ca1be0d7a1b087354c7286dd9934eca0.ppt
- Количество слайдов: 33
 An Update on Network Protocol Security Anupam Datta John Mitchell Stanford University Stanford Computer Forum, 2007
An Update on Network Protocol Security Anupam Datta John Mitchell Stanford University Stanford Computer Forum, 2007
 Roadmap u. Network protocol examples u. Are industrial protocols secure? • Case studies of industry standards u. Research state-of-the-art • Fully automated bug-finding tools • Methods for proving absence of bugs – Protocol Composition Logic • Modular proof-techniques • Cryptographic soundness u. Conclusions and Future Work
Roadmap u. Network protocol examples u. Are industrial protocols secure? • Case studies of industry standards u. Research state-of-the-art • Fully automated bug-finding tools • Methods for proving absence of bugs – Protocol Composition Logic • Modular proof-techniques • Cryptographic soundness u. Conclusions and Future Work
 Many Protocols u. Authentication • Kerberos u. Key Exchange • SSL/TLS handshake, IKE, JFK, IKEv 2, u. Wireless and mobile computing • Mobile IP, WEP, 802. 11 i, 802. 16 e, Wi-Fi u. Electronic commerce • Contract signing, SET, electronic cash, …
Many Protocols u. Authentication • Kerberos u. Key Exchange • SSL/TLS handshake, IKE, JFK, IKEv 2, u. Wireless and mobile computing • Mobile IP, WEP, 802. 11 i, 802. 16 e, Wi-Fi u. Electronic commerce • Contract signing, SET, electronic cash, …
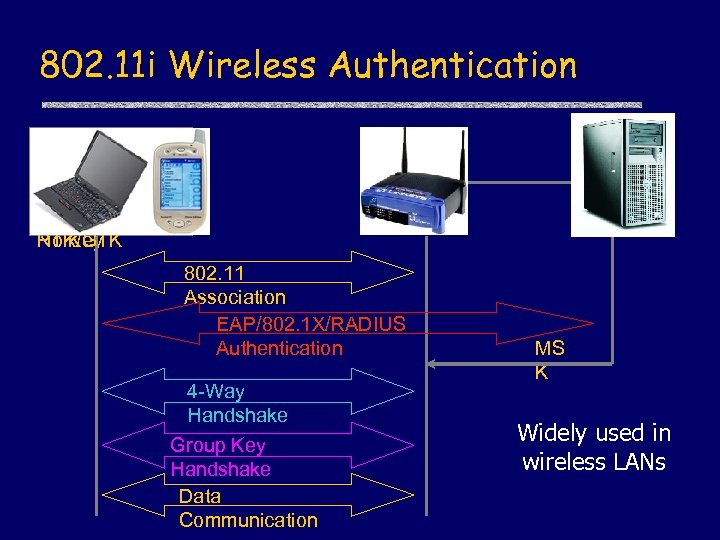 802. 11 i Wireless Authentication Supplicant Auth/Assoc Un. Auth/Un. Asso 802. 1 X c Un. Blocked 802. 1 X Blocked PTK/GTK No Key 802. 11 Association EAP/802. 1 X/RADIUS Authentication 4 -Way Handshake Group Key Handshake Data Communication MS K Widely used in wireless LANs
802. 11 i Wireless Authentication Supplicant Auth/Assoc Un. Auth/Un. Asso 802. 1 X c Un. Blocked 802. 1 X Blocked PTK/GTK No Key 802. 11 Association EAP/802. 1 X/RADIUS Authentication 4 -Way Handshake Group Key Handshake Data Communication MS K Widely used in wireless LANs
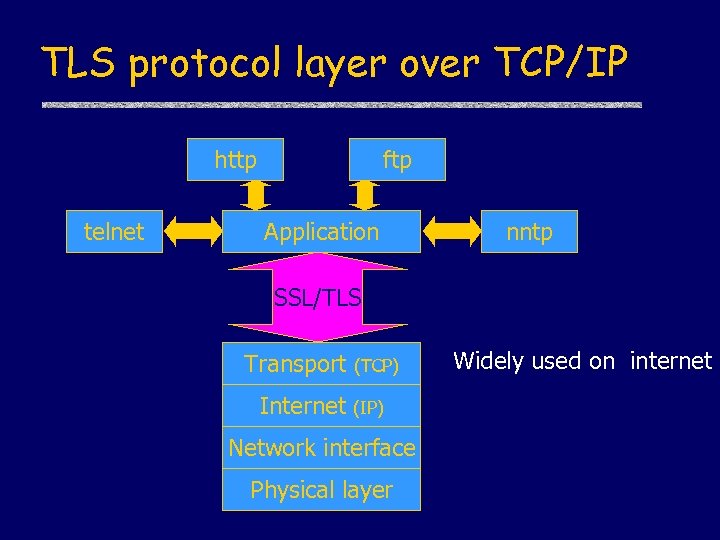 TLS protocol layer over TCP/IP http telnet ftp Application nntp SSL/TLS Transport Internet (TCP) (IP) Network interface Physical layer Widely used on internet
TLS protocol layer over TCP/IP http telnet ftp Application nntp SSL/TLS Transport Internet (TCP) (IP) Network interface Physical layer Widely used on internet
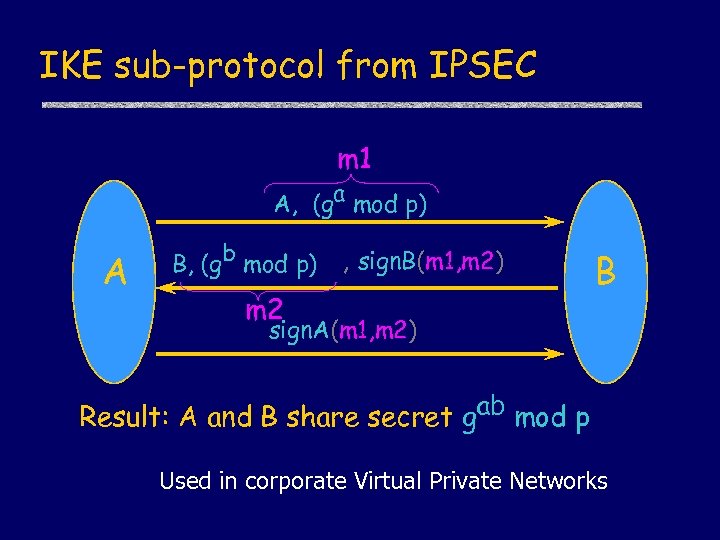 IKE sub-protocol from IPSEC m 1 A, (ga mod p) A B, (gb mod p) , sign. B(m 1, m 2) m 2 B sign. A(m 1, m 2) Result: A and B share secret gab mod p Used in corporate Virtual Private Networks
IKE sub-protocol from IPSEC m 1 A, (ga mod p) A B, (gb mod p) , sign. B(m 1, m 2) m 2 B sign. A(m 1, m 2) Result: A and B share secret gab mod p Used in corporate Virtual Private Networks
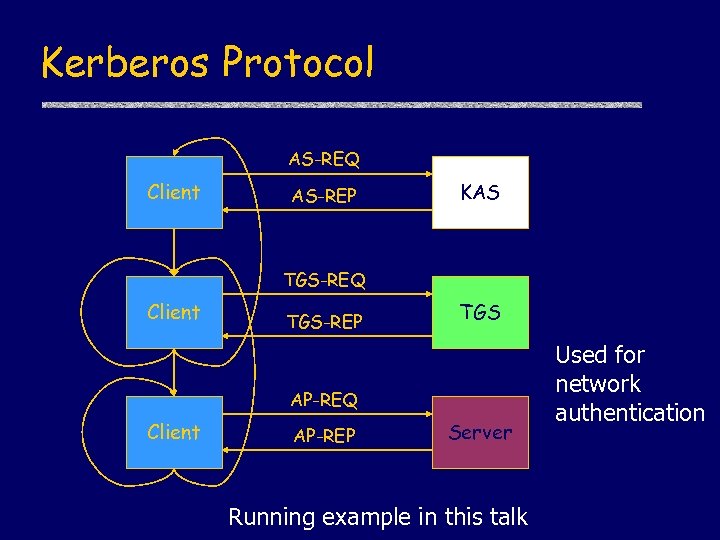 Kerberos Protocol AS-REQ Client AS-REP KAS TGS-REQ Client TGS-REP TGS AP-REQ Client AP-REP Server Running example in this talk Used for network authentication
Kerberos Protocol AS-REQ Client AS-REP KAS TGS-REQ Client TGS-REP TGS AP-REQ Client AP-REP Server Running example in this talk Used for network authentication
