2ed57a5bbe6fa7412a39aaf63bd0c4d2.ppt
- Количество слайдов: 54
Authentication Prof. Bill Buchanan w. buchanan@napier. ac. uk C. 63 X 2759 w_j_buchanan@hotmail. com http: //www. dcs. napier. ac. uk/~bill http: //buchananweb. co. uk Author: Bill Buchanan +Contact: Room: Telephone: MSN Messenger: WWW:
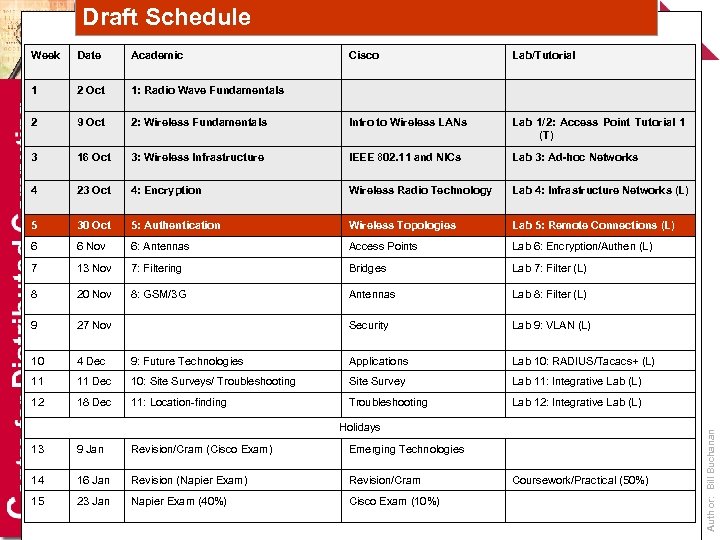
Draft Schedule Date Academic Cisco Lab/Tutorial 1 2 Oct 1: Radio Wave Fundamentals 2 9 Oct 2: Wireless Fundamentals Intro to Wireless LANs Lab 1/2: Access Point Tutorial 1 (T) 3 16 Oct 3: Wireless Infrastructure IEEE 802. 11 and NICs Lab 3: Ad-hoc Networks 4 23 Oct 4: Encryption Wireless Radio Technology Lab 4: Infrastructure Networks (L) 5 30 Oct 5: Authentication Wireless Topologies Lab 5: Remote Connections (L) 6 6 Nov 6: Antennas Access Points Lab 6: Encryption/Authen (L) 7 13 Nov 7: Filtering Bridges Lab 7: Filter (L) 8 20 Nov 8: GSM/3 G Antennas Lab 8: Filter (L) 9 27 Nov Security Lab 9: VLAN (L) 10 4 Dec 9: Future Technologies Applications Lab 10: RADIUS/Tacacs+ (L) 11 11 Dec 10: Site Surveys/ Troubleshooting Site Survey Lab 11: Integrative Lab (L) 12 18 Dec 11: Location-finding Troubleshooting Lab 12: Integrative Lab (L) Holidays 13 9 Jan Revision/Cram (Cisco Exam) Emerging Technologies 14 16 Jan Revision (Napier Exam) Revision/Cram 15 23 Jan Napier Exam (40%) Cisco Exam (10%) Coursework/Practical (50%) Author: Bill Buchanan Week
Wireless connections … which technology? Areas covered: Author: Bill Buchanan Authentication methods Ways? LEAP, PEAP, and so on Methods and weaknesses. Configurating authentication on an Aironet A simple example with local Radius

Author: Bill Buchanan Ways to Authenticate
Authentication methods Users Devices Author: Bill Buchanan Systems
Authentication methods Users Devices Systems Author: Bill Buchanan Network/physical addresses. These are simple method of verifying a device. The network address, such as the IP address can be easily spoofed, but the physical address is less easy and is a more secure implementation. Unfortunately the physical address can also be spoofed, either through software modifications of the wireless data frame, or by reprogramming the network interface card. Methods include DHCP. Username and password. The use is usernames and passwords are well known but are open to security breaches, especially from dictionary attacks on passwords, and from social engineering attacks. Methods include PEAP, EAP-FAST and EAP-SRP.
Authentication methods Pre-shared keys. This uses a pre-defined secret key. Methods include EAP-Archie. Users Devices Systems Author: Bill Buchanan Biometrics. This is a better method than a smart card where a physical feature of the user is scanned. The scanned parameter requires to be unchanging, such as fingerprints or retina images.
