4ca50e8dc5100af44e12cc535b8ac5cf.ppt
- Количество слайдов: 83
 An Economic Response to Unsolicited Communication Thede Loder Marshall Van Alstyne Rick Wash University of Michigan Boston University & MIT University of Michigan tloder@umich. edu mva@bu. edu marshall@mit. edu rwash@umich. edu
An Economic Response to Unsolicited Communication Thede Loder Marshall Van Alstyne Rick Wash University of Michigan Boston University & MIT University of Michigan tloder@umich. edu mva@bu. edu marshall@mit. edu rwash@umich. edu
 2 © 2006 Loder, Van Alstyne & Wash, all rights reserved.
2 © 2006 Loder, Van Alstyne & Wash, all rights reserved.
 Agenda • Description of the problem – From regulatory and technical perspectives – From an economic perspective • Application of the Coase Theorem plus Signaling & Screening from information economics • Comparison against idealized perfect filter and perfect tax. • Cover surrounding issues of adoption, spoofing, free speech, viruses & spam zombies. 4 © 2006 Loder, Van Alstyne & Wash, all rights reserved.
Agenda • Description of the problem – From regulatory and technical perspectives – From an economic perspective • Application of the Coase Theorem plus Signaling & Screening from information economics • Comparison against idealized perfect filter and perfect tax. • Cover surrounding issues of adoption, spoofing, free speech, viruses & spam zombies. 4 © 2006 Loder, Van Alstyne & Wash, all rights reserved.
 Data on the Spam Problem • • Estimated yearly loss to business $20 billion (Ferris Rsch) Federal ‘Can Spam’ Act enacted in 2004 with near unanimous support; superceding 8 State laws (NYT) …but no impact (Pew Internet Report) 55% (Brightmail 2003) , 77% (CDT 2004) of all email is now spam 29% of Americans report curtailing e-mail use (Pew Internet report) Zombies send 50 -80% of all spam (FTC), 25% of US pc’s infected (Symantec) No consensus definition: 92% adult, 74% political/religious, 65% charities, 32% unsolicited + prior biz relation, 11% unsolicited + granted permission to market. 1/3 users clicked on link, 5% admit to purchase, 3% provided pers. info. (Pew) Spammer Alan Ralsky vowed to carry on (NYT) 5 © 2006 Loder, Van Alstyne & Wash, all rights reserved.
Data on the Spam Problem • • Estimated yearly loss to business $20 billion (Ferris Rsch) Federal ‘Can Spam’ Act enacted in 2004 with near unanimous support; superceding 8 State laws (NYT) …but no impact (Pew Internet Report) 55% (Brightmail 2003) , 77% (CDT 2004) of all email is now spam 29% of Americans report curtailing e-mail use (Pew Internet report) Zombies send 50 -80% of all spam (FTC), 25% of US pc’s infected (Symantec) No consensus definition: 92% adult, 74% political/religious, 65% charities, 32% unsolicited + prior biz relation, 11% unsolicited + granted permission to market. 1/3 users clicked on link, 5% admit to purchase, 3% provided pers. info. (Pew) Spammer Alan Ralsky vowed to carry on (NYT) 5 © 2006 Loder, Van Alstyne & Wash, all rights reserved.
 Existing or Proposed Solutions • Legislative/Regulatory: – Banning, labeling – Taxation, stamps • Technological: – Filtering: Rule based (static or dynamic), Bayesian Filters, collective/community classification – Challenge Response: quasi-Turing tests, return address testing, computational challenge • Economic – computational challenge – Bonds 10 © 2006 Loder, Van Alstyne & Wash, all rights reserved.
Existing or Proposed Solutions • Legislative/Regulatory: – Banning, labeling – Taxation, stamps • Technological: – Filtering: Rule based (static or dynamic), Bayesian Filters, collective/community classification – Challenge Response: quasi-Turing tests, return address testing, computational challenge • Economic – computational challenge – Bonds 10 © 2006 Loder, Van Alstyne & Wash, all rights reserved.
 Problems with Existing Solutions Legislation Technologyy • Whose spam definition? • Banning and labeling • Filtering (Rules, Collaborative, Bayesian): – False positives, false negatives – Increases spam email traffic (attempts to penetrate) – Costly arms-race – Consensus definition – Blocks automated correspondence – Enforceability, jurisdiction? – Costly to police and adjudicate – Labeling lacks incentive compatibility – Exemptions for prior biz relations, political groups • Taxing & e-stamps • Challenge-Response (Reverse Turing Tests) – Blocks wanted along with unwanted email – Blunts cost-effectiveness of email as medium – Cheaply hire real people – Unrecoverable costs 12 © 2006 Loder, Van Alstyne & Wash, all rights reserved.
Problems with Existing Solutions Legislation Technologyy • Whose spam definition? • Banning and labeling • Filtering (Rules, Collaborative, Bayesian): – False positives, false negatives – Increases spam email traffic (attempts to penetrate) – Costly arms-race – Consensus definition – Blocks automated correspondence – Enforceability, jurisdiction? – Costly to police and adjudicate – Labeling lacks incentive compatibility – Exemptions for prior biz relations, political groups • Taxing & e-stamps • Challenge-Response (Reverse Turing Tests) – Blocks wanted along with unwanted email – Blunts cost-effectiveness of email as medium – Cheaply hire real people – Unrecoverable costs 12 © 2006 Loder, Van Alstyne & Wash, all rights reserved.
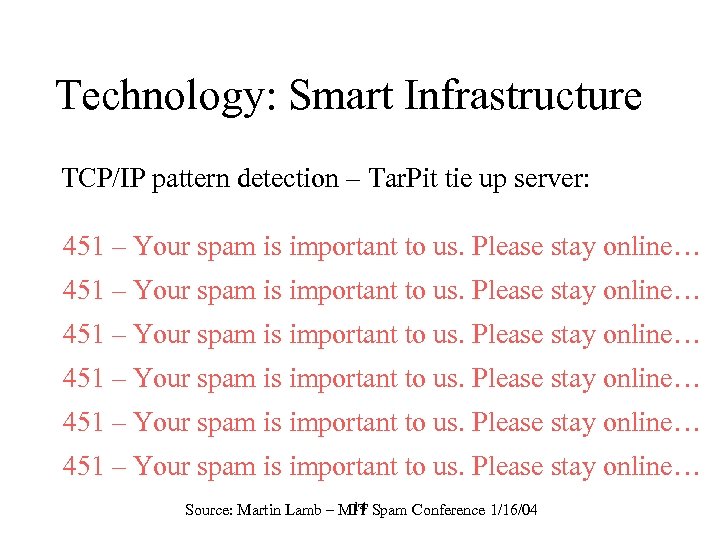 Technology: Smart Infrastructure TCP/IP pattern detection – Tar. Pit tie up server: 451 – Your spam is important to us. Please stay online… 14 Source: Martin Lamb – MIT Spam Conference 1/16/04
Technology: Smart Infrastructure TCP/IP pattern detection – Tar. Pit tie up server: 451 – Your spam is important to us. Please stay online… 14 Source: Martin Lamb – MIT Spam Conference 1/16/04
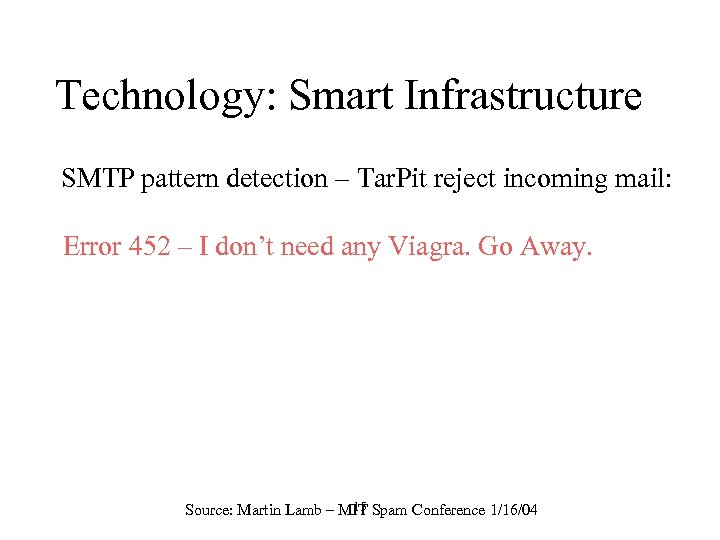 Technology: Smart Infrastructure SMTP pattern detection – Tar. Pit reject incoming mail: Error 452 – I don’t need any Viagra. Go Away. 15 Source: Martin Lamb – MIT Spam Conference 1/16/04
Technology: Smart Infrastructure SMTP pattern detection – Tar. Pit reject incoming mail: Error 452 – I don’t need any Viagra. Go Away. 15 Source: Martin Lamb – MIT Spam Conference 1/16/04
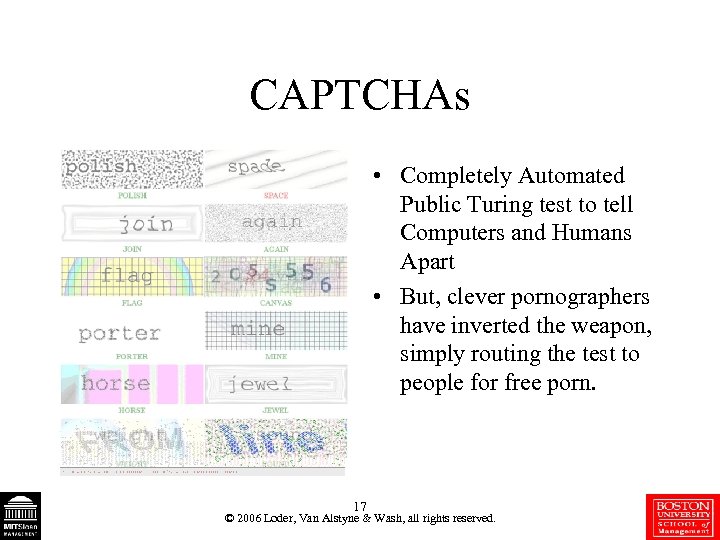 CAPTCHAs • Completely Automated Public Turing test to tell Computers and Humans Apart • But, clever pornographers have inverted the weapon, simply routing the test to people for free porn. 17 © 2006 Loder, Van Alstyne & Wash, all rights reserved.
