/edg/etc/lcmaps/groupmapfile -mapmin 0“ vomspoolaccount = "lcmaps_voms_poolaccount. mod / -gridmapfile /opt/edg/etc/lcmaps/gridmapfile / -gridmapdir /etc/grid-security/gridmapdir -override_inconsistency“ USED FOR OLD STYLE GRID PROXY MAP. USED FOR VOMS PROXY MAP. vomslocalaccount = "lcmaps_voms_localaccount. mod / -gridmapfile /opt/edg/etc/lcmaps/gridmapfile -use_voms_gid" www. ccr. infn. it Scuola Amministratori Grid, Martina Franca (Taranto), 05/11/2007 42 http: //grid. infn. it/
Mapping on the CE: LCMAPS The /opt/edg/etc/lcmaps. db file: Contains all the configuration parameters for lcmaps, in particular the location of the gridmap and groupmap files From a production LCG CE localaccount = "lcmaps_localaccount. mod / -gridmapfile /etc/grid-security/grid-mapfile“ poolaccount = "lcmaps_poolaccount. mod / -gridmapfile /etc/grid-security/grid-mapfile / -gridmapdir /etc/grid-security/gridmapdir/ -override_inconsistency“ vomsextract = "lcmaps_voms. mod -vomsdir /etc/grid-security/vomsdir/ -certdir /etc/grid-security/certificates/“ vomslocalgroup = "lcmaps_voms_localgroup. mod / -groupmapfile /opt/edg/etc/lcmaps/groupmapfile -mapmin 0“ vomspoolaccount = "lcmaps_voms_poolaccount. mod / -gridmapfile /opt/edg/etc/lcmaps/gridmapfile / -gridmapdir /etc/grid-security/gridmapdir -override_inconsistency“ USED FOR OLD STYLE GRID PROXY MAP. USED FOR VOMS PROXY MAP. vomslocalaccount = "lcmaps_voms_localaccount. mod / -gridmapfile /opt/edg/etc/lcmaps/gridmapfile -use_voms_gid" www. ccr. infn. it Scuola Amministratori Grid, Martina Franca (Taranto), 05/11/2007 42 http: //grid. infn. it/
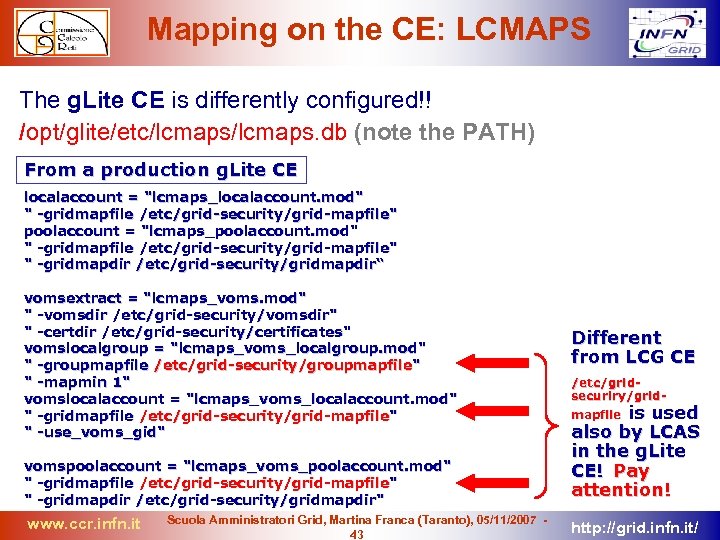 Mapping on the CE: LCMAPS The g. Lite CE is differently configured!! /opt/glite/etc/lcmaps. db (note the PATH) From a production g. Lite CE localaccount = "lcmaps_localaccount. mod" " -gridmapfile /etc/grid-security/grid-mapfile" poolaccount = "lcmaps_poolaccount. mod" " -gridmapfile /etc/grid-security/grid-mapfile" " -gridmapdir /etc/grid-security/gridmapdir“ vomsextract = "lcmaps_voms. mod" " -vomsdir /etc/grid-security/vomsdir" " -certdir /etc/grid-security/certificates" vomslocalgroup = "lcmaps_voms_localgroup. mod" " -groupmapfile /etc/grid-security/groupmapfile" " -mapmin 1" vomslocalaccount = "lcmaps_voms_localaccount. mod" " -gridmapfile /etc/grid-security/grid-mapfile" " -use_voms_gid" vomspoolaccount = "lcmaps_voms_poolaccount. mod" " -gridmapfile /etc/grid-security/grid-mapfile" " -gridmapdir /etc/grid-security/gridmapdir" www. ccr. infn. it Scuola Amministratori Grid, Martina Franca (Taranto), 05/11/2007 43 Different from LCG CE /etc/gridsecuriry/gridmapfile is used also by LCAS in the g. Lite CE! Pay attention! http: //grid. infn. it/
Mapping on the CE: LCMAPS The g. Lite CE is differently configured!! /opt/glite/etc/lcmaps. db (note the PATH) From a production g. Lite CE localaccount = "lcmaps_localaccount. mod" " -gridmapfile /etc/grid-security/grid-mapfile" poolaccount = "lcmaps_poolaccount. mod" " -gridmapfile /etc/grid-security/grid-mapfile" " -gridmapdir /etc/grid-security/gridmapdir“ vomsextract = "lcmaps_voms. mod" " -vomsdir /etc/grid-security/vomsdir" " -certdir /etc/grid-security/certificates" vomslocalgroup = "lcmaps_voms_localgroup. mod" " -groupmapfile /etc/grid-security/groupmapfile" " -mapmin 1" vomslocalaccount = "lcmaps_voms_localaccount. mod" " -gridmapfile /etc/grid-security/grid-mapfile" " -use_voms_gid" vomspoolaccount = "lcmaps_voms_poolaccount. mod" " -gridmapfile /etc/grid-security/grid-mapfile" " -gridmapdir /etc/grid-security/gridmapdir" www. ccr. infn. it Scuola Amministratori Grid, Martina Franca (Taranto), 05/11/2007 43 Different from LCG CE /etc/gridsecuriry/gridmapfile is used also by LCAS in the g. Lite CE! Pay attention! http: //grid. infn. it/
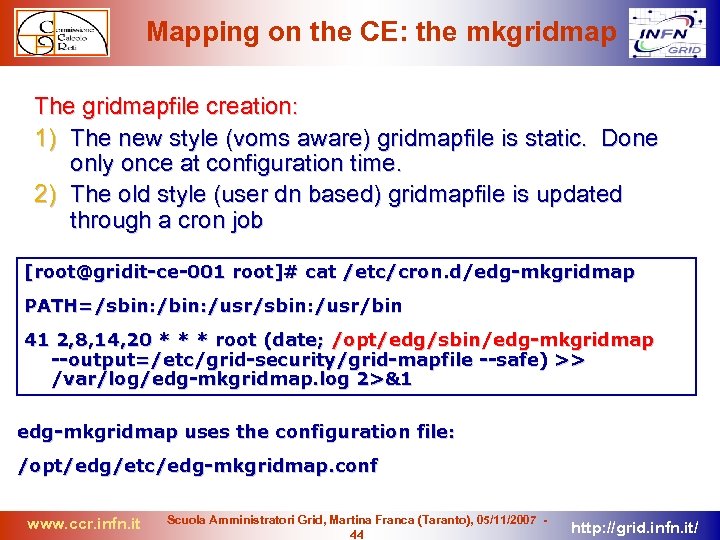 Mapping on the CE: the mkgridmap The gridmapfile creation: 1) The new style (voms aware) gridmapfile is static. Done only once at configuration time. 2) The old style (user dn based) gridmapfile is updated through a cron job [root@gridit-ce-001 root]# cat /etc/cron. d/edg-mkgridmap PATH=/sbin: /usr/sbin: /usr/bin 41 2, 8, 14, 20 * * * root (date; /opt/edg/sbin/edg-mkgridmap --output=/etc/grid-security/grid-mapfile --safe) >> /var/log/edg-mkgridmap. log 2>&1 edg-mkgridmap uses the configuration file: /opt/edg/etc/edg-mkgridmap. conf www. ccr. infn. it Scuola Amministratori Grid, Martina Franca (Taranto), 05/11/2007 44 http: //grid. infn. it/
