dea534a03e4897486d6ca6a4864434f1.ppt
- Количество слайдов: 44
 An Introduction to SSL/TLS and Certificates Providing secure communication over the Internet Frederick J. Hirsch fjh@fjhirsch. com
An Introduction to SSL/TLS and Certificates Providing secure communication over the Internet Frederick J. Hirsch fjh@fjhirsch. com
 Cert. Co Overview • Background Established in 1996. Banker’s Trust spinoff. Privately held. • Mission Cert. Co provides secure and cost-effective business solutions that enable trust institutions to build a worldwide trust infrastructure to support high-value, secure electronic commerce. • Expertise Cryptography, risk management, law, technology and banking. • Location Headquarters: New York City Regional Offices: Cambridge (MA), Washington, DC, United Kingdom. 2
Cert. Co Overview • Background Established in 1996. Banker’s Trust spinoff. Privately held. • Mission Cert. Co provides secure and cost-effective business solutions that enable trust institutions to build a worldwide trust infrastructure to support high-value, secure electronic commerce. • Expertise Cryptography, risk management, law, technology and banking. • Location Headquarters: New York City Regional Offices: Cambridge (MA), Washington, DC, United Kingdom. 2
 Outline • Problem: Creating applications which can communicate securely over the Internet • TLS: Transport Layer Security (SSL) • Certificates • Related technology: S-HTTP, IPSec, SET, SASL • References 3
Outline • Problem: Creating applications which can communicate securely over the Internet • TLS: Transport Layer Security (SSL) • Certificates • Related technology: S-HTTP, IPSec, SET, SASL • References 3
 Security Issues • Privacy – Anyone can see content • Integrity – Someone might alter content • Authentication – Not clear who you are talking with 4
Security Issues • Privacy – Anyone can see content • Integrity – Someone might alter content • Authentication – Not clear who you are talking with 4
 TLS: Transport Layer Security • formerly known as SSL: Secure Sockets Layer • Addresses issues of privacy, integrity and authentication – What is it? – How does it address the issues? – How is it used 5
TLS: Transport Layer Security • formerly known as SSL: Secure Sockets Layer • Addresses issues of privacy, integrity and authentication – What is it? – How does it address the issues? – How is it used 5
