8e43adbd80364756d44e6eaf05abd3dd.ppt
- Количество слайдов: 82
 An Introduction to VPLS Jeff Apcar, Distinguished Services Engineer APAC Technical Practices, Advanced Services Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 1
An Introduction to VPLS Jeff Apcar, Distinguished Services Engineer APAC Technical Practices, Advanced Services Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 1
 Agenda § VPLS Introduction § Pseudo Wire Refresher § VPLS Architecture § VPLS Configuration Example § VPLS Deployment § Summary Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 2
Agenda § VPLS Introduction § Pseudo Wire Refresher § VPLS Architecture § VPLS Configuration Example § VPLS Deployment § Summary Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 2
 Do you want to date VPLS? “VPLS is like having Paris Hilton as your girlfriend. The concept is fantastic, but in reality the experience might not be what you expected. But… we’re still willing to give it a go as long as we can understand/handle her behaviour” Me, Just Then Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 3
Do you want to date VPLS? “VPLS is like having Paris Hilton as your girlfriend. The concept is fantastic, but in reality the experience might not be what you expected. But… we’re still willing to give it a go as long as we can understand/handle her behaviour” Me, Just Then Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 3
 VPLS Introduction Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 4
VPLS Introduction Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 4
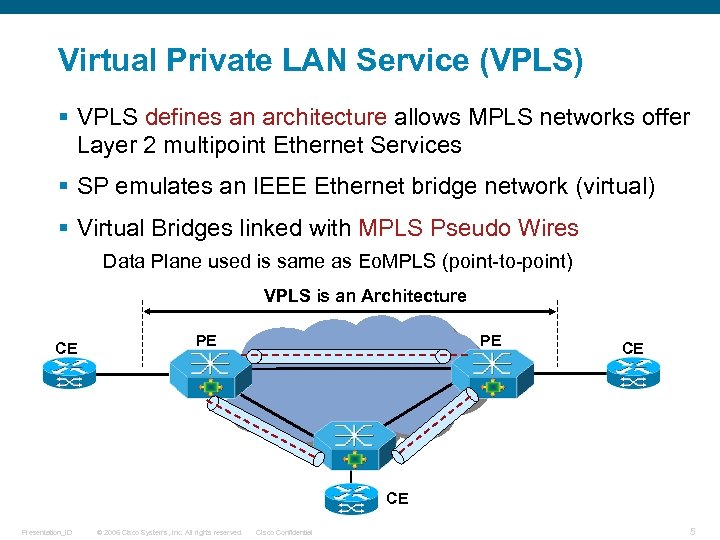 Virtual Private LAN Service (VPLS) § VPLS defines an architecture allows MPLS networks offer Layer 2 multipoint Ethernet Services § SP emulates an IEEE Ethernet bridge network (virtual) § Virtual Bridges linked with MPLS Pseudo Wires Data Plane used is same as Eo. MPLS (point-to-point) VPLS is an Architecture CE PE PE CE CE Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 5
Virtual Private LAN Service (VPLS) § VPLS defines an architecture allows MPLS networks offer Layer 2 multipoint Ethernet Services § SP emulates an IEEE Ethernet bridge network (virtual) § Virtual Bridges linked with MPLS Pseudo Wires Data Plane used is same as Eo. MPLS (point-to-point) VPLS is an Architecture CE PE PE CE CE Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 5
 Virtual Private LAN Service § End-to-end architecture that allows MPLS networks to provide Multipoint Ethernet services § It is “Virtual” because multiple instances of this service share the same physical infrastructure § It is “Private” because each instance of the service is independent and isolated from one another § It is “LAN Service” because it emulates Layer 2 multipoint connectivity between subscribers Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 6
Virtual Private LAN Service § End-to-end architecture that allows MPLS networks to provide Multipoint Ethernet services § It is “Virtual” because multiple instances of this service share the same physical infrastructure § It is “Private” because each instance of the service is independent and isolated from one another § It is “LAN Service” because it emulates Layer 2 multipoint connectivity between subscribers Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 6
 Why Provide A Layer 2 Service? § Customer have full operational control over their routing neighbours § Privacy of addressing space - they do not have to be shared with the carrier network § Customer has a choice of using any routing protocol including non IP based (IPX, Apple. Talk) § Customers could use an Ethernet switch instead of a router as the CPE § A single connection could reach all other edge points emulating an Ethernet LAN (VPLS) Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 7
Why Provide A Layer 2 Service? § Customer have full operational control over their routing neighbours § Privacy of addressing space - they do not have to be shared with the carrier network § Customer has a choice of using any routing protocol including non IP based (IPX, Apple. Talk) § Customers could use an Ethernet switch instead of a router as the CPE § A single connection could reach all other edge points emulating an Ethernet LAN (VPLS) Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 7
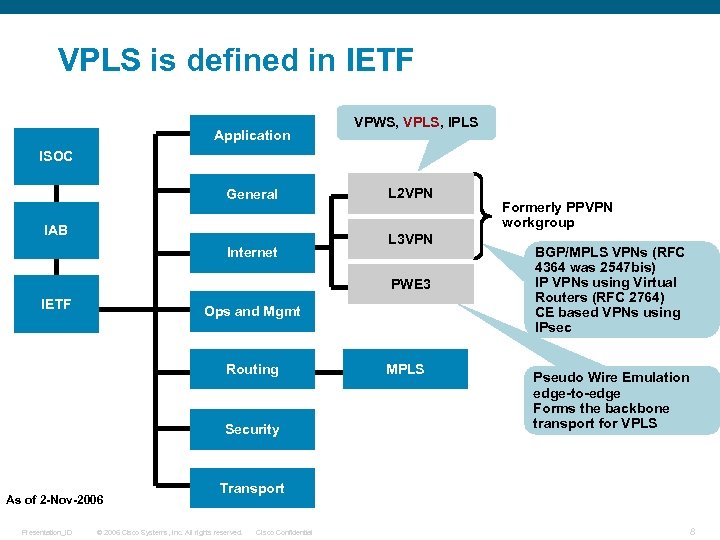 VPLS is defined in IETF Application VPWS, VPLS, IPLS ISOC General IAB Internet L 2 VPN L 3 VPN PWE 3 IETF Ops and Mgmt Routing Security As of 2 -Nov-2006 Presentation_ID MPLS Formerly PPVPN workgroup BGP/MPLS VPNs (RFC 4364 was 2547 bis) IP VPNs using Virtual Routers (RFC 2764) CE based VPNs using IPsec Pseudo Wire Emulation edge-to-edge Forms the backbone transport for VPLS Transport © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 8
VPLS is defined in IETF Application VPWS, VPLS, IPLS ISOC General IAB Internet L 2 VPN L 3 VPN PWE 3 IETF Ops and Mgmt Routing Security As of 2 -Nov-2006 Presentation_ID MPLS Formerly PPVPN workgroup BGP/MPLS VPNs (RFC 4364 was 2547 bis) IP VPNs using Virtual Routers (RFC 2764) CE based VPNs using IPsec Pseudo Wire Emulation edge-to-edge Forms the backbone transport for VPLS Transport © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 8
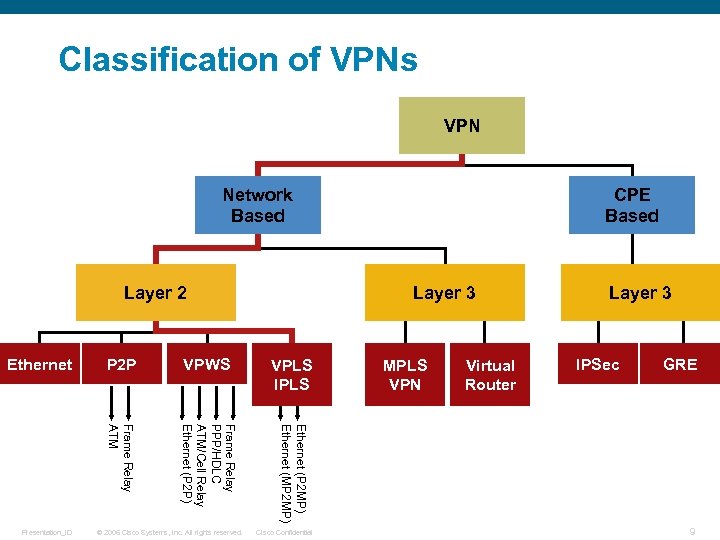 Classification of VPNs VPN Network Based Layer 2 © 2006 Cisco Systems, Inc. All rights reserved. Layer 3 VPLS IPLS MPLS VPN Virtual Router Layer 3 IPSec GRE Ethernet (P 2 MP) Ethernet (MP 2 MP) VPWS Frame Relay PPP/HDLC ATM/Cell Relay Ethernet (P 2 P) Presentation_ID P 2 P Frame Relay ATM Ethernet CPE Based Cisco Confidential 9
Classification of VPNs VPN Network Based Layer 2 © 2006 Cisco Systems, Inc. All rights reserved. Layer 3 VPLS IPLS MPLS VPN Virtual Router Layer 3 IPSec GRE Ethernet (P 2 MP) Ethernet (MP 2 MP) VPWS Frame Relay PPP/HDLC ATM/Cell Relay Ethernet (P 2 P) Presentation_ID P 2 P Frame Relay ATM Ethernet CPE Based Cisco Confidential 9
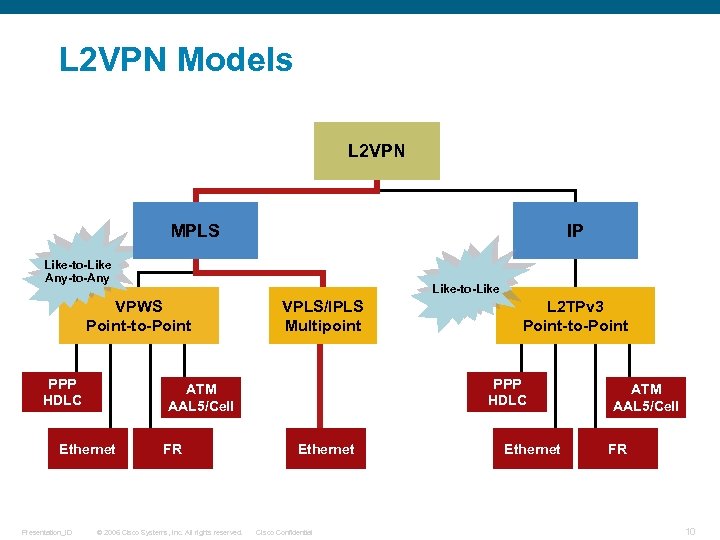 L 2 VPN Models L 2 VPN MPLS IP Like-to-Like Any-to-Any Like-to-Like VPWS Point-to-Point PPP HDLC FR © 2006 Cisco Systems, Inc. All rights reserved. L 2 TPv 3 Point-to-Point PPP HDLC ATM AAL 5/Cell Ethernet Presentation_ID VPLS/IPLS Multipoint Ethernet Cisco Confidential Ethernet ATM AAL 5/Cell FR 10
L 2 VPN Models L 2 VPN MPLS IP Like-to-Like Any-to-Any Like-to-Like VPWS Point-to-Point PPP HDLC FR © 2006 Cisco Systems, Inc. All rights reserved. L 2 TPv 3 Point-to-Point PPP HDLC ATM AAL 5/Cell Ethernet Presentation_ID VPLS/IPLS Multipoint Ethernet Cisco Confidential Ethernet ATM AAL 5/Cell FR 10
 IP LAN-Like Service (IPLS) § An IPLS is very similar to a VPLS except The CE devices must be hosts or routers not switches The service will only carry IPv 4 or IPv 6 packets IP Control packets are also supported – ARP, ICMP Layer 2 packets that do not contain IP are not supported § IPLS is a functional subset of the VPLS service MAC address learning and aging not required Simpler mechanism to match MAC to CE can be used Bridging operations removed from the PE Simplifies hardware capabilities and operation § Defined in draft-ietf-l 2 vpn-ipls Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 11
IP LAN-Like Service (IPLS) § An IPLS is very similar to a VPLS except The CE devices must be hosts or routers not switches The service will only carry IPv 4 or IPv 6 packets IP Control packets are also supported – ARP, ICMP Layer 2 packets that do not contain IP are not supported § IPLS is a functional subset of the VPLS service MAC address learning and aging not required Simpler mechanism to match MAC to CE can be used Bridging operations removed from the PE Simplifies hardware capabilities and operation § Defined in draft-ietf-l 2 vpn-ipls Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 11
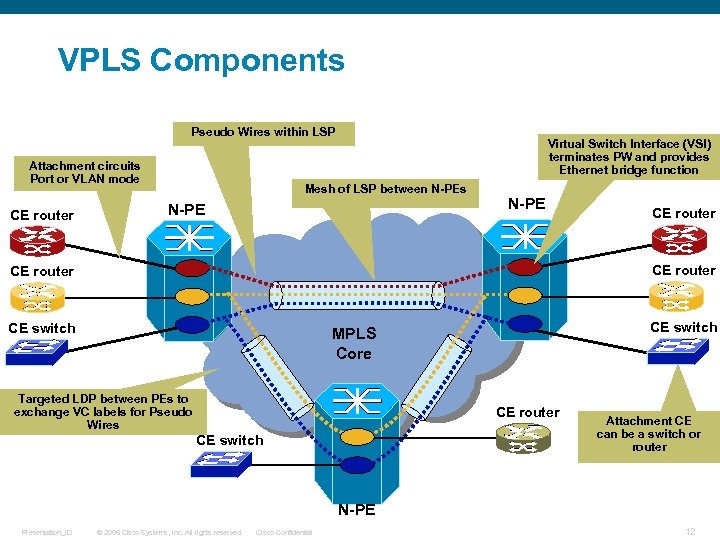 VPLS Components Pseudo Wires within LSP Attachment circuits Port or VLAN mode CE router Virtual Switch Interface (VSI) terminates PW and provides Ethernet bridge function Mesh of LSP between N-PEs N-PE CE router CE switch MPLS Core Targeted LDP between PEs to exchange VC labels for Pseudo Wires CE router CE switch Attachment CE can be a switch or router N-PE Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 12
VPLS Components Pseudo Wires within LSP Attachment circuits Port or VLAN mode CE router Virtual Switch Interface (VSI) terminates PW and provides Ethernet bridge function Mesh of LSP between N-PEs N-PE CE router CE switch MPLS Core Targeted LDP between PEs to exchange VC labels for Pseudo Wires CE router CE switch Attachment CE can be a switch or router N-PE Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 12
 Virtual Switch Interface § Flooding / Forwarding MAC table instances per customer (port/vlan) for each PE VFI will participate in learning and forwarding process Associate ports to MAC, flood unknowns to all other ports § Address Learning / Aging LDP enhanced with additional MAC List TLV (label withdrawal) MAC timers refreshed with incoming frames § Loop Prevention Create full-mesh of Pseudo Wire VCs (Eo. MPLS) Unidirectional LSP carries VCs between pair of N-PE Per A VPLS use “split horizon” concepts to prevent loops Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 13
