1e2991d51d3fb7805fdcad8e88d92041.ppt
- Количество слайдов: 43

Application Delivery Network for Microsoft Radovan Gibala R. Gibala@f 5. com
2 Agenda Application Ready Network – Introduction & Benefits Basic Components of ARN – Availability – Performance – Security Deployment Infrastructure for Microsoft Applications Exchange – Deployment Guides Share. Point – Deployment Guides Integration with MOM
3 IT Challenge - Out of Control Applications and networks behave independently Many network functions require high degrees of manual intervention Distributed architectures and web services increase complexity Historically, applications and protocols for communicating with network devices inflexible at best ! RESULT: Applications and Networks operate without regard to each other limiting scale, performance, reliability, and security
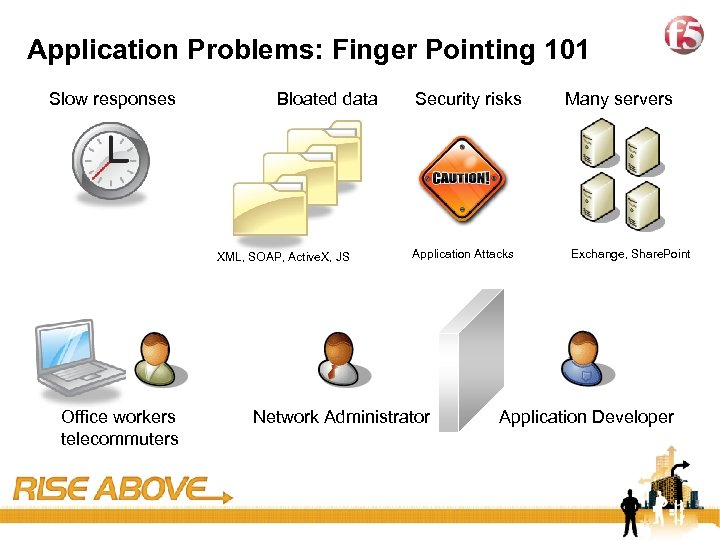
4 Application Problems: Finger Pointing 101 Slow responses Bloated data XML, SOAP, Active. X, JS Office workers telecommuters Security risks Application Attacks Network Administrator Many servers Exchange, Share. Point Application Developer
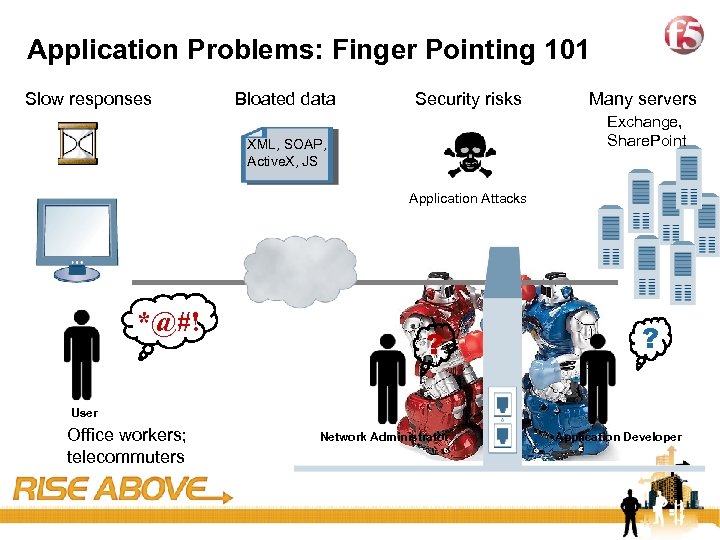
5 Application Problems: Finger Pointing 101 Slow responses Bloated data Security risks Many servers Exchange, Share. Point XML, SOAP, Active. X, JS Application Attacks *@#! ? ? User Office workers; telecommuters Network Administrator Application Developer

