0cebde13e359eefe26a1da367ccb1b66.ppt
- Количество слайдов: 14
 anonymous P 2 P communications platform for secure mining of personal data with minimum risks on privacy Mnemonic Security, Inc. Fujitsu Prime Software Technologies Limited Imai Lab, IIS, University of Tokyo
anonymous P 2 P communications platform for secure mining of personal data with minimum risks on privacy Mnemonic Security, Inc. Fujitsu Prime Software Technologies Limited Imai Lab, IIS, University of Tokyo
 leakage of privacy information • • restoration is just impossible descendants could be influenced punishment makes no solution some corporate data are as critical
leakage of privacy information • • restoration is just impossible descendants could be influenced punishment makes no solution some corporate data are as critical
 risk management There could be no unbreakable data center, since men of flesh and blood are in charge. The key is minimizing the damage to the smallest unit – one individual. Depend less on centralized management Develop distributed management
risk management There could be no unbreakable data center, since men of flesh and blood are in charge. The key is minimizing the damage to the smallest unit – one individual. Depend less on centralized management Develop distributed management
 mining of personal data mining of piecemeal personal data ↓ out-of-mark propositions or spam mails received pertinent propositions received ↓ How much of my privacy is known to them? When/how they gathered it without me knowing? nightmare of leaking privacy for data centers nightmare of having privacy leaked for individuals
mining of personal data mining of piecemeal personal data ↓ out-of-mark propositions or spam mails received pertinent propositions received ↓ How much of my privacy is known to them? When/how they gathered it without me knowing? nightmare of leaking privacy for data centers nightmare of having privacy leaked for individuals
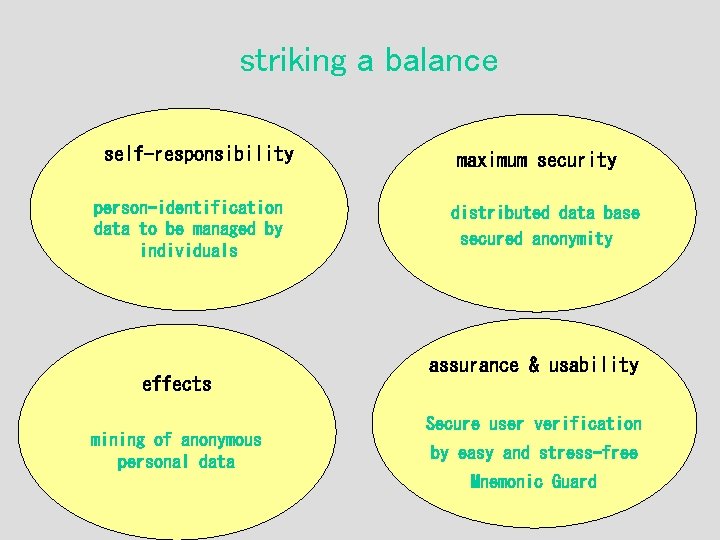 striking a balance self-responsibility maximum security person-identification data to be managed by individuals distributed data base secured anonymity effects mining of anonymous personal data assurance & usability Secure user verification by easy and stress-free Mnemonic Guard
striking a balance self-responsibility maximum security person-identification data to be managed by individuals distributed data base secured anonymity effects mining of anonymous personal data assurance & usability Secure user verification by easy and stress-free Mnemonic Guard