Mapping on the CE: the mkgridmap The gridmapfile creation: 1) The new style (voms aware) gridmapfile is static. Done only once at configuration time. 2) The old style (user dn based) gridmapfile is updated through a cron job [root@gridit-ce-001 root]# cat /etc/cron. d/edg-mkgridmap PATH=/sbin: /usr/sbin: /usr/bin 41 2, 8, 14, 20 * * * root (date; /opt/edg/sbin/edg-mkgridmap --output=/etc/grid-security/grid-mapfile --safe) >> /var/log/edg-mkgridmap. log 2>&1 edg-mkgridmap uses the configuration file: /opt/edg/etc/edg-mkgridmap. conf www. ccr. infn. it Scuola Amministratori Grid, Martina Franca (Taranto), 05/11/2007 44 http: //grid. infn. it/
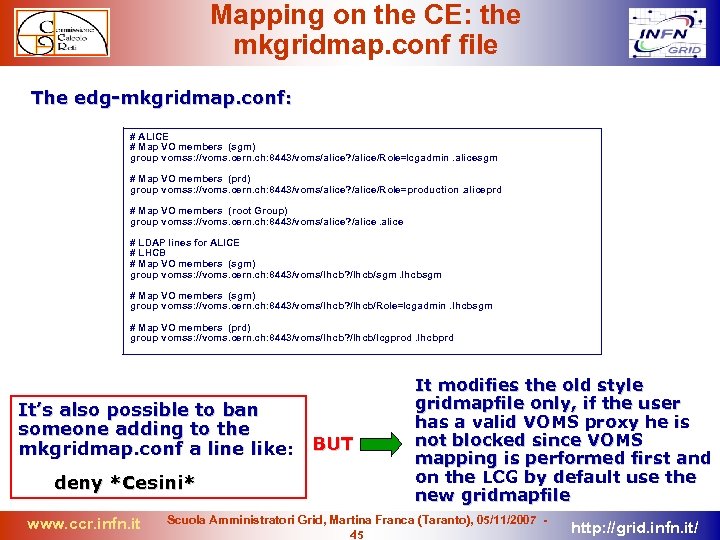 Mapping on the CE: the mkgridmap. conf file The edg-mkgridmap. conf: # ALICE # Map VO members (sgm) group vomss: //voms. cern. ch: 8443/voms/alice? /alice/Role=lcgadmin. alicesgm # Map VO members (prd) group vomss: //voms. cern. ch: 8443/voms/alice? /alice/Role=production. aliceprd # Map VO members (root Group) group vomss: //voms. cern. ch: 8443/voms/alice? /alice # LDAP lines for ALICE # LHCB # Map VO members (sgm) group vomss: //voms. cern. ch: 8443/voms/lhcb? /lhcb/sgm. lhcbsgm # Map VO members (sgm) group vomss: //voms. cern. ch: 8443/voms/lhcb? /lhcb/Role=lcgadmin. lhcbsgm # Map VO members (prd) group vomss: //voms. cern. ch: 8443/voms/lhcb? /lhcb/lcgprod. lhcbprd It’s also possible to ban someone adding to the mkgridmap. conf a line like: BUT deny *Cesini* www. ccr. infn. it It modifies the old style gridmapfile only, if the user has a valid VOMS proxy he is not blocked since VOMS mapping is performed first and on the LCG by default use the new gridmapfile Scuola Amministratori Grid, Martina Franca (Taranto), 05/11/2007 45 http: //grid. infn. it/
Mapping on the CE: the mkgridmap. conf file The edg-mkgridmap. conf: # ALICE # Map VO members (sgm) group vomss: //voms. cern. ch: 8443/voms/alice? /alice/Role=lcgadmin. alicesgm # Map VO members (prd) group vomss: //voms. cern. ch: 8443/voms/alice? /alice/Role=production. aliceprd # Map VO members (root Group) group vomss: //voms. cern. ch: 8443/voms/alice? /alice # LDAP lines for ALICE # LHCB # Map VO members (sgm) group vomss: //voms. cern. ch: 8443/voms/lhcb? /lhcb/sgm. lhcbsgm # Map VO members (sgm) group vomss: //voms. cern. ch: 8443/voms/lhcb? /lhcb/Role=lcgadmin. lhcbsgm # Map VO members (prd) group vomss: //voms. cern. ch: 8443/voms/lhcb? /lhcb/lcgprod. lhcbprd It’s also possible to ban someone adding to the mkgridmap. conf a line like: BUT deny *Cesini* www. ccr. infn. it It modifies the old style gridmapfile only, if the user has a valid VOMS proxy he is not blocked since VOMS mapping is performed first and on the LCG by default use the new gridmapfile Scuola Amministratori Grid, Martina Franca (Taranto), 05/11/2007 45 http: //grid. infn. it/
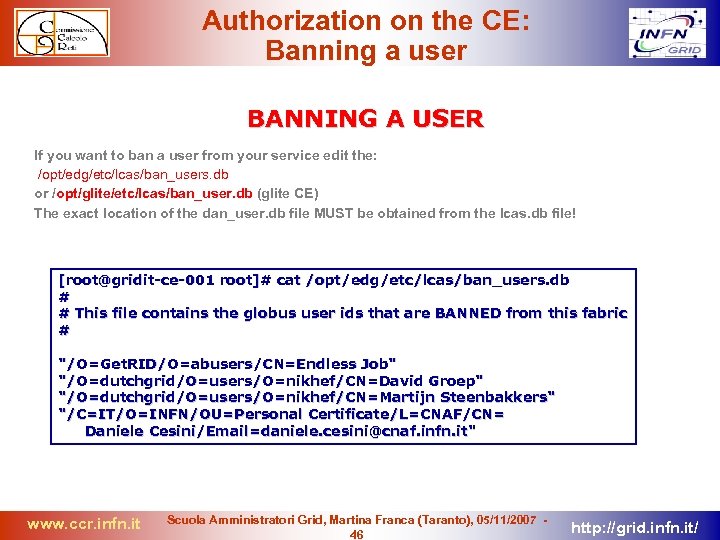 Authorization on the CE: Banning a user BANNING A USER If you want to ban a user from your service edit the: /opt/edg/etc/lcas/ban_users. db or /opt/glite/etc/lcas/ban_user. db (glite CE) The exact location of the dan_user. db file MUST be obtained from the lcas. db file! [root@gridit-ce-001 root]# cat /opt/edg/etc/lcas/ban_users. db # # This file contains the globus user ids that are BANNED from this fabric # "/O=Get. RID/O=abusers/CN=Endless Job" "/O=dutchgrid/O=users/O=nikhef/CN=David Groep" "/O=dutchgrid/O=users/O=nikhef/CN=Martijn Steenbakkers" "/C=IT/O=INFN/OU=Personal Certificate/L=CNAF/CN= Daniele Cesini/Email=daniele. cesini@cnaf. infn. it" www. ccr. infn. it Scuola Amministratori Grid, Martina Franca (Taranto), 05/11/2007 46 http: //grid. infn. it/
Authorization on the CE: Banning a user BANNING A USER If you want to ban a user from your service edit the: /opt/edg/etc/lcas/ban_users. db or /opt/glite/etc/lcas/ban_user. db (glite CE) The exact location of the dan_user. db file MUST be obtained from the lcas. db file! [root@gridit-ce-001 root]# cat /opt/edg/etc/lcas/ban_users. db # # This file contains the globus user ids that are BANNED from this fabric # "/O=Get. RID/O=abusers/CN=Endless Job" "/O=dutchgrid/O=users/O=nikhef/CN=David Groep" "/O=dutchgrid/O=users/O=nikhef/CN=Martijn Steenbakkers" "/C=IT/O=INFN/OU=Personal Certificate/L=CNAF/CN= Daniele Cesini/Email=daniele. cesini@cnaf. infn. it" www. ccr. infn. it Scuola Amministratori Grid, Martina Franca (Taranto), 05/11/2007 46 http: //grid. infn. it/
