5d17d15b8715dae13c20497fb65f0805.ppt
- Количество слайдов: 21
 ARSA: An Attack-Resilient Security Architecture for Multi-hop Wireless Mesh Networks IEEE Journal on Selected Areas in Communications, 2006 Ki-Woong Park Computer Engineering Research Laboratory Korea Advanced Institute Science & Technology Oct 18, 2007
ARSA: An Attack-Resilient Security Architecture for Multi-hop Wireless Mesh Networks IEEE Journal on Selected Areas in Communications, 2006 Ki-Woong Park Computer Engineering Research Laboratory Korea Advanced Institute Science & Technology Oct 18, 2007
 Prologue v Wireless Mesh Network at KAIST Wi. Mesh Router § Low deployment costs § Self-Configuration, Self-maintenance § Scalability, Robustness In this paper, § Security Architecture • Authentication, Key Agreement • Attack-Resilient Security Protocol 2/20 COMPANY LOGO
Prologue v Wireless Mesh Network at KAIST Wi. Mesh Router § Low deployment costs § Self-Configuration, Self-maintenance § Scalability, Robustness In this paper, § Security Architecture • Authentication, Key Agreement • Attack-Resilient Security Protocol 2/20 COMPANY LOGO
 Contents 1 Introduction to Wireless Mesh Network 2 Problem to solve 3 Authentication and Key Agreement 4 Security Enhancement 5 Discussion § Performance Evaluation 3/20 COMPANY LOGO
Contents 1 Introduction to Wireless Mesh Network 2 Problem to solve 3 Authentication and Key Agreement 4 Security Enhancement 5 Discussion § Performance Evaluation 3/20 COMPANY LOGO
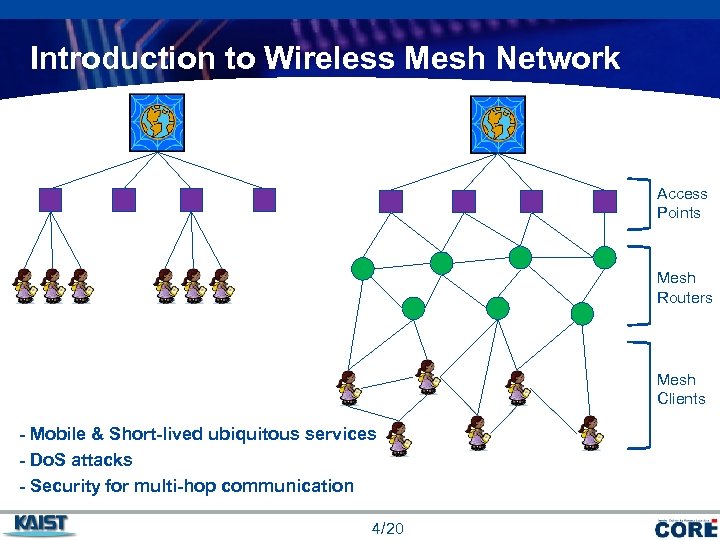 Introduction to Wireless Mesh Network Access Points Mesh Routers Mesh Clients - Mobile & Short-lived ubiquitous services - Do. S attacks - Security for multi-hop communication 4/20 COMPANY LOGO
Introduction to Wireless Mesh Network Access Points Mesh Routers Mesh Clients - Mobile & Short-lived ubiquitous services - Do. S attacks - Security for multi-hop communication 4/20 COMPANY LOGO
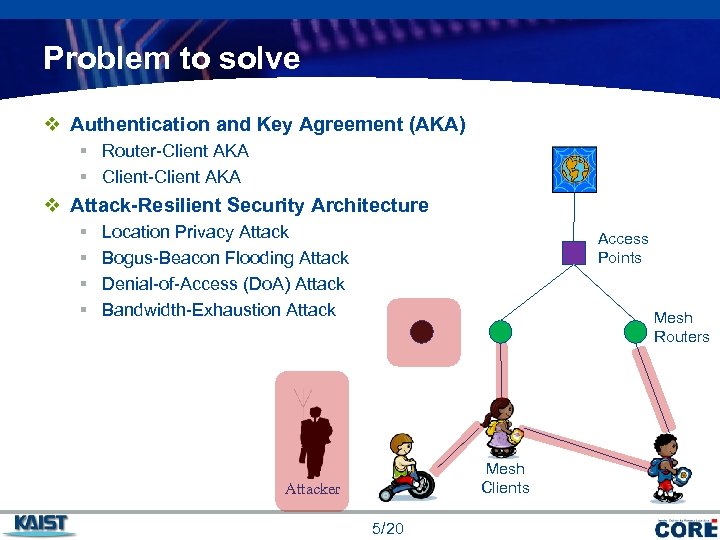 Problem to solve v Authentication and Key Agreement (AKA) § Router-Client AKA § Client-Client AKA v Attack-Resilient Security Architecture § § Location Privacy Attack Bogus-Beacon Flooding Attack Denial-of-Access (Do. A) Attack Bandwidth-Exhaustion Attack Access Points Mesh Routers Mesh Clients Attacker 5/20 COMPANY LOGO