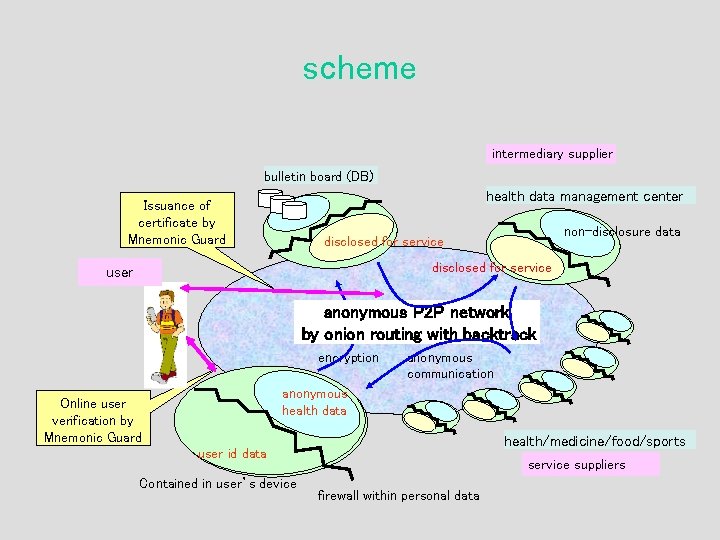 scheme intermediary supplier bulletin board (DB) health data management center Issuance of certificate by Mnemonic Guard 公開サービス disclosed non-disclosure 非公開情報 for service data 公開サービス disclosed for service user anonymous P 2 P network by onion routing with backtrack encryption Online user verification by Mnemonic Guard anonymous communication 健康データ anonymous ・計測データ (血圧、体重等) health data ・年代 ・性別 固定データ ・名前 ・住所 ・年齢 user id data ・電話番号 Contained in user’s device health/medicine/food/sports service suppliers firewall within personal data
scheme intermediary supplier bulletin board (DB) health data management center Issuance of certificate by Mnemonic Guard 公開サービス disclosed non-disclosure 非公開情報 for service data 公開サービス disclosed for service user anonymous P 2 P network by onion routing with backtrack encryption Online user verification by Mnemonic Guard anonymous communication 健康データ anonymous ・計測データ (血圧、体重等) health data ・年代 ・性別 固定データ ・名前 ・住所 ・年齢 user id data ・電話番号 Contained in user’s device health/medicine/food/sports service suppliers firewall within personal data
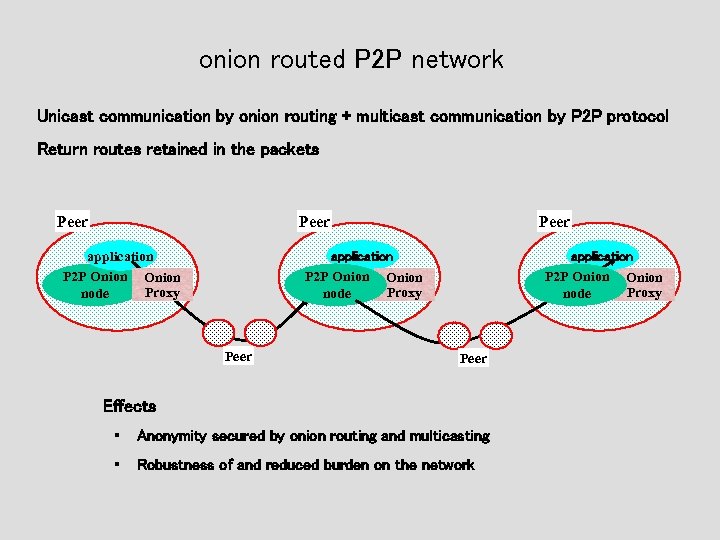 onion routed P 2 P network Unicast communication by onion routing + multicast communication by P 2 P protocol Return routes retained in the packets Peer application P 2 P Onion Proxy node Peer application P 2 P Onion Proxy node Peer Effects ・ Anonymity secured by onion routing and multicasting ・ Robustness of and reduced burden on the network
onion routed P 2 P network Unicast communication by onion routing + multicast communication by P 2 P protocol Return routes retained in the packets Peer application P 2 P Onion Proxy node Peer application P 2 P Onion Proxy node Peer Effects ・ Anonymity secured by onion routing and multicasting ・ Robustness of and reduced burden on the network
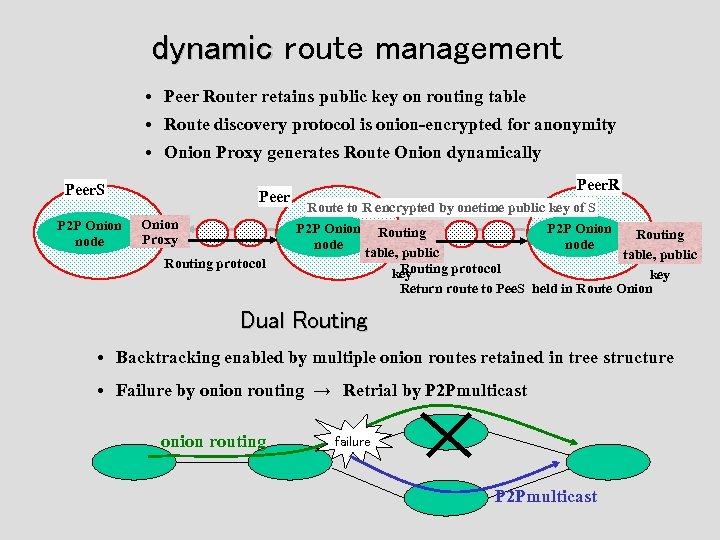 dynamic route management • Peer Router retains public key on routing table • Route discovery protocol is onion-encrypted for anonymity • Onion Proxy generates Route Onion dynamically Peer. S P 2 P Onion node Peer Onion Proxy Routing protocol Peer. R Route to R encrypted by onetime public key of S P 2 P Onion Routing node table, public Routing protocol key Return route to Pee. S held in Route Onion Dual Routing • Backtracking enabled by multiple onion routes retained in tree structure • Failure by onion routing → Retrial by P 2 Pmulticast onion routing failure P 2 Pmulticast
