dfac7186965fdef53893daa1f1129f55.ppt
- Количество слайдов: 37
Authentication of Kerberos and Wireless Communication • Kerberos • AMPS • IS-95 : A-Key • GSM • DECT • Bluetooth • 802. 11 b

Kerberos
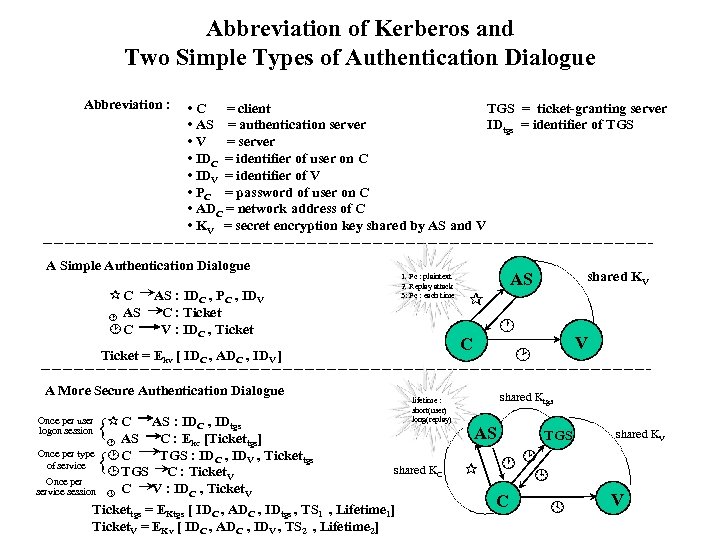
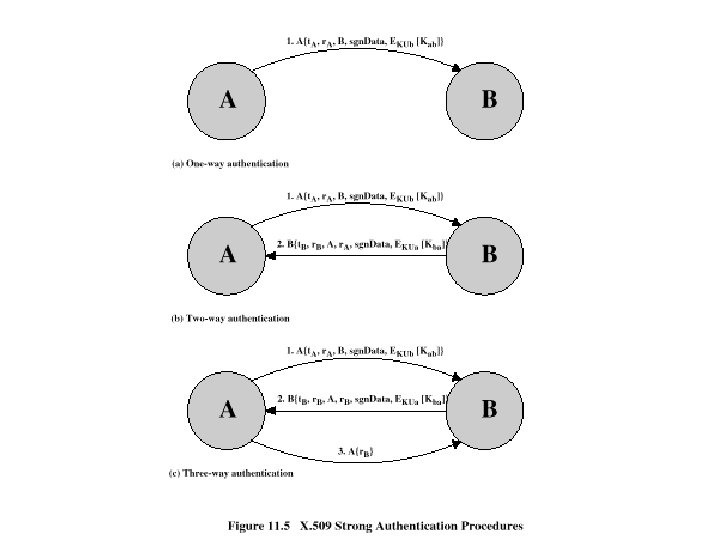
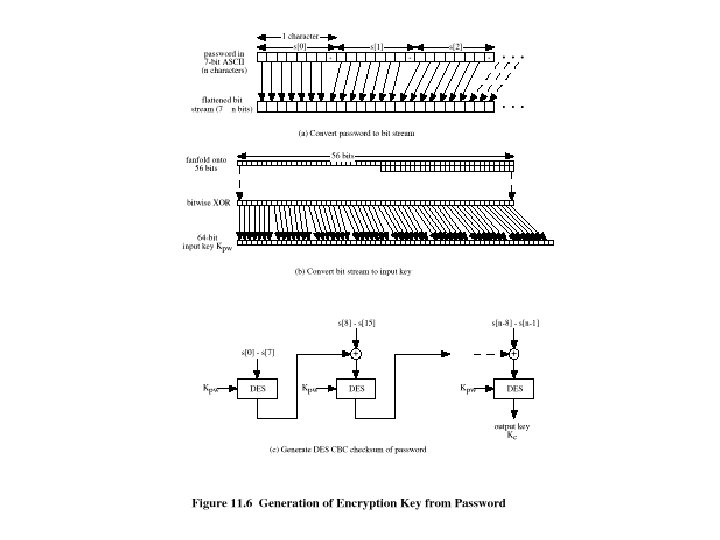
Abbreviation of Kerberos and Two Simple Types of Authentication Dialogue Abbreviation : • C = client TGS = ticket-granting server • AS = authentication server IDtgs = identifier of TGS • V = server • IDC = identifier of user on C • IDV = identifier of V • PC = password of user on C • ADC = network address of C • KV = secret encryption key shared by AS and V A Simple Authentication Dialogue 1. Pc : plaintext 2. Replay attack 3: Pc : each time ¶ C AS : IDC , PC , IDV C : Ticket · AS ¸C V : IDC , Ticket A More Secure Authentication Dialogue C ID , ID {¶ AS AS : : E [Ticket C Once per type ¸ C TGS : ID , ID of service { ¹ TGS C : Ticket C · tgs kc C Once per service session V lifetime : short(user) long(replay) tgs] V , Tickettgs shared KC C V : IDC , Ticket. V Tickettgs = EKtgs [ IDC , ADC , IDtgs , TS 1 , Lifetime 1] Ticket. V = EKv [ IDC , ADC , IDV , TS 2 , Lifetime 2] º shared KV ¶ · C Ticket = Ekv [ IDC , ADC , IDV ] Once per user logon session AS V ¸ shared Ktgs AS ¶ TGS shared KV ·¸ ¹ C º V