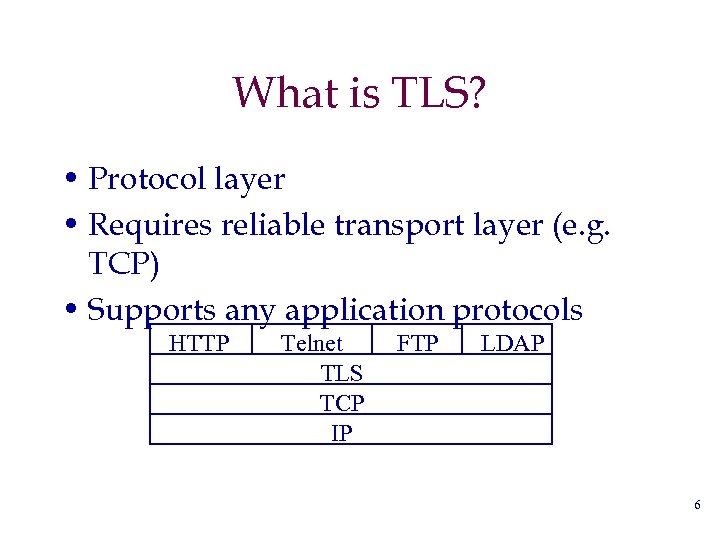 What is TLS? • Protocol layer • Requires reliable transport layer (e. g. TCP) • Supports any application protocols HTTP Telnet TLS TCP IP FTP LDAP 6
What is TLS? • Protocol layer • Requires reliable transport layer (e. g. TCP) • Supports any application protocols HTTP Telnet TLS TCP IP FTP LDAP 6
 TLS: Privacy • Encrypt message so it cannot be read • Use conventional cryptography with shared key – DES, 3 DES – RC 2, RC 4 – IDEA A Message $%&#!@ B Message 7
TLS: Privacy • Encrypt message so it cannot be read • Use conventional cryptography with shared key – DES, 3 DES – RC 2, RC 4 – IDEA A Message $%&#!@ B Message 7
 TLS: Key Exchange • Need secure method to exchange secret key • Use public key encryption for this – “key pair” is used - either one can encrypt and then the other can decrypt – slower than conventional cryptography – share one key, keep the other private • Choices are RSA or Diffie-Hellman 8
TLS: Key Exchange • Need secure method to exchange secret key • Use public key encryption for this – “key pair” is used - either one can encrypt and then the other can decrypt – slower than conventional cryptography – share one key, keep the other private • Choices are RSA or Diffie-Hellman 8
 TLS: Integrity • Compute fixed-length Message Authentication Code (MAC) – Includes hash of message – Includes a shared secret – Include sequence number • Transmit MAC with message 9
TLS: Integrity • Compute fixed-length Message Authentication Code (MAC) – Includes hash of message – Includes a shared secret – Include sequence number • Transmit MAC with message 9
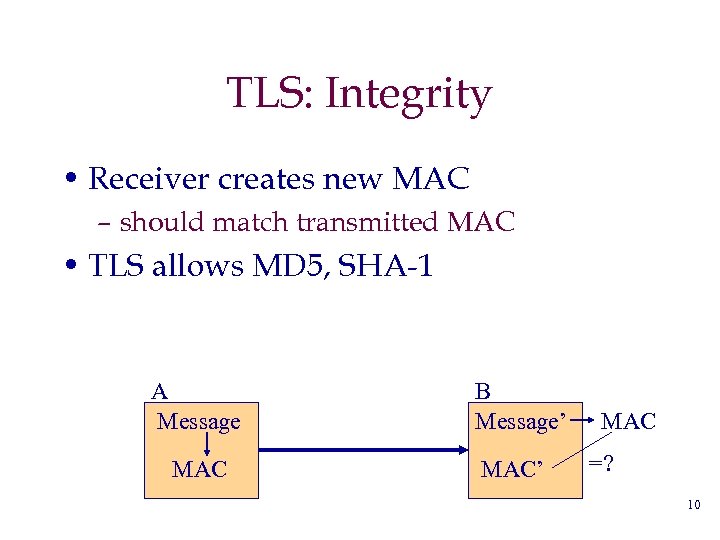 TLS: Integrity • Receiver creates new MAC – should match transmitted MAC • TLS allows MD 5, SHA-1 A Message MAC B Message’ MAC =? 10
TLS: Integrity • Receiver creates new MAC – should match transmitted MAC • TLS allows MD 5, SHA-1 A Message MAC B Message’ MAC =? 10
 TLS: Authentication • Verify identities of participants • Client authentication is optional • Certificate is used to associate identity with public key and other attributes A Certificate B Certificate 11
TLS: Authentication • Verify identities of participants • Client authentication is optional • Certificate is used to associate identity with public key and other attributes A Certificate B Certificate 11
 TLS: Overview • Establish a session – Agree on algorithms – Share secrets – Perform authentication • Transfer application data – Ensure privacy and integrity 12