Authentication methods Authentication certificate. This certificate verifies a user or a device by providing a digital certificate which can be verified by a reputable source. Methods include EAP-TLS. Users Devices Systems Author: Bill Buchanan Tokens/Smart cards. With this method a user can only gain access to the system after they have inserted their personal smart card into the computer and then entered their PIN code. Methods include RSA Secur. ID Token Card and Smartcard EAP.

Author: Bill Buchanan IEEE 802. 11 Frame Format
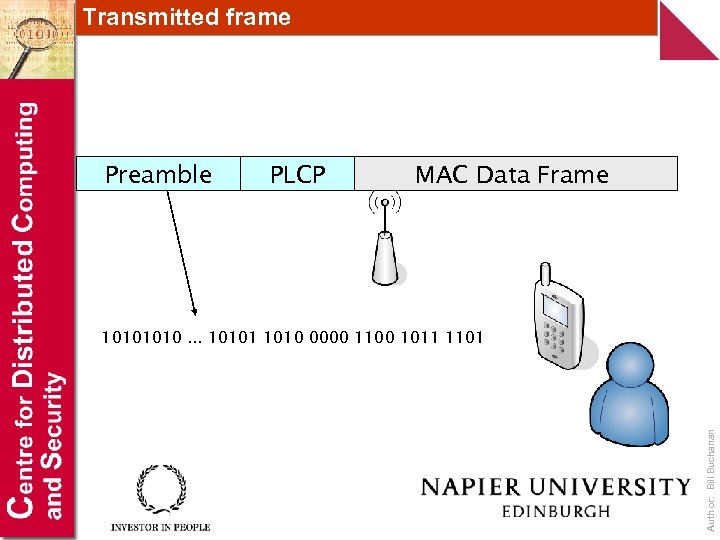
Transmitted frame Preamble PLCP MAC Data Frame Author: Bill Buchanan 1010. . . 10101 1010 0000 1100 1011 1101
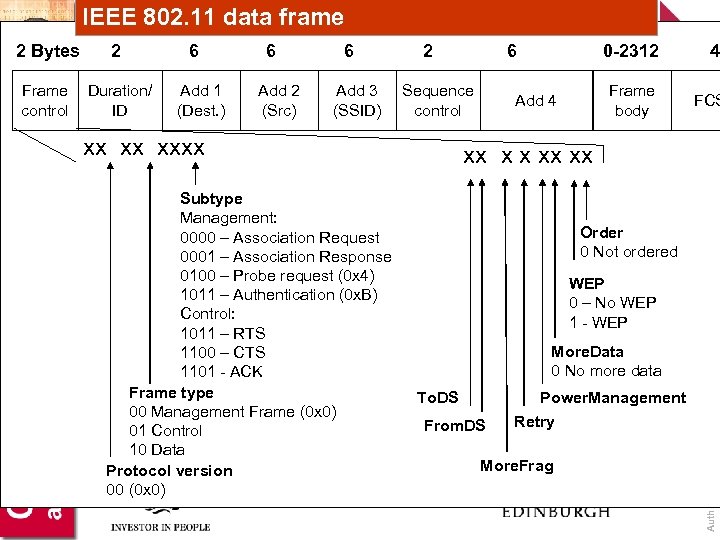
IEEE 802. 11 data frame 2 Frame control Duration/ ID 6 Add 1 (Dest. ) 6 Add 2 (Src) 6 Add 3 (SSID) 2 Sequence control xx xx xxxx Subtype Management: 0000 – Association Request 0001 – Association Response 0100 – Probe request (0 x 4) 1011 – Authentication (0 x. B) Control: 1011 – RTS 1100 – CTS 1101 - ACK Frame type 00 Management Frame (0 x 0) 01 Control 10 Data Protocol version 00 (0 x 0) 6 0 -2312 Frame body Add 4 4 FCS xx x x xx xx Order 0 Not ordered WEP 0 – No WEP 1 - WEP More. Data 0 No more data To. DS Power. Management From. DS Retry More. Frag Author: Bill Buchanan 2 Bytes
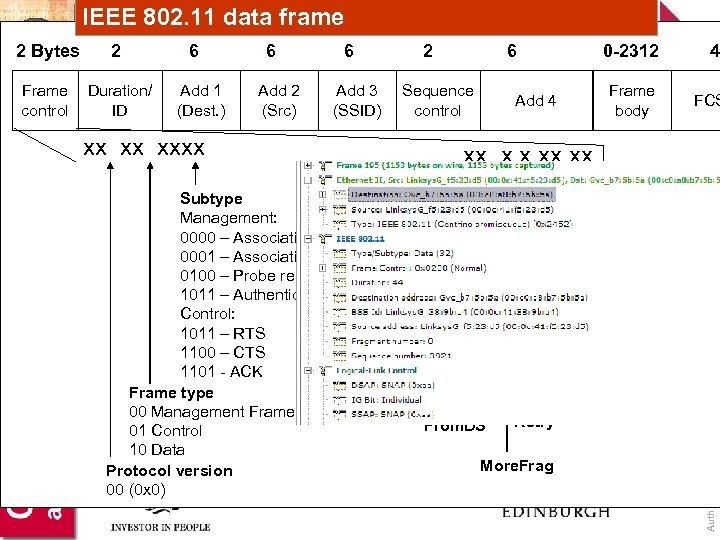
IEEE 802. 11 data frame 2 Frame control Duration/ ID 6 Add 1 (Dest. ) 6 Add 2 (Src) 6 Add 3 (SSID) 2 Sequence control xx xx xxxx Subtype Management: 0000 – Association Request 0001 – Association Response 0100 – Probe request (0 x 4) 1011 – Authentication (0 x. B) Control: 1011 – RTS 1100 – CTS 1101 - ACK Frame type 00 Management Frame (0 x 0) 01 Control 10 Data Protocol version 00 (0 x 0) 6 0 -2312 Frame body Add 4 4 FCS xx x x xx xx Order 0 Not ordered WEP 0 – No WEP 1 - WEP More. Data 0 No more data To. DS Power. Management From. DS Retry More. Frag Author: Bill Buchanan 2 Bytes
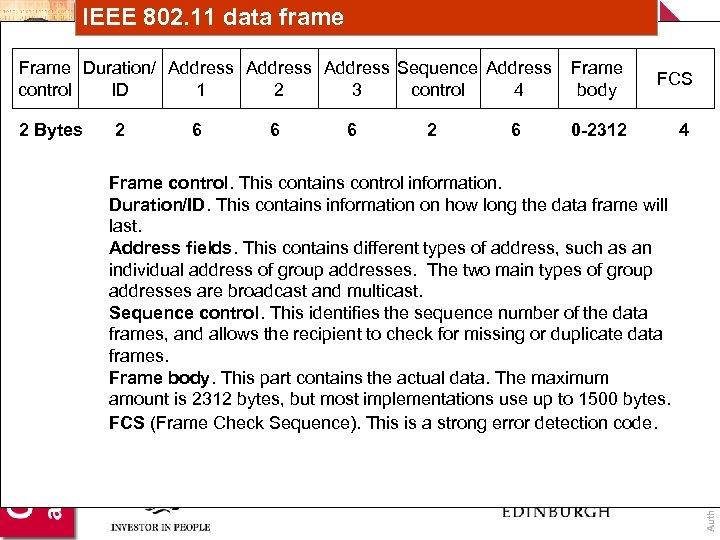
IEEE 802. 11 data frame Frame body FCS 2 Bytes 0 -2312 4 2 6 6 6 2 6 Frame control. This contains control information. Duration/ID. This contains information on how long the data frame will last. Address fields. This contains different types of address, such as an individual address of group addresses. The two main types of group addresses are broadcast and multicast. Sequence control. This identifies the sequence number of the data frames, and allows the recipient to check for missing or duplicate data frames. Frame body. This part contains the actual data. The maximum amount is 2312 bytes, but most implementations use up to 1500 bytes. FCS (Frame Check Sequence). This is a strong error detection code. Author: Bill Buchanan Frame Duration/ Address Sequence Address control ID 1 2 3 control 4
Frame body FCS 2 Bytes 0 -2312 4 2 6 6 6 2 6 Author: Bill Buchanan Frame Duration/ Address Sequence Address control ID 1 2 3 control 4

Author: Bill Buchanan Wireless Authentication
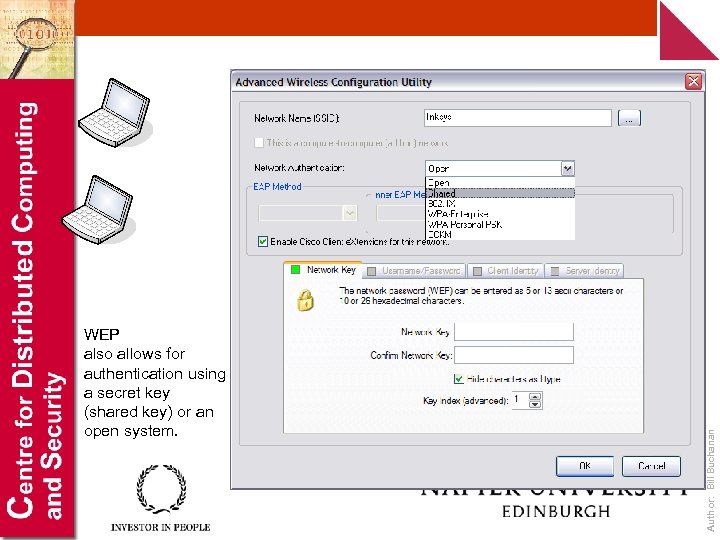
Author: Bill Buchanan WEP also allows for authentication using a secret key (shared key) or an open system.
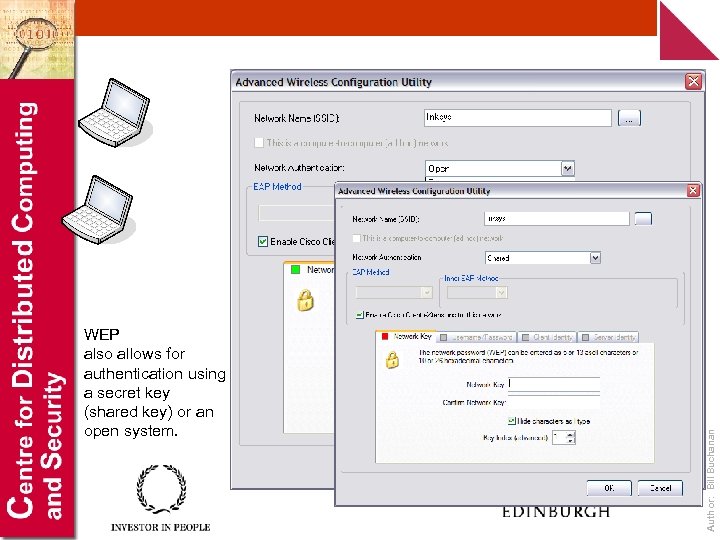
Author: Bill Buchanan WEP also allows for authentication using a secret key (shared key) or an open system.