 Roadmap u. Network protocol examples u. Are industrial protocols secure? • Case studies of industry standards u. Research state-of-the-art • Fully automated bug-finding tools • Methods for proving absence of bugs – Protocol Composition Logic • Modular proof-techniques • Cryptographic soundness u. Conclusions and Future Work
Roadmap u. Network protocol examples u. Are industrial protocols secure? • Case studies of industry standards u. Research state-of-the-art • Fully automated bug-finding tools • Methods for proving absence of bugs – Protocol Composition Logic • Modular proof-techniques • Cryptographic soundness u. Conclusions and Future Work
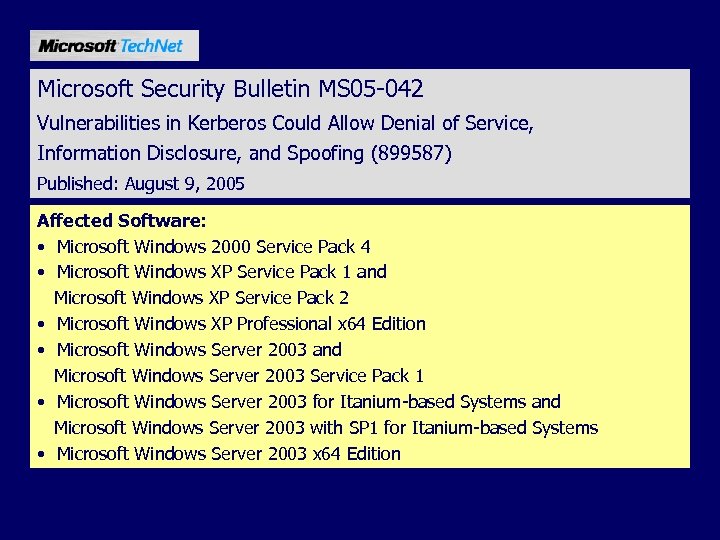 Microsoft Security Bulletin MS 05 -042 Vulnerabilities in Kerberos Could Allow Denial of Service, Information Disclosure, and Spoofing (899587) Published: August 9, 2005 Affected Software: • Microsoft Windows 2000 Service Pack 4 • Microsoft Windows XP Service Pack 1 and Microsoft Windows XP Service Pack 2 • Microsoft Windows XP Professional x 64 Edition • Microsoft Windows Server 2003 and Microsoft Windows Server 2003 Service Pack 1 • Microsoft Windows Server 2003 for Itanium-based Systems and Microsoft Windows Server 2003 with SP 1 for Itanium-based Systems • Microsoft Windows Server 2003 x 64 Edition
Microsoft Security Bulletin MS 05 -042 Vulnerabilities in Kerberos Could Allow Denial of Service, Information Disclosure, and Spoofing (899587) Published: August 9, 2005 Affected Software: • Microsoft Windows 2000 Service Pack 4 • Microsoft Windows XP Service Pack 1 and Microsoft Windows XP Service Pack 2 • Microsoft Windows XP Professional x 64 Edition • Microsoft Windows Server 2003 and Microsoft Windows Server 2003 Service Pack 1 • Microsoft Windows Server 2003 for Itanium-based Systems and Microsoft Windows Server 2003 with SP 1 for Itanium-based Systems • Microsoft Windows Server 2003 x 64 Edition
 Kerberos Error I. Cervesato, A. D. Jaggard, A. Scedrov, J. -K. Tsay, and C. Walstad u. Formal analysis of Kerberos 5 • Several steps – Detailed core protocol – Cross-realm authentication – Public-key extensions to Kerberos u. Attack on PKINIT • Breaks association of client request and the response • Prevents full authentication and confidentiality u. Formal verification of fixes preventing attack • Close, ongoing interactions with IETF WG
Kerberos Error I. Cervesato, A. D. Jaggard, A. Scedrov, J. -K. Tsay, and C. Walstad u. Formal analysis of Kerberos 5 • Several steps – Detailed core protocol – Cross-realm authentication – Public-key extensions to Kerberos u. Attack on PKINIT • Breaks association of client request and the response • Prevents full authentication and confidentiality u. Formal verification of fixes preventing attack • Close, ongoing interactions with IETF WG