 Mapping on the CE: The Pool Accounts THE POOL ACCOUNT Group of local unix user (uid/gid) on which the remote grid credential are mapped. For each VO (or VO group) are defined a limited number of accounts of the kind: dteam 001 dteam 002 … dteam 050 dteamsgm 001 dteamsgm 002 …. Different Users are mapped into different pool accounts, if at the same time the number of users of the same VO (group) that are accessing the service is greater than the number of pool accounts the mapping fails! www. ccr. infn. it Scuola Amministratori Grid, Martina Franca (Taranto), 05/11/2007 47 http: //grid. infn. it/
Mapping on the CE: The Pool Accounts THE POOL ACCOUNT Group of local unix user (uid/gid) on which the remote grid credential are mapped. For each VO (or VO group) are defined a limited number of accounts of the kind: dteam 001 dteam 002 … dteam 050 dteamsgm 001 dteamsgm 002 …. Different Users are mapped into different pool accounts, if at the same time the number of users of the same VO (group) that are accessing the service is greater than the number of pool accounts the mapping fails! www. ccr. infn. it Scuola Amministratori Grid, Martina Franca (Taranto), 05/11/2007 47 http: //grid. infn. it/
 Mapping on the CE: The gridmapdir keeps track of the mapping performed on the CE: Hard links are created between two empty files: one named with a string that is a the user certificate subject and another one name as the pool account Use the inode number to identify the link It is cleaned periodically [root@gridit-ce-001 root]# ls -li /etc/grid-security/gridmapdir/| sort | less 3588653 -rw-r--r-- 2 root 0 Jun 5 09: 04 %2 fc%3 dit%2 fo%3 dinfn%2 fou%3 dpersonal%20 certificate%2 fl%3 dcnaf %2 fcn%3 ddaniele%20 cesini%2 femail%3 ddaniele%2 ecesini%40 cnaf%2 einfn%2 eit: infng rid 3588653 -rw-r--r-- 2 root 0 Jun 5 09: 04 infngrid 015 3588655 -rw-r--r-- 2 root 0 Mar 14 00: 55 %2 fc%3 dit%2 fo%3 dinfn%2 fou%3 dpersonal%20 certificate%2 fl%3 dcnaf %2 fcn%3 dgiuseppe%20 misurelli%2 femail%3 dgiuseppe%2 emisurelli%40 cnaf%2 einfn% 2 eit: infngrid 3588655 -rw-r--r-- 2 root 0 Mar 14 00: 55 infngrid 017 3588656 -rw-r--r-- 1 root 0 Sep 11 2006 infngrid 018 Free account www. ccr. infn. it Scuola Amministratori Grid, Martina Franca (Taranto), 05/11/2007 48 http: //grid. infn. it/
Mapping on the CE: The gridmapdir keeps track of the mapping performed on the CE: Hard links are created between two empty files: one named with a string that is a the user certificate subject and another one name as the pool account Use the inode number to identify the link It is cleaned periodically [root@gridit-ce-001 root]# ls -li /etc/grid-security/gridmapdir/| sort | less 3588653 -rw-r--r-- 2 root 0 Jun 5 09: 04 %2 fc%3 dit%2 fo%3 dinfn%2 fou%3 dpersonal%20 certificate%2 fl%3 dcnaf %2 fcn%3 ddaniele%20 cesini%2 femail%3 ddaniele%2 ecesini%40 cnaf%2 einfn%2 eit: infng rid 3588653 -rw-r--r-- 2 root 0 Jun 5 09: 04 infngrid 015 3588655 -rw-r--r-- 2 root 0 Mar 14 00: 55 %2 fc%3 dit%2 fo%3 dinfn%2 fou%3 dpersonal%20 certificate%2 fl%3 dcnaf %2 fcn%3 dgiuseppe%20 misurelli%2 femail%3 dgiuseppe%2 emisurelli%40 cnaf%2 einfn% 2 eit: infngrid 3588655 -rw-r--r-- 2 root 0 Mar 14 00: 55 infngrid 017 3588656 -rw-r--r-- 1 root 0 Sep 11 2006 infngrid 018 Free account www. ccr. infn. it Scuola Amministratori Grid, Martina Franca (Taranto), 05/11/2007 48 http: //grid. infn. it/
 The VOMSDIR To be authenticated the user with a VOMS proxy must have the proxy signed by a trusted VOMS server. To trust a VOMS server the service uses the /etc/gridsecurity/vomsdir where the certificates of all the trusted VOMS server must be copied. (the exact location is lcas. db or lcmaps. db files, if the voms plugin is used by the service) [root@cert-ce-05 root]# ls /etc/grid-security/vomsdir/ 4 -dec-2006 -kuiken. nikhef. nl. pem na 48 -voms. cern. ch cclcgvomsli 01. in 2 p 3. fr. 1881 voms. cern. ch. 2006 -11 -20 lcg-voms. cern. ch. 2007 -05 -07 voms-test. cern. ch. 2006 -11 -20 lcg-voms. cern. ch. 2580 If you have a proxy of an enabled VO but signed by a NOT TRUSTED VOMS server the (VOMS) authentication fails. www. ccr. infn. it Scuola Amministratori Grid, Martina Franca (Taranto), 05/11/2007 49 http: //grid. infn. it/