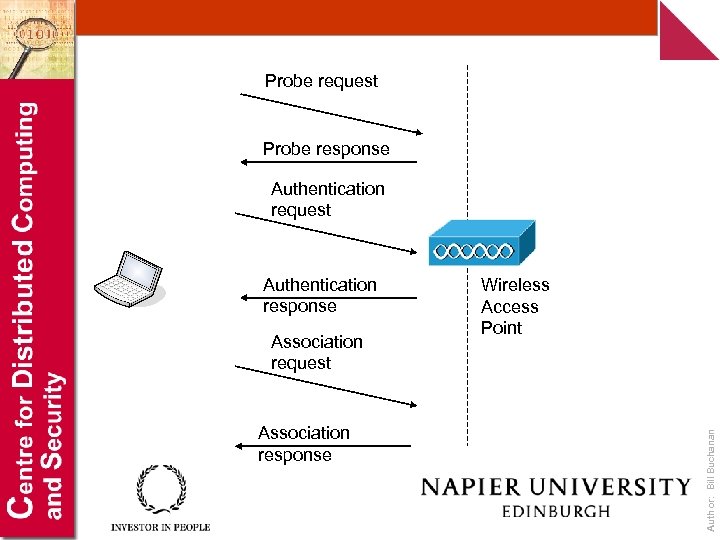
Probe request Probe response Authentication request Association response Wireless Access Point Author: Bill Buchanan Authentication response
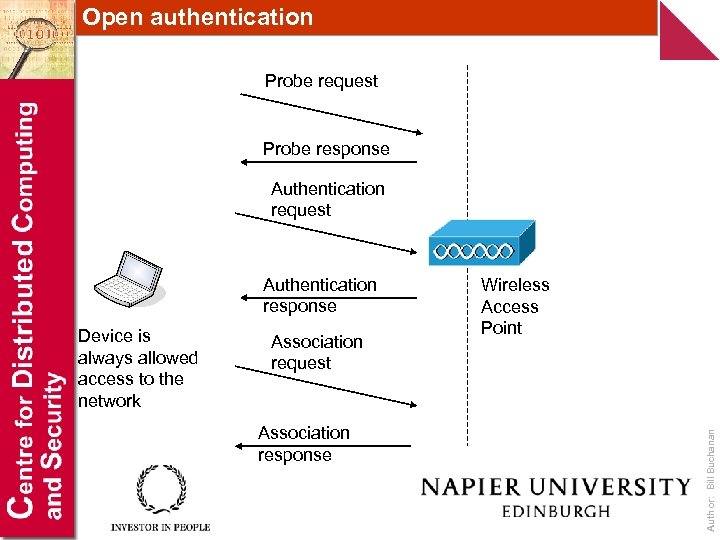
Open authentication Probe request Probe response Authentication request Device is always allowed access to the network Association request Association response Wireless Access Point Author: Bill Buchanan Authentication response
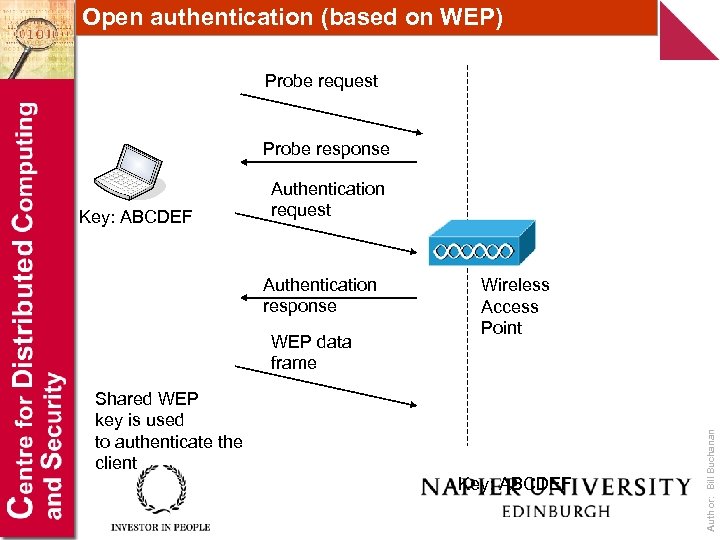
Open authentication (based on WEP) Probe request Probe response Authentication response WEP data frame Wireless Access Point Shared WEP key is used to authenticate the client Key: ABCDEF Author: Bill Buchanan Key: ABCDEF Authentication request
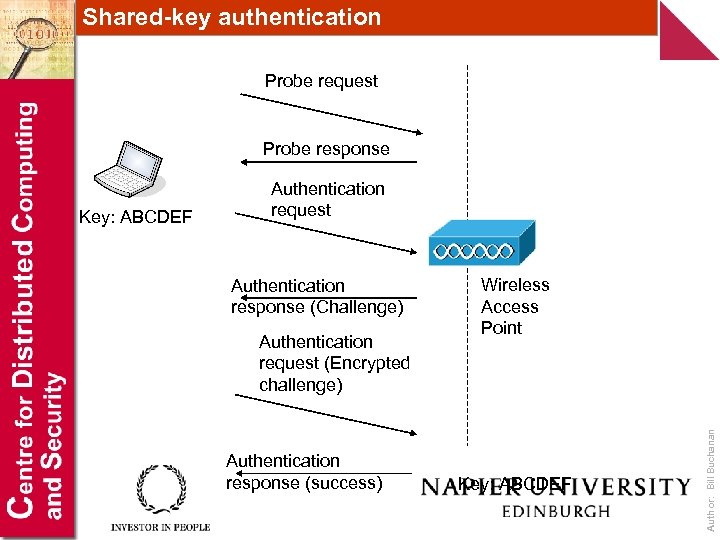
Shared-key authentication Probe request Probe response Authentication response (Challenge) Authentication request (Encrypted challenge) Authentication response (success) Wireless Access Point Key: ABCDEF Author: Bill Buchanan Key: ABCDEF Authentication request
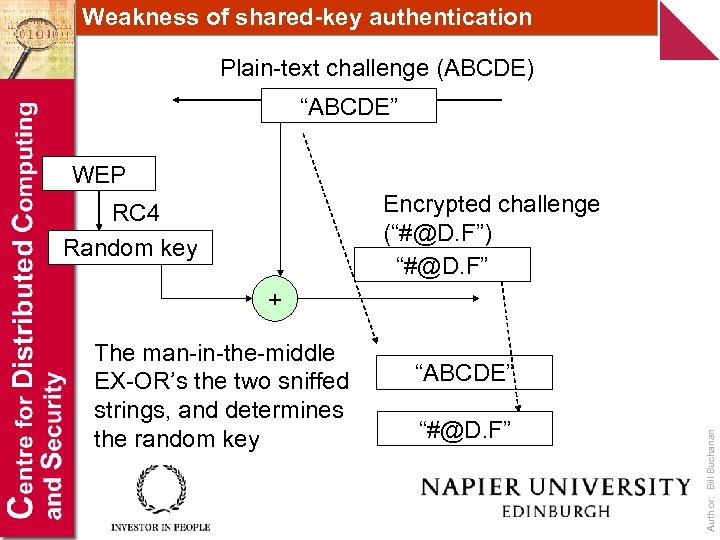
Weakness of shared-key authentication Plain-text challenge (ABCDE) “ABCDE” WEP Encrypted challenge (“#@D. F”) “#@D. F” RC 4 Random key + “ABCDE” “#@D. F” Author: Bill Buchanan The man-in-the-middle EX-OR’s the two sniffed strings, and determines the random key
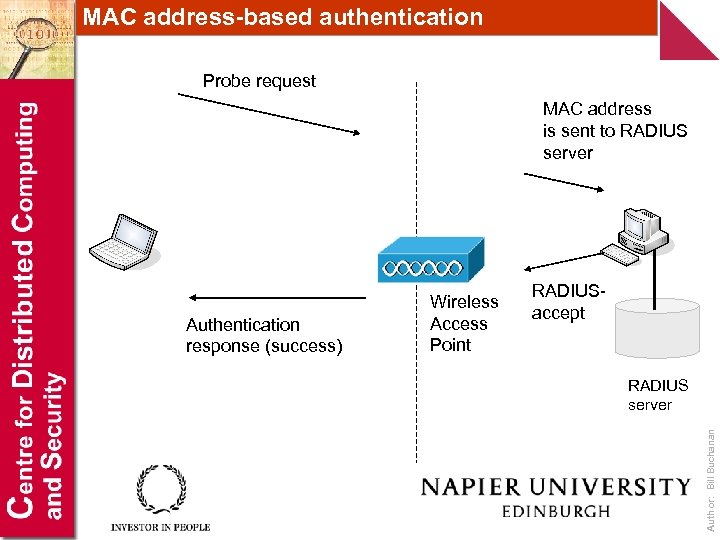
MAC address-based authentication Probe request MAC address is sent to RADIUS server RADIUSaccept RADIUS server Author: Bill Buchanan Authentication response (success) Wireless Access Point
