2bbe78b7ff4204377b27e002819745f7.ppt
- Количество слайдов: 43

ASA Remote Access VPN Technologies: SSLVPN Web. VPN IPSec. VPN http: //www. cisco. com/go/security http: //www. cisco. com/security Tim Ryan – tiryan@cisco. com Security Consulting SE CCIE, CISSP Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 1

Cisco ASA 5500 Series Convergence of Robust, Market-Proven Technologies Adaptive Threat Defense, Secure Connectivity Firewall Technology Cisco PIX App Inspection, Use Enforcement, Web Control Application Security IPS Technology Cisco IPS Malware/Content Defense, Anomaly Detection IPS & Content Security Services Content Security Trend Micro Traffic/Admission Control, Proactive Response Network Containment and Control VPN Technology Cisco VPN 3000 Secure Connectivity IPSec & SSL VPN Network Intelligence Cisco Network Services Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 2
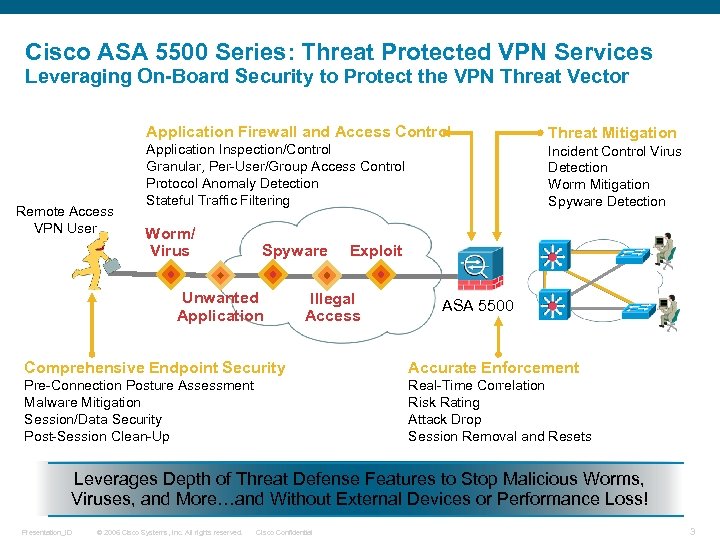
Cisco ASA 5500 Series: Threat Protected VPN Services Leveraging On-Board Security to Protect the VPN Threat Vector Application Firewall and Access Control Remote Access VPN User Threat Mitigation Application Inspection/Control Granular, Per-User/Group Access Control Protocol Anomaly Detection Stateful Traffic Filtering Incident Control Virus Detection Worm Mitigation Spyware Detection Worm/ Virus Spyware Unwanted Application Exploit Illegal Access ASA 5500 Comprehensive Endpoint Security Accurate Enforcement Pre-Connection Posture Assessment Malware Mitigation Session/Data Security Post-Session Clean-Up Real-Time Correlation Risk Rating Attack Drop Session Removal and Resets Leverages Depth of Threat Defense Features to Stop Malicious Worms, Viruses, and More…and Without External Devices or Performance Loss! Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 3
VPN Technologies for Remote Clients Encrypted Connection Protocols: SSL tunnel uses the SSL protocol with RC 4 or AES to encrypt data IPSec tunnel uses the IPSec protocol with DES, 3 DES or AES to encrypt data Encrypted Client options supported by the ASA Any. Connect VPN Client is an SSL based VPN client that is installed on a desktop and can tunnel any traffic (aka SVC) WEB VPN (aka Clientless VPN) uses the browser as the Client with the ASA acting as a proxy. It can tunnel http, https traffic and a limited number of other supported protocols such as CIFS, OWA, RDP, VNC, SSH, Telnet via plugins Cisco VPN Client is an IPSec client that can tunnel any traffic except for multicast. Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 4
ASA VPN Configuration The Any. Connect Configuration document at the url below is an excellent starting place for any ASA VPN configuration. http: //www. cisco. com/en/US/partner/products/ps 6120/products_configuration_ex ample 09186 a 00808 efbd 2. shtml Configure Step 1. Configure a Self-Issued Certificate Step 2. Upload and Identify the SSL VPN Client Image Step 3. Enable Anyconnect Access Step 4. Create a new Group Policy Configure Access List Bypass for VPN Connections Step 6. Create a Connection Profile and Tunnel Group for the Any. Connect Client Connections Step 7. Configure NAT Exemption for Any. Connect Clients Step 8. Add Users to the Local Database Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 5