 Public-Key Kerberos u Extend basic Kerberos 5 to use PKI • Change first round to avoid long-term shared keys • Originally motivated by security – If KDC is compromised, don’t need to regenerate shared keys – Avoid use of password-derived keys • Current emphasis on administrative convenience – Avoid need to register in advance of using Kerberized services u This extension is called PKINIT • • Current version is PKINIT-29 Attack found in PKINIT-25; fixed in PKINIT-27 Included in Windows and Linux (called Heimdal) Implementation developed by Cable. Labs (for cable boxes)
Public-Key Kerberos u Extend basic Kerberos 5 to use PKI • Change first round to avoid long-term shared keys • Originally motivated by security – If KDC is compromised, don’t need to regenerate shared keys – Avoid use of password-derived keys • Current emphasis on administrative convenience – Avoid need to register in advance of using Kerberized services u This extension is called PKINIT • • Current version is PKINIT-29 Attack found in PKINIT-25; fixed in PKINIT-27 Included in Windows and Linux (called Heimdal) Implementation developed by Cable. Labs (for cable boxes)
![Attack C Cert. C, [t. C, n 2]sk. C, C, T, n 1 I Attack C Cert. C, [t. C, n 2]sk. C, C, T, n 1 I](https://present5.com/presentation/ca1be0d7a1b087354c7286dd9934eca0/image-12.jpg) Attack C Cert. C, [t. C, n 2]sk. C, C, T, n 1 I I I C {[k, n 2]sk. K}pk. C, C, TGT, {AK, …}k • I knows fresh keys k and AK • C receives K’s signature over k, n 2 and assumes k, AK, etc. , were generated for C (not I) Cert. I, [t. C, n 2]sk. I, I, T, n 1 {[k, n 2]sk. K}pk. I, I, TGT, {AK, …}k K K I • Principal P has secret key sk. P, public key pk. P • {msg}key is encryption of msg with key • [msg]key is signature over msg with key
Attack C Cert. C, [t. C, n 2]sk. C, C, T, n 1 I I I C {[k, n 2]sk. K}pk. C, C, TGT, {AK, …}k • I knows fresh keys k and AK • C receives K’s signature over k, n 2 and assumes k, AK, etc. , were generated for C (not I) Cert. I, [t. C, n 2]sk. I, I, T, n 1 {[k, n 2]sk. K}pk. I, I, TGT, {AK, …}k K K I • Principal P has secret key sk. P, public key pk. P • {msg}key is encryption of msg with key • [msg]key is signature over msg with key
 Fix Adopted in pk-init-27 u. The KDC signs k, cksum (instead of k, n 2) – k is reply. Key – cksum is checksum over AS-REQ – Easier to implement than signing C, k, n 2 u. Formal proof: this guarantees authentication • Assume checksum is preimage resistant • Assume KDC’s signature keys are secret
Fix Adopted in pk-init-27 u. The KDC signs k, cksum (instead of k, n 2) – k is reply. Key – cksum is checksum over AS-REQ – Easier to implement than signing C, k, n 2 u. Formal proof: this guarantees authentication • Assume checksum is preimage resistant • Assume KDC’s signature keys are secret
![Attacks on Industry Standards u. IKE [Meadows; 1999] • Reflection attack; fix adopted by Attacks on Industry Standards u. IKE [Meadows; 1999] • Reflection attack; fix adopted by](https://present5.com/presentation/ca1be0d7a1b087354c7286dd9934eca0/image-14.jpg) Attacks on Industry Standards u. IKE [Meadows; 1999] • Reflection attack; fix adopted by IETF WG u. IEEE 802. 11 i [He, Mitchell; 2004] • Do. S attack; fix adopted by IEEE WG u. GDOI [Meadows, Pavlovic; 2004] • Composition attack; fix adopted by IETF WG u. Kerberos V 5 [Scedrov et al; 2005] • Identity misbinding attack; fix adopted by IETF WG; Windows update released by Microsoft Identified using logical methods