Problem to solve v Authentication and Key Agreement (AKA) § Router-Client AKA § Client-Client AKA v Attack-Resilient Security Architecture § § Location Privacy Attack Bogus-Beacon Flooding Attack Denial-of-Access (Do. A) Attack Bandwidth-Exhaustion Attack Access Points Mesh Routers Mesh Clients Attacker 5/20 COMPANY LOGO
 Preliminaries v Cryptographic foundation of ARSA § Identity-Based Cryptography • Eliminates the need for public-key distribution Publicly known identity information Public Key : Cyclic additive group of large prime order q : Cyclic multiplicative group of large prime order q 6/20 COMPANY LOGO
Preliminaries v Cryptographic foundation of ARSA § Identity-Based Cryptography • Eliminates the need for public-key distribution Publicly known identity information Public Key : Cyclic additive group of large prime order q : Cyclic multiplicative group of large prime order q 6/20 COMPANY LOGO
 System Model and Notation (1/3) v Credit-card-based business model § Kerberos, PKINIT al rs ve WMN Router(j) U ni R eq ue st P as fo s r p as s Broker(i) WMN Operator (i) Customer (j) WMN Router (j) 7/20 COMPANY LOGO
System Model and Notation (1/3) v Credit-card-based business model § Kerberos, PKINIT al rs ve WMN Router(j) U ni R eq ue st P as fo s r p as s Broker(i) WMN Operator (i) Customer (j) WMN Router (j) 7/20 COMPANY LOGO
 System Model and Notation (2/3) v Domain Parameter & Certificate P : Generator of Access Points H 1 : hash function mapping to : Domain Secret (Private Key) Mesh Routers : Domain public Key domain-cert § Domain Parameter : publicly known § Domain Secret : keep confidential § , : unique to each domain From TTP 8/20 COMPANY LOGO
System Model and Notation (2/3) v Domain Parameter & Certificate P : Generator of Access Points H 1 : hash function mapping to : Domain Secret (Private Key) Mesh Routers : Domain public Key domain-cert § Domain Parameter : publicly known § Domain Secret : keep confidential § , : unique to each domain From TTP 8/20 COMPANY LOGO
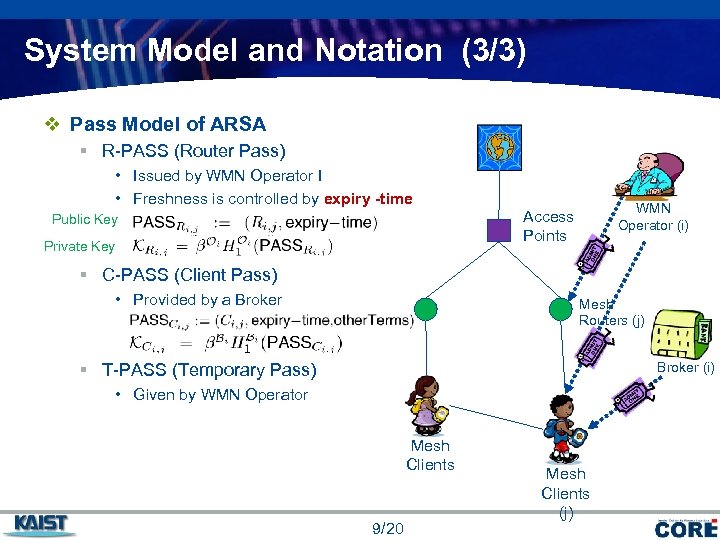 System Model and Notation (3/3) v Pass Model of ARSA § R-PASS (Router Pass) • Issued by WMN Operator I • Freshness is controlled by expiry -time Public Key Private Key WMN Operator (i) Access Points § C-PASS (Client Pass) • Provided by a Broker Mesh Routers (j) Broker (i) § T-PASS (Temporary Pass) • Given by WMN Operator Mesh Clients 9/20 Mesh Clients (j) COMPANY LOGO