VPN Connection Flow Summary During Client connection time Group Policy settings takes precedence over Connection Profile settings. If Connection Profile has a setting and Group Policy is set to "inherit" then Connection Profile settings are used. ANYCONNECT CLIENT Connection Profile (called tunnel group at CLI) = SSLClient. Profile Uses Group Policy = Group. Policy 1 Alias = SSLClient IPSEC CLIENT Connection Profile (called tunnel group at CLI) = IPSec. VPN Uses Group Policy = IPSec. Client IPSec Client settings: Groupname=IPSec. VPN , pre-shared key=cisco 123 WEBVPN - BROWSER CLIENT Connection Profile Clientless SSL VPN Access (tunnel group in. CLI) = Web. VPN Uses Group Policy = Web. Group Alias = Web. VPN Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 6
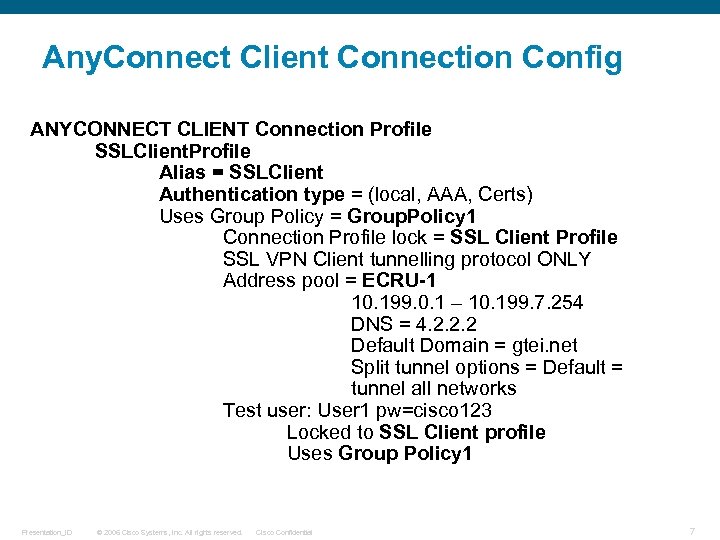
Any. Connect Client Connection Config ANYCONNECT CLIENT Connection Profile SSLClient. Profile Alias = SSLClient Authentication type = (local, AAA, Certs) Uses Group Policy = Group. Policy 1 Connection Profile lock = SSL Client Profile SSL VPN Client tunnelling protocol ONLY Address pool = ECRU-1 10. 199. 0. 1 – 10. 199. 7. 254 DNS = 4. 2. 2. 2 Default Domain = gtei. net Split tunnel options = Default = tunnel all networks Test user: User 1 pw=cisco 123 Locked to SSL Client profile Uses Group Policy 1 Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 7

Client-Based SSL VPN (Any. Connect/ SSL VPN Client) Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 25
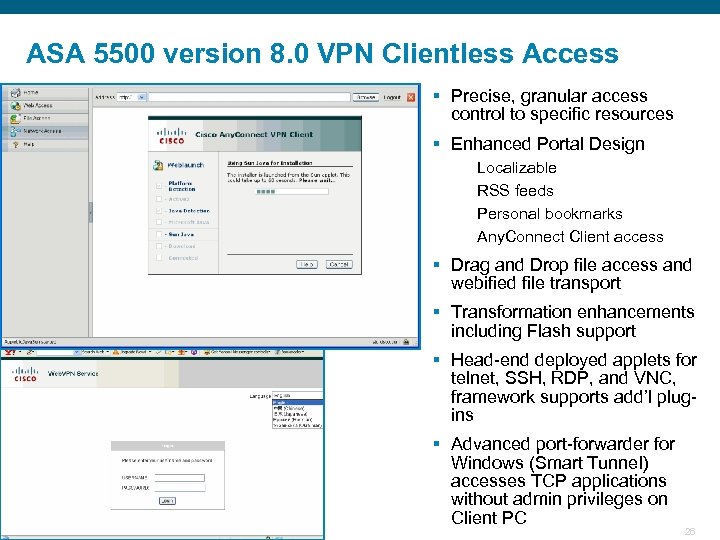
ASA 5500 version 8. 0 VPN Clientless Access § Precise, granular access control to specific resources § Enhanced Portal Design Localizable RSS feeds Personal bookmarks Any. Connect Client access § Drag and Drop file access and webified file transport § Transformation enhancements including Flash support § Head-end deployed applets for telnet, SSH, RDP, and VNC, framework supports add’l plugins § Advanced port-forwarder for Windows (Smart Tunnel) accesses TCP applications without admin privileges on Client PC Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 26
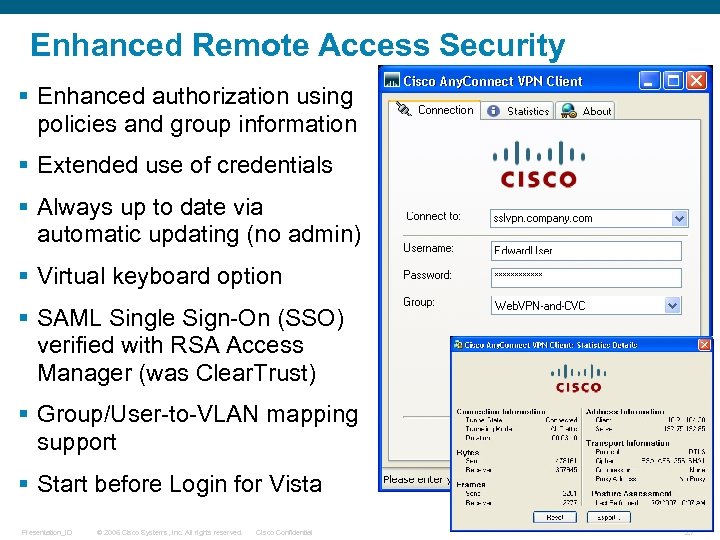
Enhanced Remote Access Security § Enhanced authorization using policies and group information § Extended use of credentials § Always up to date via automatic updating (no admin) § Virtual keyboard option § SAML Single Sign-On (SSO) verified with RSA Access Manager (was Clear. Trust) § Group/User-to-VLAN mapping support § Start before Login for Vista Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 27
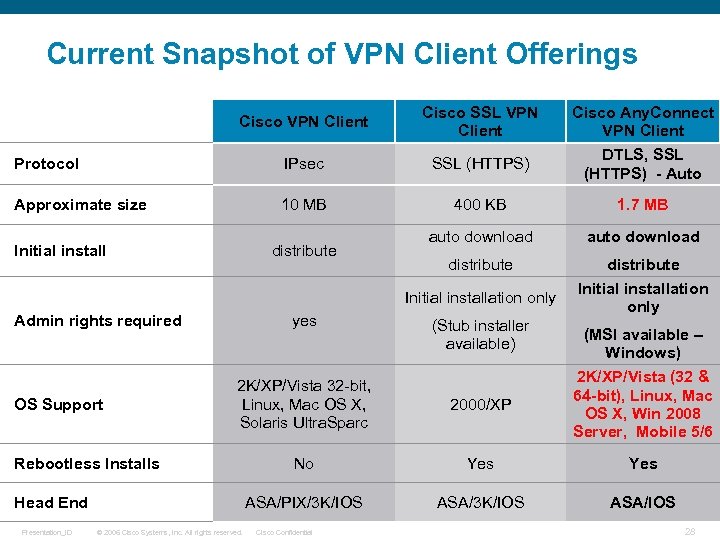
