9c85127acf836c00aac803b6ddcc03ac.ppt
- Количество слайдов: 29
 Anony. Sense: Privacy-Aware People-Centric Sensing Cory Conelius, Apu Kapadia, David Kotz, Dan Peebles, Minho Shin [Institute for Security Technology Studies Dartmouth College, USA] Nikos Triandopoulos [Department of Computer Science University of Aarhus, Denmark] Mobi. Sys’ 08 Presented By: Leyla Kazemi
Anony. Sense: Privacy-Aware People-Centric Sensing Cory Conelius, Apu Kapadia, David Kotz, Dan Peebles, Minho Shin [Institute for Security Technology Studies Dartmouth College, USA] Nikos Triandopoulos [Department of Computer Science University of Aarhus, Denmark] Mobi. Sys’ 08 Presented By: Leyla Kazemi
 Outline n n Motivation Anony. Sense Architecture ¡ ¡ n Protocol ¡ ¡ ¡ n System Design Task Language Threat Model Trust Model Tasking Protocol Reporting Protocol Security Properties Evaluation
Outline n n Motivation Anony. Sense Architecture ¡ ¡ n Protocol ¡ ¡ ¡ n System Design Task Language Threat Model Trust Model Tasking Protocol Reporting Protocol Security Properties Evaluation
 Motivation n Personal Mobile Devices equipped with many sensors (e. g. , cameras, microphones, accelerometers) n Opportunity for cooperative sensing applications n Users Contributing data to information services n Challenge: Protecting the user privacy while their devices reliably contribute data
Motivation n Personal Mobile Devices equipped with many sensors (e. g. , cameras, microphones, accelerometers) n Opportunity for cooperative sensing applications n Users Contributing data to information services n Challenge: Protecting the user privacy while their devices reliably contribute data
 Motivation n Opportunistic sensing: Leveraging users’ mobile devices to collectively measure environmental data (context) n Introducing people-centric, dynamic, and highly mobile communication n Applications: Car. Tel, Mobiscopes, Urbanet, Senseweb, Metrosense n Examples: Finding Parking Spots, Locating lost Bluetooth-enabled objects, collecting traffic reports of a street Sensor-enabled cellphones
Motivation n Opportunistic sensing: Leveraging users’ mobile devices to collectively measure environmental data (context) n Introducing people-centric, dynamic, and highly mobile communication n Applications: Car. Tel, Mobiscopes, Urbanet, Senseweb, Metrosense n Examples: Finding Parking Spots, Locating lost Bluetooth-enabled objects, collecting traffic reports of a street Sensor-enabled cellphones
 Challenges n Dependent on a large-scale, and heterogeneous personal devices n Should be implemented across autonomous wireless access points, and public internet n Protecting users’ privacy