System Model and Notation (3/3) v Pass Model of ARSA § R-PASS (Router Pass) • Issued by WMN Operator I • Freshness is controlled by expiry -time Public Key Private Key WMN Operator (i) Access Points § C-PASS (Client Pass) • Provided by a Broker Mesh Routers (j) Broker (i) § T-PASS (Temporary Pass) • Given by WMN Operator Mesh Clients 9/20 Mesh Clients (j) COMPANY LOGO
 AKA (Authentication and Key Agreement) (1/4) WMN Operator “a” WMN Operator “b” Access Points Mesh Routers Inter-domain AKA Intra-domain AKA Client-Client AKA 10/20 COMPANY LOGO
AKA (Authentication and Key Agreement) (1/4) WMN Operator “a” WMN Operator “b” Access Points Mesh Routers Inter-domain AKA Intra-domain AKA Client-Client AKA 10/20 COMPANY LOGO
 AKA (Authentication and Key Agreement) (2/4) v Inter-domain AKA WMN Operator (i) Mesh Routers A. 1 §Time check for t 1 Expiry –time check §Validate domain-cert §Verify A. 2 hot list check of broker v. To validate domain-cert From TTP A. 3 T-PASS 11/20 COMPANY LOGO
AKA (Authentication and Key Agreement) (2/4) v Inter-domain AKA WMN Operator (i) Mesh Routers A. 1 §Time check for t 1 Expiry –time check §Validate domain-cert §Verify A. 2 hot list check of broker v. To validate domain-cert From TTP A. 3 T-PASS 11/20 COMPANY LOGO
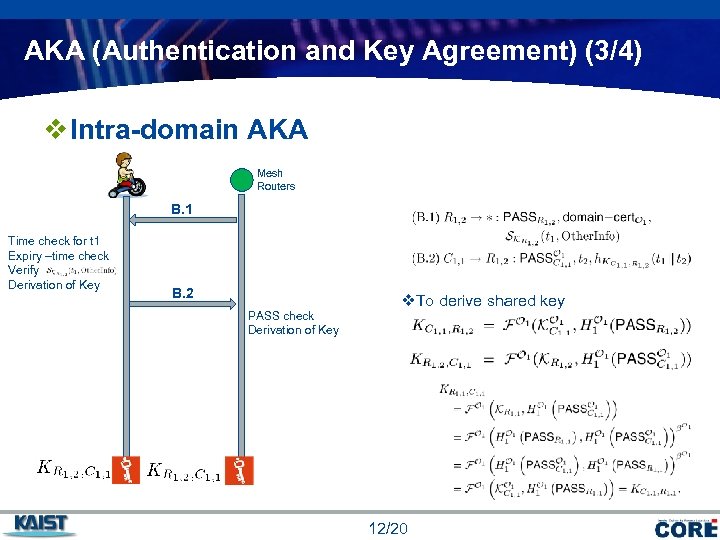 AKA (Authentication and Key Agreement) (3/4) v Intra-domain AKA Mesh Routers B. 1 Time check for t 1 Expiry –time check Verify Derivation of Key B. 2 PASS check Derivation of Key v. To derive shared key 12/20 COMPANY LOGO
AKA (Authentication and Key Agreement) (3/4) v Intra-domain AKA Mesh Routers B. 1 Time check for t 1 Expiry –time check Verify Derivation of Key B. 2 PASS check Derivation of Key v. To derive shared key 12/20 COMPANY LOGO
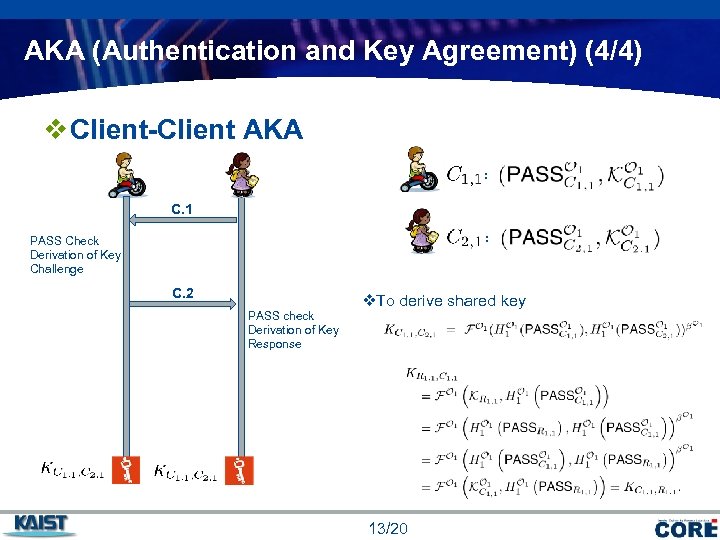 AKA (Authentication and Key Agreement) (4/4) v Client-Client AKA : C. 1 : PASS Check Derivation of Key Challenge C. 2 PASS check Derivation of Key Response v. To derive shared key 13/20 COMPANY LOGO
AKA (Authentication and Key Agreement) (4/4) v Client-Client AKA : C. 1 : PASS Check Derivation of Key Challenge C. 2 PASS check Derivation of Key Response v. To derive shared key 13/20 COMPANY LOGO
