5a3519381f5538268360a86819910bea.ppt
- Количество слайдов: 21
 Application Data Security Stallion Winter Seminar 2009 Otepää, March 06 th 2009
Application Data Security Stallion Winter Seminar 2009 Otepää, March 06 th 2009
 Agenda § Corporate Overview § Application Data Security § Introduction to Imperva Solutions § Why Customers Select Imperva 2 - CONFIDENTIAL -
Agenda § Corporate Overview § Application Data Security § Introduction to Imperva Solutions § Why Customers Select Imperva 2 - CONFIDENTIAL -
 Why Should You Care? 85% of organizations have experienced a data breach Theft, Abuse, Misuse & Leakage Happen Even in Leading Organizations Sources: Privacy Rights Clearinghouse & Ponemon Institute Survey, “The Business Impact of Data Breach” 3 - CONFIDENTIAL -
Why Should You Care? 85% of organizations have experienced a data breach Theft, Abuse, Misuse & Leakage Happen Even in Leading Organizations Sources: Privacy Rights Clearinghouse & Ponemon Institute Survey, “The Business Impact of Data Breach” 3 - CONFIDENTIAL -
 Why Should You Care? Governing your data is not optional PCI – Required to process credit card transaction SOX – Required to report financial results HIPAA – Required to store Patient Health Data 4 - CONFIDENTIAL -
Why Should You Care? Governing your data is not optional PCI – Required to process credit card transaction SOX – Required to report financial results HIPAA – Required to store Patient Health Data 4 - CONFIDENTIAL -
 Security and Compliance Requirements § Full Visibility § Who is accessing your data? § Who has accessed your data? § Granular Controls § Who is attacking your data and how? § Is your data leaking outside the organization? § How do you protect your data? Imperva delivers the industry’s most robust and widely deployed solution for addressing the entire application data security lifecycle. 5 - CONFIDENTIAL -