Challenges n Dependent on a large-scale, and heterogeneous personal devices n Should be implemented across autonomous wireless access points, and public internet n Protecting users’ privacy
 Privacy Issue n n Report includes time and location of the sensor revealing user’s location at that time Integrity of system and reliability of report User trusted? ? Wilshire, Stanley Ave, 90036 10: 00 am Mar 20 th 2009
Privacy Issue n n Report includes time and location of the sensor revealing user’s location at that time Integrity of system and reliability of report User trusted? ? Wilshire, Stanley Ave, 90036 10: 00 am Mar 20 th 2009
 Anony. Sense n n n A privacy-aware architecture for realizing pervasive applications based on collaborative, opportunistic sensing by personal mobile devices Allowing applications to submit sensing tasks that will be distributed across anonymous devices Receiving verified, yet anonymized sensor data reports System Task App Anonymous Verified Report
Anony. Sense n n n A privacy-aware architecture for realizing pervasive applications based on collaborative, opportunistic sensing by personal mobile devices Allowing applications to submit sensing tasks that will be distributed across anonymous devices Receiving verified, yet anonymized sensor data reports System Task App Anonymous Verified Report
 System Components n Mobile Nodes (MN): ¡ ¡ n Sensing Computation Memory Wireless communication Carrier: ¡ carries the mobile node
System Components n Mobile Nodes (MN): ¡ ¡ n Sensing Computation Memory Wireless communication Carrier: ¡ carries the mobile node
 Components n Registration Authority (RA): ¡ Registering nodes n n n ¡ Verifying the proper installation on the MNs Verifying the attributes of the MNs Installing a private group key on the node Issuing certificates to task service and report service n Apps and nodes can later verify the authenticity of the services
Components n Registration Authority (RA): ¡ Registering nodes n n n ¡ Verifying the proper installation on the MNs Verifying the attributes of the MNs Installing a private group key on the node Issuing certificates to task service and report service n Apps and nodes can later verify the authenticity of the services
 Components n Task Service (TS): ¡ ¡ n Receiving Task descriptions from apps Performing Consistency checking Distributing current task to MNs Returning a token to app for later retrieving the tasked data Report Service (RS): ¡ ¡ ¡ Receiving reports from MNs Aggregating them for more privacy Responding to queries from apps
