7fd15aea53177aba6e43491341b53cb2.ppt
- Количество слайдов: 18
 Analysis of a Fair Exchange Protocol Vitaly Shmatikov John Mitchell Stanford University
Analysis of a Fair Exchange Protocol Vitaly Shmatikov John Mitchell Stanford University
 Agreement in Hostile Environment l Cannot trust the communication channel l Cannot trust the other party in the protocol l Trusted third party may exist n Last resort: use only if something goes wrong
Agreement in Hostile Environment l Cannot trust the communication channel l Cannot trust the other party in the protocol l Trusted third party may exist n Last resort: use only if something goes wrong
 Contract Signing Immunity deal Both parties want to sign the contract l Neither wants to commit first l
Contract Signing Immunity deal Both parties want to sign the contract l Neither wants to commit first l
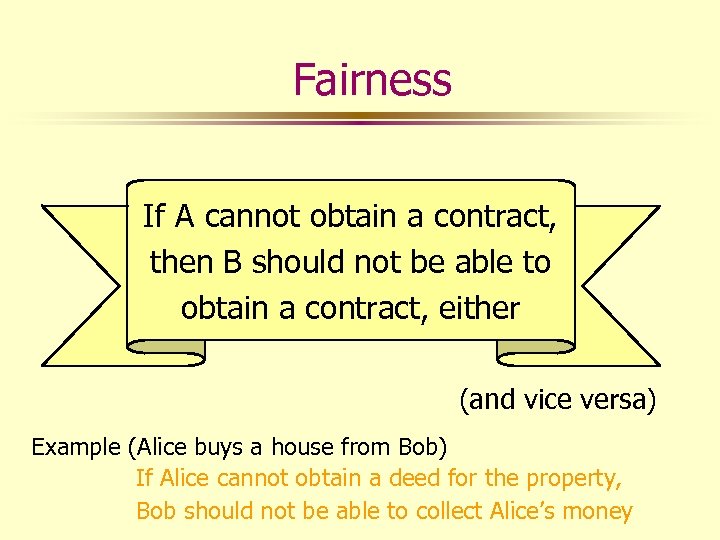 Fairness If A cannot obtain a contract, then B should not be able to obtain a contract, either (and vice versa) Example (Alice buys a house from Bob) If Alice cannot obtain a deed for the property, Bob should not be able to collect Alice’s money
Fairness If A cannot obtain a contract, then B should not be able to obtain a contract, either (and vice versa) Example (Alice buys a house from Bob) If Alice cannot obtain a deed for the property, Bob should not be able to collect Alice’s money
 Accountability If trusted party T misbehaves, then honest party should be able to prove T’s misbehavior Example (Alice buys a house from Bob) If escrow service gives Bob Alice’s money without giving Alice the deed, Alice should be able to prove to a judge that escrow service is cheating