dynamic route management • Peer Router retains public key on routing table • Route discovery protocol is onion-encrypted for anonymity • Onion Proxy generates Route Onion dynamically Peer. S P 2 P Onion node Peer Onion Proxy Routing protocol Peer. R Route to R encrypted by onetime public key of S P 2 P Onion Routing node table, public Routing protocol key Return route to Pee. S held in Route Onion Dual Routing • Backtracking enabled by multiple onion routes retained in tree structure • Failure by onion routing → Retrial by P 2 Pmulticast onion routing failure P 2 Pmulticast
 applications privacy-protected data-mining Government to People Business to People Models in progress Health Care Nagoya Int’l Exposition secrecy-protected data mining Government Business Government to Business
applications privacy-protected data-mining Government to People Business to People Models in progress Health Care Nagoya Int’l Exposition secrecy-protected data mining Government Business Government to Business
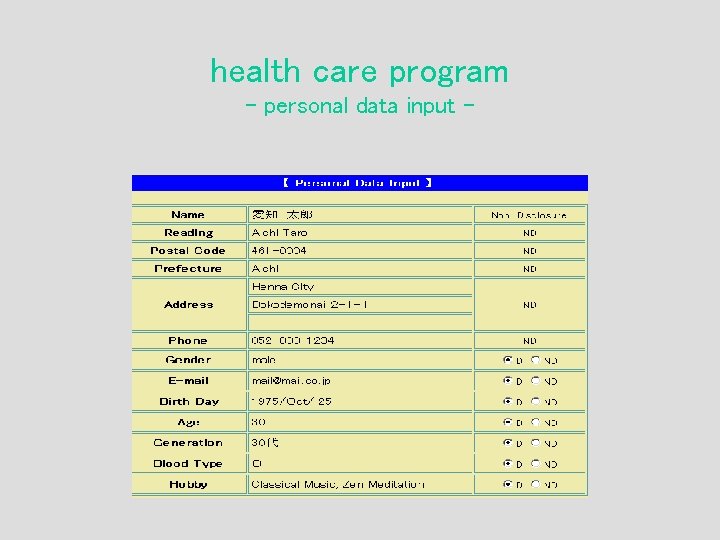 health care program - personal data input -
health care program - personal data input -
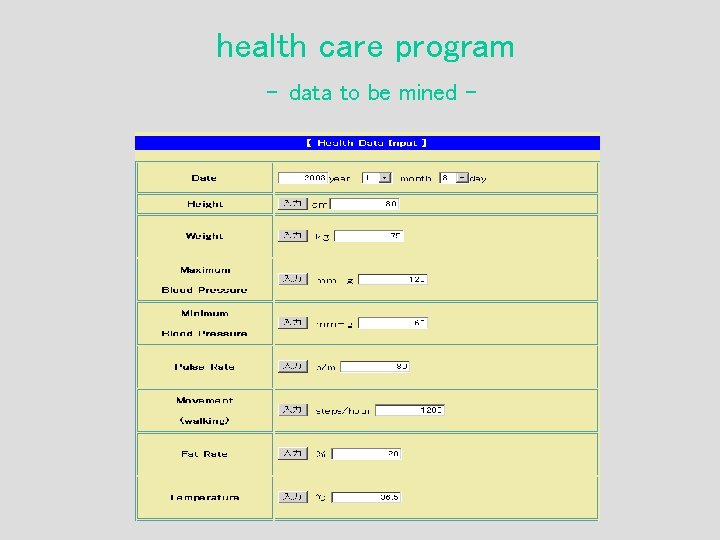 health care program - data to be mined -
health care program - data to be mined -
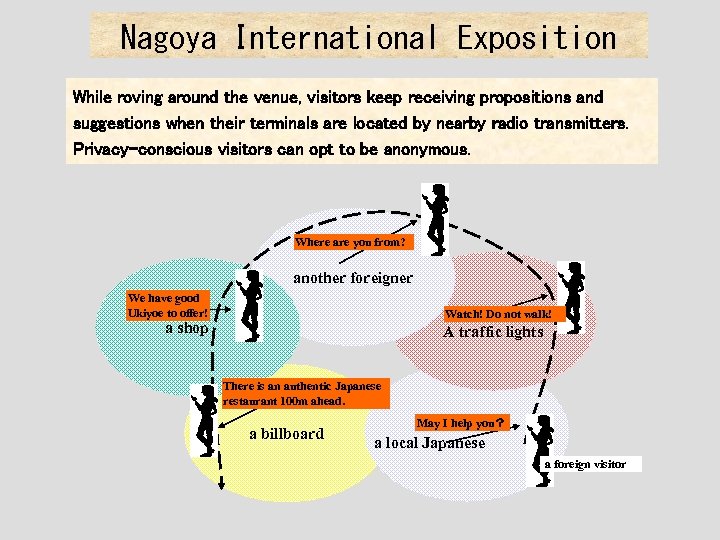 Nagoya International Exposition While roving around the venue, visitors keep receiving propositions and suggestions when their terminals are located by nearby radio transmitters. Privacy-conscious visitors can opt to be anonymous. Where are you from? another foreigner We have good Ukiyoe to offer! Watch! Do not walk! a shop A traffic lights There is an authentic Japanese restaurant 100 m ahead. a billboard May I help you? a local Japanese a foreign visitor
Nagoya International Exposition While roving around the venue, visitors keep receiving propositions and suggestions when their terminals are located by nearby radio transmitters. Privacy-conscious visitors can opt to be anonymous. Where are you from? another foreigner We have good Ukiyoe to offer! Watch! Do not walk! a shop A traffic lights There is an authentic Japanese restaurant 100 m ahead. a billboard May I help you? a local Japanese a foreign visitor