Virtual Switch Interface § Flooding / Forwarding MAC table instances per customer (port/vlan) for each PE VFI will participate in learning and forwarding process Associate ports to MAC, flood unknowns to all other ports § Address Learning / Aging LDP enhanced with additional MAC List TLV (label withdrawal) MAC timers refreshed with incoming frames § Loop Prevention Create full-mesh of Pseudo Wire VCs (Eo. MPLS) Unidirectional LSP carries VCs between pair of N-PE Per A VPLS use “split horizon” concepts to prevent loops Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 13
 Pseudo Wire Refresher Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 14
Pseudo Wire Refresher Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 14
 Pseudo Wires in VPLS § IETF working group PWE 3 ‘Pseudo Wire Emulation Edge to Edge’; Requirements detailed in RFC 3916 Architecture details in RFC 3985 § Develop standards for the encapsulation & service emulation of “Pseudo Wires” Across a packet switched backbone § A VPLS is based on a full mesh of Pseudo Wires Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 15
Pseudo Wires in VPLS § IETF working group PWE 3 ‘Pseudo Wire Emulation Edge to Edge’; Requirements detailed in RFC 3916 Architecture details in RFC 3985 § Develop standards for the encapsulation & service emulation of “Pseudo Wires” Across a packet switched backbone § A VPLS is based on a full mesh of Pseudo Wires Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 15
 Pseudo Wire Reference Model (RFC 3916) Emulated Service Pseudo Wire Customer Site PSN Tunnel (LSP in MPLS) CE CE Customer Site IP/MPLS PW 1 Attachment Circuit PW 2 Customer Site CE PE 1 PE 2 Pseudo Wire PDUs CE Customer Site Packet Switched Network (PSN) IP or MPLS § A Pseudo Wire (PW) is a connection between two provider edge devices connecting two attachment circuits (ACs) § In an MPLS core a Pseudo Wire uses two MPLS labels Tunnel Label (LSP) identifying remote PE router VC Label identifying Pseudo Wire circuit within tunnel Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 16
Pseudo Wire Reference Model (RFC 3916) Emulated Service Pseudo Wire Customer Site PSN Tunnel (LSP in MPLS) CE CE Customer Site IP/MPLS PW 1 Attachment Circuit PW 2 Customer Site CE PE 1 PE 2 Pseudo Wire PDUs CE Customer Site Packet Switched Network (PSN) IP or MPLS § A Pseudo Wire (PW) is a connection between two provider edge devices connecting two attachment circuits (ACs) § In an MPLS core a Pseudo Wire uses two MPLS labels Tunnel Label (LSP) identifying remote PE router VC Label identifying Pseudo Wire circuit within tunnel Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 16
 Pseudo Wire Standards (Care for a Martini? ) § RFC 4446 – Numeric values for PW types § RFC 4447 – Distribution mechanism for VC labels Previously called draft-martini-l 2 circuit-trans-mpls § RFC 4448 – Encapsulation for Ethernet using MPLS Previously called draft-martini-l 2 circuit-encap-mpls § Other drafts are addressing different encapsulations draft-ietf-pwe 3 -frame-relay/draft-ietf-pwe 3 -atm-encap draft-ietf-pwe 3 -ppp-hdlc-encap-mpls Originally part of draft-martini-l 2 circuit-encap-mpls Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 17
Pseudo Wire Standards (Care for a Martini? ) § RFC 4446 – Numeric values for PW types § RFC 4447 – Distribution mechanism for VC labels Previously called draft-martini-l 2 circuit-trans-mpls § RFC 4448 – Encapsulation for Ethernet using MPLS Previously called draft-martini-l 2 circuit-encap-mpls § Other drafts are addressing different encapsulations draft-ietf-pwe 3 -frame-relay/draft-ietf-pwe 3 -atm-encap draft-ietf-pwe 3 -ppp-hdlc-encap-mpls Originally part of draft-martini-l 2 circuit-encap-mpls Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 17
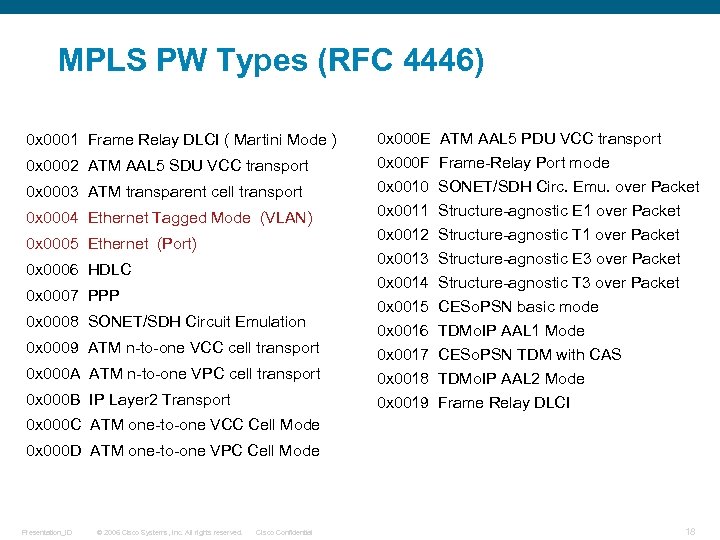 MPLS PW Types (RFC 4446) 0 x 0001 Frame Relay DLCI ( Martini Mode ) 0 x 000 E ATM AAL 5 PDU VCC transport 0 x 0002 ATM AAL 5 SDU VCC transport 0 x 000 F 0 x 0010 0 x 0011 0 x 0012 0 x 0013 0 x 0003 ATM transparent cell transport 0 x 0004 Ethernet Tagged Mode (VLAN) 0 x 0005 Ethernet (Port) 0 x 0006 HDLC Frame-Relay Port mode SONET/SDH Circ. Emu. over Packet Structure-agnostic E 1 over Packet Structure-agnostic T 1 over Packet Structure-agnostic E 3 over Packet 0 x 0014 Structure-agnostic T 3 over Packet 0 x 0007 PPP 0 x 0008 SONET/SDH Circuit Emulation 0 x 0009 ATM n-to-one VCC cell transport 0 x 000 A ATM n-to-one VPC cell transport 0 x 000 B IP Layer 2 Transport 0 x 0015 CESo. PSN basic mode 0 x 0016 TDMo. IP AAL 1 Mode 0 x 0017 CESo. PSN TDM with CAS 0 x 0018 TDMo. IP AAL 2 Mode 0 x 0019 Frame Relay DLCI 0 x 000 C ATM one-to-one VCC Cell Mode 0 x 000 D ATM one-to-one VPC Cell Mode Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 18
MPLS PW Types (RFC 4446) 0 x 0001 Frame Relay DLCI ( Martini Mode ) 0 x 000 E ATM AAL 5 PDU VCC transport 0 x 0002 ATM AAL 5 SDU VCC transport 0 x 000 F 0 x 0010 0 x 0011 0 x 0012 0 x 0013 0 x 0003 ATM transparent cell transport 0 x 0004 Ethernet Tagged Mode (VLAN) 0 x 0005 Ethernet (Port) 0 x 0006 HDLC Frame-Relay Port mode SONET/SDH Circ. Emu. over Packet Structure-agnostic E 1 over Packet Structure-agnostic T 1 over Packet Structure-agnostic E 3 over Packet 0 x 0014 Structure-agnostic T 3 over Packet 0 x 0007 PPP 0 x 0008 SONET/SDH Circuit Emulation 0 x 0009 ATM n-to-one VCC cell transport 0 x 000 A ATM n-to-one VPC cell transport 0 x 000 B IP Layer 2 Transport 0 x 0015 CESo. PSN basic mode 0 x 0016 TDMo. IP AAL 1 Mode 0 x 0017 CESo. PSN TDM with CAS 0 x 0018 TDMo. IP AAL 2 Mode 0 x 0019 Frame Relay DLCI 0 x 000 C ATM one-to-one VCC Cell Mode 0 x 000 D ATM one-to-one VPC Cell Mode Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 18
 VC Information Distribution (RFC 4447) § VC labels are exchanged across a targeted LDP session between PE routers Generic Label TLV within LDP Label Mapping Message § LDP FEC element defined to carry VC information Such PW Type (RFC 4446) and VCID § VC information exchanged using Downstream Unsolicited label distribution procedures § Separate “MAC List” TLV for VPLS Defined in draft-ietf-l 2 vpn-vpls-ldp Use to withdraw labels associated with MAC addresses Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 19
VC Information Distribution (RFC 4447) § VC labels are exchanged across a targeted LDP session between PE routers Generic Label TLV within LDP Label Mapping Message § LDP FEC element defined to carry VC information Such PW Type (RFC 4446) and VCID § VC information exchanged using Downstream Unsolicited label distribution procedures § Separate “MAC List” TLV for VPLS Defined in draft-ietf-l 2 vpn-vpls-ldp Use to withdraw labels associated with MAC addresses Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 19
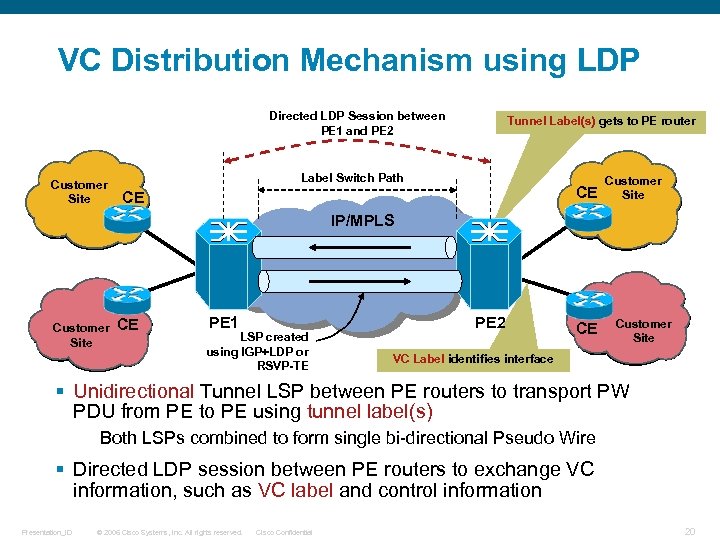 VC Distribution Mechanism using LDP Directed LDP Session between PE 1 and PE 2 Customer Site Tunnel Label(s) gets to PE router Label Switch Path CE CE Customer Site IP/MPLS Customer Site CE PE 1 LSP created using IGP+LDP or RSVP-TE PE 2 CE Customer Site VC Label identifies interface § Unidirectional Tunnel LSP between PE routers to transport PW PDU from PE to PE using tunnel label(s) Both LSPs combined to form single bi-directional Pseudo Wire § Directed LDP session between PE routers to exchange VC information, such as VC label and control information Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 20
VC Distribution Mechanism using LDP Directed LDP Session between PE 1 and PE 2 Customer Site Tunnel Label(s) gets to PE router Label Switch Path CE CE Customer Site IP/MPLS Customer Site CE PE 1 LSP created using IGP+LDP or RSVP-TE PE 2 CE Customer Site VC Label identifies interface § Unidirectional Tunnel LSP between PE routers to transport PW PDU from PE to PE using tunnel label(s) Both LSPs combined to form single bi-directional Pseudo Wire § Directed LDP session between PE routers to exchange VC information, such as VC label and control information Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 20
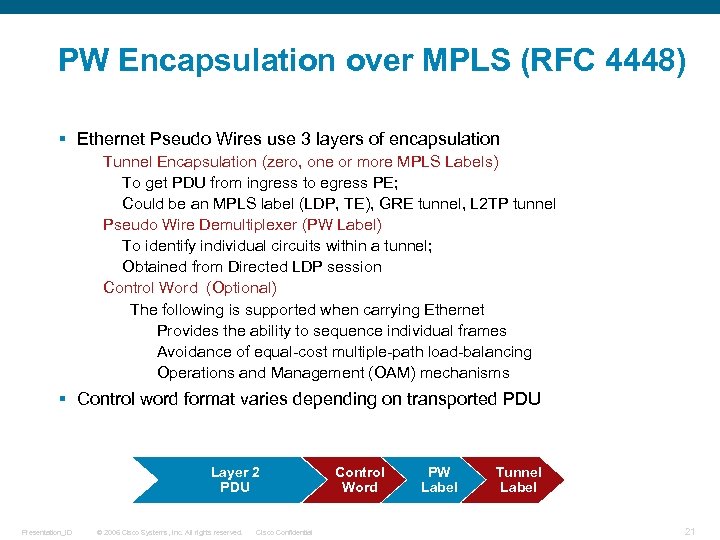 PW Encapsulation over MPLS (RFC 4448) § Ethernet Pseudo Wires use 3 layers of encapsulation Tunnel Encapsulation (zero, one or more MPLS Labels) To get PDU from ingress to egress PE; Could be an MPLS label (LDP, TE), GRE tunnel, L 2 TP tunnel Pseudo Wire Demultiplexer (PW Label) To identify individual circuits within a tunnel; Obtained from Directed LDP session Control Word (Optional) The following is supported when carrying Ethernet Provides the ability to sequence individual frames Avoidance of equal-cost multiple-path load-balancing Operations and Management (OAM) mechanisms § Control word format varies depending on transported PDU Layer 2 PDU Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential Control Word PW Label Tunnel Label 21
PW Encapsulation over MPLS (RFC 4448) § Ethernet Pseudo Wires use 3 layers of encapsulation Tunnel Encapsulation (zero, one or more MPLS Labels) To get PDU from ingress to egress PE; Could be an MPLS label (LDP, TE), GRE tunnel, L 2 TP tunnel Pseudo Wire Demultiplexer (PW Label) To identify individual circuits within a tunnel; Obtained from Directed LDP session Control Word (Optional) The following is supported when carrying Ethernet Provides the ability to sequence individual frames Avoidance of equal-cost multiple-path load-balancing Operations and Management (OAM) mechanisms § Control word format varies depending on transported PDU Layer 2 PDU Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential Control Word PW Label Tunnel Label 21