Security and Compliance Requirements § Full Visibility § Who is accessing your data? § Who has accessed your data? § Granular Controls § Who is attacking your data and how? § Is your data leaking outside the organization? § How do you protect your data? Imperva delivers the industry’s most robust and widely deployed solution for addressing the entire application data security lifecycle. 5 - CONFIDENTIAL -
 Imperva Overview § Founded in 2002 § The leader in Application Data Security § Global company with int’l revenue consisting of 40%+ § § North American HQ in California; International HQ in Israel Local presence in all major markets (EMEA, APAC, Japan) Customers in 35 countries Strong global network of channel partners § Over 700 customers and 4500+ organizations protected § Shlomo Kramer, CEO & President § SC Magazine 2008 CEO of the Year § One of three founders of Check Point 6 - CONFIDENTIAL -
Imperva Overview § Founded in 2002 § The leader in Application Data Security § Global company with int’l revenue consisting of 40%+ § § North American HQ in California; International HQ in Israel Local presence in all major markets (EMEA, APAC, Japan) Customers in 35 countries Strong global network of channel partners § Over 700 customers and 4500+ organizations protected § Shlomo Kramer, CEO & President § SC Magazine 2008 CEO of the Year § One of three founders of Check Point 6 - CONFIDENTIAL -
 Imperva Application Defense Center § Application Data Security experts § Research the latest threats and compliance best practices § Applications (SAP, Oracle EBS, PHP, Perl, OWA & others) § Databases (Oracle, DB 2, SQL-Server & others) § Compliance mandates (SOX, PCI, HIPAA & others) § Deliver actionable, up-to-date content to Imperva customers 7 - CONFIDENTIAL -
Imperva Application Defense Center § Application Data Security experts § Research the latest threats and compliance best practices § Applications (SAP, Oracle EBS, PHP, Perl, OWA & others) § Databases (Oracle, DB 2, SQL-Server & others) § Compliance mandates (SOX, PCI, HIPAA & others) § Deliver actionable, up-to-date content to Imperva customers 7 - CONFIDENTIAL -