The VOMSDIR To be authenticated the user with a VOMS proxy must have the proxy signed by a trusted VOMS server. To trust a VOMS server the service uses the /etc/gridsecurity/vomsdir where the certificates of all the trusted VOMS server must be copied. (the exact location is lcas. db or lcmaps. db files, if the voms plugin is used by the service) [root@cert-ce-05 root]# ls /etc/grid-security/vomsdir/ 4 -dec-2006 -kuiken. nikhef. nl. pem na 48 -voms. cern. ch cclcgvomsli 01. in 2 p 3. fr. 1881 voms. cern. ch. 2006 -11 -20 lcg-voms. cern. ch. 2007 -05 -07 voms-test. cern. ch. 2006 -11 -20 lcg-voms. cern. ch. 2580 If you have a proxy of an enabled VO but signed by a NOT TRUSTED VOMS server the (VOMS) authentication fails. www. ccr. infn. it Scuola Amministratori Grid, Martina Franca (Taranto), 05/11/2007 49 http: //grid. infn. it/
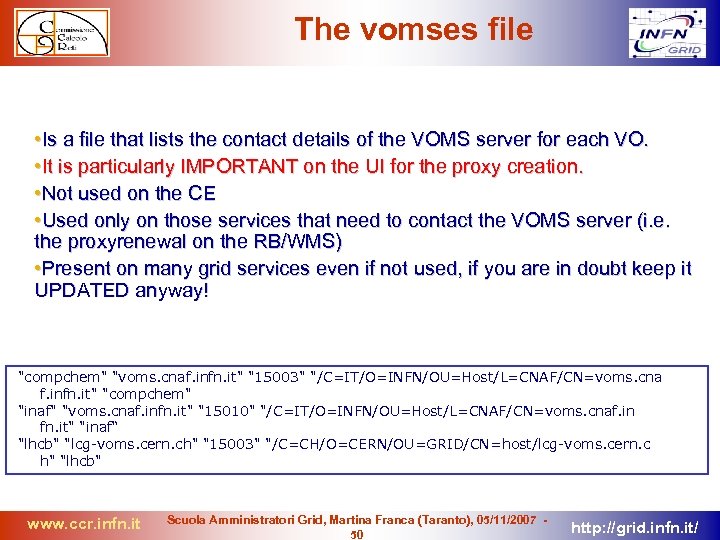 The vomses file • Is a file that lists the contact details of the VOMS server for each VO. • It is particularly IMPORTANT on the UI for the proxy creation. • Not used on the CE • Used only on those services that need to contact the VOMS server (i. e. the proxyrenewal on the RB/WMS) • Present on many grid services even if not used, if you are in doubt keep it UPDATED anyway! "compchem" "voms. cnaf. infn. it" "15003" "/C=IT/O=INFN/OU=Host/L=CNAF/CN=voms. cna f. infn. it" "compchem" "inaf" "voms. cnaf. infn. it" "15010" "/C=IT/O=INFN/OU=Host/L=CNAF/CN=voms. cnaf. in fn. it" "inaf“ "lhcb" "lcg-voms. cern. ch" "15003" "/C=CH/O=CERN/OU=GRID/CN=host/lcg-voms. cern. c h" "lhcb" www. ccr. infn. it Scuola Amministratori Grid, Martina Franca (Taranto), 05/11/2007 50 http: //grid. infn. it/
The vomses file • Is a file that lists the contact details of the VOMS server for each VO. • It is particularly IMPORTANT on the UI for the proxy creation. • Not used on the CE • Used only on those services that need to contact the VOMS server (i. e. the proxyrenewal on the RB/WMS) • Present on many grid services even if not used, if you are in doubt keep it UPDATED anyway! "compchem" "voms. cnaf. infn. it" "15003" "/C=IT/O=INFN/OU=Host/L=CNAF/CN=voms. cna f. infn. it" "compchem" "inaf" "voms. cnaf. infn. it" "15010" "/C=IT/O=INFN/OU=Host/L=CNAF/CN=voms. cnaf. in fn. it" "inaf“ "lhcb" "lcg-voms. cern. ch" "15003" "/C=CH/O=CERN/OU=GRID/CN=host/lcg-voms. cern. c h" "lhcb" www. ccr. infn. it Scuola Amministratori Grid, Martina Franca (Taranto), 05/11/2007 50 http: //grid. infn. it/
 Authorization: NTP Be sure that NTP is correctly configured and there is no clock skew on every server that needs GSI authentication. To configure ntp edit /etc/ntp. conf [root@gridit-ce-001 root]# cat /etc/ntp. conf restrict ripe. cnaf. infn. it mask 255 nomodify notrap noquery server ripe. cnaf. infn. it restrict ntp-3. infn. it mask 255 nomodify notrap noquery server ntp-3. infn. it restrict ntp-1. infn. it mask 255 nomodify notrap noquery server ntp-1. infn. it www. ccr. infn. it Scuola Amministratori Grid, Martina Franca (Taranto), 05/11/2007 51 http: //grid. infn. it/
Authorization: NTP Be sure that NTP is correctly configured and there is no clock skew on every server that needs GSI authentication. To configure ntp edit /etc/ntp. conf [root@gridit-ce-001 root]# cat /etc/ntp. conf restrict ripe. cnaf. infn. it mask 255 nomodify notrap noquery server ripe. cnaf. infn. it restrict ntp-3. infn. it mask 255 nomodify notrap noquery server ntp-3. infn. it restrict ntp-1. infn. it mask 255 nomodify notrap noquery server ntp-1. infn. it www. ccr. infn. it Scuola Amministratori Grid, Martina Franca (Taranto), 05/11/2007 51 http: //grid. infn. it/
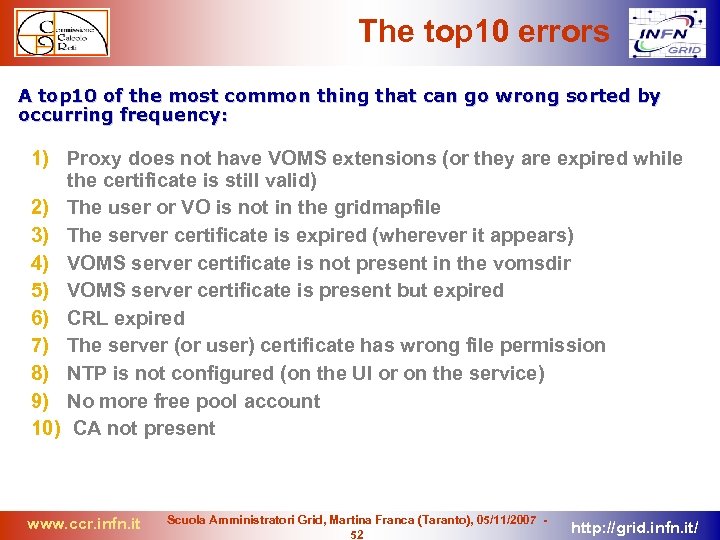 The top 10 errors A top 10 of the most common thing that can go wrong sorted by occurring frequency: 1) Proxy does not have VOMS extensions (or they are expired while the certificate is still valid) 2) The user or VO is not in the gridmapfile 3) The server certificate is expired (wherever it appears) 4) VOMS server certificate is not present in the vomsdir 5) VOMS server certificate is present but expired 6) CRL expired 7) The server (or user) certificate has wrong file permission 8) NTP is not configured (on the UI or on the service) 9) No more free pool account 10) CA not present www. ccr. infn. it Scuola Amministratori Grid, Martina Franca (Taranto), 05/11/2007 52 http: //grid. infn. it/
The top 10 errors A top 10 of the most common thing that can go wrong sorted by occurring frequency: 1) Proxy does not have VOMS extensions (or they are expired while the certificate is still valid) 2) The user or VO is not in the gridmapfile 3) The server certificate is expired (wherever it appears) 4) VOMS server certificate is not present in the vomsdir 5) VOMS server certificate is present but expired 6) CRL expired 7) The server (or user) certificate has wrong file permission 8) NTP is not configured (on the UI or on the service) 9) No more free pool account 10) CA not present www. ccr. infn. it Scuola Amministratori Grid, Martina Franca (Taranto), 05/11/2007 52 http: //grid. infn. it/