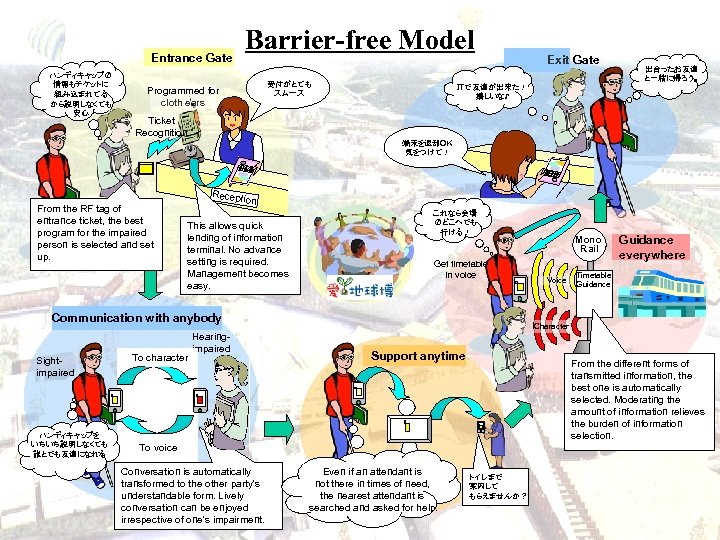 Entrance Gate ハンディキャップの 情報もチケットに 組み込まれてる から説明しなくても 安心 Barrier-free Model 受付がとても スムース Programmed for cloth ears Exit Gate 出合ったお友達 と一緒に帰ろう。 ITで友達が出来た! 嬉しいな♪ Ticket Recognition 端末を返却OK 気をつけて! From the RF tag of entrance ticket, the best program for the impaired person is selected and set up. Recepti on This allows quick lending of information terminal. No advance setting is required. Management becomes easy. これなら会場 のどこへでも 行ける! Get timetable in voice Communication with anybody Sightimpaired ハンディキャップを いちいち説明しなくても 誰とでも友達になれる To character Hearingimpaired Voice Guidance everywhere Timetable Guidance Character Support anytime From the different forms of transmitted information, the best one is automatically selected. Moderating the amount of information relieves the burden of information selection. To voice Conversation is automatically transformed to the other party's understandable form. Lively conversation can be enjoyed irrespective of one's impairment. Mono Rail Even if an attendant is not there in times of need, the nearest attendant is searched and asked for help. トイレまで 案内して もらえませんか?
Entrance Gate ハンディキャップの 情報もチケットに 組み込まれてる から説明しなくても 安心 Barrier-free Model 受付がとても スムース Programmed for cloth ears Exit Gate 出合ったお友達 と一緒に帰ろう。 ITで友達が出来た! 嬉しいな♪ Ticket Recognition 端末を返却OK 気をつけて! From the RF tag of entrance ticket, the best program for the impaired person is selected and set up. Recepti on This allows quick lending of information terminal. No advance setting is required. Management becomes easy. これなら会場 のどこへでも 行ける! Get timetable in voice Communication with anybody Sightimpaired ハンディキャップを いちいち説明しなくても 誰とでも友達になれる To character Hearingimpaired Voice Guidance everywhere Timetable Guidance Character Support anytime From the different forms of transmitted information, the best one is automatically selected. Moderating the amount of information relieves the burden of information selection. To voice Conversation is automatically transformed to the other party's understandable form. Lively conversation can be enjoyed irrespective of one's impairment. Mono Rail Even if an attendant is not there in times of need, the nearest attendant is searched and asked for help. トイレまで 案内して もらえませんか?
 the end Imai Lab, IIS, University of Tokyo Fujitsu Prime Software Technologies Limited Mnemonic Security, Inc.
the end Imai Lab, IIS, University of Tokyo Fujitsu Prime Software Technologies Limited Mnemonic Security, Inc.