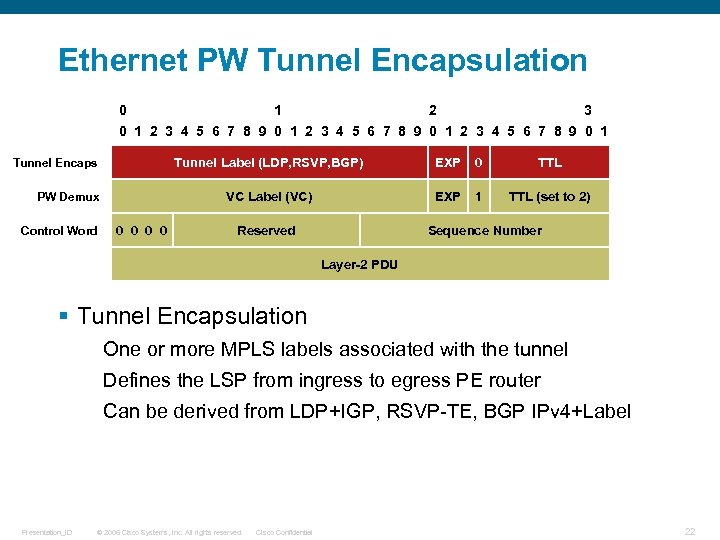 Ethernet PW Tunnel Encapsulation 0 1 2 3 4 5 6 7 8 9 0 1 Tunnel Label (LDP, RSVP, BGP) PW Demux Control Word 0 0 EXP 0 TTL VC Label (VC) Tunnel Encaps EXP 1 TTL (set to 2) Reserved Sequence Number Layer-2 PDU § Tunnel Encapsulation One or more MPLS labels associated with the tunnel Defines the LSP from ingress to egress PE router Can be derived from LDP+IGP, RSVP-TE, BGP IPv 4+Label Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 22
Ethernet PW Tunnel Encapsulation 0 1 2 3 4 5 6 7 8 9 0 1 Tunnel Label (LDP, RSVP, BGP) PW Demux Control Word 0 0 EXP 0 TTL VC Label (VC) Tunnel Encaps EXP 1 TTL (set to 2) Reserved Sequence Number Layer-2 PDU § Tunnel Encapsulation One or more MPLS labels associated with the tunnel Defines the LSP from ingress to egress PE router Can be derived from LDP+IGP, RSVP-TE, BGP IPv 4+Label Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 22
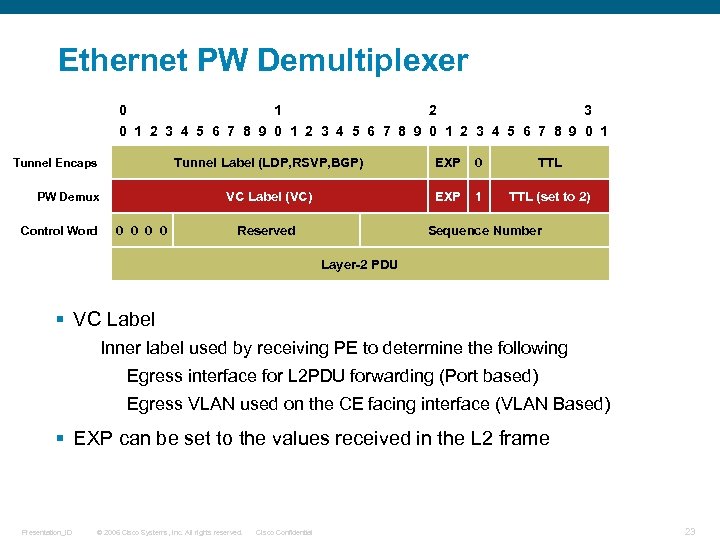 Ethernet PW Demultiplexer 0 1 2 3 4 5 6 7 8 9 0 1 Tunnel Label (LDP, RSVP, BGP) PW Demux Control Word 0 0 EXP 0 TTL VC Label (VC) Tunnel Encaps EXP 1 TTL (set to 2) Reserved Sequence Number Layer-2 PDU § VC Label Inner label used by receiving PE to determine the following Egress interface for L 2 PDU forwarding (Port based) Egress VLAN used on the CE facing interface (VLAN Based) § EXP can be set to the values received in the L 2 frame Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 23
Ethernet PW Demultiplexer 0 1 2 3 4 5 6 7 8 9 0 1 Tunnel Label (LDP, RSVP, BGP) PW Demux Control Word 0 0 EXP 0 TTL VC Label (VC) Tunnel Encaps EXP 1 TTL (set to 2) Reserved Sequence Number Layer-2 PDU § VC Label Inner label used by receiving PE to determine the following Egress interface for L 2 PDU forwarding (Port based) Egress VLAN used on the CE facing interface (VLAN Based) § EXP can be set to the values received in the L 2 frame Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 23
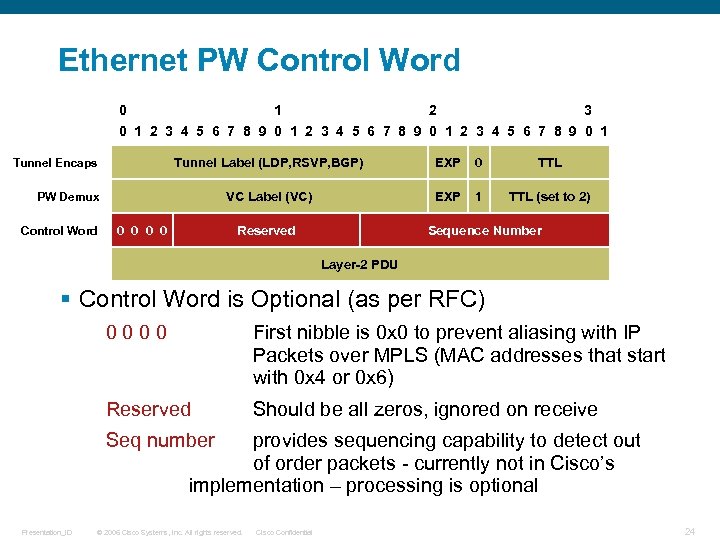 Ethernet PW Control Word 0 1 2 3 4 5 6 7 8 9 0 1 Tunnel Label (LDP, RSVP, BGP) EXP 0 TTL VC Label (VC) Tunnel Encaps EXP 1 TTL (set to 2) PW Demux Control Word 0 0 Reserved Sequence Number Layer-2 PDU § Control Word is Optional (as per RFC) 0000 First nibble is 0 x 0 to prevent aliasing with IP Packets over MPLS (MAC addresses that start with 0 x 4 or 0 x 6) Reserved Should be all zeros, ignored on receive Seq number provides sequencing capability to detect out of order packets - currently not in Cisco’s implementation – processing is optional Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 24
Ethernet PW Control Word 0 1 2 3 4 5 6 7 8 9 0 1 Tunnel Label (LDP, RSVP, BGP) EXP 0 TTL VC Label (VC) Tunnel Encaps EXP 1 TTL (set to 2) PW Demux Control Word 0 0 Reserved Sequence Number Layer-2 PDU § Control Word is Optional (as per RFC) 0000 First nibble is 0 x 0 to prevent aliasing with IP Packets over MPLS (MAC addresses that start with 0 x 4 or 0 x 6) Reserved Should be all zeros, ignored on receive Seq number provides sequencing capability to detect out of order packets - currently not in Cisco’s implementation – processing is optional Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 24
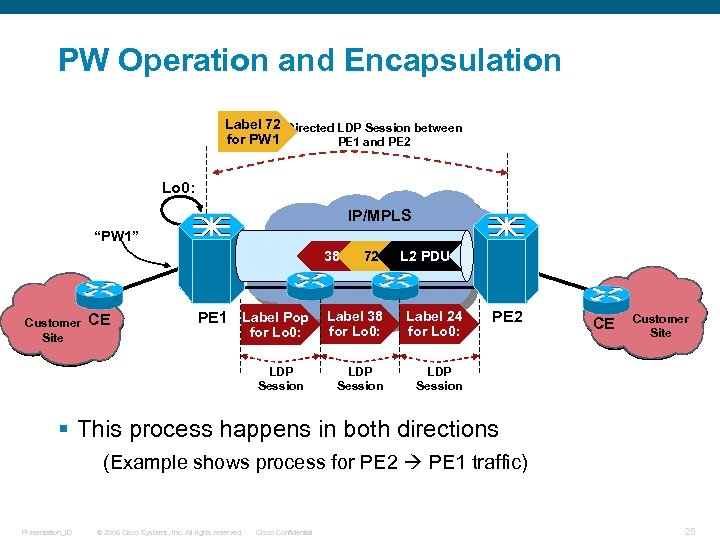 PW Operation and Encapsulation Label 72 Directed LDP Session between for PW 1 PE 1 and PE 2 Lo 0: IP/MPLS “PW 1” 38 72 L 2 P 1 24 LSP P 2 PDU CE for Lo 0: Label 38 for Lo 0: Label 24 for Lo 0: LDP Session Customer Site LDP Session PE 2 LDP Session PE 1 Label Pop CE Customer Site § This process happens in both directions (Example shows process for PE 2 PE 1 traffic) Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 25
PW Operation and Encapsulation Label 72 Directed LDP Session between for PW 1 PE 1 and PE 2 Lo 0: IP/MPLS “PW 1” 38 72 L 2 P 1 24 LSP P 2 PDU CE for Lo 0: Label 38 for Lo 0: Label 24 for Lo 0: LDP Session Customer Site LDP Session PE 2 LDP Session PE 1 Label Pop CE Customer Site § This process happens in both directions (Example shows process for PE 2 PE 1 traffic) Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 25
 VPLS Architecture Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 26
VPLS Architecture Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 26
 VPLS Standards § Architecture allows IEEE 802. 1 bridge behaviour in SP plus: Autodiscovery of other N-PE in same VPLS instance Signaling of PWs to interconnect VPLS instances Loop avoidance & MAC Address withdrawal § Two drafts have been approved by IETF L 2 VPN Working Group § draft-ietf-l 2 vpn-vpls-ldp Uses LDP for signalling, agnostic on PE discovery method Predominant support from carriers and vendors Cisco supports this draft § draft-ietf-l 2 vpn-vpls-bgp Uses BGP for signalling and autodiscovery Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 27
VPLS Standards § Architecture allows IEEE 802. 1 bridge behaviour in SP plus: Autodiscovery of other N-PE in same VPLS instance Signaling of PWs to interconnect VPLS instances Loop avoidance & MAC Address withdrawal § Two drafts have been approved by IETF L 2 VPN Working Group § draft-ietf-l 2 vpn-vpls-ldp Uses LDP for signalling, agnostic on PE discovery method Predominant support from carriers and vendors Cisco supports this draft § draft-ietf-l 2 vpn-vpls-bgp Uses BGP for signalling and autodiscovery Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 27
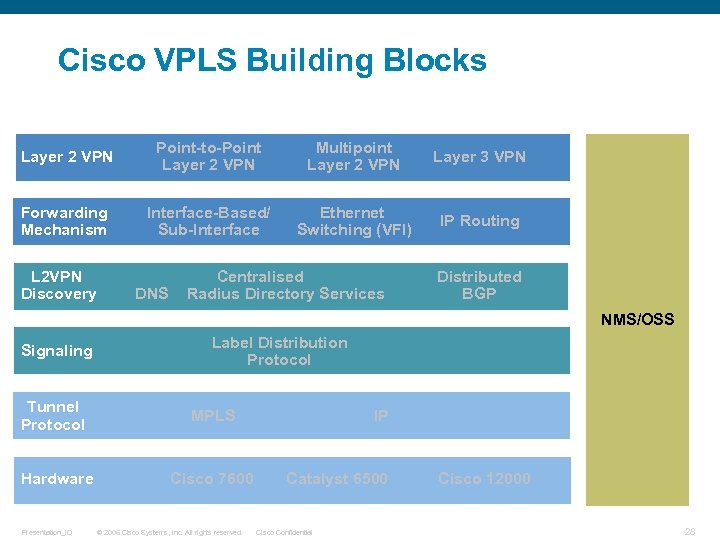 Cisco VPLS Building Blocks Layer 2 VPN Point-to-Point Layer 2 VPN Multipoint Layer 2 VPN Layer 3 VPN Forwarding Mechanism Interface-Based/ Sub-Interface Ethernet Switching (VFI) IP Routing L 2 VPN Discovery DNS Centralised Radius Directory Services Distributed BGP NMS/OSS Signaling Label Distribution Protocol Tunnel Protocol MPLS Hardware Cisco 7600 Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. IP Catalyst 6500 Cisco Confidential Cisco 12000 28
Cisco VPLS Building Blocks Layer 2 VPN Point-to-Point Layer 2 VPN Multipoint Layer 2 VPN Layer 3 VPN Forwarding Mechanism Interface-Based/ Sub-Interface Ethernet Switching (VFI) IP Routing L 2 VPN Discovery DNS Centralised Radius Directory Services Distributed BGP NMS/OSS Signaling Label Distribution Protocol Tunnel Protocol MPLS Hardware Cisco 7600 Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. IP Catalyst 6500 Cisco Confidential Cisco 12000 28
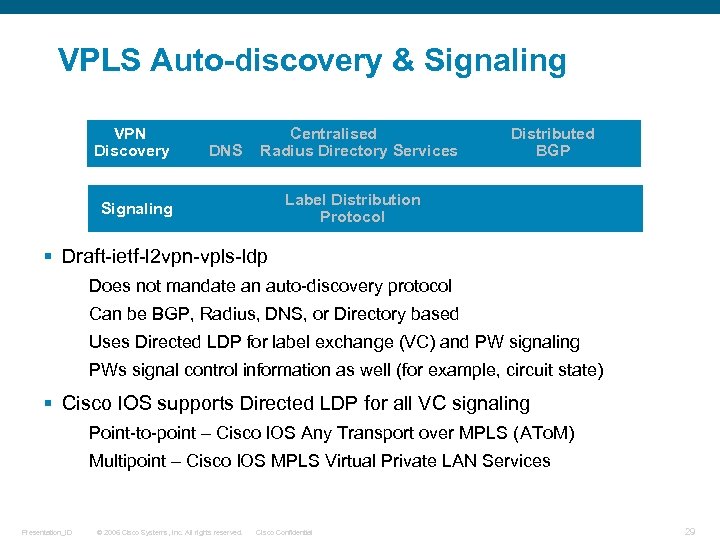 VPLS Auto-discovery & Signaling VPN Discovery DNS Centralised Radius Directory Services Distributed BGP Label Distribution Protocol Signaling § Draft-ietf-l 2 vpn-vpls-ldp Does not mandate an auto-discovery protocol Can be BGP, Radius, DNS, or Directory based Uses Directed LDP for label exchange (VC) and PW signaling PWs signal control information as well (for example, circuit state) § Cisco IOS supports Directed LDP for all VC signaling Point-to-point – Cisco IOS Any Transport over MPLS (ATo. M) Multipoint – Cisco IOS MPLS Virtual Private LAN Services Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 29
VPLS Auto-discovery & Signaling VPN Discovery DNS Centralised Radius Directory Services Distributed BGP Label Distribution Protocol Signaling § Draft-ietf-l 2 vpn-vpls-ldp Does not mandate an auto-discovery protocol Can be BGP, Radius, DNS, or Directory based Uses Directed LDP for label exchange (VC) and PW signaling PWs signal control information as well (for example, circuit state) § Cisco IOS supports Directed LDP for all VC signaling Point-to-point – Cisco IOS Any Transport over MPLS (ATo. M) Multipoint – Cisco IOS MPLS Virtual Private LAN Services Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 29
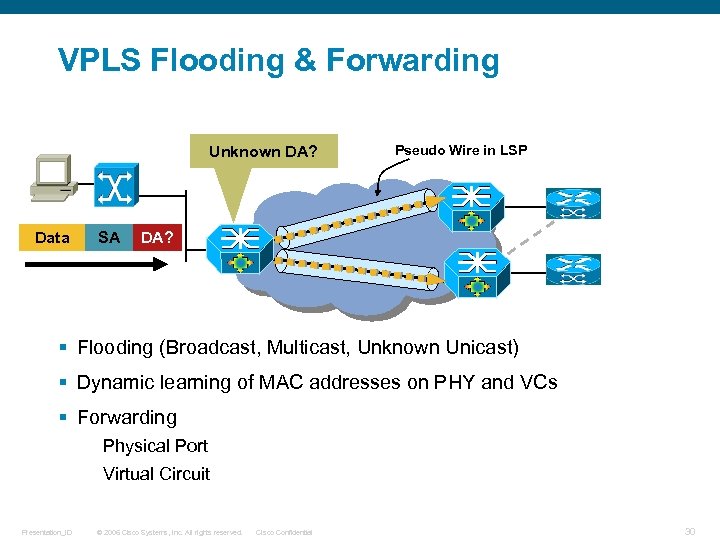 VPLS Flooding & Forwarding Unknown DA? Data SA Pseudo Wire in LSP DA? § Flooding (Broadcast, Multicast, Unknown Unicast) § Dynamic learning of MAC addresses on PHY and VCs § Forwarding Physical Port Virtual Circuit Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 30
VPLS Flooding & Forwarding Unknown DA? Data SA Pseudo Wire in LSP DA? § Flooding (Broadcast, Multicast, Unknown Unicast) § Dynamic learning of MAC addresses on PHY and VCs § Forwarding Physical Port Virtual Circuit Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 30
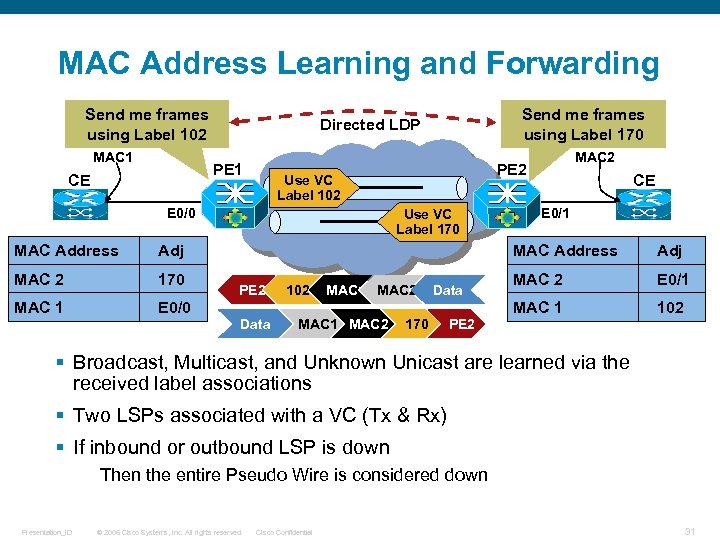 MAC Address Learning and Forwarding Send me frames using Label 102 MAC 1 PE 1 CE 170 MAC 1 E 0/0 Use VC Label 170 Adj MAC 2 PE 2 Use VC Label 102 E 0/0 MAC Address Send me frames using Label 170 Directed LDP CE E 0/1 MAC Address PE 2 Data 102 MAC 1 MAC 2 Data 170 PE 2 Adj MAC 2 E 0/1 MAC 1 102 § Broadcast, Multicast, and Unknown Unicast are learned via the received label associations § Two LSPs associated with a VC (Tx & Rx) § If inbound or outbound LSP is down Then the entire Pseudo Wire is considered down Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 31
