3e3ff3a27f599860596b635c31605ede.ppt
- Количество слайдов: 28

Argos Emulator Georgios Portokalidis Asia Slowinska Herbert Bos Vrije Universiteit Amsterdam Georgios Portokalidis VU Amsterdam
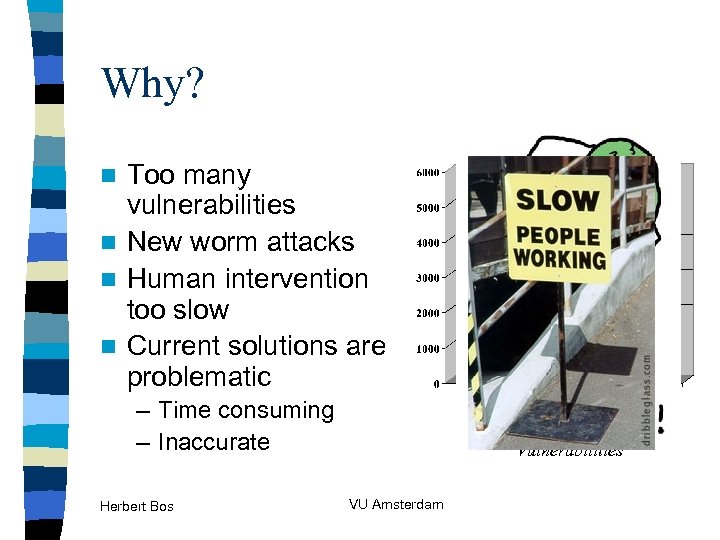
Why? Too many vulnerabilities n New worm attacks n Human intervention too slow n Current solutions are problematic n – Time consuming – Inaccurate Herbert Bos CERT/CC Reported Vulnerabilities VU Amsterdam
Goals Platform for next generation honeypots n Protect entire OS n Detect most common attack vectors n Accuracy n Herbert Bos VU Amsterdam

It Works! Apache chunked encoding overflow IIS ISAPI. printer host header overflow Web. Dav ntdll. dll overflow Front. Page Server Extensions Debug Overflow