bbf9998e4591d3bd336f9f09c5bbcdbc.ppt
- Количество слайдов: 18

ARCHER: Using Symbolic, Pathsensitive Analysis to Detect Memory Access Errors Yichen Xie, Andy Chou, and Dawson Engler Computer Systems Laboratory Stanford University Stanford, CA 94305, U. S. A. Wei Tao 5070379106
Authors Yichen Xie Stanford University
Authors Andy Chou

Authors Dawson Engler Associate Professor Computer Science and Electrical Engineering Gates Building 3 A-314 353 Serra Mall Stanford University
Authors
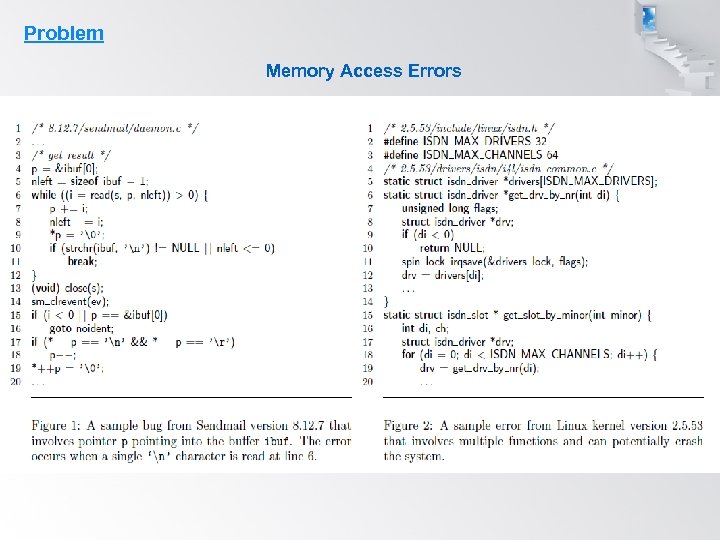
Problem Memory Access Errors

Introduction ARCHER (ARray CHeck. ER): ØNo annotations needed. ØSpeed. ØFew false positives. ØDrawbacks.

Introduction Key features: ØInterprocedural ØFully symbolic ØPath sensitive ØContext sensitive ØAware of pointer aliases for buffers

Overview The core of ARCHER consists of three pieces: Øa translator Øa traversal module Øa solver
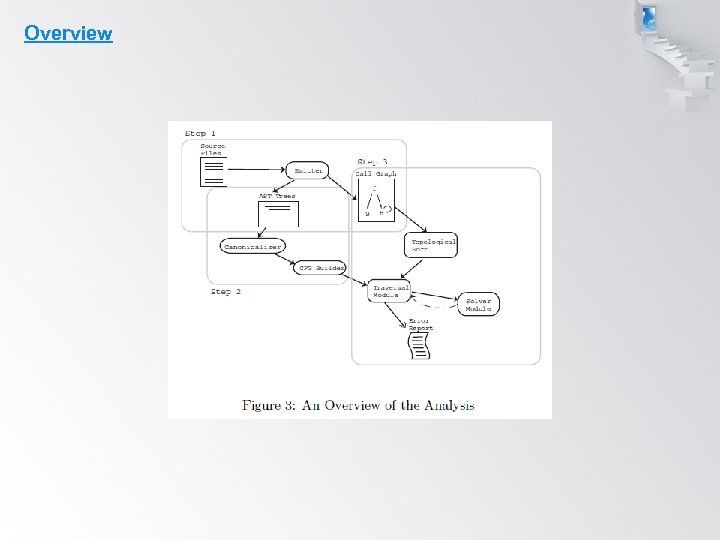
Overview
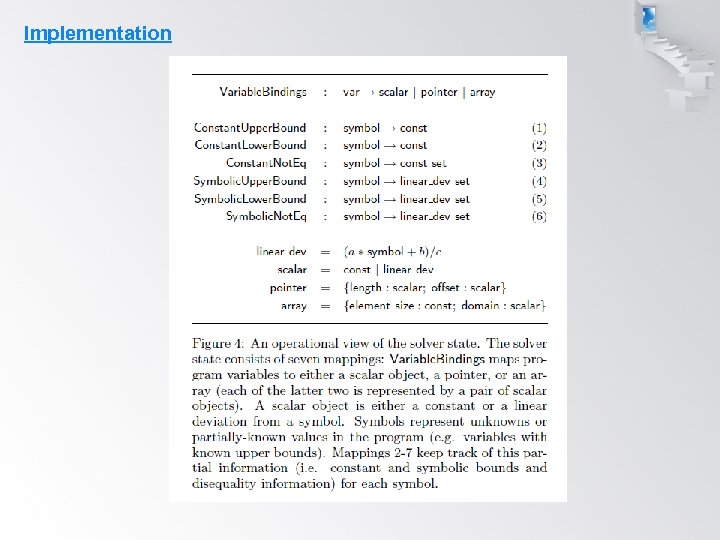
Implementation