MAC Address Learning and Forwarding Send me frames using Label 102 MAC 1 PE 1 CE 170 MAC 1 E 0/0 Use VC Label 170 Adj MAC 2 PE 2 Use VC Label 102 E 0/0 MAC Address Send me frames using Label 170 Directed LDP CE E 0/1 MAC Address PE 2 Data 102 MAC 1 MAC 2 Data 170 PE 2 Adj MAC 2 E 0/1 MAC 1 102 § Broadcast, Multicast, and Unknown Unicast are learned via the received label associations § Two LSPs associated with a VC (Tx & Rx) § If inbound or outbound LSP is down Then the entire Pseudo Wire is considered down Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 31
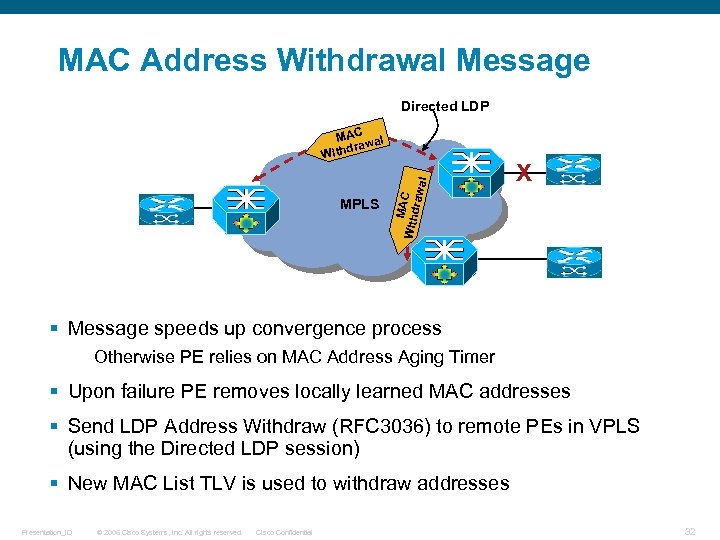 MAC Address Withdrawal Message Directed LDP MPLS MA Withd C rawa l MAC wal dra With X § Message speeds up convergence process Otherwise PE relies on MAC Address Aging Timer § Upon failure PE removes locally learned MAC addresses § Send LDP Address Withdraw (RFC 3036) to remote PEs in VPLS (using the Directed LDP session) § New MAC List TLV is used to withdraw addresses Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 32
MAC Address Withdrawal Message Directed LDP MPLS MA Withd C rawa l MAC wal dra With X § Message speeds up convergence process Otherwise PE relies on MAC Address Aging Timer § Upon failure PE removes locally learned MAC addresses § Send LDP Address Withdraw (RFC 3036) to remote PEs in VPLS (using the Directed LDP session) § New MAC List TLV is used to withdraw addresses Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 32
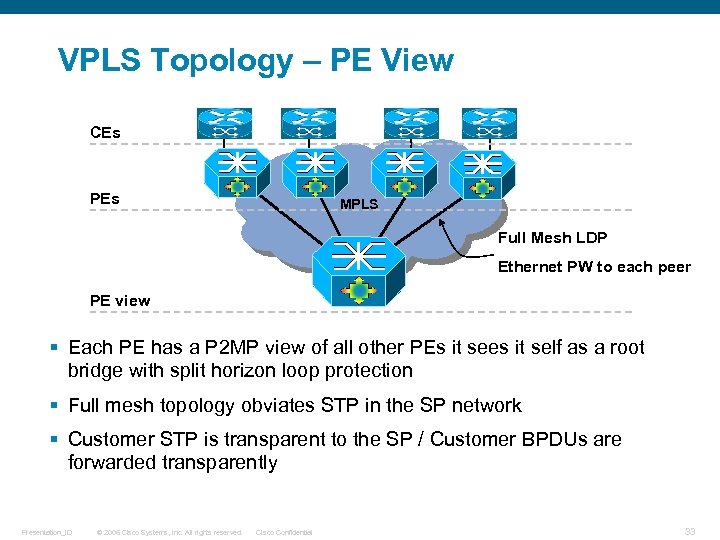 VPLS Topology – PE View CEs PEs MPLS Full Mesh LDP Ethernet PW to each peer PE view § Each PE has a P 2 MP view of all other PEs it sees it self as a root bridge with split horizon loop protection § Full mesh topology obviates STP in the SP network § Customer STP is transparent to the SP / Customer BPDUs are forwarded transparently Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 33
VPLS Topology – PE View CEs PEs MPLS Full Mesh LDP Ethernet PW to each peer PE view § Each PE has a P 2 MP view of all other PEs it sees it self as a root bridge with split horizon loop protection § Full mesh topology obviates STP in the SP network § Customer STP is transparent to the SP / Customer BPDUs are forwarded transparently Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 33
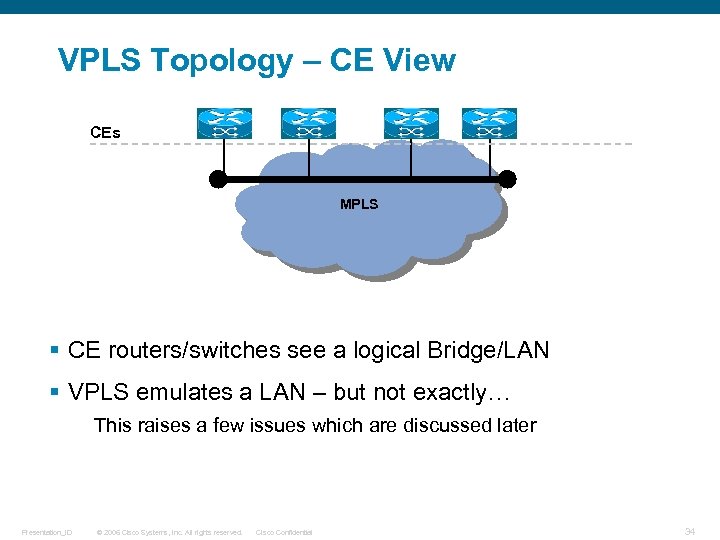 VPLS Topology – CE View CEs PEs MPLS Core VPLS Full Mesh LDP Ethernet PW to each peer PE view § CE routers/switches see a logical Bridge/LAN § VPLS emulates a LAN – but not exactly… This raises a few issues which are discussed later Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 34
VPLS Topology – CE View CEs PEs MPLS Core VPLS Full Mesh LDP Ethernet PW to each peer PE view § CE routers/switches see a logical Bridge/LAN § VPLS emulates a LAN – but not exactly… This raises a few issues which are discussed later Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 34
 VPLS Architectures § VPLS defines two Architectures Direct Attachment (Flat) Described in section 4 of Draft-ietf-l 2 vpn-vpls-ldp Hierarchical or H-VPLS comprising of two access methods Ethernet Edge (EE-H-VPLS) – Qin. Q tunnels MPLS Edge (ME-H-VPLS) - PWE 3 Pseudo Wires (Eo. MPLS) Described in section 10 of Draft-ietf-l 2 vpn-vpls-ldp § Each architecture has different scaling characteristics Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 35
VPLS Architectures § VPLS defines two Architectures Direct Attachment (Flat) Described in section 4 of Draft-ietf-l 2 vpn-vpls-ldp Hierarchical or H-VPLS comprising of two access methods Ethernet Edge (EE-H-VPLS) – Qin. Q tunnels MPLS Edge (ME-H-VPLS) - PWE 3 Pseudo Wires (Eo. MPLS) Described in section 10 of Draft-ietf-l 2 vpn-vpls-ldp § Each architecture has different scaling characteristics Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 35
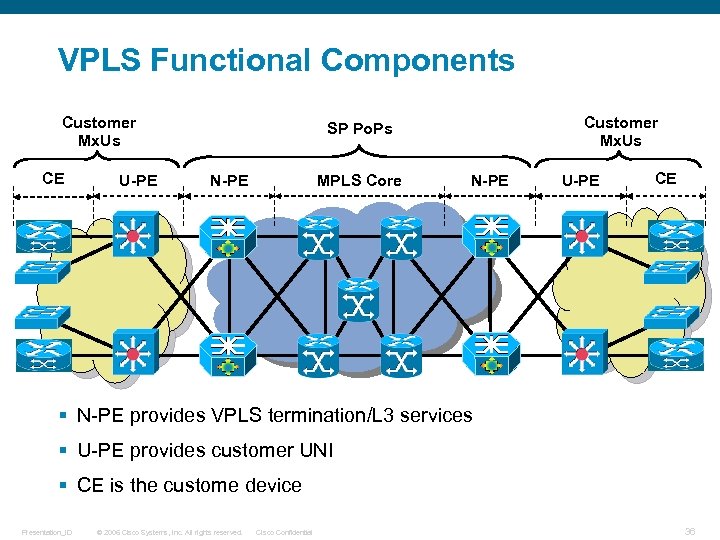 VPLS Functional Components Customer Mx. Us CE U-PE Customer Mx. Us SP Po. Ps N-PE MPLS Core N-PE U-PE CE § N-PE provides VPLS termination/L 3 services § U-PE provides customer UNI § CE is the custome device Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 36
VPLS Functional Components Customer Mx. Us CE U-PE Customer Mx. Us SP Po. Ps N-PE MPLS Core N-PE U-PE CE § N-PE provides VPLS termination/L 3 services § U-PE provides customer UNI § CE is the custome device Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 36
 Directed attachment (Flat) Characteristics § Suitable for simple/small implementations § Full mesh of directed LDP sessions required N*(N-1)/2 Pseudo Wires required Scalability issue a number of PE routers grows § No hierarchical scalability § VLAN and Port level support (no Qin. Q) § Potential signaling and packet replication overhead Large amount of multicast replication over same physical CPU overhead for replication Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 37
Directed attachment (Flat) Characteristics § Suitable for simple/small implementations § Full mesh of directed LDP sessions required N*(N-1)/2 Pseudo Wires required Scalability issue a number of PE routers grows § No hierarchical scalability § VLAN and Port level support (no Qin. Q) § Potential signaling and packet replication overhead Large amount of multicast replication over same physical CPU overhead for replication Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 37
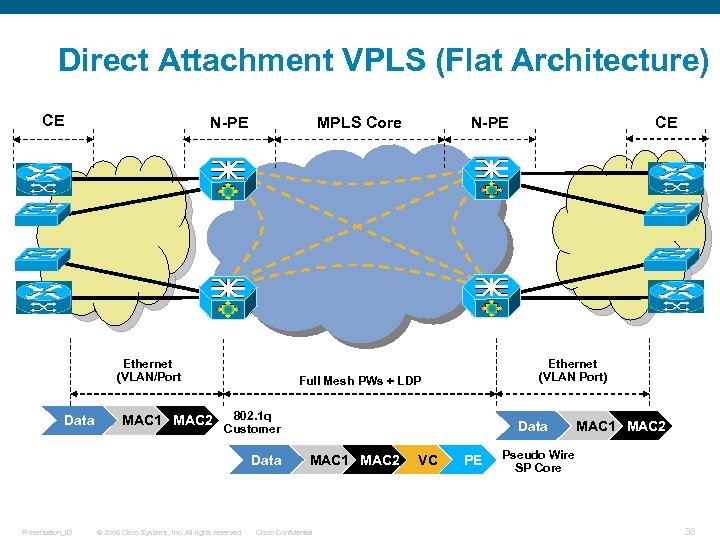 Direct Attachment VPLS (Flat Architecture) CE N-PE MPLS Core Ethernet (VLAN/Port Data MAC 1 MAC 2 Presentation_ID Ethernet (VLAN Port) Full Mesh PWs + LDP 802. 1 q Customer Data © 2006 Cisco Systems, Inc. All rights reserved. CE N-PE Data MAC 1 MAC 2 Cisco Confidential VC PE MAC 1 MAC 2 Pseudo Wire SP Core 38
Direct Attachment VPLS (Flat Architecture) CE N-PE MPLS Core Ethernet (VLAN/Port Data MAC 1 MAC 2 Presentation_ID Ethernet (VLAN Port) Full Mesh PWs + LDP 802. 1 q Customer Data © 2006 Cisco Systems, Inc. All rights reserved. CE N-PE Data MAC 1 MAC 2 Cisco Confidential VC PE MAC 1 MAC 2 Pseudo Wire SP Core 38
 Hierarchical VPLS (H-VPLS) § Best for larger scale deployment § Reduction in packet replication and signaling overhead § Consists of two levels in a Hub and Spoke topology Hub consists of full mesh VPLS Pseudo Wires in MPLS core Spokes consist of L 2/L 3 tunnels connecting to VPLS (Hub) PEs Q-in-Q (L 2), MPLS (L 3), L 2 TPv 3 (L 3) § Some additional H-VPLS terms MTU-s PE-r Non bridging PE router PE-rs Presentation_ID Multi-Tenant Unit Switch capable of bridging (U-PE) Bridging and Routing capable PE © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 39
Hierarchical VPLS (H-VPLS) § Best for larger scale deployment § Reduction in packet replication and signaling overhead § Consists of two levels in a Hub and Spoke topology Hub consists of full mesh VPLS Pseudo Wires in MPLS core Spokes consist of L 2/L 3 tunnels connecting to VPLS (Hub) PEs Q-in-Q (L 2), MPLS (L 3), L 2 TPv 3 (L 3) § Some additional H-VPLS terms MTU-s PE-r Non bridging PE router PE-rs Presentation_ID Multi-Tenant Unit Switch capable of bridging (U-PE) Bridging and Routing capable PE © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 39
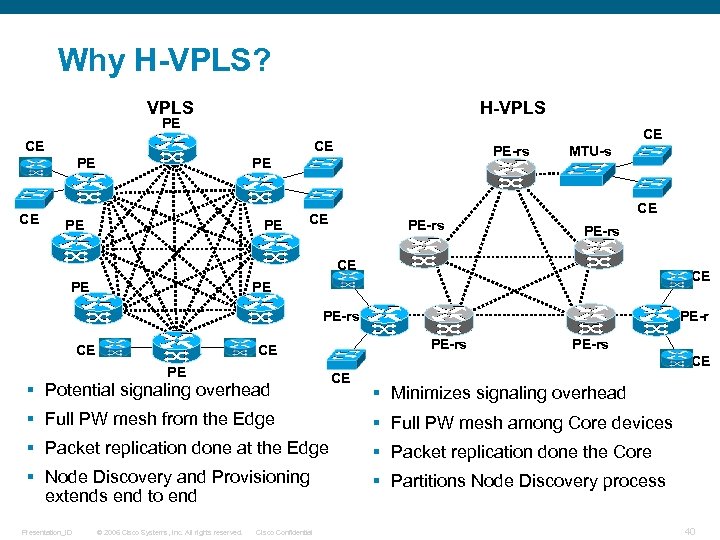 Why H-VPLS? VPLS H-VPLS PE CE CE CE PE-rs PE PE PE MTU-s CE CE PE-rs CE PE § Potential signaling overhead PE-rs CE CE § Minimizes signaling overhead § Full PW mesh from the Edge § Full PW mesh among Core devices § Packet replication done at the Edge § Packet replication done the Core § Node Discovery and Provisioning extends end to end § Partitions Node Discovery process Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 40
Why H-VPLS? VPLS H-VPLS PE CE CE CE PE-rs PE PE PE MTU-s CE CE PE-rs CE PE § Potential signaling overhead PE-rs CE CE § Minimizes signaling overhead § Full PW mesh from the Edge § Full PW mesh among Core devices § Packet replication done at the Edge § Packet replication done the Core § Node Discovery and Provisioning extends end to end § Partitions Node Discovery process Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 40
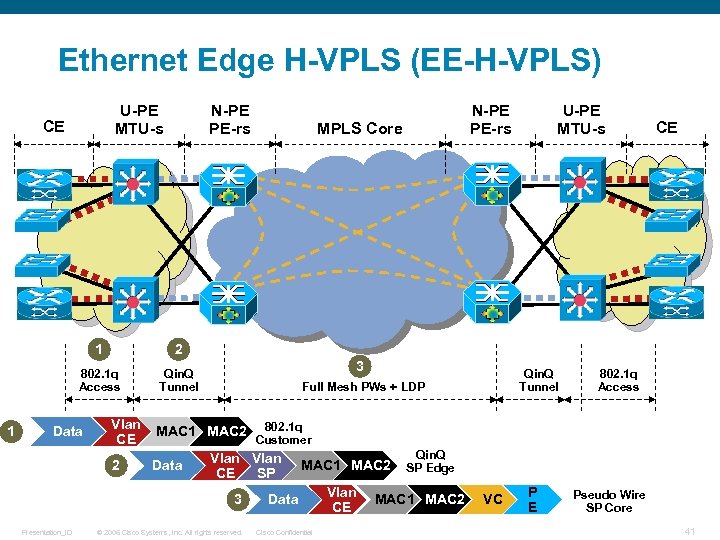 Ethernet Edge H-VPLS (EE-H-VPLS) U-PE MTU-s CE N-PE PE-rs 1 1 Qin. Q Tunnel Data Vlan CE 2 3 MAC 1 MAC 2 Data Qin. Q Tunnel Full Mesh PWs + LDP CE © 2006 Cisco Systems, Inc. All rights reserved. 802. 1 q Access 802. 1 q Customer Vlan CE SP 3 Presentation_ID MPLS Core U-PE MTU-s 2 802. 1 q Access N-PE PE-rs MAC 1 MAC 2 Data Cisco Confidential Vlan CE Qin. Q SP Edge MAC 1 MAC 2 VC P E Pseudo Wire SP Core 41
Ethernet Edge H-VPLS (EE-H-VPLS) U-PE MTU-s CE N-PE PE-rs 1 1 Qin. Q Tunnel Data Vlan CE 2 3 MAC 1 MAC 2 Data Qin. Q Tunnel Full Mesh PWs + LDP CE © 2006 Cisco Systems, Inc. All rights reserved. 802. 1 q Access 802. 1 q Customer Vlan CE SP 3 Presentation_ID MPLS Core U-PE MTU-s 2 802. 1 q Access N-PE PE-rs MAC 1 MAC 2 Data Cisco Confidential Vlan CE Qin. Q SP Edge MAC 1 MAC 2 VC P E Pseudo Wire SP Core 41
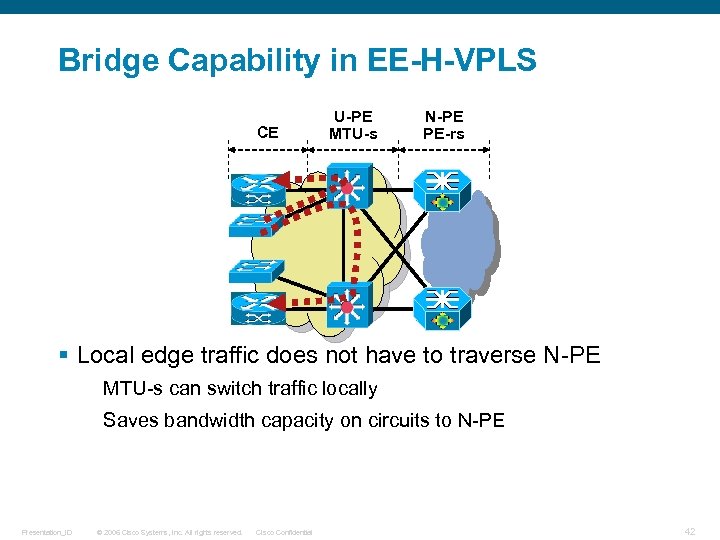 Bridge Capability in EE-H-VPLS CE U-PE MTU-s N-PE PE-rs § Local edge traffic does not have to traverse N-PE MTU-s can switch traffic locally Saves bandwidth capacity on circuits to N-PE Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 42
Bridge Capability in EE-H-VPLS CE U-PE MTU-s N-PE PE-rs § Local edge traffic does not have to traverse N-PE MTU-s can switch traffic locally Saves bandwidth capacity on circuits to N-PE Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 42