CAPTCHAs • Completely Automated Public Turing test to tell Computers and Humans Apart • But, clever pornographers have inverted the weapon, simply routing the test to people for free porn. 17 © 2006 Loder, Van Alstyne & Wash, all rights reserved.
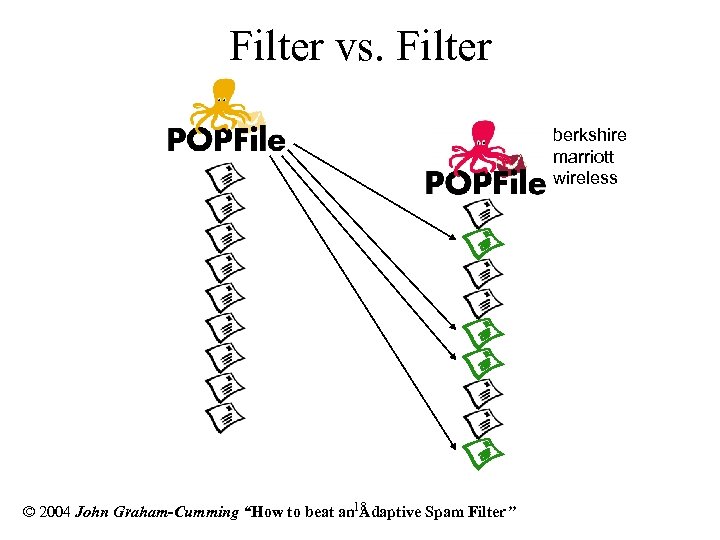 Filter vs. Filter berkshire marriott wireless © 2004 John Graham-Cumming “How to beat an 18 Adaptive Spam Filter”
Filter vs. Filter berkshire marriott wireless © 2004 John Graham-Cumming “How to beat an 18 Adaptive Spam Filter”
 Warning: risqué! © 2006 Loder, Van Alstyne & Wash, all rights reserved.
Warning: risqué! © 2006 Loder, Van Alstyne & Wash, all rights reserved.
 Where is “v 1@grya” or
Where is “v 1@grya” or
 Where is “v 1@grya” or
Where is “v 1@grya” or
 Where is “v 1@grya” or
Where is “v 1@grya” or
 What is spam? © 2006 Loder, Van Alstyne & Wash, all rights reserved.
What is spam? © 2006 Loder, Van Alstyne & Wash, all rights reserved.
 Improving Welfare I. In economic terms, spam is “message pollution” a negative externality arising from sender attempts to reach a tiny group of people who want their products. The approaches to pollution are filters, regulation, and … 28 © 2006 Loder, Van Alstyne & Wash, all rights reserved.
Improving Welfare I. In economic terms, spam is “message pollution” a negative externality arising from sender attempts to reach a tiny group of people who want their products. The approaches to pollution are filters, regulation, and … 28 © 2006 Loder, Van Alstyne & Wash, all rights reserved.
 The Coase Theorem – Property Rights Resolve why the market failed… Old: Pigou’s theory that gov’t should force private parties to “internalize” externalities by means of taxes. New: Coase argues that affected parties can do so via trade and negotiation, if (1) property rights are well defined and (2) transaction costs are negligible. Nobel 1991 – “for his discovery and clarification of the significance of transaction costs and property rights for the institutional structure and functioning of the economy. ” Regardless of initial assignment, the social outcome is at least as efficient. No unilateral solution can do better. 29 © 2006 Loder, Van Alstyne & Wash, all rights reserved.
The Coase Theorem – Property Rights Resolve why the market failed… Old: Pigou’s theory that gov’t should force private parties to “internalize” externalities by means of taxes. New: Coase argues that affected parties can do so via trade and negotiation, if (1) property rights are well defined and (2) transaction costs are negligible. Nobel 1991 – “for his discovery and clarification of the significance of transaction costs and property rights for the institutional structure and functioning of the economy. ” Regardless of initial assignment, the social outcome is at least as efficient. No unilateral solution can do better. 29 © 2006 Loder, Van Alstyne & Wash, all rights reserved.
 Improving Welfare I. In economic terms, spam is “message pollution” a negative externality arising from sender attempts to reach a tiny group of people who want their products. II. The Coase Theorem: one solution is to define attention rights, i. e. create a mechanism to charge those who create waste. III. But assign property rights to recipients! a. A sender right to waste recipient time encourages extortion. Spammers just threaten to send more. b. Seems obvious, but no. Also interpreted as right to be heard. c. If transaction costs are high, assign rights to the party with higher costs of avoiding waste. 30 © 2006 Loder, Van Alstyne & Wash, all rights reserved.
Improving Welfare I. In economic terms, spam is “message pollution” a negative externality arising from sender attempts to reach a tiny group of people who want their products. II. The Coase Theorem: one solution is to define attention rights, i. e. create a mechanism to charge those who create waste. III. But assign property rights to recipients! a. A sender right to waste recipient time encourages extortion. Spammers just threaten to send more. b. Seems obvious, but no. Also interpreted as right to be heard. c. If transaction costs are high, assign rights to the party with higher costs of avoiding waste. 30 © 2006 Loder, Van Alstyne & Wash, all rights reserved.
![Terminology & Assumptions • [r, r] and [s, s] are bounds on reader and Terminology & Assumptions • [r, r] and [s, s] are bounds on reader and](https://present5.com/presentation/4ca50e8dc5100af44e12cc535b8ac5cf/image-19.jpg) Terminology & Assumptions • [r, r] and [s, s] are bounds on reader and sender values. • Sender knows own value s and cost cs before sending, won’t send when s < cs. • There may be good SG and bad SB sender distributions, sender knows from which distribution he draws. • Recipient only knows her r value after reading and incurring cost cr. • Filtering results in a fraction of messages not getting through. 32 © 2006 Loder, Van Alstyne & Wash, all rights reserved.