Implementation
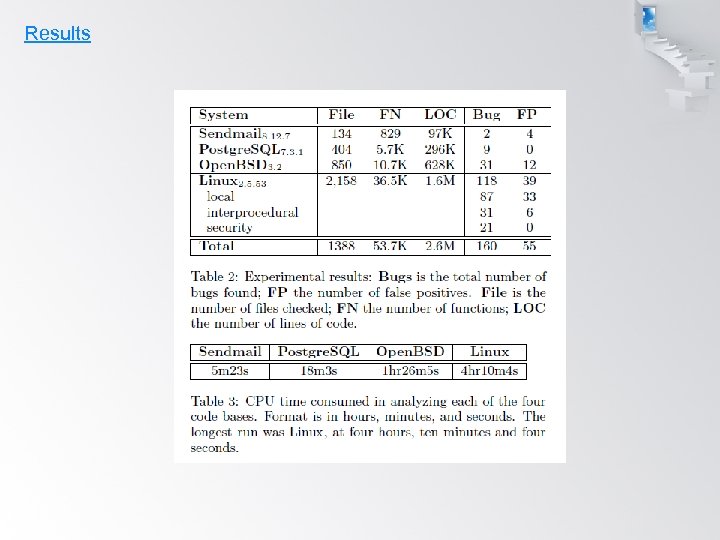
Results
![References [1] K. Ashcraft and D. R. Engler. Using programmer -written compiler extensions to References [1] K. Ashcraft and D. R. Engler. Using programmer -written compiler extensions to](https://present5.com/presentation/bbf9998e4591d3bd336f9f09c5bbcdbc/image-14.jpg)
References [1] K. Ashcraft and D. R. Engler. Using programmer -written compiler extensions to catch security holes. In IEEE Symposium on Security and Privacy, Oakland, California, May 2002. [2] R. Bodik, R. Gupta, and V. Sarkar. ABCD: Eliminating array bounds checks on demand. In SIGPLAN Conference on Programming Language Design and Implementation, pages 321– 333, June 2000. [3] W. R. Bush, J. D. Pincus, and D. J. Sielaff. A static analyzer for finding dynamic programming errors. Software: Practice and Experience, 30(7): 775– 802, June 2000. [4] B. Chess. Improving computer security using extended static checking. In IEEE Symposium on Security and Privacy, Oakland, California, May 2002. [5] Microsoft Corporation. AST Toolkit. http: //research. microsoft. com/sbt/. [6] N. Dor, M. Rodeh, and M. Sagiv. CSSV: towards a realistic tool for statically detecting all buffer overflows in c. In Proceedings of the ACM SIGPLAN 2003 Conference on Programming Language Design and Implementation, pages 155– 167. ACM Press, June 2003. [7] D. R. Engler, B. Chelf, A. Chou, and S. Hallem. Checking system rules using system-specific, programmerwritten compiler extensions. In Proceedings of Operating Systems Design and Implementation (OSDI), September 2000. [8] D. R. Engler, D. Y. Chen, S. Hallem, A. Chou, and B. Chelf. Bugs as deviant behavior: A general approach to inferring errors in systems code. In Proceedings of the Eighteenth ACM Symposium on Operating Systems Principles, 2001.
![[12] D. Freedman, R. Pisani, and R. Purves. Statistics. W W References Norton & [12] D. Freedman, R. Pisani, and R. Purves. Statistics. W W References Norton &](https://present5.com/presentation/bbf9998e4591d3bd336f9f09c5bbcdbc/image-15.jpg)
[12] D. Freedman, R. Pisani, and R. Purves. Statistics. W W References Norton & Co. , third edition, September 1997. [13] S. Hallem, B. Chelf, Y. Xie, and D. R. Engler. A [9] C. Flanagan and K. R. M. Leino. Houdini, an system and annotation language for building system-specific, static assistant for ESC/Java. In Symposium of Formal analyses. In Methods Proceedings of the ACM SIGPLAN 2002 Conference Europe, pages 500– 517, March 2001. on [10] C. Flanagan, K. R. M. Leino, M. Lillibridge, G. Programming Language Design and Nelson, J. B. Implementation, Saxe, and R. Stata. Extended static checking for Berlin, Germany, June 2002. Java. In Proceedings of the ACM SIGPLAN 2002 Conference [14] R. Hastings and B. Joyce. Purify: Fast detection of on memory leaks and access errors. In Proceedings of Programming Language Design and the Implementation, pages Winter USENIX Conference, December 1992. 