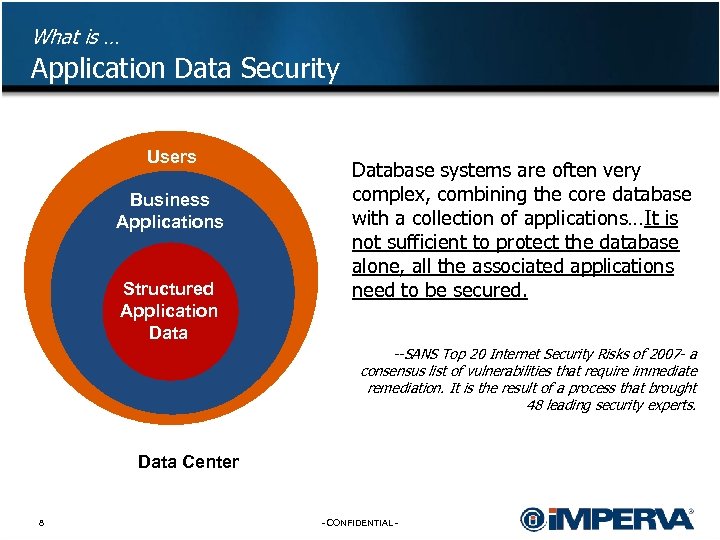 What is … Application Data Security Users Business Applications Structured Application Database systems are often very complex, combining the core database with a collection of applications…It is not sufficient to protect the database alone, all the associated applications need to be secured. --SANS Top 20 Internet Security Risks of 2007 - a consensus list of vulnerabilities that require immediate remediation. It is the result of a process that brought 48 leading security experts. Data Center 8 - CONFIDENTIAL -
What is … Application Data Security Users Business Applications Structured Application Database systems are often very complex, combining the core database with a collection of applications…It is not sufficient to protect the database alone, all the associated applications need to be secured. --SANS Top 20 Internet Security Risks of 2007 - a consensus list of vulnerabilities that require immediate remediation. It is the result of a process that brought 48 leading security experts. Data Center 8 - CONFIDENTIAL -
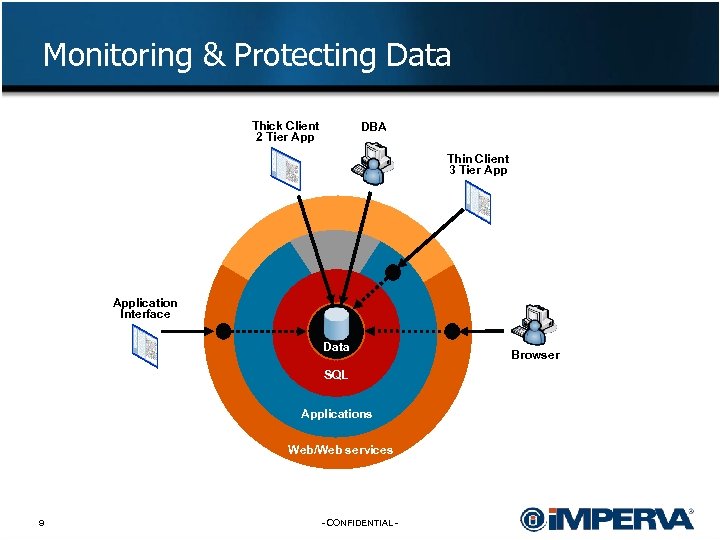 Monitoring & Protecting Data Thick Client 2 Tier App DBA Thin Client 3 Tier Application Interface Data SQL Applications Web/Web services 9 - CONFIDENTIAL - Browser
Monitoring & Protecting Data Thick Client 2 Tier App DBA Thin Client 3 Tier Application Interface Data SQL Applications Web/Web services 9 - CONFIDENTIAL - Browser
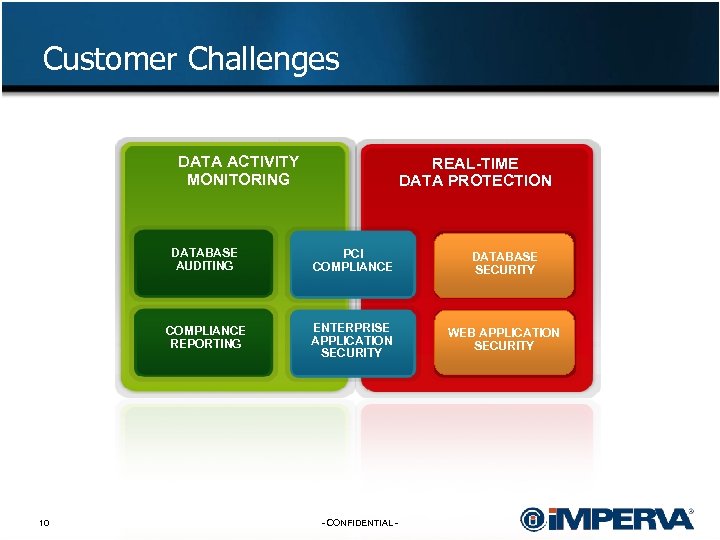 Customer Challenges DATA ACTIVITY MONITORING REAL-TIME DATA PROTECTION DATABASE AUDITING DATABASE SECURITY COMPLIANCE REPORTING 10 PCI COMPLIANCE ENTERPRISE APPLICATION SECURITY WEB APPLICATION SECURITY - CONFIDENTIAL -
Customer Challenges DATA ACTIVITY MONITORING REAL-TIME DATA PROTECTION DATABASE AUDITING DATABASE SECURITY COMPLIANCE REPORTING 10 PCI COMPLIANCE ENTERPRISE APPLICATION SECURITY WEB APPLICATION SECURITY - CONFIDENTIAL -
