21a14e32c7b5080e29f236c926e61228.ppt
- Количество слайдов: 29

Applying ASD in Designing And Verifying: Be. X Orchestration Controller Harsh Beohar
Goal • To briefly describe ASD as a methodology. • To describe the behavior of system under design in brief. • To briefly describe the scenarios which are designed using ASD. • Problems encountered while using ASD. CONFIDENTIAL BL-Components, Harsh Beohar, April 04, 2008 2
![ASD Methodology[1] CONFIDENTIAL BL-Components, Harsh Beohar, April 04, 2008 3 ASD Methodology[1] CONFIDENTIAL BL-Components, Harsh Beohar, April 04, 2008 3](https://present5.com/presentation/21a14e32c7b5080e29f236c926e61228/image-3.jpg)
ASD Methodology[1] CONFIDENTIAL BL-Components, Harsh Beohar, April 04, 2008 3
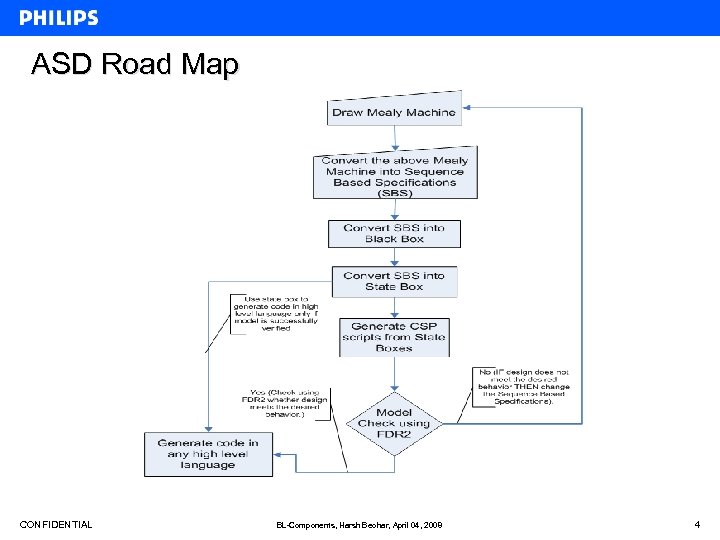
ASD Road Map CONFIDENTIAL BL-Components, Harsh Beohar, April 04, 2008 4
Mealy Machine • Differences with Automaton: – A Mealy machine does not have final states – In Mealy machine each transition produces output based on current state and input. • This motivates us to model a reactive system through Mealy Machine. • To enable the use of predicates in transition of states, we need to add one more tuple in Mealy Machine. • M=(Q, Σ, Γ, P, δ, λ, qi) – Q : is a finite set of states. – Σ : is a finite set of stimulus S (finite input alphabet). – Γ : is a finite set of responses R (finite output alphabet). – P : is a set of unbounded predicates. – δ : Q × Σ → Q (next state function). – λ : Q × Σ → Γ (output function). – qi : initial state CONFIDENTIAL BL-Components, Harsh Beohar, April 04, 2008 5
Box structure development methodology (BSDM) • Operates by identifying and refining abstractions to develop a software system through 3 views[2]: – Black Box. – State Box. – Clear Box. • Black box is a state-free description of external view of system. • Let S & R denote the set of stimulus and response respectively of a system. Then the black box function BB of a system is • Defined as total function that maps stimulus history to responses. CONFIDENTIAL BL-Components, Harsh Beohar, April 04, 2008 6
