5a1f5511dcf7a6edd9c2fb1dab122290.ppt
- Количество слайдов: 142
 Anatomy of Internet and Network Attacks
Anatomy of Internet and Network Attacks

 Who Is Who?
Who Is Who?
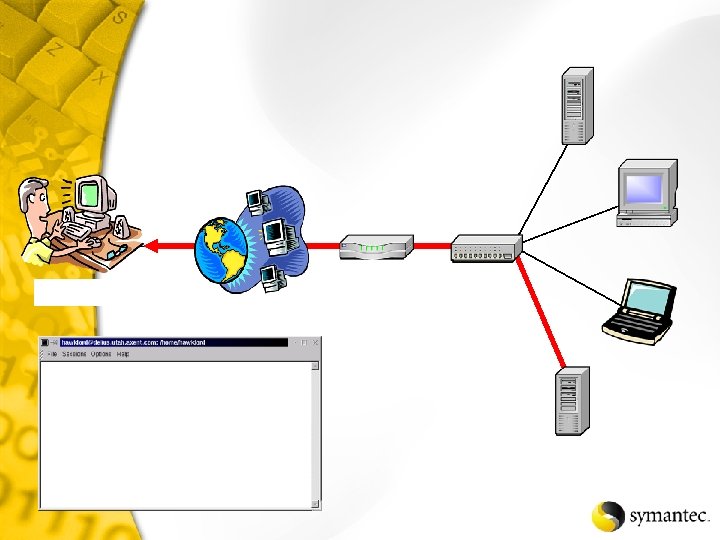
 Where Do I Want to Go?
Where Do I Want to Go?


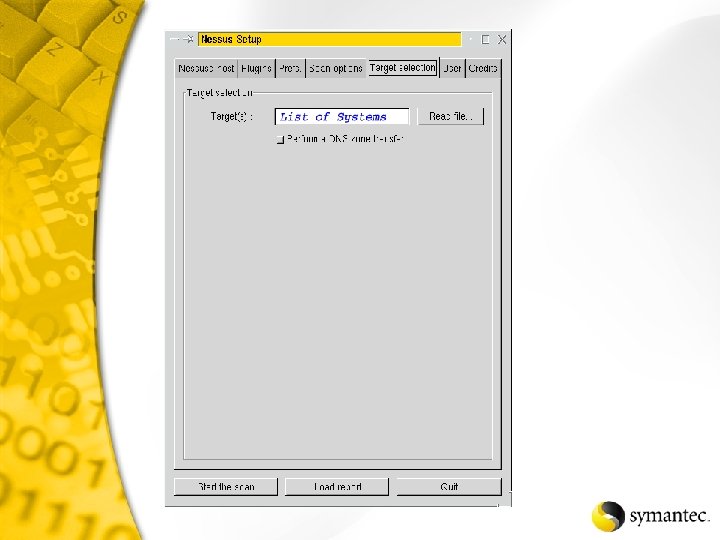
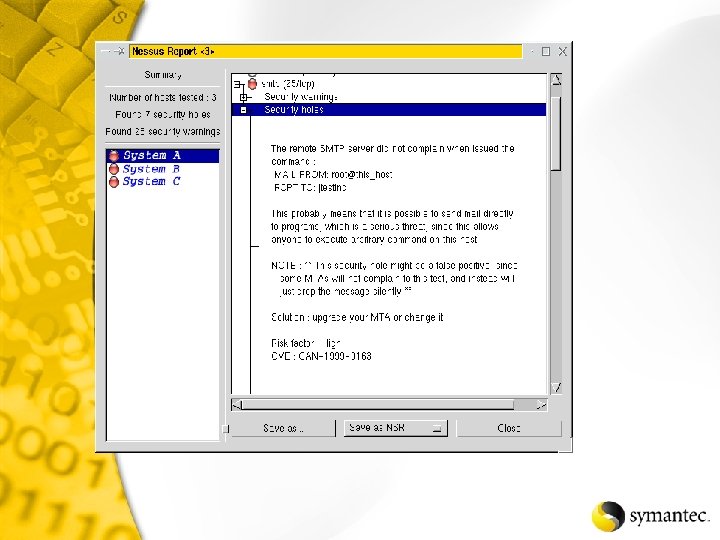
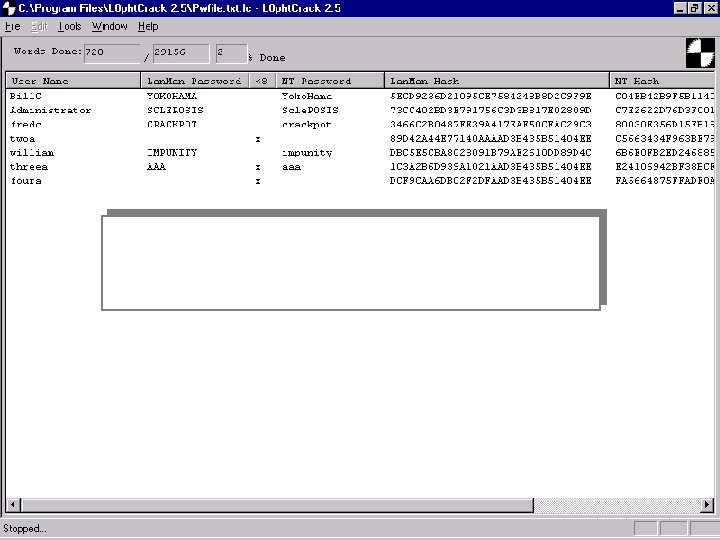
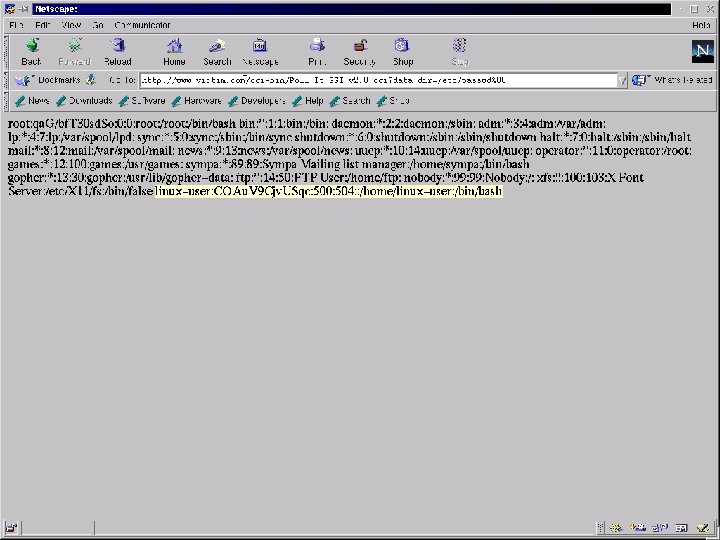
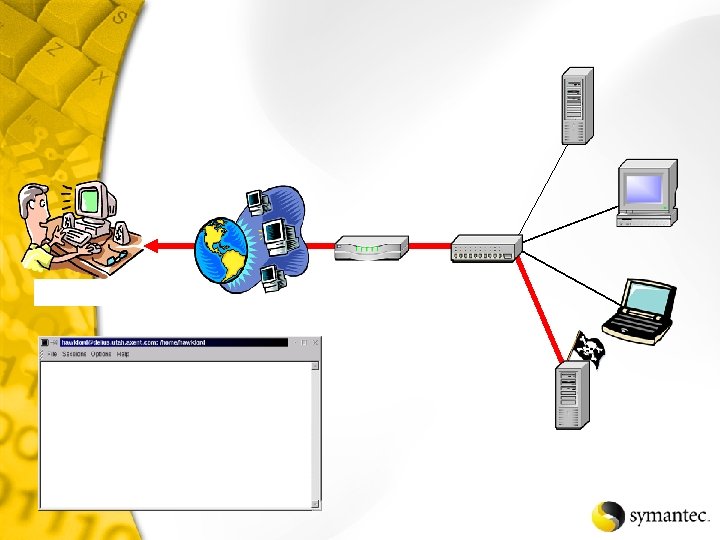
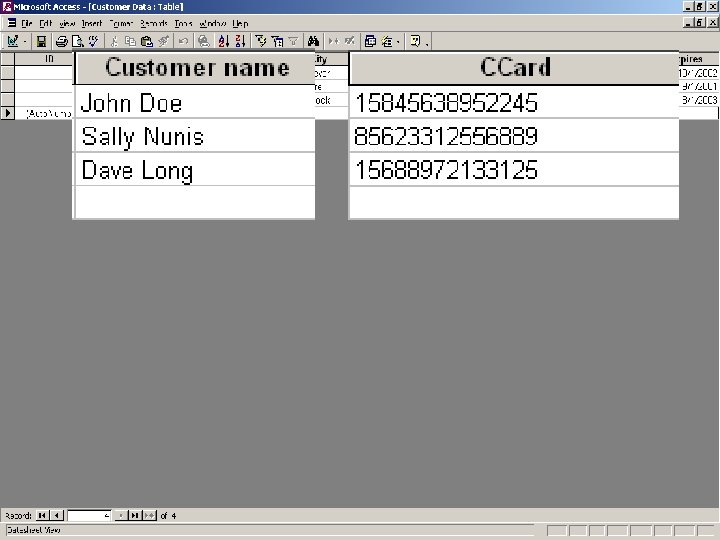
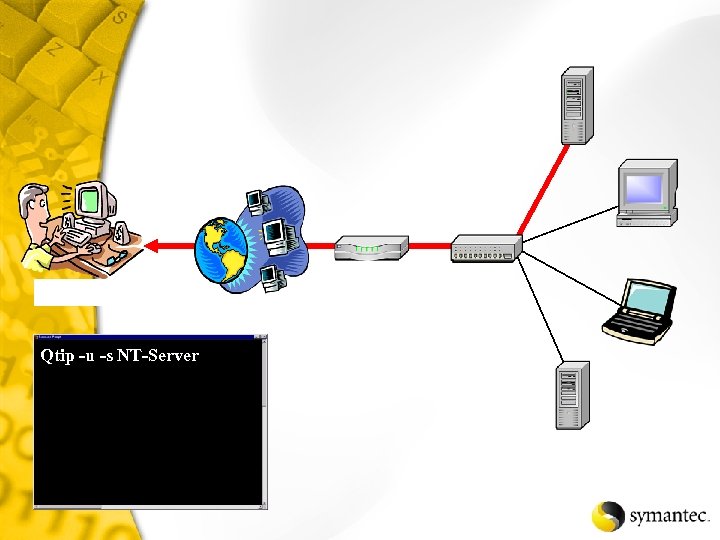 Qtip -u -s NT-Server
Qtip -u -s NT-Server