TLS: Overview • Establish a session – Agree on algorithms – Share secrets – Perform authentication • Transfer application data – Ensure privacy and integrity 12
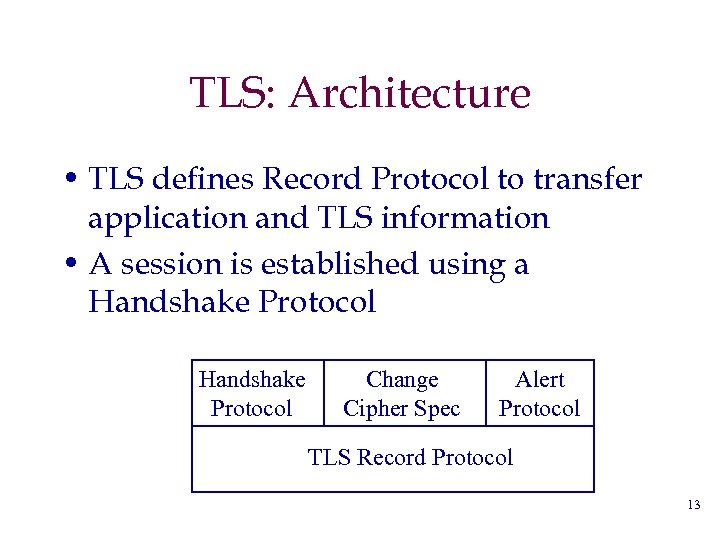 TLS: Architecture • TLS defines Record Protocol to transfer application and TLS information • A session is established using a Handshake Protocol Change Cipher Spec Alert Protocol TLS Record Protocol 13
TLS: Architecture • TLS defines Record Protocol to transfer application and TLS information • A session is established using a Handshake Protocol Change Cipher Spec Alert Protocol TLS Record Protocol 13
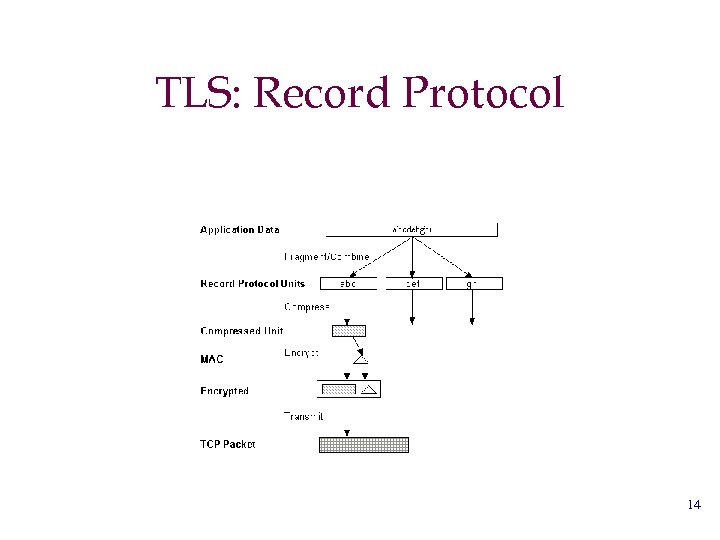 TLS: Record Protocol 14
TLS: Record Protocol 14
 TLS: Handshake • Negotiate Cipher-Suite Algorithms – Symmetric cipher to use – Key exchange method – Message digest function • Establish and share master secret • Optionally authenticate server and/or client 15
TLS: Handshake • Negotiate Cipher-Suite Algorithms – Symmetric cipher to use – Key exchange method – Message digest function • Establish and share master secret • Optionally authenticate server and/or client 15
 Handshake Phases • Hello messages • Certificate and Key Exchange messages • Change Cipher. Spec and Finished messages 16
Handshake Phases • Hello messages • Certificate and Key Exchange messages • Change Cipher. Spec and Finished messages 16
 TLS: Hello • Client “Hello” - initiates session – Propose protocol version – Propose cipher suite – Server chooses protocol and suite • Client may request use of cached session – Server chooses whether to honor request 17
TLS: Hello • Client “Hello” - initiates session – Propose protocol version – Propose cipher suite – Server chooses protocol and suite • Client may request use of cached session – Server chooses whether to honor request 17
 TLS: Key Exchange • Server sends certificate containing public key (RSA) or Diffie-Hellman parameters • Client sends encrypted “pre-master” secret to server using Client Key Exchange message • Master secret calculated – Use random values passed in Client and Server Hello messages 18
TLS: Key Exchange • Server sends certificate containing public key (RSA) or Diffie-Hellman parameters • Client sends encrypted “pre-master” secret to server using Client Key Exchange message • Master secret calculated – Use random values passed in Client and Server Hello messages 18