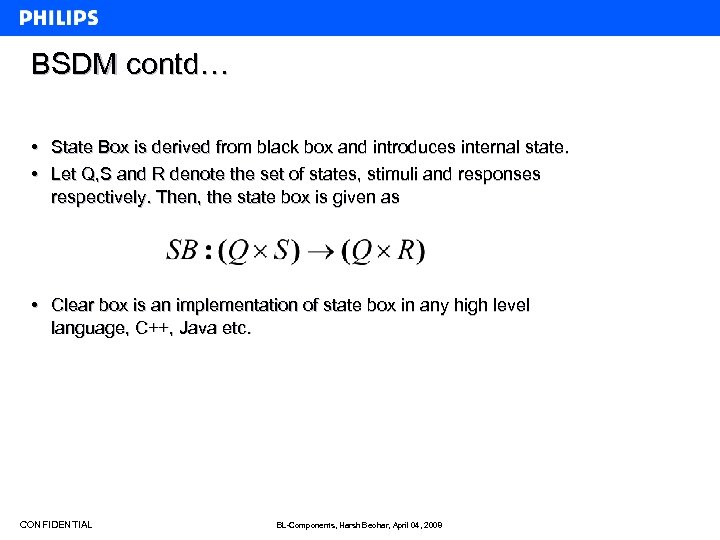
BSDM contd… • State Box is derived from black box and introduces internal state. • Let Q, S and R denote the set of states, stimuli and responses respectively. Then, the state box is given as • Clear box is an implementation of state box in any high level language, C++, Java etc. CONFIDENTIAL BL-Components, Harsh Beohar, April 04, 2008
![Sequence Based Specification • SBS[3] is a method for producing consistent, complete and traceably Sequence Based Specification • SBS[3] is a method for producing consistent, complete and traceably](https://present5.com/presentation/21a14e32c7b5080e29f236c926e61228/image-8.jpg)
Sequence Based Specification • SBS[3] is a method for producing consistent, complete and traceably correct software specifications. • SBS is used to derive black box function. • Black box function and next state function (δ) from Mealy machine are used to derive state box functions. • In [3], Prowell and Poore presented the SBS method for systematically defining: – Consistency: Each stimulus history maps to only one response. – Completeness: A response is defined for every stimulus history. – Correctness: Requirements Traceability. • A sample sequence based specification Orchestration. Controller CONFIDENTIAL BL-Components, Harsh Beohar, April 04, 2008 8
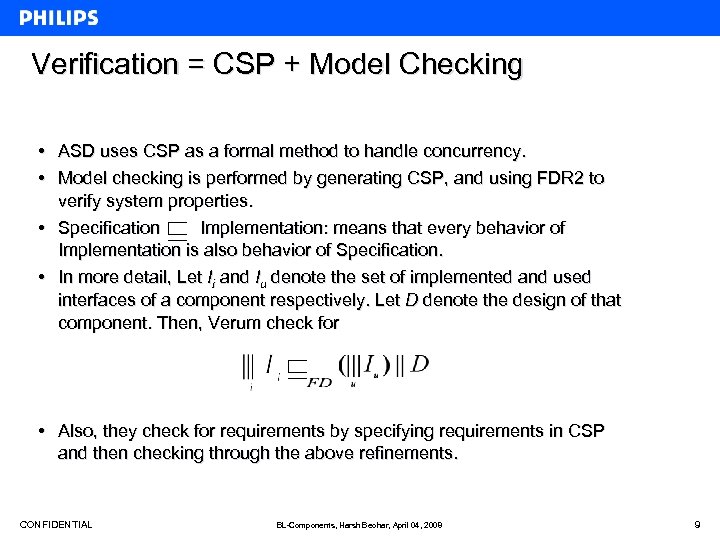
Verification = CSP + Model Checking • ASD uses CSP as a formal method to handle concurrency. • Model checking is performed by generating CSP, and using FDR 2 to verify system properties. • Specification Implementation: means that every behavior of Implementation is also behavior of Specification. • In more detail, Let Ii and Iu denote the set of implemented and used interfaces of a component respectively. Let D denote the design of that component. Then, Verum check for • Also, they check for requirements by specifying requirements in CSP and then checking through the above refinements. CONFIDENTIAL BL-Components, Harsh Beohar, April 04, 2008 9