War-FTP overflow ASN. 1 Library Bitstring Heap Overflow Windows Message Queueing Remote Overflow RPC DCOM Interface overflow LSASS Overflow Windows Pn. P Service Remote Overflow nb. SMTP remote format string exploit WMF exploit Herbert Bos VU Amsterdam
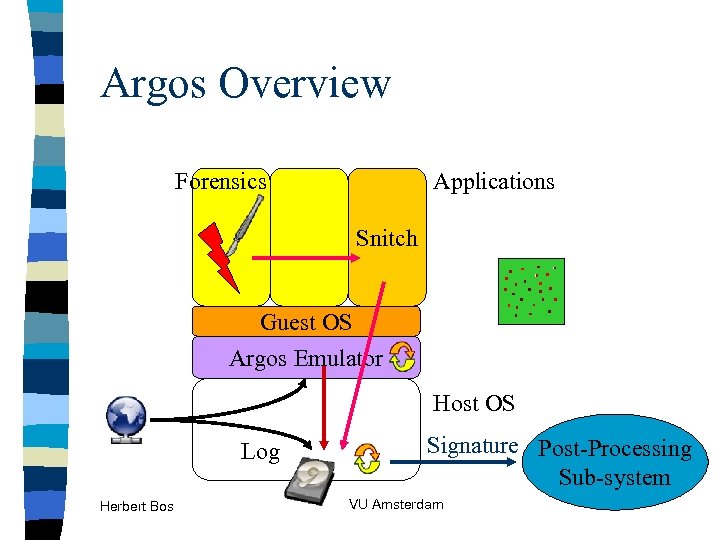
Argos Overview Forensics Applications Snitch Guest OS Argos Emulator Host OS Log Herbert Bos Signature Post-Processing Sub-system VU Amsterdam
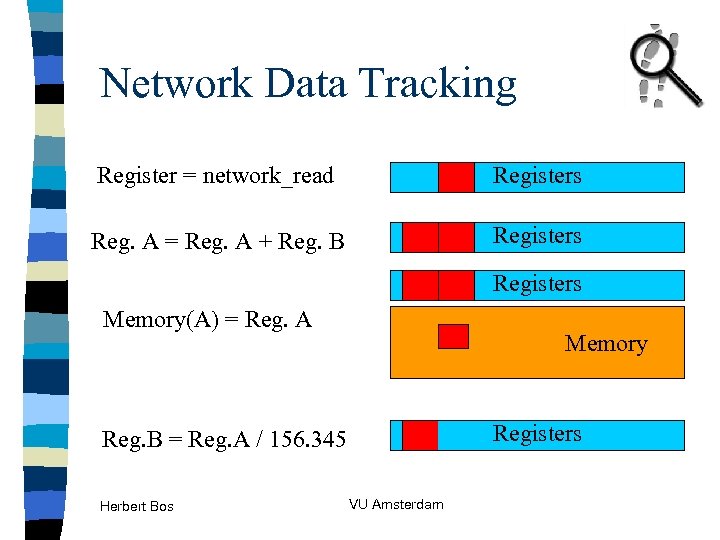
Network Data Tracking Register = network_read Registers Reg. A = Reg. A + Reg. B Registers Memory(A) = Reg. A Memory Registers Reg. B = Reg. A / 156. 345 Herbert Bos VU Amsterdam
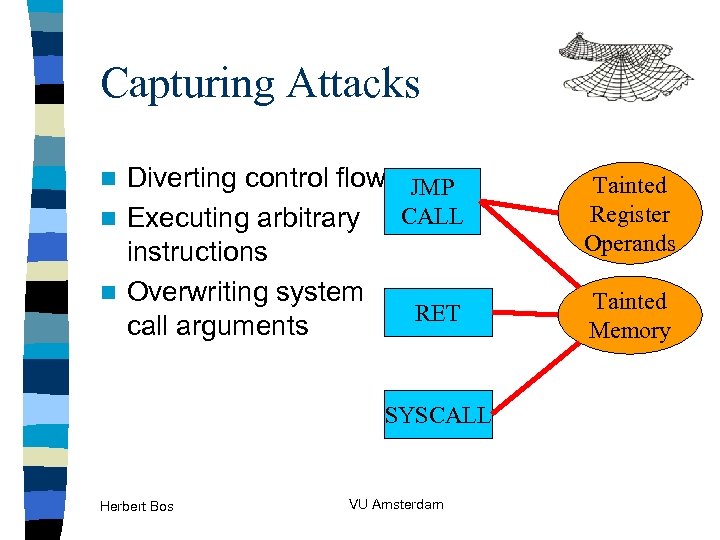