6 10 Most Common Deployment Mistakes 1 Lack of end-user involvement or it happens at the end (too late) 2 The solution is ‘thrown over the wall’ to the infrastructure team! 3 No clear session management approach 4 No clear separation of business logic from the user interface 5 There is no predictable build process of the solution 6 Testers are testing the developers – but who is testing the testers? 7 Performance & security design is kept till the end of the project 8 Browser compatibility is on the agenda yet testing is under estimated 9 Accessibility, globalization and localization are forgotten 10 In accurate project estimates, lack of financial control and frequent financial/time reconciliation processes Note: The majority of these are infrastructure and process issues. Source: Vajira Weerasekera Principal Consultant – Microsoft Solutions Development Center
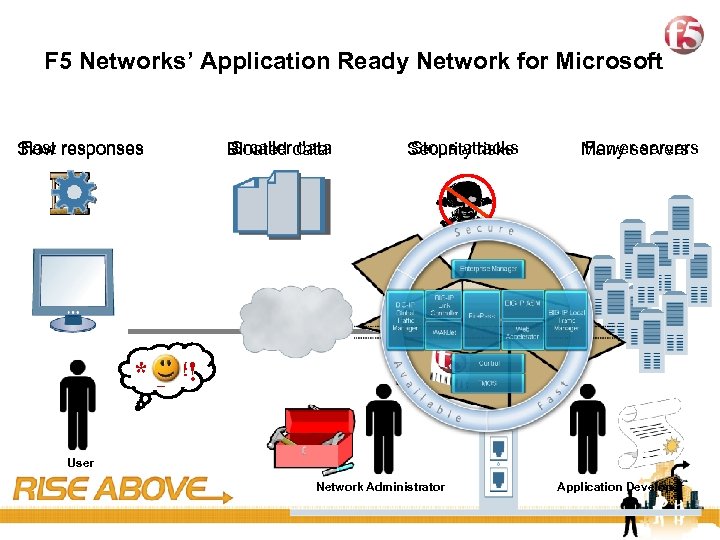
7 F 5 Networks’ Application Ready Network for Microsoft Fast Slow responses Smaller data Bloated data Stops attacks Security risks Fewer servers Many servers *@#! User Network Administrator Application Developer
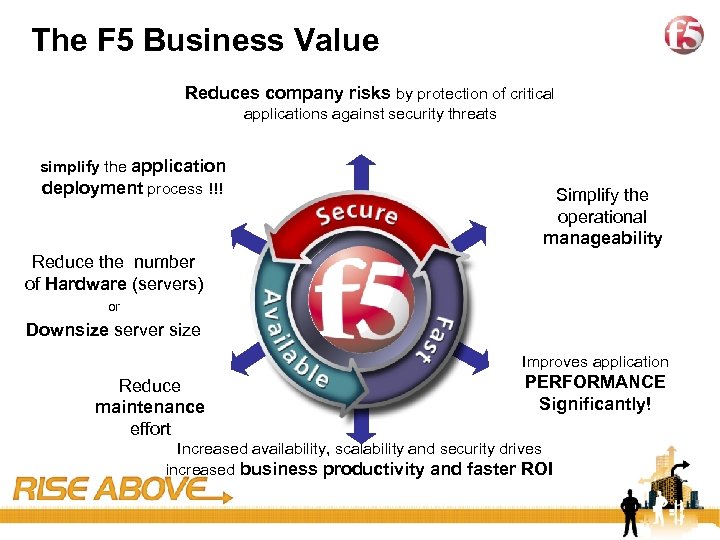
8 The F 5 Business Value Reduces company risks by protection of critical applications against security threats simplify the application deployment process !!! Simplify the operational manageability Reduce the number of Hardware (servers) or Downsize server size Improves application Reduce maintenance effort PERFORMANCE Significantly! Increased availability, scalability and security drives increased business productivity and faster ROI
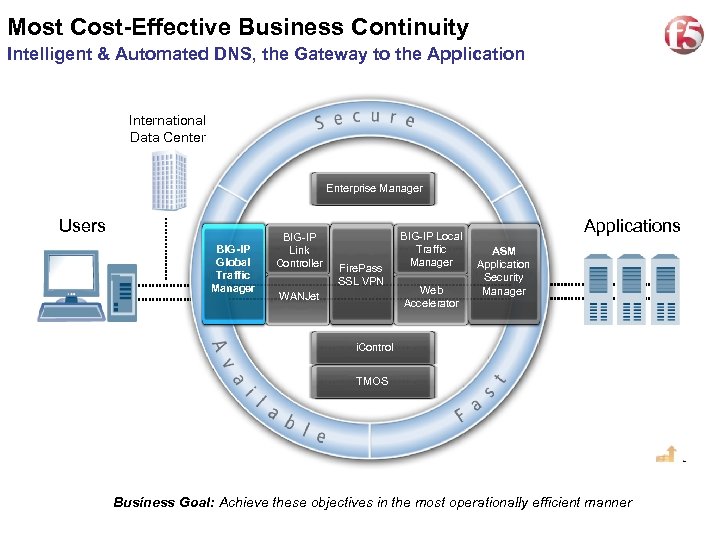