Attacks on Industry Standards u. IKE [Meadows; 1999] • Reflection attack; fix adopted by IETF WG u. IEEE 802. 11 i [He, Mitchell; 2004] • Do. S attack; fix adopted by IEEE WG u. GDOI [Meadows, Pavlovic; 2004] • Composition attack; fix adopted by IETF WG u. Kerberos V 5 [Scedrov et al; 2005] • Identity misbinding attack; fix adopted by IETF WG; Windows update released by Microsoft Identified using logical methods
 Roadmap u. Network protocol examples u. Are industrial protocols secure? • Case studies of industry standards u. Security analysis state-of-the-art • Fully automated bug-finding tools • Methods for proving absence of bugs – Protocol Composition Logic • Modular proof-techniques • Cryptographic soundness u. Conclusions and Future Work
Roadmap u. Network protocol examples u. Are industrial protocols secure? • Case studies of industry standards u. Security analysis state-of-the-art • Fully automated bug-finding tools • Methods for proving absence of bugs – Protocol Composition Logic • Modular proof-techniques • Cryptographic soundness u. Conclusions and Future Work
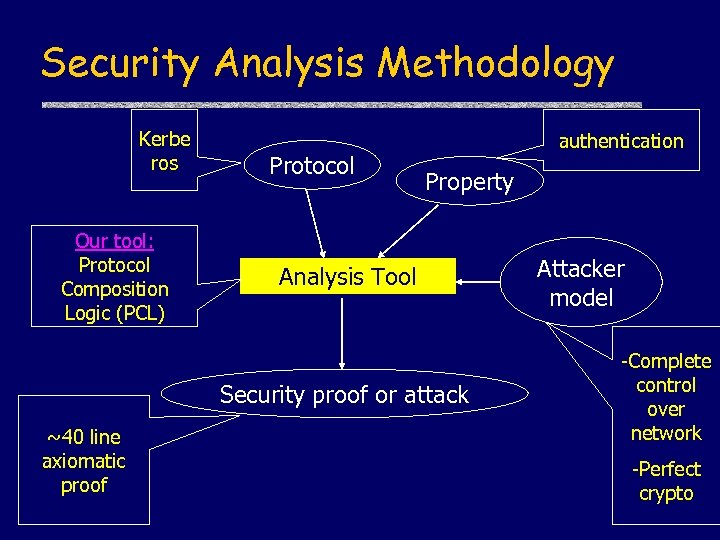 Security Analysis Methodology Kerbe ros Our tool: Protocol Composition Logic (PCL) Protocol authentication Property Analysis Tool Security proof or attack ~40 line axiomatic proof Attacker model -Complete control over network -Perfect crypto
Security Analysis Methodology Kerbe ros Our tool: Protocol Composition Logic (PCL) Protocol authentication Property Analysis Tool Security proof or attack ~40 line axiomatic proof Attacker model -Complete control over network -Perfect crypto
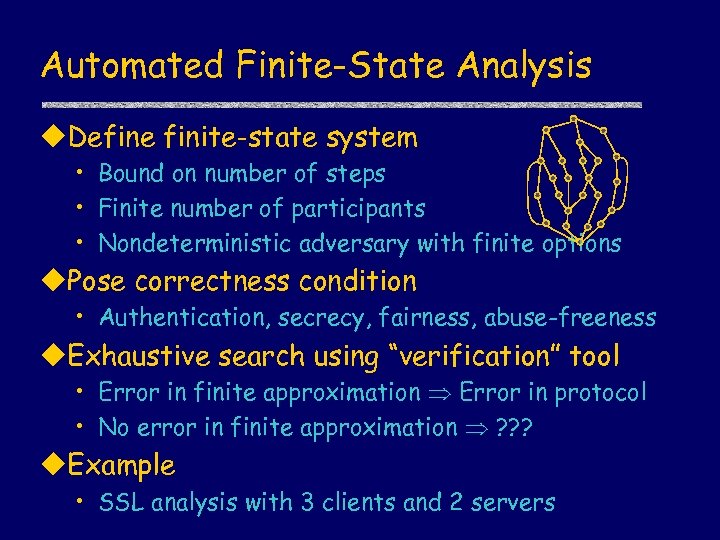 Automated Finite-State Analysis u. Define finite-state system • Bound on number of steps • Finite number of participants • Nondeterministic adversary with finite options u. Pose correctness condition • Authentication, secrecy, fairness, abuse-freeness u. Exhaustive search using “verification” tool • Error in finite approximation Error in protocol • No error in finite approximation ? ? ? u. Example • SSL analysis with 3 clients and 2 servers
Automated Finite-State Analysis u. Define finite-state system • Bound on number of steps • Finite number of participants • Nondeterministic adversary with finite options u. Pose correctness condition • Authentication, secrecy, fairness, abuse-freeness u. Exhaustive search using “verification” tool • Error in finite approximation Error in protocol • No error in finite approximation ? ? ? u. Example • SSL analysis with 3 clients and 2 servers
 Bug-finding Tools and Case Studies u. Murphi model-checking of protocols • Generic model-checker developed by David Dill’s group at Stanford • Method for security protocol analysis developed by Mitchell, Shmatikov et al (1997 -) • Many case studies including SSL, 802. 11 i • Tool and case studies available at http: //cs 259. stanford. edu u. Many other fully automated tools • AVISPA project, SRI constraint solver, … u. Ready for industrial use