 Introducing Secure. Sphere § Only complete solution for enterprise data that includes: § Data activity monitoring § Real-time data protection § Full visibility and granular control of data usage § From end user through application and into database § Full stack protection § Unmatched ease-of-use and ease-of-deployment 11 - CONFIDENTIAL -
Introducing Secure. Sphere § Only complete solution for enterprise data that includes: § Data activity monitoring § Real-time data protection § Full visibility and granular control of data usage § From end user through application and into database § Full stack protection § Unmatched ease-of-use and ease-of-deployment 11 - CONFIDENTIAL -
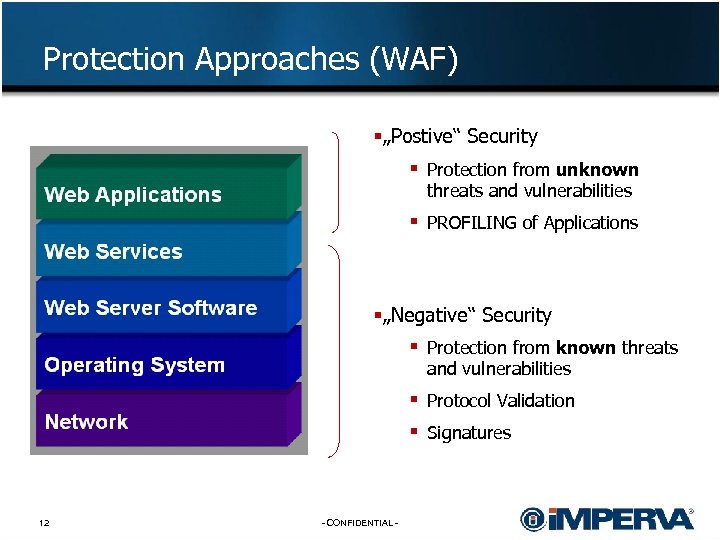 Protection Approaches (WAF) §„Postive“ Security § Protection from unknown threats and vulnerabilities § PROFILING of Applications §„Negative“ Security § Protection from known threats and vulnerabilities § Protocol Validation § Signatures 12 - CONFIDENTIAL -
Protection Approaches (WAF) §„Postive“ Security § Protection from unknown threats and vulnerabilities § PROFILING of Applications §„Negative“ Security § Protection from known threats and vulnerabilities § Protocol Validation § Signatures 12 - CONFIDENTIAL -
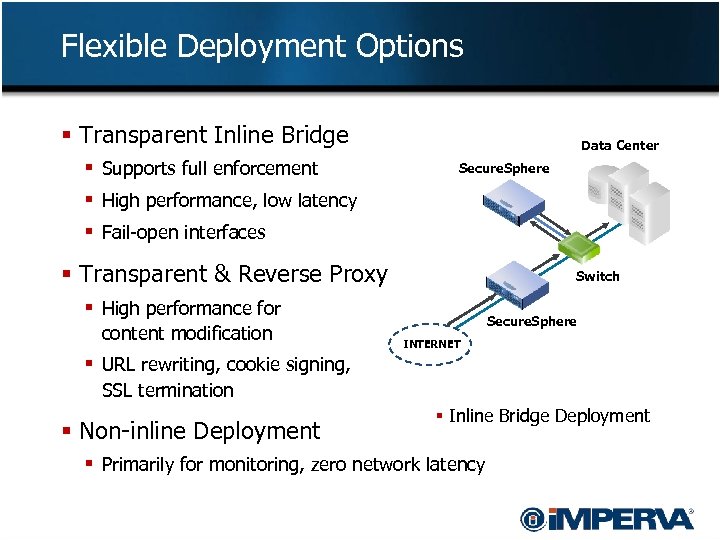 Flexible Deployment Options § Transparent Inline Bridge § Supports full enforcement § High performance, low latency § Fail-open interfaces Data Center Secure. Sphere § Transparent & Reverse Proxy Switch § High performance for content modification Secure. Sphere INTERNET § URL rewriting, cookie signing, SSL termination § Non-inline Deployment § Reverse Proxy Deployment § § Non-Inline Deployment Inline Bridge Deployment § Primarily for monitoring, zero network latency