9 Most Cost-Effective Business Continuity Intelligent & Automated DNS, the Gateway to the Application International Data Center Enterprise Manager Users BIG-IP Global Traffic Manager BIG-IP Link Controller Fire. Pass SSL VPN WANJet BIG-IP Local Traffic Manager Web Accelerator Applications ASM Application Security Manager i. Control TMOS Business Goal: Achieve these objectives in the most operationally efficient manner
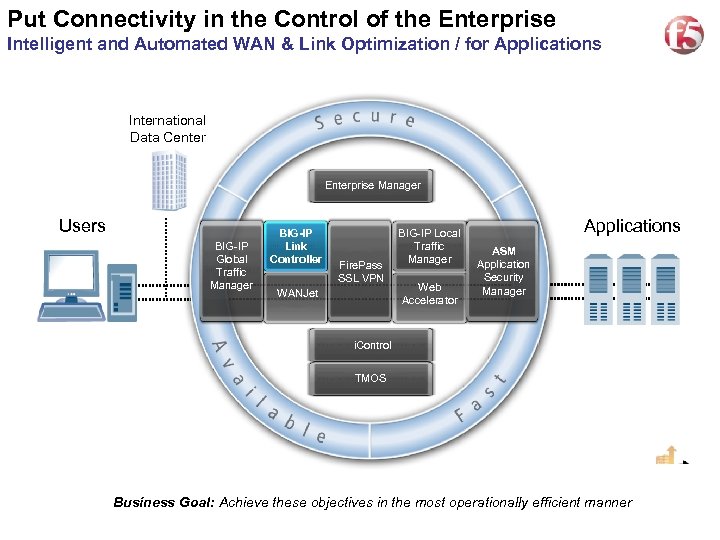
Put Connectivity in the Control of the Enterprise 10 Intelligent and Automated WAN & Link Optimization / for Applications International Data Center Enterprise Manager Users BIG-IP Global Traffic Manager BIG-IP Link Controller Fire. Pass SSL VPN WANJet BIG-IP Local Traffic Manager Web Accelerator Applications ASM Application Security Manager i. Control TMOS Business Goal: Achieve these objectives in the most operationally efficient manner
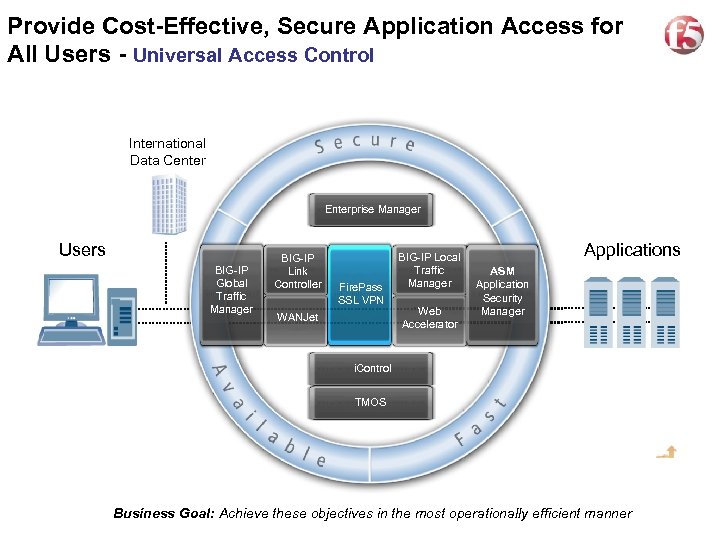
Provide Cost-Effective, Secure Application Access for All Users - Universal Access Control International Data Center Enterprise Manager Users BIG-IP Global Traffic Manager BIG-IP Link Controller Fire. Pass SSL VPN WANJet BIG-IP Local Traffic Manager Web Accelerator Applications ASM Application Security Manager i. Control TMOS Business Goal: Achieve these objectives in the most operationally efficient manner 11
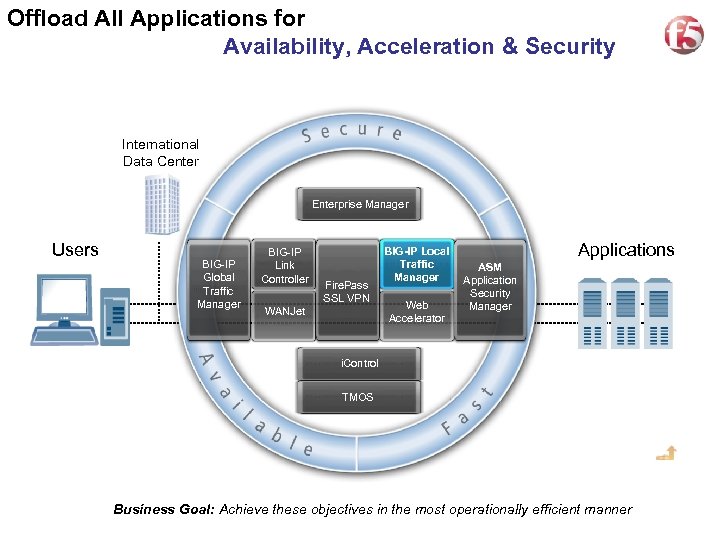
Offload All Applications for Availability, Acceleration & Security International Data Center Enterprise Manager Users BIG-IP Global Traffic Manager BIG-IP Link Controller Fire. Pass SSL VPN WANJet BIG-IP Local Traffic Manager Web Accelerator Applications ASM Application Security Manager i. Control TMOS Business Goal: Achieve these objectives in the most operationally efficient manner 12
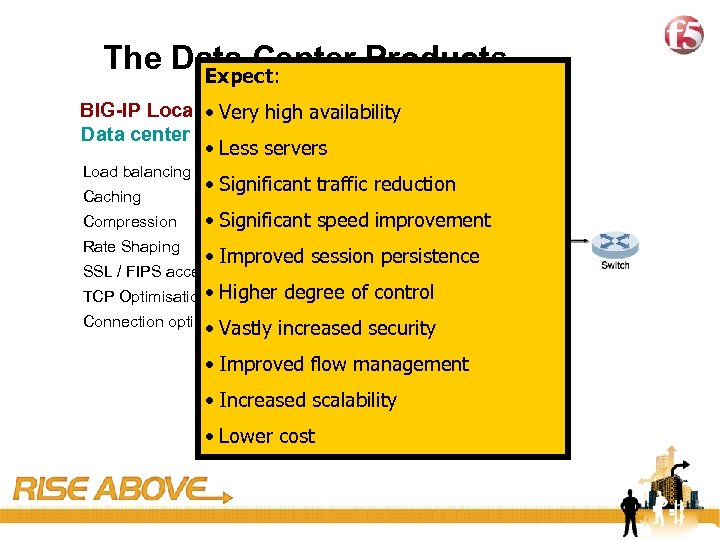