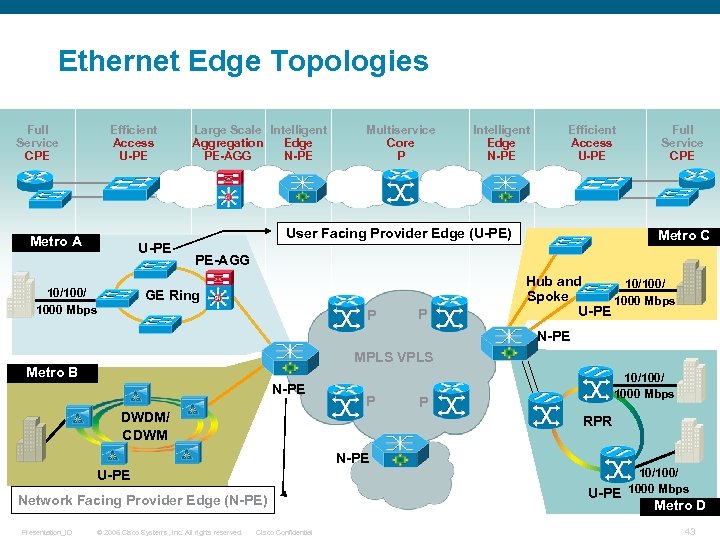 Ethernet Edge Topologies Full Service CPE Efficient Access U-PE Metro A U-PE 10/100/ 1000 Mbps Large Scale Intelligent Aggregation Edge PE-AGG N-PE Multiservice Core P Intelligent Edge N-PE Efficient Access U-PE User Facing Provider Edge (U-PE) Full Service CPE Metro C PE-AGG GE Ring P P Hub and 10/100/ Spoke 1000 Mbps U-PE N-PE MPLS VPLS Metro B N-PE P DWDM/ CDWM 10/100/ 1000 Mbps P RPR N-PE U-PE Network Facing Provider Edge (N-PE) Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 10/100/ U-PE 1000 Mbps Metro D 43
Ethernet Edge Topologies Full Service CPE Efficient Access U-PE Metro A U-PE 10/100/ 1000 Mbps Large Scale Intelligent Aggregation Edge PE-AGG N-PE Multiservice Core P Intelligent Edge N-PE Efficient Access U-PE User Facing Provider Edge (U-PE) Full Service CPE Metro C PE-AGG GE Ring P P Hub and 10/100/ Spoke 1000 Mbps U-PE N-PE MPLS VPLS Metro B N-PE P DWDM/ CDWM 10/100/ 1000 Mbps P RPR N-PE U-PE Network Facing Provider Edge (N-PE) Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 10/100/ U-PE 1000 Mbps Metro D 43
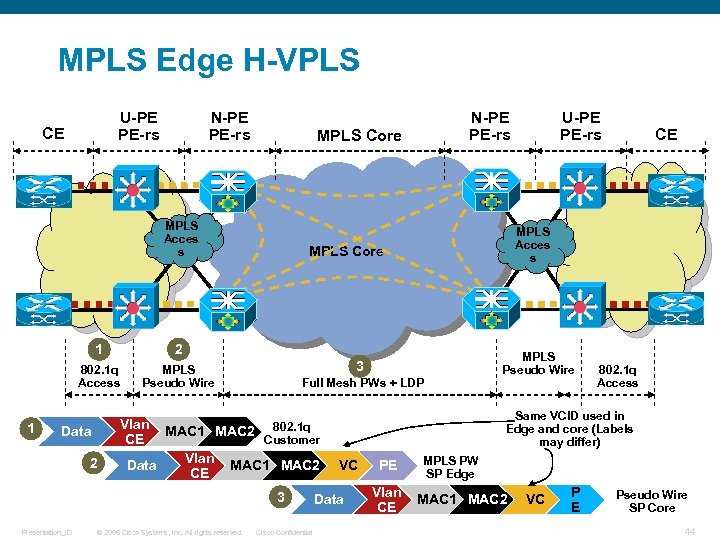 MPLS Edge H-VPLS U-PE PE-rs CE N-PE PE-rs MPLS Core MPLS Acces s 1 1 MPLS Core MPLS Pseudo Wire Vlan CE Data 2 Data 3 Full Mesh PWs + LDP MAC 1 MAC 2 3 Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential CE MPLS Pseudo Wire 802. 1 q Access Same VCID used in Edge and core (Labels may differ) MAC 1 MAC 2 802. 1 q Customer Vlan CE U-PE PE-rs MPLS Acces s 2 802. 1 q Access N-PE PE-rs VC Data PE Vlan CE MPLS PW SP Edge MAC 1 MAC 2 VC P E Pseudo Wire SP Core 44
MPLS Edge H-VPLS U-PE PE-rs CE N-PE PE-rs MPLS Core MPLS Acces s 1 1 MPLS Core MPLS Pseudo Wire Vlan CE Data 2 Data 3 Full Mesh PWs + LDP MAC 1 MAC 2 3 Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential CE MPLS Pseudo Wire 802. 1 q Access Same VCID used in Edge and core (Labels may differ) MAC 1 MAC 2 802. 1 q Customer Vlan CE U-PE PE-rs MPLS Acces s 2 802. 1 q Access N-PE PE-rs VC Data PE Vlan CE MPLS PW SP Edge MAC 1 MAC 2 VC P E Pseudo Wire SP Core 44
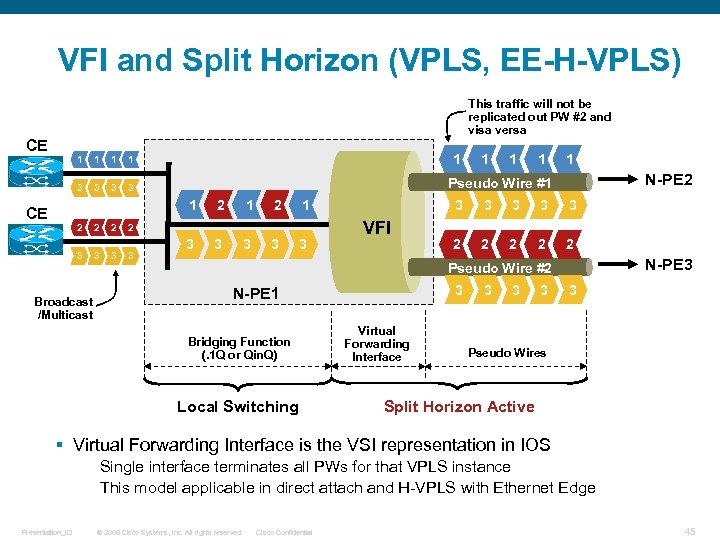 VFI and Split Horizon (VPLS, EE-H-VPLS) This traffic will not be replicated out PW #2 and visa versa CE 1 1 1 3 3 3 1 1 3 2 2 2 3 3 3 2 1 2 3 Broadcast /Multicast 1 1 1 N-PE 2 Pseudo Wire #1 1 CE 1 3 3 3 VFI 3 3 2 2 2 N-PE 3 Pseudo Wire #2 3 N-PE 1 Bridging Function (. 1 Q or Qin. Q) Local Switching Virtual Forwarding Interface 3 3 Pseudo Wires Split Horizon Active § Virtual Forwarding Interface is the VSI representation in IOS Single interface terminates all PWs for that VPLS instance This model applicable in direct attach and H-VPLS with Ethernet Edge Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 45
VFI and Split Horizon (VPLS, EE-H-VPLS) This traffic will not be replicated out PW #2 and visa versa CE 1 1 1 3 3 3 1 1 3 2 2 2 3 3 3 2 1 2 3 Broadcast /Multicast 1 1 1 N-PE 2 Pseudo Wire #1 1 CE 1 3 3 3 VFI 3 3 2 2 2 N-PE 3 Pseudo Wire #2 3 N-PE 1 Bridging Function (. 1 Q or Qin. Q) Local Switching Virtual Forwarding Interface 3 3 Pseudo Wires Split Horizon Active § Virtual Forwarding Interface is the VSI representation in IOS Single interface terminates all PWs for that VPLS instance This model applicable in direct attach and H-VPLS with Ethernet Edge Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 45
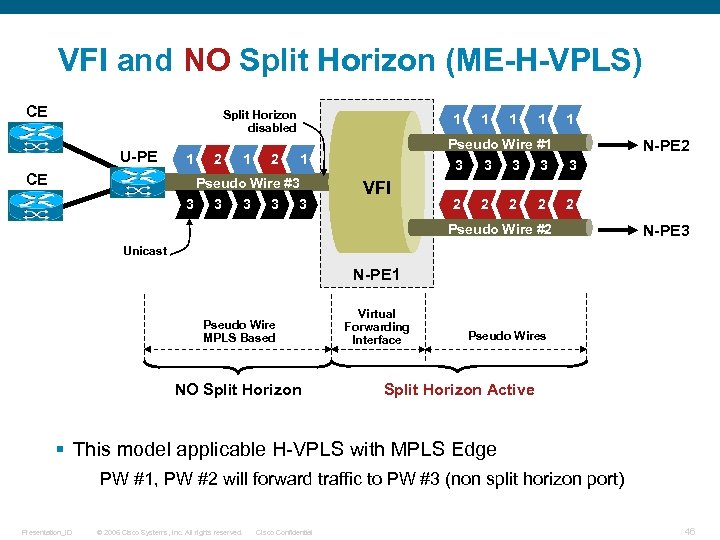 VFI and NO Split Horizon (ME-H-VPLS) CE Split Horizon disabled U-PE 1 CE 2 1 3 3 3 1 1 1 Pseudo Wire #3 1 N-PE 2 3 VFI 3 3 2 2 2 Pseudo Wire #2 N-PE 3 Unicast N-PE 1 Pseudo Wire MPLS Based NO Split Horizon Virtual Forwarding Interface Pseudo Wires Split Horizon Active § This model applicable H-VPLS with MPLS Edge PW #1, PW #2 will forward traffic to PW #3 (non split horizon port) Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 46
VFI and NO Split Horizon (ME-H-VPLS) CE Split Horizon disabled U-PE 1 CE 2 1 3 3 3 1 1 1 Pseudo Wire #3 1 N-PE 2 3 VFI 3 3 2 2 2 Pseudo Wire #2 N-PE 3 Unicast N-PE 1 Pseudo Wire MPLS Based NO Split Horizon Virtual Forwarding Interface Pseudo Wires Split Horizon Active § This model applicable H-VPLS with MPLS Edge PW #1, PW #2 will forward traffic to PW #3 (non split horizon port) Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 46
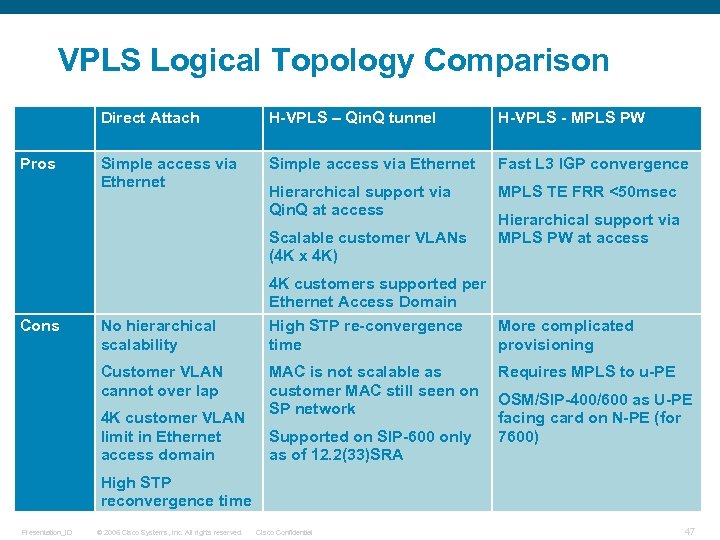 VPLS Logical Topology Comparison Direct Attach Pros H-VPLS – Qin. Q tunnel H-VPLS - MPLS PW Simple access via Ethernet Fast L 3 IGP convergence Hierarchical support via Qin. Q at access MPLS TE FRR <50 msec Scalable customer VLANs (4 K x 4 K) Cons No hierarchical scalability Customer VLAN cannot over lap 4 K customer VLAN limit in Ethernet access domain Hierarchical support via MPLS PW at access 4 K customers supported per Ethernet Access Domain High STP re-convergence More complicated time provisioning MAC is not scalable as customer MAC still seen on SP network Supported on SIP-600 only as of 12. 2(33)SRA Requires MPLS to u-PE OSM/SIP-400/600 as U-PE facing card on N-PE (for 7600) High STP reconvergence time Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 47
VPLS Logical Topology Comparison Direct Attach Pros H-VPLS – Qin. Q tunnel H-VPLS - MPLS PW Simple access via Ethernet Fast L 3 IGP convergence Hierarchical support via Qin. Q at access MPLS TE FRR <50 msec Scalable customer VLANs (4 K x 4 K) Cons No hierarchical scalability Customer VLAN cannot over lap 4 K customer VLAN limit in Ethernet access domain Hierarchical support via MPLS PW at access 4 K customers supported per Ethernet Access Domain High STP re-convergence More complicated time provisioning MAC is not scalable as customer MAC still seen on SP network Supported on SIP-600 only as of 12. 2(33)SRA Requires MPLS to u-PE OSM/SIP-400/600 as U-PE facing card on N-PE (for 7600) High STP reconvergence time Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 47
 Configuration Examples Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 48
Configuration Examples Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 48
 Configuration Examples § Direct Attachment Using a Router as a CE (VLAN Based) Using a Switch as a CE (Port Based) § H-VPLS Ethernet Qin. Q Eo. MPLS Pseudo Wire (VLAN Based) Eo. MPLS Pseudo Wire (Port Based) § Sample Output Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 49
Configuration Examples § Direct Attachment Using a Router as a CE (VLAN Based) Using a Switch as a CE (Port Based) § H-VPLS Ethernet Qin. Q Eo. MPLS Pseudo Wire (VLAN Based) Eo. MPLS Pseudo Wire (Port Based) § Sample Output Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 49
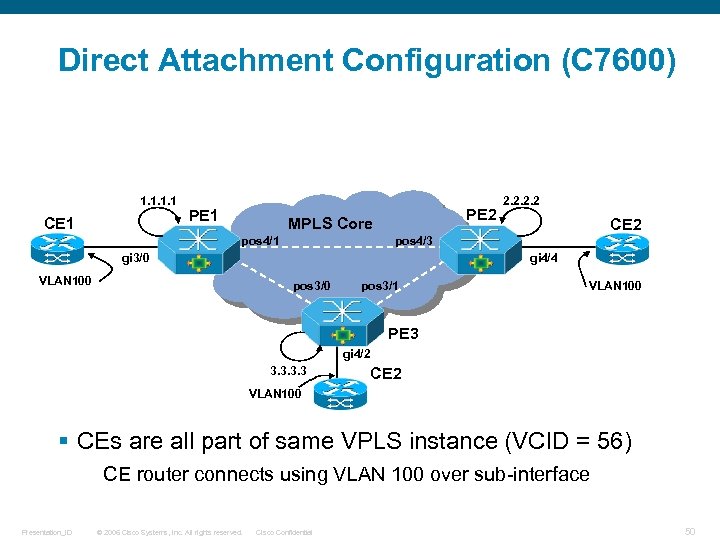 Direct Attachment Configuration (C 7600) 1. 1 CE 1 PE 2 MPLS Core pos 4/1 CE 2 pos 4/3 gi 3/0 VLAN 100 2. 2 gi 4/4 pos 3/0 pos 3/1 VLAN 100 PE 3 gi 4/2 3. 3 CE 2 VLAN 100 § CEs are all part of same VPLS instance (VCID = 56) CE router connects using VLAN 100 over sub-interface Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 50
Direct Attachment Configuration (C 7600) 1. 1 CE 1 PE 2 MPLS Core pos 4/1 CE 2 pos 4/3 gi 3/0 VLAN 100 2. 2 gi 4/4 pos 3/0 pos 3/1 VLAN 100 PE 3 gi 4/2 3. 3 CE 2 VLAN 100 § CEs are all part of same VPLS instance (VCID = 56) CE router connects using VLAN 100 over sub-interface Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 50
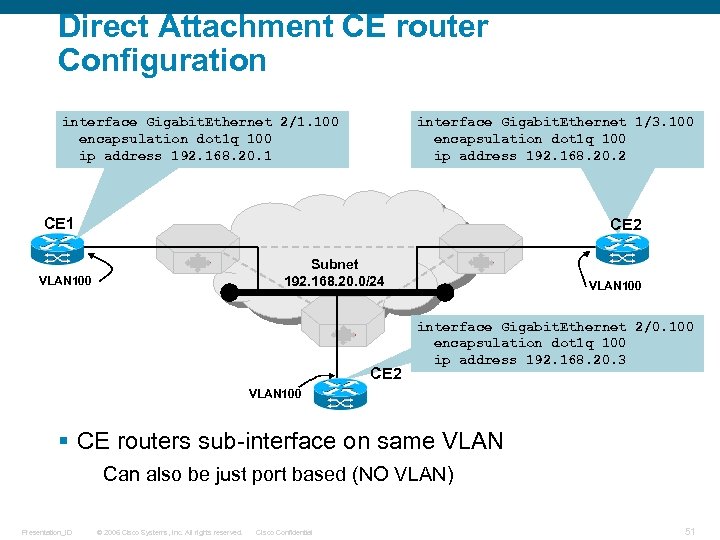 Direct Attachment CE router Configuration interface Gigabit. Ethernet 2/1. 100 encapsulation dot 1 q 100 ip address 192. 168. 20. 1 interface Gigabit. Ethernet 1/3. 100 encapsulation dot 1 q 100 ip address 192. 168. 20. 2 CE 1 CE 2 Subnet 192. 168. 20. 0/24 VLAN 100 CE 2 VLAN 100 interface Gigabit. Ethernet 2/0. 100 encapsulation dot 1 q 100 ip address 192. 168. 20. 3 VLAN 100 § CE routers sub-interface on same VLAN Can also be just port based (NO VLAN) Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 51
Direct Attachment CE router Configuration interface Gigabit. Ethernet 2/1. 100 encapsulation dot 1 q 100 ip address 192. 168. 20. 1 interface Gigabit. Ethernet 1/3. 100 encapsulation dot 1 q 100 ip address 192. 168. 20. 2 CE 1 CE 2 Subnet 192. 168. 20. 0/24 VLAN 100 CE 2 VLAN 100 interface Gigabit. Ethernet 2/0. 100 encapsulation dot 1 q 100 ip address 192. 168. 20. 3 VLAN 100 § CE routers sub-interface on same VLAN Can also be just port based (NO VLAN) Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 51
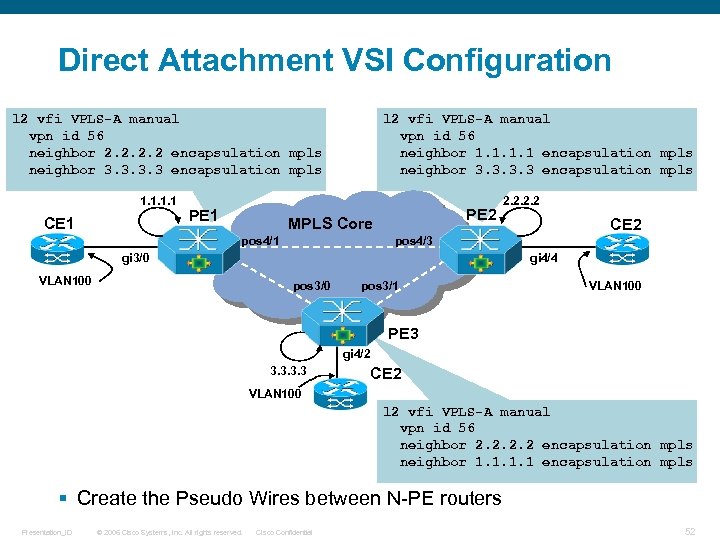 Direct Attachment VSI Configuration l 2 vfi VPLS-A manual vpn id 56 neighbor 2. 2 encapsulation mpls neighbor 3. 3 encapsulation mpls 1. 1 CE 1 PE 1 l 2 vfi VPLS-A manual vpn id 56 neighbor 1. 1 encapsulation mpls neighbor 3. 3 encapsulation mpls PE 2 MPLS Core pos 4/1 CE 2 pos 4/3 gi 3/0 VLAN 100 2. 2 gi 4/4 pos 3/0 pos 3/1 VLAN 100 PE 3 gi 4/2 3. 3 CE 2 VLAN 100 l 2 vfi VPLS-A manual vpn id 56 neighbor 2. 2 encapsulation mpls neighbor 1. 1 encapsulation mpls § Create the Pseudo Wires between N-PE routers Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 52
