 Anonymity in MANETs Threats and Mitigations Roy Friedman, Neer Roggel Technion, Israel Institute of Technology Computer Science Department {roy, nroggel}@cs. technion. ac. il 1
Anonymity in MANETs Threats and Mitigations Roy Friedman, Neer Roggel Technion, Israel Institute of Technology Computer Science Department {roy, nroggel}@cs. technion. ac. il 1
 Outline • • • What are MANETs? Anonymity scenarios Attackers and threats Our approach: IP hopping Limitations and future work Open discussion 2
Outline • • • What are MANETs? Anonymity scenarios Attackers and threats Our approach: IP hopping Limitations and future work Open discussion 2
 What is a MANET? 3
What is a MANET? 3
 4
4
 5
5
 What are MANETs? 6
What are MANETs? 6
 What are MANETs? 7
What are MANETs? 7
 Anonymity Scenarios • Battlefield – Units in motion – Sensor network • Content sharing – Oppressive regime – Rights protected content 8
Anonymity Scenarios • Battlefield – Units in motion – Sensor network • Content sharing – Oppressive regime – Rights protected content 8
 Attacker Capabilities • • Eavesdropping Geolocating a node Device fingerprinting Generating traffic Man in the middle Node compromise Worm holes 9
Attacker Capabilities • • Eavesdropping Geolocating a node Device fingerprinting Generating traffic Man in the middle Node compromise Worm holes 9
 Threats to Anonymity • • • Irrefutably implicating a node Distorting route construction “Chattering laptops” Attacks on timing Traffic analysis 10
Threats to Anonymity • • • Irrefutably implicating a node Distorting route construction “Chattering laptops” Attacks on timing Traffic analysis 10
 Traffic Analysis 11
Traffic Analysis 11
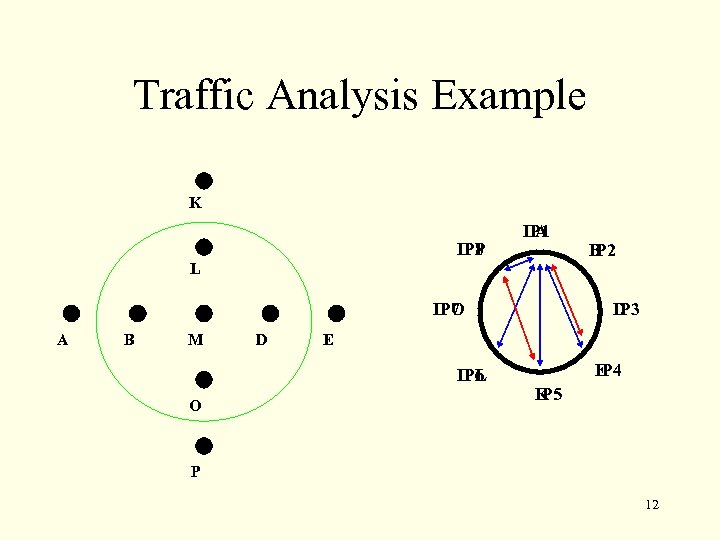 Traffic Analysis Example K IP 8 P A IP 1 B IP 2 L IP 7 O A B M D E IP 6 L O IP 3 D IP 4 E IP 5 K P 12
Traffic Analysis Example K IP 8 P A IP 1 B IP 2 L IP 7 O A B M D E IP 6 L O IP 3 D IP 4 E IP 5 K P 12
 Our Approach 13
Our Approach 13
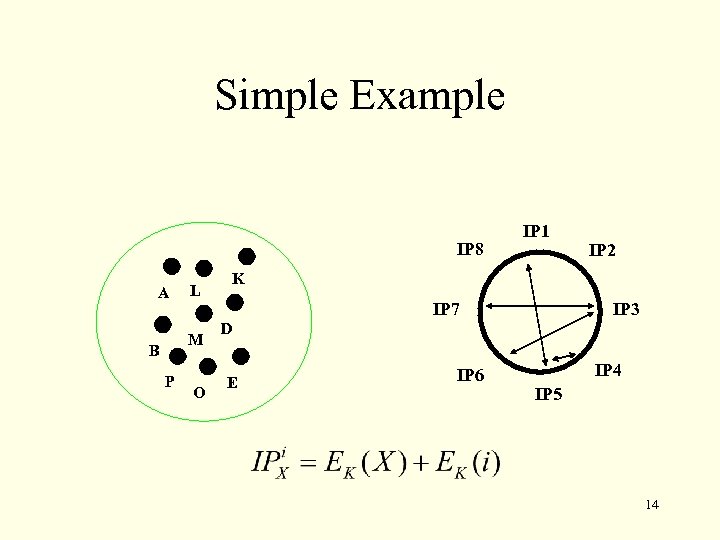 Simple Example IP 8 A L M B P O IP 1 IP 2 K IP 7 IP 3 D E IP 6 IP 4 IP 5 14