13 The Data Center Products Expect: BIG-IP Local Traffichigh availability • Very Manager Data center optimization • Less servers Load balancing Caching • Significant traffic reduction Compression • Significant speed improvement Rate Shaping • Improved session persistence SSL / FIPS acceleration TCP Optimisation • Higher degree of control Connection optimisation • Vastly increased security • Improved flow management • Increased scalability • Lower cost
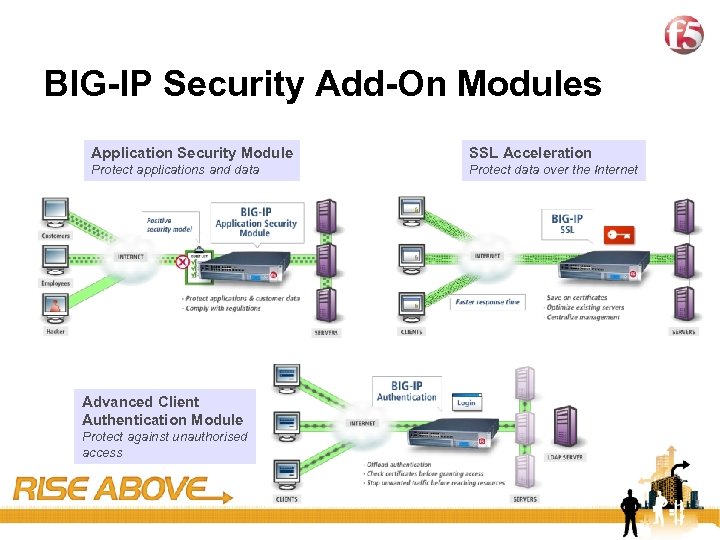
14 BIG-IP Security Add-On Modules Application Security Module SSL Acceleration Protect applications and data Protect data over the Internet Advanced Client Authentication Module Protect against unauthorised access
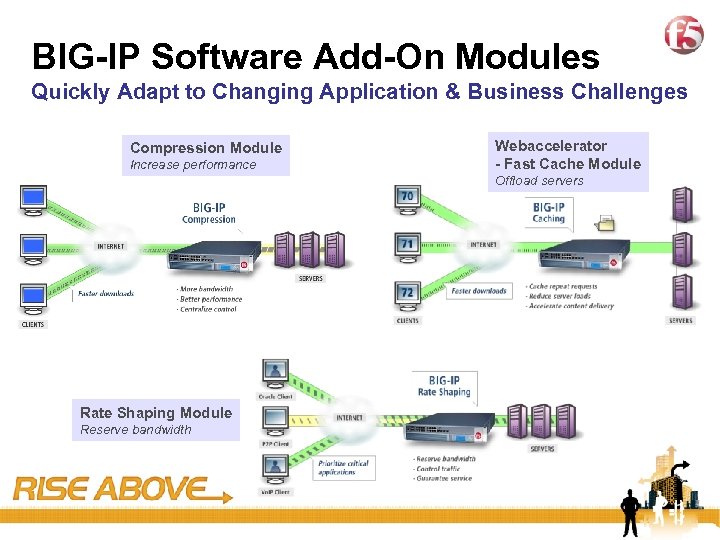
15 BIG-IP Software Add-On Modules Quickly Adapt to Changing Application & Business Challenges Compression Module Increase performance Webaccelerator - Fast Cache Module Offload servers Rate Shaping Module Reserve bandwidth
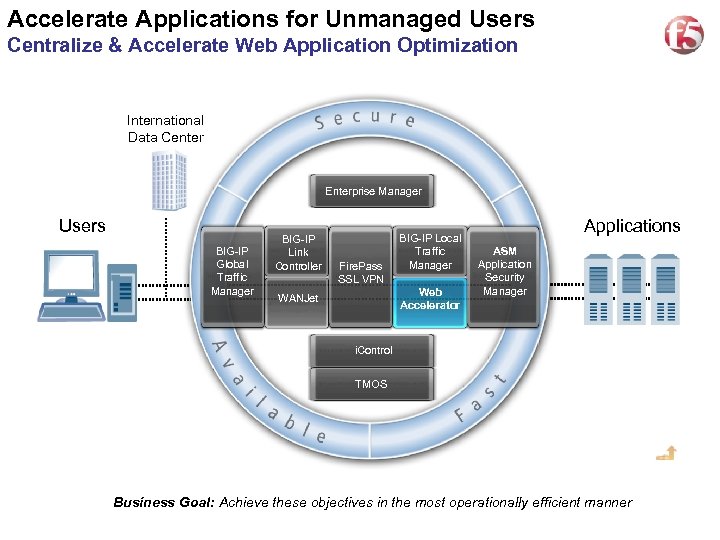
Accelerate Applications for Unmanaged Users 16 Centralize & Accelerate Web Application Optimization International Data Center Enterprise Manager Users BIG-IP Global Traffic Manager BIG-IP Link Controller Fire. Pass SSL VPN BIG-IP Local Traffic Manager Web Accelerator WANJet Applications ASM Application Security Manager i. Control TMOS Business Goal: Achieve these objectives in the most operationally efficient manner
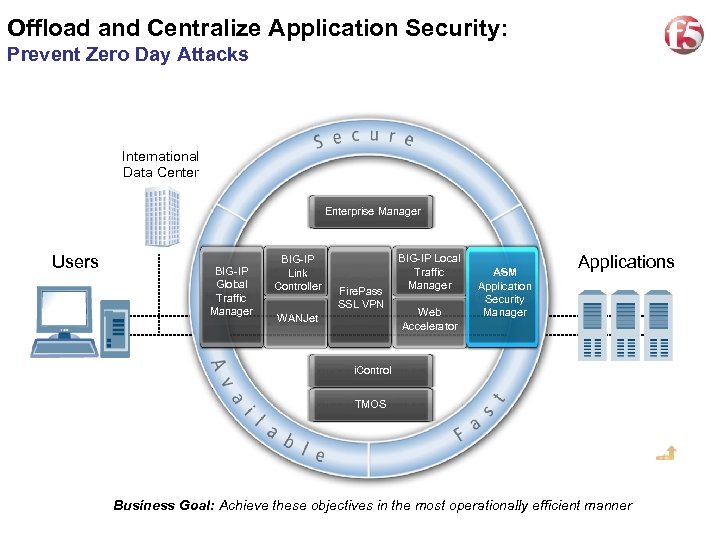