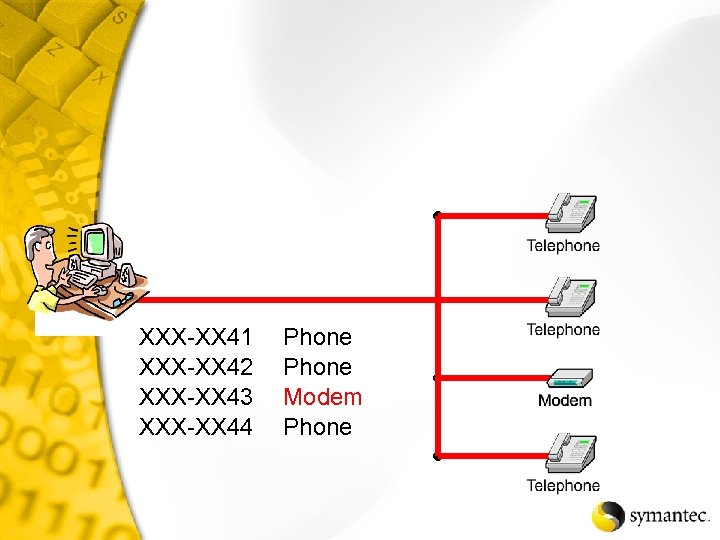 XXX-XX 41 XXX-XX 42 XXX-XX 43 XXX-XX 44 Phone Modem Phone
XXX-XX 41 XXX-XX 42 XXX-XX 43 XXX-XX 44 Phone Modem Phone




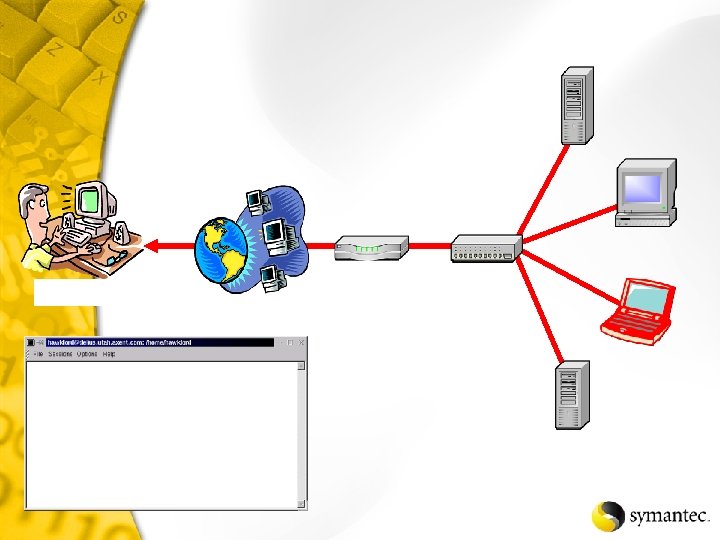
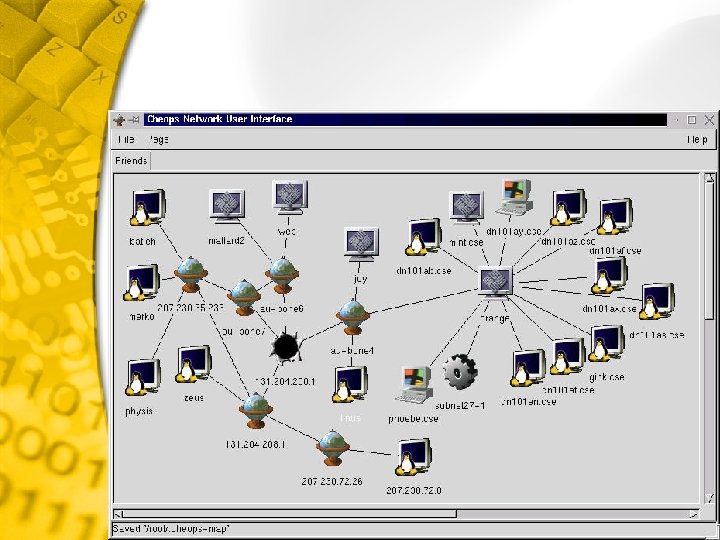