Bug-finding Tools and Case Studies u. Murphi model-checking of protocols • Generic model-checker developed by David Dill’s group at Stanford • Method for security protocol analysis developed by Mitchell, Shmatikov et al (1997 -) • Many case studies including SSL, 802. 11 i • Tool and case studies available at http: //cs 259. stanford. edu u. Many other fully automated tools • AVISPA project, SRI constraint solver, … u. Ready for industrial use
 Roadmap u. Network protocol examples u. Are industrial protocols secure? • Case studies of industry standards u. Security analysis state-of-the-art • Fully automated bug-finding tools • Methods for proving absence of bugs – Protocol Composition Logic • Modular proof-techniques • Cryptographic soundness u. Conclusions and Future Work
Roadmap u. Network protocol examples u. Are industrial protocols secure? • Case studies of industry standards u. Security analysis state-of-the-art • Fully automated bug-finding tools • Methods for proving absence of bugs – Protocol Composition Logic • Modular proof-techniques • Cryptographic soundness u. Conclusions and Future Work
 Proving Security of Protocols u. Cryptographic reductions • More realistic model involving probabilistic polynomial time attackers • Difficult to scale to industrial protocols u. Symbolic methods and proof tools • NRL Protocol Analyzer, Paulson’s Inductive Method, Process calculi, Specialized protocol logics, MSR (see http: //cs 259. stanford. edu ) • 2 challenges: – Scale to industrial protocols: modular analysis desired – Use cryptographic model instead of idealized symbolic model • Progress on challenges in last 5 years
Proving Security of Protocols u. Cryptographic reductions • More realistic model involving probabilistic polynomial time attackers • Difficult to scale to industrial protocols u. Symbolic methods and proof tools • NRL Protocol Analyzer, Paulson’s Inductive Method, Process calculi, Specialized protocol logics, MSR (see http: //cs 259. stanford. edu ) • 2 challenges: – Scale to industrial protocols: modular analysis desired – Use cryptographic model instead of idealized symbolic model • Progress on challenges in last 5 years
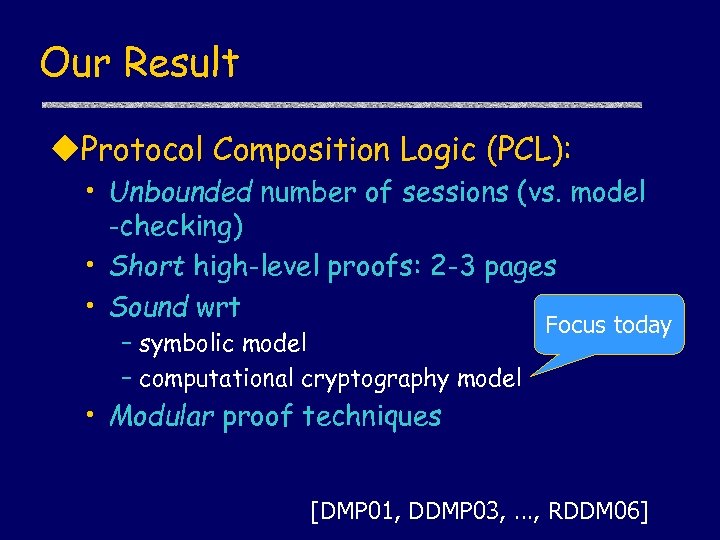 Our Result u. Protocol Composition Logic (PCL): • Unbounded number of sessions (vs. model -checking) • Short high-level proofs: 2 -3 pages • Sound wrt – symbolic model – computational cryptography model Focus today • Modular proof techniques [DMP 01, DDMP 03, …, RDDM 06]
Our Result u. Protocol Composition Logic (PCL): • Unbounded number of sessions (vs. model -checking) • Short high-level proofs: 2 -3 pages • Sound wrt – symbolic model – computational cryptography model Focus today • Modular proof techniques [DMP 01, DDMP 03, …, RDDM 06]