Terminology & Assumptions • [r, r] and [s, s] are bounds on reader and sender values. • Sender knows own value s and cost cs before sending, won’t send when s < cs. • There may be good SG and bad SB sender distributions, sender knows from which distribution he draws. • Recipient only knows her r value after reading and incurring cost cr. • Filtering results in a fraction of messages not getting through. 32 © 2006 Loder, Van Alstyne & Wash, all rights reserved.
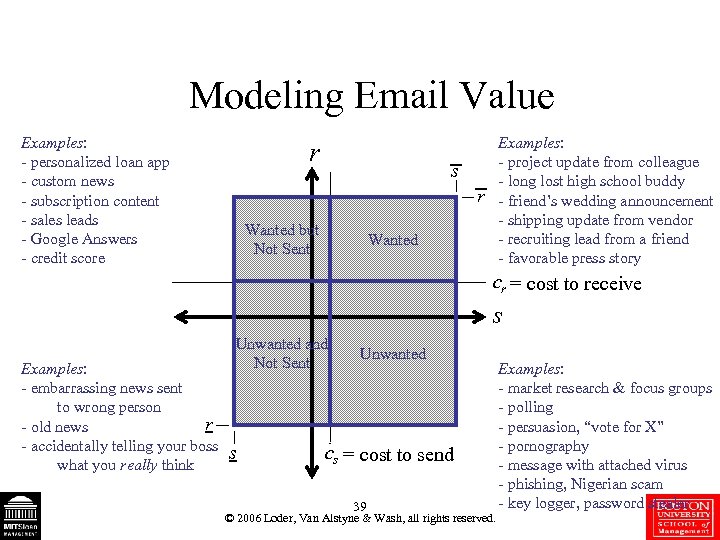 Modeling Email Value Examples: - personalized loan app - custom news - subscription content - sales leads - Google Answers - credit score r Examples: - project update from colleague - long lost high school buddy - friend’s wedding announcement - shipping update from vendor - recruiting lead from a friend - favorable press story s r Wanted but Not Sent Wanted cr = cost to receive s Examples: - embarrassing news sent to wrong person r - old news - accidentally telling your boss what you really think Unwanted and Not Sent s Unwanted cs = cost to send 39 © 2006 Loder, Van Alstyne & Wash, all rights reserved. Examples: - market research & focus groups - polling - persuasion, “vote for X” - pornography - message with attached virus - phishing, Nigerian scam - key logger, password stealer
Modeling Email Value Examples: - personalized loan app - custom news - subscription content - sales leads - Google Answers - credit score r Examples: - project update from colleague - long lost high school buddy - friend’s wedding announcement - shipping update from vendor - recruiting lead from a friend - favorable press story s r Wanted but Not Sent Wanted cr = cost to receive s Examples: - embarrassing news sent to wrong person r - old news - accidentally telling your boss what you really think Unwanted and Not Sent s Unwanted cs = cost to send 39 © 2006 Loder, Van Alstyne & Wash, all rights reserved. Examples: - market research & focus groups - polling - persuasion, “vote for X” - pornography - message with attached virus - phishing, Nigerian scam - key logger, password stealer
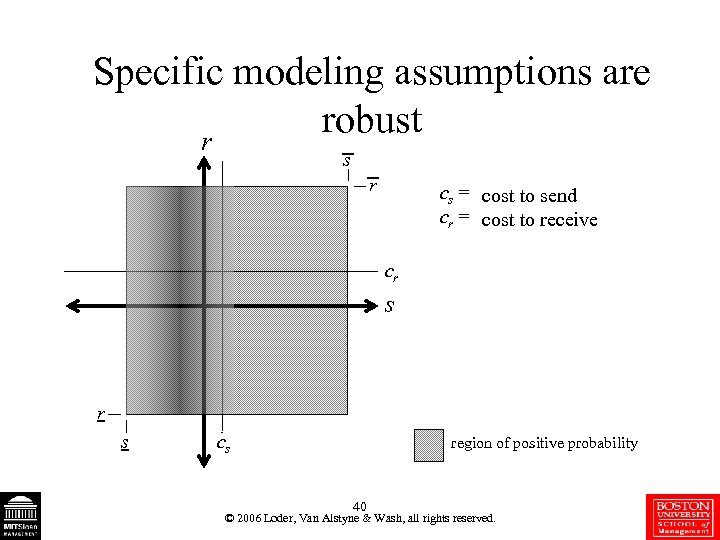 Specific modeling assumptions are robust r s r cs = cost to send cr = cost to receive cr s cs region of positive probability 40 © 2006 Loder, Van Alstyne & Wash, all rights reserved.
Specific modeling assumptions are robust r s r cs = cost to send cr = cost to receive cr s cs region of positive probability 40 © 2006 Loder, Van Alstyne & Wash, all rights reserved.
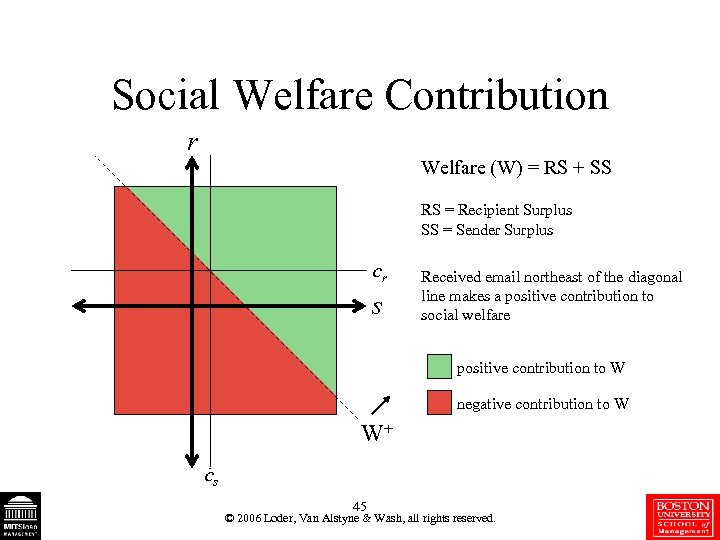 Social Welfare Contribution r Welfare (W) = RS + SS RS = Recipient Surplus SS = Sender Surplus cr s Received email northeast of the diagonal line makes a positive contribution to social welfare positive contribution to W negative contribution to W W+ cs 45 © 2006 Loder, Van Alstyne & Wash, all rights reserved.
Social Welfare Contribution r Welfare (W) = RS + SS RS = Recipient Surplus SS = Sender Surplus cr s Received email northeast of the diagonal line makes a positive contribution to social welfare positive contribution to W negative contribution to W W+ cs 45 © 2006 Loder, Van Alstyne & Wash, all rights reserved.