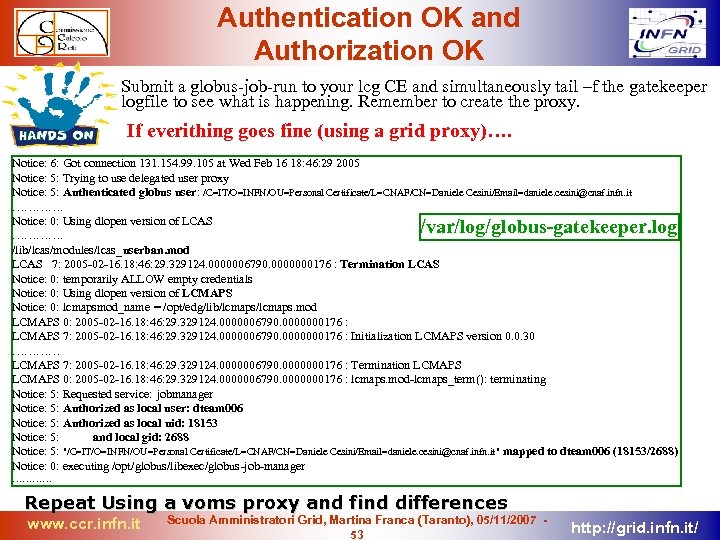 Authentication OK and Authorization OK Submit a globus-job-run to your lcg CE and simultaneously tail –f the gatekeeper logfile to see what is happening. Remember to create the proxy. If everithing goes fine (using a grid proxy)…. Notice: 6: Got connection 131. 154. 99. 105 at Wed Feb 16 18: 46: 29 2005 Notice: 5: Trying to use delegated user proxy Notice: 5: Authenticated globus user: /C=IT/O=INFN/OU=Personal Certificate/L=CNAF/CN=Daniele Cesini/Email=daniele. cesini@cnaf. infn. it …………. Notice: 0: Using dlopen version of LCAS …………. /lib/lcas/modules/lcas_userban. mod LCAS 7: 2005 -02 -16. 18: 46: 29. 329124. 0000006790. 0000000176 : Termination LCAS Notice: 0: temporarily ALLOW empty credentials Notice: 0: Using dlopen version of LCMAPS Notice: 0: lcmapsmod_name = /opt/edg/lib/lcmaps. mod LCMAPS 0: 2005 -02 -16. 18: 46: 29. 329124. 0000006790. 0000000176 : LCMAPS 7: 2005 -02 -16. 18: 46: 29. 329124. 0000006790. 0000000176 : Initialization LCMAPS version 0. 0. 30 ………… LCMAPS 7: 2005 -02 -16. 18: 46: 29. 329124. 0000006790. 0000000176 : Termination LCMAPS 0: 2005 -02 -16. 18: 46: 29. 329124. 0000006790. 0000000176 : lcmaps. mod-lcmaps_term(): terminating Notice: 5: Requested service: jobmanager Notice: 5: Authorized as local user: dteam 006 Notice: 5: Authorized as local uid: 18153 Notice: 5: and local gid: 2688 Notice: 5: "/C=IT/O=INFN/OU=Personal Certificate/L=CNAF/CN=Daniele Cesini/Email=daniele. cesini@cnaf. infn. it" mapped to dteam 006 (18153/2688) Notice: 0: executing /opt/globus/libexec/globus-job-manager /var/log/globus-gatekeeper. log ………… Repeat Using a voms proxy and find differences www. ccr. infn. it Scuola Amministratori Grid, Martina Franca (Taranto), 05/11/2007 53 http: //grid. infn. it/
Authentication OK and Authorization OK Submit a globus-job-run to your lcg CE and simultaneously tail –f the gatekeeper logfile to see what is happening. Remember to create the proxy. If everithing goes fine (using a grid proxy)…. Notice: 6: Got connection 131. 154. 99. 105 at Wed Feb 16 18: 46: 29 2005 Notice: 5: Trying to use delegated user proxy Notice: 5: Authenticated globus user: /C=IT/O=INFN/OU=Personal Certificate/L=CNAF/CN=Daniele Cesini/Email=daniele. cesini@cnaf. infn. it …………. Notice: 0: Using dlopen version of LCAS …………. /lib/lcas/modules/lcas_userban. mod LCAS 7: 2005 -02 -16. 18: 46: 29. 329124. 0000006790. 0000000176 : Termination LCAS Notice: 0: temporarily ALLOW empty credentials Notice: 0: Using dlopen version of LCMAPS Notice: 0: lcmapsmod_name = /opt/edg/lib/lcmaps. mod LCMAPS 0: 2005 -02 -16. 18: 46: 29. 329124. 0000006790. 0000000176 : LCMAPS 7: 2005 -02 -16. 18: 46: 29. 329124. 0000006790. 0000000176 : Initialization LCMAPS version 0. 0. 30 ………… LCMAPS 7: 2005 -02 -16. 18: 46: 29. 329124. 0000006790. 0000000176 : Termination LCMAPS 0: 2005 -02 -16. 18: 46: 29. 329124. 0000006790. 0000000176 : lcmaps. mod-lcmaps_term(): terminating Notice: 5: Requested service: jobmanager Notice: 5: Authorized as local user: dteam 006 Notice: 5: Authorized as local uid: 18153 Notice: 5: and local gid: 2688 Notice: 5: "/C=IT/O=INFN/OU=Personal Certificate/L=CNAF/CN=Daniele Cesini/Email=daniele. cesini@cnaf. infn. it" mapped to dteam 006 (18153/2688) Notice: 0: executing /opt/globus/libexec/globus-job-manager /var/log/globus-gatekeeper. log ………… Repeat Using a voms proxy and find differences www. ccr. infn. it Scuola Amministratori Grid, Martina Franca (Taranto), 05/11/2007 53 http: //grid. infn. it/
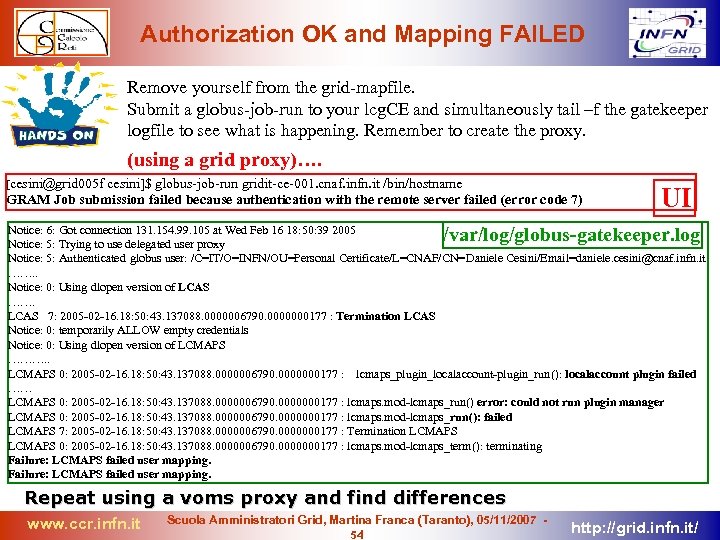 Authorization OK and Mapping FAILED Remove yourself from the grid-mapfile. Submit a globus-job-run to your lcg. CE and simultaneously tail –f the gatekeeper logfile to see what is happening. Remember to create the proxy. (using a grid proxy)…. [cesini@grid 005 f cesini]$ globus-job-run gridit-ce-001. cnaf. infn. it /bin/hostname GRAM Job submission failed because authentication with the remote server failed (error code 7) UI Notice: 6: Got connection 131. 154. 99. 105 at Wed Feb 16 18: 50: 39 2005 Notice: 5: Trying to use delegated user proxy Notice: 5: Authenticated globus user: /C=IT/O=INFN/OU=Personal Certificate/L=CNAF/CN=Daniele Cesini/Email=daniele. cesini@cnaf. infn. it ……. . Notice: 0: Using dlopen version of LCAS ……. LCAS 7: 2005 -02 -16. 