Components n Task Service (TS): ¡ ¡ n Receiving Task descriptions from apps Performing Consistency checking Distributing current task to MNs Returning a token to app for later retrieving the tasked data Report Service (RS): ¡ ¡ ¡ Receiving reports from MNs Aggregating them for more privacy Responding to queries from apps
 Components n Mix Network (MIX): ¡ ¡ Anonymizing channel between MNs and RS De-linking reports submitted by MNs Allowing users to anonymously send messages How: n n waiting for enough incoming messages before sending messages to the next node Delaying and mixing of messages makes it difficult to correlate incoming and outgoing messages
Components n Mix Network (MIX): ¡ ¡ Anonymizing channel between MNs and RS De-linking reports submitted by MNs Allowing users to anonymously send messages How: n n waiting for enough incoming messages before sending messages to the next node Delaying and mixing of messages makes it difficult to correlate incoming and outgoing messages
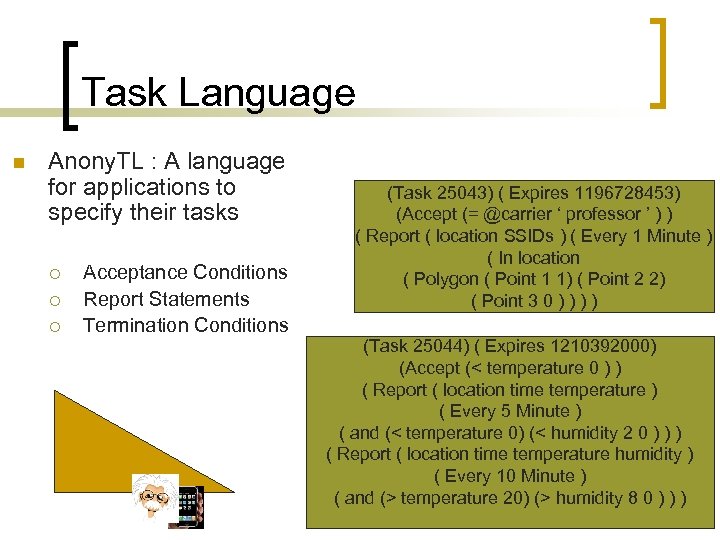 Task Language n Anony. TL : A language for applications to specify their tasks ¡ ¡ ¡ Acceptance Conditions Report Statements Termination Conditions (Task 25043) ( Expires 1196728453) (Accept (= @carrier ‘ professor ’ ) ) ( Report ( location SSIDs ) ( Every 1 Minute ) ( In location ( Polygon ( Point 1 1) ( Point 2 2) ( Point 3 0 ) ) (Task 25044) ( Expires 1210392000) (Accept (< temperature 0 ) ) ( Report ( location time temperature ) ( Every 5 Minute ) ( and (< temperature 0) (< humidity 2 0 ) ) ) ( Report ( location time temperature humidity ) ( Every 10 Minute ) ( and (> temperature 20) (> humidity 8 0 ) ) )
Task Language n Anony. TL : A language for applications to specify their tasks ¡ ¡ ¡ Acceptance Conditions Report Statements Termination Conditions (Task 25043) ( Expires 1196728453) (Accept (= @carrier ‘ professor ’ ) ) ( Report ( location SSIDs ) ( Every 1 Minute ) ( In location ( Polygon ( Point 1 1) ( Point 2 2) ( Point 3 0 ) ) (Task 25044) ( Expires 1210392000) (Accept (< temperature 0 ) ) ( Report ( location time temperature ) ( Every 5 Minute ) ( and (< temperature 0) (< humidity 2 0 ) ) ) ( Report ( location time temperature humidity ) ( Every 10 Minute ) ( and (> temperature 20) (> humidity 8 0 ) ) )
 Threat Model n Carrier Anonymity ¡ ¡ n Data Integrity ¡ ¡ n De-anonymizing a carrier by linking a report to the carrier Eavesdropping on communication between MN and APs Submitting tasks, and retrieve the reports Registering as MN Tampering with the sensor data Submitting bogus reports to RS Impersonating the RS to deliver bogus reports to the apps Tampering with MN hardware or software Other threats (Not considered) ¡ ¡ Tampering directly with MN sensors Denial-of-service threats