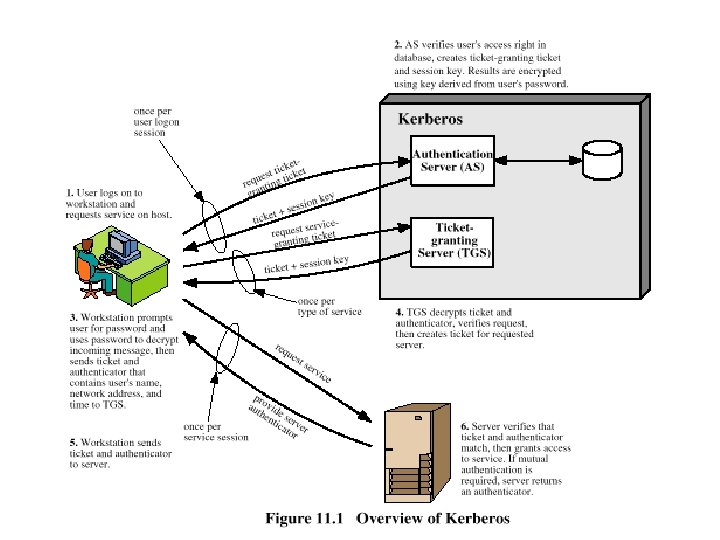
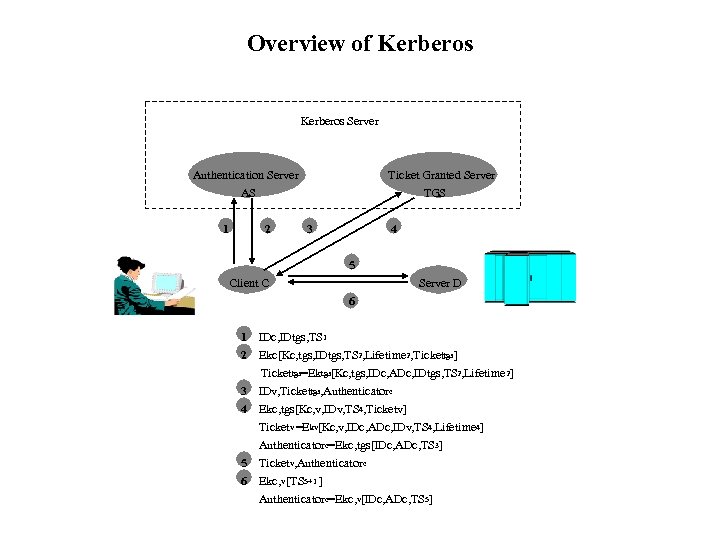
Overview of Kerberos Server Authentication Server AS 1 2 Ticket Granted Server TGS 3 4 5 Client C Server D 6 1 IDc, IDtgs, TS 1 2 Ekc[Kc, tgs, IDtgs, TS 2, Lifetime 2, Tickettgs] Tickettgs=Ektgs[Kc, tgs, IDc, ADc, IDtgs, TS 2, Lifetime 2] 3 IDv, Tickettgs, Authenticatorc 4 Ekc, tgs[Kc, v, IDv, TS 4, Ticketv] Ticketv =Ekv[Kc, v, IDc, ADc, IDv, TS 4, Lifetime 4] Authenticatorc=Ekc, tgs[IDc, ADc, TS 3] 5 Ticketv, Authenticatorc 6 Ekc, v [TS 5+1 ] Authenticatorc=Ekc, v[IDc, ADc, TS 5]
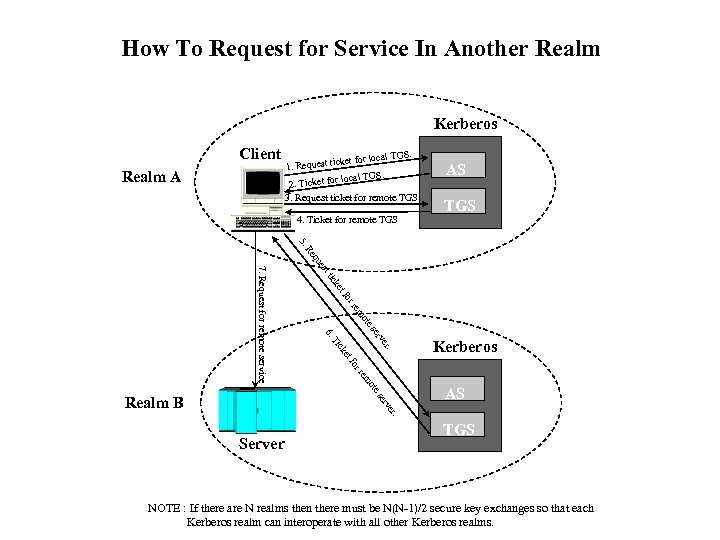
How To Request for Service In Another Realm Kerberos Client Realm A S. l TG cket for loca 1. Request ti local TGS. 2. Ticket for 3. Request ticket for remote TGS 4. Ticket for remote TGS AS TGS 5. t es qu Re or tf ke tic ote rem rv se 6. et ck er. Ti ote em rr fo 7. Request for remote service AS er. rv se Realm B Kerberos Server TGS NOTE : If there are N realms then there must be N(N-1)/2 secure key exchanges so that each Kerberos realm can interoperate with all other Kerberos realms.
