24bf085220a3a7602bb6d0005577d6f2.ppt
- Количество слайдов: 33
 Analytical Projects 1. SHA-3 contest - Your Round 3 Report 2. Analyzing the Influence of a Computer Platform on Ranking of the SHA-3 Candidates in Terms of Performance in Software 3. Homomorphic Encryption 4. Security of GSM and 3 G/4 G Telephony 5. Security of Metro/Subway Cards 6. Security of Voting Machines 7. Survey of Codebreaking Machines and Projects Based on FPGAs, 1
Analytical Projects 1. SHA-3 contest - Your Round 3 Report 2. Analyzing the Influence of a Computer Platform on Ranking of the SHA-3 Candidates in Terms of Performance in Software 3. Homomorphic Encryption 4. Security of GSM and 3 G/4 G Telephony 5. Security of Metro/Subway Cards 6. Security of Voting Machines 7. Survey of Codebreaking Machines and Projects Based on FPGAs, 1
 Cryptographic Standard Contests
Cryptographic Standard Contests
 Cryptographic Standards Before 1997 Secret-Key Block Ciphers IBM & NSA DES – Data Encryption Standard Triple DES 1993 1995 Hash Functions 2003 SHA-1–Secure Hash Algorithm NSA SHA-2 SHA 1970 2005 1999 1977 1980 1990 2000 2010 time
Cryptographic Standards Before 1997 Secret-Key Block Ciphers IBM & NSA DES – Data Encryption Standard Triple DES 1993 1995 Hash Functions 2003 SHA-1–Secure Hash Algorithm NSA SHA-2 SHA 1970 2005 1999 1977 1980 1990 2000 2010 time
 Why a Contest for a Cryptographic Standard? • Avoid back-door theories • Speed-up the acceptance of the standard • Stimulate non-classified research on methods of designing a specific cryptographic transformation • Focus the effort of a relatively small cryptographic community
Why a Contest for a Cryptographic Standard? • Avoid back-door theories • Speed-up the acceptance of the standard • Stimulate non-classified research on methods of designing a specific cryptographic transformation • Focus the effort of a relatively small cryptographic community
 Cryptographic Standard Contests IX. 1997 X. 2000 AES 15 block ciphers 1 winner NESSIE I. 2000 XII. 2002 CRYPTREC V. 2008 XI. 2004 34 stream ciphers 4 HW winners + 4 SW winners e. STREAM XII. 2012 X. 2007 51 hash functions 1 winner SHA-3 96 97 98 99 00 01 02 03 04 05 06 07 08 09 10 11 12 13 time
Cryptographic Standard Contests IX. 1997 X. 2000 AES 15 block ciphers 1 winner NESSIE I. 2000 XII. 2002 CRYPTREC V. 2008 XI. 2004 34 stream ciphers 4 HW winners + 4 SW winners e. STREAM XII. 2012 X. 2007 51 hash functions 1 winner SHA-3 96 97 98 99 00 01 02 03 04 05 06 07 08 09 10 11 12 13 time
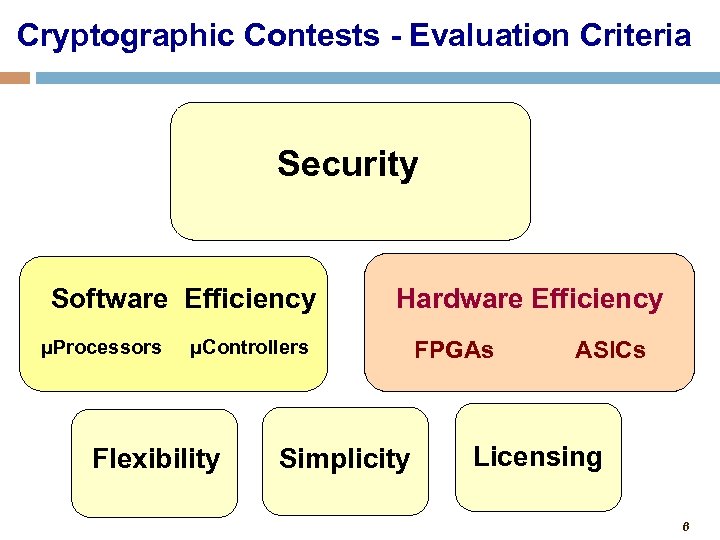 Cryptographic Contests - Evaluation Criteria Security Software Efficiency μProcessors Hardware Efficiency μControllers Flexibility Simplicity FPGAs ASICs Licensing 6
Cryptographic Contests - Evaluation Criteria Security Software Efficiency μProcessors Hardware Efficiency μControllers Flexibility Simplicity FPGAs ASICs Licensing 6
 AES Contest 1997 -2000
AES Contest 1997 -2000
 Rules of the Contest Each team submits Detailed cipher specification Justification of design decisions Source code in C Source code in Java Tentative results of cryptanalysis Test vectors
Rules of the Contest Each team submits Detailed cipher specification Justification of design decisions Source code in C Source code in Java Tentative results of cryptanalysis Test vectors
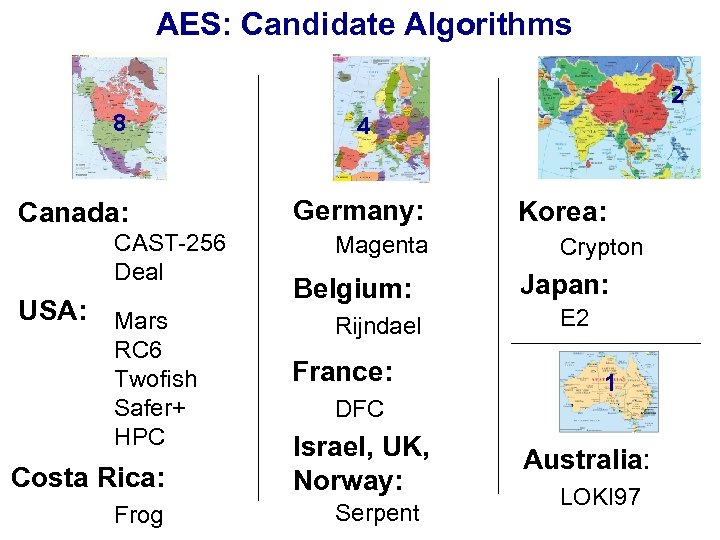 AES: Candidate Algorithms 2 8 Canada: CAST-256 Deal USA: Mars RC 6 Twofish Safer+ HPC Costa Rica: Frog 4 Germany: Magenta Belgium: Rijndael France: DFC Israel, UK, Norway: Serpent Korea: Crypton Japan: E 2 1 Australia: LOKI 97