Current Snapshot of VPN Client Offerings Cisco VPN Client Cisco SSL VPN Client Protocol IPsec SSL (HTTPS) Approximate size 10 MB 400 KB 1. 7 MB auto download distribute Initial installation only Initial install distribute Initial installation only yes Admin rights required (MSI available – Windows) 2 K/XP/Vista (32 & 64 -bit), Linux, Mac OS X, Win 2008 Server, Mobile 5/6 2 K/XP/Vista 32 -bit, Linux, Mac OS X, Solaris Ultra. Sparc 2000/XP No Yes ASA/PIX/3 K/IOS OS Support ASA/3 K/IOS ASA/IOS Rebootless Installs Head End Presentation_ID (Stub installer available) Cisco Any. Connect VPN Client DTLS, SSL (HTTPS) - Auto © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 28
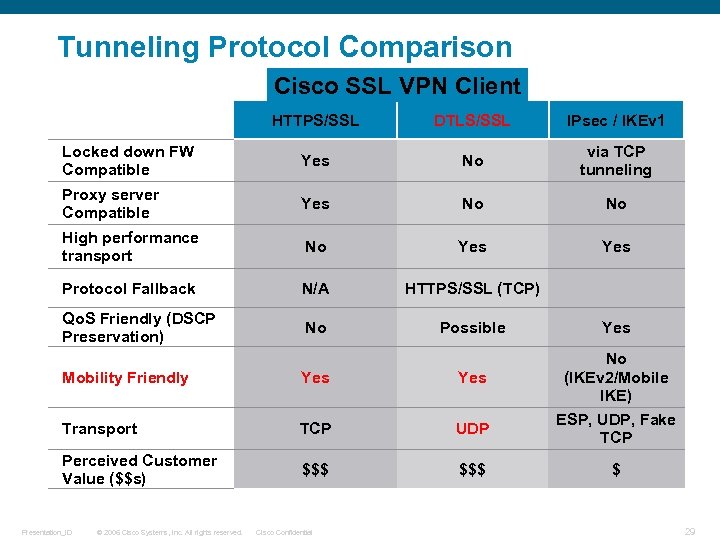
Tunneling Protocol Comparison Cisco SSL VPN Client HTTPS/SSL DTLS/SSL IPsec / IKEv 1 Locked down FW Compatible Yes No via TCP tunneling Proxy server Compatible Yes No No High performance transport No Yes Protocol Fallback N/A HTTPS/SSL (TCP) Qo. S Friendly (DSCP Preservation) No Possible Mobility Friendly Yes Transport TCP UDP Perceived Customer Value ($$s) $$$ Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential Yes No (IKEv 2/Mobile IKE) ESP, UDP, Fake TCP $ 29
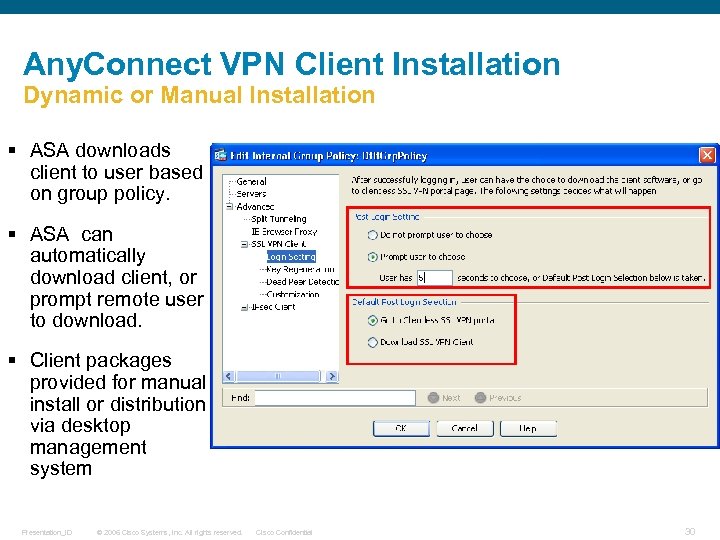
Any. Connect VPN Client Installation Dynamic or Manual Installation § ASA downloads client to user based on group policy. § ASA can automatically download client, or prompt remote user to download. § Client packages provided for manual install or distribution via desktop management system Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 30
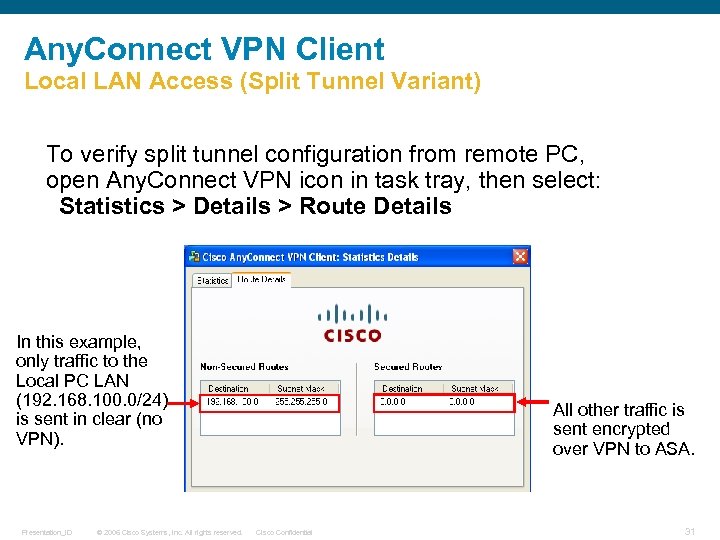
Any. Connect VPN Client Local LAN Access (Split Tunnel Variant) To verify split tunnel configuration from remote PC, open Any. Connect VPN icon in task tray, then select: Statistics > Details > Route Details In this example, only traffic to the Local PC LAN (192. 168. 100. 0/24) is sent in clear (no VPN). Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Text All other traffic is sent encrypted over VPN to ASA. Cisco Confidential 31
Any. Connect VPN Client Datagram Transport Layer Security (DTLS) Defined in RFC 4347 Implemented as part of the standard Open. SSL package Limitations of TLS (HTTPS/SSL) with SSL VPN tunnels TLS is used to tunnel TCP/IP over TCP/443 TCP requires retransmission of lost packets Both application and TLS wind up retransmitting when packet loss is detected. DTLS solves the TCP over TCP problem DTLS replaces underlying transport TCP/443 with UDP/443 DTLS uses TLS to negotiate and establish DTLS connection (control messages and key exchange) Datagrams only are transmitted over DTLS Other benefits Low latency for real time applications DTLS is enabled by default; dynamically negotiated at connect time. DTLS is optional and will automatically fallback to TLS (HTTPS) Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 32

Clientless Web. VPN Features Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 33
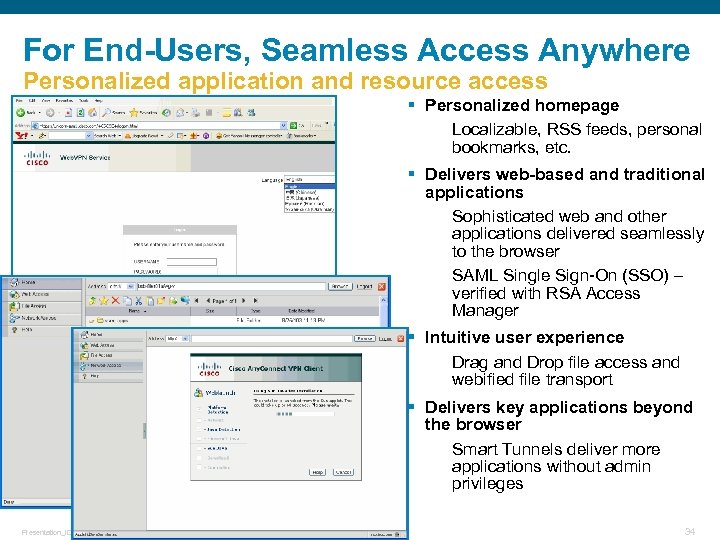