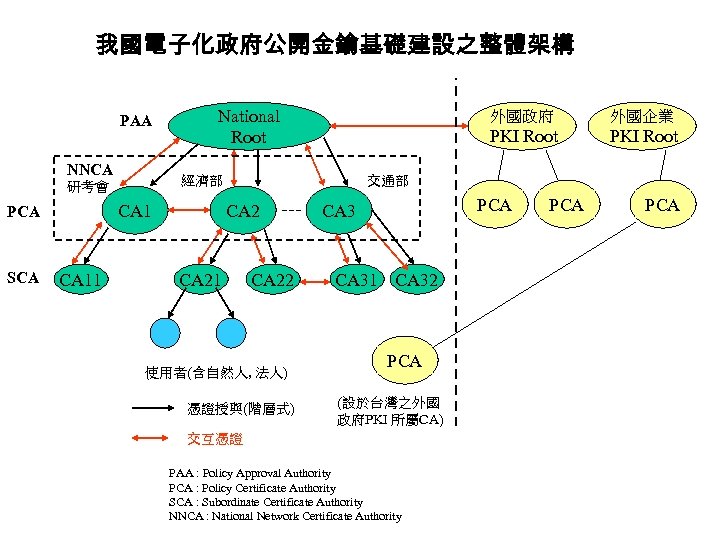
我國電子化政府公開金鑰基礎建設之整體架構 PAA NNCA CA 1 PCA CA 11 外國政府 外國企業 PKI Root 經濟部 研考會 SCA National Root PKI Root 交通部 CA 21 CA 22 使用者(含自然人, 法人) 憑證授與(階層式) PCA CA 31 CA 32 PCA (設於台灣之外國 政府PKI 所屬CA) 交互憑證 PAA : Policy Approval Authority PCA : Policy Certificate Authority SCA : Subordinate Certificate Authority NNCA : National Network Certificate Authority PCA
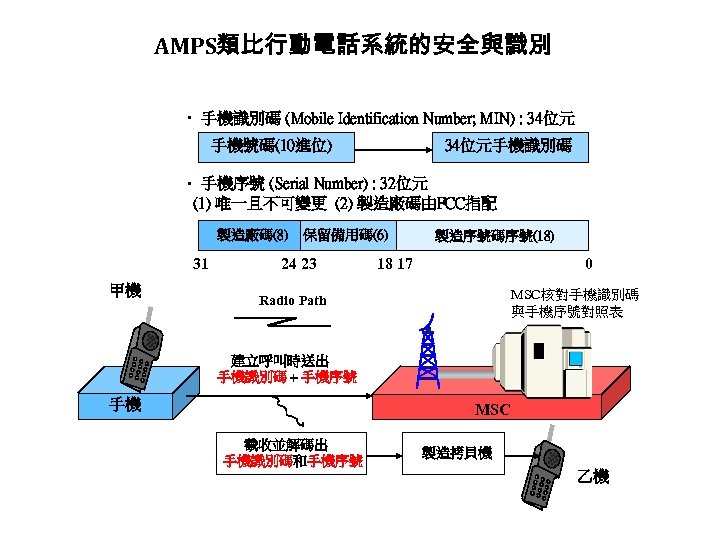
AMPS類比行動電話系統的安全與識別 • 手機識別碼 (Mobile Identification Number; MIN) : 34位元 手機號碼(10進位) 34位元手機識別碼 • 手機序號 (Serial Number) : 32位元 (1) 唯一且不可變更 (2) 製造廠碼由FCC指配 製造廠碼(8) 31 甲機 保留備用碼(6) 24 23 製造序號碼序號(18) 18 17 0 MSC核對手機識別碼 與手機序號對照表 Radio Path 建立呼叫時送出 手機識別碼 + 手機序號 手機 MSC 截收並解碼出 手機識別碼和手機序號 製造拷貝機 乙機
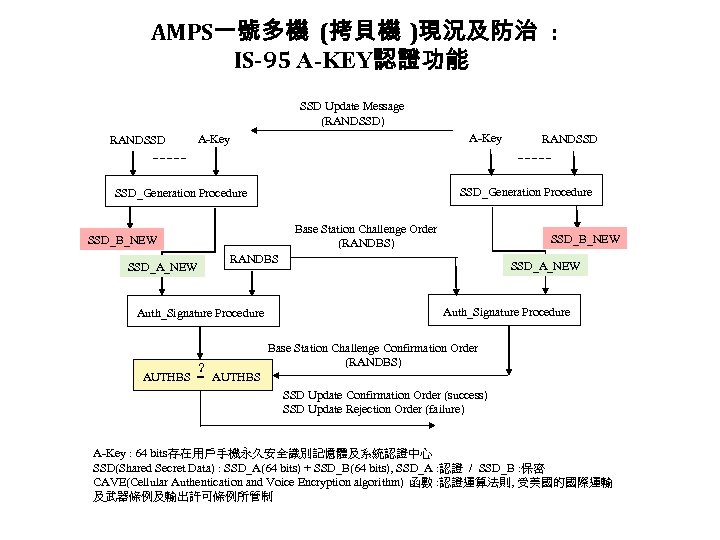