Simple Example IP 8 A L M B P O IP 1 IP 2 K IP 7 IP 3 D E IP 6 IP 4 IP 5 14
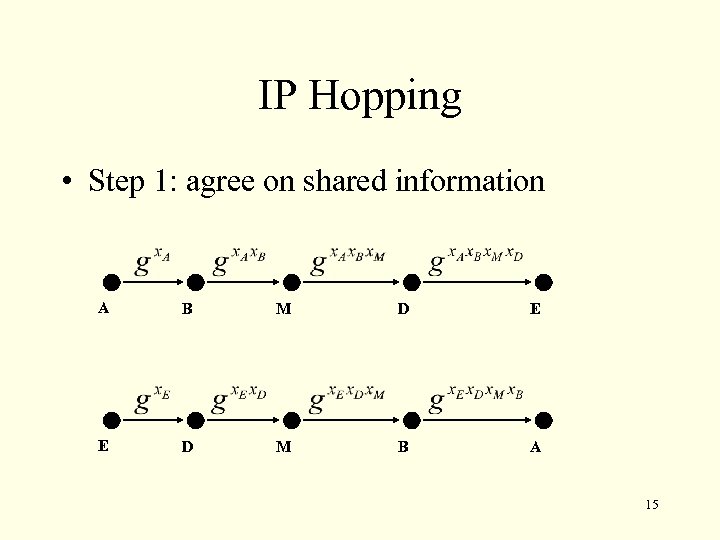 IP Hopping • Step 1: agree on shared information A B M D E E D M B A 15
IP Hopping • Step 1: agree on shared information A B M D E E D M B A 15
 IP Hopping • Step 2: derive temporary addresses 16
IP Hopping • Step 2: derive temporary addresses 16
![IP Hopping • Step 3: use temporary addresses [Ai, B, M, D, Ei] A IP Hopping • Step 3: use temporary addresses [Ai, B, M, D, Ei] A](https://present5.com/presentation/e719d746f76886a54c289a6ad2722376/image-17.jpg) IP Hopping • Step 3: use temporary addresses [Ai, B, M, D, Ei] A [Ai, B, M, D, Ei] B [Ai, B, M, D, Ei] M D E 17
IP Hopping • Step 3: use temporary addresses [Ai, B, M, D, Ei] A [Ai, B, M, D, Ei] B [Ai, B, M, D, Ei] M D E 17
 Traffic Analysis Revisited K IP 8 IP 1 IP 2 L IP 7 A B M D E IP 6 O IP 3 IP 4 IP 5 P 18
Traffic Analysis Revisited K IP 8 IP 1 IP 2 L IP 7 A B M D E IP 6 O IP 3 IP 4 IP 5 P 18
 Limitations • Routing efficiency – Discovery, maintenance • In-band agreement • Network services – Authentication, service discovery, address binding, address assignment 19
Limitations • Routing efficiency – Discovery, maintenance • In-band agreement • Network services – Authentication, service discovery, address binding, address assignment 19
 Future Research Directions • More IP information leaks • Better routing mechanisms • TCP stream information leaks 20
Future Research Directions • More IP information leaks • Better routing mechanisms • TCP stream information leaks 20
 Discussion • How can we tell the network to help us find someone we are looking for without telling the network who it is we are looking for? • Once the route is known, how do we ensure that all nodes along the way are capable of receiving the packet and forwarding it? 21
Discussion • How can we tell the network to help us find someone we are looking for without telling the network who it is we are looking for? • Once the route is known, how do we ensure that all nodes along the way are capable of receiving the packet and forwarding it? 21