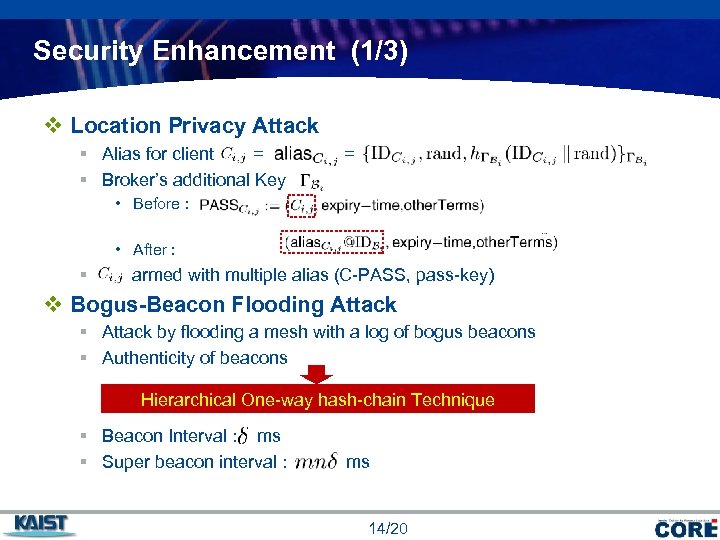 Security Enhancement (1/3) v Location Privacy Attack § Alias for client = § Broker’s additional Key : • Before : • After : § armed with multiple alias (C-PASS, pass-key) v Bogus-Beacon Flooding Attack § Attack by flooding a mesh with a log of bogus beacons § Authenticity of beacons Hierarchical One-way hash-chain Technique § Beacon Interval : ms § Super beacon interval : ms 14/20 COMPANY LOGO
Security Enhancement (1/3) v Location Privacy Attack § Alias for client = § Broker’s additional Key : • Before : • After : § armed with multiple alias (C-PASS, pass-key) v Bogus-Beacon Flooding Attack § Attack by flooding a mesh with a log of bogus beacons § Authenticity of beacons Hierarchical One-way hash-chain Technique § Beacon Interval : ms § Super beacon interval : ms 14/20 COMPANY LOGO
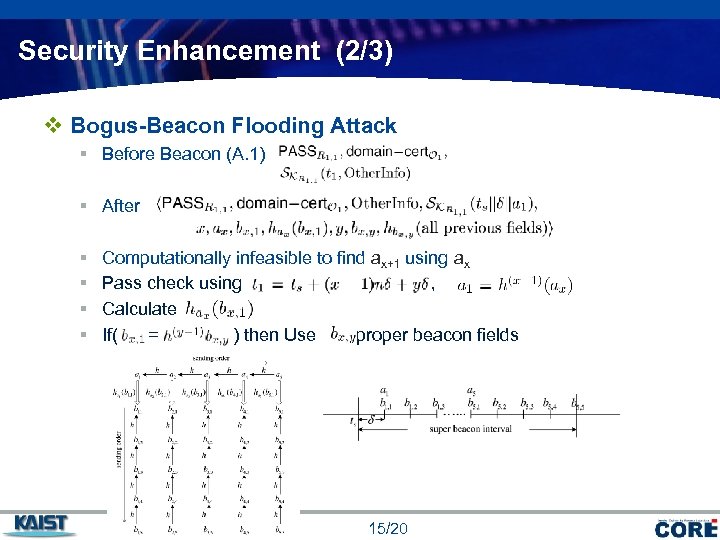 Security Enhancement (2/3) v Bogus-Beacon Flooding Attack § Before Beacon (A. 1) § After § § Computationally infeasible to find ax+1 using ax Pass check using , Calculate If( = ) then Use to proper beacon fields 15/20 COMPANY LOGO
Security Enhancement (2/3) v Bogus-Beacon Flooding Attack § Before Beacon (A. 1) § After § § Computationally infeasible to find ax+1 using ax Pass check using , Calculate If( = ) then Use to proper beacon fields 15/20 COMPANY LOGO
 Security Enhancement (3/3) v Denial-of-Access (Do. A) Attack v Bandwidth-Exhaustion Attack § CPU-bound puzzles § : random nonce created by Router § : puzzle indicator (Initial value = 0) § Client • Generate nonce N • Performing a brute-force search for a X – = # of Zero bits is zero • Finding solution : 16/20 COMPANY LOGO
Security Enhancement (3/3) v Denial-of-Access (Do. A) Attack v Bandwidth-Exhaustion Attack § CPU-bound puzzles § : random nonce created by Router § : puzzle indicator (Initial value = 0) § Client • Generate nonce N • Performing a brute-force search for a X – = # of Zero bits is zero • Finding solution : 16/20 COMPANY LOGO
 Discussion v Identify a number of unique security requirements of the emerging multi-hop WMNs v ARSA : Attack-Resilient Security Architecture § More practical and lightweight § Mutual Authentication & Key Agreement § Attack-Resilient Technique • Location Privacy Attack / Bogus-Beacon Flooding Attack • Denial-of-Access (Do. A) Attack / Bandwidth-Exhaustion Attack v Critique § § No experiment / Simulation Result Computationally Efficiency Difference with Kerberos / PKINIT Comparison with PKI 17/20 COMPANY LOGO