AES: Candidate Algorithms 2 8 Canada: CAST-256 Deal USA: Mars RC 6 Twofish Safer+ HPC Costa Rica: Frog 4 Germany: Magenta Belgium: Rijndael France: DFC Israel, UK, Norway: Serpent Korea: Crypton Japan: E 2 1 Australia: LOKI 97
 AES Contest Timeline June 1998 15 Candidates CAST-256, Crypton, Deal, DFC, E 2, Frog, HPC, LOKI 97, Magenta, Mars, RC 6, Rijndael, Safer+, Serpent, Twofish, August 1999 Round 1 Security Software efficiency Round 2 5 final candidates Mars, RC 6, Twofish (USA) Rijndael, Serpent (Europe) October 2000 1 winner: Rijndael Belgium Security Software efficiency Hardware efficiency
AES Contest Timeline June 1998 15 Candidates CAST-256, Crypton, Deal, DFC, E 2, Frog, HPC, LOKI 97, Magenta, Mars, RC 6, Rijndael, Safer+, Serpent, Twofish, August 1999 Round 1 Security Software efficiency Round 2 5 final candidates Mars, RC 6, Twofish (USA) Rijndael, Serpent (Europe) October 2000 1 winner: Rijndael Belgium Security Software efficiency Hardware efficiency
 Security: Theoretical attacks better than exhaustive key search Serpent 9 Twofish 23 10 6 Mars Rijndael 7 RC 6 3 15 0 16 5 11 32 16 without 16 mixing rounds 10 5 20 5 10 15 20 25 30 35 # of rounds in the attack/total # of rounds
Security: Theoretical attacks better than exhaustive key search Serpent 9 Twofish 23 10 6 Mars Rijndael 7 RC 6 3 15 0 16 5 11 32 16 without 16 mixing rounds 10 5 20 5 10 15 20 25 30 35 # of rounds in the attack/total # of rounds
 Security: Theoretical attacks better than exhaustive key search 28% Serpent 72% 38% Twofish Mars 62% 31% 69% 70% Rijndael RC 6 30% 25% 75% 0 10 20 30 40 50 60 70 80 90 100 # of rounds in the attack/total # of rounds 100%
Security: Theoretical attacks better than exhaustive key search 28% Serpent 72% 38% Twofish Mars 62% 31% 69% 70% Rijndael RC 6 30% 25% 75% 0 10 20 30 40 50 60 70 80 90 100 # of rounds in the attack/total # of rounds 100%
 Security: Authors of attacks Attacked cipher Team Twofish Kelsey, Kohno, Schneier Ferguson, Stay, Wagner, Whiting Serpent Knudsen, Meier MARS Serpent Rijndael RC 6 Other groups Lucks, U. Mannheim Twofish Gilbert, Minier, France Telecom Gilbert, Handschuh, Joux, Vaudenay, France Telecom
Security: Authors of attacks Attacked cipher Team Twofish Kelsey, Kohno, Schneier Ferguson, Stay, Wagner, Whiting Serpent Knudsen, Meier MARS Serpent Rijndael RC 6 Other groups Lucks, U. Mannheim Twofish Gilbert, Minier, France Telecom Gilbert, Handschuh, Joux, Vaudenay, France Telecom
 NIST Report: Security & Simplicity Security High MARS Twofish Serpent Rijndael Adequate RC 6 Complex Simple Simplicity
NIST Report: Security & Simplicity Security High MARS Twofish Serpent Rijndael Adequate RC 6 Complex Simple Simplicity
![Efficiency in software: NIST-specified platform 200 MHz Pentium Pro, Borland C++ Throughput [Mbits/s] 128 Efficiency in software: NIST-specified platform 200 MHz Pentium Pro, Borland C++ Throughput [Mbits/s] 128](https://present5.com/presentation/24bf085220a3a7602bb6d0005577d6f2/image-15.jpg) Efficiency in software: NIST-specified platform 200 MHz Pentium Pro, Borland C++ Throughput [Mbits/s] 128 -bit key 192 -bit key 30 256 -bit key 25 20 15 10 5 0 Rijndael RC 6 Twofish Mars Serpent
Efficiency in software: NIST-specified platform 200 MHz Pentium Pro, Borland C++ Throughput [Mbits/s] 128 -bit key 192 -bit key 30 256 -bit key 25 20 15 10 5 0 Rijndael RC 6 Twofish Mars Serpent