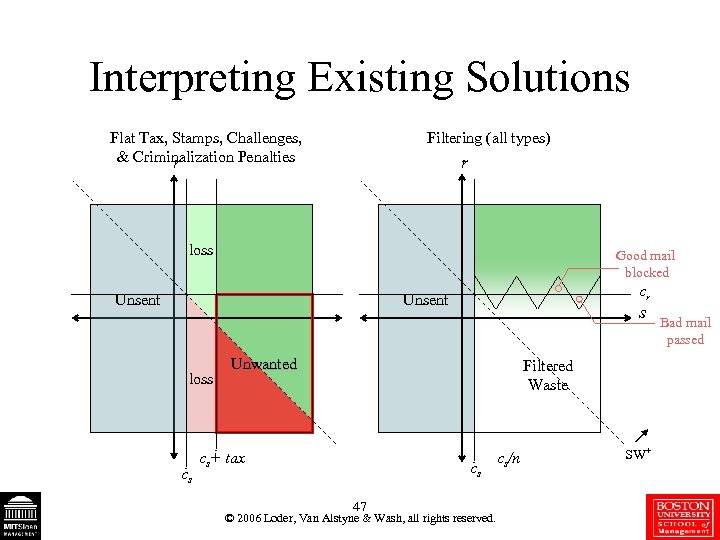 Interpreting Existing Solutions Flat Tax, Stamps, Challenges, & Criminalization Penalties r Filtering (all types) r loss Good mail blocked Unsent cr Unsent loss cs s Unwanted Filtered Waste cs+ tax cs 47 © 2006 Loder, Van Alstyne & Wash, all rights reserved. cs/n SW+ Bad mail passed
Interpreting Existing Solutions Flat Tax, Stamps, Challenges, & Criminalization Penalties r Filtering (all types) r loss Good mail blocked Unsent cr Unsent loss cs s Unwanted Filtered Waste cs+ tax cs 47 © 2006 Loder, Van Alstyne & Wash, all rights reserved. cs/n SW+ Bad mail passed
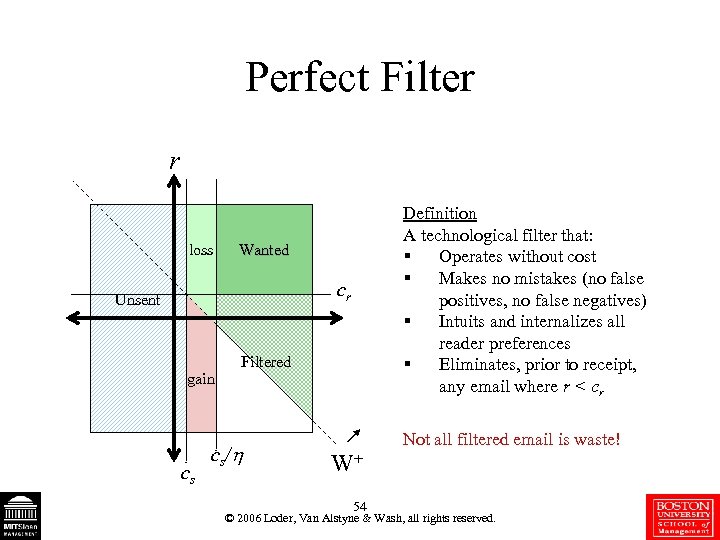 Perfect Filter r loss Definition A technological filter that: § Operates without cost § Makes no mistakes (no false positives, no false negatives) § Intuits and internalizes all reader preferences § Eliminates, prior to receipt, any email where r < cr Wanted cr Unsent gain cs Filtered cs/ Not all filtered email is waste! W+ 54 © 2006 Loder, Van Alstyne & Wash, all rights reserved.
Perfect Filter r loss Definition A technological filter that: § Operates without cost § Makes no mistakes (no false positives, no false negatives) § Intuits and internalizes all reader preferences § Eliminates, prior to receipt, any email where r < cr Wanted cr Unsent gain cs Filtered cs/ Not all filtered email is waste! W+ 54 © 2006 Loder, Van Alstyne & Wash, all rights reserved.
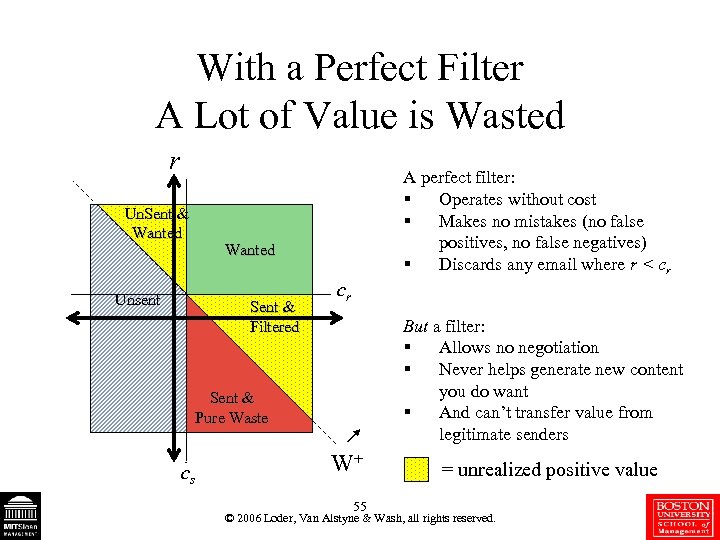 With a Perfect Filter A Lot of Value is Wasted r Un. Sent & Wanted Unsent A perfect filter: § Operates without cost § Makes no mistakes (no false positives, no false negatives) § Discards any email where r < cr Wanted Sent & Filtered cr But a filter: § Allows no negotiation § Never helps generate new content you do want § And can’t transfer value from legitimate senders Sent & Pure Waste cs W+ 55 = unrealized positive value © 2006 Loder, Van Alstyne & Wash, all rights reserved.
With a Perfect Filter A Lot of Value is Wasted r Un. Sent & Wanted Unsent A perfect filter: § Operates without cost § Makes no mistakes (no false positives, no false negatives) § Discards any email where r < cr Wanted Sent & Filtered cr But a filter: § Allows no negotiation § Never helps generate new content you do want § And can’t transfer value from legitimate senders Sent & Pure Waste cs W+ 55 = unrealized positive value © 2006 Loder, Van Alstyne & Wash, all rights reserved.
 Reverse Signaling – Buying Leads • Judson Brady, the owner of Broad Street Flowers, pays Ingenio around $4. 15 for each call from a prospect. NYT Feb 27, 2006 • Google Answers lets you pledge your credit card as bond for getting answers to critical questions. 56 © 2006 Loder, Van Alstyne & Wash, all rights reserved.
Reverse Signaling – Buying Leads • Judson Brady, the owner of Broad Street Flowers, pays Ingenio around $4. 15 for each call from a prospect. NYT Feb 27, 2006 • Google Answers lets you pledge your credit card as bond for getting answers to critical questions. 56 © 2006 Loder, Van Alstyne & Wash, all rights reserved.
 Problem: How do you reveal information without negotiation? © 2006 Loder, Van Alstyne & Wash, all rights reserved.
Problem: How do you reveal information without negotiation? © 2006 Loder, Van Alstyne & Wash, all rights reserved.
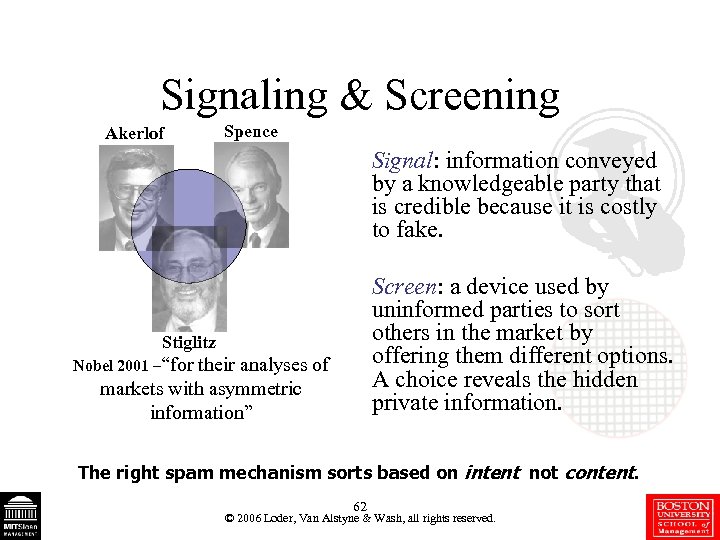 Signaling & Screening Akerlof Spence Signal: information conveyed by a knowledgeable party that is credible because it is costly to fake. Screen: a device used by uninformed parties to sort others in the market by offering them different options. A choice reveals the hidden private information. Stiglitz Nobel 2001 –“for their analyses of markets with asymmetric information” The right spam mechanism sorts based on intent not content. 62 © 2006 Loder, Van Alstyne & Wash, all rights reserved.
Signaling & Screening Akerlof Spence Signal: information conveyed by a knowledgeable party that is credible because it is costly to fake. Screen: a device used by uninformed parties to sort others in the market by offering them different options. A choice reveals the hidden private information. Stiglitz Nobel 2001 –“for their analyses of markets with asymmetric information” The right spam mechanism sorts based on intent not content. 62 © 2006 Loder, Van Alstyne & Wash, all rights reserved.