Threat Model n Carrier Anonymity ¡ ¡ n Data Integrity ¡ ¡ n De-anonymizing a carrier by linking a report to the carrier Eavesdropping on communication between MN and APs Submitting tasks, and retrieve the reports Registering as MN Tampering with the sensor data Submitting bogus reports to RS Impersonating the RS to deliver bogus reports to the apps Tampering with MN hardware or software Other threats (Not considered) ¡ ¡ Tampering directly with MN sensors Denial-of-service threats
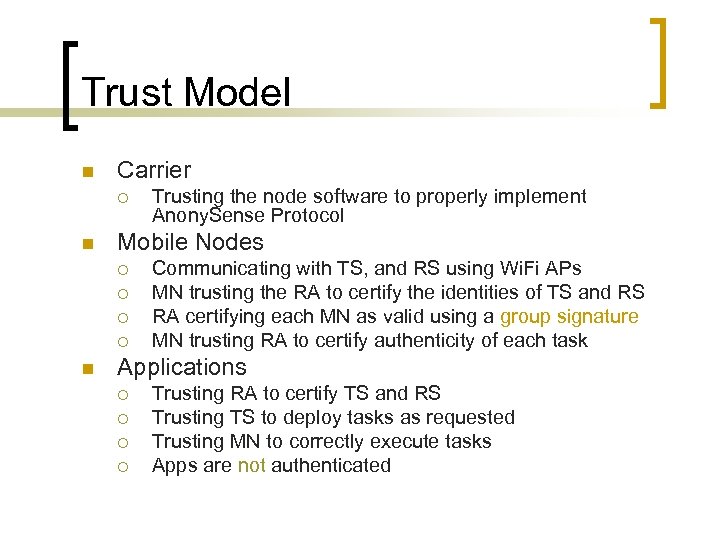 Trust Model n Carrier ¡ n Mobile Nodes ¡ ¡ n Trusting the node software to properly implement Anony. Sense Protocol Communicating with TS, and RS using Wi. Fi APs MN trusting the RA to certify the identities of TS and RS RA certifying each MN as valid using a group signature MN trusting RA to certify authenticity of each task Applications ¡ ¡ Trusting RA to certify TS and RS Trusting TS to deploy tasks as requested Trusting MN to correctly execute tasks Apps are not authenticated
Trust Model n Carrier ¡ n Mobile Nodes ¡ ¡ n Trusting the node software to properly implement Anony. Sense Protocol Communicating with TS, and RS using Wi. Fi APs MN trusting the RA to certify the identities of TS and RS RA certifying each MN as valid using a group signature MN trusting RA to certify authenticity of each task Applications ¡ ¡ Trusting RA to certify TS and RS Trusting TS to deploy tasks as requested Trusting MN to correctly execute tasks Apps are not authenticated
 Trust Model n Registration Authority ¡ n TS/RS ¡ ¡ n Trust Nothing Trusting RA to certify valid MNs only Not trusting apps Certifying MNs ¡ ¡ ¡ Running proper version of Anony. TL Verifying the MN’s attributes Providing MN with a group signature MN maintain anonymous
Trust Model n Registration Authority ¡ n TS/RS ¡ ¡ n Trust Nothing Trusting RA to certify valid MNs only Not trusting apps Certifying MNs ¡ ¡ ¡ Running proper version of Anony. TL Verifying the MN’s attributes Providing MN with a group signature MN maintain anonymous
 Protocol n Tasking Protocol: Getting tasks from apps to mobile nodes ¡ ¡ n Reporting Protocol: MNs reporting sensor data back to apps ¡ ¡ ¡ n Task Generation Task Verification Response to App Tasking Nodes Data fusion Data retrieval MAC address recycling Security Properties
Protocol n Tasking Protocol: Getting tasks from apps to mobile nodes ¡ ¡ n Reporting Protocol: MNs reporting sensor data back to apps ¡ ¡ ¡ n Task Generation Task Verification Response to App Tasking Nodes Data fusion Data retrieval MAC address recycling Security Properties