For End-Users, Seamless Access Anywhere Personalized application and resource access § Personalized homepage Localizable, RSS feeds, personal bookmarks, etc. § Delivers web-based and traditional applications Sophisticated web and other applications delivered seamlessly to the browser SAML Single Sign-On (SSO) – verified with RSA Access Manager § Intuitive user experience Drag and Drop file access and webified file transport § Delivers key applications beyond the browser Smart Tunnels deliver more applications without admin privileges Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 34
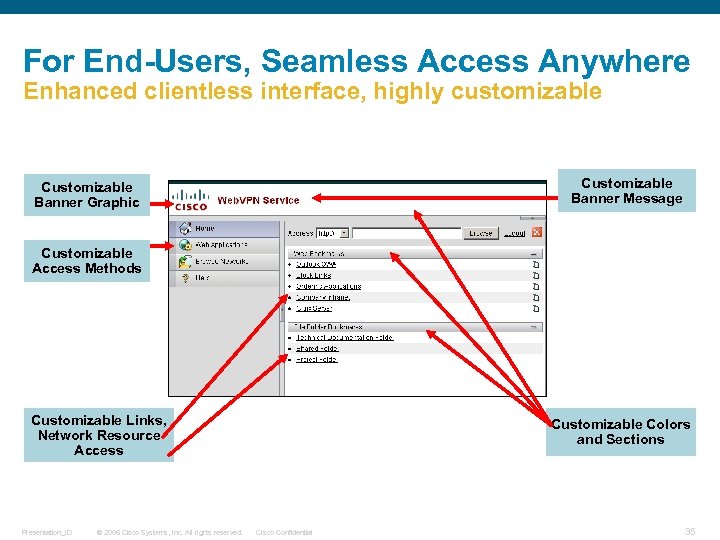
For End-Users, Seamless Access Anywhere Enhanced clientless interface, highly customizable Customizable Banner Message Customizable Banner Graphic Customizable Access Methods Customizable Links, Network Resource Access Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Customizable Colors and Sections Cisco Confidential 35
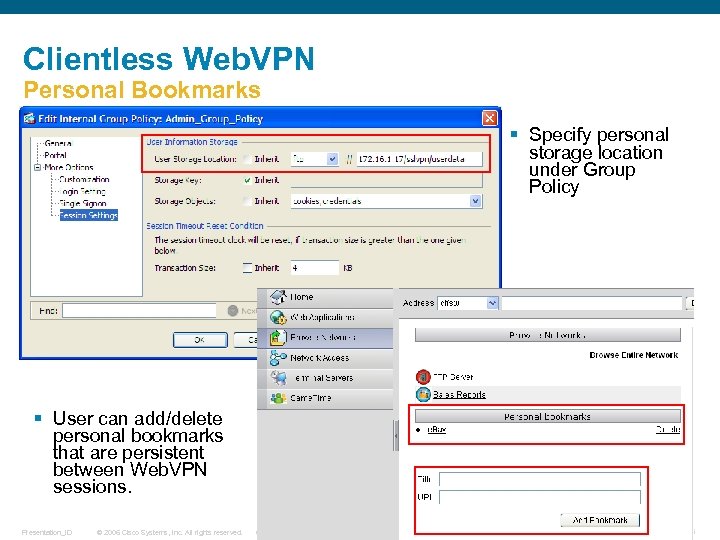
Clientless Web. VPN Personal Bookmarks § Specify personal storage location under Group Policy § User can add/delete personal bookmarks that are persistent between Web. VPN sessions. Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 36
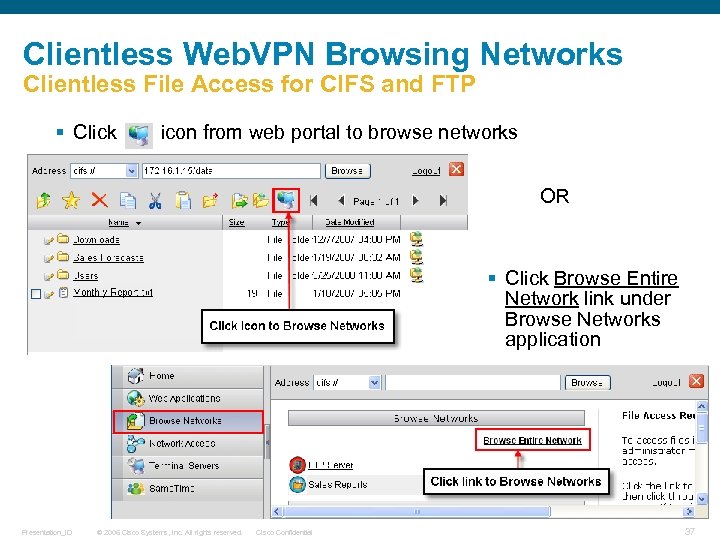
Clientless Web. VPN Browsing Networks Clientless File Access for CIFS and FTP § Click icon from web portal to browse networks OR § Click Browse Entire Network link under Browse Networks application Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 37
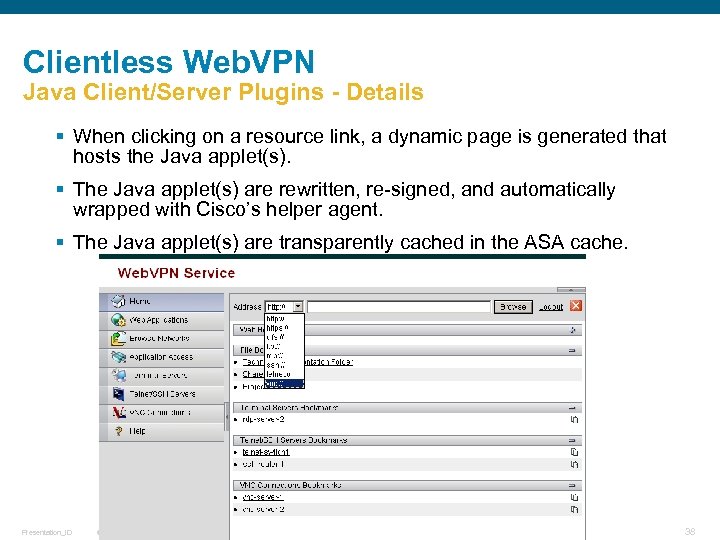
Clientless Web. VPN Java Client/Server Plugins - Details § When clicking on a resource link, a dynamic page is generated that hosts the Java applet(s). § The Java applet(s) are rewritten, re-signed, and automatically wrapped with Cisco’s helper agent. § The Java applet(s) are transparently cached in the ASA cache. Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 38
Clientless Web. VPN Plugins RDP, VNC, Sametime, SSH, Telnet, Post § Remote Desktop Plugin for Windows Terminal Services Native Windows support using Active. X or Proper. RDP client using Java § Virtual Network Computing (VNC) remote server access based on Tight. VNC § SSH/Telnet – Combined open source plugin provides either SSHv 1 or Telnet access to manage devices and servers § Lotus Sametime – Secure instant messaging application from IBM § POST plugin – Provides Portal Homepage with optional SSO Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 39
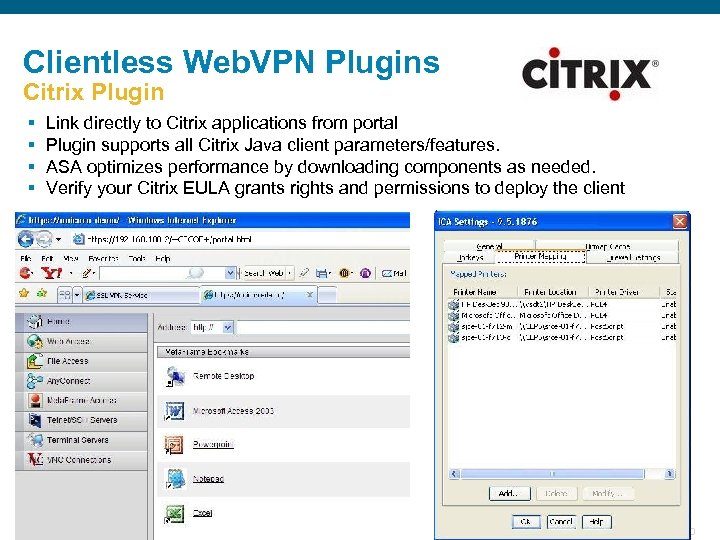
Clientless Web. VPN Plugins Citrix Plugin § § Link directly to Citrix applications from portal Plugin supports all Citrix Java client parameters/features. ASA optimizes performance by downloading components as needed. Verify your Citrix EULA grants rights and permissions to deploy the client Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 40
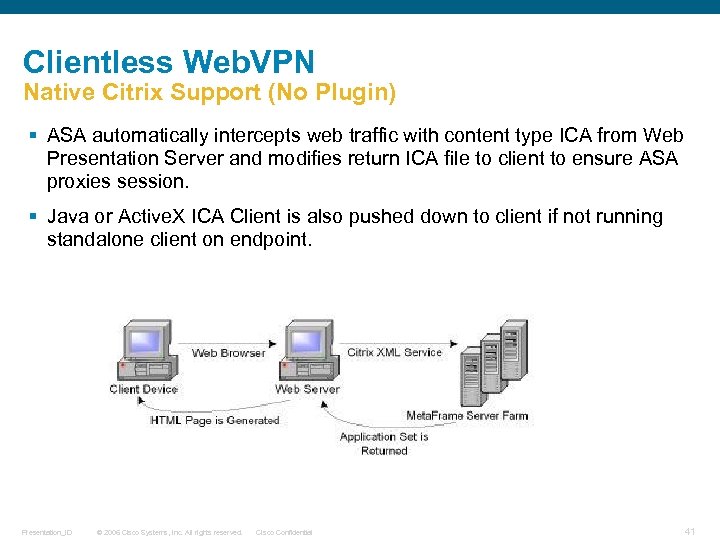