Capturing Attacks Diverting control flow JMP CALL n Executing arbitrary instructions n Overwriting system RET call arguments n SYSCALL Herbert Bos VU Amsterdam Tainted Register Operands Tainted Memory
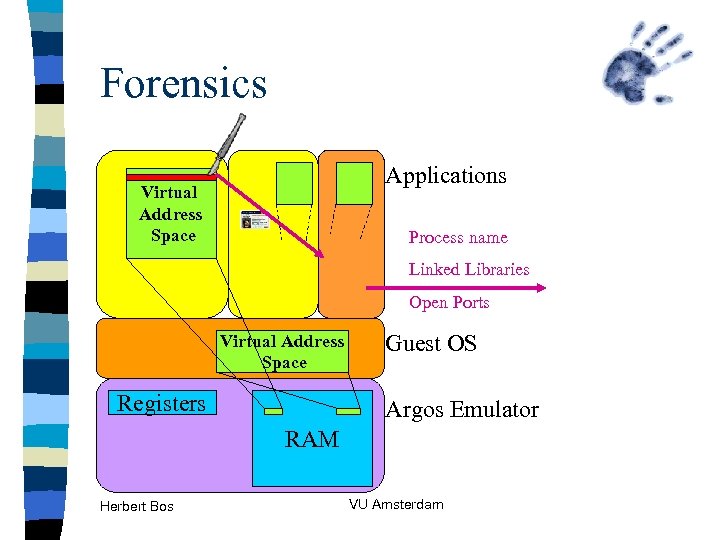
Forensics Applications Virtual Address Space Process name Linked Libraries Open Ports Virtual Address Space Registers Guest OS Argos Emulator RAM Herbert Bos VU Amsterdam

Signature Generation Herbert Bos VU Amsterdam

Multiple Signature Generators Herbert Bos VU Amsterdam
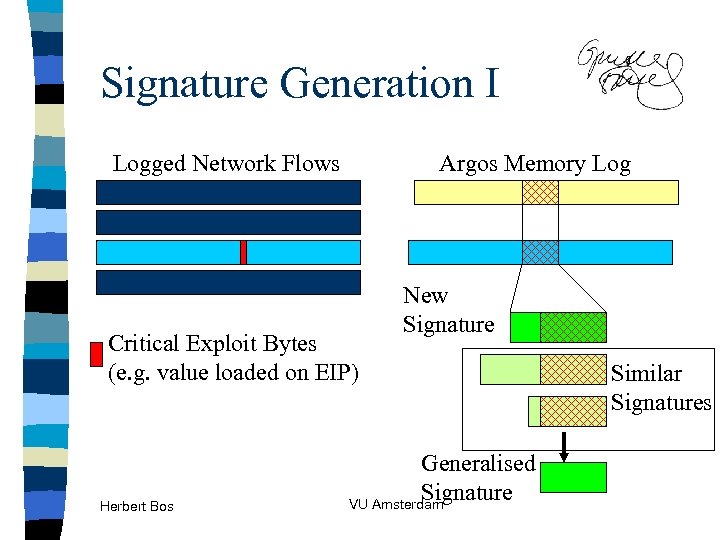
Signature Generation I Logged Network Flows Argos Memory Log Critical Exploit Bytes (e. g. value loaded on EIP) Herbert Bos New Signature Generalised Signature VU Amsterdam Similar Signatures
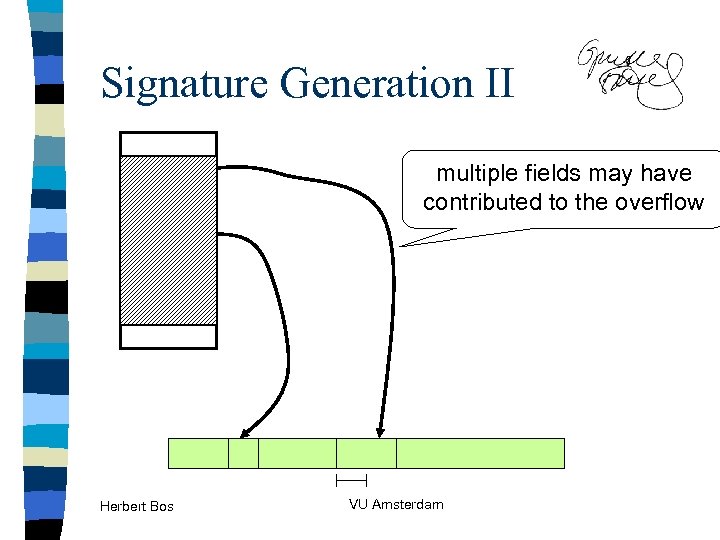