234– 245. ACM Press, 2002. [15] Intrinsa. A technical introduction to [11] C. Flanagan and S. Qadeer. Predicate PREfix/Enterprise. abstraction for Technical report, Intrinsa Corporation, 1998. software verification. In Proceedings of the 29 th [16] R. W. M. Jones and P. H. J. Kelly. Backwards. Annual compatible Symposium on Principles of Programming bounds checking for arrays and pointers in C Languages, June programs. In 2002. Automated and Algorithmic Debugging, pages 13– 26, May 1997.
![References [17] W. Landi, B. G. Ryder, and S. Zhang. Interprocedural modification side effect References [17] W. Landi, B. G. Ryder, and S. Zhang. Interprocedural modification side effect](https://present5.com/presentation/bbf9998e4591d3bd336f9f09c5bbcdbc/image-16.jpg)
References [17] W. Landi, B. G. Ryder, and S. Zhang. Interprocedural modification side effect analysis with pointer aliasing. In Proceedings of the ACM SIGPLAN 1993 Conference on Programming Language Design and Implementation, pages 56– 67. ACM Press, 1993. [18] D. Larochelle and D. Evans. Statically detecting likely buffer overflow vulnerabilities. In 10 th USENIX Security Symposium, August 2001. [19] G. C. Necula, S. Mc. Peak, S. P. Rahul, and W. Weimer. CIL: Intermediate language and tools for analysis and transformation of c programs. In International Conference on Compiler Construction, March 2002. [20] G. C. Necula, S. Mc. Peak, and W. Weimer. CCured: type-safe retrofitting of legacy code. In Symposium on Principles of Programming Languages, pages 128– 139, January 2002. [21] W. Pugh. The omega test: a fast and practical integer programming algorithm for dependence analysis. In Supercomputing, pages 4– 13, November 1991. [22] B. Schneier. Risks to cybersecurity. Congressional Testimony by Federal Document Clearing House, June 2003.
![References [23] M. N. Velev and R. E. Bryant. Effective use of boolean satisfiability References [23] M. N. Velev and R. E. Bryant. Effective use of boolean satisfiability](https://present5.com/presentation/bbf9998e4591d3bd336f9f09c5bbcdbc/image-17.jpg)
References [23] M. N. Velev and R. E. Bryant. Effective use of boolean satisfiability procedures in the formal verification of superscalar and VLIW microprocessors. Journal of Symbolic Computation, special issue on Integration of Automated Reasoning and Computer Algebra Systems, 2002. [24] D. Wagner, J. Foster, E. Brewer, and A. Aiken. A first step towards automated detection of buffer overrun vulnerabilities. In The 2000 Network and Distributed Systems Security Conference. San Diego, CA, February 2000.

Thank you!
bbf9998e4591d3bd336f9f09c5bbcdbc.ppt