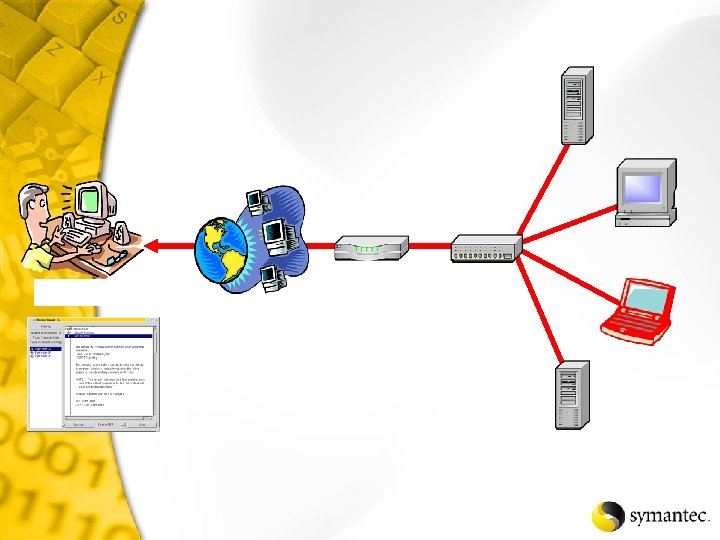

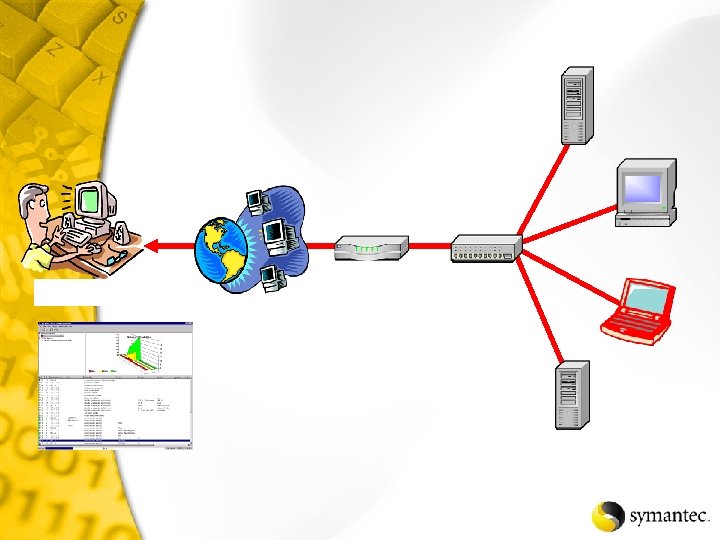
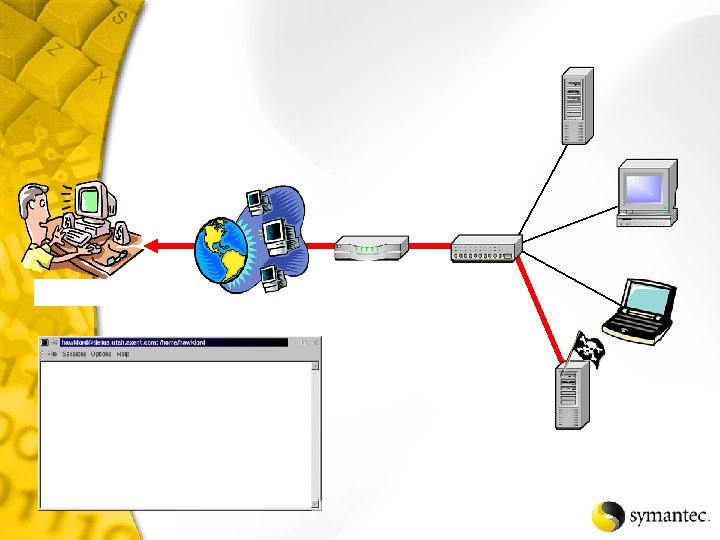
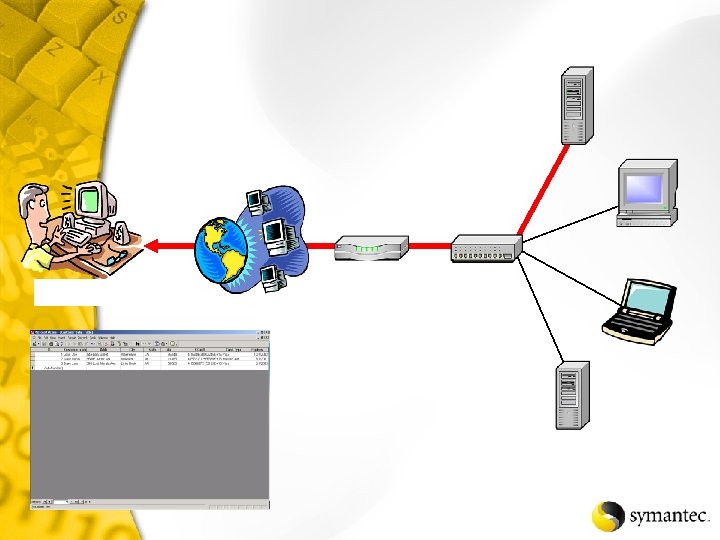
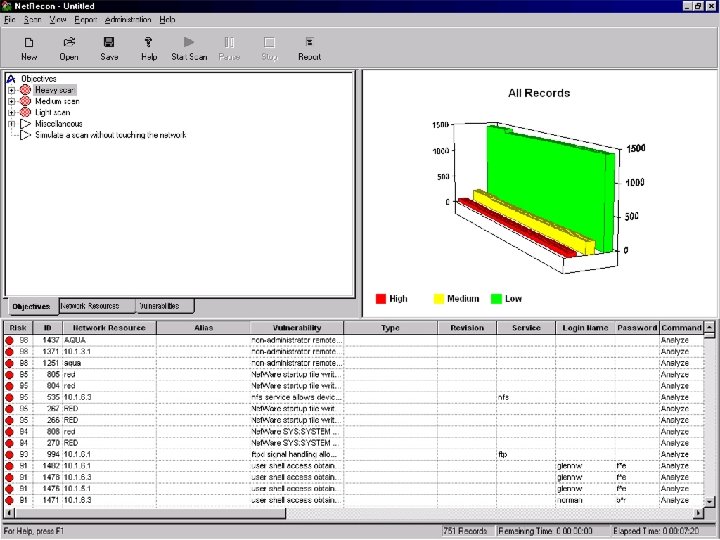 Net. Recon Scans the specified network looking for vulnerabilities
Net. Recon Scans the specified network looking for vulnerabilities








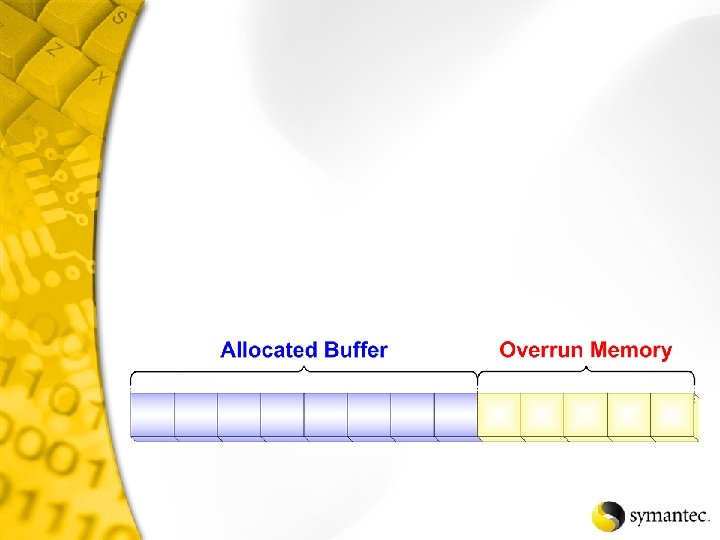
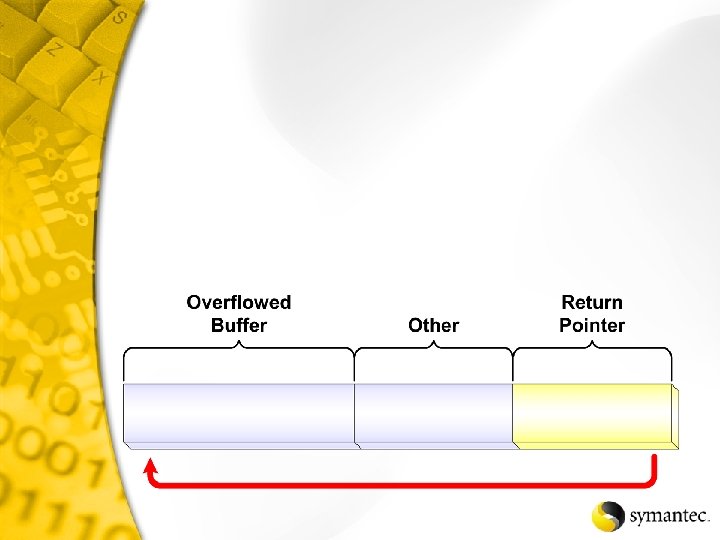