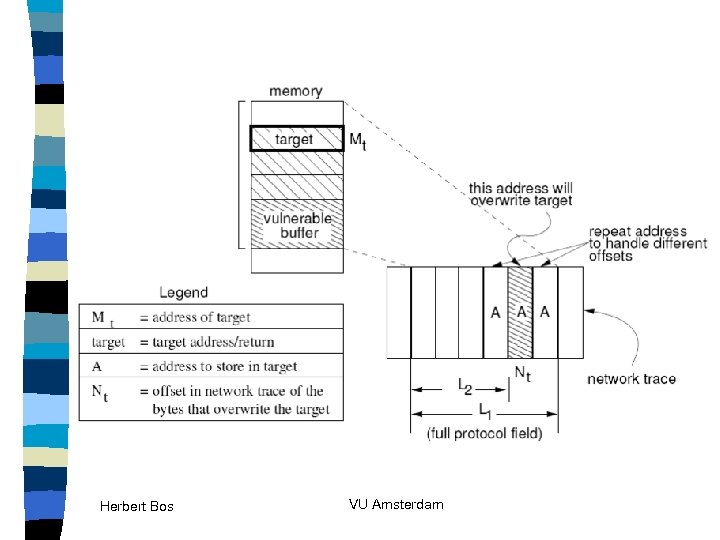
Signature Generation II target Herbert Bos multiple fields may have contributed to the overflow VU Amsterdam
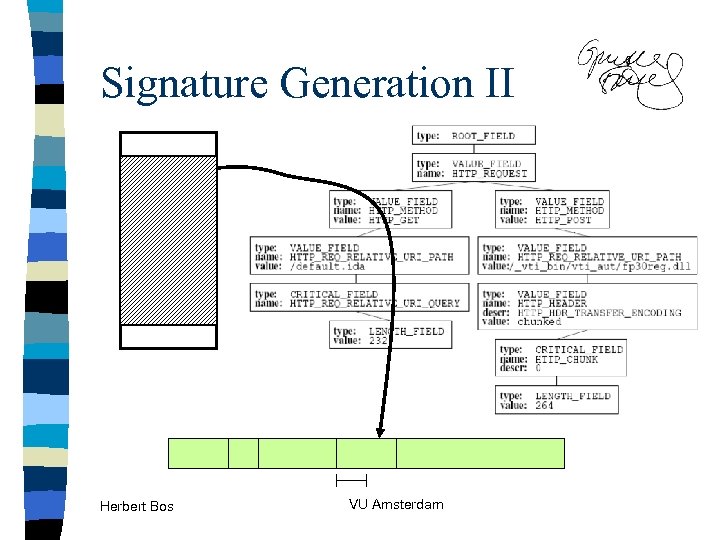
Signature Generation II target Herbert Bos VU Amsterdam

Signature Generator II n handles polymorphic attacks n easy to check n great when considering false positives Herbert Bos VU Amsterdam
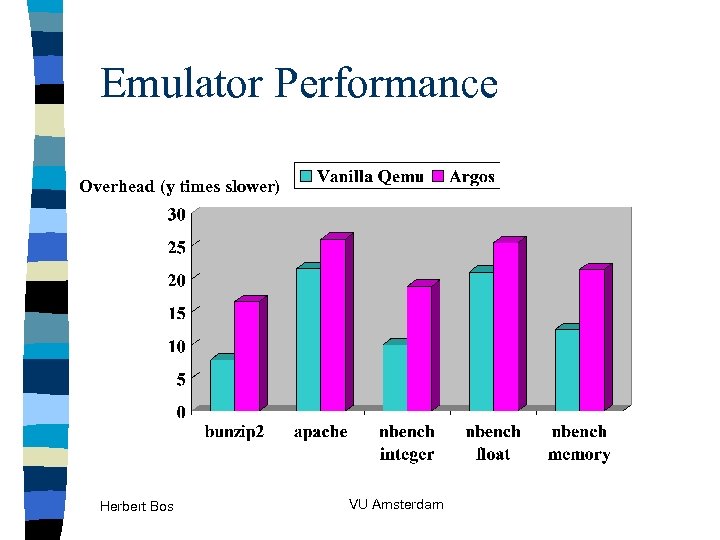
Emulator Performance Overhead (y times slower) Herbert Bos VU Amsterdam
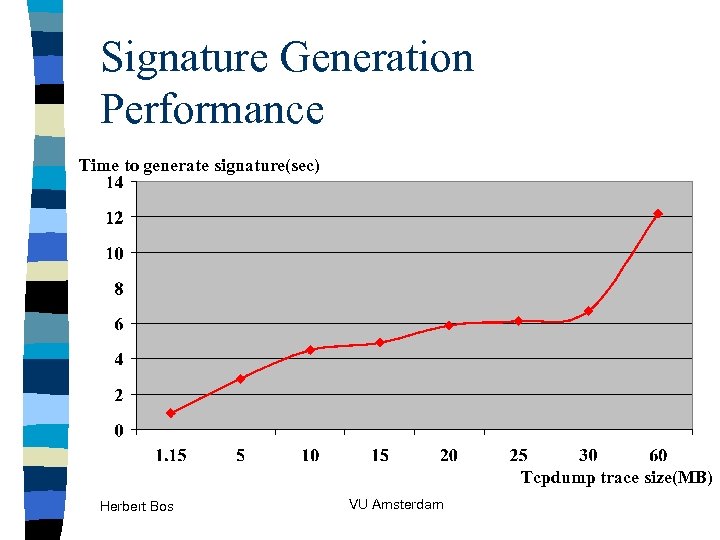
Signature Generation Performance Time to generate signature(sec) Tcpdump trace size(MB) Herbert Bos VU Amsterdam