 Public Key Certificates • X. 509 Certificate associates public key with identity • Certification Authority (CA) creates certificate – Adheres to policies and verifies identity – Signs certificate • User of Certificate must ensure it is valid 19
Public Key Certificates • X. 509 Certificate associates public key with identity • Certification Authority (CA) creates certificate – Adheres to policies and verifies identity – Signs certificate • User of Certificate must ensure it is valid 19
 Validating a Certificate • Must recognize accepted CA in certificate chain – One CA may issue certificate for another CA • Must verify that certificate has not been revoked – CA publishes Certificate Revocation List (CRL) 20
Validating a Certificate • Must recognize accepted CA in certificate chain – One CA may issue certificate for another CA • Must verify that certificate has not been revoked – CA publishes Certificate Revocation List (CRL) 20
 X. 509: Certificate Content • Version • Serial Number • Signature Algorithm Identifier – Object Identifier (OID) – e. g. id-dsa: {iso(1) memberbody(2) us(840) x 9 -57 (10040) x 9 algorithm(4) 1} • Issuer (CA) X. 500 name • Validity Period (Start, End) • Subject X. 500 name • Subject Public Key – Algorithm – Value • Issuer Unique Id (Version 2 , 3) • Subject Unique Id (Version 2, 3) • Extensions (version 3) – optional • CA digital Signature 21
X. 509: Certificate Content • Version • Serial Number • Signature Algorithm Identifier – Object Identifier (OID) – e. g. id-dsa: {iso(1) memberbody(2) us(840) x 9 -57 (10040) x 9 algorithm(4) 1} • Issuer (CA) X. 500 name • Validity Period (Start, End) • Subject X. 500 name • Subject Public Key – Algorithm – Value • Issuer Unique Id (Version 2 , 3) • Subject Unique Id (Version 2, 3) • Extensions (version 3) – optional • CA digital Signature 21
 Subject Names • X. 500 Distinguished Name (DN) • Associated with node in hierarchical directory (X. 500) • Each node has Relative Distinguished Name (RDN) – Path for parent node – Unique set of attribute/value pairs for this node 22
Subject Names • X. 500 Distinguished Name (DN) • Associated with node in hierarchical directory (X. 500) • Each node has Relative Distinguished Name (RDN) – Path for parent node – Unique set of attribute/value pairs for this node 22