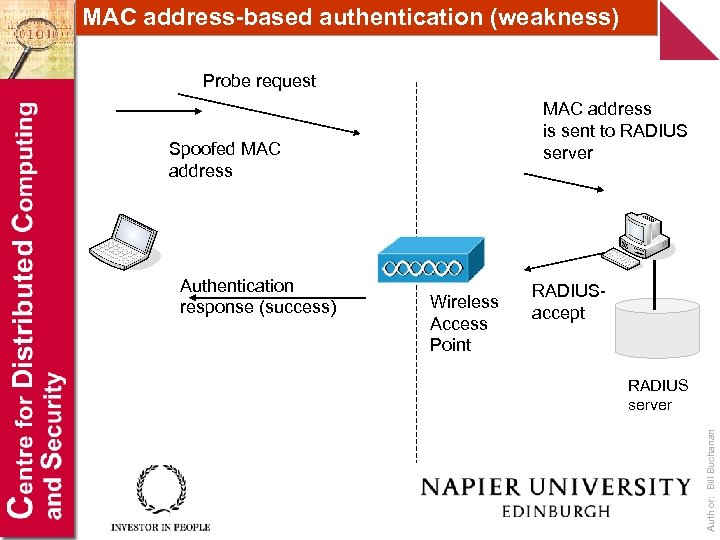
MAC address-based authentication (weakness) Probe request MAC address is sent to RADIUS server Authentication response (success) Wireless Access Point RADIUSaccept RADIUS server Author: Bill Buchanan Spoofed MAC address

Author: Bill Buchanan Enhanced Security
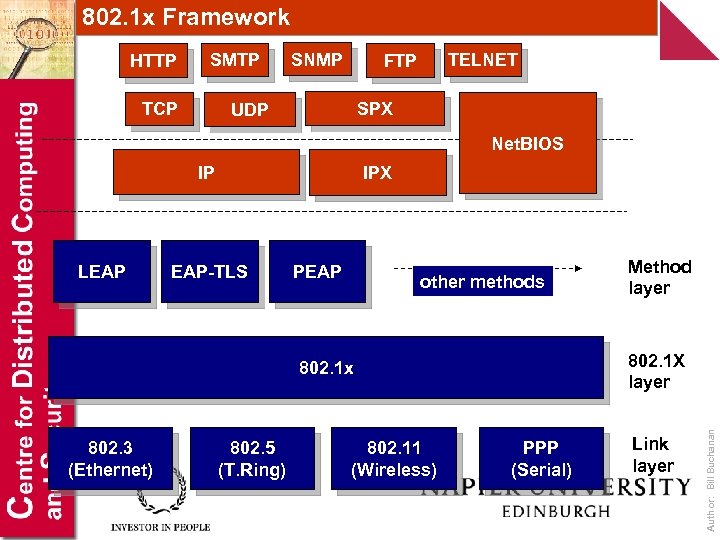
802. 1 x Framework HTTP SMTP TCP SNMP TELNET FTP SPX UDP Net. BIOS IP EAP-TLS PEAP other methods 802. 1 X layer 802. 1 x 802. 3 (Ethernet) 802. 5 (T. Ring) 802. 11 (Wireless) Method layer PPP (Serial) Link layer Author: Bill Buchanan LEAP IPX
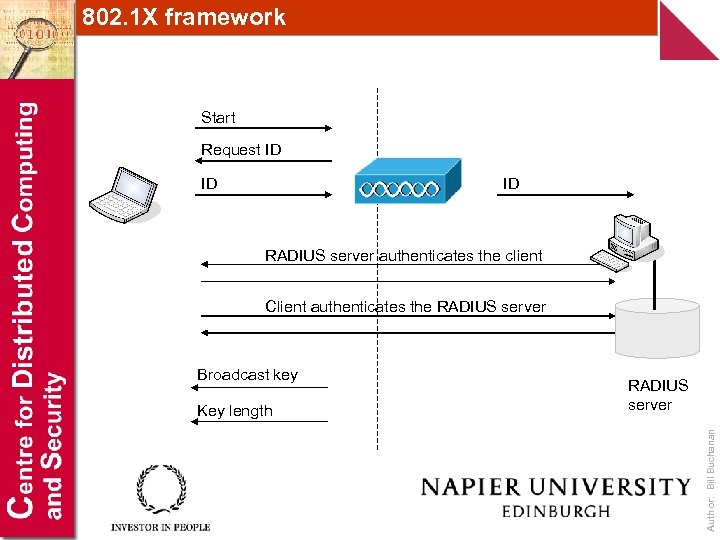
802. 1 X framework Start Request ID ID ID RADIUS server authenticates the client Client authenticates the RADIUS server Key length RADIUS server Author: Bill Buchanan Broadcast key

Author: Bill Buchanan EAP

EAP - Efficient Application Protocols EAP provides centralized authentication and dynamic key distribution. It has been developed by the IEEE 802. 11 i Task Group as an end-toend framework and uses 802. 1 X and EAP. This is: Authentication. This is of both the client and the authentication server (such as a RADIUS server). Encryption keys. These are dynamically created after authentication. They are not common to the whole network. Centralized policy control. A session time-out generates a reauthentication and the generation of new encryption keys. Author: Bill Buchanan A wireless client cannot gain access to the network, unless it has been authenticated by the access point or a RADIUS server, and has encryption keys.