![Converting SBS into CSP using state box[4] CONFIDENTIAL BL-Components, Harsh Beohar, April 04, 2008 Converting SBS into CSP using state box[4] CONFIDENTIAL BL-Components, Harsh Beohar, April 04, 2008](https://present5.com/presentation/21a14e32c7b5080e29f236c926e61228/image-10.jpg)
Converting SBS into CSP using state box[4] CONFIDENTIAL BL-Components, Harsh Beohar, April 04, 2008
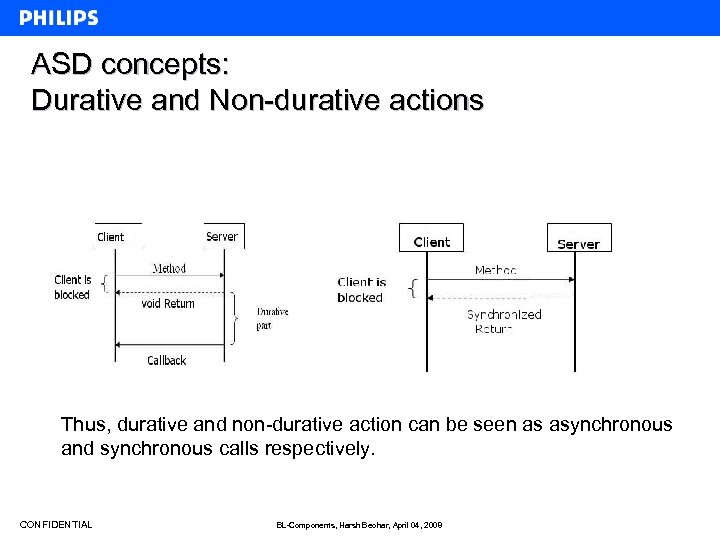
ASD concepts: Durative and Non-durative actions Thus, durative and non-durative action can be seen as asynchronous and synchronous calls respectively. CONFIDENTIAL BL-Components, Harsh Beohar, April 04, 2008
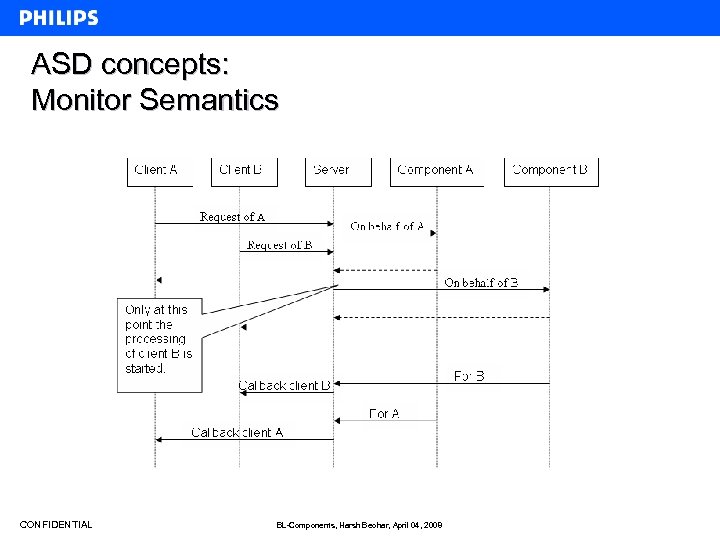
ASD concepts: Monitor Semantics CONFIDENTIAL BL-Components, Harsh Beohar, April 04, 2008
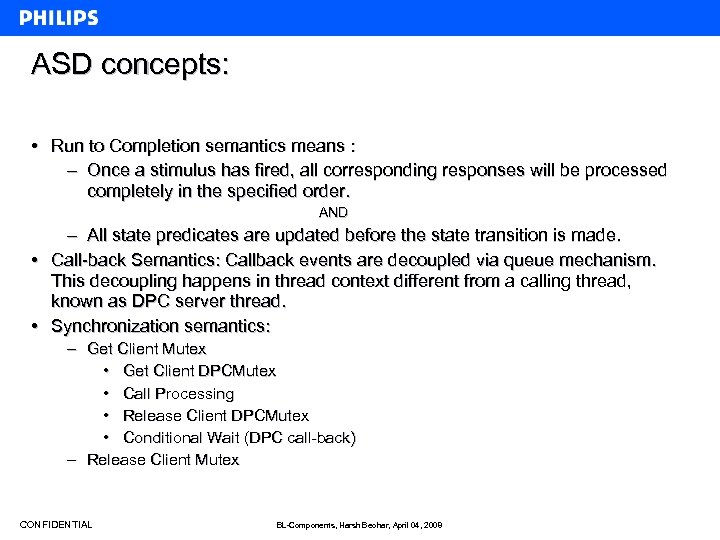
ASD concepts: • Run to Completion semantics means : – Once a stimulus has fired, all corresponding responses will be processed completely in the specified order. AND – All state predicates are updated before the state transition is made. • Call-back Semantics: Callback events are decoupled via queue mechanism. This decoupling happens in thread context different from a calling thread, known as DPC server thread. • Synchronization semantics: – Get Client Mutex • Get Client DPCMutex • Call Processing • Release Client DPCMutex • Conditional Wait (DPC call-back) – Release Client Mutex CONFIDENTIAL BL-Components, Harsh Beohar, April 04, 2008
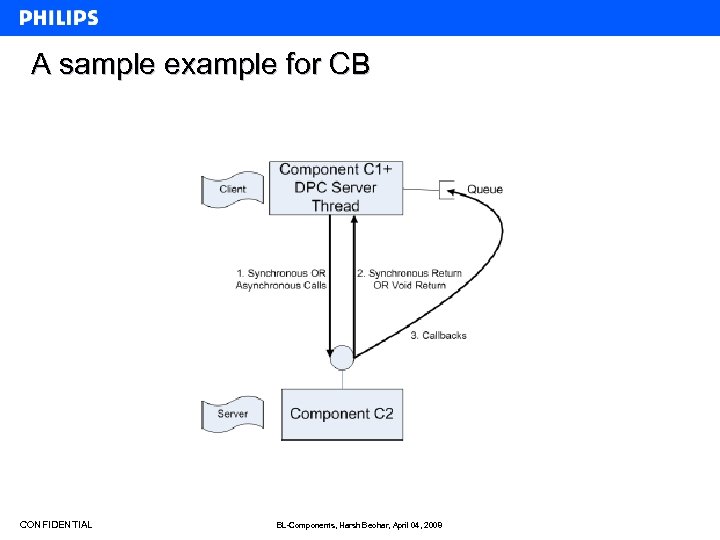
A sample example for CB CONFIDENTIAL BL-Components, Harsh Beohar, April 04, 2008
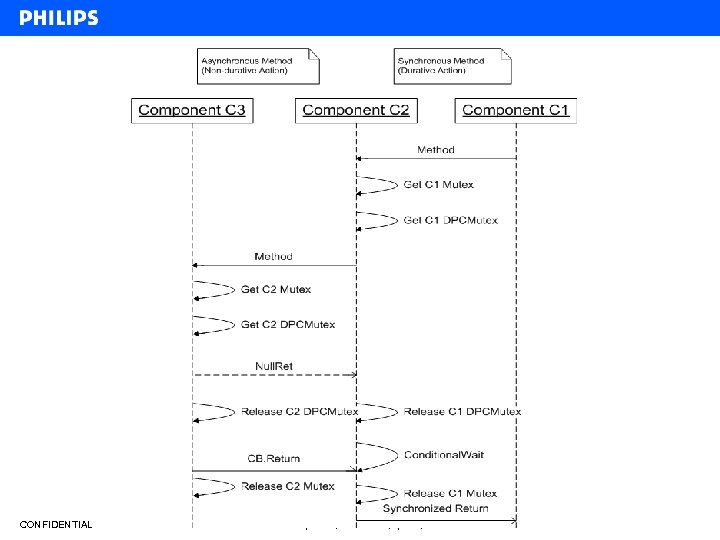
CONFIDENTIAL BL-Components, Harsh Beohar, April 04, 2008
![Events with parameters • Chan. Stim[i>>]: specifies that the parameter value ‘i’ will be Events with parameters • Chan. Stim[i>>]: specifies that the parameter value ‘i’ will be](https://present5.com/presentation/21a14e32c7b5080e29f236c926e61228/image-16.jpg)