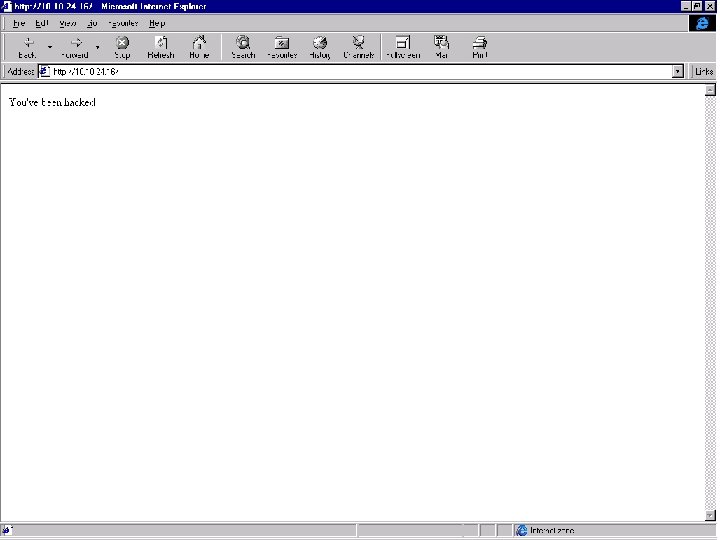
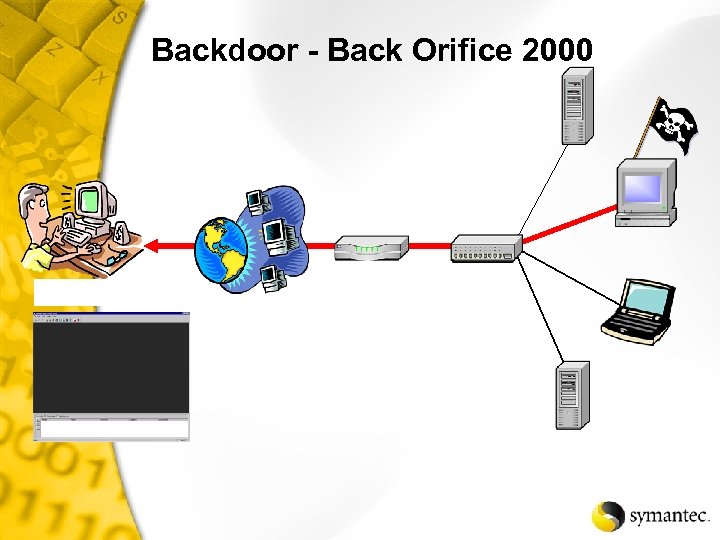 Backdoor - Back Orifice 2000
Backdoor - Back Orifice 2000
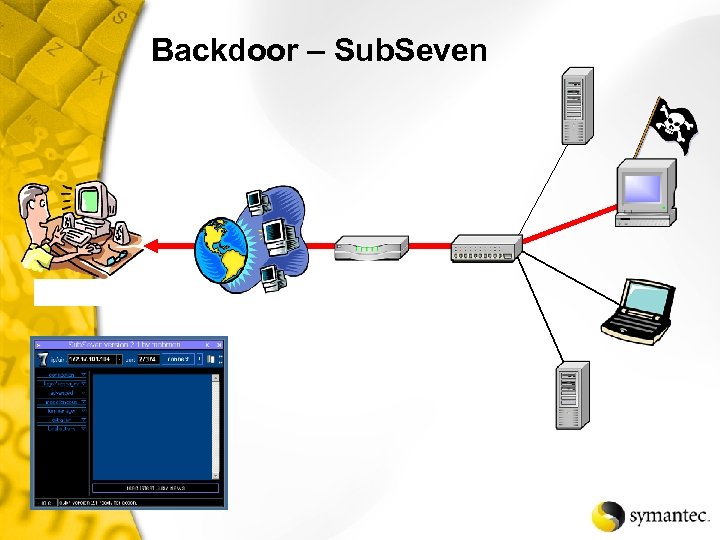 Backdoor – Sub. Seven
Backdoor – Sub. Seven
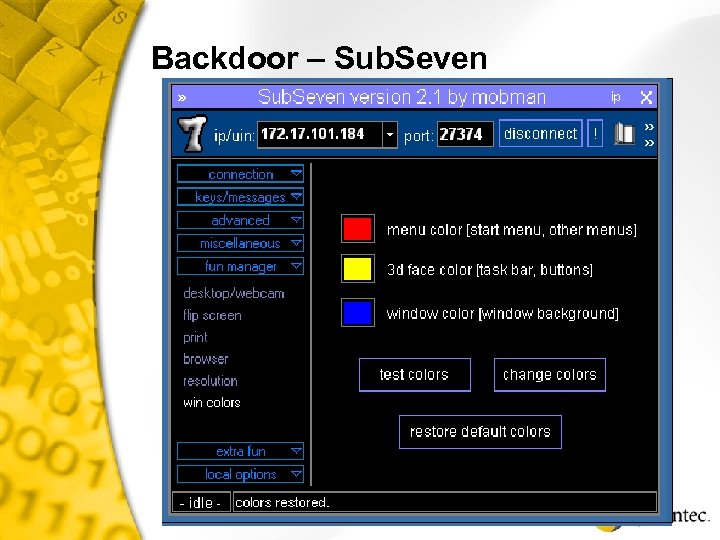 Backdoor – Sub. Seven Connect to remote system
Backdoor – Sub. Seven Connect to remote system
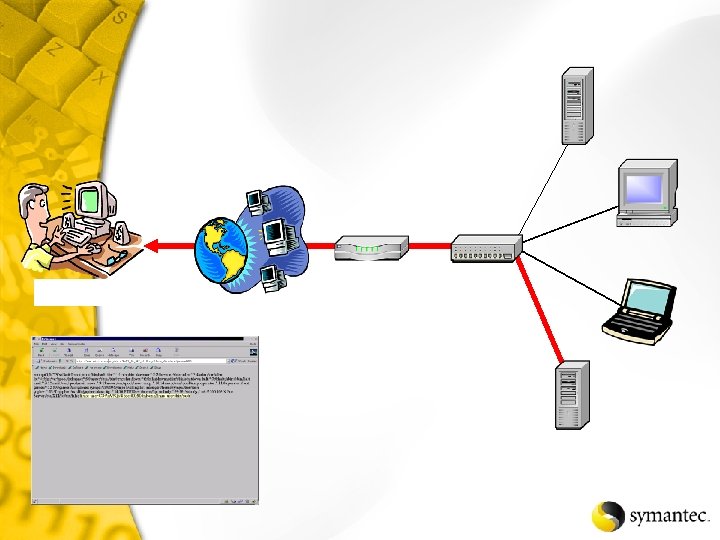
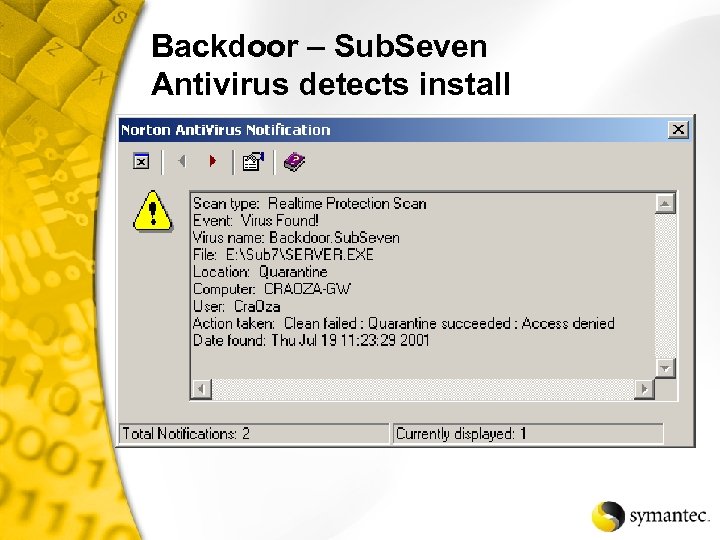 Backdoor – Sub. Seven Antivirus detects install
Backdoor – Sub. Seven Antivirus detects install
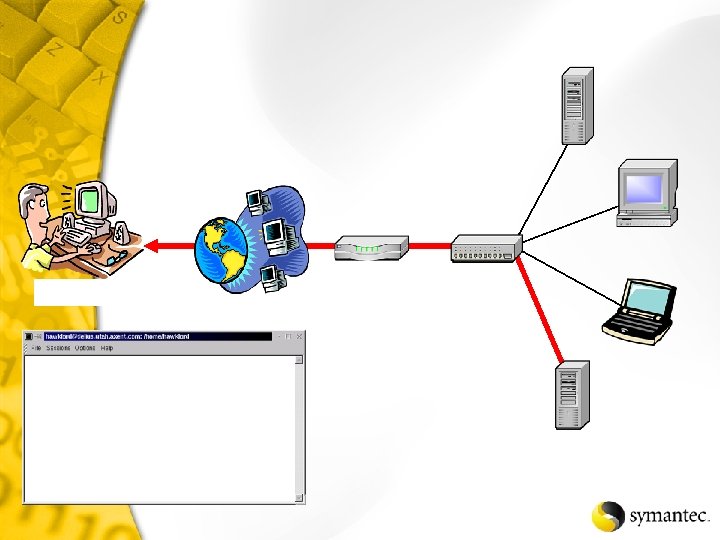
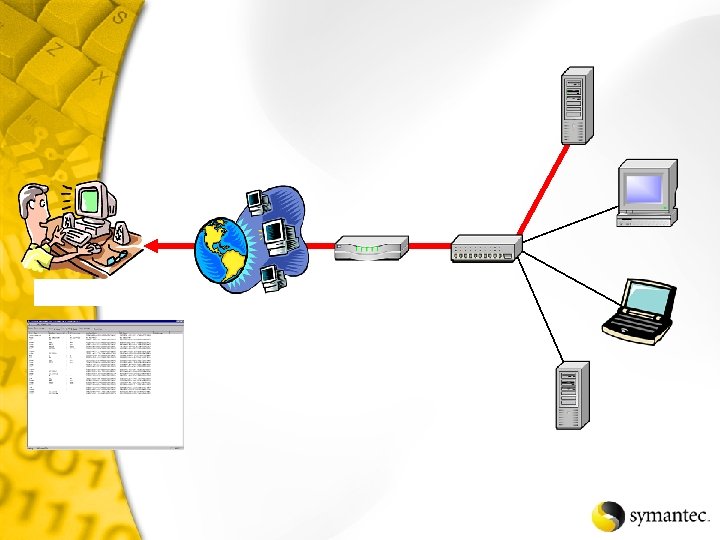
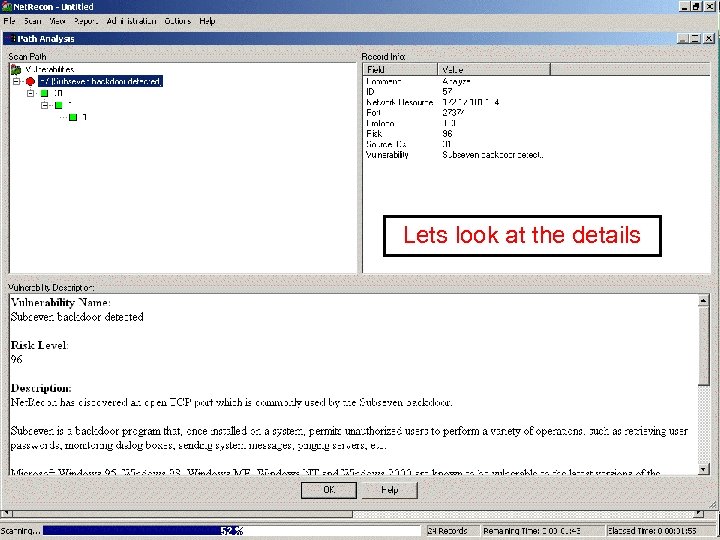 Backdoor – Sub. Seven Net. Recon detects backdoor Start scan Lets look at the details Fond Sub. Seven
Backdoor – Sub. Seven Net. Recon detects backdoor Start scan Lets look at the details Fond Sub. Seven