Flexible Deployment Options § Transparent Inline Bridge § Supports full enforcement § High performance, low latency § Fail-open interfaces Data Center Secure. Sphere § Transparent & Reverse Proxy Switch § High performance for content modification Secure. Sphere INTERNET § URL rewriting, cookie signing, SSL termination § Non-inline Deployment § Reverse Proxy Deployment § § Non-Inline Deployment Inline Bridge Deployment § Primarily for monitoring, zero network latency
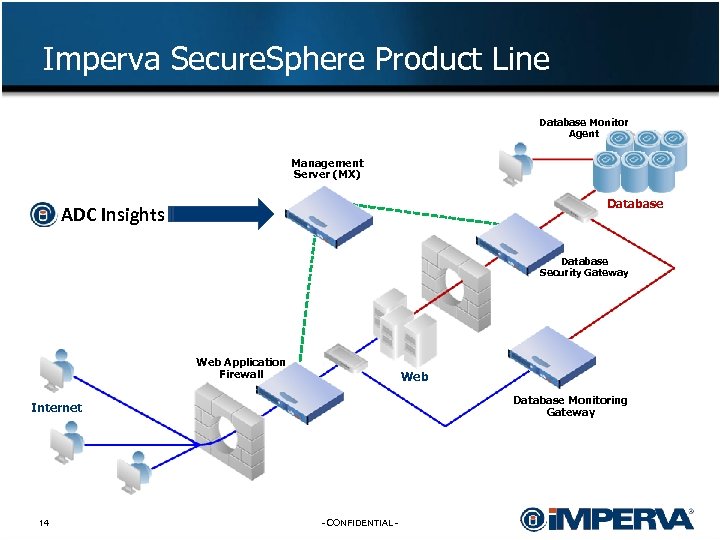 Imperva Secure. Sphere Product Line Database Monitor Agent Management Server (MX) Database ADC Insights Database Security Gateway Web Application Firewall Web Database Monitoring Gateway Internet 14 - CONFIDENTIAL -
Imperva Secure. Sphere Product Line Database Monitor Agent Management Server (MX) Database ADC Insights Database Security Gateway Web Application Firewall Web Database Monitoring Gateway Internet 14 - CONFIDENTIAL -
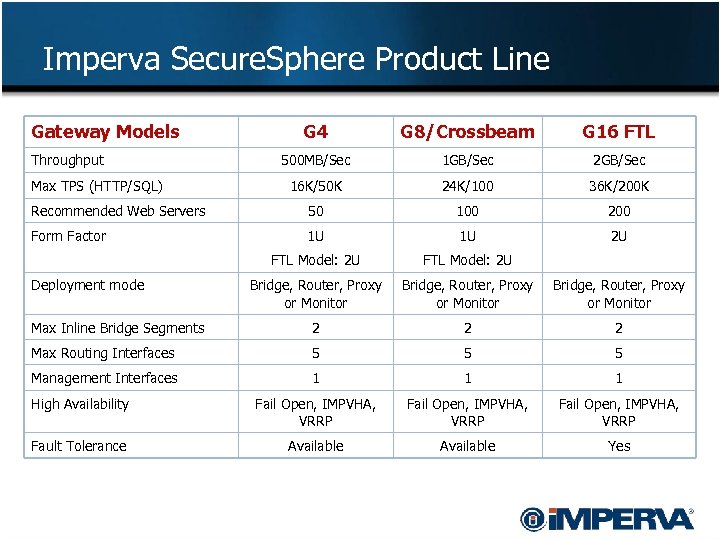 Imperva Secure. Sphere Product Line Gateway Models G 4 G 8/Crossbeam G 16 FTL 500 MB/Sec 1 GB/Sec 2 GB/Sec 16 K/50 K 24 K/100 36 K/200 K Recommended Web Servers 50 100 200 Form Factor 1 U 1 U 2 U FTL Model: 2 U Bridge, Router, Proxy or Monitor Max Inline Bridge Segments 2 2 2 Max Routing Interfaces 5 5 5 Management Interfaces 1 1 1 High Availability Fail Open, IMPVHA, VRRP Fault Tolerance Available Yes Throughput Max TPS (HTTP/SQL) Deployment mode
Imperva Secure. Sphere Product Line Gateway Models G 4 G 8/Crossbeam G 16 FTL 500 MB/Sec 1 GB/Sec 2 GB/Sec 16 K/50 K 24 K/100 36 K/200 K Recommended Web Servers 50 100 200 Form Factor 1 U 1 U 2 U FTL Model: 2 U Bridge, Router, Proxy or Monitor Max Inline Bridge Segments 2 2 2 Max Routing Interfaces 5 5 5 Management Interfaces 1 1 1 High Availability Fail Open, IMPVHA, VRRP Fault Tolerance Available Yes Throughput Max TPS (HTTP/SQL) Deployment mode
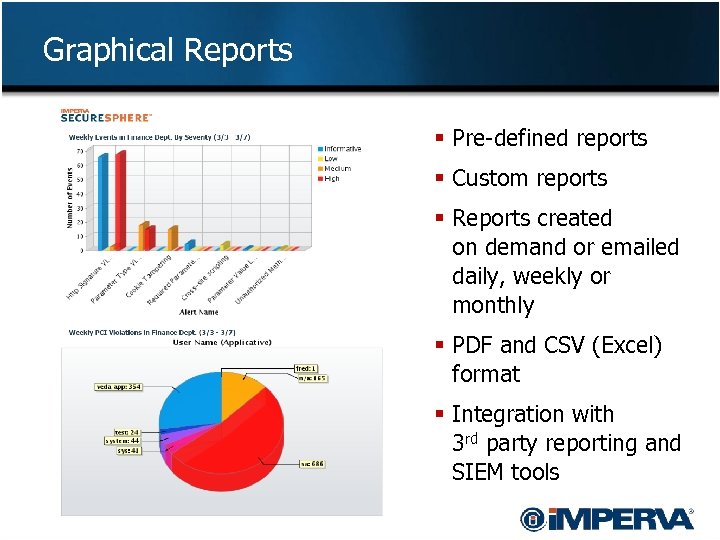 Graphical Reports § Pre-defined reports § Custom reports § Reports created on demand or emailed daily, weekly or monthly § PDF and CSV (Excel) format § Integration with 3 rd party reporting and SIEM tools