AMPS一號多機 (拷貝機 )現況及防治 : IS-95 A-KEY認證功能 SSD Update Message (RANDSSD) RANDSSD A-Key SSD_Generation Procedure Base Station Challenge Order (RANDBS) SSD_B_NEW RANDBS SSD_A_NEW Auth_Signature Procedure ? RANDSSD SSD_A_NEW Auth_Signature Procedure Base Station Challenge Confirmation Order (RANDBS) AUTHBS = AUTHBS SSD Update Confirmation Order (success) SSD Update Rejection Order (failure) A-Key : 64 bits存在用戶手機永久安全識別記憶體及系統認證中心 SSD(Shared Secret Data) : SSD_A(64 bits) + SSD_B(64 bits), SSD_A : 認證 / SSD_B : 保密 CAVE(Cellular Authentication and Voice Encryption algorithm) 函數 : 認證運算法則, 受美國的國際運輸 及武器條例及輸出許可條例所管制
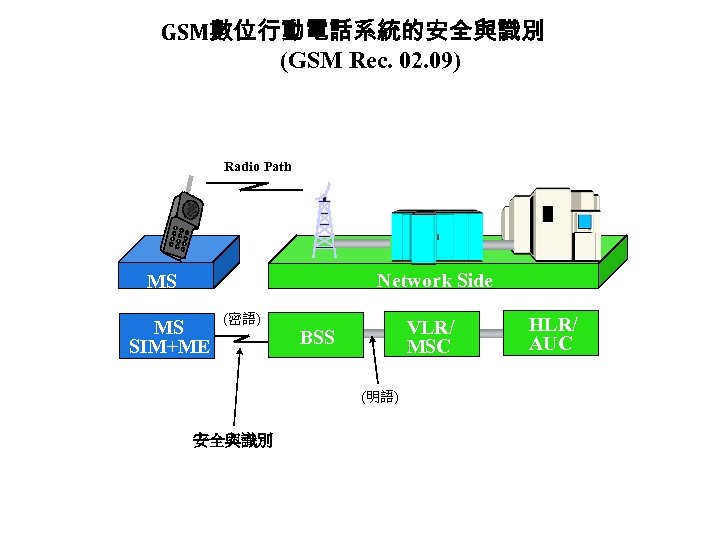
GSM數位行動電話系統的安全與識別 (GSM Rec. 02. 09) Radio Path Network Side MS MS SIM+ME (密語) VLR/ MSC BSS (明語) 安全與識別 HLR/ AUC
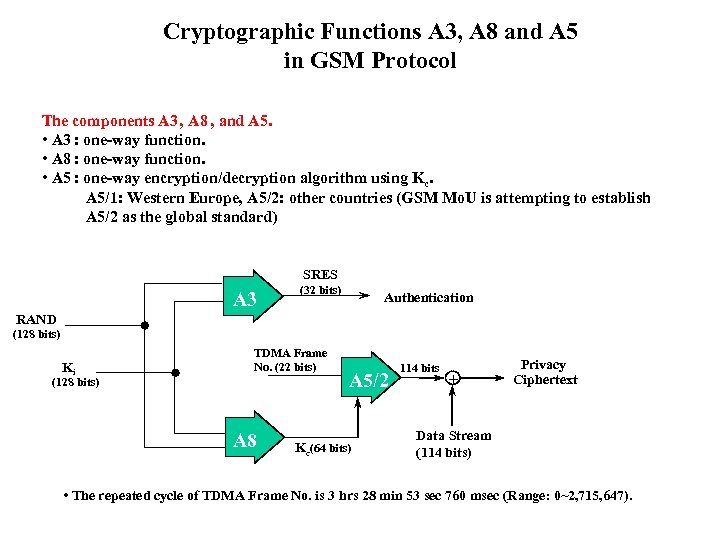