Events with parameters • Chan. Stim[i>>]: specifies that the parameter value ‘i’ will be captured on entry into a context variable associated with the name ‘i’. To be meaningful, ‘i’ should be an “in” parameter. • Chan. Stim[i<<]: to denote ‘i’ is an out parameter. • Chan. Rsp[i>>]: to denote ‘i’ is an in parameter. • Chan. Rsp[i<<]: to denote ‘i’ is an out parameter. • Chan. event[$x]: x is a literal (usually used for enumerated constant. ) • Parameters are removed from event in generation of CSP scripts. • Callback Events should not have an out parameter. CONFIDENTIAL BL-Components, Harsh Beohar, April 04, 2008
Introduction to Be. X Controller • Workflow is based on the concept of centralized controller, named as Orchestration Controller. • Aim is to design this Orchestration Controller using ASD and provide it as a study model. • An orchestration scenario comprises a number of ordered stimuli to realise an overall system function that involves multiple units. • It is a logical flow of messages/stimuli between the Orchestration Controller and other units in the System. CONFIDENTIAL BL-Components, Harsh Beohar, April 04, 2008 17

Some terminology • System: collection of software components one is interested in specifying. • Environment: all entities external to the system with which the system (when implemented) directly communicates. • Stimuli: Events (inputs, interrupts, invocations) in environment which can affect system behavior. • Responses: System behavior[s] which are observable in the environment. • These above definitions are very helpful to make a context diagram. CONFIDENTIAL BL-Components, Harsh Beohar, April 04, 2008 18
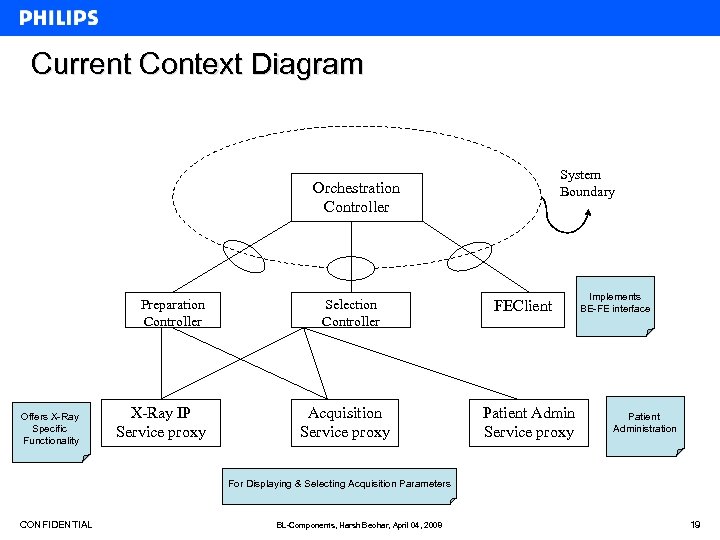
Current Context Diagram System Boundary Orchestration Controller Preparation Controller Offers X-Ray Specific Functionality X-Ray IP Service proxy Selection Controller Acquisition Service proxy FEClient Patient Admin Service proxy Implements BE-FE interface Patient Administration For Displaying & Selecting Acquisition Parameters CONFIDENTIAL BL-Components, Harsh Beohar, April 04, 2008 19
