c2f9a660f9923bd911aa9ad39afdc0db.ppt
- Количество слайдов: 24

An Introduction to Computer Forensics Randy Ribler Department of Computer Science Lynchburg College

Computer Forensics Definition n Computer forensics is simply the application of computer investigation and analysis techniques in the interests of determining potential legal evidence. - Judd Robins, “An Explanation of Computer Forensics”

Application of Computer Forensics n Securing evidence in criminal and civil litigation n n Terrorism Child Pornography Industrial Espionage Documenting/Investigating a breach of network security Recovering inadvertently deleted data

High-profile Computer Forensics Cases Dismissal of U. S. attorneys controversy n Lost emails n n Some official e-mails have potentially been lost and that is a mistake the White House is aggressively working to correct. " - Scott Stanzel, Whitehouse spokesman Forged Email n n Larry Ellison loses sexual harassment case against former employee Employee later shown to have been the forger of incriminating email that appeared to be confirming Ellison’s role in her firing. (She was later convicted of perjury. )

Principal Targets of Computer Forensics n n Hard Disk Drives USB Drives, floppy disks SD memory, Compact Flash, and other static memory RAM (Random Access Memory)
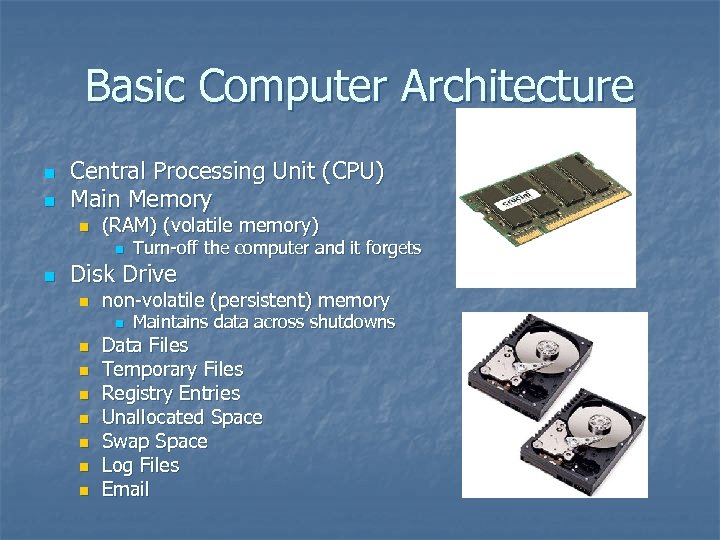
Basic Computer Architecture n n Central Processing Unit (CPU) Main Memory n (RAM) (volatile memory) n n Turn-off the computer and it forgets Disk Drive n non-volatile (persistent) memory n n n n Maintains data across shutdowns Data Files Temporary Files Registry Entries Unallocated Space Swap Space Log Files Email
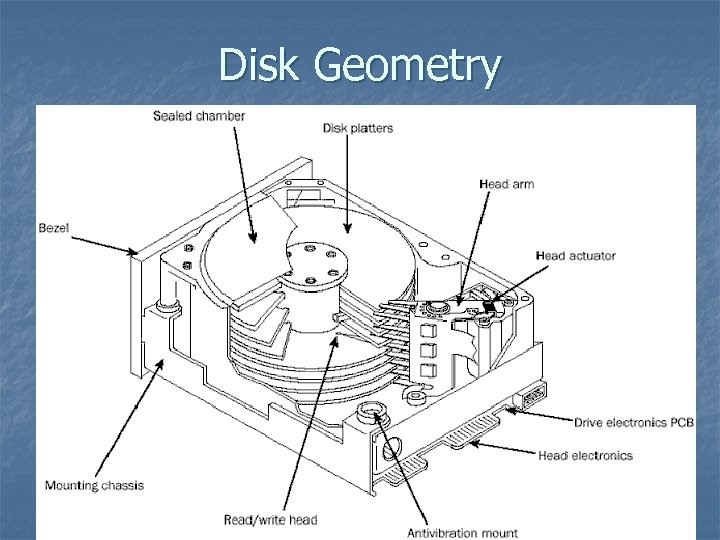
Disk Geometry
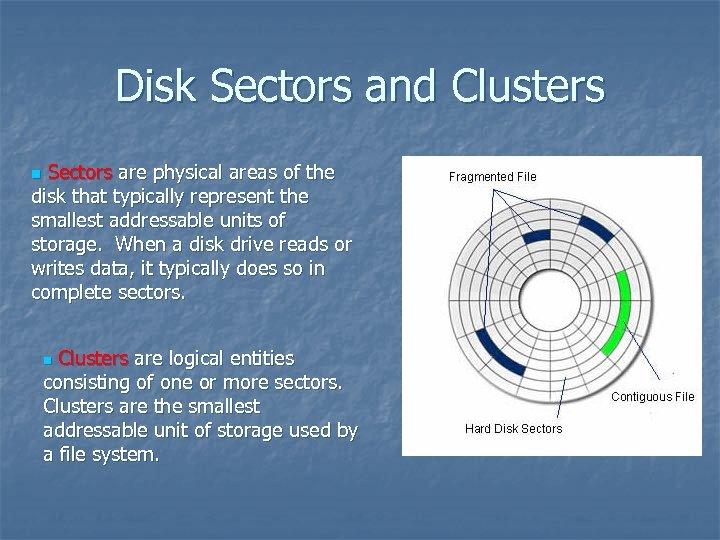
Disk Sectors and Clusters Sectors are physical areas of the disk that typically represent the smallest addressable units of storage. When a disk drive reads or writes data, it typically does so in complete sectors. n Clusters are logical entities consisting of one or more sectors. Clusters are the smallest addressable unit of storage used by a file system. n