Cryptographic Functions A 3, A 8 and A 5 in GSM Protocol The components A 3 , A 8 , and A 5. • A 3 : one-way function. • A 8 : one-way function. • A 5 : one-way encryption/decryption algorithm using Kc. A 5/1: Western Europe, A 5/2: other countries (GSM Mo. U is attempting to establish A 5/2 as the global standard) SRES A 3 (32 bits) Authentication RAND (128 bits) Ki TDMA Frame No. (22 bits) (128 bits) A 8 A 5/2 Kc(64 bits) 114 bits + Privacy Ciphertext Data Stream (114 bits) • The repeated cycle of TDMA Frame No. is 3 hrs 28 min 53 sec 760 msec (Range: 0~2, 715, 647).
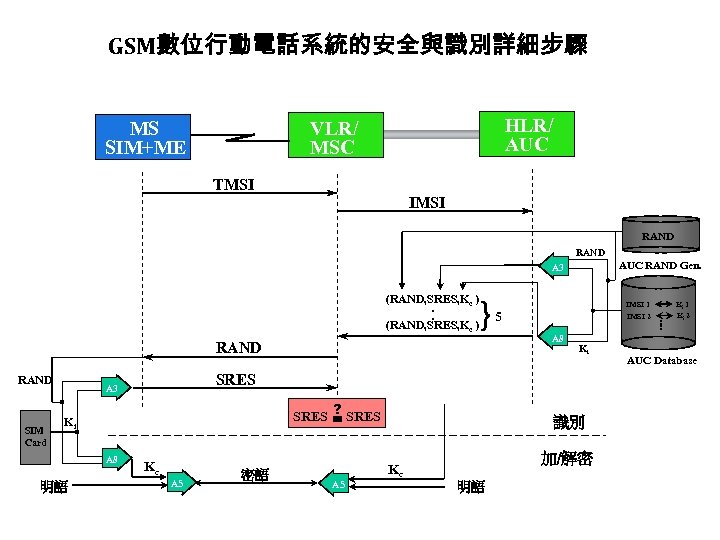
GSM數位行動電話系統的安全與識別詳細步驟 HLR/ AUC VLR/ MSC MS SIM+ME TMSI IMSI RAND AUC RAND Gen. A 3 }5 RAND SIM Card ? SRES = SRES Ki 明語 A 8 Ki SRES A 3 A 8 IMSI 1 IMSI 2 Kc A 5 密語 識別 加/解密 Kc A 5 明語 . . (RAND, SRES, Kc ). . (RAND, SRES, Kc ) Ki 1 Ki 2 AUC Database
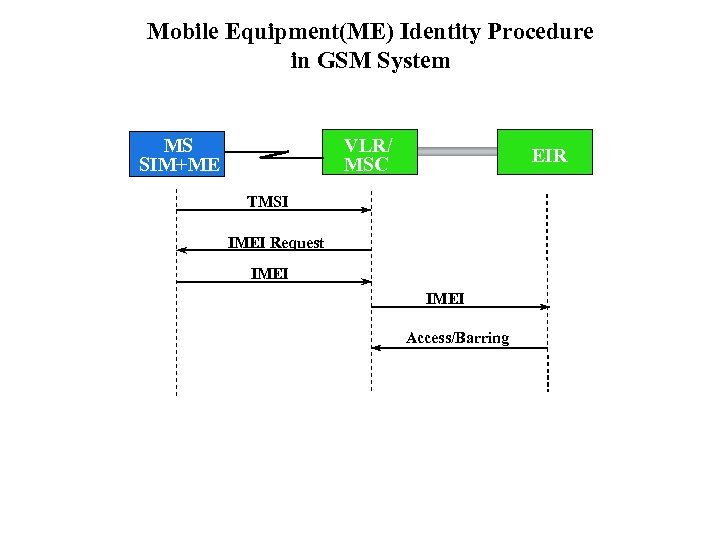