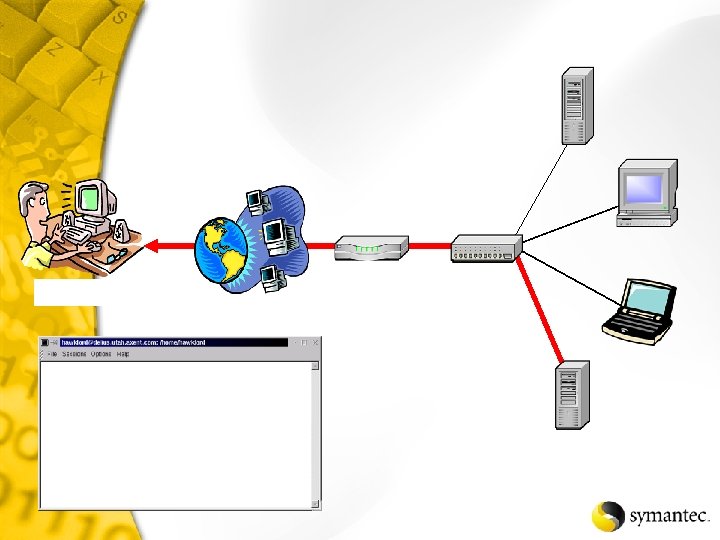
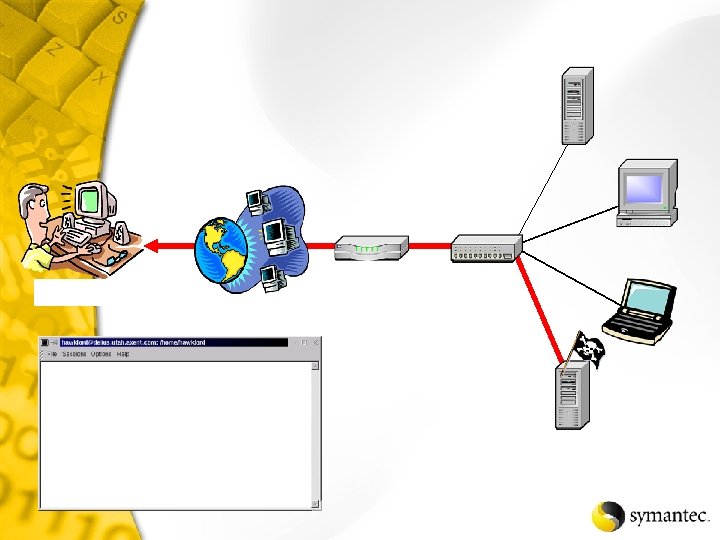
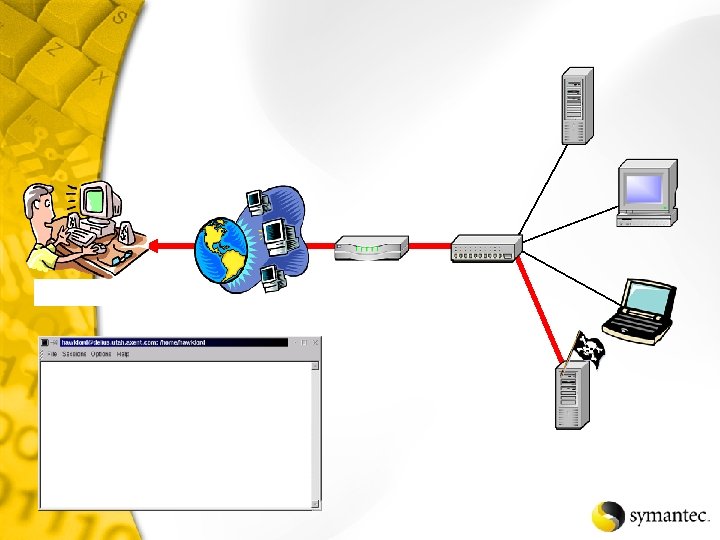
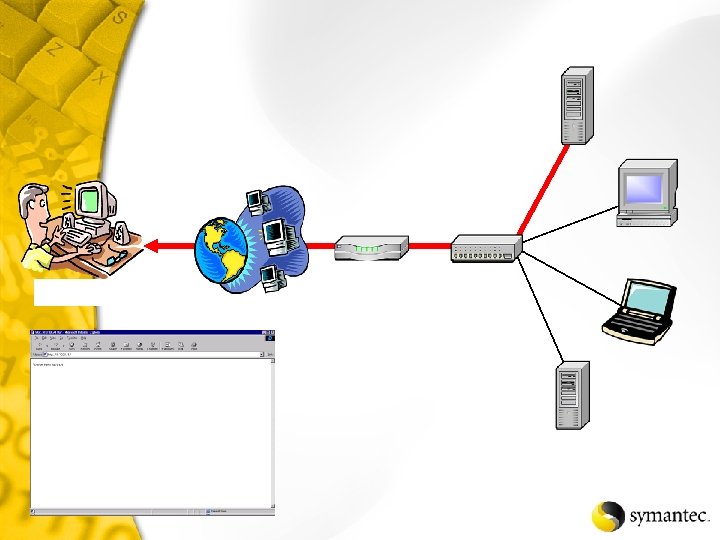
 Now, where can I go?
Now, where can I go?

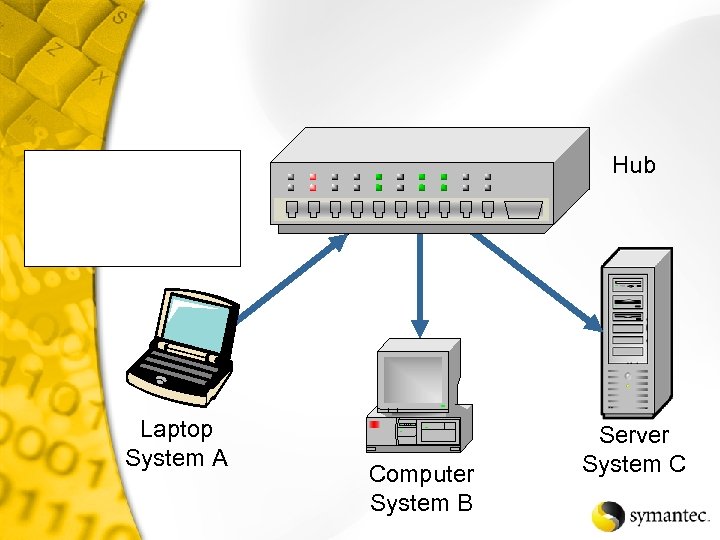 Hub Laptop System A Computer System B Server System C
Hub Laptop System A Computer System B Server System C
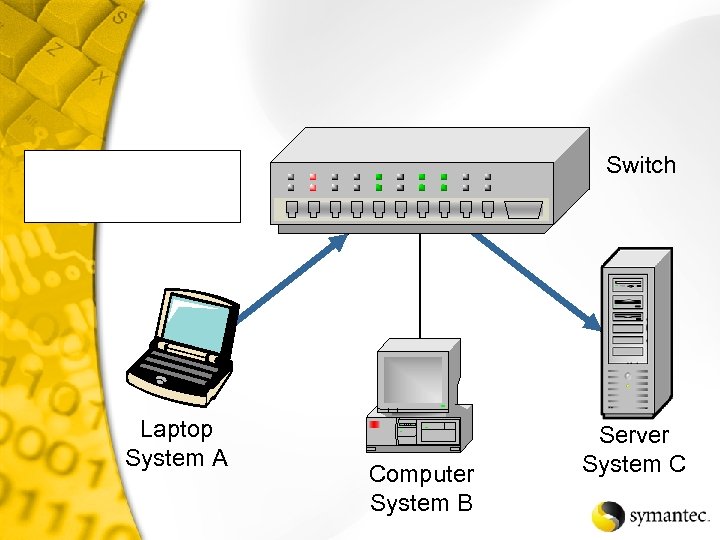 Switch Laptop System A Computer System B Server System C
Switch Laptop System A Computer System B Server System C


 What Else Can We Do…?
What Else Can We Do…?