![PCL Results: Industrial Protocols u IEEE 802. 11 i [IEEE Standards; 2004] [HSDDM 05] PCL Results: Industrial Protocols u IEEE 802. 11 i [IEEE Standards; 2004] [HSDDM 05]](https://present5.com/presentation/ca1be0d7a1b087354c7286dd9934eca0/image-22.jpg) PCL Results: Industrial Protocols u IEEE 802. 11 i [IEEE Standards; 2004] [HSDDM 05] u. TLS/SSL [RFC 2246] is a component (Attack using model-checking; fix adopted by WG) u GDOI Secure Group Communication [RFC 3547] [MP 04] (Attack using PCL; fix adopted by IETF WG) u Kerberos V 5 [IETF ID; 2004] [CMP 05, RDDM 06] u Mobile IPv 6 [RFC 3775] in progress u IKE/JFK family u. IKEv 2 [IETF ID; 2004] in progress [RDM 06] Except Kerberos, results currently apply only to symbolic model
PCL Results: Industrial Protocols u IEEE 802. 11 i [IEEE Standards; 2004] [HSDDM 05] u. TLS/SSL [RFC 2246] is a component (Attack using model-checking; fix adopted by WG) u GDOI Secure Group Communication [RFC 3547] [MP 04] (Attack using PCL; fix adopted by IETF WG) u Kerberos V 5 [IETF ID; 2004] [CMP 05, RDDM 06] u Mobile IPv 6 [RFC 3775] in progress u IKE/JFK family u. IKEv 2 [IETF ID; 2004] in progress [RDM 06] Except Kerberos, results currently apply only to symbolic model
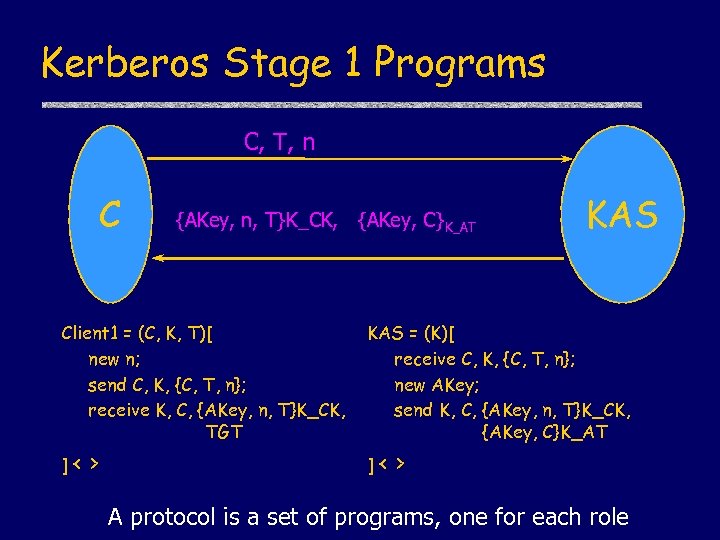 Kerberos Stage 1 Programs C, T, n C {AKey, n, T}K_CK, {AKey, C}K_AT KAS Client 1 = (C, K, T)[ new n; send C, K, {C, T, n}; receive K, C, {AKey, n, T}K_CK, TGT KAS = (K)[ receive C, K, {C, T, n}; new AKey; send K, C, {AKey, n, T}K_CK, {AKey, C}K_AT ]< ]< > > A protocol is a set of programs, one for each role
Kerberos Stage 1 Programs C, T, n C {AKey, n, T}K_CK, {AKey, C}K_AT KAS Client 1 = (C, K, T)[ new n; send C, K, {C, T, n}; receive K, C, {AKey, n, T}K_CK, TGT KAS = (K)[ receive C, K, {C, T, n}; new AKey; send K, C, {AKey, n, T}K_CK, {AKey, C}K_AT ]< ]< > > A protocol is a set of programs, one for each role
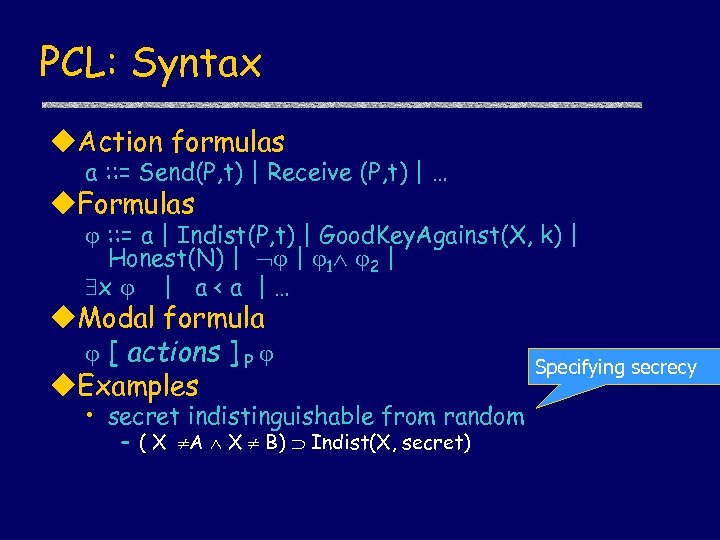 PCL: Syntax u. Action formulas a : : = Send(P, t) | Receive (P, t) | … u. Formulas : : = a | Indist(P, t) | Good. Key. Against(X, k) | Honest(N) | | 1 2 | x | a < a | … u. Modal formula [ actions ] P u. Examples • secret indistinguishable from random – ( X A X B) Indist(X, secret) Specifying secrecy
PCL: Syntax u. Action formulas a : : = Send(P, t) | Receive (P, t) | … u. Formulas : : = a | Indist(P, t) | Good. Key. Against(X, k) | Honest(N) | | 1 2 | x | a < a | … u. Modal formula [ actions ] P u. Examples • secret indistinguishable from random – ( X A X B) Indist(X, secret) Specifying secrecy
![Kerberos Stage 1 Property u. Client guarantee true [ Client 1(C, T, K) ] Kerberos Stage 1 Property u. Client guarantee true [ Client 1(C, T, K) ]](https://present5.com/presentation/ca1be0d7a1b087354c7286dd9934eca0/image-25.jpg) Kerberos Stage 1 Property u. Client guarantee true [ Client 1(C, T, K) ] C Honest(C, T, K) (Good. Key. Against(X, AKey) X {C, T, K} ) u. Key usable for encryption
Kerberos Stage 1 Property u. Client guarantee true [ Client 1(C, T, K) ] C Honest(C, T, K) (Good. Key. Against(X, AKey) X {C, T, K} ) u. Key usable for encryption
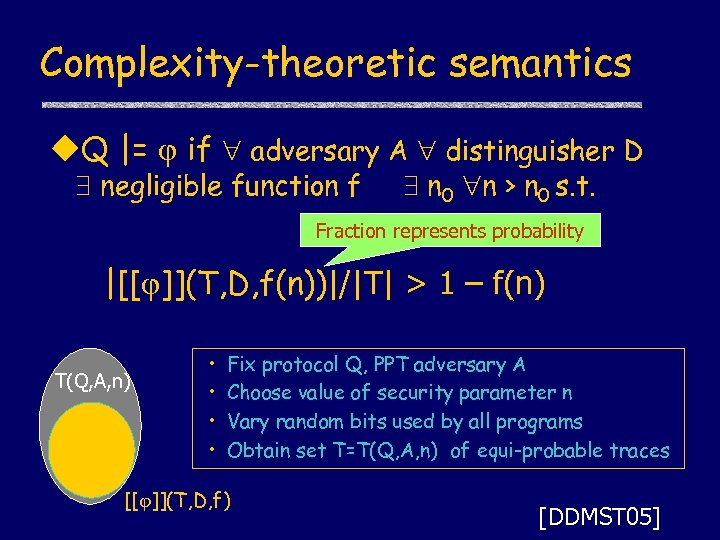 Complexity-theoretic semantics u. Q |= if adversary A distinguisher D negligible function f n 0 n > n 0 s. t. Fraction represents probability |[[ ]](T, D, f(n))|/|T| > 1 – f(n) T(Q, A, n) • • Fix protocol Q, PPT adversary A Choose value of security parameter n Vary random bits used by all programs Obtain set T=T(Q, A, n) of equi-probable traces [[ ]](T, D, f) [DDMST 05]
