cfbd373dc96a3f39cdb745474f491d6e.ppt
- Количество слайдов: 31

ASP. NET Web Application Security Hannes Preishuber ppedv AG Hannes. P@ppedv. de

Classic rules u Passwords Ø encrypted Ø Min. Ø u length & case sensitive & unusual Dictionary attack Sniffers Ø Men Ø Trojan Ø Network u Not limited to Microsoft!

ASP. NET Features u Authentication Ø IIS, ASP. NET Ø u Authorization Ø u Access to Directories, Files Role-Based Security Ø u ASP. NET: Forms, Windows, Passport, Default, and Custom if User. Is. In. Role("Admin") Impersonation Ø Code and User

Authentication u ASP. NET is an ISAPI extension Ø u Only receives requests for mapped content Windows Authentication (via IIS) Basic, Digest, NTLM, Kerberos, Certificate Support Ø Leverages platform authentication Ø u Forms-based (Cookie) Authentication Ø u u Application credential verification Supports Microsoft® Passport Authentication Custom Authentication

Forms-Based Authentication u Easy to implement Ø u Steps Ø Ø Ø u ASP. NET provides redirection Configure IIS to allow anonymous users (typically) Configure ASP. NET cookie authentication Write your login page Secures not all Ø Only Files with named extensions
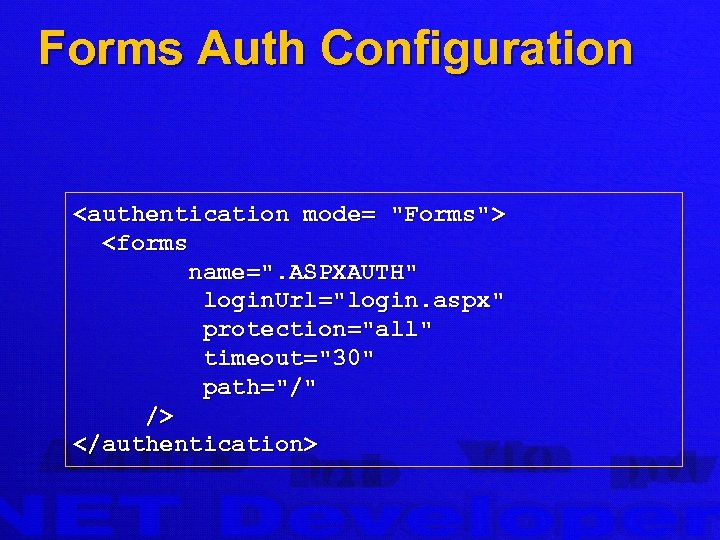
Forms Auth Configuration <authentication mode= "Forms"> <forms name=". ASPXAUTH" login. Url="login. aspx" protection="all" timeout="30" path="/" /> </authentication>

Risk u Authentication Data Ø Username Ø Shown in web pages Ø Password u Authentication Flow Ø HTTP Ø is clear text use SSL Ø ASP. NET Ø to Database is clear text Store hashed passwords

Show

Risk Cookieless u u Sends Session ID in Query String Web. Config Ø u Session lives 20 minutes Ø u From last activity Attach on Session Ø Ø u <session. State cookieless=“true“ public terminal Sniffer Also for HTTP Headers and Cookies

Show

Config Topics u Machine. config Ø System. Web. Http. Forbidden. Handler Ø <process. Model Ø u user. Name=“machine" Web. Config <custom. Errors mode="On" /> Ø Encrypt Connection Strings Ø u Http. Only Ø Client side script

Show

SQL Injection u u How Web pages works? INPUT rendered from Textbox Web Control Query String Use values concat a SQL command Ø Search knowledge base Ø Paged results Ø Look for specific record Ø User credentials