How Clusters are Allocated to Files n n n Initially, the disk drive consists of a large number of unallocated clusters When a file is stored, the number of clusters needed to store the data are allocated to that file. A File Allocation Table keeps track of which clusters are allocated to which files
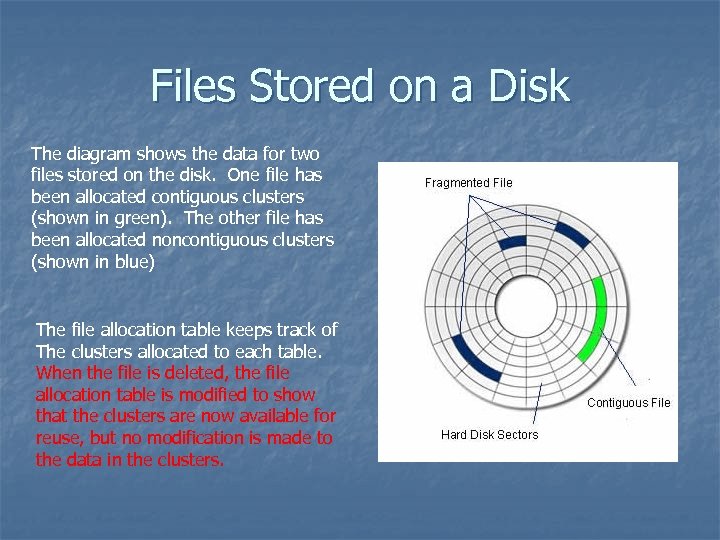
Files Stored on a Disk The diagram shows the data for two files stored on the disk. One file has been allocated contiguous clusters (shown in green). The other file has been allocated noncontiguous clusters (shown in blue) The file allocation table keeps track of The clusters allocated to each table. When the file is deleted, the file allocation table is modified to show that the clusters are now available for reuse, but no modification is made to the data in the clusters.

Foolproof methods for rendering previously stored data unreadable n n n Using a sledge hammer to reduce the disk platters to dust Overwrite every sector on the disk Store at least one irreplaceable file on it, for which you have no backup (Unproven, but with strong anecdotal evidence)

Deleting Disk Data n “Wiping” a file consists of deleting the file and overwriting the contents of the associated clusters n n Random data All ones and/or all zeros Multiple overwrites Single overwrite seems to be adequate for modern disk drives http: //www. springerlink. com/content/408263 ql 11460147/ n Remnants of the file may still exist in other parts of the system (e. g. , swapfile, temporary files, registry entries, etc). If so, data from wiped files can still be recovered.

Protection of evidence is critical n n n n Ensure that: no possible evidence is damaged, destroyed, or otherwise compromised by the procedures used to investigate the computer. no possible computer virus is introduced to a subject computer during the analysis process. extracted and possibly relevant evidence is properly handled and protected from later mechanical or electromagnetic damage. a continuing chain of custody is established and maintained. business operations are affected for a limited amount of time, if at all. any client-attorney information that is inadvertently acquired during a forensic exploration is ethically and legally respected and not divulged. * Bullet points from Judd Robbins : http: //www. computerforensics. net/forensics. htm

Forensic Procedure for Securing Disk Data for Analysis n n Extreme care must be taken to ensure that the data does not become modified as a side-effect of forensic analysis Turn the computer off if it is on n Remove the disk from the computer Write-protect the drive Use forensic software to create an “image file” n n n Image files contain a byte for byte copy of the sectors contained on the disk Secure the original disk All further analysis must be performed on the image file.

Computer Forensic Software n n n Many software tools exist to recover deleted files and find keywords and other data of interest En. Case is one of the more popular and powerful tools available http: //www. youtube. com/watch? v=O 4 ce 7 4 q 2 zq. M

E-mail – The most frequently smoking gun n “You can't erase e-mails, not today…They've gone through too many servers. Those e-mails are there –” n Senator Patrick Leahy

Finding lost Emails n Emails can be recovered from a number of different locations n Local user files n POP 3 email client protocols copy all email data to the local disk n n n IMAP email client protocols leave the email on the server, but local copies are likely to exist in temporary or swap files Servers n n Under many email clients (including Outlook) deleted emails exist in the local archive even after they are purged from the deleted mail folder. Mail servers will maintain email records Backups n Backups of both client and server machines can provide copies of deleted emails

Encryption/Decryption n Data is encrypted before it is stored on the disk Without the key, the data cannot be understood n Deleted file are unreadable n n Data in memory is not encrypted n Such data might still be referenced in swap files, system logs, and registry entries

String Search Techniques n String search algorithms n Search for “regular expression” n n CS[1 -3][0 -9][ ]*[r. R][i. I][b. B][l. L][e. E][r. R] Index the entire disk n Make a list of all the places on the disk each keyword appears n n n Indexes can be very large Very fast response to keyword queries Indexes are generally created in a “batch” mode, and interactive investigation proceeds after the index generation is complete

Princeton Encryption Hack n http: //www. youtube. com/watch? v=JDaic. P Ign 9 U

Implications of the Princeton Encryption Hack n n Perhaps computer forensic investigation will no include investigation of RAM images. The same techniques used for disks can be applied. l Many encryption

Steganography n steganography http: //en. wikipedia. org/wiki/Steganograph y

Credibility of Digital Data n n n Unlike other forensic evidence, digital data on a computer can be modified without physical access to the computer. How do we know that incriminating evidence has not been planted? Recent case of files in Windows Options directory http: //news. bbc. co. uk/1/hi/scotland/tayside_and _central/6968663. stm

Problems with Digital Data n n n Meta data, such as file access/creation times, file ownership ccan be changed easily Emails and any other data can be fabricated Given a blank disk, we can create any image we like
c2f9a660f9923bd911aa9ad39afdc0db.ppt