There are many versions of EAP, including: LEAP - Lightweight EAP-TLS - EAP-Transport Layer Security PEAP - Protected EAP-TTLS - EAP-Tunnelled TLS EAP-SIM - EAP-Subscriber Identity Module Author: Bill Buchanan • • •
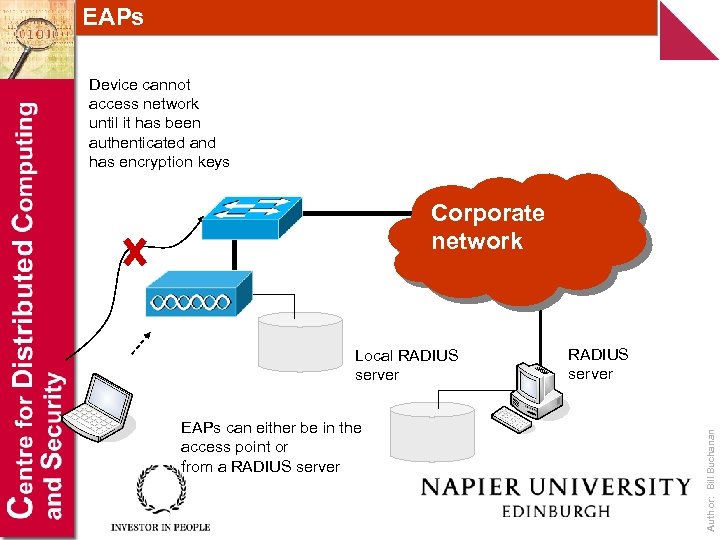
EAPs Device cannot access network until it has been authenticated and has encryption keys Corporate network EAPs can either be in the access point or from a RADIUS server Author: Bill Buchanan Local RADIUS server

EAPs 1. Client associates with the access point. 2. Client provides authentication details. 3. RADIUS server authenticates the user. 4. User authenticates the RADIUS server. 5. Client and RADIUS server derive unicast WEP key. 6. RADIUS server gives broadcast WEP key to access point. 7. Access point sends broadcast WEP key to client using unicast WEP key. Corporate network EAPs can either be in the access point or from a RADIUS server Author: Bill Buchanan Local RADIUS server
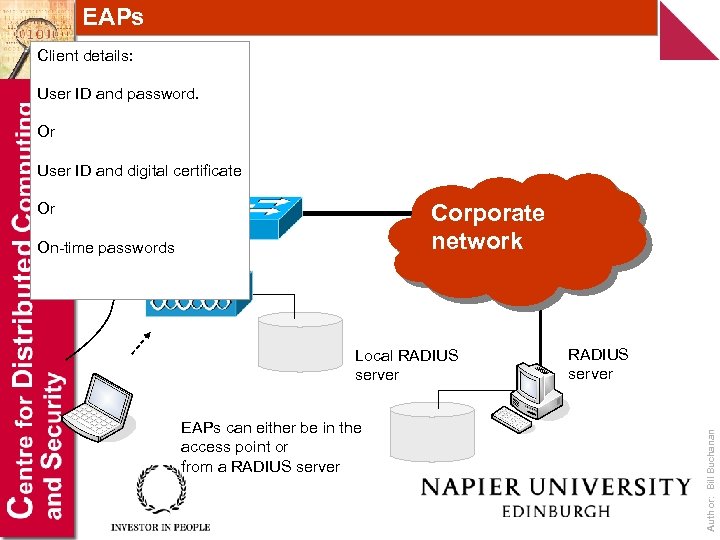
EAPs Client details: User ID and password. Or User ID and digital certificate Corporate network On-time passwords Local RADIUS server EAPs can either be in the access point or from a RADIUS server Author: Bill Buchanan Or
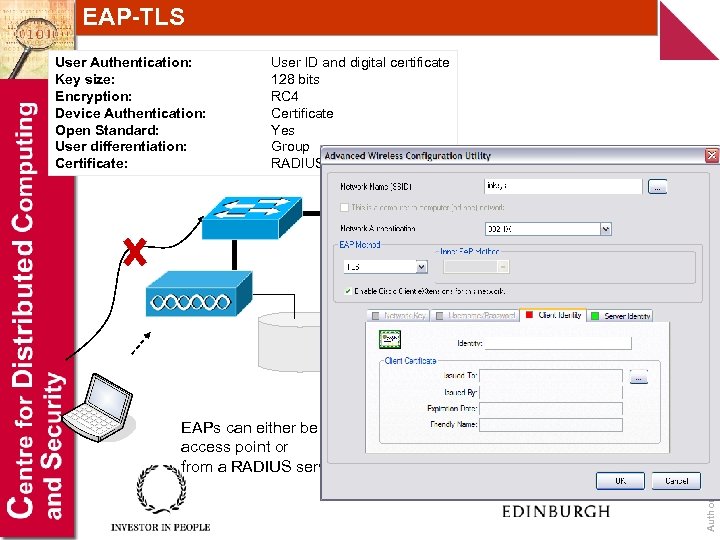
EAP-TLS User Authentication: Key size: Encryption: Device Authentication: Open Standard: User differentiation: Certificate: User ID and digital certificate 128 bits RC 4 Certificate Yes Group RADIUS server/WLAN client Corporate network EAPs can either be in the access point or from a RADIUS server Author: Bill Buchanan Local RADIUS server
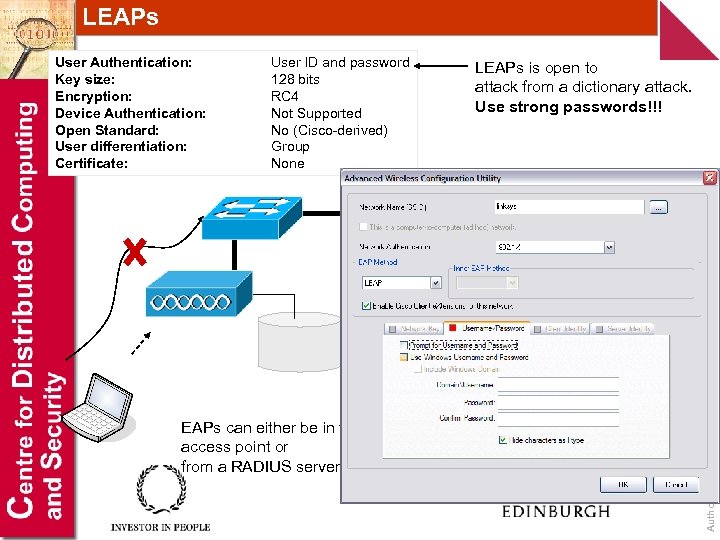
LEAPs User Authentication: Key size: Encryption: Device Authentication: Open Standard: User differentiation: Certificate: User ID and password 128 bits RC 4 Not Supported No (Cisco-derived) Group None LEAPs is open to attack from a dictionary attack. Use strong passwords!!! Corporate network EAPs can either be in the access point or from a RADIUS server Author: Bill Buchanan Local RADIUS server

LEAPs uses MS-CHAP (Microsoft Handshake Authentication Protocol) to continually challenge the device for its ID. It uses a challenge-response, mutual authentication protocol using Message Digest 4 (MD 4) and Data Encryption Standard (DES) algorithms to encrypt responses. The authenticating device challenges the client and vice-versa. If either challenge is incorrect, the connection is rejected. The password is converted into password hash using MD 4. It is thus not possible for an intruder to listen to the password. The hashed password is then converted into a Windows NT key, which has the advantage of being compatible with Microsoft Windows systems. Normally authentication is achieved using the Microsoft login screen, where the user name and the Windows NT key are passed from the client to the access point. Author: Bill Buchanan LEAPs is open to attack from a dictionary attack, thus strong passwords should be used. There also many programs which can search for passwords and determine their hash function.