What really exists! u DON’T LIKE Ø More comfort for the user string sql = "select * from KB where content like '" + search. Text + "' u Hacker types: % string sql = "select * from KB where content like '%' u User authentication!
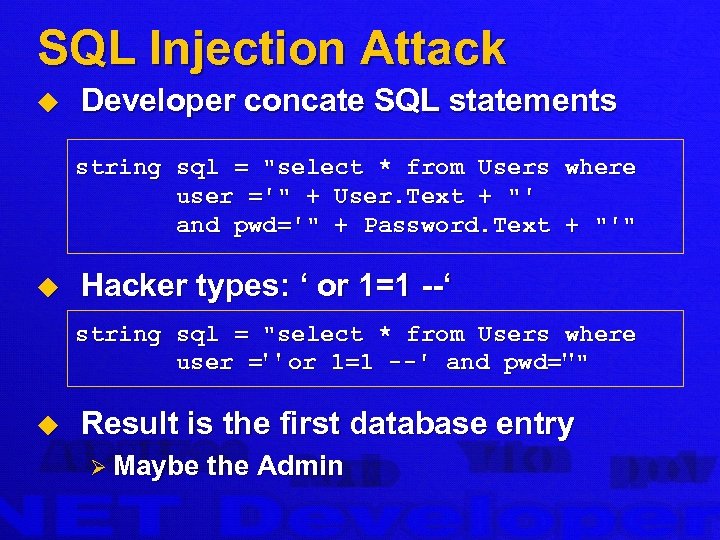
SQL Injection Attack u Developer concate SQL statements string sql = "select * from Users where user ='" + User. Text + "' and pwd='" + Password. Text + "'" u Hacker types: ‘ or 1=1 --‘ string sql = "select * from Users where user =' ' or 1=1 --' and pwd=''" u Result is the first database entry Ø Maybe the Admin

Show
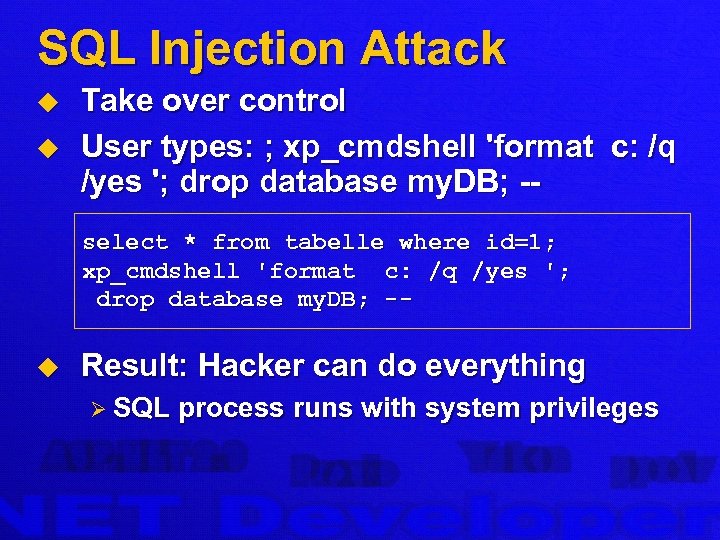
SQL Injection Attack u u Take over control User types: ; xp_cmdshell 'format c: /q /yes '; drop database my. DB; -select * from tabelle where id=1; xp_cmdshell 'format c: /q /yes '; drop database my. DB; -- u Result: Hacker can do everything Ø SQL process runs with system privileges

SQL Injection Attack u Never use “sa” Ø Default blank password Ø Hacker knows a lot about sa Ø Trusted Security Ø Application user Ø u Only with needed access rights Storing Connection Strings Ø Web. Config Ø Hashed not clear text Ø error case source code is often visible

Best Tip u Use parameterized Select sql = "select * from Users where user = @user and pwd = @pwd"; Sql. Command cmd = new Sql. Command(sql, con); cmd. Parameters. Add("@user", User. Text); cmd. Parameters. Add("@pwd", Password. Text); u u Use Stored Procedures Cookie & URL Injection