 Example Subject Name • Country at Highest Level (e. g. US) • Organization typically at next level (e. g. Cert. Co) • Individual below (e. g. Common Name “Elizabeth” with Id = 1) DN = { • C=US; • O=Cert. Co; • CN=Elizabeth, ID=1} 23
Example Subject Name • Country at Highest Level (e. g. US) • Organization typically at next level (e. g. Cert. Co) • Individual below (e. g. Common Name “Elizabeth” with Id = 1) DN = { • C=US; • O=Cert. Co; • CN=Elizabeth, ID=1} 23
 Version 3 Certificates • Version 3 X. 509 Certificates support alternative name formats as extensions – X. 500 names – Internet domain names – e-mail addresses – URLs • Certificate may include more than one name 24
Version 3 Certificates • Version 3 X. 509 Certificates support alternative name formats as extensions – X. 500 names – Internet domain names – e-mail addresses – URLs • Certificate may include more than one name 24
 Certificate Signature • RSA Signature – Create hash of certificate – Encrypt using CA’s private key • Signature verification – Decrypt using CA’s public key – Verify hash 25
Certificate Signature • RSA Signature – Create hash of certificate – Encrypt using CA’s private key • Signature verification – Decrypt using CA’s public key – Verify hash 25
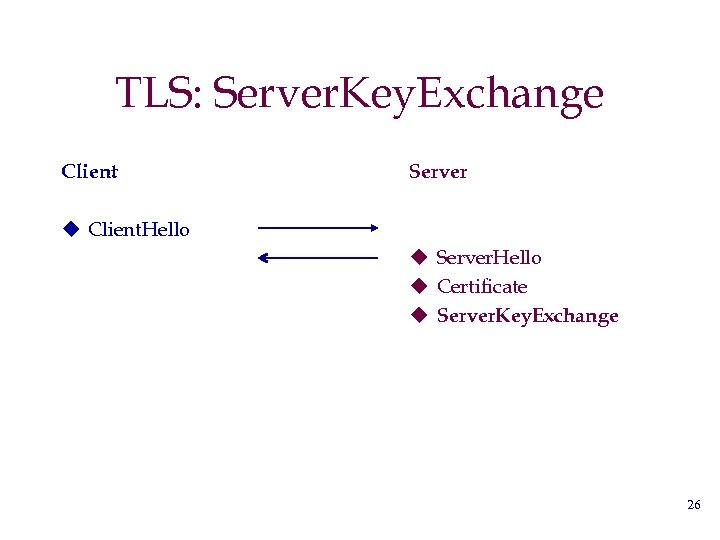 TLS: Server. Key. Exchange Client Server u Client. Hello u Server. Hello u Certificate u Server. Key. Exchange 26
TLS: Server. Key. Exchange Client Server u Client. Hello u Server. Hello u Certificate u Server. Key. Exchange 26
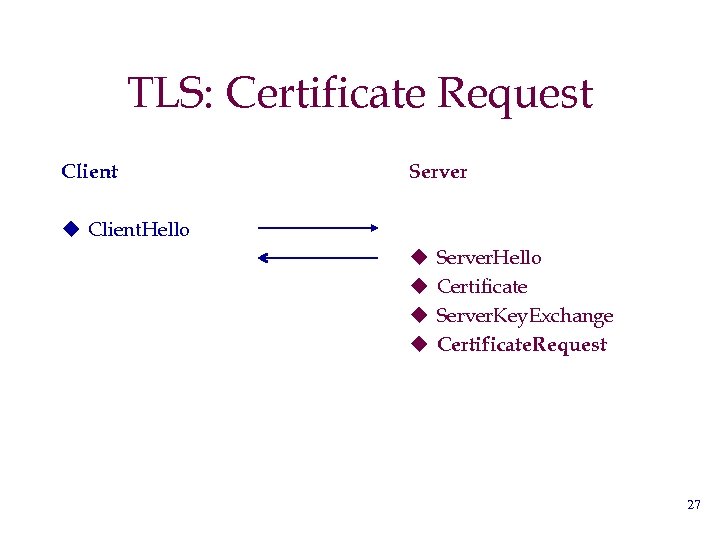 TLS: Certificate Request Client Server u Client. Hello u u Server. Hello Certificate Server. Key. Exchange Certificate. Request 27
TLS: Certificate Request Client Server u Client. Hello u u Server. Hello Certificate Server. Key. Exchange Certificate. Request 27
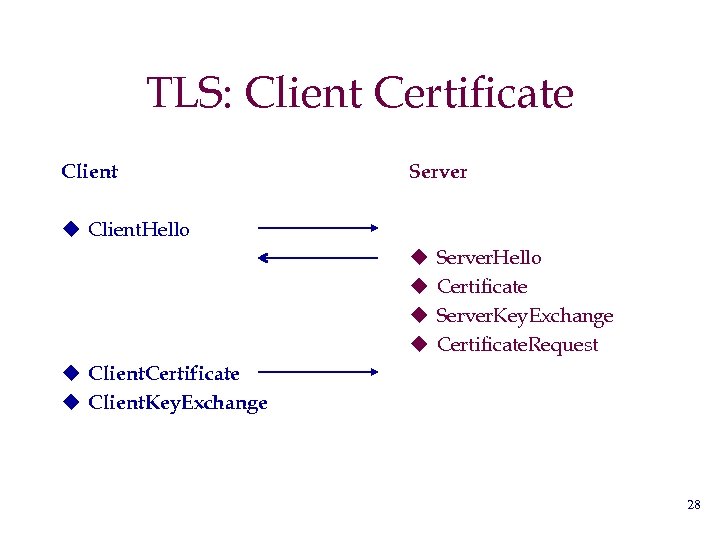 TLS: Client Certificate Client Server u Client. Hello u u Server. Hello Certificate Server. Key. Exchange Certificate. Request u Client. Certificate u Client. Key. Exchange 28
TLS: Client Certificate Client Server u Client. Hello u u Server. Hello Certificate Server. Key. Exchange Certificate. Request u Client. Certificate u Client. Key. Exchange 28
![TLS: Change Cipher Spec, Finished Client Server u [Change. Cipher. Spec] u Finished u TLS: Change Cipher Spec, Finished Client Server u [Change. Cipher. Spec] u Finished u](https://present5.com/presentation/dea534a03e4897486d6ca6a4864434f1/image-29.jpg) TLS: Change Cipher Spec, Finished Client Server u [Change. Cipher. Spec] u Finished u Application Data 29