Direct Attachment VSI Configuration l 2 vfi VPLS-A manual vpn id 56 neighbor 2. 2 encapsulation mpls neighbor 3. 3 encapsulation mpls 1. 1 CE 1 PE 1 l 2 vfi VPLS-A manual vpn id 56 neighbor 1. 1 encapsulation mpls neighbor 3. 3 encapsulation mpls PE 2 MPLS Core pos 4/1 CE 2 pos 4/3 gi 3/0 VLAN 100 2. 2 gi 4/4 pos 3/0 pos 3/1 VLAN 100 PE 3 gi 4/2 3. 3 CE 2 VLAN 100 l 2 vfi VPLS-A manual vpn id 56 neighbor 2. 2 encapsulation mpls neighbor 1. 1 encapsulation mpls § Create the Pseudo Wires between N-PE routers Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 52
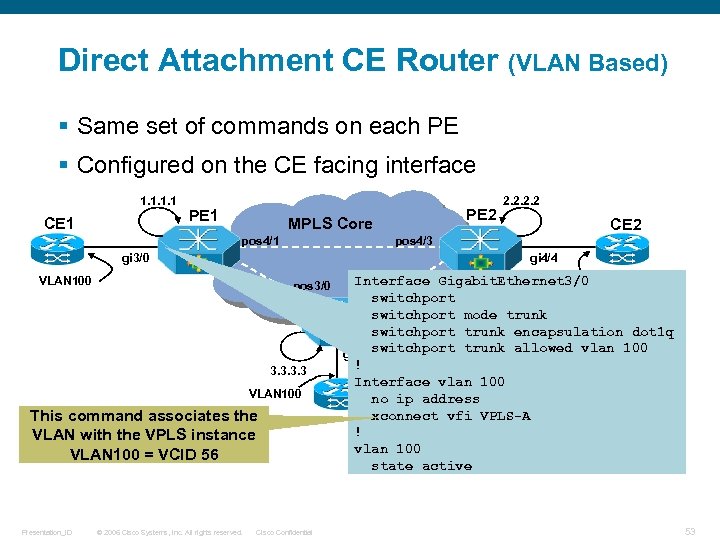 Direct Attachment CE Router (VLAN Based) § Same set of commands on each PE § Configured on the CE facing interface 1. 1 CE 1 PE 1 pos 4/1 gi 4/4 VLAN 100 pos 3/0 3. 3 VLAN 100 This command associates the VLAN with the VPLS instance VLAN 100 = VCID 56 © 2006 Cisco Systems, Inc. All rights reserved. CE 2 pos 4/3 gi 3/0 Presentation_ID PE 2 MPLS Core 2. 2 Cisco Confidential Interface Gigabit. Ethernet 3/0 VLAN 100 pos 3/1 switchport mode trunk switchport trunk encapsulation dot 1 q PE 3 gi 4/2 switchport trunk allowed vlan 100 ! CE 2 Interface vlan 100 no ip address xconnect vfi VPLS-A ! vlan 100 state active 53
Direct Attachment CE Router (VLAN Based) § Same set of commands on each PE § Configured on the CE facing interface 1. 1 CE 1 PE 1 pos 4/1 gi 4/4 VLAN 100 pos 3/0 3. 3 VLAN 100 This command associates the VLAN with the VPLS instance VLAN 100 = VCID 56 © 2006 Cisco Systems, Inc. All rights reserved. CE 2 pos 4/3 gi 3/0 Presentation_ID PE 2 MPLS Core 2. 2 Cisco Confidential Interface Gigabit. Ethernet 3/0 VLAN 100 pos 3/1 switchport mode trunk switchport trunk encapsulation dot 1 q PE 3 gi 4/2 switchport trunk allowed vlan 100 ! CE 2 Interface vlan 100 no ip address xconnect vfi VPLS-A ! vlan 100 state active 53
 Configuration Examples § Direct Attachment Using a Router as a CE (VLAN Based) Using a Switch as a CE (Port Based) § H-VPLS Ethernet Qin. Q Eo. MPLS Pseudo Wire (VLAN Based) Eo. MPLS Pseudo Wire (Port Based) § Sample Output Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 54
Configuration Examples § Direct Attachment Using a Router as a CE (VLAN Based) Using a Switch as a CE (Port Based) § H-VPLS Ethernet Qin. Q Eo. MPLS Pseudo Wire (VLAN Based) Eo. MPLS Pseudo Wire (Port Based) § Sample Output Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 54
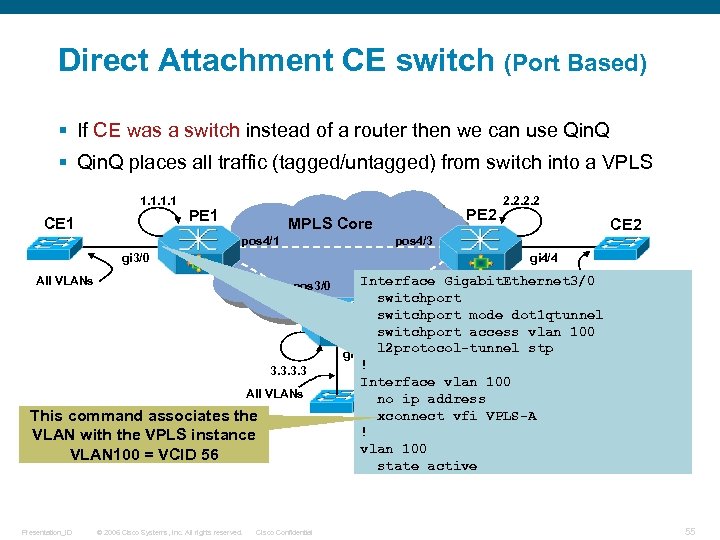 Direct Attachment CE switch (Port Based) § If CE was a switch instead of a router then we can use Qin. Q § Qin. Q places all traffic (tagged/untagged) from switch into a VPLS 1. 1 CE 1 PE 1 pos 4/1 gi 4/4 All VLANs pos 3/0 3. 3 All VLANs This command associates the VLAN with the VPLS instance VLAN 100 = VCID 56 © 2006 Cisco Systems, Inc. All rights reserved. CE 2 pos 4/3 gi 3/0 Presentation_ID PE 2 MPLS Core 2. 2 Cisco Confidential Interface Gigabit. Ethernet 3/0 VLANs pos 3/1 All switchport mode dot 1 qtunnel switchport access vlan 100 PE 3 gi 4/2 l 2 protocol-tunnel stp ! CE 2 Interface vlan 100 no ip address xconnect vfi VPLS-A ! vlan 100 state active 55
Direct Attachment CE switch (Port Based) § If CE was a switch instead of a router then we can use Qin. Q § Qin. Q places all traffic (tagged/untagged) from switch into a VPLS 1. 1 CE 1 PE 1 pos 4/1 gi 4/4 All VLANs pos 3/0 3. 3 All VLANs This command associates the VLAN with the VPLS instance VLAN 100 = VCID 56 © 2006 Cisco Systems, Inc. All rights reserved. CE 2 pos 4/3 gi 3/0 Presentation_ID PE 2 MPLS Core 2. 2 Cisco Confidential Interface Gigabit. Ethernet 3/0 VLANs pos 3/1 All switchport mode dot 1 qtunnel switchport access vlan 100 PE 3 gi 4/2 l 2 protocol-tunnel stp ! CE 2 Interface vlan 100 no ip address xconnect vfi VPLS-A ! vlan 100 state active 55
 Configuration Examples § Direct Attachment Using a Router as a CE (VLAN Based) Using a Switch as a CE (Port Based) § H-VPLS Ethernet Qin. Q Eo. MPLS Pseudo Wire (VLAN Based) Eo. MPLS Pseudo Wire (Port Based) § Sample Output Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 56
Configuration Examples § Direct Attachment Using a Router as a CE (VLAN Based) Using a Switch as a CE (Port Based) § H-VPLS Ethernet Qin. Q Eo. MPLS Pseudo Wire (VLAN Based) Eo. MPLS Pseudo Wire (Port Based) § Sample Output Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 56
 H-VPLS Configuration (C 7600/3750 ME) U-PE 1 1. 1 Cisco 3750 ME 2. 2 MPLS Core pos 4/1 Cisco 3750 ME pos 4/3 gi 3/0 gi 4/4 gi 1/1/1 pos 3/0 N-PE 1 CE 1 U-PE 2 pos 3/1 CE 1 gi 4/2 CE 2 U-PE 3 CE 1 fa 1/0/1 N-PE 2 N-PE 3 3. 3 CE 2 4. 4 Cisco 3750 ME § U-PEs provide services to customer edge device CE traffic then carried in Qin. Q or Eo. MPLS PW to N-PE PW VSI mesh configuration is same as previous examples Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 57
H-VPLS Configuration (C 7600/3750 ME) U-PE 1 1. 1 Cisco 3750 ME 2. 2 MPLS Core pos 4/1 Cisco 3750 ME pos 4/3 gi 3/0 gi 4/4 gi 1/1/1 pos 3/0 N-PE 1 CE 1 U-PE 2 pos 3/1 CE 1 gi 4/2 CE 2 U-PE 3 CE 1 fa 1/0/1 N-PE 2 N-PE 3 3. 3 CE 2 4. 4 Cisco 3750 ME § U-PEs provide services to customer edge device CE traffic then carried in Qin. Q or Eo. MPLS PW to N-PE PW VSI mesh configuration is same as previous examples Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 57
 Configuration Examples § Direct Attachment Using a Router as a CE (VLAN Based) Using a Switch as a CE (Port Based) § H-VPLS Ethernet Qin. Q Eo. MPLS Pseudo Wire (VLAN Based) Eo. MPLS Pseudo Wire (Port Based) § Sample Output Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 58
Configuration Examples § Direct Attachment Using a Router as a CE (VLAN Based) Using a Switch as a CE (Port Based) § H-VPLS Ethernet Qin. Q Eo. MPLS Pseudo Wire (VLAN Based) Eo. MPLS Pseudo Wire (Port Based) § Sample Output Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 58
 H-VPLS Qin. Q Tunnel (Ethernet Edge) § U-PE carries all traffic from CE using Qin. Q Outer tag is VLAN 100, inner tags are customer’s U-PE 1 Cisco 3750 ME 1. 1 2. 2 MPLS Core pos 4/1 pos 4/3 U-PE 2 Cisco 3750 ME 4. 4 fa 1/0/1 gi 3/0 gi 4/4 gi 1/1/1 Interface Gigabit. Ethernet 4/4 switchport pos 3/0 pos 3/1 N-PE 2 switchport mode trunk switchport trunk encapsulation dot 1 q CE 1 switchport trunk allowed vlan 100 N-PE 3 3. 3 CE 1 CE 2 ! interface Fast. Ethernet 1/0/1 gi 4/2 Interface vlan 100 switchport CE 2 no ip address switchport access vlan 100 U-PE 3 xconnect vfi VPLS-A switchport mode dot 1 q-tunnel Cisco 3750 ME CE 1 ! switchport trunk allow vlan 1 -1005 vlan 100 ! state active interface Gigabit. Ethernet 1/1/1 switchport mode trunk switchport allow vlan 1 -1005 Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 59
H-VPLS Qin. Q Tunnel (Ethernet Edge) § U-PE carries all traffic from CE using Qin. Q Outer tag is VLAN 100, inner tags are customer’s U-PE 1 Cisco 3750 ME 1. 1 2. 2 MPLS Core pos 4/1 pos 4/3 U-PE 2 Cisco 3750 ME 4. 4 fa 1/0/1 gi 3/0 gi 4/4 gi 1/1/1 Interface Gigabit. Ethernet 4/4 switchport pos 3/0 pos 3/1 N-PE 2 switchport mode trunk switchport trunk encapsulation dot 1 q CE 1 switchport trunk allowed vlan 100 N-PE 3 3. 3 CE 1 CE 2 ! interface Fast. Ethernet 1/0/1 gi 4/2 Interface vlan 100 switchport CE 2 no ip address switchport access vlan 100 U-PE 3 xconnect vfi VPLS-A switchport mode dot 1 q-tunnel Cisco 3750 ME CE 1 ! switchport trunk allow vlan 1 -1005 vlan 100 ! state active interface Gigabit. Ethernet 1/1/1 switchport mode trunk switchport allow vlan 1 -1005 Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 59
 Configuration Examples § Direct Attachment Using a Router as a CE (VLAN Based) Using a Switch as a CE (Port Based) § H-VPLS Ethernet Qin. Q Eo. MPLS Pseudo Wire (VLAN Based) Eo. MPLS Pseudo Wire (Port Based) § Sample Output Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 60
Configuration Examples § Direct Attachment Using a Router as a CE (VLAN Based) Using a Switch as a CE (Port Based) § H-VPLS Ethernet Qin. Q Eo. MPLS Pseudo Wire (VLAN Based) Eo. MPLS Pseudo Wire (Port Based) § Sample Output Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 60
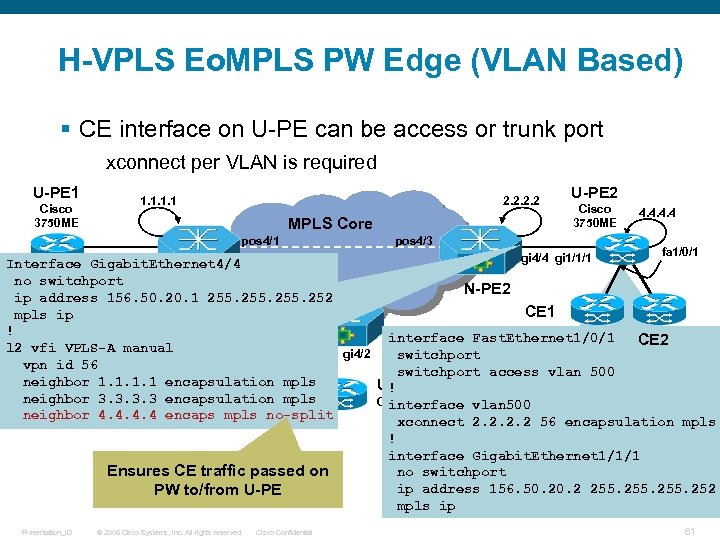 H-VPLS Eo. MPLS PW Edge (VLAN Based) § CE interface on U-PE can be access or trunk port xconnect per VLAN is required U-PE 1 Cisco 3750 ME 1. 1 2. 2 MPLS Core pos 4/1 pos 4/3 U-PE 2 Cisco 3750 ME 4. 4 fa 1/0/1 gi 3/0 gi 4/4 gi 1/1/1 Interface Gigabit. Ethernet 4/4 no switchport pos 3/0 pos 3/1 N-PE 2 ip address 156. 50. 20. 1 255. 252 CE 1 mpls ip ! N-PE 3 3. 3 interface Fast. Ethernet 1/0/1 CE 2 manual CE 2 l 2 vfi VPLS-A gi 4/2 switchport vpn id 56 switchport access vlan 500 CE 2 neighbor 1. 1 encapsulation mpls U-PE 3 ! neighbor 3. 3 encapsulation mpls Cisco 3750 ME vlan 500 interface CE 1 neighbor 4. 4 encaps mpls no-split xconnect 2. 2 56 encapsulation mpls ! interface Gigabit. Ethernet 1/1/1 Ensures CE traffic passed on no switchport ip address 156. 50. 2 255. 252 PW to/from U-PE mpls ip Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 61
H-VPLS Eo. MPLS PW Edge (VLAN Based) § CE interface on U-PE can be access or trunk port xconnect per VLAN is required U-PE 1 Cisco 3750 ME 1. 1 2. 2 MPLS Core pos 4/1 pos 4/3 U-PE 2 Cisco 3750 ME 4. 4 fa 1/0/1 gi 3/0 gi 4/4 gi 1/1/1 Interface Gigabit. Ethernet 4/4 no switchport pos 3/0 pos 3/1 N-PE 2 ip address 156. 50. 20. 1 255. 252 CE 1 mpls ip ! N-PE 3 3. 3 interface Fast. Ethernet 1/0/1 CE 2 manual CE 2 l 2 vfi VPLS-A gi 4/2 switchport vpn id 56 switchport access vlan 500 CE 2 neighbor 1. 1 encapsulation mpls U-PE 3 ! neighbor 3. 3 encapsulation mpls Cisco 3750 ME vlan 500 interface CE 1 neighbor 4. 4 encaps mpls no-split xconnect 2. 2 56 encapsulation mpls ! interface Gigabit. Ethernet 1/1/1 Ensures CE traffic passed on no switchport ip address 156. 50. 2 255. 252 PW to/from U-PE mpls ip Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 61