 AES Contest: Encryption time in clock cycles on various platforms Twofish team: Bruce Schneier & Doug Whiting better
AES Contest: Encryption time in clock cycles on various platforms Twofish team: Bruce Schneier & Doug Whiting better
 NIST Report: Software Efficiency Encryption and Decryption Speed 32 -bit processors high medium low 64 -bit processors DSPs RC 6 Rijndael Twofish Rijndael Mars Twofish Mars RC 6 Serpent
NIST Report: Software Efficiency Encryption and Decryption Speed 32 -bit processors high medium low 64 -bit processors DSPs RC 6 Rijndael Twofish Rijndael Mars Twofish Mars RC 6 Serpent
 NIST Report: Software Efficiency Encryption and decryption speed in software on smart cards 8 -bit processors high medium low 32 -bit processors Rijndael RC 6 Mars Twofish Mars Serpent Twofish Serpent
NIST Report: Software Efficiency Encryption and decryption speed in software on smart cards 8 -bit processors high medium low 32 -bit processors Rijndael RC 6 Mars Twofish Mars Serpent Twofish Serpent
 Efficiency in Software Strong dependence on: 1. Instruction set architecture (e. g. , variable rotations) 2. Programming language (assembler, C, Java) 3. Compiler 4. Compiler options 5. Programming style
Efficiency in Software Strong dependence on: 1. Instruction set architecture (e. g. , variable rotations) 2. Programming language (assembler, C, Java) 3. Compiler 4. Compiler options 5. Programming style
![Efficiency in FPGAs: Speed Xilinx Virtex XCV-1000 Throughput [Mbit/s] 500 450 400 350 300 Efficiency in FPGAs: Speed Xilinx Virtex XCV-1000 Throughput [Mbit/s] 500 450 400 350 300](https://present5.com/presentation/24bf085220a3a7602bb6d0005577d6f2/image-20.jpg) Efficiency in FPGAs: Speed Xilinx Virtex XCV-1000 Throughput [Mbit/s] 500 450 400 350 300 431 444 George Mason University 414 University of Southern California 353 Worcester Polytechnic Institute 294 250 200 150 100 177 173 149 143 104 62 112 88 102 61 50 0 Serpent Rijndael x 8 Twofish Serpent RC 6 x 1 Mars
Efficiency in FPGAs: Speed Xilinx Virtex XCV-1000 Throughput [Mbit/s] 500 450 400 350 300 431 444 George Mason University 414 University of Southern California 353 Worcester Polytechnic Institute 294 250 200 150 100 177 173 149 143 104 62 112 88 102 61 50 0 Serpent Rijndael x 8 Twofish Serpent RC 6 x 1 Mars
![Efficiency in ASICs: Speed Throughput [Mbit/s] 700 MOSIS 0. 5μm, NSA Group 606 128 Efficiency in ASICs: Speed Throughput [Mbit/s] 700 MOSIS 0. 5μm, NSA Group 606 128](https://present5.com/presentation/24bf085220a3a7602bb6d0005577d6f2/image-21.jpg) Efficiency in ASICs: Speed Throughput [Mbit/s] 700 MOSIS 0. 5μm, NSA Group 606 128 -bit key scheduling 600 500 3 -in-1 (128, 192, 256 bit) key scheduling 443 400 300 202 200 105 103 104 57 57 100 0 Rijndael Serpent x 1 Twofish RC 6 Mars
Efficiency in ASICs: Speed Throughput [Mbit/s] 700 MOSIS 0. 5μm, NSA Group 606 128 -bit key scheduling 600 500 3 -in-1 (128, 192, 256 bit) key scheduling 443 400 300 202 200 105 103 104 57 57 100 0 Rijndael Serpent x 1 Twofish RC 6 Mars
 Lessons Learned Results for ASICs matched very well results for FPGAs, and were both very different than software FPGA ASIC x 8 x 1 GMU+USC, Xilinx Virtex XCV-1000 x 1 NSA Team, ASIC, 0. 5μm MOSIS Serpent fastest in hardware, slowest in software
Lessons Learned Results for ASICs matched very well results for FPGAs, and were both very different than software FPGA ASIC x 8 x 1 GMU+USC, Xilinx Virtex XCV-1000 x 1 NSA Team, ASIC, 0. 5μm MOSIS Serpent fastest in hardware, slowest in software