Accountability If trusted party T misbehaves, then honest party should be able to prove T’s misbehavior Example (Alice buys a house from Bob) If escrow service gives Bob Alice’s money without giving Alice the deed, Alice should be able to prove to a judge that escrow service is cheating
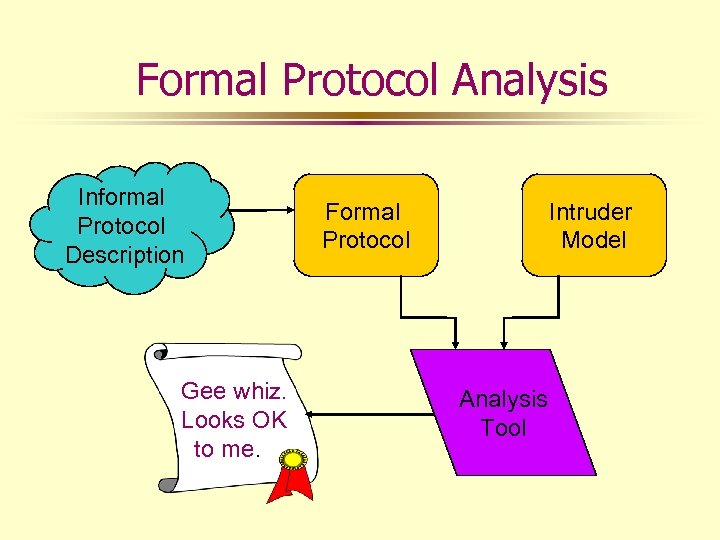 Formal Protocol Analysis Informal Protocol Description Gee whiz. Looks OK to me. Formal Protocol Intruder Model Analysis Tool
Formal Protocol Analysis Informal Protocol Description Gee whiz. Looks OK to me. Formal Protocol Intruder Model Analysis Tool
![Murj l [Dill et al. ] Describe finite-state system State variables with initial values Murj l [Dill et al. ] Describe finite-state system State variables with initial values](https://present5.com/presentation/7fd15aea53177aba6e43491341b53cb2/image-7.jpg) Murj l [Dill et al. ] Describe finite-state system State variables with initial values n Transition rules n Communication by shared variables n Scalable: choose system size parameters n Specify correctness condition l Automatic exhaustive state enumeration l n Hash table to avoid repeating states Success with research, industrial protocol verification
Murj l [Dill et al. ] Describe finite-state system State variables with initial values n Transition rules n Communication by shared variables n Scalable: choose system size parameters n Specify correctness condition l Automatic exhaustive state enumeration l n Hash table to avoid repeating states Success with research, industrial protocol verification