Graphical Reports § Pre-defined reports § Custom reports § Reports created on demand or emailed daily, weekly or monthly § PDF and CSV (Excel) format § Integration with 3 rd party reporting and SIEM tools
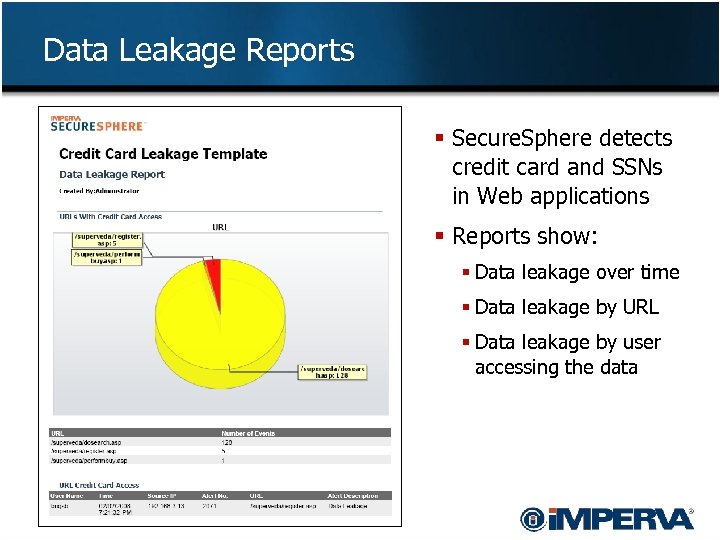 Data Leakage Reports § Secure. Sphere detects credit card and SSNs in Web applications § Reports show: § Data leakage over time § Data leakage by URL § Data leakage by user accessing the data
Data Leakage Reports § Secure. Sphere detects credit card and SSNs in Web applications § Reports show: § Data leakage over time § Data leakage by URL § Data leakage by user accessing the data
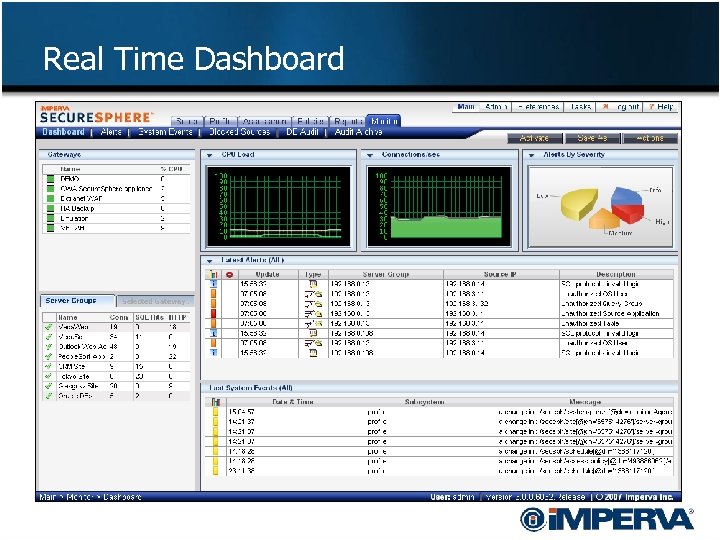 Real Time Dashboard
Real Time Dashboard
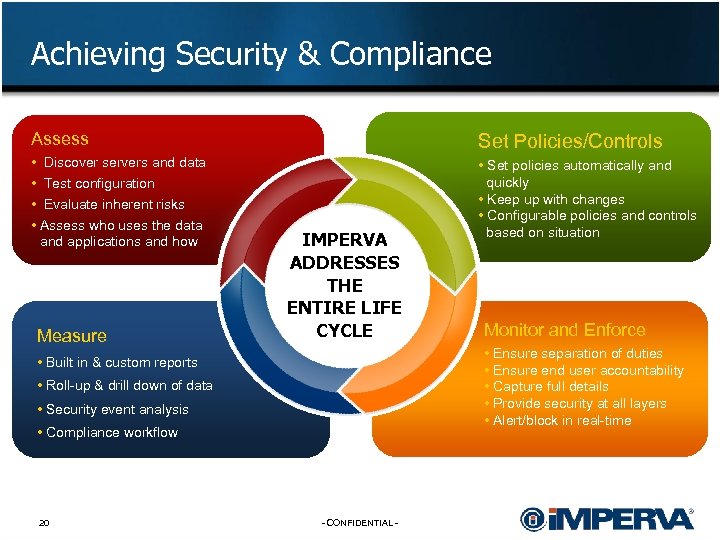 Achieving Security & Compliance Assess Set Policies/Controls • Discover servers and data • Test configuration • Evaluate inherent risks • Assess who uses the data and applications and how • Set policies automatically and quickly • Keep up with changes • Configurable policies and controls based on situation Measure IMPERVA ADDRESSES THE ENTIRE LIFE CYCLE • Ensure separation of duties • Ensure end user accountability • Capture full details • Provide security at all layers • Alert/block in real-time • Built in & custom reports • Roll-up & drill down of data • Security event analysis • Compliance workflow 20 Monitor and Enforce - CONFIDENTIAL -
Achieving Security & Compliance Assess Set Policies/Controls • Discover servers and data • Test configuration • Evaluate inherent risks • Assess who uses the data and applications and how • Set policies automatically and quickly • Keep up with changes • Configurable policies and controls based on situation Measure IMPERVA ADDRESSES THE ENTIRE LIFE CYCLE • Ensure separation of duties • Ensure end user accountability • Capture full details • Provide security at all layers • Alert/block in real-time • Built in & custom reports • Roll-up & drill down of data • Security event analysis • Compliance workflow 20 Monitor and Enforce - CONFIDENTIAL -