 Resources
Resources
 Resources
Resources
 Resources No More Resources
Resources No More Resources
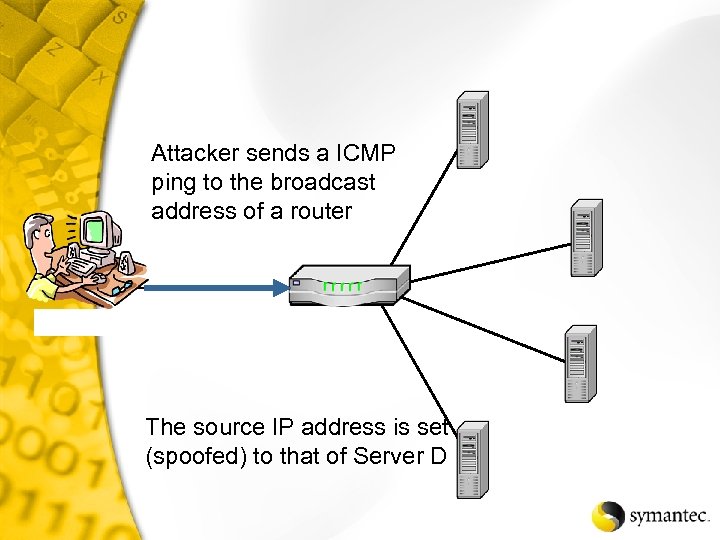 Attacker sends a ICMP ping to the broadcast address of a router The source IP address is set (spoofed) to that of Server D
Attacker sends a ICMP ping to the broadcast address of a router The source IP address is set (spoofed) to that of Server D
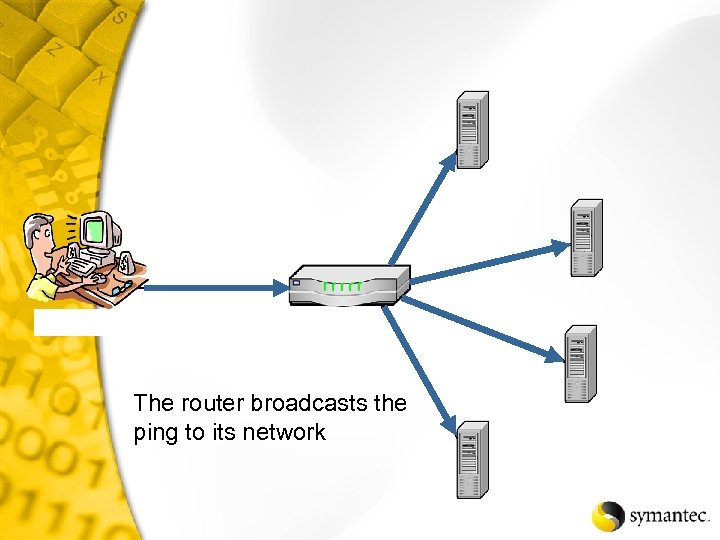 The router broadcasts the ping to its network
The router broadcasts the ping to its network
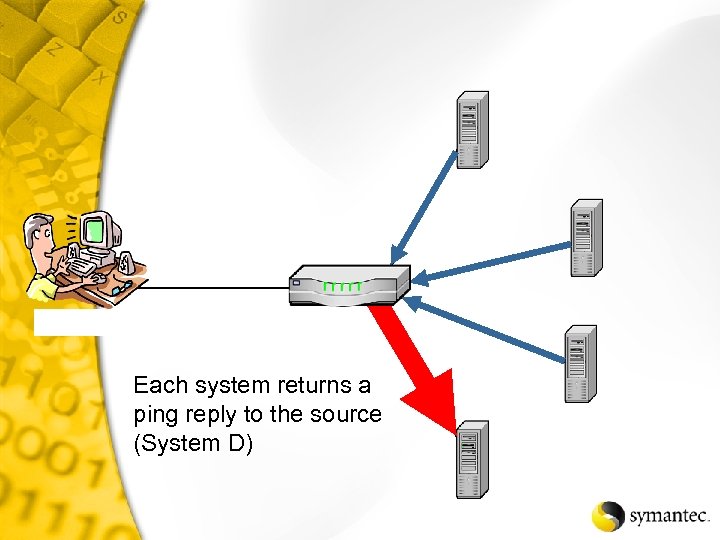 Each system returns a ping reply to the source (System D)
Each system returns a ping reply to the source (System D)
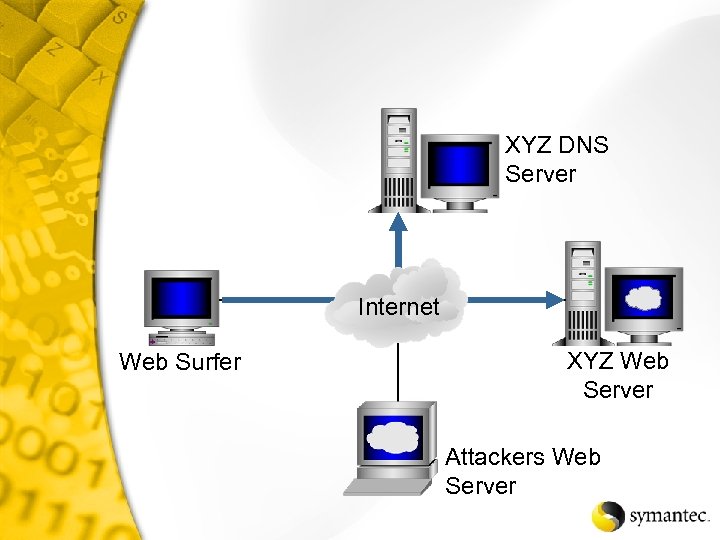 XYZ DNS Server Internet Web Surfer XYZ Web Server Attackers Web Server
XYZ DNS Server Internet Web Surfer XYZ Web Server Attackers Web Server
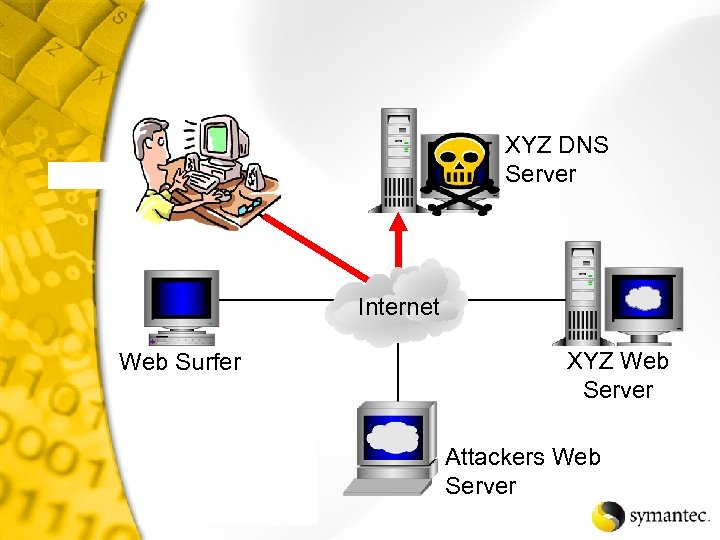 XYZ DNS Server Internet Web Surfer XYZ Web Server Attackers Web Server
XYZ DNS Server Internet Web Surfer XYZ Web Server Attackers Web Server
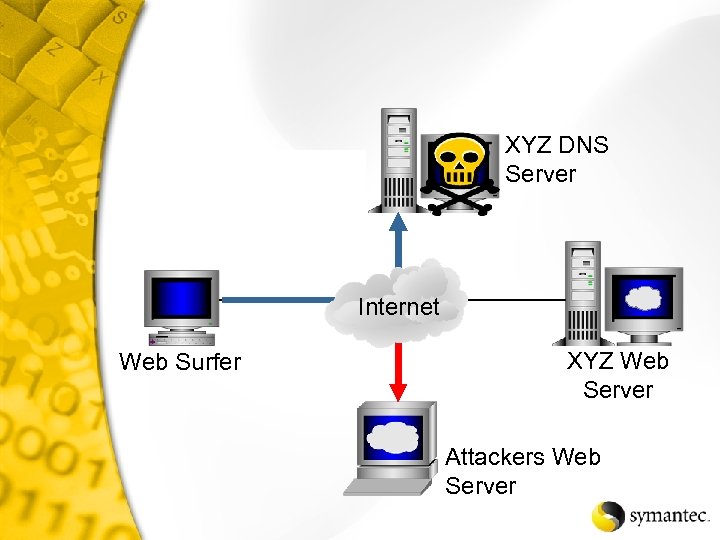 XYZ DNS Server Internet Web Surfer XYZ Web Server Attackers Web Server
XYZ DNS Server Internet Web Surfer XYZ Web Server Attackers Web Server