 Consider an “Attention Bond” Initially, the sender knows more about message content than the receiver, so force them to reveal that private knowledge: • • Simple screening mechanism applied to unrecognized senders. Challenge demands an escrowed bond fee of amount . Recipient has sole discretion to claim or return , with expected bond forfeiture b=p , all proceeds go to recipient Effects: 1. A recipient-controlled variable ‘tax’ on senders, based on sender behavior 2. Shift task from ex ante classification (hard) to ex post verification (easy). 3. Compensates recipient directly for any wasted time 63 © 2006 Loder, Van Alstyne & Wash, all rights reserved.
Consider an “Attention Bond” Initially, the sender knows more about message content than the receiver, so force them to reveal that private knowledge: • • Simple screening mechanism applied to unrecognized senders. Challenge demands an escrowed bond fee of amount . Recipient has sole discretion to claim or return , with expected bond forfeiture b=p , all proceeds go to recipient Effects: 1. A recipient-controlled variable ‘tax’ on senders, based on sender behavior 2. Shift task from ex ante classification (hard) to ex post verification (easy). 3. Compensates recipient directly for any wasted time 63 © 2006 Loder, Van Alstyne & Wash, all rights reserved.
 Consider an “Attention Bond” If the sender knows more about message content than the receiver, force him to reveal that private knowledge: 1. 2. 3. Recipient sets screen, chooses bond size bi. Unknown senders must post bond bi to get through. On reading message, recipient chooses to claim or return bi, with expected bond forfeiture i =pibi. • Effects: – – Seized bonds are side-payments -- increase recipient willingness to accept low value messages. Bond choice functions as a (weak) price signal indicating recipient type. Willingness to post bond signals sender private knowledge of message value. Shift task from ex ante classification (hard) to ex post verification (easy). 64 © 2006 Loder, Van Alstyne & Wash, all rights reserved.
Consider an “Attention Bond” If the sender knows more about message content than the receiver, force him to reveal that private knowledge: 1. 2. 3. Recipient sets screen, chooses bond size bi. Unknown senders must post bond bi to get through. On reading message, recipient chooses to claim or return bi, with expected bond forfeiture i =pibi. • Effects: – – Seized bonds are side-payments -- increase recipient willingness to accept low value messages. Bond choice functions as a (weak) price signal indicating recipient type. Willingness to post bond signals sender private knowledge of message value. Shift task from ex ante classification (hard) to ex post verification (easy). 64 © 2006 Loder, Van Alstyne & Wash, all rights reserved.
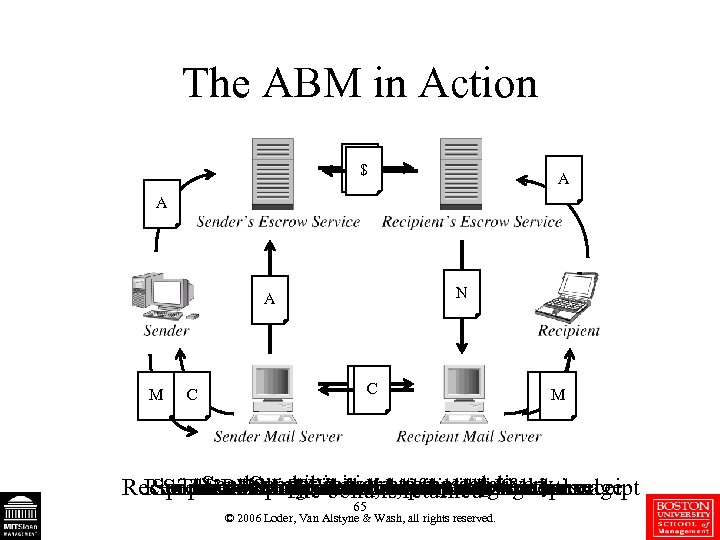 The ABM in Action $ $ A A N A M C MM Sender on issues bond-challenge Recipient’s mailissues notification of bond receipt Recipient’s. Sender claimsdelivers deliveredmessage Sender Recipient. Server is returned Sender… Sendernot. Sender initiates abond original issued or …and Mail Whitelist, mail the it expire. The challenge server is postedauthorization the Escrow is delivered to lets Sender The bond or delivery onserver issues message The bond attempts whitelist, authorization 65 © 2006 Loder, Van Alstyne & Wash, all rights reserved.
The ABM in Action $ $ A A N A M C MM Sender on issues bond-challenge Recipient’s mailissues notification of bond receipt Recipient’s. Sender claimsdelivers deliveredmessage Sender Recipient. Server is returned Sender… Sendernot. Sender initiates abond original issued or …and Mail Whitelist, mail the it expire. The challenge server is postedauthorization the Escrow is delivered to lets Sender The bond or delivery onserver issues message The bond attempts whitelist, authorization 65 © 2006 Loder, Van Alstyne & Wash, all rights reserved.
 Warning: economics! © 2006 Loder, Van Alstyne & Wash, all rights reserved.
Warning: economics! © 2006 Loder, Van Alstyne & Wash, all rights reserved.
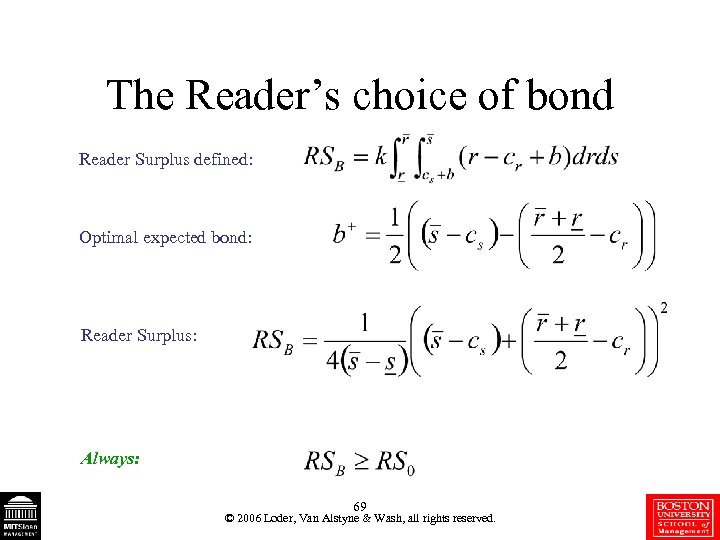 The Reader’s choice of bond Reader Surplus defined: Optimal expected bond: Reader Surplus: Always: 69 © 2006 Loder, Van Alstyne & Wash, all rights reserved.
The Reader’s choice of bond Reader Surplus defined: Optimal expected bond: Reader Surplus: Always: 69 © 2006 Loder, Van Alstyne & Wash, all rights reserved.
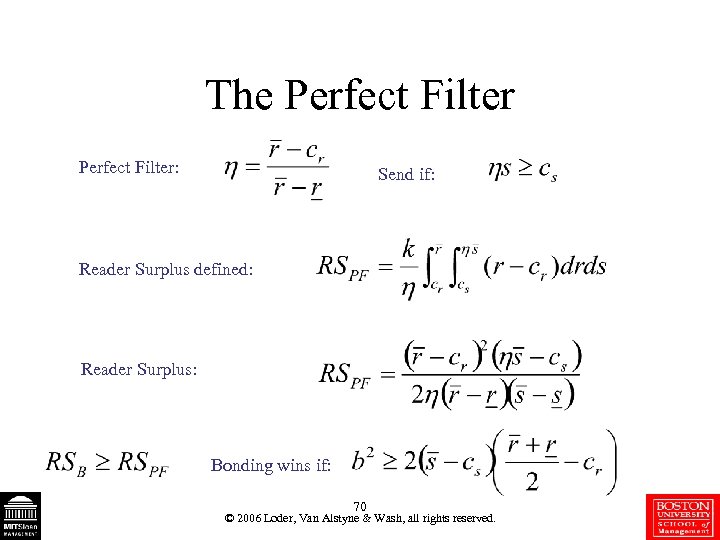 The Perfect Filter: Send if: Reader Surplus defined: Reader Surplus: Bonding wins if: 70 © 2006 Loder, Van Alstyne & Wash, all rights reserved.
The Perfect Filter: Send if: Reader Surplus defined: Reader Surplus: Bonding wins if: 70 © 2006 Loder, Van Alstyne & Wash, all rights reserved.