17 Offload and Centralize Application Security: Prevent Zero Day Attacks International Data Center Enterprise Manager Users BIG-IP Global Traffic Manager BIG-IP Link Controller Fire. Pass SSL VPN WANJet BIG-IP Local Traffic Manager Web Accelerator ASM Application Security Manager Applications i. Control TMOS Business Goal: Achieve these objectives in the most operationally efficient manner
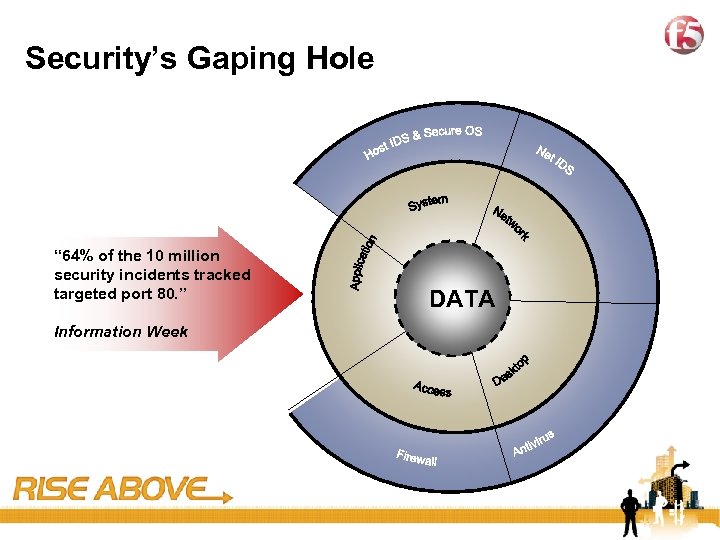
18 Security’s Gaping Hole “ 64% of the 10 million security incidents tracked targeted port 80. ” Information Week DATA
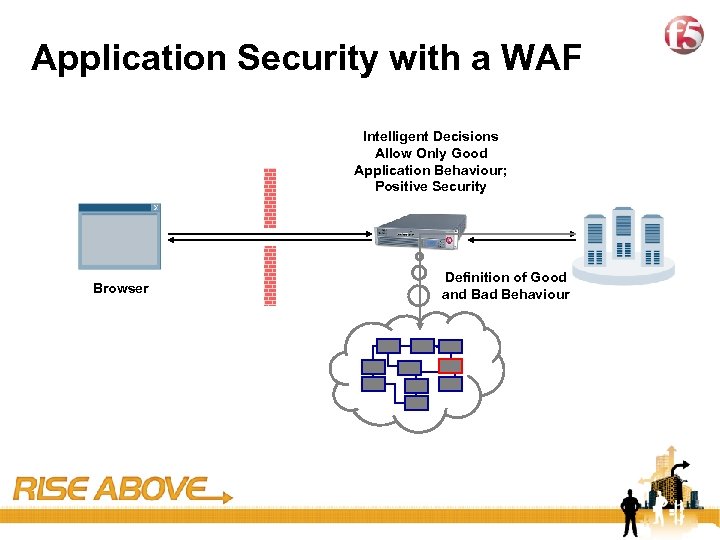
19 Application Security with a WAF Intelligent Decisions Allow Only Good Application Behaviour; Positive Security Browser Definition of Good and Bad Behaviour
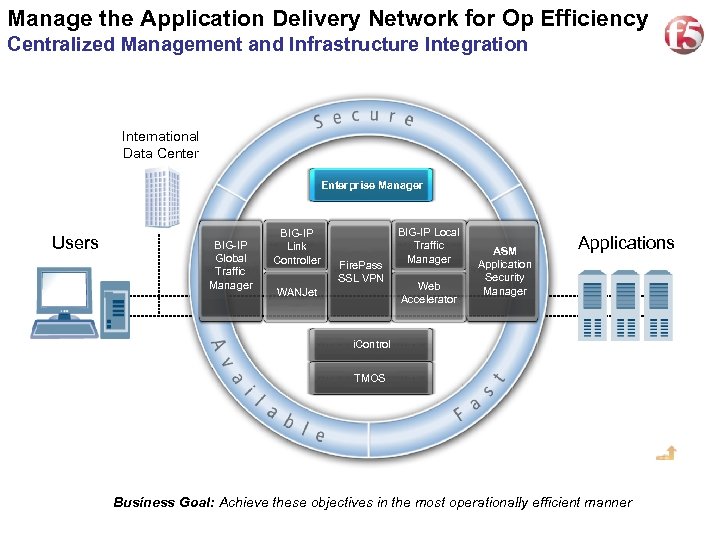
Manage the Application Delivery Network for Op Efficiency Centralized Management and Infrastructure Integration International Data Center Enterprise Manager Users BIG-IP Global Traffic Manager BIG-IP Link Controller Fire. Pass SSL VPN WANJet BIG-IP Local Traffic Manager Web Accelerator ASM Application Security Manager Applications i. Control TMOS Business Goal: Achieve these objectives in the most operationally efficient manner 20
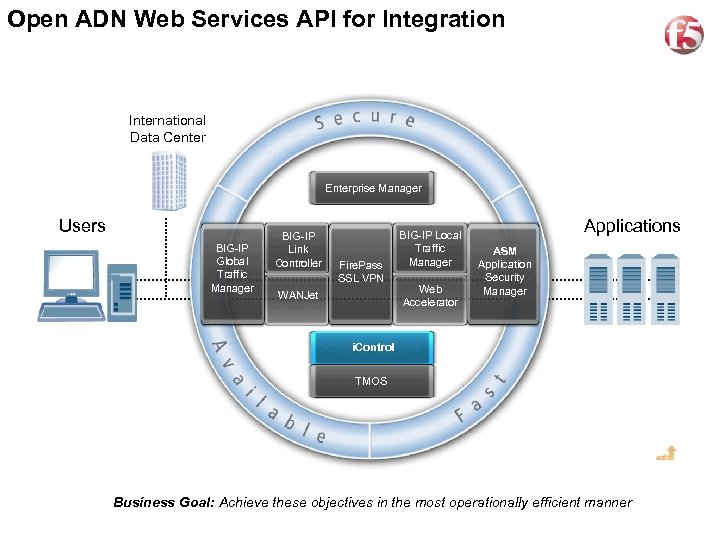
Open ADN Web Services API for Integration 21 International Data Center Enterprise Manager Users BIG-IP Global Traffic Manager BIG-IP Link Controller Fire. Pass SSL VPN WANJet BIG-IP Local Traffic Manager Web Accelerator Applications ASM Application Security Manager i. Control TMOS Business Goal: Achieve these objectives in the most operationally efficient manner
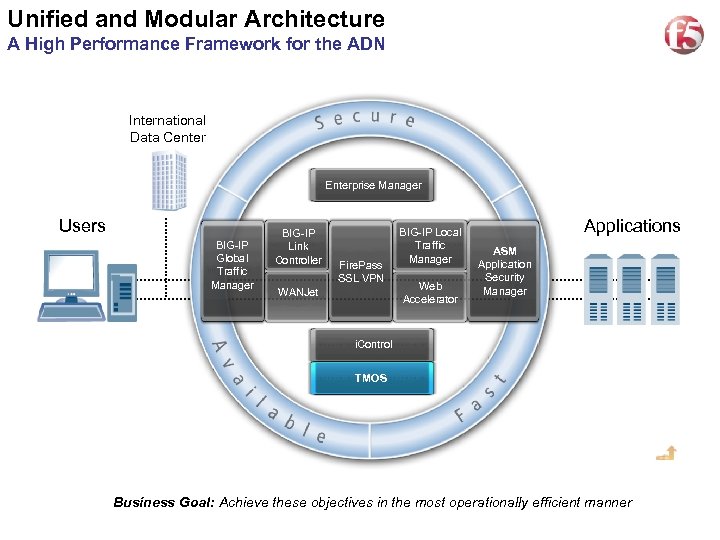