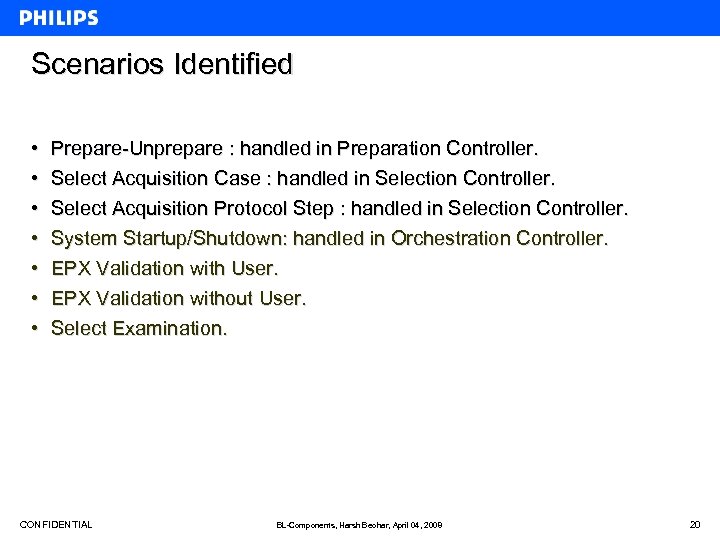
Scenarios Identified • • Prepare-Unprepare : handled in Preparation Controller. Select Acquisition Case : handled in Selection Controller. Select Acquisition Protocol Step : handled in Selection Controller. System Startup/Shutdown: handled in Orchestration Controller. EPX Validation with User. EPX Validation without User. Select Examination. CONFIDENTIAL BL-Components, Harsh Beohar, April 04, 2008 20
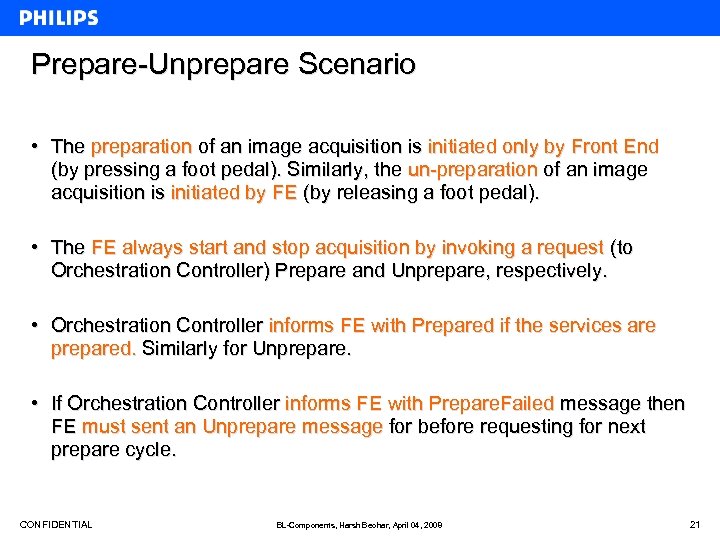
Prepare-Unprepare Scenario • The preparation of an image acquisition is initiated only by Front End (by pressing a foot pedal). Similarly, the un-preparation of an image acquisition is initiated by FE (by releasing a foot pedal). • The FE always start and stop acquisition by invoking a request (to Orchestration Controller) Prepare and Unprepare, respectively. • Orchestration Controller informs FE with Prepared if the services are prepared. Similarly for Unprepare. • If Orchestration Controller informs FE with Prepare. Failed message then FE must sent an Unprepare message for before requesting for next prepare cycle. CONFIDENTIAL BL-Components, Harsh Beohar, April 04, 2008 21
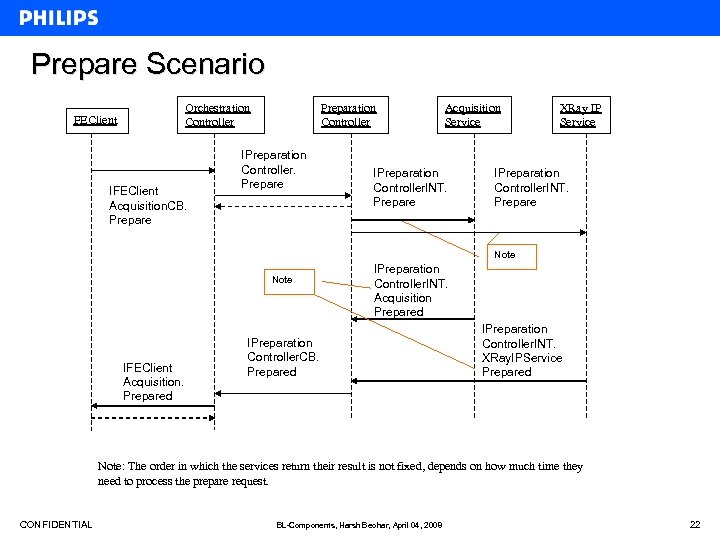
Prepare Scenario Orchestration Controller FEClient IFEClient Acquisition. CB. Prepare Preparation Controller IPreparation Controller. Prepare Acquisition Service IPreparation Controller. INT. Prepare XRay IP Service IPreparation Controller. INT. Prepare Note IFEClient Acquisition. Prepared IPreparation Controller. INT. Acquisition Prepared IPreparation Controller. CB. Prepared IPreparation Controller. INT. XRay. IPService Prepared Note: The order in which the services return their result is not fixed, depends on how much time they need to process the prepare request. CONFIDENTIAL BL-Components, Harsh Beohar, April 04, 2008 22