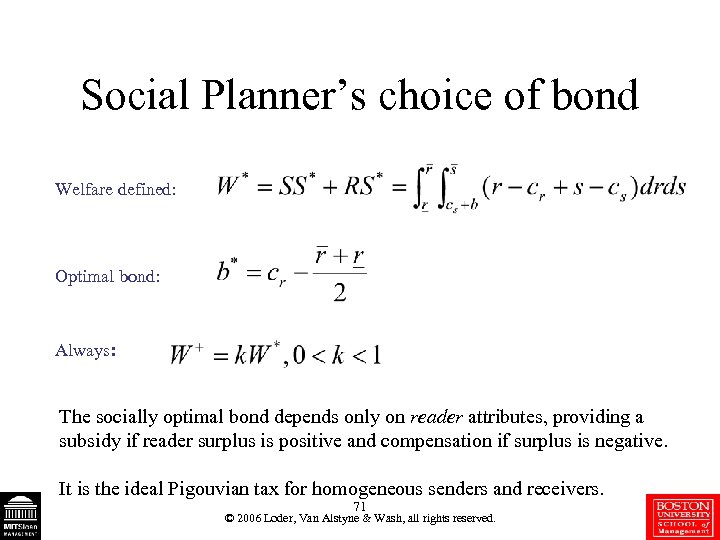 Social Planner’s choice of bond Welfare defined: Optimal bond: Always: The socially optimal bond depends only on reader attributes, providing a subsidy if reader surplus is positive and compensation if surplus is negative. It is the ideal Pigouvian tax for homogeneous senders and receivers. 71 © 2006 Loder, Van Alstyne & Wash, all rights reserved.
Social Planner’s choice of bond Welfare defined: Optimal bond: Always: The socially optimal bond depends only on reader attributes, providing a subsidy if reader surplus is positive and compensation if surplus is negative. It is the ideal Pigouvian tax for homogeneous senders and receivers. 71 © 2006 Loder, Van Alstyne & Wash, all rights reserved.
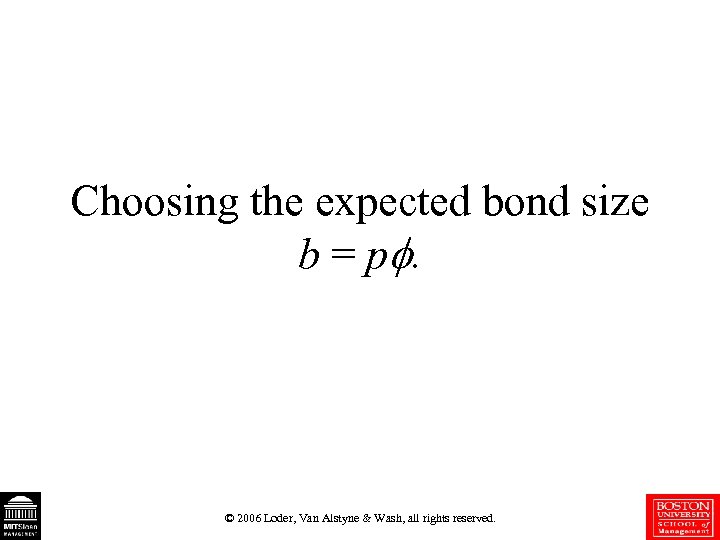 Choosing the expected bond size b = p. © 2006 Loder, Van Alstyne & Wash, all rights reserved.
Choosing the expected bond size b = p. © 2006 Loder, Van Alstyne & Wash, all rights reserved.
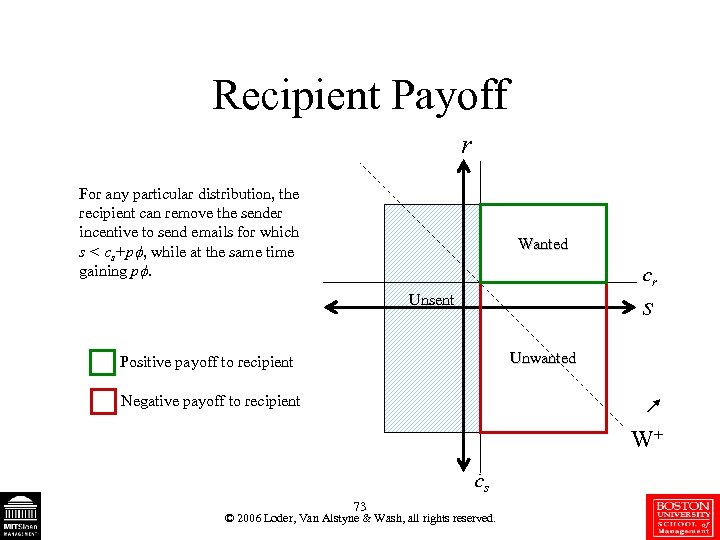 Recipient Payoff r For any particular distribution, the recipient can remove the sender incentive to send emails for which s < cs+p , while at the same time gaining p. Wanted cr s Unsent Unwanted Positive payoff to recipient Negative payoff to recipient W+ cs 73 © 2006 Loder, Van Alstyne & Wash, all rights reserved.
Recipient Payoff r For any particular distribution, the recipient can remove the sender incentive to send emails for which s < cs+p , while at the same time gaining p. Wanted cr s Unsent Unwanted Positive payoff to recipient Negative payoff to recipient W+ cs 73 © 2006 Loder, Van Alstyne & Wash, all rights reserved.
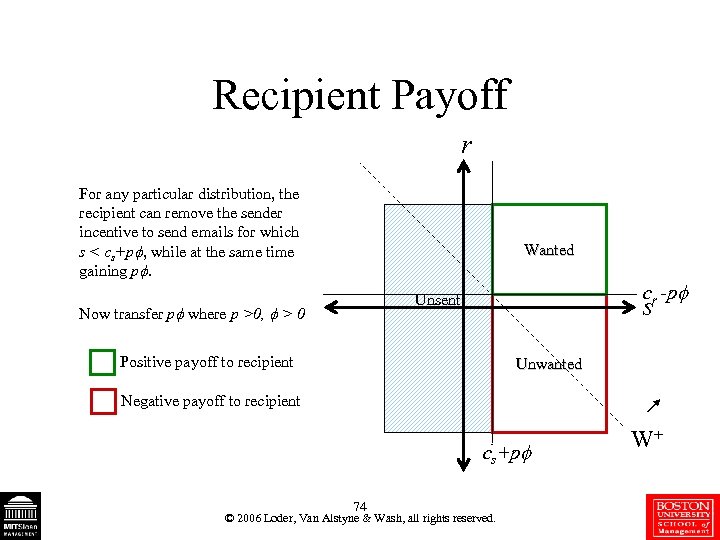 Recipient Payoff r For any particular distribution, the recipient can remove the sender incentive to send emails for which s < cs+p , while at the same time gaining p. Wanted cr -p s Unsent Now transfer p where p >0, > 0 Positive payoff to recipient Unwanted Negative payoff to recipient cs+p 74 © 2006 Loder, Van Alstyne & Wash, all rights reserved. W+
Recipient Payoff r For any particular distribution, the recipient can remove the sender incentive to send emails for which s < cs+p , while at the same time gaining p. Wanted cr -p s Unsent Now transfer p where p >0, > 0 Positive payoff to recipient Unwanted Negative payoff to recipient cs+p 74 © 2006 Loder, Van Alstyne & Wash, all rights reserved. W+
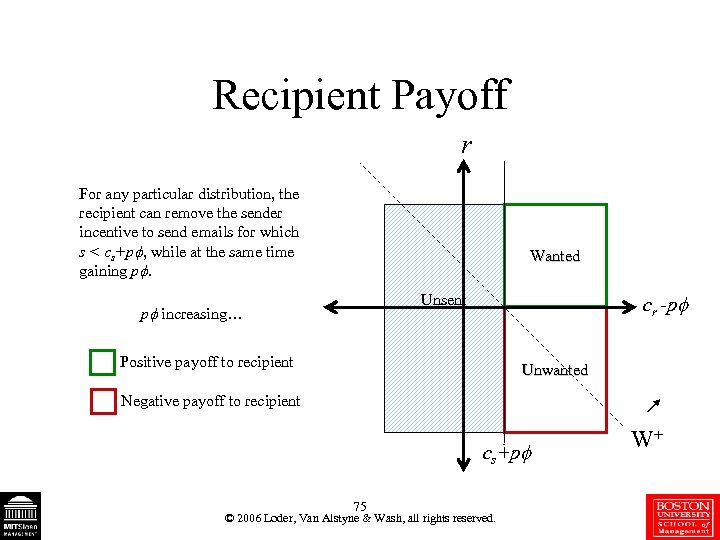 Recipient Payoff r For any particular distribution, the recipient can remove the sender incentive to send emails for which s < cs+p , while at the same time gaining p. Wanted cr -p Unsent p increasing… Positive payoff to recipient Unwanted Negative payoff to recipient cs+p 75 © 2006 Loder, Van Alstyne & Wash, all rights reserved. W+