18: 50: 43. 137088. 0000006790. 0000000177 : Termination LCAS Notice: 0: temporarily ALLOW empty credentials Notice: 0: Using dlopen version of LCMAPS ………. . LCMAPS 0: 2005 -02 -16. 18: 50: 43. 137088. 0000006790. 0000000177 : lcmaps_plugin_localaccount-plugin_run(): localaccount plugin failed …… LCMAPS 0: 2005 -02 -16. 18: 50: 43. 137088. 0000006790. 0000000177 : lcmaps. mod-lcmaps_run() error: could not run plugin manager LCMAPS 0: 2005 -02 -16. 18: 50: 43. 137088. 0000006790. 0000000177 : lcmaps. mod-lcmaps_run(): failed LCMAPS 7: 2005 -02 -16. 18: 50: 43. 137088. 0000006790. 0000000177 : Termination LCMAPS 0: 2005 -02 -16. 18: 50: 43. 137088. 0000006790. 0000000177 : lcmaps. mod-lcmaps_term(): terminating Failure: LCMAPS failed user mapping. /var/log/globus-gatekeeper. log Repeat using a voms proxy and find differences www. ccr. infn. it Scuola Amministratori Grid, Martina Franca (Taranto), 05/11/2007 54 http: //grid. infn. it/
Authorization OK and Mapping FAILED Remove yourself from the grid-mapfile. Submit a globus-job-run to your lcg. CE and simultaneously tail –f the gatekeeper logfile to see what is happening. Remember to create the proxy. (using a grid proxy)…. [cesini@grid 005 f cesini]$ globus-job-run gridit-ce-001. cnaf. infn. it /bin/hostname GRAM Job submission failed because authentication with the remote server failed (error code 7) UI Notice: 6: Got connection 131. 154. 99. 105 at Wed Feb 16 18: 50: 39 2005 Notice: 5: Trying to use delegated user proxy Notice: 5: Authenticated globus user: /C=IT/O=INFN/OU=Personal Certificate/L=CNAF/CN=Daniele Cesini/Email=daniele. cesini@cnaf. infn. it ……. . Notice: 0: Using dlopen version of LCAS ……. LCAS 7: 2005 -02 -16. 18: 50: 43. 137088. 0000006790. 0000000177 : Termination LCAS Notice: 0: temporarily ALLOW empty credentials Notice: 0: Using dlopen version of LCMAPS ………. . LCMAPS 0: 2005 -02 -16. 18: 50: 43. 137088. 0000006790. 0000000177 : lcmaps_plugin_localaccount-plugin_run(): localaccount plugin failed …… LCMAPS 0: 2005 -02 -16. 18: 50: 43. 137088. 0000006790. 0000000177 : lcmaps. mod-lcmaps_run() error: could not run plugin manager LCMAPS 0: 2005 -02 -16. 18: 50: 43. 137088. 0000006790. 0000000177 : lcmaps. mod-lcmaps_run(): failed LCMAPS 7: 2005 -02 -16. 18: 50: 43. 137088. 0000006790. 0000000177 : Termination LCMAPS 0: 2005 -02 -16. 18: 50: 43. 137088. 0000006790. 0000000177 : lcmaps. mod-lcmaps_term(): terminating Failure: LCMAPS failed user mapping. /var/log/globus-gatekeeper. log Repeat using a voms proxy and find differences www. ccr. infn. it Scuola Amministratori Grid, Martina Franca (Taranto), 05/11/2007 54 http: //grid. infn. it/
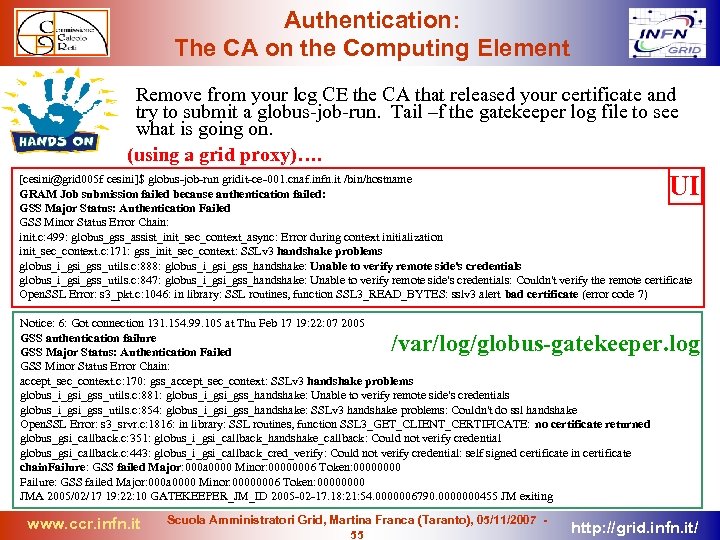 Authentication: The CA on the Computing Element Remove from your lcg CE the CA that released your certificate and try to submit a globus-job-run. Tail –f the gatekeeper log file to see what is going on. (using a grid proxy)…. UI [cesini@grid 005 f cesini]$ globus-job-run gridit-ce-001. cnaf. infn. it /bin/hostname GRAM Job submission failed because authentication failed: GSS Major Status: Authentication Failed GSS Minor Status Error Chain: init. c: 499: globus_gss_assist_init_sec_context_async: Error during context initialization init_sec_context. c: 171: gss_init_sec_context: SSLv 3 handshake problems globus_i_gss_utils. c: 888: globus_i_gss_handshake: Unable to verify remote side's credentials globus_i_gss_utils. c: 847: globus_i_gss_handshake: Unable to verify remote side's credentials: Couldn't verify the remote certificate Open. SSL Error: s 3_pkt. c: 1046: in library: SSL routines, function SSL 3_READ_BYTES: sslv 3 alert bad certificate (error code 7) Notice: 6: Got connection 131. 154. 99. 105 at Thu Feb 17 19: 22: 07 2005 GSS authentication failure GSS Major Status: Authentication Failed GSS Minor Status Error Chain: accept_sec_context. c: 170: gss_accept_sec_context: SSLv 3 handshake problems globus_i_gss_utils. c: 881: globus_i_gss_handshake: Unable to verify remote side's credentials globus_i_gss_utils. c: 854: globus_i_gss_handshake: SSLv 3 handshake problems: Couldn't do ssl handshake Open. SSL Error: s 3_srvr. c: 1816: in library: SSL routines, function SSL 3_GET_CLIENT_CERTIFICATE: no certificate returned globus_gsi_callback. c: 351: globus_i_gsi_callback_handshake_callback: Could not verify credential globus_gsi_callback. c: 443: globus_i_gsi_callback_cred_verify: Could not verify credential: self signed certificate in certificate chain. Failure: GSS failed Major: 000 a 0000 Minor: 00000006 Token: 00000000 JMA 2005/02/17 19: 22: 10 GATEKEEPER_JM_ID 2005 -02 -17. 18: 21: 54. 0000006790. 0000000455 JM exiting /var/log/globus-gatekeeper. log www. ccr. infn. it Scuola Amministratori Grid, Martina Franca (Taranto), 05/11/2007 55 http: //grid. infn. it/