Decisions Made • Prepare-Unprepare Scenarios : – The orchestration-controller will send a Prepare command to the services for next run even though the after-run-data for current run has not yet been received. – The services will prepare and send Prepared/Prepare. Failed to the orchestration controller. – The orchestration-controller will then wait for the after-run-data from the FE (with a time-out). – If After. Run. Data is received, Orchestration will send prepared to FE upon receiving the After. Run. Data and handle the After. Run. Data asynchronously. CONFIDENTIAL BL-Components, Harsh Beohar, April 04, 2008 23
![Mealy Machine* For Preparation Controller *=Exact [Stimuli & Predicate]/Res ponse can be found in Mealy Machine* For Preparation Controller *=Exact [Stimuli & Predicate]/Res ponse can be found in](https://present5.com/presentation/21a14e32c7b5080e29f236c926e61228/image-24.jpg)
Mealy Machine* For Preparation Controller *=Exact [Stimuli & Predicate]/Res ponse can be found in excel sheet. Sorry for slight abuse of notation for the sake of simplicity in the figure. CONFIDENTIAL BL-Components, Harsh Beohar, April 04, 2008 24
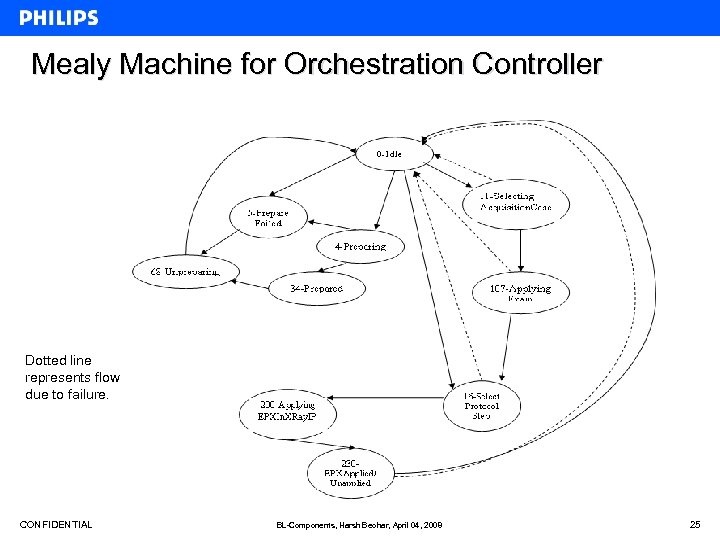
Mealy Machine for Orchestration Controller Dotted line represents flow due to failure. CONFIDENTIAL BL-Components, Harsh Beohar, April 04, 2008 25
Further Work. • Represent the remaining scenarios as Sequence Based Specification (in Excel Sheet). • Model Check – Preparation Controller (Interface Model), – PAACSelector (Interface Model), and – Orchestration Controller (Design Model). – Does Individual components and components under parallel composition are deadlock free, live lock free? • Still to explore code-generation limitations and test case generation while using ASD. CONFIDENTIAL BL-Components, Harsh Beohar, April 04, 2008 26