Recipient Payoff r For any particular distribution, the recipient can remove the sender incentive to send emails for which s < cs+p , while at the same time gaining p. Wanted cr -p Unsent p increasing… Positive payoff to recipient Unwanted Negative payoff to recipient cs+p 75 © 2006 Loder, Van Alstyne & Wash, all rights reserved. W+
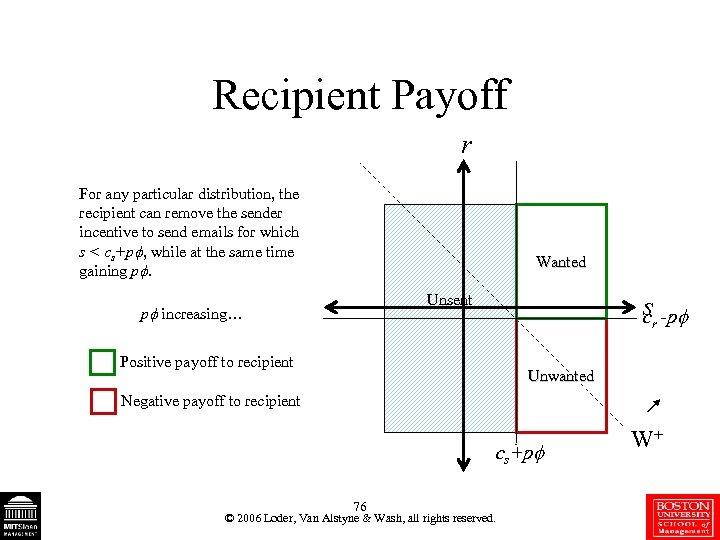 Recipient Payoff r For any particular distribution, the recipient can remove the sender incentive to send emails for which s < cs+p , while at the same time gaining p. Wanted sr -p c Unsent p increasing… Positive payoff to recipient Unwanted Negative payoff to recipient cs+p 76 © 2006 Loder, Van Alstyne & Wash, all rights reserved. W+
Recipient Payoff r For any particular distribution, the recipient can remove the sender incentive to send emails for which s < cs+p , while at the same time gaining p. Wanted sr -p c Unsent p increasing… Positive payoff to recipient Unwanted Negative payoff to recipient cs+p 76 © 2006 Loder, Van Alstyne & Wash, all rights reserved. W+
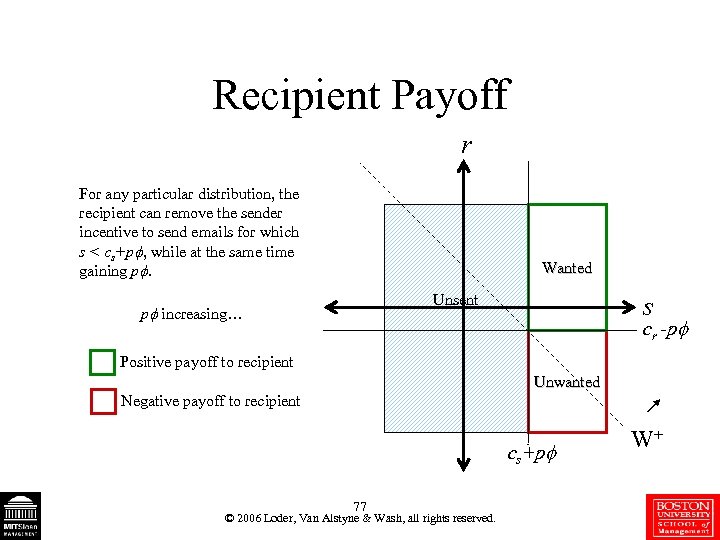 Recipient Payoff r For any particular distribution, the recipient can remove the sender incentive to send emails for which s < cs+p , while at the same time gaining p. Wanted s Unsent p increasing… cr -p Positive payoff to recipient Unwanted Negative payoff to recipient cs+p 77 © 2006 Loder, Van Alstyne & Wash, all rights reserved. W+
Recipient Payoff r For any particular distribution, the recipient can remove the sender incentive to send emails for which s < cs+p , while at the same time gaining p. Wanted s Unsent p increasing… cr -p Positive payoff to recipient Unwanted Negative payoff to recipient cs+p 77 © 2006 Loder, Van Alstyne & Wash, all rights reserved. W+
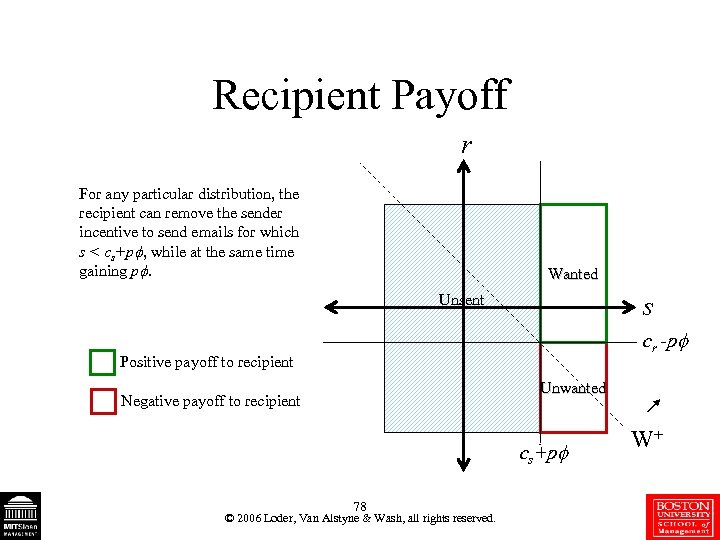 Recipient Payoff r For any particular distribution, the recipient can remove the sender incentive to send emails for which s < cs+p , while at the same time gaining p. Wanted s Unsent cr -p Positive payoff to recipient Unwanted Negative payoff to recipient cs+p 78 © 2006 Loder, Van Alstyne & Wash, all rights reserved. W+
Recipient Payoff r For any particular distribution, the recipient can remove the sender incentive to send emails for which s < cs+p , while at the same time gaining p. Wanted s Unsent cr -p Positive payoff to recipient Unwanted Negative payoff to recipient cs+p 78 © 2006 Loder, Van Alstyne & Wash, all rights reserved. W+