Future Work n Replaying attacks n Integration with nepenthes honeypot n Increase data tracking precision n Protocol aware signature generation n Generate self certifying alerts Herbert Bos VU Amsterdam

On The Web http: //www. few. vu. nl/argos Herbert Bos VU Amsterdam
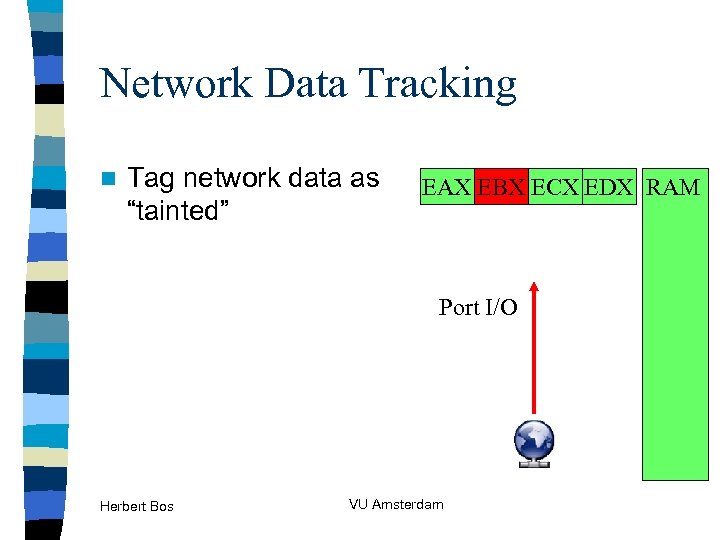
Network Data Tracking n Tag network data as “tainted” EAX EBX ECX EDX RAM Port I/O Herbert Bos VU Amsterdam
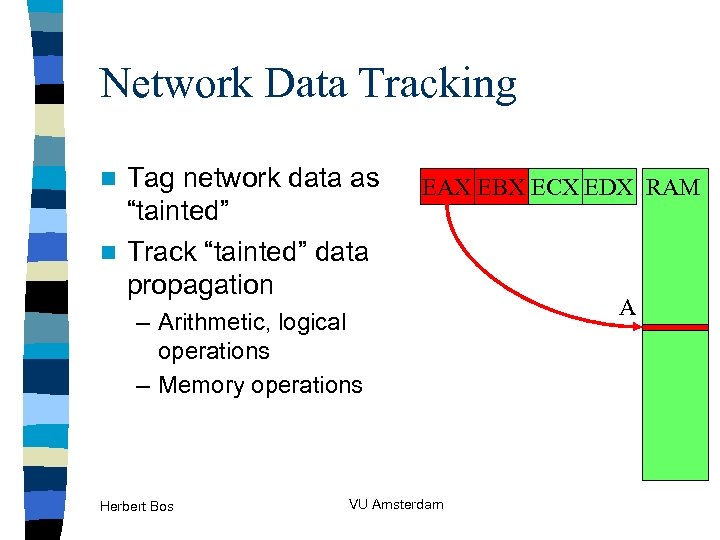
Network Data Tracking Tag network data as “tainted” n Track “tainted” data propagation n EAX EBX ECX EDX RAM – Arithmetic, logical operations – Memory operations Herbert Bos VU Amsterdam A
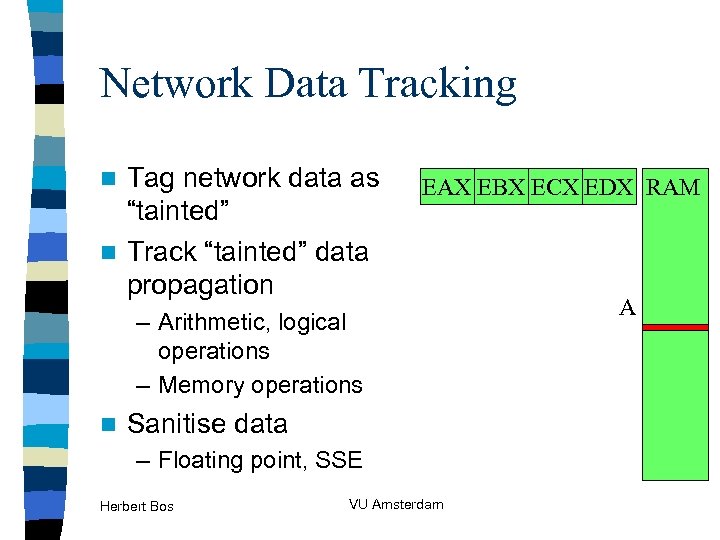
Network Data Tracking Tag network data as “tainted” n Track “tainted” data propagation n EAX EBX ECX EDX RAM – Arithmetic, logical operations – Memory operations n Sanitise data – Floating point, SSE Herbert Bos VU Amsterdam A