Complexity-theoretic semantics u. Q |= if adversary A distinguisher D negligible function f n 0 n > n 0 s. t. Fraction represents probability |[[ ]](T, D, f(n))|/|T| > 1 – f(n) T(Q, A, n) • • Fix protocol Q, PPT adversary A Choose value of security parameter n Vary random bits used by all programs Obtain set T=T(Q, A, n) of equi-probable traces [[ ]](T, D, f) [DDMST 05]
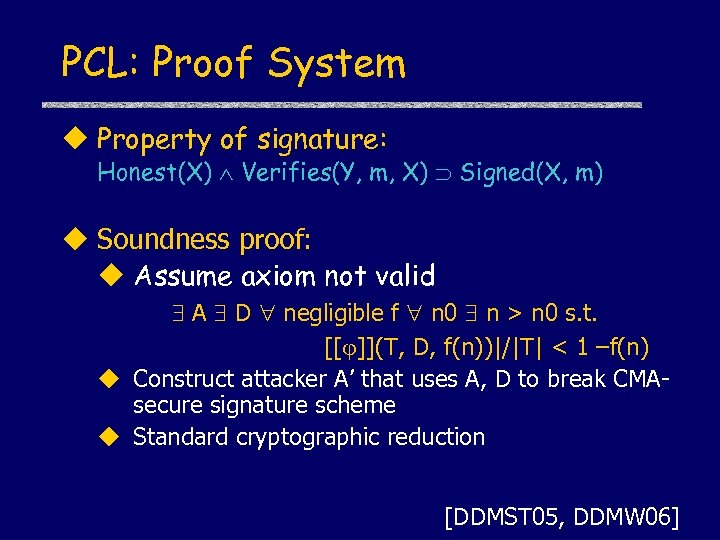 PCL: Proof System u Property of signature: Honest(X) Verifies(Y, m, X) Signed(X, m) u Soundness proof: u Assume axiom not valid A D negligible f n 0 n > n 0 s. t. [[ ]](T, D, f(n))|/|T| < 1 –f(n) u Construct attacker A’ that uses A, D to break CMAsecure signature scheme u Standard cryptographic reduction [DDMST 05, DDMW 06]
PCL: Proof System u Property of signature: Honest(X) Verifies(Y, m, X) Signed(X, m) u Soundness proof: u Assume axiom not valid A D negligible f n 0 n > n 0 s. t. [[ ]](T, D, f(n))|/|T| < 1 –f(n) u Construct attacker A’ that uses A, D to break CMAsecure signature scheme u Standard cryptographic reduction [DDMST 05, DDMW 06]
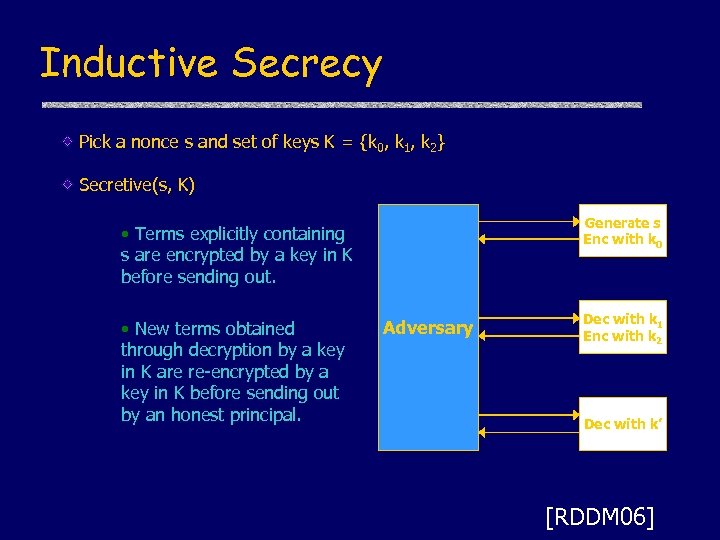 Inductive Secrecy Pick a nonce s and set of keys K = {k 0, k 1, k 2} Secretive(s, K) Generate s Enc with k 0 • Terms explicitly containing s are encrypted by a key in K before sending out. • New terms obtained through decryption by a key in K are re-encrypted by a key in K before sending out by an honest principal. Adversary Dec with k 1 Enc with k 2 Dec with k’ [RDDM 06]
Inductive Secrecy Pick a nonce s and set of keys K = {k 0, k 1, k 2} Secretive(s, K) Generate s Enc with k 0 • Terms explicitly containing s are encrypted by a key in K before sending out. • New terms obtained through decryption by a key in K are re-encrypted by a key in K before sending out by an honest principal. Adversary Dec with k 1 Enc with k 2 Dec with k’ [RDDM 06]
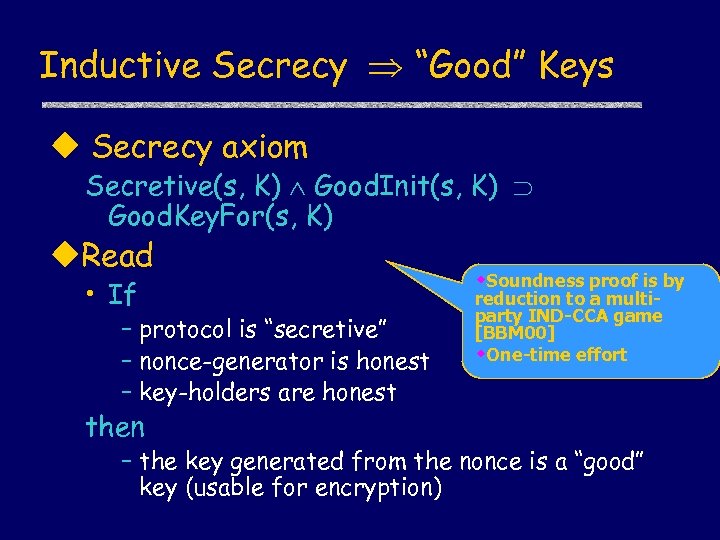 Inductive Secrecy “Good” Keys u Secrecy axiom Secretive(s, K) Good. Init(s, K) Good. Key. For(s, K) u. Read • If – protocol is “secretive” – nonce-generator is honest – key-holders are honest then w. Soundness proof is by reduction to a multiparty IND-CCA game [BBM 00] w. One-time effort – the key generated from the nonce is a “good” key (usable for encryption)
Inductive Secrecy “Good” Keys u Secrecy axiom Secretive(s, K) Good. Init(s, K) Good. Key. For(s, K) u. Read • If – protocol is “secretive” – nonce-generator is honest – key-holders are honest then w. Soundness proof is by reduction to a multiparty IND-CCA game [BBM 00] w. One-time effort – the key generated from the nonce is a “good” key (usable for encryption)
 CPCL analysis of Kerberos V 5 u Kerberos has a staged architecture • First stage generates a nonce and sends it encrypted • Second stage uses this nonce as a key to encrypt another nonce. • Third stage uses the nonce exchanged in the second stage to encrypt other terms u We prove “Good. Key”-ness of both the nonces assuming encryption scheme is IND-CCA u Authentication properties proved assuming encryption scheme is INT-CTXT secure u Modular proofs (including PKINIT) using composition theorems u Result by Boldyreva et al showing that encryption scheme provides required properties
