0ad5aeafa85f053b9966936555e142bd.ppt
- Количество слайдов: 14
 Analysis of Direct Anonymous Attestation (DAA) Sudip Regmi Ilya Pirkin
Analysis of Direct Anonymous Attestation (DAA) Sudip Regmi Ilya Pirkin
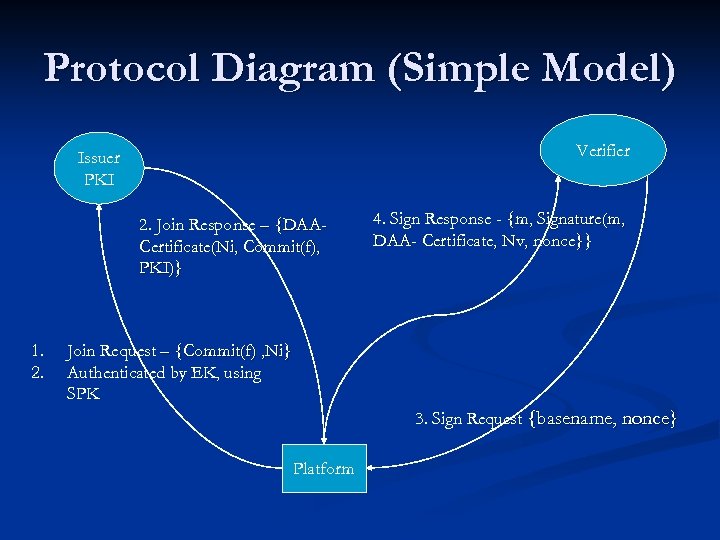 Protocol Diagram (Simple Model) Verifier Issuer PKI 2. Join Response – {DAACertificate(Ni, Commit(f), PKI)} 1. 2. 4. Sign Response - {m, Signature(m, DAA- Certificate, Nv, nonce}} Join Request – {Commit(f) , Ni} Authenticated by EK, using SPK 3. Sign Request {basename, nonce} Platform
Protocol Diagram (Simple Model) Verifier Issuer PKI 2. Join Response – {DAACertificate(Ni, Commit(f), PKI)} 1. 2. 4. Sign Response - {m, Signature(m, DAA- Certificate, Nv, nonce}} Join Request – {Commit(f) , Ni} Authenticated by EK, using SPK 3. Sign Request {basename, nonce} Platform
 Security Properties n Correctness n The verifier completes the protocol for message m only if: • • m was signed by an honest TPM using a DAA-Certificate and verifier’s basename; The DAA-Certificate was issued by an honest Issuer for the TPM before signing message m. The issuer which the verifier knows is the same as the issuer which generated DAA-Certificate(f) used in the signature TPM is not on the rogue list
Security Properties n Correctness n The verifier completes the protocol for message m only if: • • m was signed by an honest TPM using a DAA-Certificate and verifier’s basename; The DAA-Certificate was issued by an honest Issuer for the TPM before signing message m. The issuer which the verifier knows is the same as the issuer which generated DAA-Certificate(f) used in the signature TPM is not on the rogue list
 Security Properties n n Anonymity – A transaction of an honest platform cannot be linked with its Endorsement Key (EK). n Checked by comparing pseudonyms in the sign response and the join request. If they are equal anonymity breaks Unlinkability – Transactions of an honest platform with different Verifiers are not linkable. n Checked by comparing PKI, pseudonyms in sign responses. Transactions are linkable if: n n Values are the same if came from the same TPM Values are different if came from different TPM
Security Properties n n Anonymity – A transaction of an honest platform cannot be linked with its Endorsement Key (EK). n Checked by comparing pseudonyms in the sign response and the join request. If they are equal anonymity breaks Unlinkability – Transactions of an honest platform with different Verifiers are not linkable. n Checked by comparing PKI, pseudonyms in sign responses. Transactions are linkable if: n n Values are the same if came from the same TPM Values are different if came from different TPM