 Lessons Learned Hardware results matter! Final round of the AES Contest, 2000 Speed in FPGAs GMU results Votes at the AES 3 conference
Lessons Learned Hardware results matter! Final round of the AES Contest, 2000 Speed in FPGAs GMU results Votes at the AES 3 conference
 Limitations of the AES Evaluation • Optimization for maximum throughput • Single high-speed architecture per candidate • No use of embedded resources of FPGAs (Block RAMs, dedicated multipliers) • Single FPGA family from a single vendor: Xilinx Virtex
Limitations of the AES Evaluation • Optimization for maximum throughput • Single high-speed architecture per candidate • No use of embedded resources of FPGAs (Block RAMs, dedicated multipliers) • Single FPGA family from a single vendor: Xilinx Virtex
 SHA-3 Contest 2007 -2012
SHA-3 Contest 2007 -2012
 NIST SHA-3 Contest - Timeline Round 1 51 candidates 14 July 2009 Oct. 2008 Round 3 Round 2 5 Dec. 2010 1 Mid 2012
NIST SHA-3 Contest - Timeline Round 1 51 candidates 14 July 2009 Oct. 2008 Round 3 Round 2 5 Dec. 2010 1 Mid 2012
 SHA-3 Contest – Recent and Future Milestones 23 Aug 2010 – Second SHA-3 Candidate Conference, Santa Barbara, USA 9 Dec 2010 – Announcement of 5 algorithms qualified to Round 3 31 Jan 2011 – Acceptance of final tweaks for Round 3 Candidates 16 Feb 2011 – Publication of Round 2 report 22 Mar 2012 – Third SHA-3 Candidate Conference, Washington D. C. or Gaithersburg, MD, USA Summer 2012 – Announcement of the winner Beginning of 2013 – Publication of the new FIPS standard
SHA-3 Contest – Recent and Future Milestones 23 Aug 2010 – Second SHA-3 Candidate Conference, Santa Barbara, USA 9 Dec 2010 – Announcement of 5 algorithms qualified to Round 3 31 Jan 2011 – Acceptance of final tweaks for Round 3 Candidates 16 Feb 2011 – Publication of Round 2 report 22 Mar 2012 – Third SHA-3 Candidate Conference, Washington D. C. or Gaithersburg, MD, USA Summer 2012 – Announcement of the winner Beginning of 2013 – Publication of the new FIPS standard
 e. BACS: ECRYPT Benchmarking of Cryptographic Systems: http: //bench. cr. yp. to/ SUPERCOP - toolkit developed by D. Bernstein and T. Lange for measuring performance of cryptographic software • measurements on multiple machines (currently over 90) • each implementation is recompiled multiple times (currently over 1600 times) with various compiler options • time measured in clock cycles/byte for multiple input/output sizes • median, lower quartile (25 th percentile), and upper quartile (75 th percentile) reported • standardized function arguments (common API) 28
e. BACS: ECRYPT Benchmarking of Cryptographic Systems: http: //bench. cr. yp. to/ SUPERCOP - toolkit developed by D. Bernstein and T. Lange for measuring performance of cryptographic software • measurements on multiple machines (currently over 90) • each implementation is recompiled multiple times (currently over 1600 times) with various compiler options • time measured in clock cycles/byte for multiple input/output sizes • median, lower quartile (25 th percentile), and upper quartile (75 th percentile) reported • standardized function arguments (common API) 28
 SUPERCOP Extension for Microcontrollers – XBX: 2009 -present Allows on-board timing measurements Supports at least the following microcontrollers: 8 -bit: Atmel ATmega 1284 P (AVR) Developers: Ø Christian Wenzel-Benner, ITK Engineering AG, Germany Ø Jens Gräf, Li. Net. Co Gmb. H, Heiger, Germany 32 -bit: TI AR 7 (MIPS) Atmel AT 91 RM 9200 (ARM 920 T) Intel XScale IXP 420 (ARM v 5 TE) Cortex-M 3 (ARM)