![Optimistic Contract Signing [Asokan, Shoup, Waidner] m 1 = sig. A (PKA, PKB, T, Optimistic Contract Signing [Asokan, Shoup, Waidner] m 1 = sig. A (PKA, PKB, T,](https://present5.com/presentation/7fd15aea53177aba6e43491341b53cb2/image-8.jpg) Optimistic Contract Signing [Asokan, Shoup, Waidner] m 1 = sig. A (PKA, PKB, T, text, hash(RA)) A m 2 = sig. B (m 1, hash(RB)) m 3 = R A m 4 = R B m 1, R A , m 2, R B B
Optimistic Contract Signing [Asokan, Shoup, Waidner] m 1 = sig. A (PKA, PKB, T, text, hash(RA)) A m 2 = sig. B (m 1, hash(RB)) m 3 = R A m 4 = R B m 1, R A , m 2, R B B
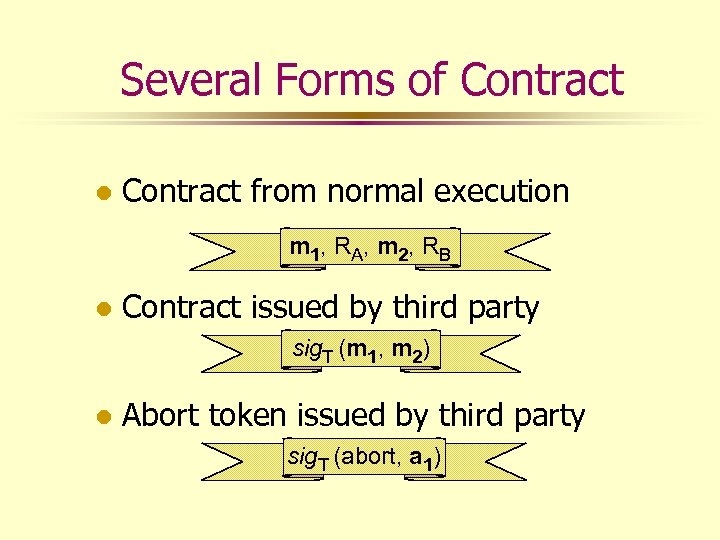 Several Forms of Contract l Contract from normal execution m 1, R A , m 2, R B l Contract issued by third party sig. T (m 1, m 2) l Abort token issued by third party sig. T (abort, a 1)
Several Forms of Contract l Contract from normal execution m 1, R A , m 2, R B l Contract issued by third party sig. T (m 1, m 2) l Abort token issued by third party sig. T (abort, a 1)
 Role of Trusted Third Party l T can issue an abort token Promise not to resolve the protocol in the future l T can issue a replacement contract Proof that both parties are committed l T decides whether to abort or resolve on the first-come-first-serve basis l T only gets involved if requested by A or B
Role of Trusted Third Party l T can issue an abort token Promise not to resolve the protocol in the future l T can issue a replacement contract Proof that both parties are committed l T decides whether to abort or resolve on the first-come-first-serve basis l T only gets involved if requested by A or B
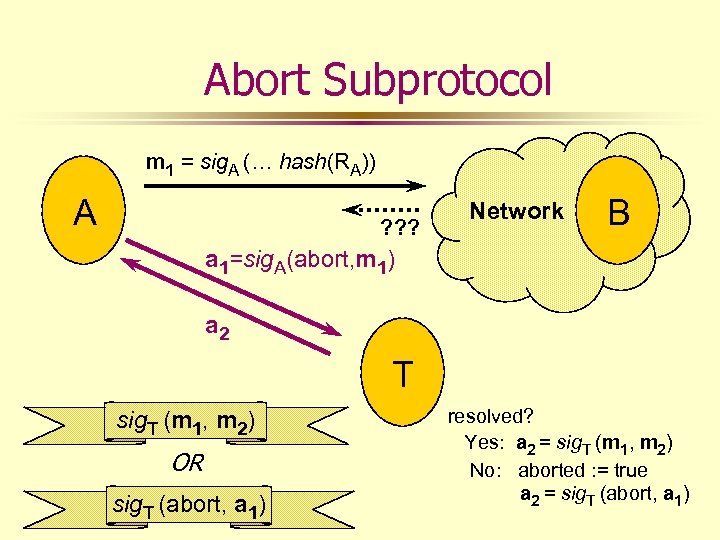 Abort Subprotocol m 1 = sig. A (… hash(RA)) A ? ? ? Network B a 1=sig. A(abort, m 1) a 2 T sig. T (m 1, m 2) OR sig. T (abort, a 1) resolved? Yes: a 2 = sig. T (m 1, m 2) No: aborted : = true a 2 = sig. T (abort, a 1)