Clientless Web. VPN Native Citrix Support (No Plugin) § ASA automatically intercepts web traffic with content type ICA from Web Presentation Server and modifies return ICA file to client to ensure ASA proxies session. § Java or Active. X ICA Client is also pushed down to client if not running standalone client on endpoint. Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 41
Clientless Web. VPN Smart Tunnels § Smart Tunnels are application-level port forwarding § It is a connection between a Winsock 2, TCP-based application and the private site, using a clientless (browser-based) SSL VPN session. § You can specify client applications which you want to grant Smart Tunnel access including Telnet, SSH, RDP, VNC, Passive FTP, Outlook Express, Lotus Notes, Sametime, Citrix Program Neighborhood client, and Outlook via POP/SMTP/IMAP. § SSL VPN loads a stub into each process spawned by an authorized application, and intercepts socket calls to redirect via ASA. § This can be used where other methods such as Any. Connect or Port Forwarding cannot be used. § A browser with Active-X, Java or Java. Script support is required on 32 -bit OS’s only, such as Windows XP & 2 K Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 42
Clientless Web. VPN General Configuration Overview 1. Import Web Content (Optional) 2. Define Bookmarks and assign to Group Policies 3. Customize Login/Logout and Portal Pages and assign to Connection Profiles and Group Policies, respectively (Optional) 4. Import plugins and apply to bookmarks (Optional) 5. Define Smart Tunnels and enable in bookmarks or Group Policies (Optional) 6. Review and tune User/Group Policies as required. 7. Apply Cisco Secure Desktop, Endpoint Assessment, DAP, and enforcement policies (covered in later training sessions Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 43

Secure Session (aka Secure Desktop or Vault) Overview § Encrypts data and files associated with or downloaded during remote session into a secure desktop partition § Provides tasktray icon to signify a safe environment for remote user to work in. § Upon session termination, uses U. S. Department of Defense (Do. D) sanitation algorithm to remove the partition. § Typically used during clientless SSL VPN sessions--attempts to reduce the possibility that cookies, browser history, temporary files, and downloaded content remain after a remote user logs out, the session times out, or after an abrupt termination occurs. § Runs over Microsoft Windows Vista, Windows XP, and Windows 2000. § If Prelogin policy is configured to install Secure Session, but remote OS does not support Secure Session, then Cache Cleaner install attempted instead. Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 44
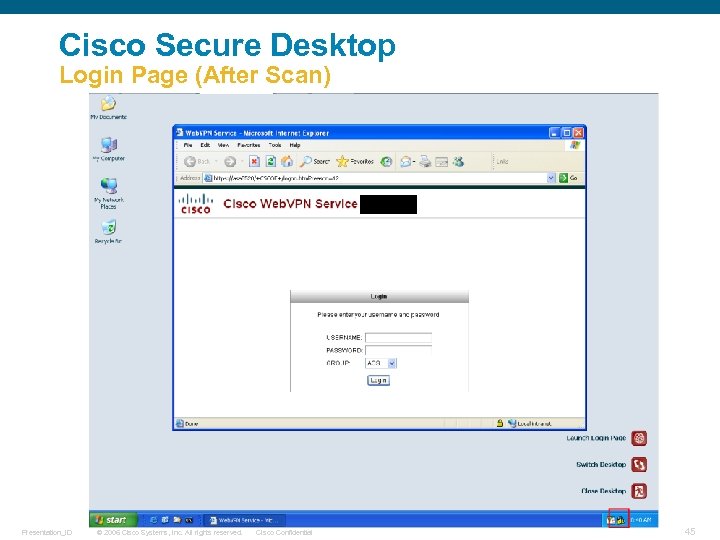
Cisco Secure Desktop Login Page (After Scan) Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 45

Policy Inheritance Overview Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 46