 Configuration Examples § Direct Attachment Using a Router as a CE (VLAN Based) Using a Switch as a CE (Port Based) § H-VPLS Ethernet Qin. Q Eo. MPLS Pseudo Wire (VLAN Based) Eo. MPLS Pseudo Wire (Port Based) § Sample Output Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 62
Configuration Examples § Direct Attachment Using a Router as a CE (VLAN Based) Using a Switch as a CE (Port Based) § H-VPLS Ethernet Qin. Q Eo. MPLS Pseudo Wire (VLAN Based) Eo. MPLS Pseudo Wire (Port Based) § Sample Output Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 62
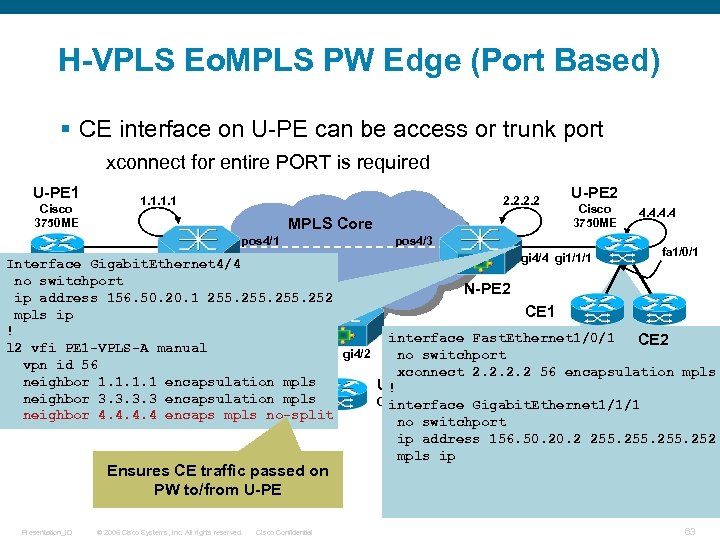 H-VPLS Eo. MPLS PW Edge (Port Based) § CE interface on U-PE can be access or trunk port xconnect for entire PORT is required U-PE 1 Cisco 3750 ME 1. 1 2. 2 MPLS Core pos 4/1 pos 4/3 U-PE 2 Cisco 3750 ME 4. 4 fa 1/0/1 gi 3/0 gi 4/4 gi 1/1/1 Interface Gigabit. Ethernet 4/4 no switchport pos 3/0 pos 3/1 N-PE 2 ip address 156. 50. 20. 1 255. 252 CE 1 mpls ip ! N-PE 3 3. 3 interface Fast. Ethernet 1/0/1 CE 2 l 2 vfi PE 1 -VPLS-A manual gi 4/2 no switchport vpn id 56 xconnect 2. 2 56 encapsulation mpls CE 2 neighbor 1. 1 encapsulation mpls U-PE 3 ! neighbor 3. 3 encapsulation mpls Cisco 3750 ME Gigabit. Ethernet 1/1/1 interface CE 1 neighbor 4. 4 encaps mpls no-split no switchport ip address 156. 50. 2 255. 252 mpls ip Ensures CE traffic passed on PW to/from U-PE Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 63
H-VPLS Eo. MPLS PW Edge (Port Based) § CE interface on U-PE can be access or trunk port xconnect for entire PORT is required U-PE 1 Cisco 3750 ME 1. 1 2. 2 MPLS Core pos 4/1 pos 4/3 U-PE 2 Cisco 3750 ME 4. 4 fa 1/0/1 gi 3/0 gi 4/4 gi 1/1/1 Interface Gigabit. Ethernet 4/4 no switchport pos 3/0 pos 3/1 N-PE 2 ip address 156. 50. 20. 1 255. 252 CE 1 mpls ip ! N-PE 3 3. 3 interface Fast. Ethernet 1/0/1 CE 2 l 2 vfi PE 1 -VPLS-A manual gi 4/2 no switchport vpn id 56 xconnect 2. 2 56 encapsulation mpls CE 2 neighbor 1. 1 encapsulation mpls U-PE 3 ! neighbor 3. 3 encapsulation mpls Cisco 3750 ME Gigabit. Ethernet 1/1/1 interface CE 1 neighbor 4. 4 encaps mpls no-split no switchport ip address 156. 50. 2 255. 252 mpls ip Ensures CE traffic passed on PW to/from U-PE Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 63
 Configuration Examples § Direct Attachment Using a Router as a CE (VLAN Based) Using a Switch as a CE (Port Based) § H-VPLS Ethernet Qin. Q Eo. MPLS Pseudo Wire (VLAN Based) Eo. MPLS Pseudo Wire (Port Based) § Sample Output Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 64
Configuration Examples § Direct Attachment Using a Router as a CE (VLAN Based) Using a Switch as a CE (Port Based) § H-VPLS Ethernet Qin. Q Eo. MPLS Pseudo Wire (VLAN Based) Eo. MPLS Pseudo Wire (Port Based) § Sample Output Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 64
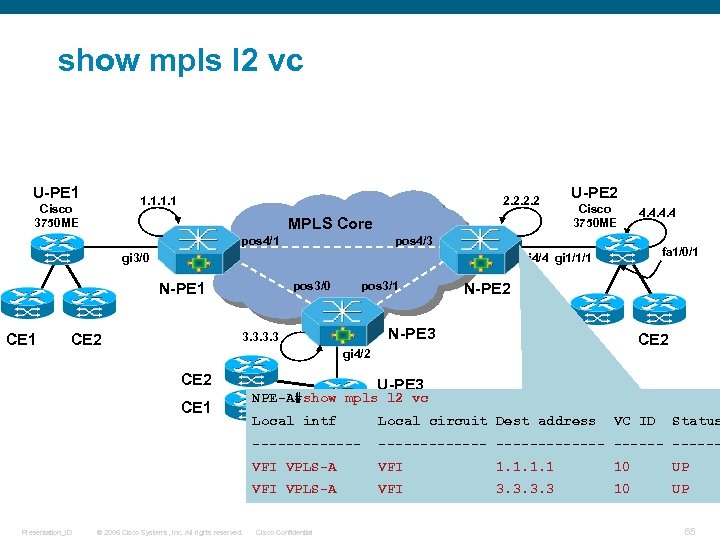 show mpls l 2 vc U-PE 1 1. 1 Cisco 3750 ME 2. 2 MPLS Core pos 4/1 U-PE 2 Cisco 3750 ME 4. 4 pos 4/3 gi 3/0 fa 1/0/1 gi 4/4 gi 1/1/1 pos 3/0 N-PE 1 pos 3/1 N-PE 2 CE 1 N-PE 3 3. 3 CE 2 gi 4/2 CE 1 U-PE 3 NPE-A#show mpls. Cisco vc l 2 3750 ME ------------- VFI VPLS-A VFI 1. 1 10 UP VFI VPLS-A © 2006 Cisco Systems, Inc. All rights reserved. Local circuit Dest address ------- Presentation_ID Local intf VFI 3. 3 10 UP Cisco Confidential VC ID Status 65
show mpls l 2 vc U-PE 1 1. 1 Cisco 3750 ME 2. 2 MPLS Core pos 4/1 U-PE 2 Cisco 3750 ME 4. 4 pos 4/3 gi 3/0 fa 1/0/1 gi 4/4 gi 1/1/1 pos 3/0 N-PE 1 pos 3/1 N-PE 2 CE 1 N-PE 3 3. 3 CE 2 gi 4/2 CE 1 U-PE 3 NPE-A#show mpls. Cisco vc l 2 3750 ME ------------- VFI VPLS-A VFI 1. 1 10 UP VFI VPLS-A © 2006 Cisco Systems, Inc. All rights reserved. Local circuit Dest address ------- Presentation_ID Local intf VFI 3. 3 10 UP Cisco Confidential VC ID Status 65
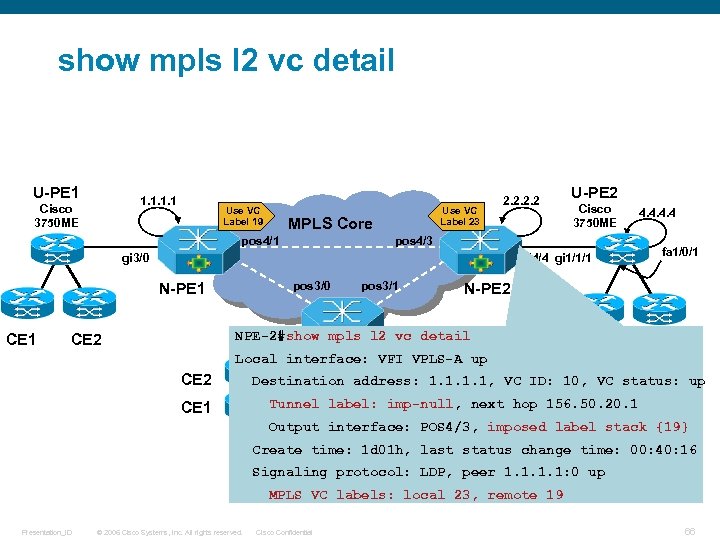 show mpls l 2 vc detail U-PE 1 1. 1 Cisco 3750 ME Use VC Label 19 Use VC Label 23 MPLS Core pos 4/1 2. 2 U-PE 2 Cisco 3750 ME 4. 4 pos 4/3 gi 3/0 fa 1/0/1 gi 4/4 gi 1/1/1 pos 3/0 N-PE 1 pos 3/1 N-PE 2 CE 1 NPE-2#show mpls l 2 N-PE 3 vc detail 3. 3 CE 2 gi 4/2 Local interface: VFI VPLS-A up CE 2 CE 1 CE 2 Destination address: 1. 1, VC ID: 10, VC status: up U-PE 3 Tunnel label: Cisco 3750 ME next hop 156. 50. 20. 1 imp-null, Output interface: POS 4/3, imposed label stack {19} Create time: 1 d 01 h, last status change time: 00: 40: 16 Signaling protocol: LDP, peer 1. 1: 0 up MPLS VC labels: local 23, remote 19 Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 66
show mpls l 2 vc detail U-PE 1 1. 1 Cisco 3750 ME Use VC Label 19 Use VC Label 23 MPLS Core pos 4/1 2. 2 U-PE 2 Cisco 3750 ME 4. 4 pos 4/3 gi 3/0 fa 1/0/1 gi 4/4 gi 1/1/1 pos 3/0 N-PE 1 pos 3/1 N-PE 2 CE 1 NPE-2#show mpls l 2 N-PE 3 vc detail 3. 3 CE 2 gi 4/2 Local interface: VFI VPLS-A up CE 2 CE 1 CE 2 Destination address: 1. 1, VC ID: 10, VC status: up U-PE 3 Tunnel label: Cisco 3750 ME next hop 156. 50. 20. 1 imp-null, Output interface: POS 4/3, imposed label stack {19} Create time: 1 d 01 h, last status change time: 00: 40: 16 Signaling protocol: LDP, peer 1. 1: 0 up MPLS VC labels: local 23, remote 19 Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 66
 Deployment Issues Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 67
Deployment Issues Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 67
 Deployment Issues § MTU Size § Broadcast Handling § Router or a Switch CPE? § Ramblings of an Engineer § A Sample Problem Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 68
Deployment Issues § MTU Size § Broadcast Handling § Router or a Switch CPE? § Ramblings of an Engineer § A Sample Problem Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 68
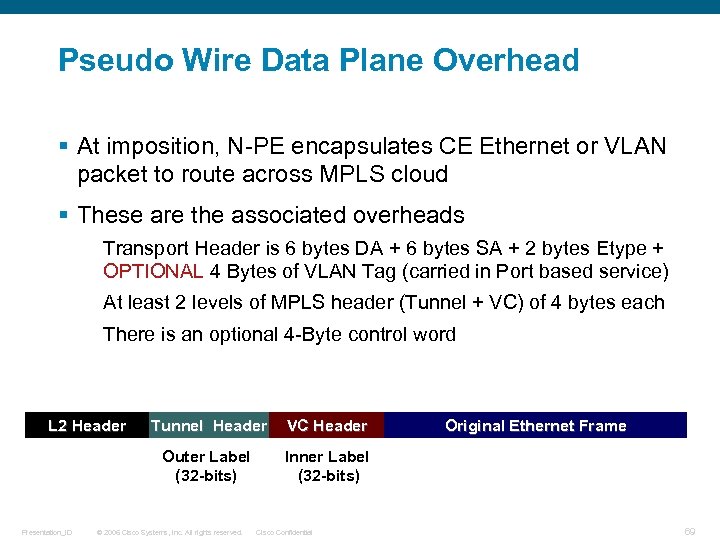 Pseudo Wire Data Plane Overhead § At imposition, N-PE encapsulates CE Ethernet or VLAN packet to route across MPLS cloud § These are the associated overheads Transport Header is 6 bytes DA + 6 bytes SA + 2 bytes Etype + OPTIONAL 4 Bytes of VLAN Tag (carried in Port based service) At least 2 levels of MPLS header (Tunnel + VC) of 4 bytes each There is an optional 4 -Byte control word L 2 Header VC Header Outer Label (32 -bits) Presentation_ID Tunnel Header Inner Label (32 -bits) © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential Original Ethernet Frame 69
Pseudo Wire Data Plane Overhead § At imposition, N-PE encapsulates CE Ethernet or VLAN packet to route across MPLS cloud § These are the associated overheads Transport Header is 6 bytes DA + 6 bytes SA + 2 bytes Etype + OPTIONAL 4 Bytes of VLAN Tag (carried in Port based service) At least 2 levels of MPLS header (Tunnel + VC) of 4 bytes each There is an optional 4 -Byte control word L 2 Header VC Header Outer Label (32 -bits) Presentation_ID Tunnel Header Inner Label (32 -bits) © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential Original Ethernet Frame 69
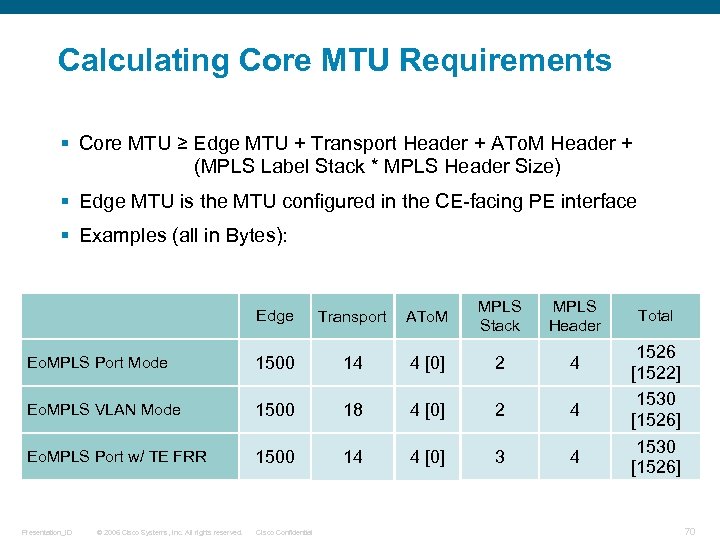 Calculating Core MTU Requirements § Core MTU ≥ Edge MTU + Transport Header + ATo. M Header + (MPLS Label Stack * MPLS Header Size) § Edge MTU is the MTU configured in the CE-facing PE interface § Examples (all in Bytes): Edge Transport ATo. M MPLS Stack MPLS Header Eo. MPLS Port Mode 1500 14 4 [0] 2 4 Eo. MPLS VLAN Mode 1500 18 4 [0] 2 4 Eo. MPLS Port w/ TE FRR 1500 14 4 [0] 3 4 Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential Total 1526 [1522] 1530 [1526] 70
Calculating Core MTU Requirements § Core MTU ≥ Edge MTU + Transport Header + ATo. M Header + (MPLS Label Stack * MPLS Header Size) § Edge MTU is the MTU configured in the CE-facing PE interface § Examples (all in Bytes): Edge Transport ATo. M MPLS Stack MPLS Header Eo. MPLS Port Mode 1500 14 4 [0] 2 4 Eo. MPLS VLAN Mode 1500 18 4 [0] 2 4 Eo. MPLS Port w/ TE FRR 1500 14 4 [0] 3 4 Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential Total 1526 [1522] 1530 [1526] 70
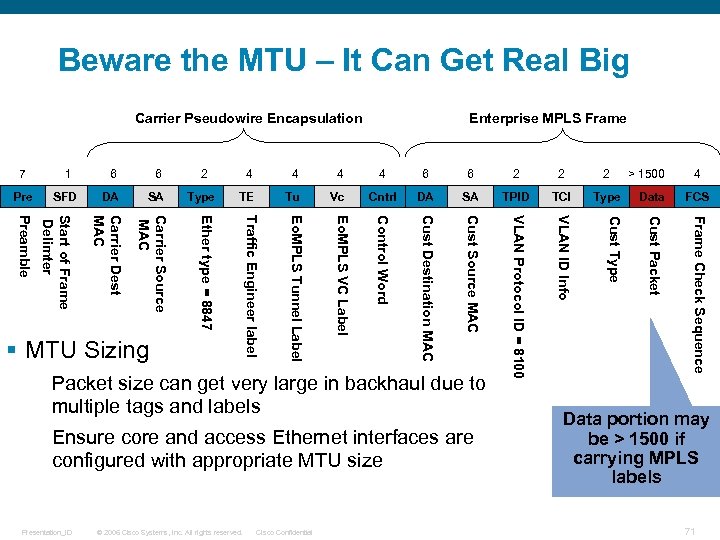 Beware the MTU – It Can Get Real Big Carrier Pseudowire Encapsulation Enterprise MPLS Frame 4 4 6 6 2 2 2 Pre SFD DA SA Type TE Tu Vc Cntrl DA SA TPID TCI Type Data Carrier Dest MAC Carrier Source MAC Control Word Cust Destination MAC Cust Source MAC VLAN Protocol ID = 8100 VLAN ID Info Cust Type Cust Packet § MTU Sizing Packet size can get very large in backhaul due to multiple tags and labels Ensure core and access Ethernet interfaces are configured with appropriate MTU size Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential > 1500 4 FCS Frame Check Sequence 4 Eo. MPLS VC Label 4 Eo. MPLS Tunnel Label 2 Traffic Engineer label 6 Ether type = 8847 6 Start of Frame Delimter 1 Preamble 7 Data portion may be > 1500 if carrying MPLS labels 71