Mobile Equipment(ME) Identity Procedure in GSM System VLR/ MSC MS SIM+ME EIR TMSI IMEI Request IMEI Access/Barring
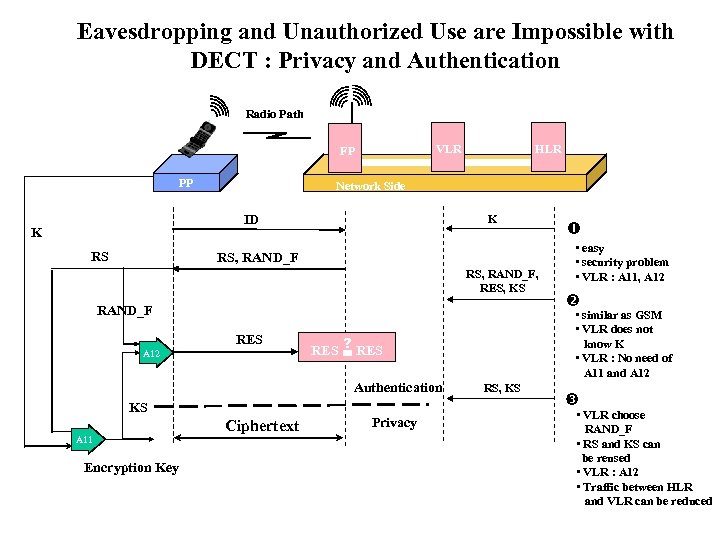
Eavesdropping and Unauthorized Use are Impossible with DECT : Privacy and Authentication Radio Path VLR FP PP Network Side ID K RS HLR K RS, RAND_F, RES, KS RAND_F RES A 12 KS A 11 Encryption Key Ciphertext Privacy • easy • security problem • VLR : A 11, A 12 • similar as GSM • VLR does not know K • VLR : No need of A 11 and A 12 ? RES = RES Authentication RS, KS • VLR choose RAND_F • RS and KS can be reused • VLR : A 12 • Traffic between HLR and VLR can be reduced
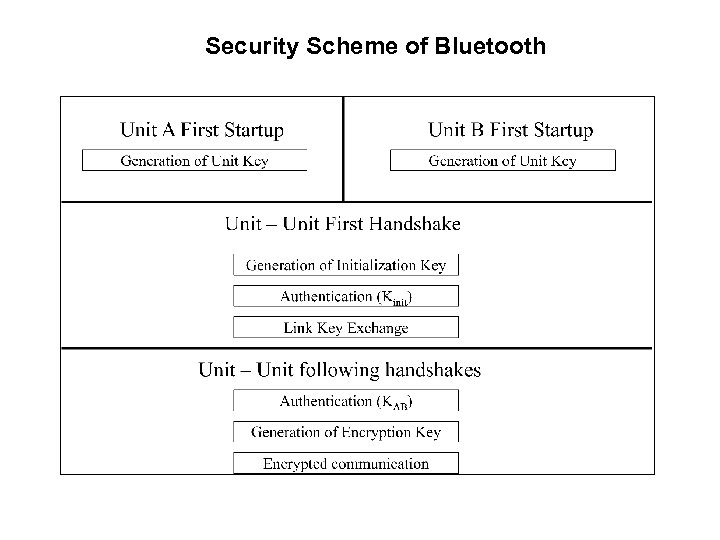
Security Scheme of Bluetooth
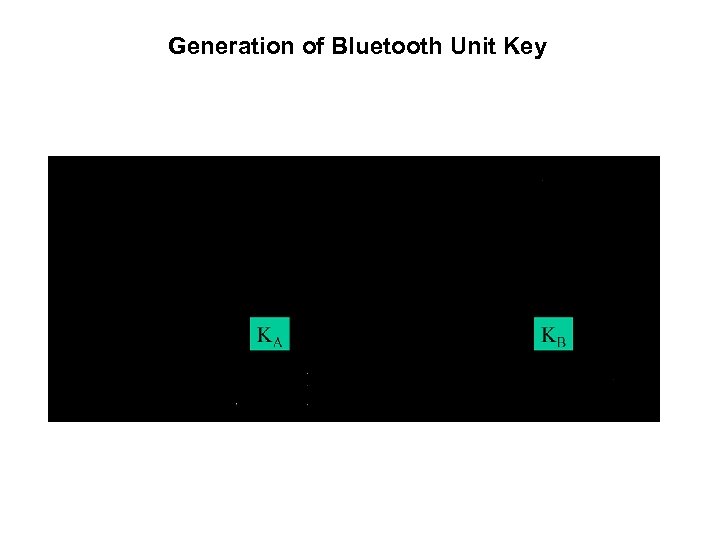
Generation of Bluetooth Unit Key
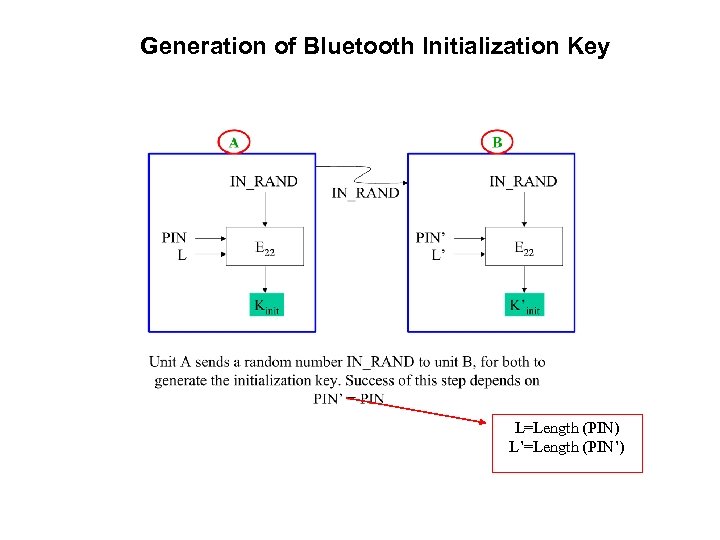
Generation of Bluetooth Initialization Key L=Length (PIN) L’=Length (PIN’)