Policy Objects § Connection Profile / Tunnel Group ú Pre-login attributes (inc. AAA, login page for Clientless, cert handling) § Group Policy (Internal and External) ú Post-login attributes (inc. portal page, bookmarks, access policies) § User Policy (Internal and External) ú User-specific attributes § Dynamic Access Policy ú Dynamically created policies based on multiple inputs (Location, Directory attributes, PC attributes) § Internal versus External ú Internal attributes – locally defined on ASA ú External attributes – returned as values from queries to external servers (for example, RADIUS and LDAP) Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 47
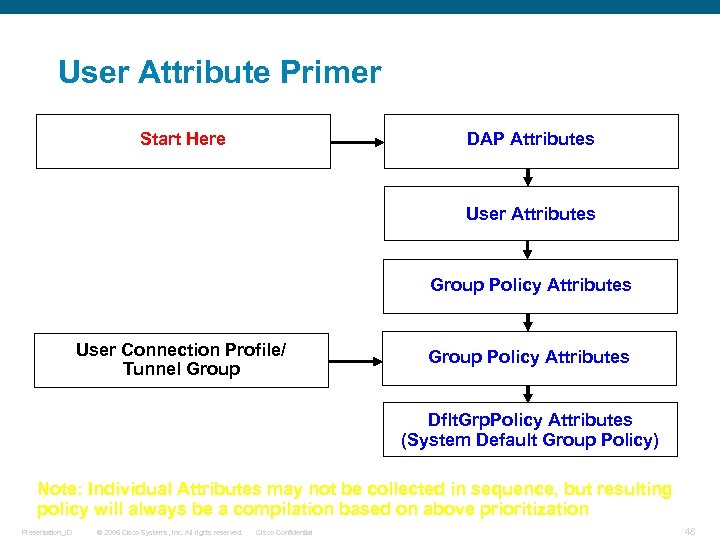
User Attribute Primer Start Here DAP Attributes User Attributes Group Policy Attributes User Connection Profile/ Tunnel Group Policy Attributes Dflt. Grp. Policy Attributes (System Default Group Policy) Note: Individual Attributes may not be collected in sequence, but resulting policy will always be a compilation based on above prioritization Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 48
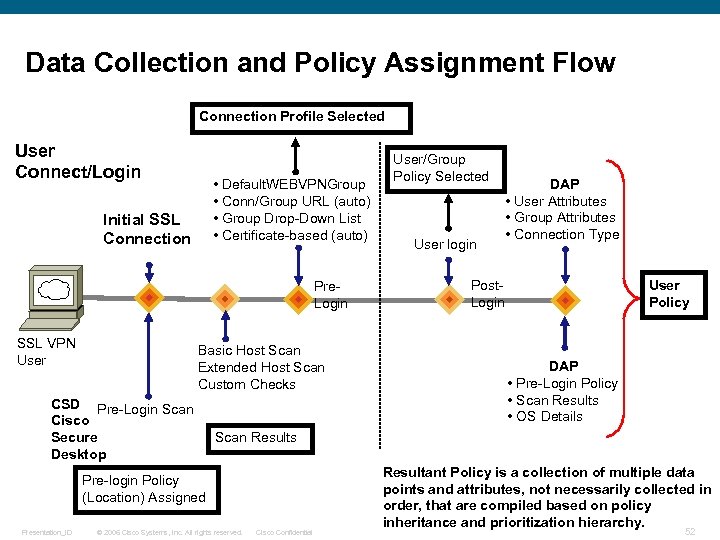
Data Collection and Policy Assignment Flow Connection Profile Selected User Connect/Login • Default. WEBVPNGroup • Conn/Group URL (auto) • Group Drop-Down List • Certificate-based (auto) Initial SSL Connection Pre. Login SSL VPN User Basic Host Scan Extended Host Scan Custom Checks CSD Pre-Login Scan Cisco Secure Desktop User login DAP • User Attributes • Group Attributes • Connection Type User Policy Post. Login DAP • Pre-Login Policy • Scan Results • OS Details Scan Results Pre-login Policy (Location) Assigned Presentation_ID User/Group Policy Selected © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential Resultant Policy is a collection of multiple data points and attributes, not necessarily collected in order, that are compiled based on policy inheritance and prioritization hierarchy. 52

ASA VPN Load Balancing Load balancing is supported on remote sessions initiated with the following: • Cisco Any. Connect VPN Client (Release 2. 0 and later) • Cisco VPN Client (Release 3. 0 and later) • Cisco VPN 3002 Hardware Client (Release 3. 5 or later) • Cisco PIX 501/506 E when acting as an Easy VPN client. Load balancing works with both IPSec clients and Web. VPN sessions. All other clients, including LAN-to-LAN connections, can connect to a security appliance on which load balancing is enabled, but they cannot participate in load balancing. You can configure the number of IPSec and Web. VPN sessions to allow, up to the maximum allowed by your configuration and license. With Release 7. 1(1), IPSec and Web. VPN sessions count or weigh equally in determining the load that each device in the cluster carries. If using Certificates you must enable redirection using a fully-qualified domain name in vpn load-balancing mode. Use the command “redirect-fqdn enable” in global configuration mode. This is disabled by default. http: //www. cisco. com/en/US/partner/docs/security/asa 81/config/gui de/vpnsysop. html 53 Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential
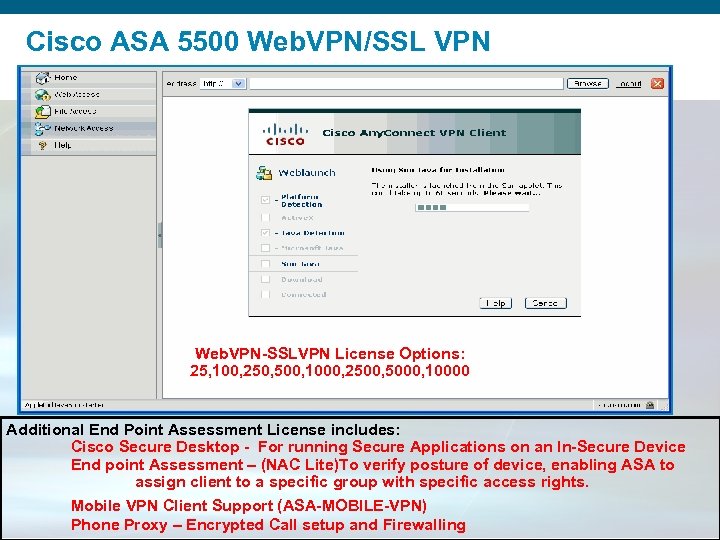
Cisco ASA 5500 Web. VPN/SSL VPN Web. VPN-SSLVPN License Options: 25, 100, 250, 500, 1000, 2500, 5000, 10000 Additional End Point Assessment License includes: Cisco Secure Desktop - For running Secure Applications on an In-Secure Device End point Assessment – (NAC Lite)To verify posture of device, enabling ASA to assign client to a specific group with specific access rights. Mobile VPN Client Support (ASA-MOBILE-VPN) Phone Proxy – Encrypted Call setup and Firewalling Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 54
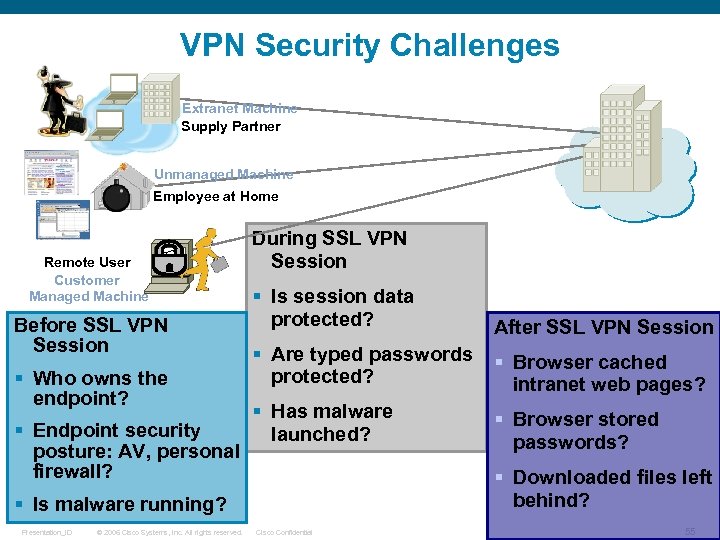
VPN Security Challenges Extranet Machine Supply Partner Unmanaged Machine Employee at Home Remote User Customer Managed Machine Before SSL VPN Session § Who owns the endpoint? § Endpoint security posture: AV, personal firewall? During SSL VPN Session § Is session data protected? After SSL VPN Session § Are typed passwords protected? § Browser cached intranet web pages? § Has malware launched? § Browser stored passwords? § Downloaded files left behind? § Is malware running? Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 55
Comprehensive End. Point Security § Cisco Secure Desktop (CSD) now supports hundreds of pre-defined products, New updated frequently in 8. 0! Anti-virus, anti-spyware, personal firewall, and more § Administrators can define custom checks including running processes § CSD posture policy presented visually to simplify configuration and troubleshooting Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 56

Cisco ASA 5500 Series Platforms and Modules Wide Range of Leading Solutions for Customers of All Sizes Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 57

Cisco ASA 5500 Series High-End Lineup Data Center Solutions New Cisco ASA 5540 Cisco ASA 5550 Cisco ASA 5580 -20 Internet Edge Campus Segmentation / Data Center Starting at $16, 995 Starting at $19, 995 Starting at $59, 995 with-8 GE Starting at $109, 995 With 8 GE 650 Mbps 325 Mbps 5000 / 2500 1. 2 Gbps 425 Mbps 5000 / 5000 5 Gbps 6. 5 Gbps 10, 000 / 10, 000 10 Gbps 14 Gbps 20 Gbps 10, 000 / 10, 000 400, 000 25, 000 500, 000 4 GE + 1 FE 8 GE + 1 FE 200 A/A and A/S 650, 000 36, 000 600, 000 8 GE + 1 FE 250 A/A and A/S 1, 000 90, 000 2, 750, 000 2 Mgmt 24 GE / 12 10 GE 250 A/A and A/S 2, 000 150, 000 5, 500, 000 2 Mgmt 24 GE / 12 10 GE 250 A/A and A/S Target Market List Price Performance Max Firewall (Real-world HTTP) Max Firewall (1400 byte) Max Firewall (Jumbo frames) Max IPSec VPN Max IPSec/SSL VPN Peers Cisco ASA 5580 -40 Data Center Platform Capabilities Max Firewall Conns Max Conns/Second Packets/Second (64 byte) Base I/O Max I/O VLANs Supported HA Supported Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 58
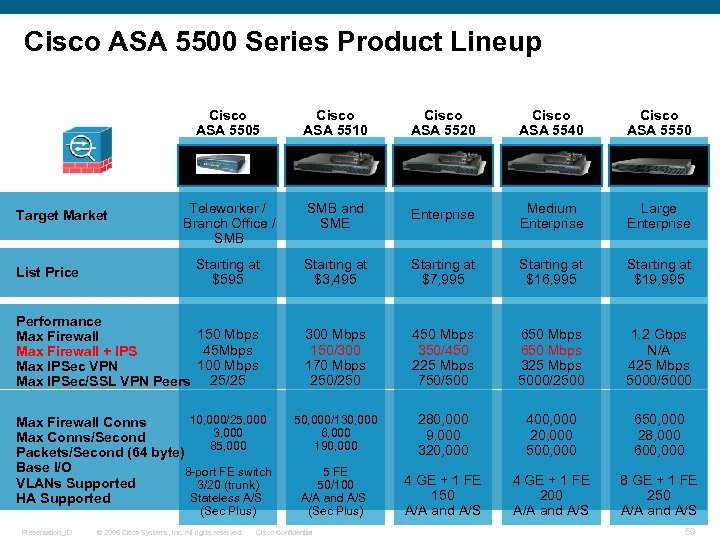