Unified and Modular Architecture 22 A High Performance Framework for the ADN International Data Center Enterprise Manager Users BIG-IP Global Traffic Manager BIG-IP Link Controller Fire. Pass SSL VPN WANJet BIG-IP Local Traffic Manager Web Accelerator Applications ASM Application Security Manager i. Control TMOS Business Goal: Achieve these objectives in the most operationally efficient manner
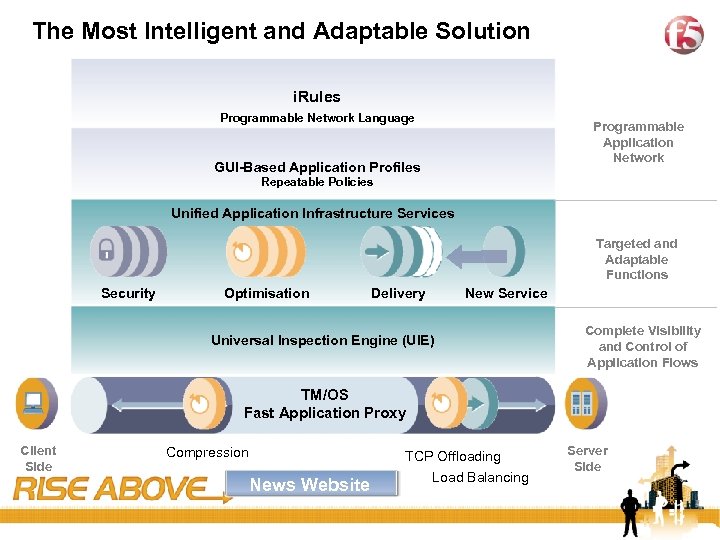
23 The Most Intelligent and Adaptable Solution i. Rules Programmable Network Language Programmable Application Network GUI-Based Application Profiles Repeatable Policies Unified Application Infrastructure Services Targeted and Adaptable Functions Security Optimisation Delivery New Service Universal Inspection Engine (UIE) Complete Visibility and Control of Application Flows TM/OS Fast Application Proxy Client Side Compression TCP Offloading News Website Load Balancing Server Side

24 Deployment Guides
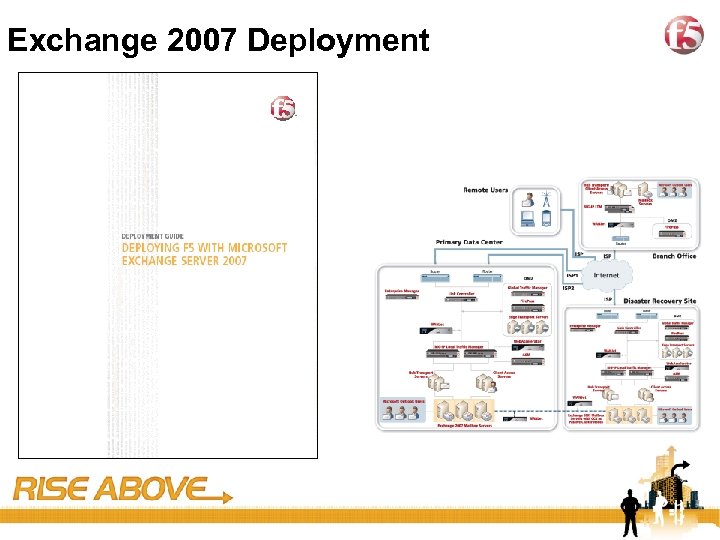
25 Exchange 2007 Deployment
26 F 5 Benefits for Exchange 2007 Reliable, Real-Time Availability Optimized Data Replication Between Data Centers. More Data, Less Time Secure Point-To-Point Data Replication Efficiently Use Existing Bandwidth == Less $$
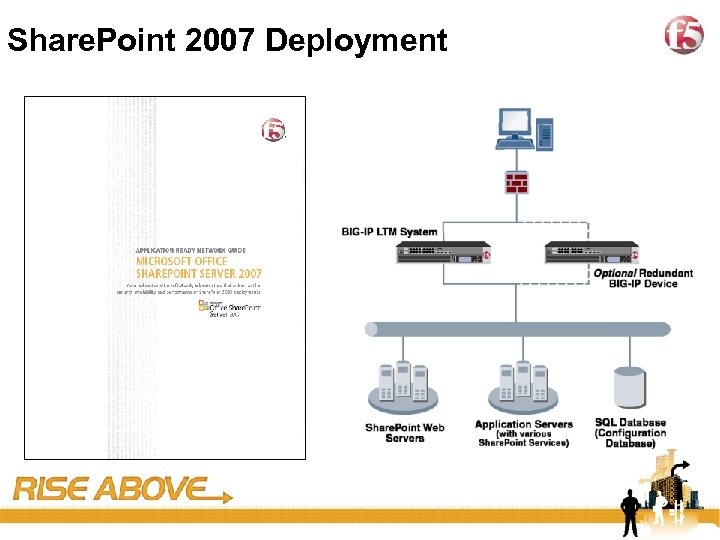
27 Share. Point 2007 Deployment
28 F 5’s Benefits for Share. Point Increase Share. Point Server Performance by 5 x 20 -30% Bandwidth Reduction for Remote Users Gain 25+% Server Capacity with Service Offload Reduce Time-Out Errors by 85% for Mobile Users Automated Failover and Access Control
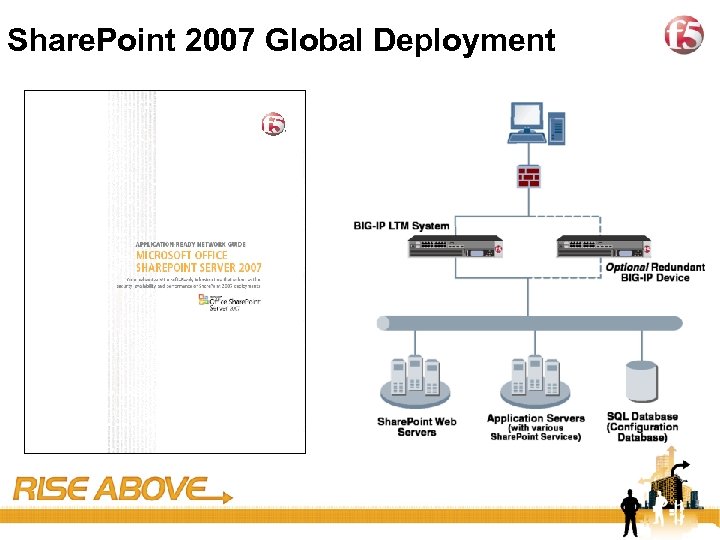
29 Share. Point 2007 Global Deployment