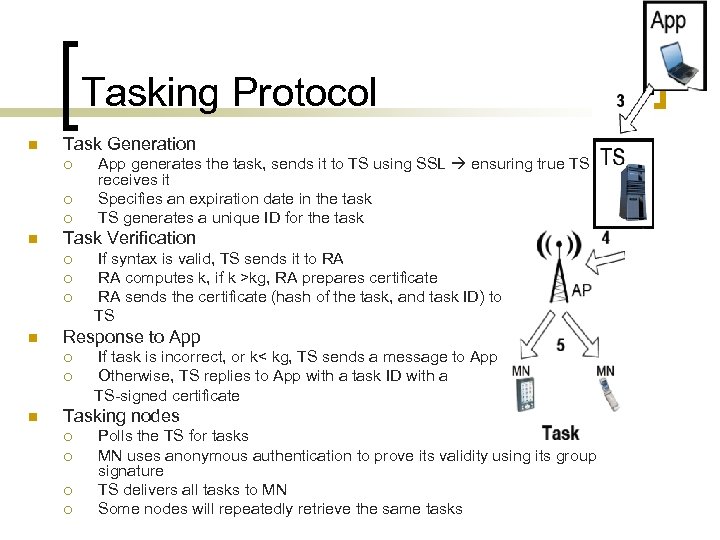 Tasking Protocol n Task Generation ¡ ¡ ¡ n Task Verification ¡ ¡ ¡ n If syntax is valid, TS sends it to RA RA computes k, if k >kg, RA prepares certificate RA sends the certificate (hash of the task, and task ID) to TS Response to App ¡ ¡ n App generates the task, sends it to TS using SSL ensuring true TS receives it Specifies an expiration date in the task TS generates a unique ID for the task If task is incorrect, or k< kg, TS sends a message to App Otherwise, TS replies to App with a task ID with a TS-signed certificate Tasking nodes ¡ ¡ Polls the TS for tasks MN uses anonymous authentication to prove its validity using its group signature TS delivers all tasks to MN Some nodes will repeatedly retrieve the same tasks
Tasking Protocol n Task Generation ¡ ¡ ¡ n Task Verification ¡ ¡ ¡ n If syntax is valid, TS sends it to RA RA computes k, if k >kg, RA prepares certificate RA sends the certificate (hash of the task, and task ID) to TS Response to App ¡ ¡ n App generates the task, sends it to TS using SSL ensuring true TS receives it Specifies an expiration date in the task TS generates a unique ID for the task If task is incorrect, or k< kg, TS sends a message to App Otherwise, TS replies to App with a task ID with a TS-signed certificate Tasking nodes ¡ ¡ Polls the TS for tasks MN uses anonymous authentication to prove its validity using its group signature TS delivers all tasks to MN Some nodes will repeatedly retrieve the same tasks
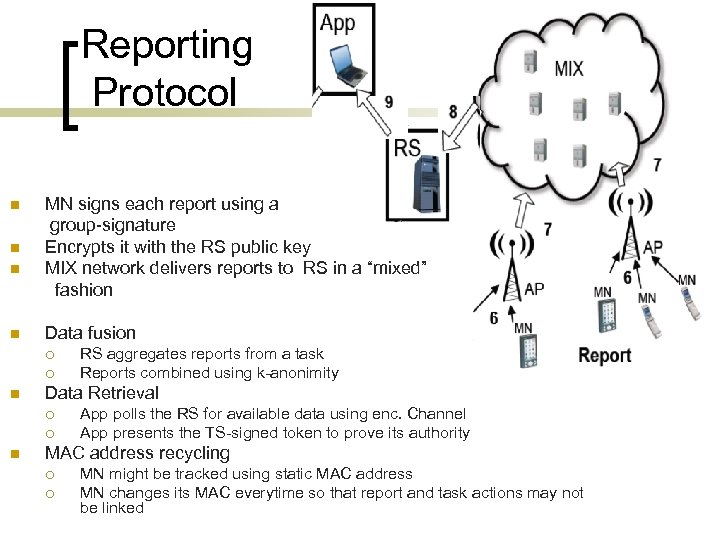 Reporting Protocol n n MN signs each report using a group-signature Encrypts it with the RS public key MIX network delivers reports to RS in a “mixed” fashion Data fusion ¡ ¡ n Data Retrieval ¡ ¡ n RS aggregates reports from a task Reports combined using k-anonimity App polls the RS for available data using enc. Channel App presents the TS-signed token to prove its authority MAC address recycling ¡ ¡ MN might be tracked using static MAC address MN changes its MAC everytime so that report and task actions may not be linked
Reporting Protocol n n MN signs each report using a group-signature Encrypts it with the RS public key MIX network delivers reports to RS in a “mixed” fashion Data fusion ¡ ¡ n Data Retrieval ¡ ¡ n RS aggregates reports from a task Reports combined using k-anonimity App polls the RS for available data using enc. Channel App presents the TS-signed token to prove its authority MAC address recycling ¡ ¡ MN might be tracked using static MAC address MN changes its MAC everytime so that report and task actions may not be linked