Cisco ASA 5500 Series Product Lineup Cisco ASA 5505 Cisco ASA 5510 Cisco ASA 5520 Cisco ASA 5540 Cisco ASA 5550 Teleworker / Branch Office / SMB and SME Enterprise Medium Enterprise Large Enterprise Starting at $595 Starting at $3, 495 Starting at $7, 995 Starting at $16, 995 Starting at $19, 995 Performance 150 Mbps Max Firewall 45 Mbps Max Firewall + IPS 100 Mbps Max IPSec VPN Max IPSec/SSL VPN Peers 25/25 300 Mbps 150/300 170 Mbps 250/250 450 Mbps 350/450 225 Mbps 750/500 650 Mbps 325 Mbps 5000/2500 1. 2 Gbps N/A 425 Mbps 5000/5000 50, 000/130, 000 6, 000 190, 000 280, 000 9, 000 320, 000 400, 000 20, 000 500, 000 650, 000 28, 000 600, 000 5 FE 50/100 A/A and A/S (Sec Plus) 4 GE + 1 FE 150 A/A and A/S 4 GE + 1 FE 200 A/A and A/S 8 GE + 1 FE 250 A/A and A/S Target Market List Price 10, 000/25, 000 Max Firewall Conns 3, 000 Max Conns/Second 85, 000 Packets/Second (64 byte) Base I/O 8 -port FE switch VLANs Supported 3/20 (trunk) Stateless A/S HA Supported (Sec Plus) Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 59
Wide Range of Management Solutions Provide Scalable, Cost Optimized Options for Businesses Integrated Remote Management Capabilities Within ASA § Configuration: Auto Update, SSH, Telnet, XML/HTTPS, and ASDM § Real-time monitoring: Syslog, SNMP, HTTPS, and ASDM § Software updates: Auto Update, SCP, HTTPS, and TFTP Cisco Security Manager (CS-Manager) § Scalable management solution for wide range of Cisco security solutions including routers, switches, blades, and appliances § Delivers centralized management of firewall, VPN, IPS/IDS, networking, and other services via flexible user interface § Supports device grouping for simplified policy maintenance § Provides role-based admin access and workflow capabilities § Available on Windows (Linux version coming) Cisco Monitoring and Response Solution (CS-MARS) § Family of high performance appliances designed to provide automated analysis of security event information to help identify, manage, and counter attacks § Supports getting events from wide range of Cisco and 3 rd party solutions—and also analyzes Net. Flow for additional intelligence § Offers event correlation, visualization, rules engine, and reporting Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 60
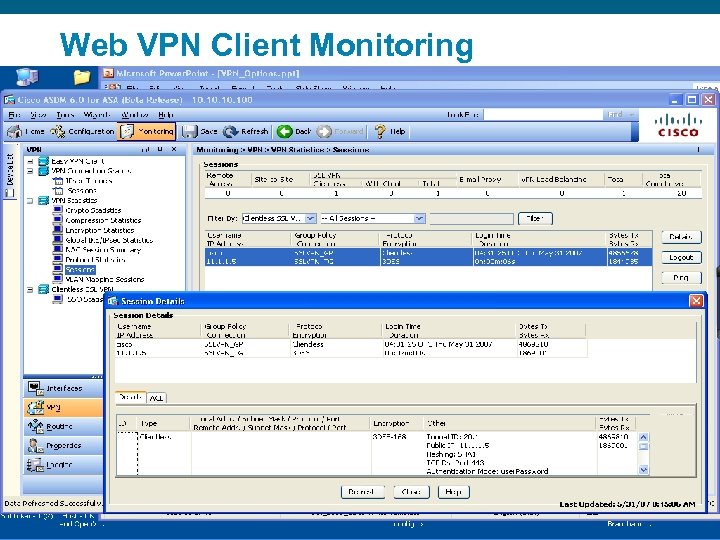
Web VPN Client Monitoring Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 61

Cisco ASA Adaptive Security Appliances Industry Certifications and Evaluations § Common Criteria New Completed: EAL 4, v 7. 0. 6—ASA 5510/20/40 (FW) Completed: EAL 2, v 6. 0—ASA SSM-10/20 (IPS) In process: EAL 4+, v 7. 2. 2—ASA Family (FW) In process: EAL 4, v 7. 2. 2—ASA Family (VPN) § FIPS 140 New Completed: Level 2, v 7. 0. 4—ASA Family Completed: Level 2, v 7. 2. 2 In process: Level 2, v 8. 0. 2 § ICSA Firewall 4. 1, Corporate Category Completed: v 7. 2. 2—ASA Family § ICSA IPSec 1. 0 D Completed: v 7. 0. 4—ASA Family § ICSA Anti-Virus Gateway Completed: v 7. 1—ASA Family § NEBS Level 3 Completed: ASA 5510, 5520, and 5540 Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 66

Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 67
2bbe78b7ff4204377b27e002819745f7.ppt