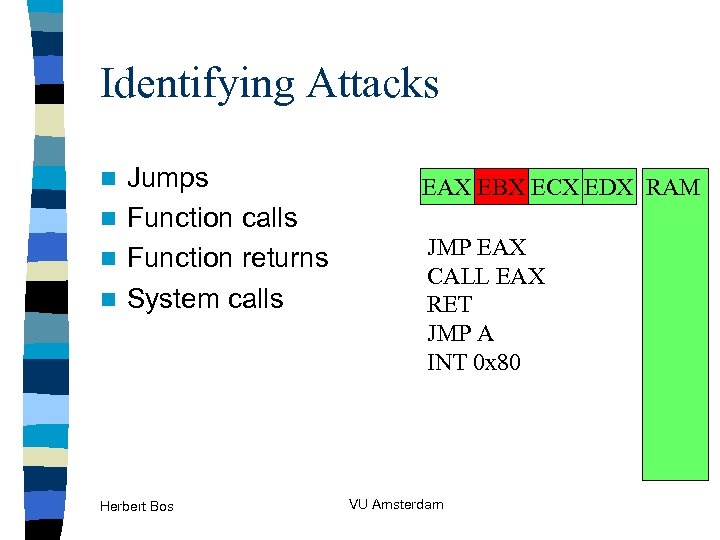
Identifying Attacks Jumps n Function calls n Function returns n System calls n Herbert Bos EAX EBX ECX EDX RAM JMP EAX CALL EAX RET JMP A INT 0 x 80 VU Amsterdam
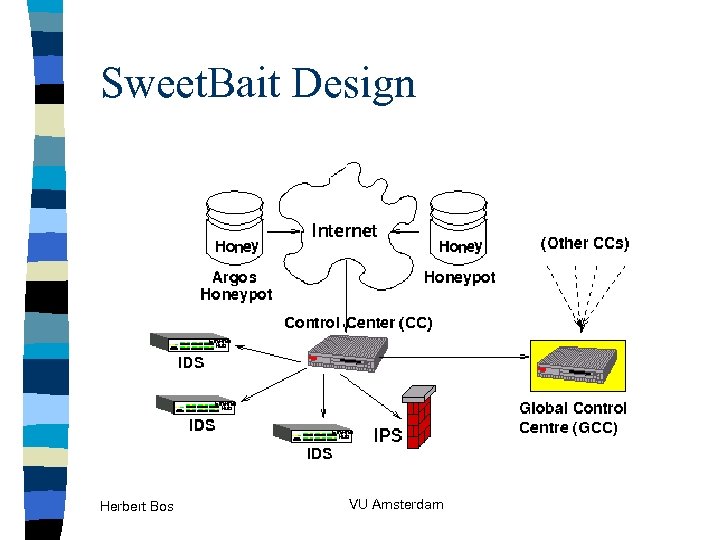
Sweet. Bait Design Herbert Bos VU Amsterdam
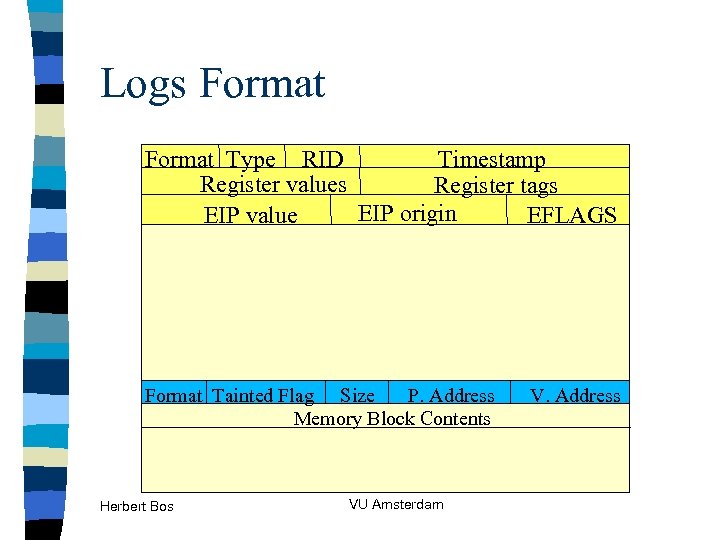
Logs Format Type RID Timestamp Register values Register tags EIP origin EIP value EFLAGS Format Tainted Flag Size P. Address Memory Block Contents Herbert Bos VU Amsterdam V. Address
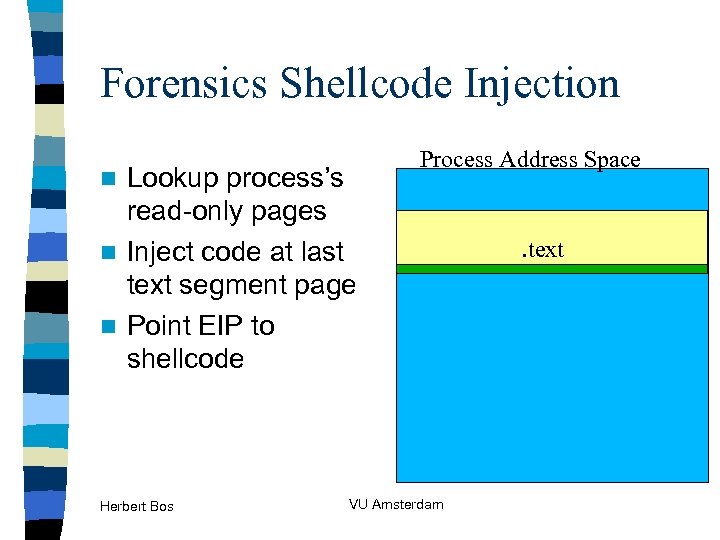