Discussion v Identify a number of unique security requirements of the emerging multi-hop WMNs v ARSA : Attack-Resilient Security Architecture § More practical and lightweight § Mutual Authentication & Key Agreement § Attack-Resilient Technique • Location Privacy Attack / Bogus-Beacon Flooding Attack • Denial-of-Access (Do. A) Attack / Bandwidth-Exhaustion Attack v Critique § § No experiment / Simulation Result Computationally Efficiency Difference with Kerberos / PKINIT Comparison with PKI 17/20 COMPANY LOGO
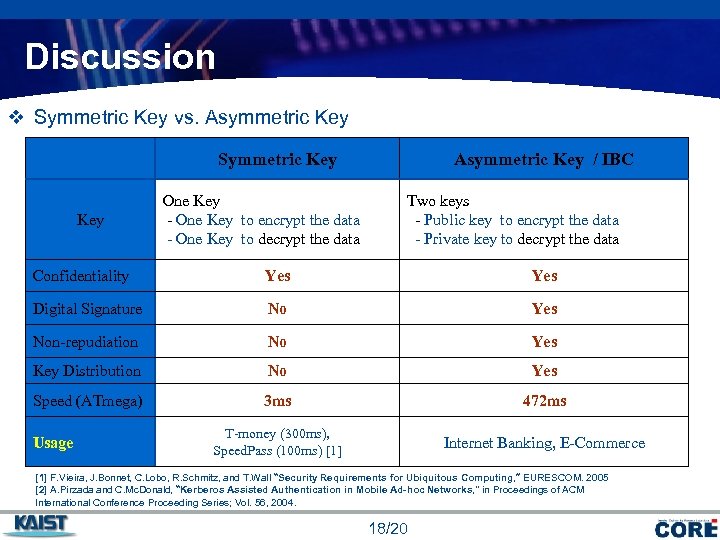 Discussion v Symmetric Key vs. Asymmetric Key Symmetric Key Asymmetric Key / IBC One Key - One Key to encrypt the data - One Key to decrypt the data Two keys - Public key to encrypt the data - Private key to decrypt the data Confidentiality Yes Digital Signature No Yes Non-repudiation No Yes Key Distribution No Yes Speed (ATmega) 3 ms 472 ms T-money (300 ms), Speed. Pass (100 ms) [1] Internet Banking, E-Commerce Usage [1] F. Vieira, J. Bonnet, C. Lobo, R. Schmitz, and T. Wall “Security Requirements for Ubiquitous Computing, ” EURESCOM. 2005 [2] A. Pirzada and C. Mc. Donald, “Kerberos Assisted Authentication in Mobile Ad-hoc Networks, " in Proceedings of ACM International Conference Proceeding Series; Vol. 56, 2004. 18/23 18/20 COMPANY LOGO
Discussion v Symmetric Key vs. Asymmetric Key Symmetric Key Asymmetric Key / IBC One Key - One Key to encrypt the data - One Key to decrypt the data Two keys - Public key to encrypt the data - Private key to decrypt the data Confidentiality Yes Digital Signature No Yes Non-repudiation No Yes Key Distribution No Yes Speed (ATmega) 3 ms 472 ms T-money (300 ms), Speed. Pass (100 ms) [1] Internet Banking, E-Commerce Usage [1] F. Vieira, J. Bonnet, C. Lobo, R. Schmitz, and T. Wall “Security Requirements for Ubiquitous Computing, ” EURESCOM. 2005 [2] A. Pirzada and C. Mc. Donald, “Kerberos Assisted Authentication in Mobile Ad-hoc Networks, " in Proceedings of ACM International Conference Proceeding Series; Vol. 56, 2004. 18/23 18/20 COMPANY LOGO