EAP - PEAPs User Authentication: Key size: Encryption: Device Authentication: Open Standard: User differentiation: Certificate: User ID and password or OTP (one-time password) 128 bits RC 4 Not supported Yes Group Yes Corporate network EAPs can either be in the access point or from a RADIUS server Author: Bill Buchanan Local RADIUS server
Author: Bill Buchanan PEAPs
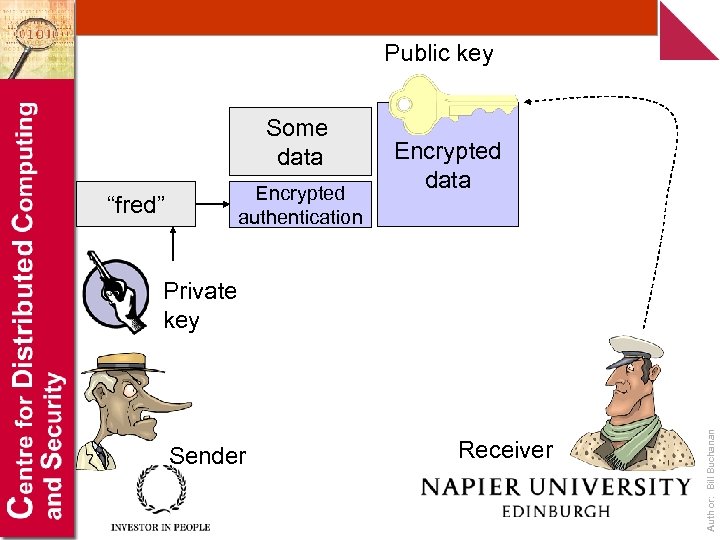
Public key Some data Encrypted authentication “fred” Encrypted data Sender Receiver Author: Bill Buchanan Private key
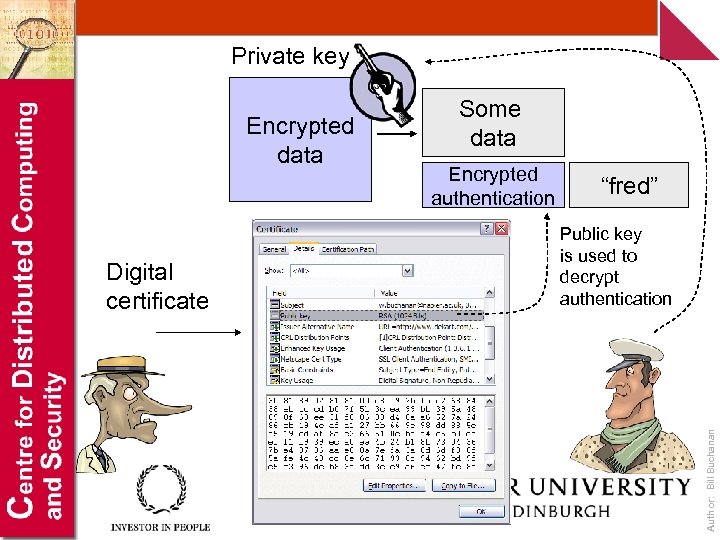
Private key Digital certificate Encrypted authentication “fred” Public key is used to decrypt authentication Author: Bill Buchanan Encrypted data Some data
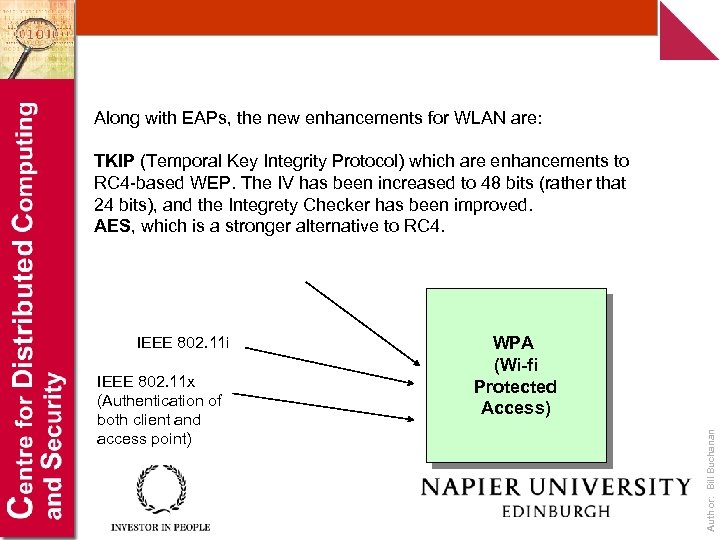
Along with EAPs, the new enhancements for WLAN are: TKIP (Temporal Key Integrity Protocol) which are enhancements to RC 4 -based WEP. The IV has been increased to 48 bits (rather that 24 bits), and the Integrety Checker has been improved. AES, which is a stronger alternative to RC 4. IEEE 802. 11 x (Authentication of both client and access point) WPA (Wi-fi Protected Access) Author: Bill Buchanan IEEE 802. 11 i
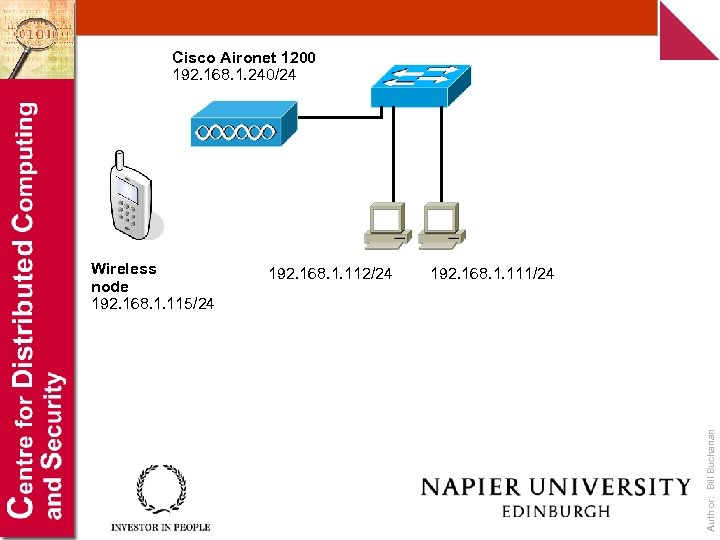
Cisco Aironet 1200 192. 168. 1. 240/24 192. 168. 1. 112/24 192. 168. 1. 111/24 Author: Bill Buchanan Wireless node 192. 168. 1. 115/24
Author: Bill Buchanan Configuration – Local RADIUS server
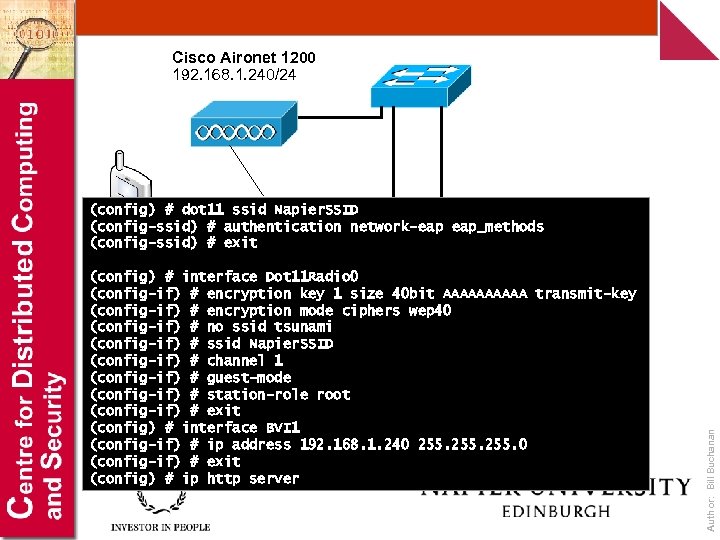
Cisco Aironet 1200 192. 168. 1. 240/24 (config) # dot 11 ssid Napier. SSID (config-ssid) # authentication network-eap eap_methods (config-ssid) # exit Author: Bill Buchanan Wireless 192. 168. 1. 112/24 192. 168. 1. 111/24 (config) # interface Dot 11 Radio 0 node (config-if) # encryption key 1 size 40 bit AAAAA transmit-key 192. 168. 1. 115/24 (config-if) # encryption mode ciphers wep 40 (config-if) # no ssid tsunami (config-if) # ssid Napier. SSID (config-if) # channel 1 (config-if) # guest-mode (config-if) # station-role root (config-if) # exit (config) # interface BVI 1 (config-if) # ip address 192. 168. 1. 240 255. 0 (config-if) # exit (config) # ip http server