Forensics Shellcode Injection Lookup process’s read-only pages n Inject code at last text segment page n Point EIP to shellcode n Herbert Bos (Windows PE, ELF, etc) Process Address Space VU Amsterdam . text
![Forensics – The Snitch Pid = getpid() n Rid [injected by Argos] n Connect(localhost) Forensics – The Snitch Pid = getpid() n Rid [injected by Argos] n Connect(localhost)](https://present5.com/presentation/3e3ff3a27f599860596b635c31605ede/image-26.jpg)
Forensics – The Snitch Pid = getpid() n Rid [injected by Argos] n Connect(localhost) n Send(pid & rid) n n n n Herbert Bos Listen() Accept() Read(pid & rid) Exec(Netstat or Open. Ports) Connect(argos host) Send(info) VU Amsterdam
Herbert Bos VU Amsterdam
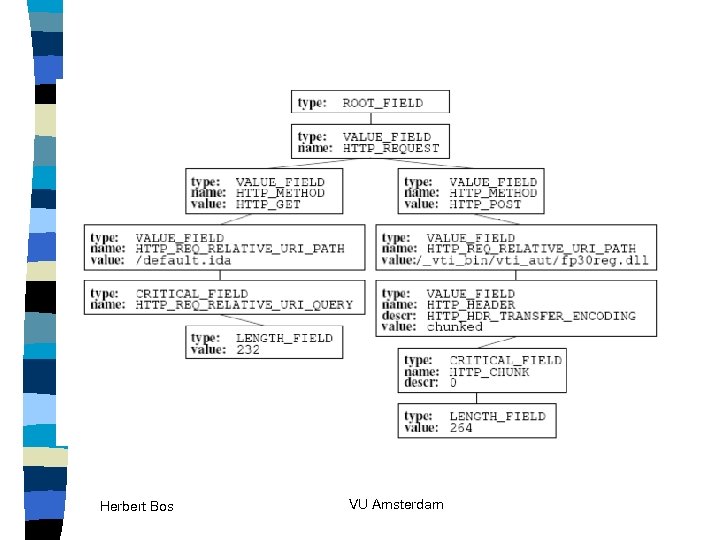
Herbert Bos VU Amsterdam
3e3ff3a27f599860596b635c31605ede.ppt