Authentication: The CA on the Computing Element Remove from your lcg CE the CA that released your certificate and try to submit a globus-job-run. Tail –f the gatekeeper log file to see what is going on. (using a grid proxy)…. UI [cesini@grid 005 f cesini]$ globus-job-run gridit-ce-001. cnaf. infn. it /bin/hostname GRAM Job submission failed because authentication failed: GSS Major Status: Authentication Failed GSS Minor Status Error Chain: init. c: 499: globus_gss_assist_init_sec_context_async: Error during context initialization init_sec_context. c: 171: gss_init_sec_context: SSLv 3 handshake problems globus_i_gss_utils. c: 888: globus_i_gss_handshake: Unable to verify remote side's credentials globus_i_gss_utils. c: 847: globus_i_gss_handshake: Unable to verify remote side's credentials: Couldn't verify the remote certificate Open. SSL Error: s 3_pkt. c: 1046: in library: SSL routines, function SSL 3_READ_BYTES: sslv 3 alert bad certificate (error code 7) Notice: 6: Got connection 131. 154. 99. 105 at Thu Feb 17 19: 22: 07 2005 GSS authentication failure GSS Major Status: Authentication Failed GSS Minor Status Error Chain: accept_sec_context. c: 170: gss_accept_sec_context: SSLv 3 handshake problems globus_i_gss_utils. c: 881: globus_i_gss_handshake: Unable to verify remote side's credentials globus_i_gss_utils. c: 854: globus_i_gss_handshake: SSLv 3 handshake problems: Couldn't do ssl handshake Open. SSL Error: s 3_srvr. c: 1816: in library: SSL routines, function SSL 3_GET_CLIENT_CERTIFICATE: no certificate returned globus_gsi_callback. c: 351: globus_i_gsi_callback_handshake_callback: Could not verify credential globus_gsi_callback. c: 443: globus_i_gsi_callback_cred_verify: Could not verify credential: self signed certificate in certificate chain. Failure: GSS failed Major: 000 a 0000 Minor: 00000006 Token: 00000000 JMA 2005/02/17 19: 22: 10 GATEKEEPER_JM_ID 2005 -02 -17. 18: 21: 54. 0000006790. 0000000455 JM exiting /var/log/globus-gatekeeper. log www. ccr. infn. it Scuola Amministratori Grid, Martina Franca (Taranto), 05/11/2007 55 http: //grid. infn. it/
 Host Certificates Request • Certificate is associated with the full qualified hostname (FQDN), not with the IP address • So if you rename your machine you need a new one and you can change the IP address of your machine without requesting a new certificate • Anyway the IP of your host must be in the dns before requesting the certificate www. ccr. infn. it Scuola Amministratori Grid, Martina Franca (Taranto), 05/11/2007 56 http: //grid. infn. it/
Host Certificates Request • Certificate is associated with the full qualified hostname (FQDN), not with the IP address • So if you rename your machine you need a new one and you can change the IP address of your machine without requesting a new certificate • Anyway the IP of your host must be in the dns before requesting the certificate www. ccr. infn. it Scuola Amministratori Grid, Martina Franca (Taranto), 05/11/2007 56 http: //grid. infn. it/
 Certificates Request • Go to http: //security. fi. infn. it/CA/ and download host. cnf from: http: //security. fi. infn. it/CA/docs/ • Generate a certificate request with the following command: openssl req -new -nodes -out req. pem -keyout hostkey. pem -config host. cnf • openssl will generate two files: hostkey. pem, the private key and req. pem, the public one. Keep the private key in a safe place! • Send the public key req. pem via mail to your local Registration Authority, signing the mail with your personal certificate otherwise your request will not be accepted • The server certificate (i. e. the public key signed by the CA) will be sent back to you in a few days www. ccr. infn. it Scuola Amministratori Grid, Martina Franca (Taranto), 05/11/2007 57 http: //grid. infn. it/