Beware the MTU – It Can Get Real Big Carrier Pseudowire Encapsulation Enterprise MPLS Frame 4 4 6 6 2 2 2 Pre SFD DA SA Type TE Tu Vc Cntrl DA SA TPID TCI Type Data Carrier Dest MAC Carrier Source MAC Control Word Cust Destination MAC Cust Source MAC VLAN Protocol ID = 8100 VLAN ID Info Cust Type Cust Packet § MTU Sizing Packet size can get very large in backhaul due to multiple tags and labels Ensure core and access Ethernet interfaces are configured with appropriate MTU size Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential > 1500 4 FCS Frame Check Sequence 4 Eo. MPLS VC Label 4 Eo. MPLS Tunnel Label 2 Traffic Engineer label 6 Ether type = 8847 6 Start of Frame Delimter 1 Preamble 7 Data portion may be > 1500 if carrying MPLS labels 71
 Broadcast/Multicast/Unknown Unicast Handling § VPLS relies on ingress replication Ingress PE replicates the multicast packet to each egress Pseudo Wire (PE neighbour) § Ethernet switches replicate broadcast/multicast flows once per output interface VPLS may duplicate packets over the same physical egress interface – for each PW that interface carriers Unnecessary replication brings the risk of resource exhaustion when the number of PWs increases § Some discussion on maybe using multicast for PWs Rather than full mesh of P 2 P Pseudo Wires Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 72
Broadcast/Multicast/Unknown Unicast Handling § VPLS relies on ingress replication Ingress PE replicates the multicast packet to each egress Pseudo Wire (PE neighbour) § Ethernet switches replicate broadcast/multicast flows once per output interface VPLS may duplicate packets over the same physical egress interface – for each PW that interface carriers Unnecessary replication brings the risk of resource exhaustion when the number of PWs increases § Some discussion on maybe using multicast for PWs Rather than full mesh of P 2 P Pseudo Wires Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 72
 Switch or Router as CE device § Ethernet Switch as CE device If directly attached SP allocates VLAN could be an issue in customer network SP UNI exposed to L 2 network of customer L 2 PDUs must be tunnelled such as STP BPDUs No visibility of network behind CE switch Many MAC address can exists on UNI High exposure to broadcast storms § Router as CE device Single MAC Address exists (for interface of router) No SPT interactions Router controls broadcast issues (multicast still happens) Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 73
Switch or Router as CE device § Ethernet Switch as CE device If directly attached SP allocates VLAN could be an issue in customer network SP UNI exposed to L 2 network of customer L 2 PDUs must be tunnelled such as STP BPDUs No visibility of network behind CE switch Many MAC address can exists on UNI High exposure to broadcast storms § Router as CE device Single MAC Address exists (for interface of router) No SPT interactions Router controls broadcast issues (multicast still happens) Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 73
 VPLS Caveats (Ramblings of an Engineer) § VPLS may introduce non-deterministic behaviour in SP Core Case in point – learning of VPN routes An MPLS-VPN provides ordered manner to learn VPNv 4 routers using MP -BGP – unknown addresses are dropped In VPLS, learning is achieved through flooding MAC address Excessive number of Unknown, Broadcast and Multicast frames could behave as a series of “packet bombs” § Solution: Ingress Threshold Filters (on U-PE or N-PE) How to selectively choose which Ethernet Frames to discard? How to avoid dropping Routing and Keepalives (control) May cause more problems in customer network… How many MAC addresses allowed? Does SP really want to take this responsibility? Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 74
VPLS Caveats (Ramblings of an Engineer) § VPLS may introduce non-deterministic behaviour in SP Core Case in point – learning of VPN routes An MPLS-VPN provides ordered manner to learn VPNv 4 routers using MP -BGP – unknown addresses are dropped In VPLS, learning is achieved through flooding MAC address Excessive number of Unknown, Broadcast and Multicast frames could behave as a series of “packet bombs” § Solution: Ingress Threshold Filters (on U-PE or N-PE) How to selectively choose which Ethernet Frames to discard? How to avoid dropping Routing and Keepalives (control) May cause more problems in customer network… How many MAC addresses allowed? Does SP really want to take this responsibility? Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 74
 VPLS Caveats (Ramblings of an Engineer) § Do. S attack has a higher probability of manifesting Whether intentional or by mis-configuration § Since traffic is carried at layer 2, a lot of chatter could be traversing the MPLS core unnecessarily. For example, status requests for printers § How is Co. S applied across for a VPLS service? Should all frames on a VPLS interface be afforded the same class of service? Should there be some sort of differentiation? Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 75
VPLS Caveats (Ramblings of an Engineer) § Do. S attack has a higher probability of manifesting Whether intentional or by mis-configuration § Since traffic is carried at layer 2, a lot of chatter could be traversing the MPLS core unnecessarily. For example, status requests for printers § How is Co. S applied across for a VPLS service? Should all frames on a VPLS interface be afforded the same class of service? Should there be some sort of differentiation? Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 75
 A Common VPLS Problem § Protocols expect LAN behaviour § VPLS is viewed as an Ethernet network Although it does not necessarily behave like one VPLS is “virtual” in its LAN service There are some behaviours which differ from a real LAN § An example The OSPF designated router problem… Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 76
A Common VPLS Problem § Protocols expect LAN behaviour § VPLS is viewed as an Ethernet network Although it does not necessarily behave like one VPLS is “virtual” in its LAN service There are some behaviours which differ from a real LAN § An example The OSPF designated router problem… Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 76
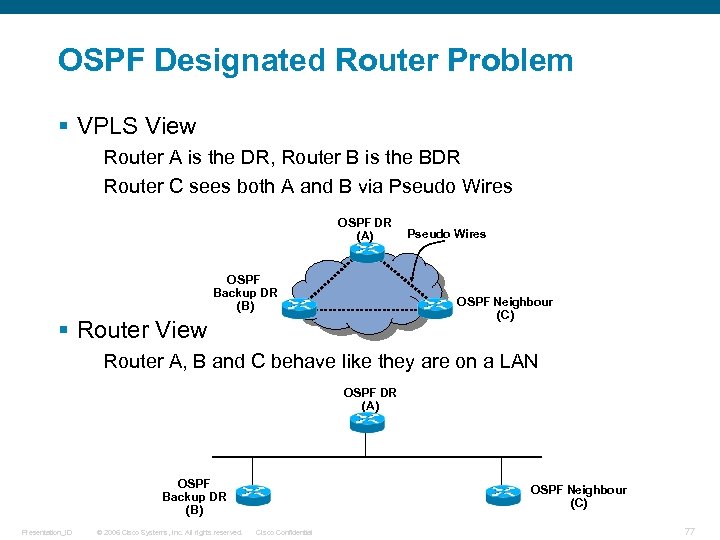 OSPF Designated Router Problem § VPLS View Router A is the DR, Router B is the BDR Router C sees both A and B via Pseudo Wires OSPF DR (A) OSPF Backup DR (B) Pseudo Wires OSPF Neighbour (C) § Router View Router A, B and C behave like they are on a LAN OSPF DR (A) OSPF Backup DR (B) Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. OSPF Neighbour (C) Cisco Confidential 77
OSPF Designated Router Problem § VPLS View Router A is the DR, Router B is the BDR Router C sees both A and B via Pseudo Wires OSPF DR (A) OSPF Backup DR (B) Pseudo Wires OSPF Neighbour (C) § Router View Router A, B and C behave like they are on a LAN OSPF DR (A) OSPF Backup DR (B) Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. OSPF Neighbour (C) Cisco Confidential 77
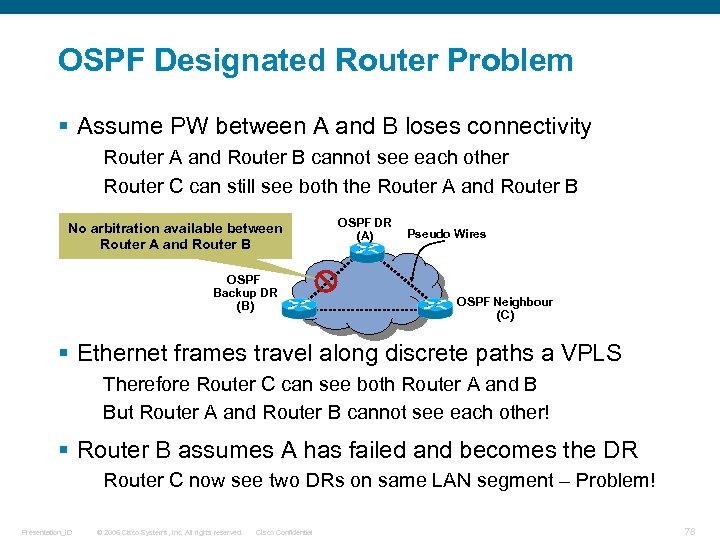 OSPF Designated Router Problem § Assume PW between A and B loses connectivity Router A and Router B cannot see each other Router C can still see both the Router A and Router B No arbitration available between Router A and Router B OSPF Backup DR (B) OSPF DR (A) Pseudo Wires OSPF Neighbour (C) § Ethernet frames travel along discrete paths a VPLS Therefore Router C can see both Router A and B But Router A and Router B cannot see each other! § Router B assumes A has failed and becomes the DR Router C now see two DRs on same LAN segment – Problem! Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 78
OSPF Designated Router Problem § Assume PW between A and B loses connectivity Router A and Router B cannot see each other Router C can still see both the Router A and Router B No arbitration available between Router A and Router B OSPF Backup DR (B) OSPF DR (A) Pseudo Wires OSPF Neighbour (C) § Ethernet frames travel along discrete paths a VPLS Therefore Router C can see both Router A and B But Router A and Router B cannot see each other! § Router B assumes A has failed and becomes the DR Router C now see two DRs on same LAN segment – Problem! Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 78
 Summary Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 79
Summary Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 79
 Summary § VPLS has its advantages and benefits Non-IP protocols supported, customers do not have routing interaction etc. . § Use routers as the CE device Understand their multicast requirements Then again, maybe MPLS-VPN could do the job? § Avoid switches as CPE Otherwise understand customer’s network requirements Devices, applications (broadcast/multicast vs unicast) Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 80
Summary § VPLS has its advantages and benefits Non-IP protocols supported, customers do not have routing interaction etc. . § Use routers as the CE device Understand their multicast requirements Then again, maybe MPLS-VPN could do the job? § Avoid switches as CPE Otherwise understand customer’s network requirements Devices, applications (broadcast/multicast vs unicast) Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 80
 Q&A Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 81
Q&A Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 81
 Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 82
Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 82