Abort Subprotocol m 1 = sig. A (… hash(RA)) A ? ? ? Network B a 1=sig. A(abort, m 1) a 2 T sig. T (m 1, m 2) OR sig. T (abort, a 1) resolved? Yes: a 2 = sig. T (m 1, m 2) No: aborted : = true a 2 = sig. T (abort, a 1)
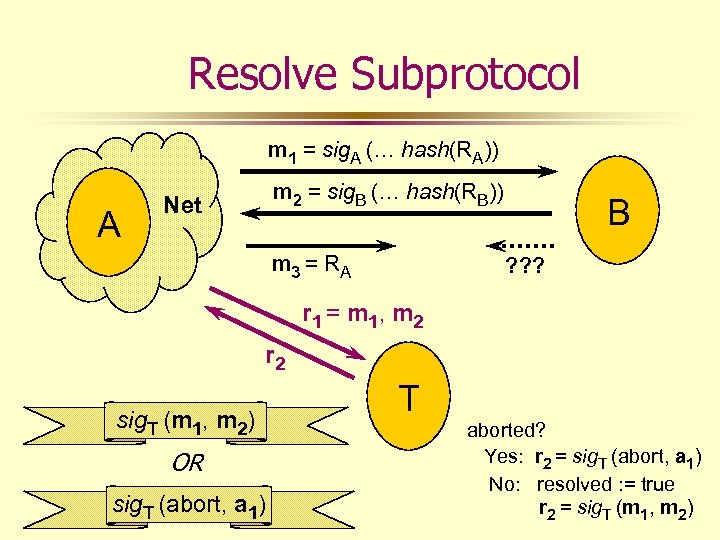 Resolve Subprotocol m 1 = sig. A (… hash(RA)) A m 2 = sig. B (… hash(RB)) Net m 3 = R A B ? ? ? r 1 = m 1, m 2 r 2 sig. T (m 1, m 2) OR sig. T (abort, a 1) T aborted? Yes: r 2 = sig. T (abort, a 1) No: resolved : = true r 2 = sig. T (m 1, m 2)
Resolve Subprotocol m 1 = sig. A (… hash(RA)) A m 2 = sig. B (… hash(RB)) Net m 3 = R A B ? ? ? r 1 = m 1, m 2 r 2 sig. T (m 1, m 2) OR sig. T (abort, a 1) T aborted? Yes: r 2 = sig. T (abort, a 1) No: resolved : = true r 2 = sig. T (m 1, m 2)
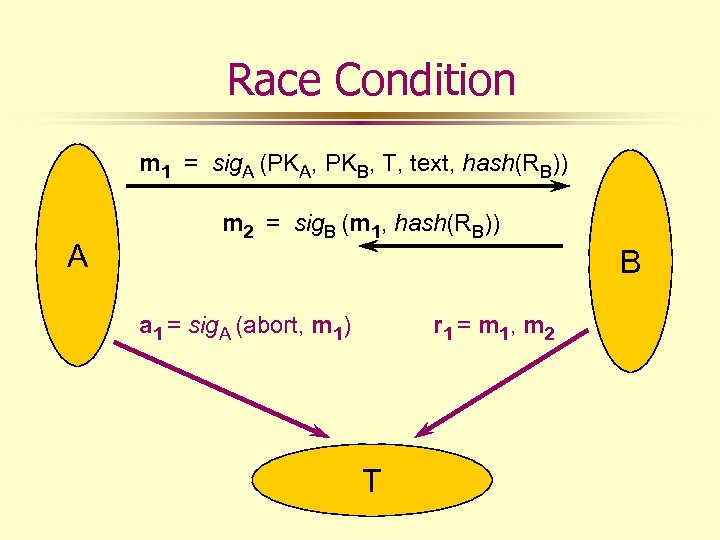 Race Condition m 1 = sig. A (PKA, PKB, T, text, hash(RB)) A m 2 = sig. B (m 1, hash(RB)) B a 1 = sig. A (abort, m 1) r 1 = m 1, m 2 T
Race Condition m 1 = sig. A (PKA, PKB, T, text, hash(RB)) A m 2 = sig. B (m 1, hash(RB)) B a 1 = sig. A (abort, m 1) r 1 = m 1, m 2 T
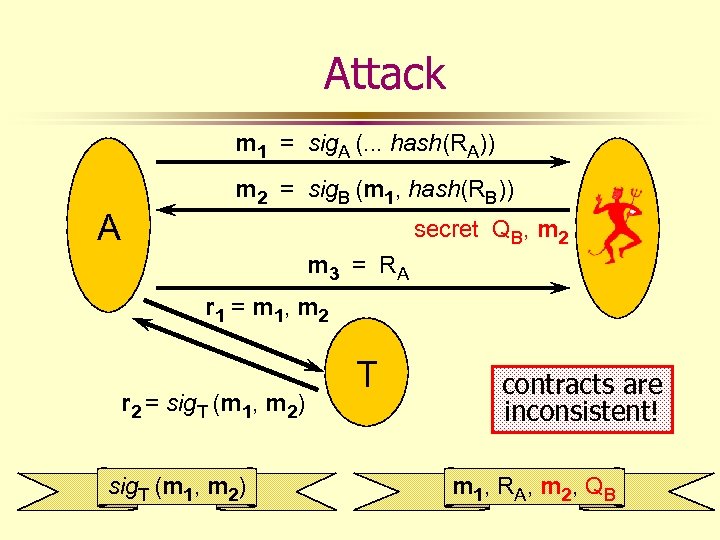 Attack m 1 = sig. A (. . . hash(RA)) A m 2 = sig. B (m 1, hash(RB)) secret QB, m 2 m 3 = R A r 1 = m 1, m 2 r 2 = sig. T (m 1, m 2) T contracts are inconsistent! m 1, R A , m 2, Q B
Attack m 1 = sig. A (. . . hash(RA)) A m 2 = sig. B (m 1, hash(RB)) secret QB, m 2 m 3 = R A r 1 = m 1, m 2 r 2 = sig. T (m 1, m 2) T contracts are inconsistent! m 1, R A , m 2, Q B
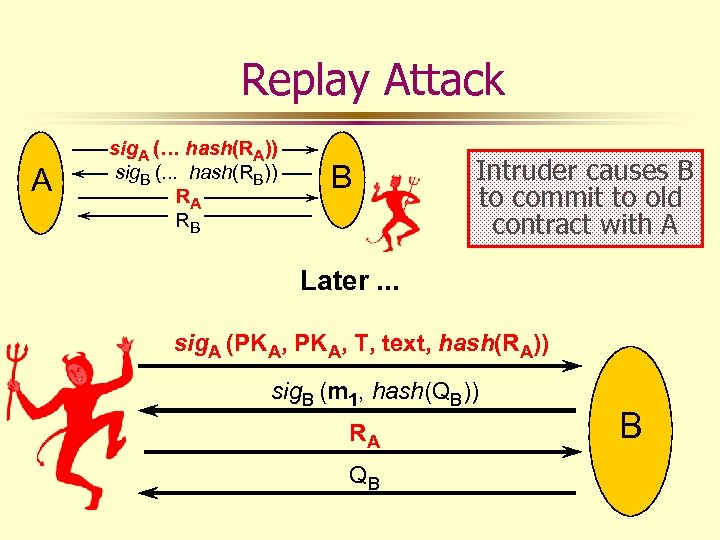 Replay Attack A sig. A (… hash(RA)) sig. B (. . . hash(RB)) RA RB B Intruder causes B to commit to old contract with A Later. . . sig. A (PKA, T, text, hash(RA)) sig. B (m 1, hash(QB)) RA QB B