 Level of Abstraction n Simple Model Treats host and TPM as one player – the platform. Ignores any interactions between these two players n Only four messages and three player n Simple Message Format. n n Full Model Considers interaction between Host and TPM n Messages reflect actual protocol messages with the exception of the interactive proofs of knowledge n
Level of Abstraction n Simple Model Treats host and TPM as one player – the platform. Ignores any interactions between these two players n Only four messages and three player n Simple Message Format. n n Full Model Considers interaction between Host and TPM n Messages reflect actual protocol messages with the exception of the interactive proofs of knowledge n
 Modeling Approach Primitives are secure n Interactive Proof of Knowledge is modeled by limiting Adversary’s capabilities n n Can’t replay Join Request n Can’t modify Join Request
Modeling Approach Primitives are secure n Interactive Proof of Knowledge is modeled by limiting Adversary’s capabilities n n Can’t replay Join Request n Can’t modify Join Request
 Adversary’s Capabilities Modeled n n n n Can intercept messages on the network Checks for use of different PK in DAA-Certificate Checks to see if he can link two transactions (Join Request with Sign Response, Sign Response with another Sign Response) Can replay intercepted messages blindly Replays Sign Response for a seen Sign Request Randomly Constructs a Sign Response in response to a seen Sign Request(Constructs from an earlier Join and Sign Response) Constructs a Sign Request with the issuer's basename. (The idea is to make the TPM to generate the same pseudonym as in the join protocol)
Adversary’s Capabilities Modeled n n n n Can intercept messages on the network Checks for use of different PK in DAA-Certificate Checks to see if he can link two transactions (Join Request with Sign Response, Sign Response with another Sign Response) Can replay intercepted messages blindly Replays Sign Response for a seen Sign Request Randomly Constructs a Sign Response in response to a seen Sign Request(Constructs from an earlier Join and Sign Response) Constructs a Sign Request with the issuer's basename. (The idea is to make the TPM to generate the same pseudonym as in the join protocol)