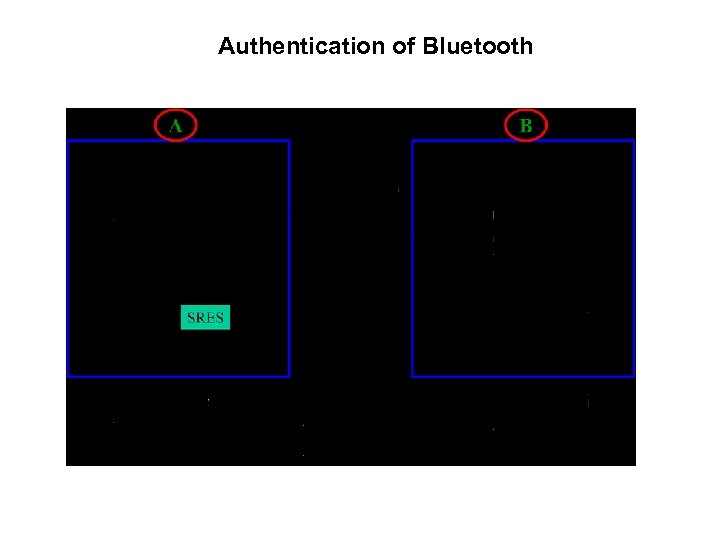
Authentication of Bluetooth
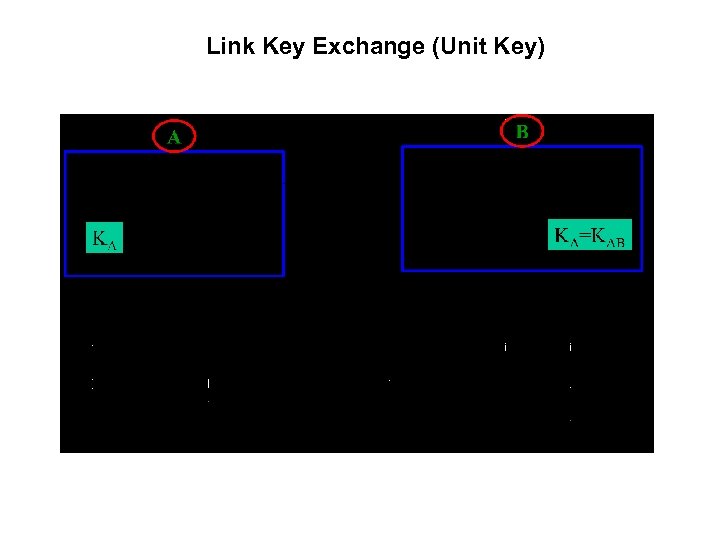
Link Key Exchange (Unit Key)
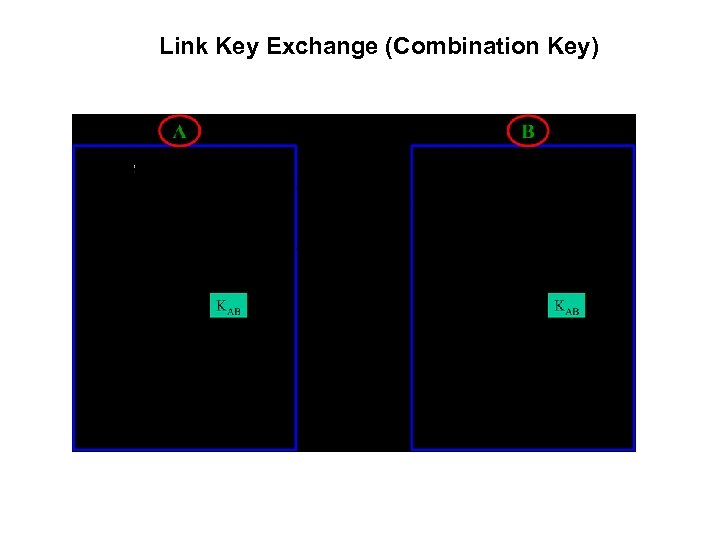
Link Key Exchange (Combination Key)
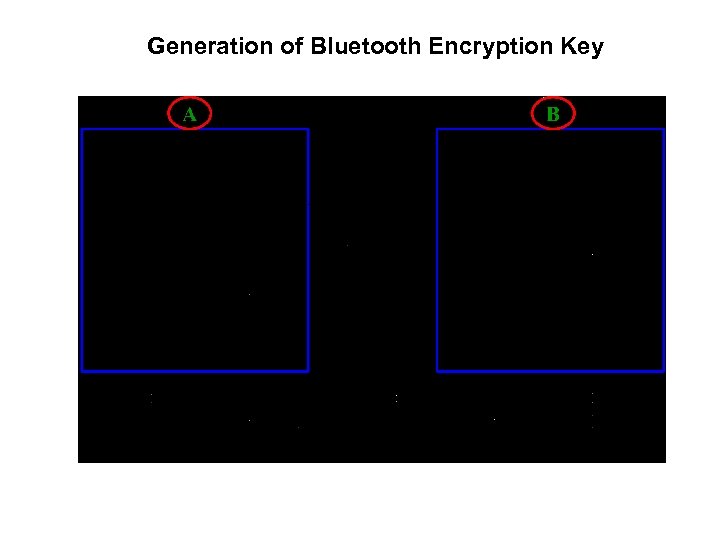
Generation of Bluetooth Encryption Key
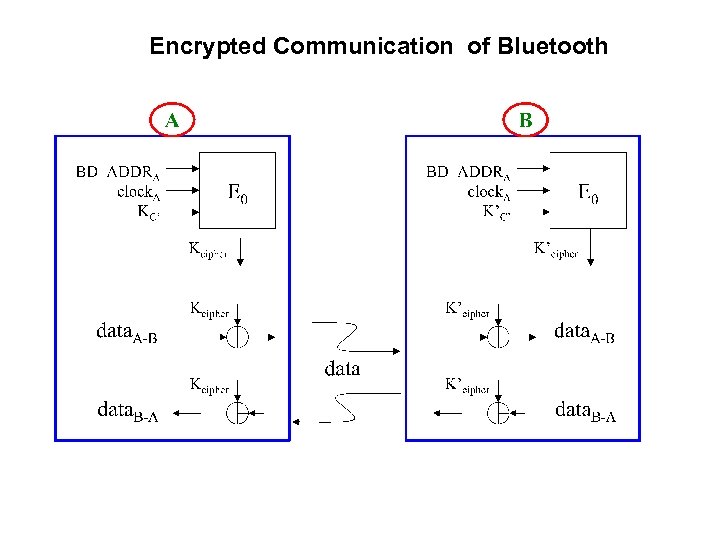
Encrypted Communication of Bluetooth
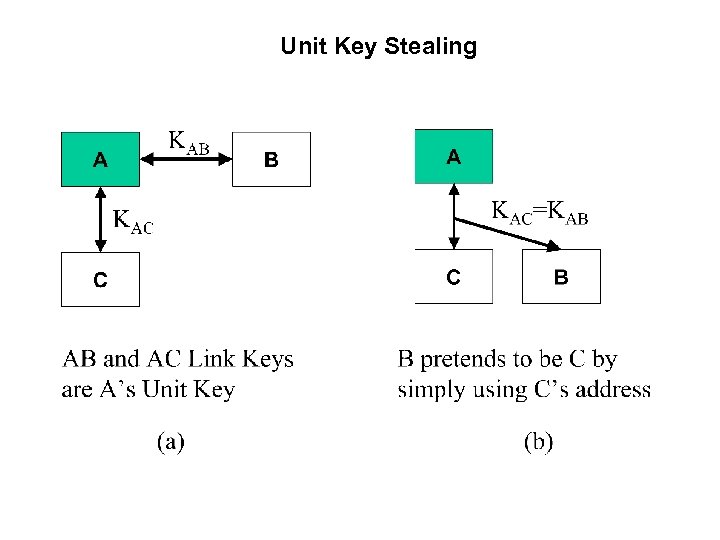
Unit Key Stealing
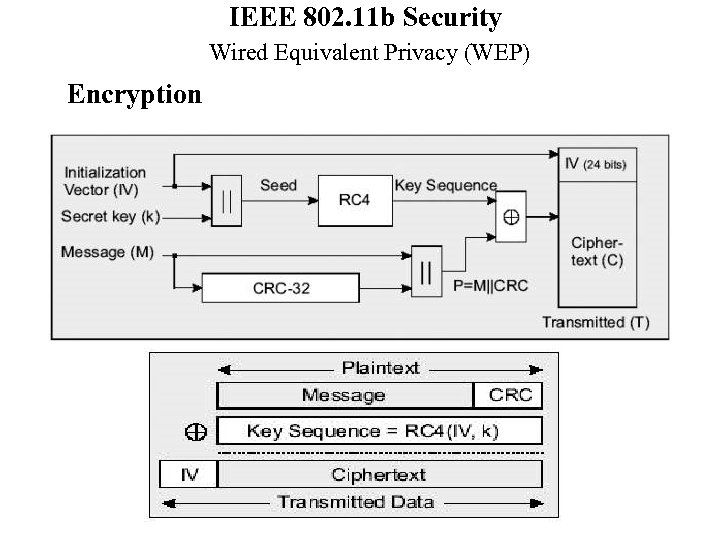
IEEE 802. 11 b Security Wired Equivalent Privacy (WEP) Encryption
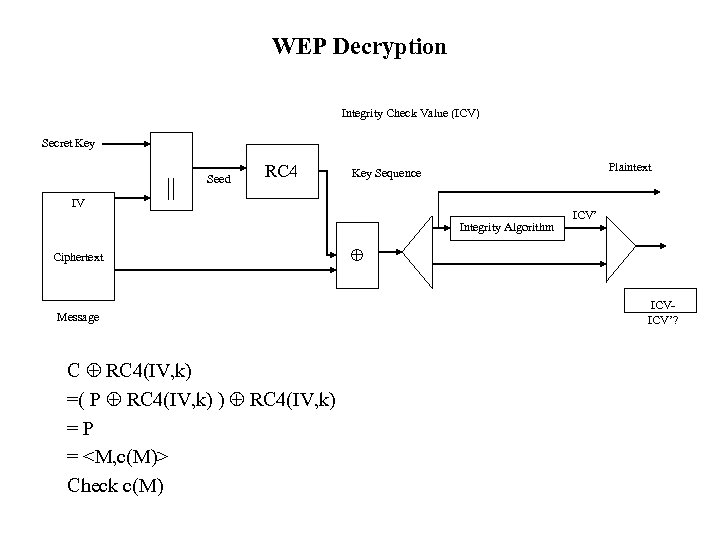
WEP Decryption Integrity Check Value (ICV) Secret Key IV || Seed RC 4 Plaintext Key Sequence Integrity Algorithm Ciphertext Message C RC 4(IV, k) =( P RC 4(IV, k) ) RC 4(IV, k) =P = <M, c(M)> Check c(M) ICV’ ICVICV’?