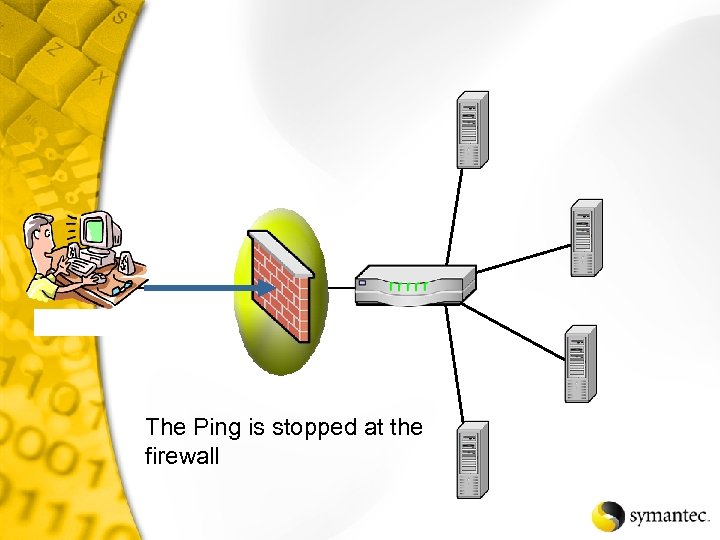 The Ping is stopped at the firewall
The Ping is stopped at the firewall
 Distributed Attack
Distributed Attack
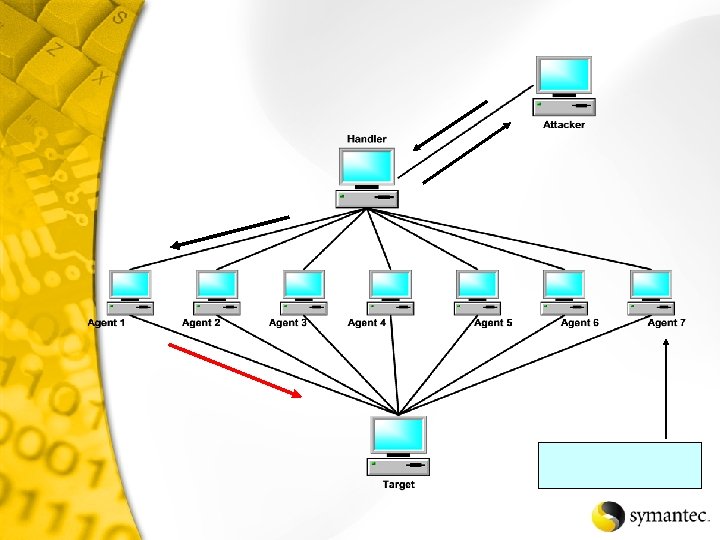
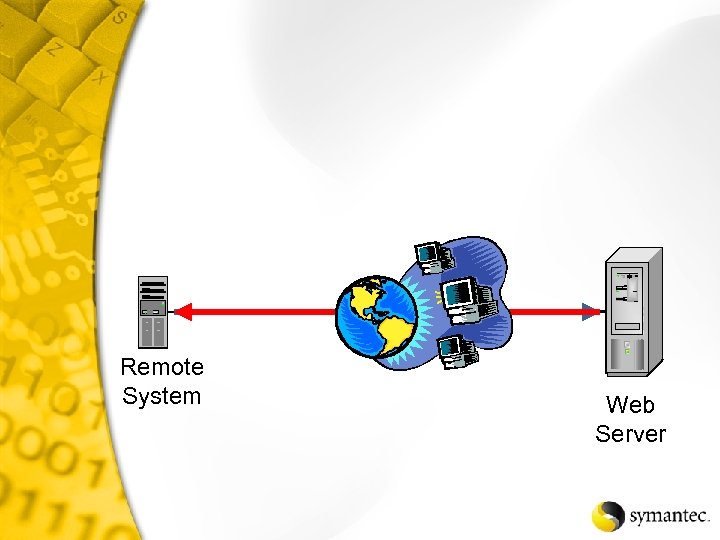 Remote System Web Server
Remote System Web Server
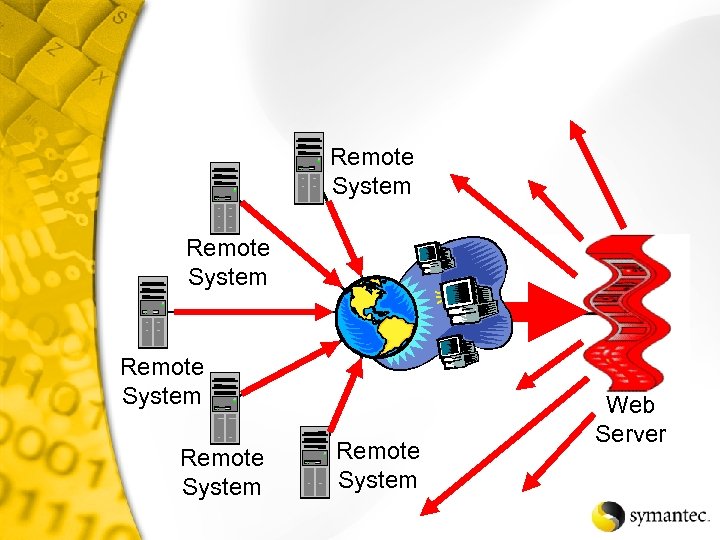 Remote System Remote System Web Server
Remote System Remote System Web Server






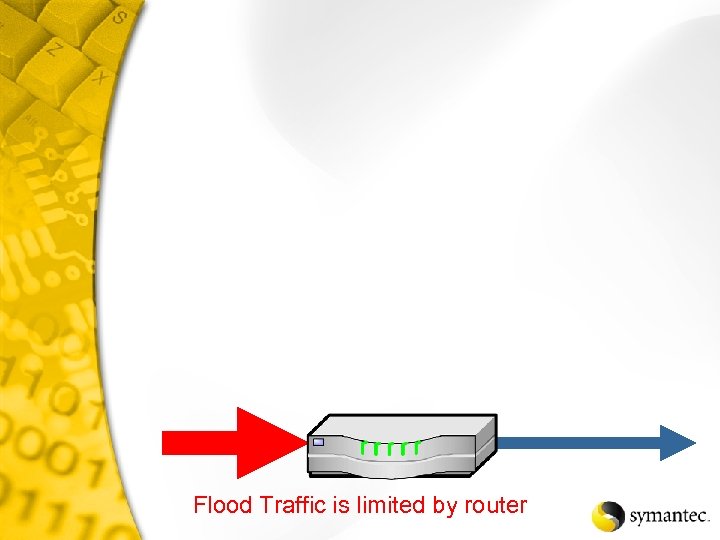 Flood Traffic is limited by router
Flood Traffic is limited by router
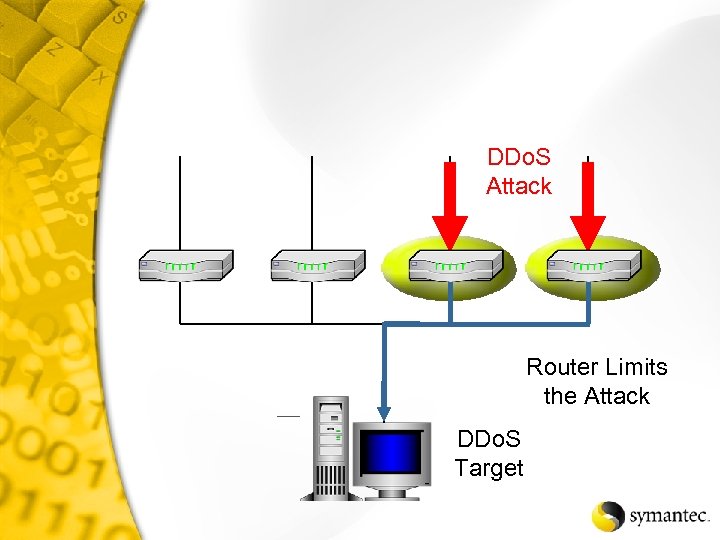 DDo. S Attack Router Limits the Attack DDo. S Target
DDo. S Attack Router Limits the Attack DDo. S Target

 The system power turns off!
The system power turns off!