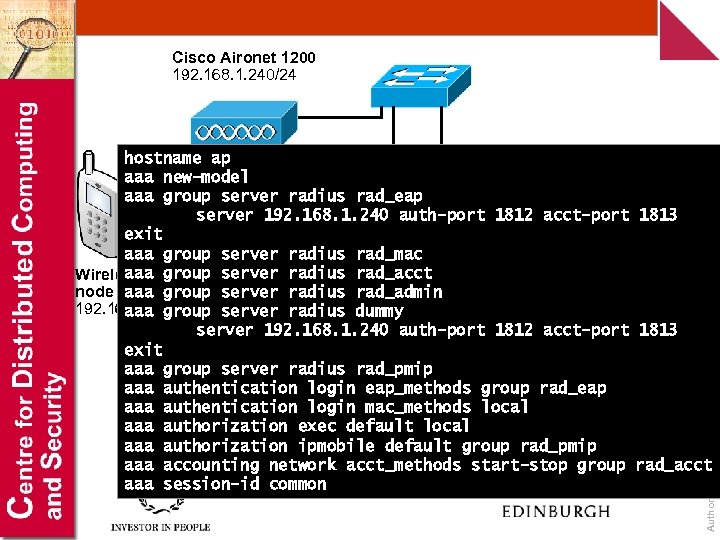
Cisco Aironet 1200 192. 168. 1. 240/24 Author: Bill Buchanan hostname ap aaa new-model aaa group server radius rad_eap server 192. 168. 1. 240 auth-port 1812 acct-port 1813 exit aaa group server radius rad_mac aaa 192. 168. 1. 112/24 Wireless group server radius rad_acct 192. 168. 1. 111/24 node aaa group server radius rad_admin 192. 168. 1. 115/24 server radius dummy aaa group server 192. 168. 1. 240 auth-port 1812 acct-port 1813 exit aaa group server radius rad_pmip aaa authentication login eap_methods group rad_eap aaa authentication login mac_methods local aaa authorization exec default local aaa authorization ipmobile default group rad_pmip aaa accounting network acct_methods start-stop group rad_acct aaa session-id common
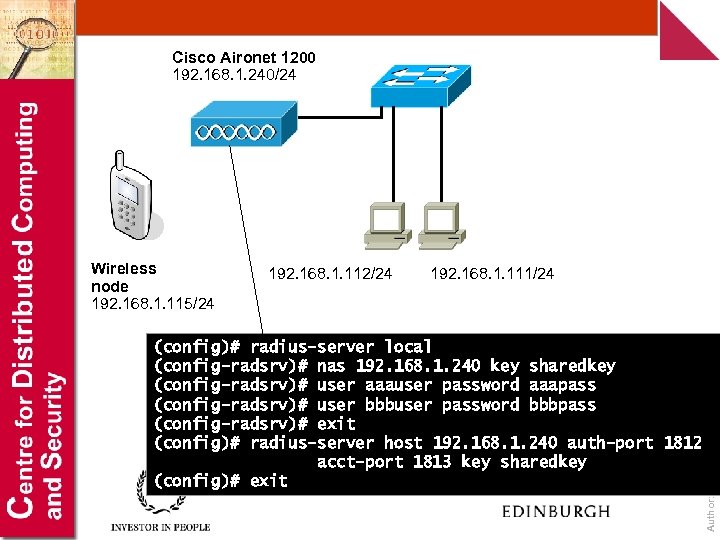
Cisco Aironet 1200 192. 168. 1. 240/24 192. 168. 1. 112/24 192. 168. 1. 111/24 (config)# radius-server local (config-radsrv)# nas 192. 168. 1. 240 key sharedkey (config-radsrv)# user aaauser password aaapass (config-radsrv)# user bbbuser password bbbpass (config-radsrv)# exit (config)# radius-server host 192. 168. 1. 240 auth-port 1812 acct-port 1813 key sharedkey (config)# exit Author: Bill Buchanan Wireless node 192. 168. 1. 115/24
Cisco Aironet 1200 192. 168. 1. 240/24 192. 168. 1. 112/24 192. 168. 1. 111/24 Author: Bill Buchanan Wireless node 192. 168. 1. 115/24
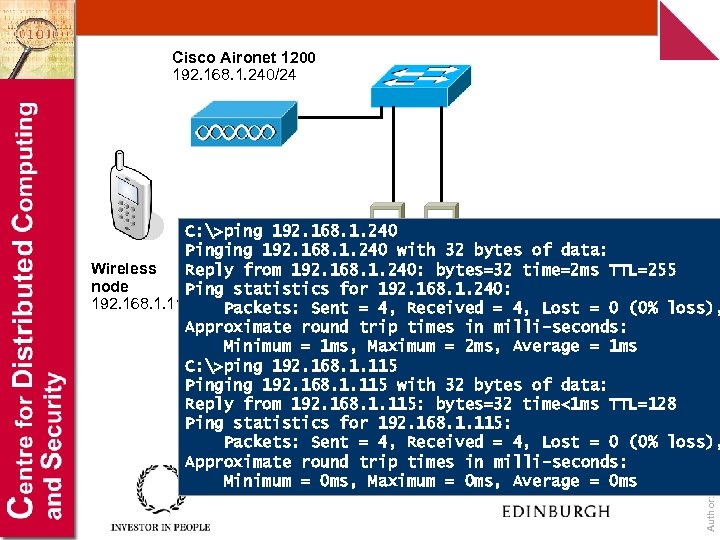
Cisco Aironet 1200 192. 168. 1. 240/24 Author: Bill Buchanan C: >ping 192. 168. 1. 240 Pinging 192. 168. 1. 240 with 32 bytes of data: Wireless Reply from 192. 168. 1. 240: 192. 168. 1. 111/24 bytes=32 time=2 ms TTL=255 192. 168. 1. 112/24 node Ping statistics for 192. 168. 1. 240: 192. 168. 1. 115/24 Packets: Sent = 4, Received = 4, Lost = 0 (0% loss), Approximate round trip times in milli-seconds: Minimum = 1 ms, Maximum = 2 ms, Average = 1 ms C: >ping 192. 168. 1. 115 Pinging 192. 168. 1. 115 with 32 bytes of data: Reply from 192. 168. 1. 115: bytes=32 time<1 ms TTL=128 Ping statistics for 192. 168. 1. 115: Packets: Sent = 4, Received = 4, Lost = 0 (0% loss), Approximate round trip times in milli-seconds: Minimum = 0 ms, Maximum = 0 ms, Average = 0 ms