 Why Customers Choose Imperva Integrated End-to-end Coverage Automation & Accuracy Business Relevant Reporting Performance & Scalability World Class Customer Service 21 Full coverage for all paths to the data. A unified view of access that simplifies management and provides full information to satisfy auditors and forensic investigators Ability to model change to applications, usage patterns and data structures over time. Highly customizable reporting for specific business applications & regulatory mandates. Capacity, availability and ease of management that meets the deployment requirements of complex global companies Imperva customers enjoy 24 X 7 X 365 access to a global team of engineers with deep technical expertise and real-world deployment experience. - CONFIDENTIAL -
Why Customers Choose Imperva Integrated End-to-end Coverage Automation & Accuracy Business Relevant Reporting Performance & Scalability World Class Customer Service 21 Full coverage for all paths to the data. A unified view of access that simplifies management and provides full information to satisfy auditors and forensic investigators Ability to model change to applications, usage patterns and data structures over time. Highly customizable reporting for specific business applications & regulatory mandates. Capacity, availability and ease of management that meets the deployment requirements of complex global companies Imperva customers enjoy 24 X 7 X 365 access to a global team of engineers with deep technical expertise and real-world deployment experience. - CONFIDENTIAL -
 Thank You Imperva 3400 Bridge Parkway, Suite 101, Redwood Shores, CA 94065 Sales: +1 -866 -926 -4678 www. imperva. com 22 - CONFIDENTIAL -
Thank You Imperva 3400 Bridge Parkway, Suite 101, Redwood Shores, CA 94065 Sales: +1 -866 -926 -4678 www. imperva. com 22 - CONFIDENTIAL -