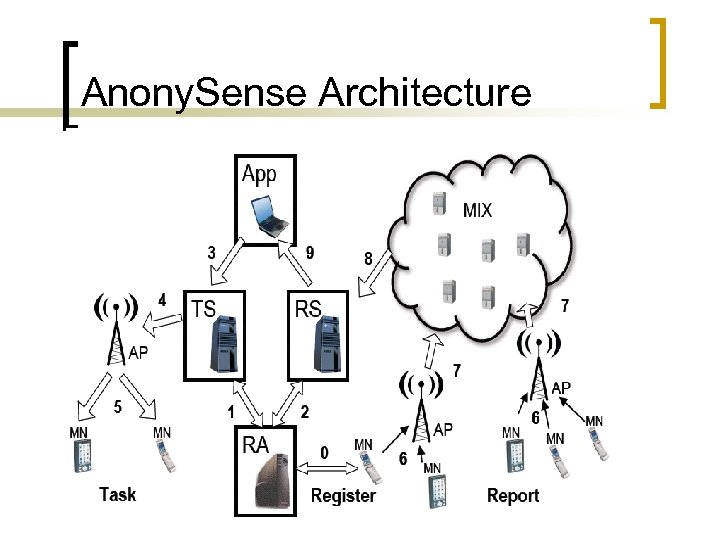 Anony. Sense Architecture
Anony. Sense Architecture
 Security Properties n Adversary can learn little by eavesdropping on MN communication all communications are encrypted n Adversary cannot pose as TS/RS MNs and Apps have certificate from RA for public key of TS/RS n TS cannot link MN’s tasks each arrives from one MAC address/ intervals are randomized n Adversary can learn little to pose as App any task must satisfy k> kg n Adversary cannot link MN’s reports each arrives from one MAC address/ intervals are randomized / uses MIX
Security Properties n Adversary can learn little by eavesdropping on MN communication all communications are encrypted n Adversary cannot pose as TS/RS MNs and Apps have certificate from RA for public key of TS/RS n TS cannot link MN’s tasks each arrives from one MAC address/ intervals are randomized n Adversary can learn little to pose as App any task must satisfy k> kg n Adversary cannot link MN’s reports each arrives from one MAC address/ intervals are randomized / uses MIX
 Evaluation n Implementation ¡ Communication n n ¡ Servers n ¡ SSL-encrypted HTTP channel MN encrypts its report with MIX node keys, sending messages using SMTP Written in Ruby PL Mobile Nodes n n n Nokia N 800 Software in C++ Downloading tasks using libcurl Verifying using RSA/ SHA-1 No MAC address rotation
Evaluation n Implementation ¡ Communication n n ¡ Servers n ¡ SSL-encrypted HTTP channel MN encrypts its report with MIX node keys, sending messages using SMTP Written in Ruby PL Mobile Nodes n n n Nokia N 800 Software in C++ Downloading tasks using libcurl Verifying using RSA/ SHA-1 No MAC address rotation
 Evaluation n Applications ¡ Rogue. Finder n n n ¡ Detecting rogue APs in a given area Tasking Anony. Sense to report all APs visible to MNs Sensor: MN’s Wi-Fi interface Object. Finder n n Finding the bluetooth Mac address of a lost object After detecting the specified MAC address, MN reports the current location
Evaluation n Applications ¡ Rogue. Finder n n n ¡ Detecting rogue APs in a given area Tasking Anony. Sense to report all APs visible to MNs Sensor: MN’s Wi-Fi interface Object. Finder n n Finding the bluetooth Mac address of a lost object After detecting the specified MAC address, MN reports the current location
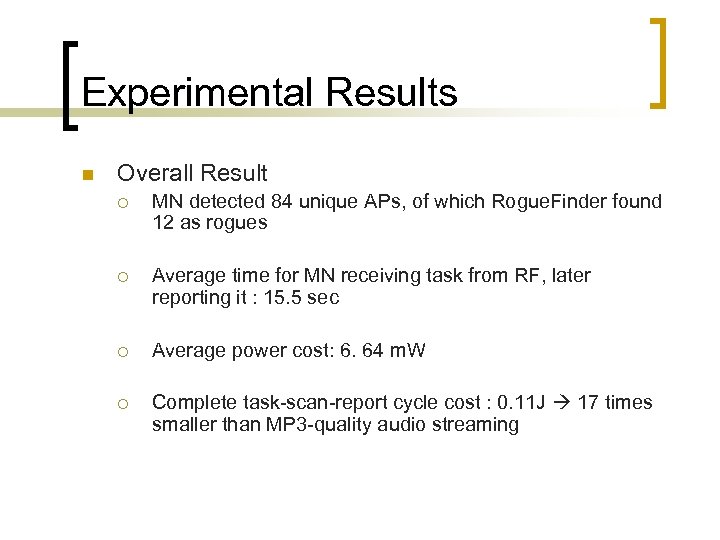 Experimental Results n Overall Result ¡ MN detected 84 unique APs, of which Rogue. Finder found 12 as rogues ¡ Average time for MN receiving task from RF, later reporting it : 15. 5 sec ¡ Average power cost: 6. 64 m. W ¡ Complete task-scan-report cycle cost : 0. 11 J 17 times smaller than MP 3 -quality audio streaming