Authentication of 802. 11 b There are two types of authentication 1. Open system authentication. This is the default authentication service that does not has any authentication. 2. Shared key authentication. This involves a shared secret key to authenticate the station to the AP(access point).
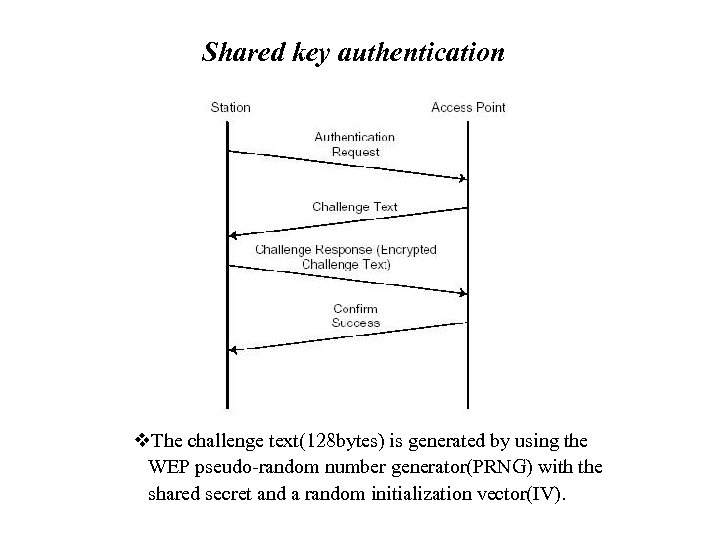
Shared key authentication v. The challenge text(128 bytes) is generated by using the WEP pseudo-random number generator(PRNG) with the shared secret and a random initialization vector(IV).

Security Flaws The risks of keystream reuse If C 1= P 1 RC 4(IV, k) and C 2= P 2 RC 4(IV, k) then C 1 C 2 = ( P 1 RC 4(IV, k)) ( P 2 RC 4(IV, k)) = P 1 P 2 v The WEP standard recommends(but does not require) that the IV be changed after every packet.
Reuse Initialization Vector • The IV field used bye WEP is only 24 bits wide, nearly guaranteeing that the same IV will be reused for multiple messages. packet size 2000 -byte at average 5 Mbps bandwidth ( ( (2000 8)/(5 106)) 224)/3600=14 hours • PCMCIA cards that they tested reset the IV to 0 each time it’s re-initialized, and the IV is incremented by one for each packet.

Decryption Dictionaries • Some access points transmit broadcast messages in plaintext and encrypted form when access control is disabled. • The attacker can build a table of the keystream corresponding to each IV. v It does not matter if 40 bits or 104 bits shared secret key use as the attack centers on the IV collision.

Message Modification v The WEP checksum is a linear function of the message. • may be chosen arbitrarily bye the attacker • A (B) : <IV, C> • (A) B : <IV, C’> • C’= C < , c( )> = RC 4(IV, k) <M, c(M)> < , c( )> = RC 4(IV, k) <M , c(M) c( )> = RC 4(IV, k) <M , c(M )> = RC 4(IV, k) <M’, c(M’)> M’=M

Message Injection v It is possible to reuse old IV values without triggering any alarms at the receiver. • That is, if attacker ever learns the complete plaintext P of any given ciphertext packet C, he can recover keystream used to encrypt the packet. P C = P (P RC 4(IV, k))= RC 4(IV, k) (A) B : <IV, C’> where C’= <M’, c(M’) > RC 4(IV, k)
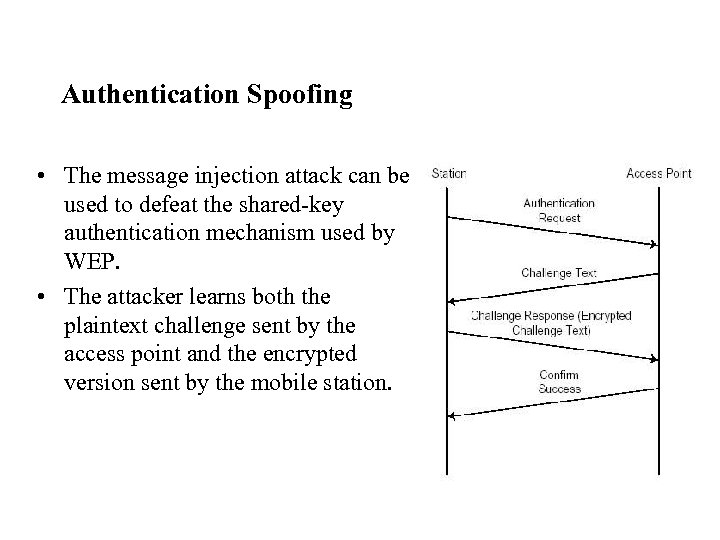
Authentication Spoofing • The message injection attack can be used to defeat the shared-key authentication mechanism used by WEP. • The attacker learns both the plaintext challenge sent by the access point and the encrypted version sent by the mobile station.
dfac7186965fdef53893daa1f1129f55.ppt