30 Global Application Health Application Aware Monitoring: Back-end system goes down, entire application is taken down and users are re-routed Global Failover Based on Application Health, Not Just Server and Data Center Health Lose an app in Warszawa, Redirect Users to Praha, Transparently Full Integration From Remote Data Centers Down to Users
31 Application Security and User Control
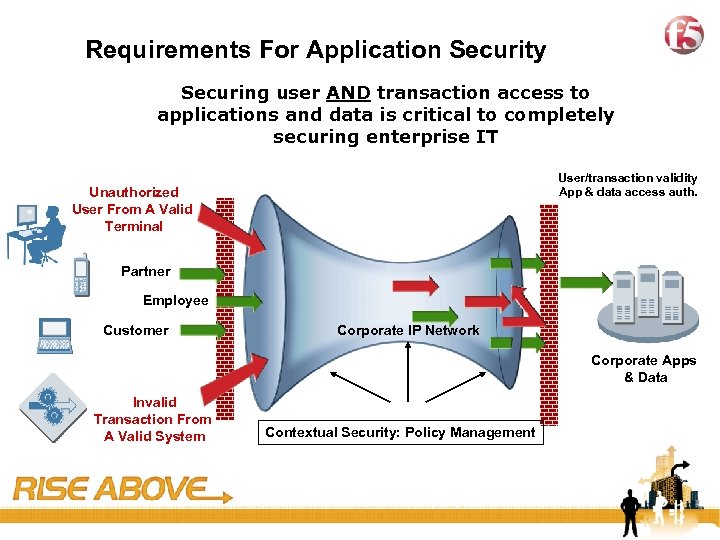
32 Requirements For Application Security Securing user AND transaction access to applications and data is critical to completely securing enterprise IT User/transaction validity App & data access auth. Unauthorized User From A Valid Terminal Partner Employee Customer Corporate IP Network Corporate Apps & Data Invalid Transaction From A Valid System Contextual Security: Policy Management

33 F 5 Sharepoint Security Benefits Secure Session Management Inline Reverse Proxy Sees All Data, Requests and Responses Granular Application Control Session-Based Policy Management Accountability: Audit Trail Application Delivery Security
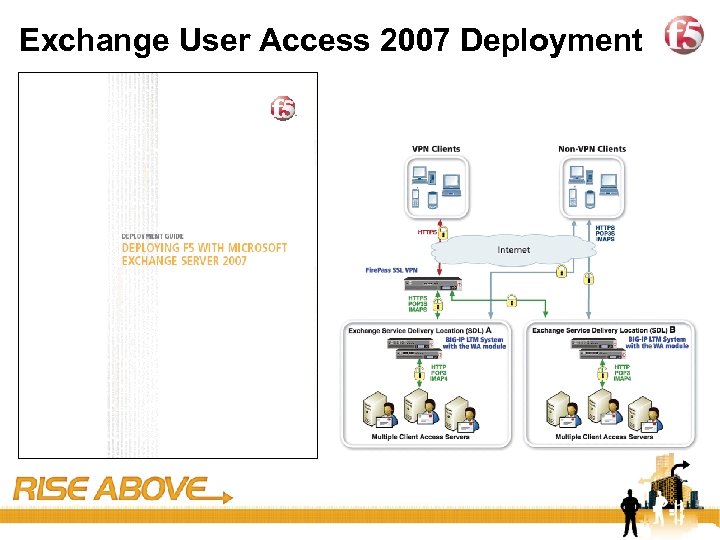
34 Exchange User Access 2007 Deployment
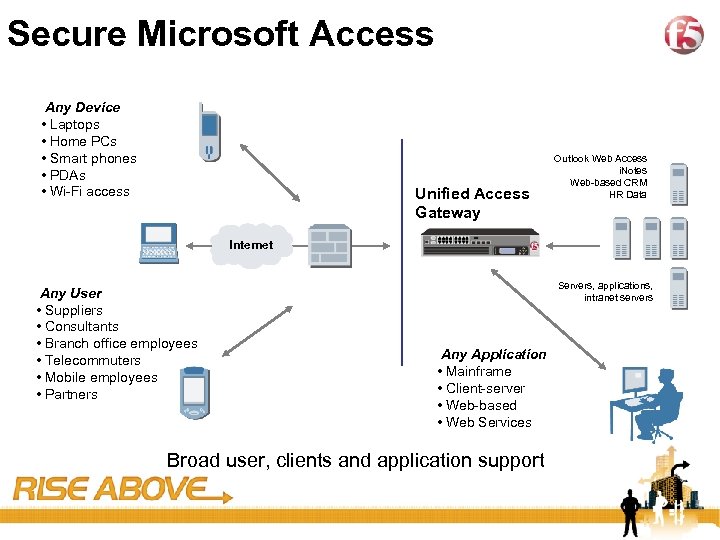
35 Secure Microsoft Access Any Device • Laptops • Home PCs • Smart phones • PDAs • Wi-Fi access Unified Access Gateway Outlook Web Access i. Notes Web-based CRM HR Data Internet Any User • Suppliers • Consultants • Branch office employees • Telecommuters • Mobile employees • Partners Servers, applications, intranet servers Any Application • Mainframe • Client-server • Web-based • Web Services Broad user, clients and application support
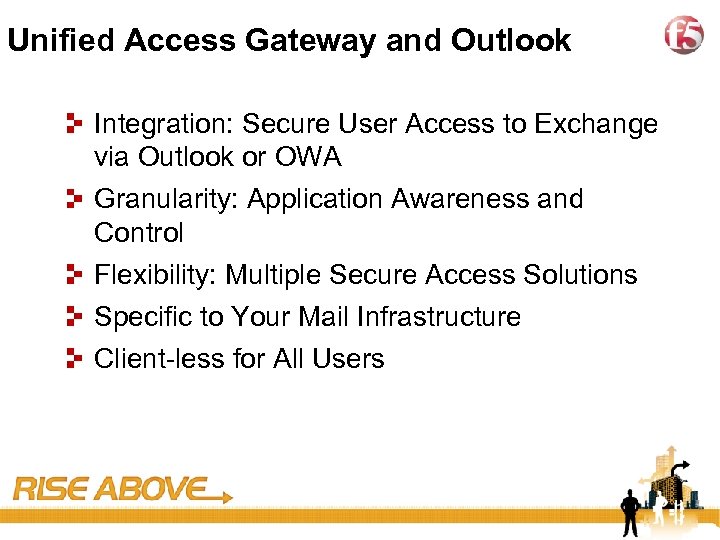