Experimental Results n Overall Result ¡ MN detected 84 unique APs, of which Rogue. Finder found 12 as rogues ¡ Average time for MN receiving task from RF, later reporting it : 15. 5 sec ¡ Average power cost: 6. 64 m. W ¡ Complete task-scan-report cycle cost : 0. 11 J 17 times smaller than MP 3 -quality audio streaming
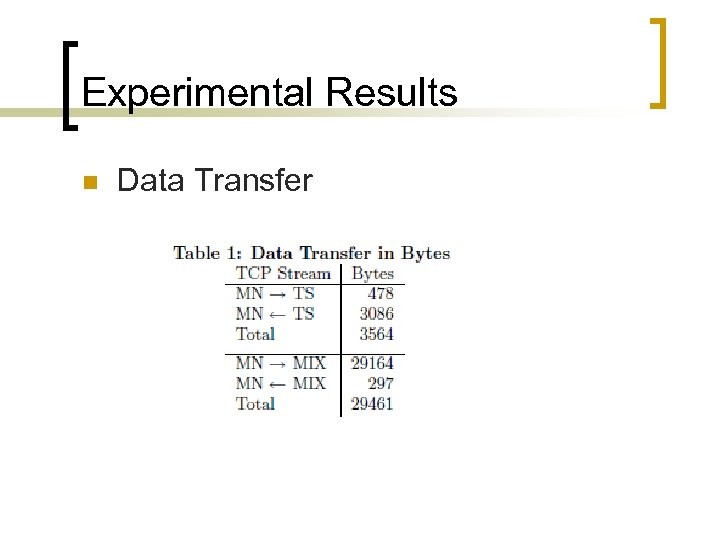 Experimental Results n Data Transfer
Experimental Results n Data Transfer
 Experimental Results n Overall Energy Consumption
Experimental Results n Overall Energy Consumption
 Experimental Results n Detailed Energy Consumption
Experimental Results n Detailed Energy Consumption
 Discussion n Scalability ¡ Reduce Increasing burden on MN n n n Carrier Policy ¡ n ¡ App may receive much more reports than needed Anony. Sense allow removing a task Delay Tolerance ¡ n Using other techniques to further enforce anonymity like “statistical kanonymity” Task Dissemination ¡ n Configuring a policy on which tasks to accept Attribute-based tasking ¡ n TS could give MN only a subset of tasks MN rejecting some tasks when overloaded The more carriers, the less latency in message passing using MIX Data Quality ¡ ¡ More accurate data Less privacy for users Allowing applications to request a certain granularity of either time or location
Discussion n Scalability ¡ Reduce Increasing burden on MN n n n Carrier Policy ¡ n ¡ App may receive much more reports than needed Anony. Sense allow removing a task Delay Tolerance ¡ n Using other techniques to further enforce anonymity like “statistical kanonymity” Task Dissemination ¡ n Configuring a policy on which tasks to accept Attribute-based tasking ¡ n TS could give MN only a subset of tasks MN rejecting some tasks when overloaded The more carriers, the less latency in message passing using MIX Data Quality ¡ ¡ More accurate data Less privacy for users Allowing applications to request a certain granularity of either time or location
 Summary n n Anony. Sense: A comprehensive system to preserve privacy of users in opportunisticsensing environments Allowing applications to request sensor data using task language Data collected in opportunistic, delaytolerant manner Data reported, while the users are anonymized but verified
Summary n n Anony. Sense: A comprehensive system to preserve privacy of users in opportunisticsensing environments Allowing applications to request sensor data using task language Data collected in opportunistic, delaytolerant manner Data reported, while the users are anonymized but verified
 Thanks
Thanks