Show

Cross site-scripting u u u User Input is stored in Database content is presented Injection of Ø HTML code Ø JScript code u A different denial of service <script> u Redirect the user to dialer page <script language=Jscript> window. navigate('net. htm'); </script>
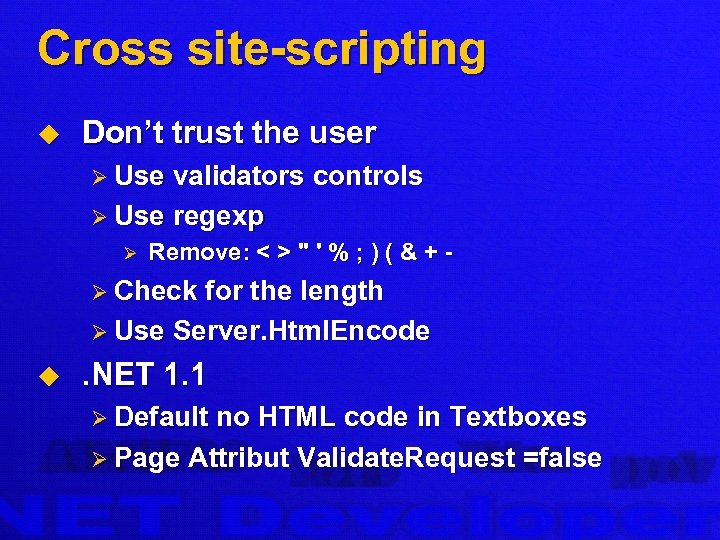
Cross site-scripting u Don’t trust the user Ø Use validators controls Ø Use regexp Ø Remove: < > " ' % ; ) ( & + - Ø Check for the length Ø Use Server. Html. Encode u . NET 1. 1 Ø Default no HTML code in Textboxes Ø Page Attribut Validate. Request =false
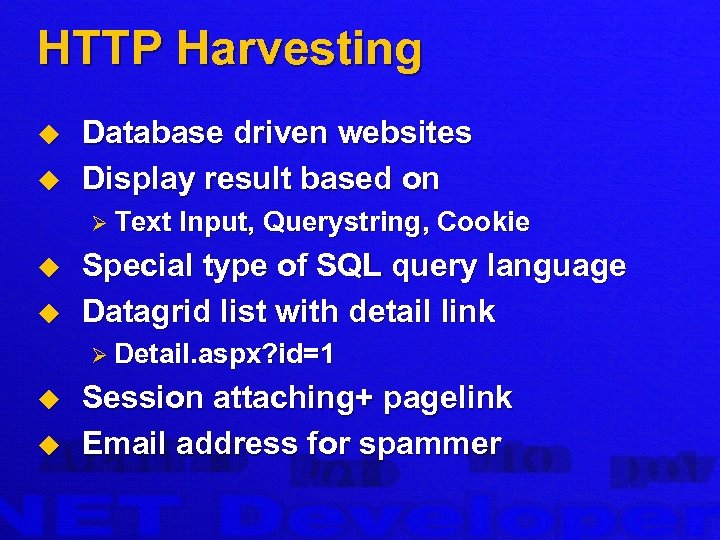
HTTP Harvesting u u Database driven websites Display result based on Ø Text u u Input, Querystring, Cookie Special type of SQL query language Datagrid list with detail link Ø Detail. aspx? id=1 u u Session attaching+ pagelink Email address for spammer

Prevent HTTP harvesting u u Encrypt querystrings Combine user input with textboxes Use Jscript to write the data Draw the data Ø System. drawing u u Monitor the web usage Third party review

Canonicalization u Character Sets URL, Querystring, Filename Ø %20=“ u u “ IP Address as decimal Compare values Ø HTMLDecode

Much more…

Architecture u Operation System Ø Reduce Ø Never use Admin Rights Ø Switch u of unused services and ports Web Farm Ø Use Ø Ø Ø IP u the rights of accounts ipsec to encrypt traffic Between SQL Server and Web Application Session Management restrictions Change common used things Ø Directories, users, path

Tools u Microsoft Baseline Security Analyzer 1. 2 Ø Scan network or local Ø Scan installed updates Ø Scan well-known issues

How to be secure u u Don't believe in 100 % Evaluate the risk Ø Risk of attack Ø Damage result u Train everybody Ø Architects, u Developer, User, Administrator Review Ø Code and user interface

Security begins in mind © 2004 ppedv AG. All rights reserved.

Hinweise u Abo Angebot ASP. NET professional Ø 24 u Euro statt 36 ( hier und jetzt) ASP-Konferenz Ø 14. -15 u Juni Burghausen Dev. Train Camp Ø 5 Tage – 50 h -. NET 29. 03 -02. 04 Burghausen u Dev. Train. de Ø Kostenfreies Community Portal
cfbd373dc96a3f39cdb745474f491d6e.ppt