SUPERCOP Extension for Microcontrollers – XBX: 2009 -present Allows on-board timing measurements Supports at least the following microcontrollers: 8 -bit: Atmel ATmega 1284 P (AVR) Developers: Ø Christian Wenzel-Benner, ITK Engineering AG, Germany Ø Jens Gräf, Li. Net. Co Gmb. H, Heiger, Germany 32 -bit: TI AR 7 (MIPS) Atmel AT 91 RM 9200 (ARM 920 T) Intel XScale IXP 420 (ARM v 5 TE) Cortex-M 3 (ARM)
 ATHENa – Automated Tool for Hardware Evaluatio. N http: //cryptography. gmu. edu/athena Open-source benchmarking environment, written in Perl, aimed at AUTOMATED generation of OPTIMIZED results for MULTIPLE hardware platforms. The most recent version 0. 6. 2 released in June 2011. Full features in ATHENa 1. 0 to be released in 2012. 30
ATHENa – Automated Tool for Hardware Evaluatio. N http: //cryptography. gmu. edu/athena Open-source benchmarking environment, written in Perl, aimed at AUTOMATED generation of OPTIMIZED results for MULTIPLE hardware platforms. The most recent version 0. 6. 2 released in June 2011. Full features in ATHENa 1. 0 to be released in 2012. 30
 Basic Dataflow of ATHENa User FPGA Synthesis and Implementation 6 5 Database query ATHENa Server 2 Ranking of designs HDL + scripts + configuration files 3 Result Summary + Database Entries 1 Download scripts and configuration files 8 HDL + FPGA Tools 4 Designer Database Entries 0 Interfaces + Testbenches 31
Basic Dataflow of ATHENa User FPGA Synthesis and Implementation 6 5 Database query ATHENa Server 2 Ranking of designs HDL + scripts + configuration files 3 Result Summary + Database Entries 1 Download scripts and configuration files 8 HDL + FPGA Tools 4 Designer Database Entries 0 Interfaces + Testbenches 31
 Hardware Projects 1. Low Area Implementation of a Selected Lightweight Hash Function 2. Use of Embedded FPGA Resources (BRAMs, DSP units, etc. ) in Implementations of 5 Round 3 SHA-3 Candidates 3. Your ECE 545 project + extension discussed with the Instructor 32
Hardware Projects 1. Low Area Implementation of a Selected Lightweight Hash Function 2. Use of Embedded FPGA Resources (BRAMs, DSP units, etc. ) in Implementations of 5 Round 3 SHA-3 Candidates 3. Your ECE 545 project + extension discussed with the Instructor 32
 Software Projects 1. Optimizing Best Available Software Implementations of the SHA-3 candidates (using coding techniques, special instructions, assembly language, etc. ). 2. Comparing the sphlib 2. 1 C (or Java) Implementations of Hash Functions with the Best C (or Java) Implementations Submitted to e. BACS. 3. Porting Selected C Implementations of the SHA-3 Candidates to the TI MSP 430 microcontroller or Other Microcontroller Available to You. 4. Software Implementations of Selected Lightweight Hash 33
Software Projects 1. Optimizing Best Available Software Implementations of the SHA-3 candidates (using coding techniques, special instructions, assembly language, etc. ). 2. Comparing the sphlib 2. 1 C (or Java) Implementations of Hash Functions with the Best C (or Java) Implementations Submitted to e. BACS. 3. Porting Selected C Implementations of the SHA-3 Candidates to the TI MSP 430 microcontroller or Other Microcontroller Available to You. 4. Software Implementations of Selected Lightweight Hash 33