Replay Attack A sig. A (… hash(RA)) sig. B (. . . hash(RB)) RA RB B Intruder causes B to commit to old contract with A Later. . . sig. A (PKA, T, text, hash(RA)) sig. B (m 1, hash(QB)) RA QB B
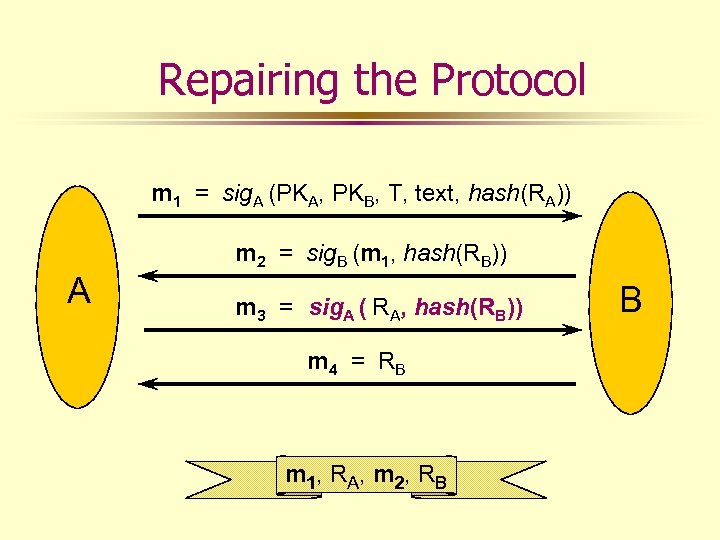 Repairing the Protocol m 1 = sig. A (PKA, PKB, T, text, hash(RA)) A m 2 = sig. B (m 1, hash(RB)) m 3 = sig. A ( RA, hash(RB)) m 4 = R B m 1, R A , m 2, R B B
Repairing the Protocol m 1 = sig. A (PKA, PKB, T, text, hash(RA)) A m 2 = sig. B (m 1, hash(RB)) m 3 = sig. A ( RA, hash(RB)) m 4 = R B m 1, R A , m 2, R B B
 Another Property: Abuse-Freeness No party should be able to prove that it can solely determine the outcome of the protocol Example (Alice buys a house from Bob) Bob should not be able to show Alice’s offer to Cynthia so that he can convince Cynthia to pay more
Another Property: Abuse-Freeness No party should be able to prove that it can solely determine the outcome of the protocol Example (Alice buys a house from Bob) Bob should not be able to show Alice’s offer to Cynthia so that he can convince Cynthia to pay more
 Conclusions l Fair exchange protocols are subtle Correctness conditions are hard to formalize n Unusual constraints on communication channels n l Several interdependent subprotocols n l Many cases and interleavings Finite-state tools are useful for case analysis
Conclusions l Fair exchange protocols are subtle Correctness conditions are hard to formalize n Unusual constraints on communication channels n l Several interdependent subprotocols n l Many cases and interleavings Finite-state tools are useful for case analysis