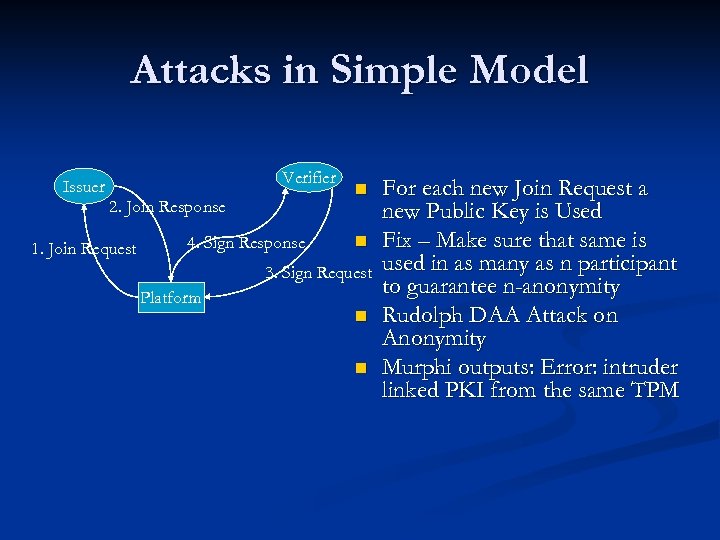 Attacks in Simple Model Verifier Issuer 2. Join Response 1. Join Request 4. Sign Response n n 3. Sign Request Platform n n For each new Join Request a new Public Key is Used Fix – Make sure that same is used in as many as n participant to guarantee n-anonymity Rudolph DAA Attack on Anonymity Murphi outputs: Error: intruder linked PKI from the same TPM
Attacks in Simple Model Verifier Issuer 2. Join Response 1. Join Request 4. Sign Response n n 3. Sign Request Platform n n For each new Join Request a new Public Key is Used Fix – Make sure that same is used in as many as n participant to guarantee n-anonymity Rudolph DAA Attack on Anonymity Murphi outputs: Error: intruder linked PKI from the same TPM
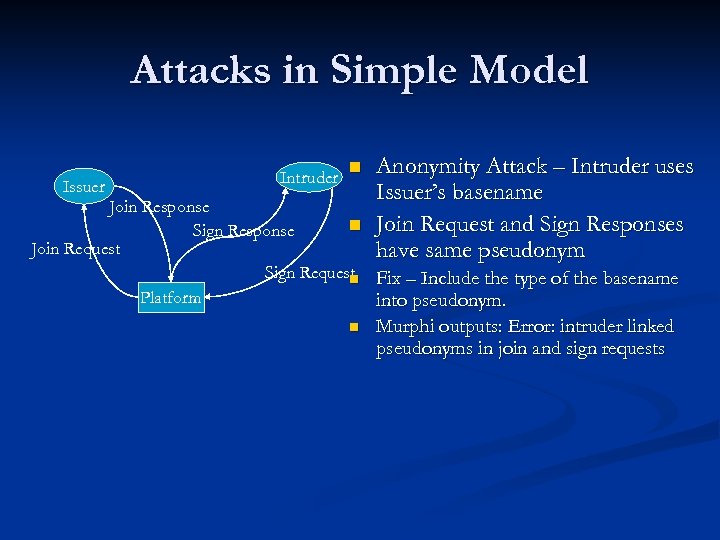 Attacks in Simple Model Issuer n Intruder Anonymity Attack – Intruder uses Issuer’s basename Join Request and Sign Responses have same pseudonym Join Response n Sign Response Join Request Sign Request Fix – Include the type of the basename n Platform into pseudonym. n Murphi outputs: Error: intruder linked pseudonyms in join and sign requests
Attacks in Simple Model Issuer n Intruder Anonymity Attack – Intruder uses Issuer’s basename Join Request and Sign Responses have same pseudonym Join Response n Sign Response Join Request Sign Request Fix – Include the type of the basename n Platform into pseudonym. n Murphi outputs: Error: intruder linked pseudonyms in join and sign requests
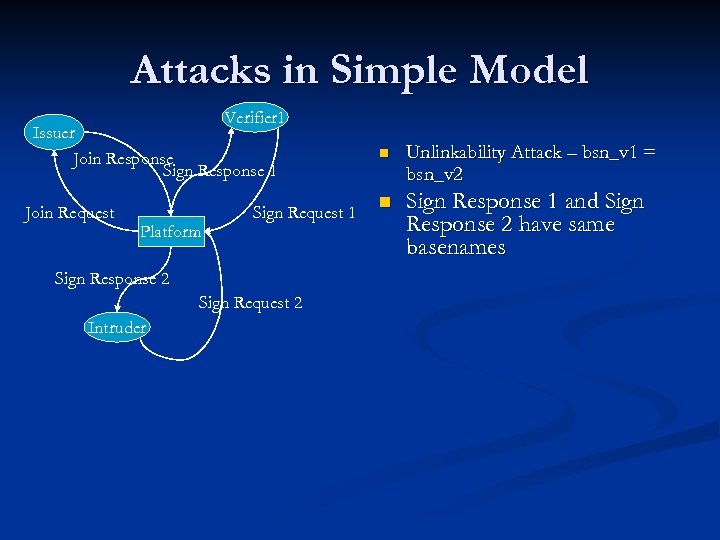 Attacks in Simple Model Verifier 1 Issuer Join Response Sign Response 1 Join Request Platform Sign Request 1 Sign Response 2 Sign Request 2 Intruder n Unlinkability Attack – bsn_v 1 = bsn_v 2 n Sign Response 1 and Sign Response 2 have same basenames
Attacks in Simple Model Verifier 1 Issuer Join Response Sign Response 1 Join Request Platform Sign Request 1 Sign Response 2 Sign Request 2 Intruder n Unlinkability Attack – bsn_v 1 = bsn_v 2 n Sign Response 1 and Sign Response 2 have same basenames
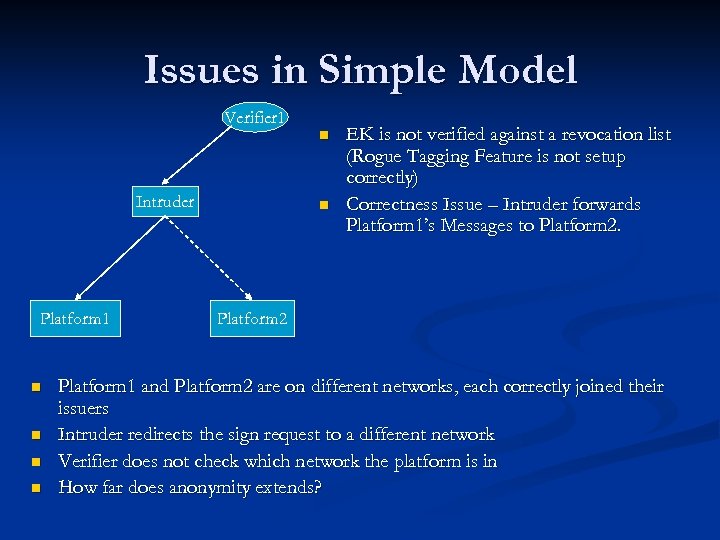 Issues in Simple Model Verifier 1 Intruder Platform 1 n n n EK is not verified against a revocation list (Rogue Tagging Feature is not setup correctly) Correctness Issue – Intruder forwards Platform 1’s Messages to Platform 2 Platform 1 and Platform 2 are on different networks, each correctly joined their issuers Intruder redirects the sign request to a different network Verifier does not check which network the platform is in How far does anonymity extends?