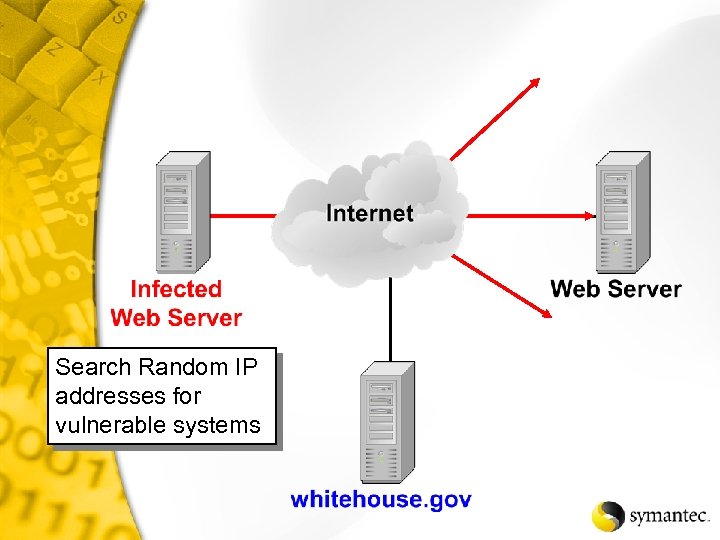 Search Random IP addresses for vulnerable systems
Search Random IP addresses for vulnerable systems
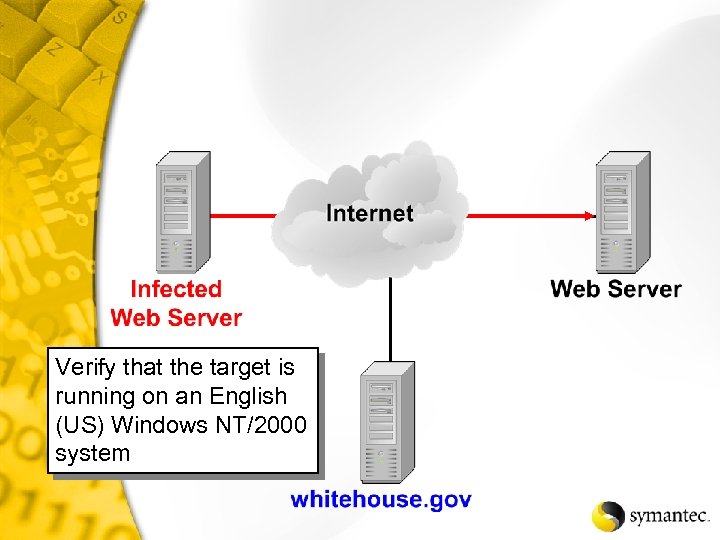 Verify that the target is running on an English (US) Windows NT/2000 system
Verify that the target is running on an English (US) Windows NT/2000 system
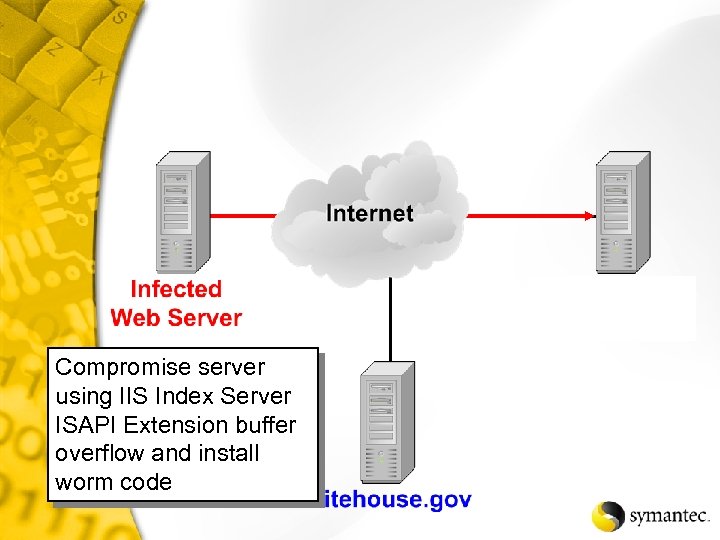 Compromise server using IIS Index Server ISAPI Extension buffer overflow and install worm code
Compromise server using IIS Index Server ISAPI Extension buffer overflow and install worm code
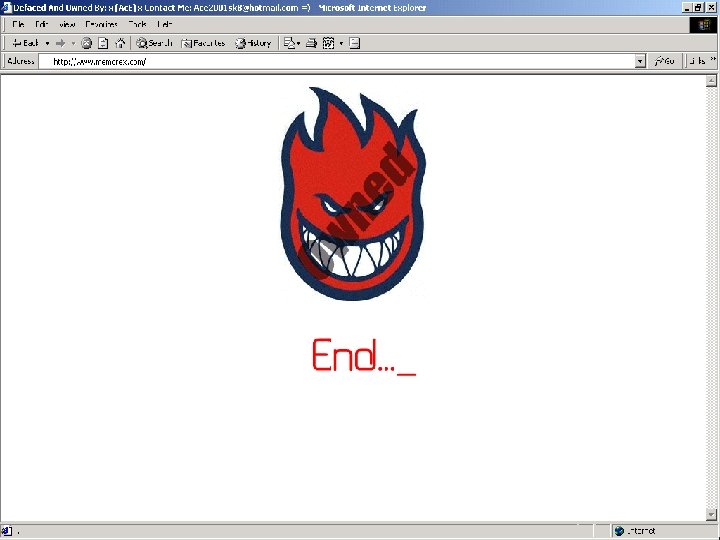
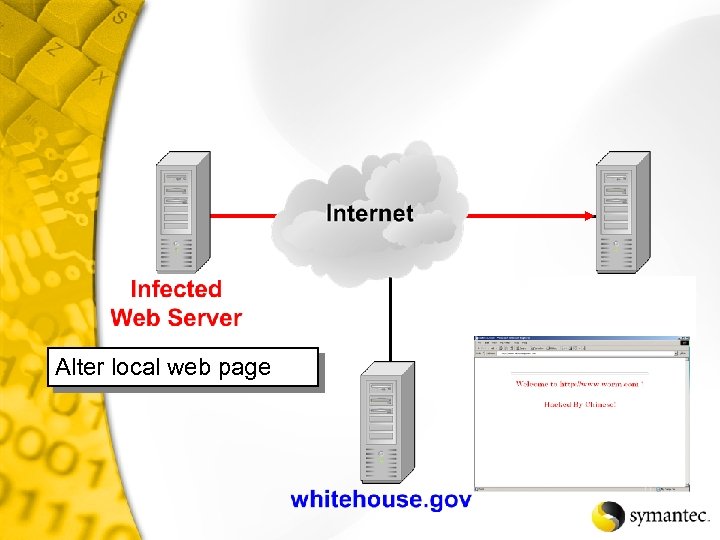 Alter local web page
Alter local web page
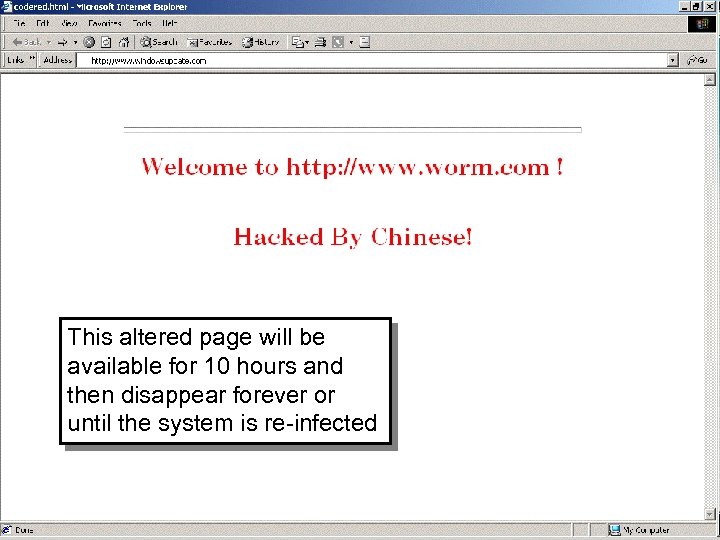 This altered page will be available for 10 hours and then disappear forever or until the system is re-infected
This altered page will be available for 10 hours and then disappear forever or until the system is re-infected
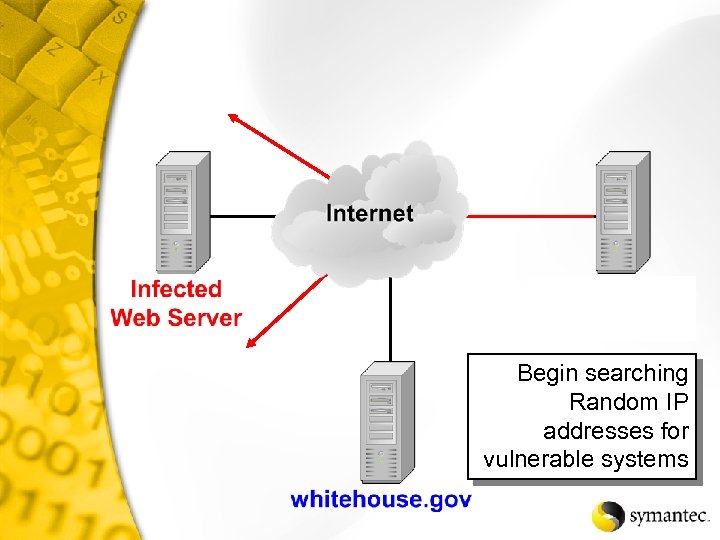 Begin searching Random IP addresses for vulnerable systems
Begin searching Random IP addresses for vulnerable systems
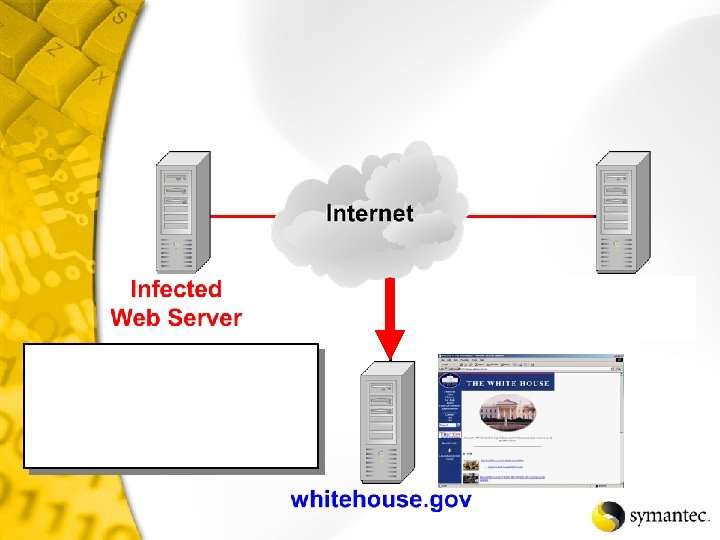
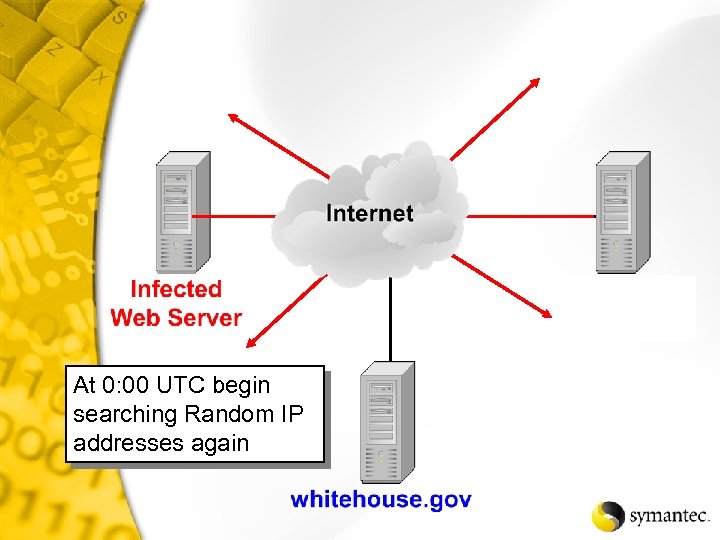 At 0: 00 UTC begin searching Random IP addresses again
At 0: 00 UTC begin searching Random IP addresses again












 Where to Look for More Information
Where to Look for More Information
 Where to Look for More Information
Where to Look for More Information
 Conclusions
Conclusions