36 Unified Access Gateway and Outlook Integration: Secure User Access to Exchange via Outlook or OWA Granularity: Application Awareness and Control Flexibility: Multiple Secure Access Solutions Specific to Your Mail Infrastructure Client-less for All Users
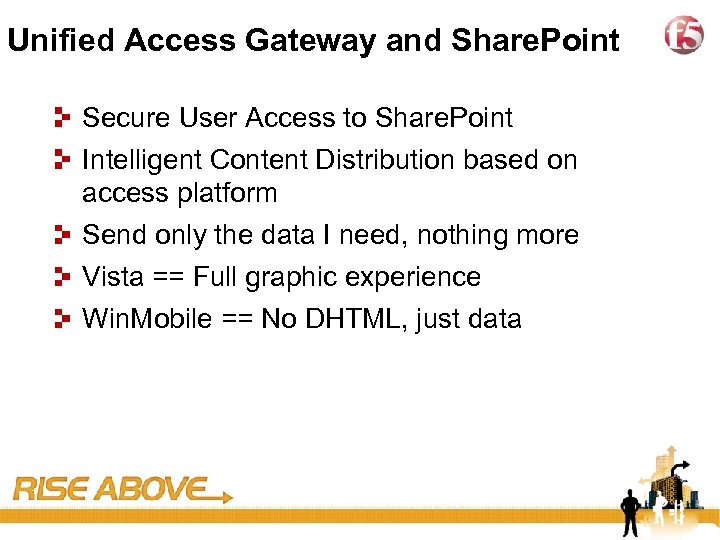
37 Unified Access Gateway and Share. Point Secure User Access to Share. Point Intelligent Content Distribution based on access platform Send only the data I need, nothing more Vista == Full graphic experience Win. Mobile == No DHTML, just data

38 F 5 Security/Windows Interoperability Vista GINA integration Internet Explorer 7 support Windows Installer Auto-launch Web App. Tunnels Enhanced user-session variables for Active Directory, and networking

39 Call To Action
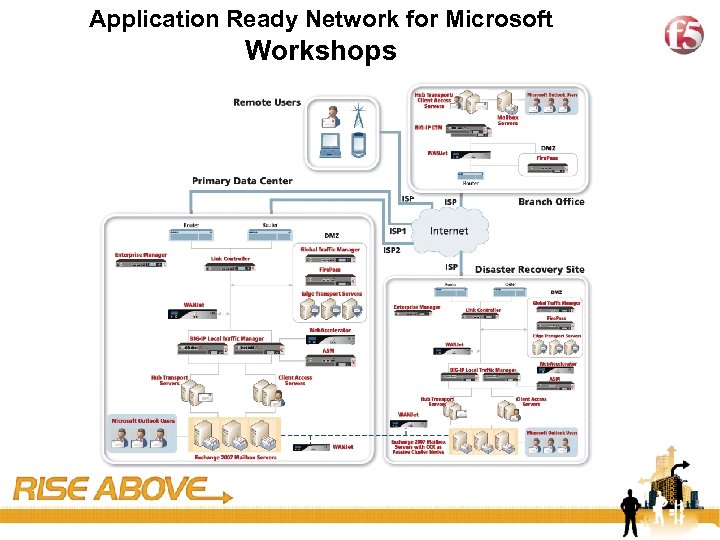
Application Ready Network for Microsoft Workshops 40

41 MTC Engagement Types Strategy briefings Architecture design session – customised session Proof of Concept workshop MTC locations in EMEA - Copenhagen, Denmark - Dubai, UAE - Munich, Germany - Paris, France - Thames Valley, UK

42 F 5 Technology Center Hosted Strategy Briefings Architecture Design – Customized Sessions On-site Technical Expertise Proof of Concept, Real-World Implementation Located At F 5 Headquarters in Seattle, WA
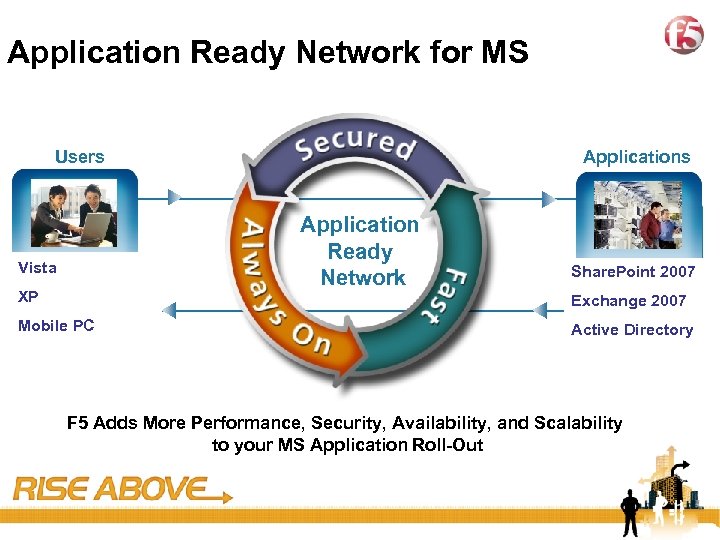
43 Application Ready Network for MS Users At Vista Home In the Office XP the Road On Mobile PC Applications Application Ready Network SAP Share. Point 2007 Exchange 2007 Oracle Active Directory F 5 Adds More Performance, Security, Availability, and Scalability to your MS Application Roll-Out
1e2991d51d3fb7805fdcad8e88d92041.ppt