 Additional Experiment v Security Aspect Authentication Digital signature Non-repudiation Secure key distribution Kerberos YES No No No PKIX YES YES M-PKINIT YES No No YES ARSA YES No No YES v Computation Efficiency System Mobile Pu Pr Service Device S Pu Pr S Total Operation Time PKIX(RSA-1024 bit) 2 2 1 2 0 0 3449 1035 ms Kerberos 0 0 8 0 0 6 8. 12 2. 4 ms M-PKINIT TGT 1 1 7 1 1 5 3305. 1 991. 53 ms M-PKINIT SGT 0 0 8 0 0 4 8. 08 2. 42 ms ARSA Inter-domain AKA 1 2 0 1 1 1 3373. 02 1011. 9 ms ARSA Intra-domain AKA 0 2 0 1 1 0 1799 539. 7 ms ARSA Client-Client AKA 0 2 1 301. 02 90. 31 ms 19/20 COMPANY LOGO
Additional Experiment v Security Aspect Authentication Digital signature Non-repudiation Secure key distribution Kerberos YES No No No PKIX YES YES M-PKINIT YES No No YES ARSA YES No No YES v Computation Efficiency System Mobile Pu Pr Service Device S Pu Pr S Total Operation Time PKIX(RSA-1024 bit) 2 2 1 2 0 0 3449 1035 ms Kerberos 0 0 8 0 0 6 8. 12 2. 4 ms M-PKINIT TGT 1 1 7 1 1 5 3305. 1 991. 53 ms M-PKINIT SGT 0 0 8 0 0 4 8. 08 2. 42 ms ARSA Inter-domain AKA 1 2 0 1 1 1 3373. 02 1011. 9 ms ARSA Intra-domain AKA 0 2 0 1 1 0 1799 539. 7 ms ARSA Client-Client AKA 0 2 1 301. 02 90. 31 ms 19/20 COMPANY LOGO
 Additional Experiment v Processing Times of cryptography operations Platform • Service Device - CPU : PXA 270 - RAM : SRAM 128 MB Cryptography RSA 1024 bit AES 128 bit Hash Function • Server - CPU : Xeon 3. 2 GHz - RAM: 4 GB RSA 1024 bit AES 128 bit Operation Time Complexity Private Key Avg. 472 ms 1574. 33 Public Key Avg. 23 ms 75. 33 Encryption Avg. 0. 3 ms 1. 0 Decryption Avg. 0. 3 ms 1. 0 SHA-1 Avg. 0. 6 ms 2. 0 Private Key Avg. 2. 917 ms 9. 72 Public Key Avg. 0. 170 ms 0. 56 Encryption Avg. 0. 006 ms 0. 02 Decryption Avg. 0. 006 ms 0. 02 20/20 COMPANY LOGO
Additional Experiment v Processing Times of cryptography operations Platform • Service Device - CPU : PXA 270 - RAM : SRAM 128 MB Cryptography RSA 1024 bit AES 128 bit Hash Function • Server - CPU : Xeon 3. 2 GHz - RAM: 4 GB RSA 1024 bit AES 128 bit Operation Time Complexity Private Key Avg. 472 ms 1574. 33 Public Key Avg. 23 ms 75. 33 Encryption Avg. 0. 3 ms 1. 0 Decryption Avg. 0. 3 ms 1. 0 SHA-1 Avg. 0. 6 ms 2. 0 Private Key Avg. 2. 917 ms 9. 72 Public Key Avg. 0. 170 ms 0. 56 Encryption Avg. 0. 006 ms 0. 02 Decryption Avg. 0. 006 ms 0. 02 20/20 COMPANY LOGO
 Thank you for attention! COMPANY LOGO
Thank you for attention! COMPANY LOGO