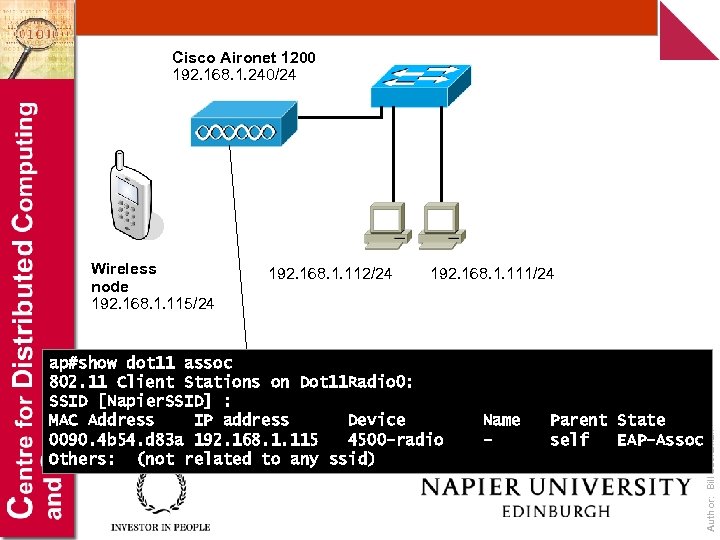
Cisco Aironet 1200 192. 168. 1. 240/24 192. 168. 1. 112/24 192. 168. 1. 111/24 ap#show dot 11 assoc 802. 11 Client Stations on Dot 11 Radio 0: SSID [Napier. SSID] : MAC Address IP address Device 0090. 4 b 54. d 83 a 192. 168. 1. 115 4500 -radio Others: (not related to any ssid) Name - Parent State self EAP-Assoc Author: Bill Buchanan Wireless node 192. 168. 1. 115/24
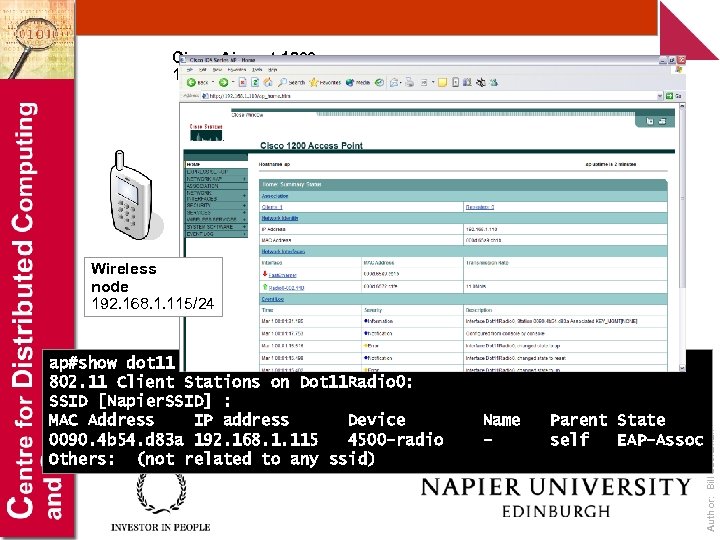
Cisco Aironet 1200 192. 168. 1. 240/24 192. 168. 1. 112/24 192. 168. 1. 111/24 ap#show dot 11 assoc 802. 11 Client Stations on Dot 11 Radio 0: SSID [Napier. SSID] : MAC Address IP address Device 0090. 4 b 54. d 83 a 192. 168. 1. 115 4500 -radio Others: (not related to any ssid) Name - Parent State self EAP-Assoc Author: Bill Buchanan Wireless node 192. 168. 1. 115/24
Author: Bill Buchanan Configure for Remote TACACS+ Server
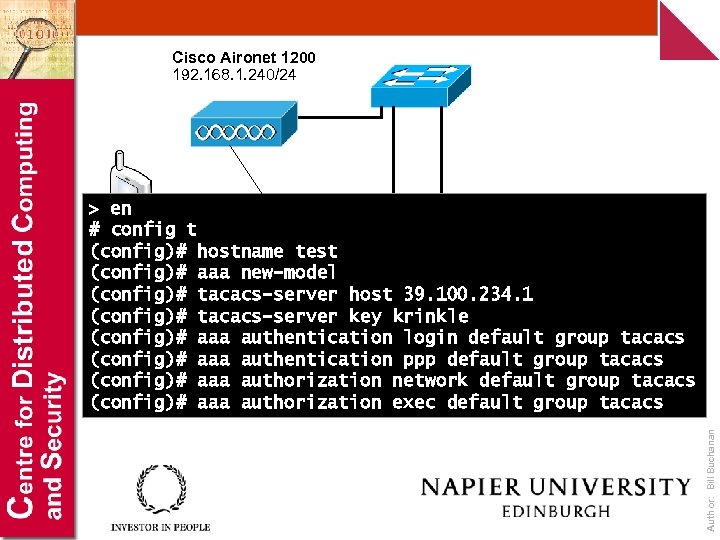
Cisco Aironet 1200 192. 168. 1. 240/24 Author: Bill Buchanan > en # config t (config)# hostname test Wireless (config)# aaa new-model 192. 168. 1. 112/24 192. 168. 1. 111/24 node (config)# tacacs-server host 39. 100. 234. 1 192. 168. 1. 115/24 (config)# tacacs-server key krinkle (config)# aaa authentication login default group tacacs (config)# aaa authentication ppp default group tacacs (config)# aaa authorization network default group tacacs (config)# aaa authorization exec default group tacacs

Author: Bill Buchanan Good Design Principles
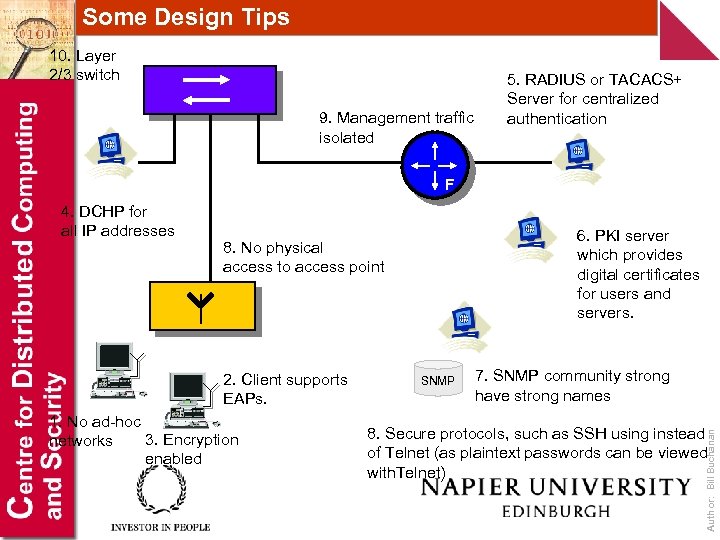
Some Design Tips 10. Layer 2/3 switch 9. Management traffic isolated 5. RADIUS or TACACS+ Server for centralized authentication F 6. PKI server which provides digital certificates for users and servers. 8. No physical access to access point 2. Client supports EAPs. 1. No ad-hoc 3. Encryption networks enabled SNMP 7. SNMP community strong have strong names 8. Secure protocols, such as SSH using instead of Telnet (as plaintext passwords can be viewed with. Telnet) Author: Bill Buchanan 4. DCHP for all IP addresses
2ed57a5bbe6fa7412a39aaf63bd0c4d2.ppt