TLS: Change Cipher Spec, Finished Client Server u [Change. Cipher. Spec] u Finished u Application Data 29
 TLS: Change Cipher Spec/Finished • Change Cipher Spec – Announce switch to negotiated algorithms and values • Finished – Send copy of handshake using new session – Permits validation of handshake 30
TLS: Change Cipher Spec/Finished • Change Cipher Spec – Announce switch to negotiated algorithms and values • Finished – Send copy of handshake using new session – Permits validation of handshake 30
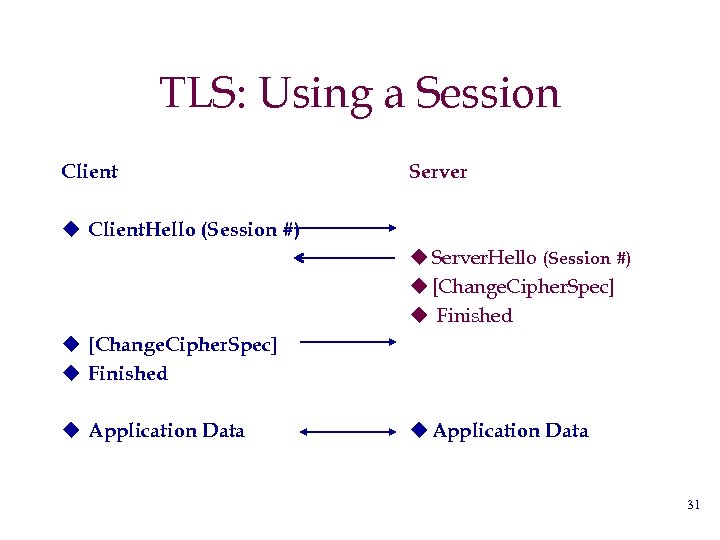 TLS: Using a Session Client Server u Client. Hello (Session #) u Server. Hello (Session #) u [Change. Cipher. Spec] u Finished u Application Data 31
TLS: Using a Session Client Server u Client. Hello (Session #) u Server. Hello (Session #) u [Change. Cipher. Spec] u Finished u Application Data 31
 Changes from SSL 3. 0 to TLS • Fortezza removed • Additional Alerts added • Modification to hash calculations • Protocol version 3. 1 in Client. Hello, Server. Hello 32
Changes from SSL 3. 0 to TLS • Fortezza removed • Additional Alerts added • Modification to hash calculations • Protocol version 3. 1 in Client. Hello, Server. Hello 32
 TLS: HTTP Application • HTTP most common TLS application – https: // • Requires TLS-capable web server • Requires TLS-capable web browser – Netscape Navigator – Internet Explorer – Cryptozilla • Netscape Mozilla sources with SSLeay 33
TLS: HTTP Application • HTTP most common TLS application – https: // • Requires TLS-capable web server • Requires TLS-capable web browser – Netscape Navigator – Internet Explorer – Cryptozilla • Netscape Mozilla sources with SSLeay 33
 Web Servers • Apache-SSL • Apache mod_ssl • Stronghold • Roxen • i. Net. Store 34
Web Servers • Apache-SSL • Apache mod_ssl • Stronghold • Roxen • i. Net. Store 34
 Other Applications • Telnet • FTP • LDAP • POP • SSLrsh • Commercial Proxies 35
Other Applications • Telnet • FTP • LDAP • POP • SSLrsh • Commercial Proxies 35
 TLS: Implementation • Cryptographic Libraries – RSARef, BSAFE • TLS/SSL packages – SSLeay – SSLRef 36
TLS: Implementation • Cryptographic Libraries – RSARef, BSAFE • TLS/SSL packages – SSLeay – SSLRef 36