Certificates Request • Go to http: //security. fi. infn. it/CA/ and download host. cnf from: http: //security. fi. infn. it/CA/docs/ • Generate a certificate request with the following command: openssl req -new -nodes -out req. pem -keyout hostkey. pem -config host. cnf • openssl will generate two files: hostkey. pem, the private key and req. pem, the public one. Keep the private key in a safe place! • Send the public key req. pem via mail to your local Registration Authority, signing the mail with your personal certificate otherwise your request will not be accepted • The server certificate (i. e. the public key signed by the CA) will be sent back to you in a few days www. ccr. infn. it Scuola Amministratori Grid, Martina Franca (Taranto), 05/11/2007 57 http: //grid. infn. it/
![Certificates Request [paolini@grid 005 f paolini]$ openssl req -new -nodes -out req. pem -keyout Certificates Request [paolini@grid 005 f paolini]$ openssl req -new -nodes -out req. pem -keyout](https://present5.com/presentation/c41ad577ec545bcc2bb14b63829d2c22/image-58.jpg) Certificates Request [paolini@grid 005 f paolini]$ openssl req -new -nodes -out req. pem -keyout hostkey. pem -config host. cnf Using configuration from host. cnf Generating a 1024 bit RSA private key. . . . ++++++ writing new private key to 'key. pem' ----You are about to be asked to enter information that will be incorporated into your certificate request. What you are about to enter is what is called a Distinguished Name or a DN. There are quite a few fields but you can leave some blank For some fields there will be a default value, If you enter '. ', the field will be left blank. ----Nazione []: IT Organizzazione []: INFN Tipo di certificato []: Host Nome Struttura (ad es. Pisa) []: CNAF FQDN del Server [ ]: prova. cnaf. infn. it Email del Server Manager [ ]: sitemanager@cnaf. infn. it [paolini@grid 005 f paolini]$ www. ccr. infn. it Scuola Amministratori Grid, Martina Franca (Taranto), 05/11/2007 58 http: //grid. infn. it/
Certificates Request [paolini@grid 005 f paolini]$ openssl req -new -nodes -out req. pem -keyout hostkey. pem -config host. cnf Using configuration from host. cnf Generating a 1024 bit RSA private key. . . . ++++++ writing new private key to 'key. pem' ----You are about to be asked to enter information that will be incorporated into your certificate request. What you are about to enter is what is called a Distinguished Name or a DN. There are quite a few fields but you can leave some blank For some fields there will be a default value, If you enter '. ', the field will be left blank. ----Nazione []: IT Organizzazione []: INFN Tipo di certificato []: Host Nome Struttura (ad es. Pisa) []: CNAF FQDN del Server [ ]: prova. cnaf. infn. it Email del Server Manager [ ]: sitemanager@cnaf. infn. it [paolini@grid 005 f paolini]$ www. ccr. infn. it Scuola Amministratori Grid, Martina Franca (Taranto), 05/11/2007 58 http: //grid. infn. it/
 Certificates Request • Copy the host certificate and the key in: /etc/grid-security/hostcert. pem /etc/grid-security/hostkey. pem • Set the required file permissions: chmod 0644 /etc/grid-security/hostcert. pem chmod 0400 /etc/grid-security/hostkey. pem www. ccr. infn. it Scuola Amministratori Grid, Martina Franca (Taranto), 05/11/2007 59 http: //grid. infn. it/
Certificates Request • Copy the host certificate and the key in: /etc/grid-security/hostcert. pem /etc/grid-security/hostkey. pem • Set the required file permissions: chmod 0644 /etc/grid-security/hostcert. pem chmod 0400 /etc/grid-security/hostkey. pem www. ccr. infn. it Scuola Amministratori Grid, Martina Franca (Taranto), 05/11/2007 59 http: //grid. infn. it/
 References Cryptography “The Handbook of Applied Cryptography” by Alfred J. Menezes, Paul C. van Oorschot and Scott A. Vanstone http: //www. cacr. math. uwaterloo. ca/hac/ RSA Inc. site : http: //www. rsasecurity. com/ Grid Security LCG Security: http: //proj-lcg-security. web. cern. ch/proj-lcg-security/ Globus Security: http: //www. globus. org/security/ Grid-it portal: http: //grid-it. cnaf. infn. it www. ccr. infn. it Scuola Amministratori Grid, Martina Franca (Taranto), 05/11/2007 60 http: //grid. infn. it/
References Cryptography “The Handbook of Applied Cryptography” by Alfred J. Menezes, Paul C. van Oorschot and Scott A. Vanstone http: //www. cacr. math. uwaterloo. ca/hac/ RSA Inc. site : http: //www. rsasecurity. com/ Grid Security LCG Security: http: //proj-lcg-security. web. cern. ch/proj-lcg-security/ Globus Security: http: //www. globus. org/security/ Grid-it portal: http: //grid-it. cnaf. infn. it www. ccr. infn. it Scuola Amministratori Grid, Martina Franca (Taranto), 05/11/2007 60 http: //grid. infn. it/