CPCL analysis of Kerberos V 5 u Kerberos has a staged architecture • First stage generates a nonce and sends it encrypted • Second stage uses this nonce as a key to encrypt another nonce. • Third stage uses the nonce exchanged in the second stage to encrypt other terms u We prove “Good. Key”-ness of both the nonces assuming encryption scheme is IND-CCA u Authentication properties proved assuming encryption scheme is INT-CTXT secure u Modular proofs (including PKINIT) using composition theorems u Result by Boldyreva et al showing that encryption scheme provides required properties
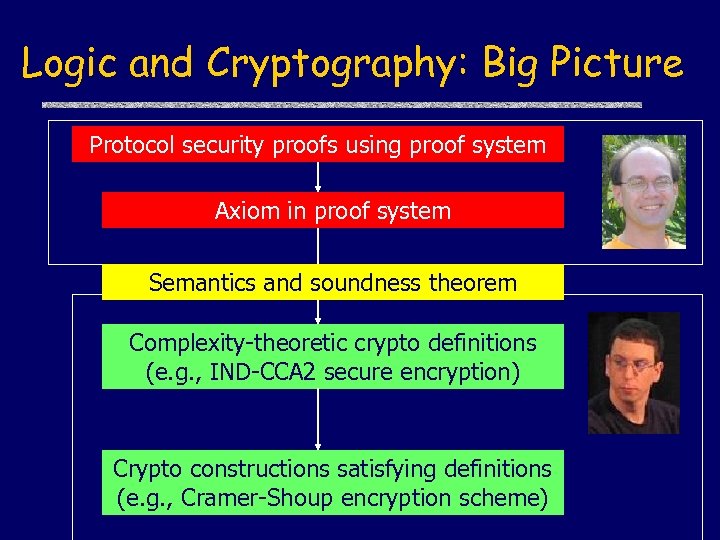 Logic and Cryptography: Big Picture Protocol security proofs using proof system Axiom in proof system Semantics and soundness theorem Complexity-theoretic crypto definitions (e. g. , IND-CCA 2 secure encryption) Crypto constructions satisfying definitions (e. g. , Cramer-Shoup encryption scheme)
Logic and Cryptography: Big Picture Protocol security proofs using proof system Axiom in proof system Semantics and soundness theorem Complexity-theoretic crypto definitions (e. g. , IND-CCA 2 secure encryption) Crypto constructions satisfying definitions (e. g. , Cramer-Shoup encryption scheme)
 Conclusions u Practical protocols may contain errors • Automated methods find bugs that humans overlook u Variety of tools • Model checking can find errors • Proof method can show correctness – with respect to specific model of execution and attack u Modular analysis is a challenge u Closing gap between logical analysis and cryptography • Symbolic model supports useful analysis – Tools, case studies, high-level proofs • Computational model more informative – Includes probability, complexity – Does not require strong cryptographic assumptions – More accurately reflects realistic attack • Two approaches can be combined – Several current projects and approaches [BPW, MW, Blan, CH, …] – One example: computational semantics for symbolic protocol logic u Research area coming of age • Interactions with and impact on industry
Conclusions u Practical protocols may contain errors • Automated methods find bugs that humans overlook u Variety of tools • Model checking can find errors • Proof method can show correctness – with respect to specific model of execution and attack u Modular analysis is a challenge u Closing gap between logical analysis and cryptography • Symbolic model supports useful analysis – Tools, case studies, high-level proofs • Computational model more informative – Includes probability, complexity – Does not require strong cryptographic assumptions – More accurately reflects realistic attack • Two approaches can be combined – Several current projects and approaches [BPW, MW, Blan, CH, …] – One example: computational semantics for symbolic protocol logic u Research area coming of age • Interactions with and impact on industry
 Thanks! Questions?
Thanks! Questions?