 X. 509 Certificate Issues • Certificate Administration is complex – Hierarchy of Certification Authorities – Mechanisms for requesting, issuing, revoking certificates • X. 500 names are complicated • Description formats are cumbersome (ASN. 1) 37
X. 509 Certificate Issues • Certificate Administration is complex – Hierarchy of Certification Authorities – Mechanisms for requesting, issuing, revoking certificates • X. 500 names are complicated • Description formats are cumbersome (ASN. 1) 37
 X. 509 Alternative: SDSI – SDSI: Simple Distributed Security Infrastructure (Rivest, Lampson) • Merging with IETF SPKI: Simple Public-Key Infrastructure in SDSI 2. 0 • Eliminate X. 500 names - use DNS and text • Everyone is their own CA • Instead of ASN. 1 use “S-expressions” and simple syntax • Name and Authorization certificates 38
X. 509 Alternative: SDSI – SDSI: Simple Distributed Security Infrastructure (Rivest, Lampson) • Merging with IETF SPKI: Simple Public-Key Infrastructure in SDSI 2. 0 • Eliminate X. 500 names - use DNS and text • Everyone is their own CA • Instead of ASN. 1 use “S-expressions” and simple syntax • Name and Authorization certificates 38
 TLS “Alternatives” • S-HTTP: secure HTTP protocol, shttp: // • IPSec: secure IP • SET: Secure Electronic Transaction – Protocol and infrastructure for bank card payments • SASL: Simple Authentication and Security Layer (RFC 2222) 39
TLS “Alternatives” • S-HTTP: secure HTTP protocol, shttp: // • IPSec: secure IP • SET: Secure Electronic Transaction – Protocol and infrastructure for bank card payments • SASL: Simple Authentication and Security Layer (RFC 2222) 39
 Summary • SSL/TLS addresses the need for security in Internet communications – Privacy - conventional encryption – Integrity - Message Authentication Codes – Authentication - X. 509 certificates • SSL in use today with web browsers and servers 40
Summary • SSL/TLS addresses the need for security in Internet communications – Privacy - conventional encryption – Integrity - Message Authentication Codes – Authentication - X. 509 certificates • SSL in use today with web browsers and servers 40
 References - 1 • Engelschall, Ralph, mod_ssl,
References - 1 • Engelschall, Ralph, mod_ssl,
 References - 2 • Rivest, Ron, SDSI,
References - 2 • Rivest, Ron, SDSI,
 References - 3 • Microsoft Security Documents
References - 3 • Microsoft Security Documents
 http: //www. fjhirsch. com/~fhirsch/SSL/ 44
http: //www. fjhirsch. com/~fhirsch/SSL/ 44