Issues in Simple Model Verifier 1 Intruder Platform 1 n n n EK is not verified against a revocation list (Rogue Tagging Feature is not setup correctly) Correctness Issue – Intruder forwards Platform 1’s Messages to Platform 2 Platform 1 and Platform 2 are on different networks, each correctly joined their issuers Intruder redirects the sign request to a different network Verifier does not check which network the platform is in How far does anonymity extends?
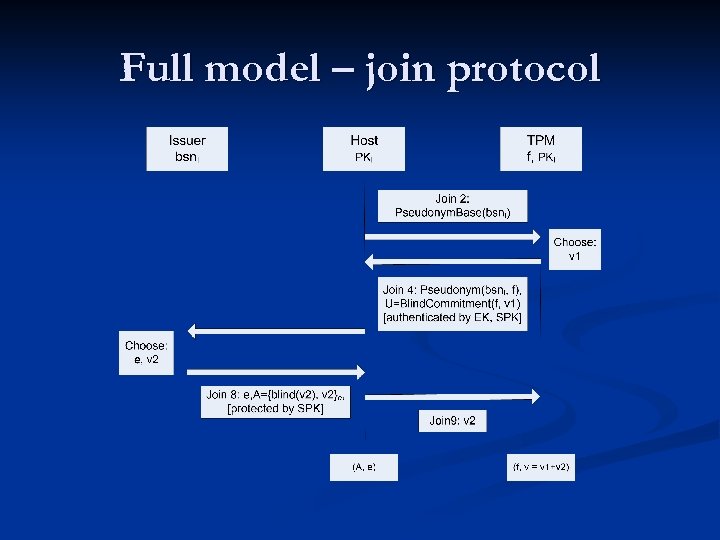 Full model – join protocol
Full model – join protocol
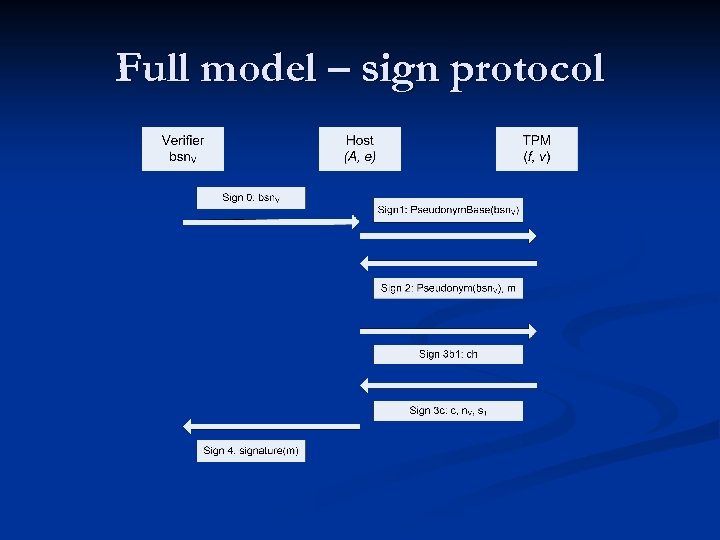 Full model – sign protocol
Full model – sign protocol
 Conclusion n The protocol is well designed n n n n Using interactive PK and nonces to ensure freshness and integrity of messages Hashes cover all possible parameters High level of description makes it difficult to verify corner conditions. Correctness in anonymous system is different from peer -to-peer. Managed to model known attacks, no new findings Cross-site attack should be taken care of by users Too Detailed Model runs out of memory
Conclusion n The protocol is well designed n n n n Using interactive PK and nonces to ensure freshness and integrity of messages Hashes cover all possible parameters High level of description makes it difficult to verify corner conditions. Correctness in anonymous system is different from peer -to-peer. Managed to model known attacks, no new findings Cross-site attack should be taken care of by users Too Detailed Model runs out of memory