ASD Limitations. • Routing a message from any Service to the Orchestration Controller [w. r. t Context Diagram] becomes complex as compared to implementation in any high level language. • ASD assumes if processes are in different process boundaries then the channel which provides communication is ideal (it will never breakdown). • Unable to describe how to transform data, whether data is to be stored persistently. • A complete system is impossible to design and verify in ASD if foreign components are present. A foreign component is generally a handwritten component or a component whose implementation is generated by other tools. • Only suited to design systems having complex state behavior. CONFIDENTIAL BL-Components, Harsh Beohar, April 04, 2008
Conclusions • Design can be rigorously verified against their requirements and interface specification. • ASD (in particular SBS method) helps in making design decisions. • Not for a complete system, but the test cases to ASD components can be generated. (by selecting an option “usage model” in the plug-in. ) • Compared to conventional software development lifecycle, design errors can be found before implementation phase. • This methodology is understandable to all project stakeholders. CONFIDENTIAL BL-Components, Harsh Beohar, April 04, 2008
![References • [1] Guy Broadfoot and Philippa J. Hopcroft. An Analytical Software Design System. References • [1] Guy Broadfoot and Philippa J. Hopcroft. An Analytical Software Design System.](https://present5.com/presentation/21a14e32c7b5080e29f236c926e61228/image-29.jpg)
References • [1] Guy Broadfoot and Philippa J. Hopcroft. An Analytical Software Design System. World Intellectual Property Organization, Nov 2005. • [2] Harlan D. Mills, Richard C. Linger, and Alan R. Hevner. Principles of Information Systems Analysis and Design. Academic Press Professional, CA, USA, 1986. • [3] S. J. Prowell and J. H. Poore. Foundations of Sequence-Based Software Specification. IEEE Trans. Of Soft. Eng. , 2003 • [4] Guy Broadfoot and Philippa J. Hopcroft. Combining the Box Structured development method and CSP. In Proceedings of 19 th IEEE International Conference on Automated Software Engineering, 2004. CONFIDENTIAL BL-Components, Harsh Beohar, April 04, 2008
21a14e32c7b5080e29f236c926e61228.ppt