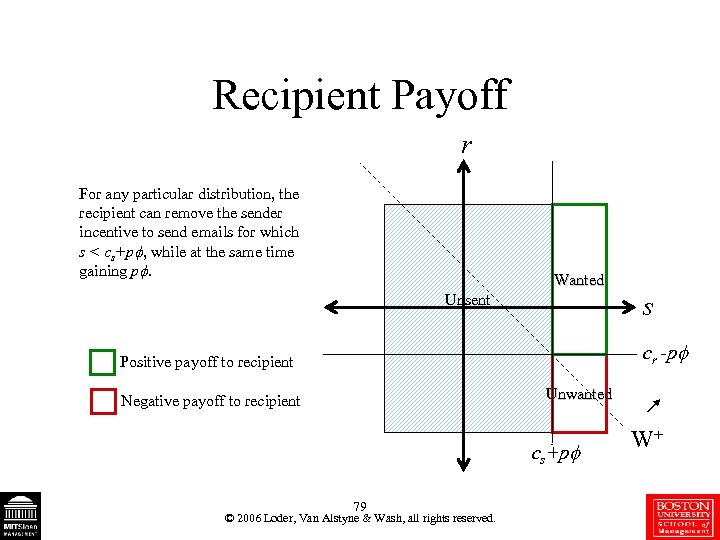 Recipient Payoff r For any particular distribution, the recipient can remove the sender incentive to send emails for which s < cs+p , while at the same time gaining p. Wanted s Unsent cr -p Positive payoff to recipient Unwanted Negative payoff to recipient cs+p 79 © 2006 Loder, Van Alstyne & Wash, all rights reserved. W+
Recipient Payoff r For any particular distribution, the recipient can remove the sender incentive to send emails for which s < cs+p , while at the same time gaining p. Wanted s Unsent cr -p Positive payoff to recipient Unwanted Negative payoff to recipient cs+p 79 © 2006 Loder, Van Alstyne & Wash, all rights reserved. W+
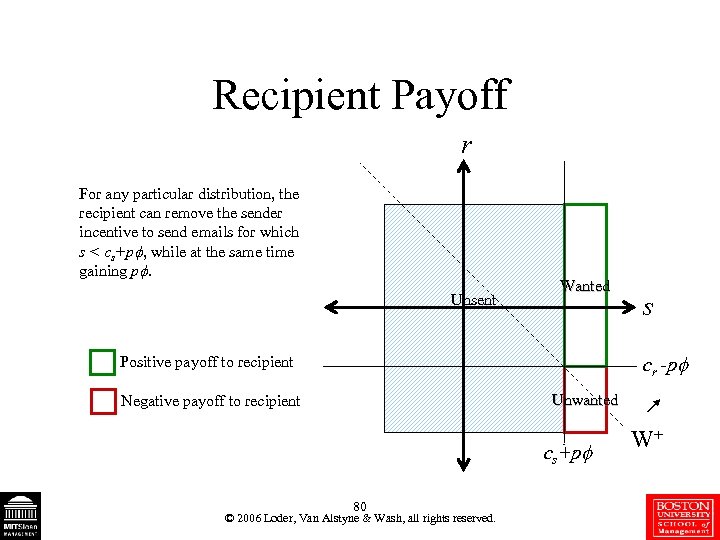 Recipient Payoff r For any particular distribution, the recipient can remove the sender incentive to send emails for which s < cs+p , while at the same time gaining p. Unsent Wanted s cr -p Positive payoff to recipient Unwanted Negative payoff to recipient cs+p 80 © 2006 Loder, Van Alstyne & Wash, all rights reserved. W+
Recipient Payoff r For any particular distribution, the recipient can remove the sender incentive to send emails for which s < cs+p , while at the same time gaining p. Unsent Wanted s cr -p Positive payoff to recipient Unwanted Negative payoff to recipient cs+p 80 © 2006 Loder, Van Alstyne & Wash, all rights reserved. W+
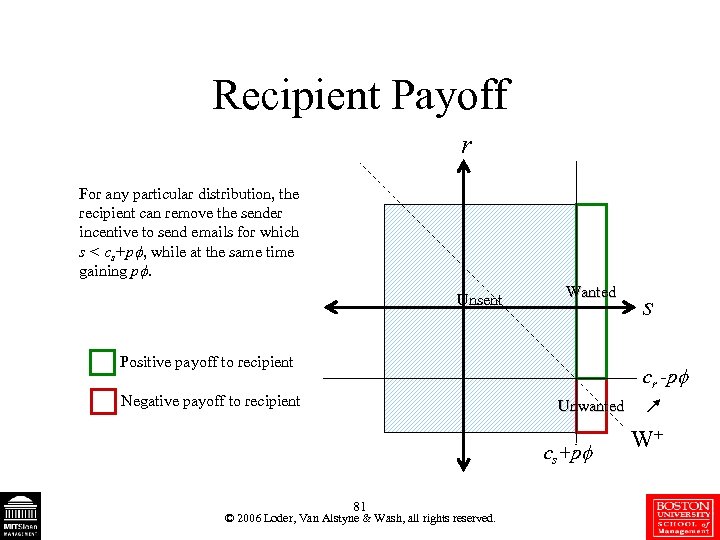 Recipient Payoff r For any particular distribution, the recipient can remove the sender incentive to send emails for which s < cs+p , while at the same time gaining p. Unsent Wanted Positive payoff to recipient s cr -p Negative payoff to recipient Unwanted cs+p 81 © 2006 Loder, Van Alstyne & Wash, all rights reserved. W+
Recipient Payoff r For any particular distribution, the recipient can remove the sender incentive to send emails for which s < cs+p , while at the same time gaining p. Unsent Wanted Positive payoff to recipient s cr -p Negative payoff to recipient Unwanted cs+p 81 © 2006 Loder, Van Alstyne & Wash, all rights reserved. W+
 Consider classes of good G and bad B senders. © 2006 Loder, Van Alstyne & Wash, all rights reserved.
Consider classes of good G and bad B senders. © 2006 Loder, Van Alstyne & Wash, all rights reserved.
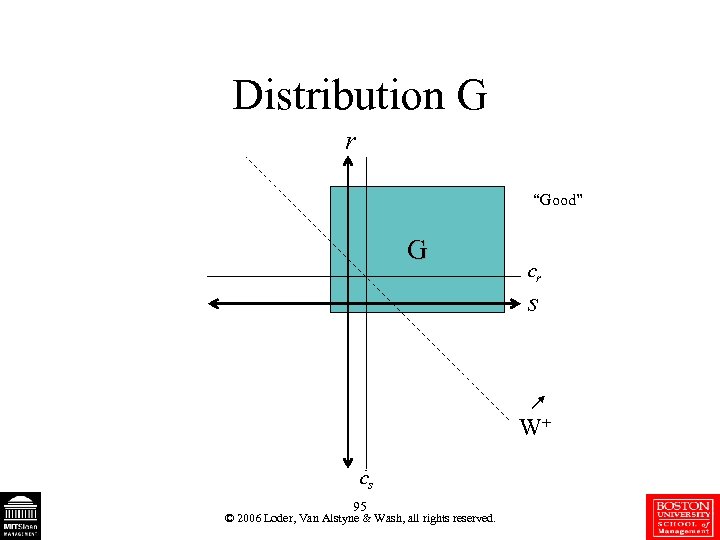 Distribution G r “Good” G cr s W+ cs 95 © 2006 Loder, Van Alstyne & Wash, all rights reserved.
Distribution G r “Good” G cr s W+ cs 95 © 2006 Loder, Van Alstyne & Wash, all rights reserved.
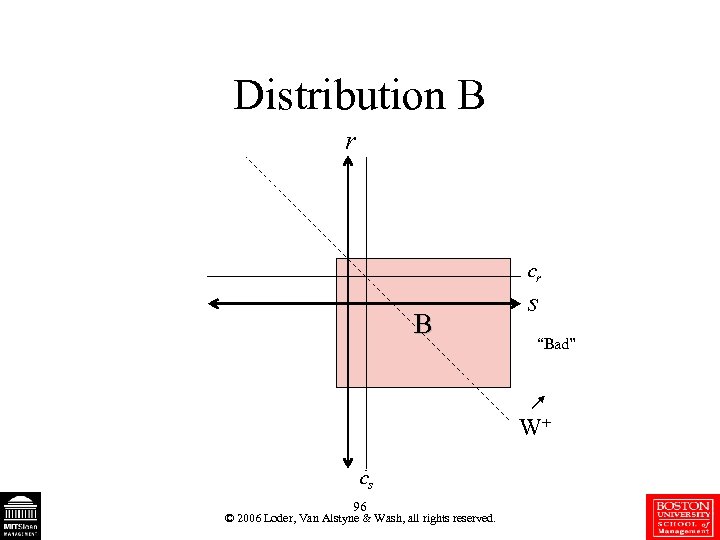 Distribution B r cr B s “Bad” W+ cs 96 © 2006 Loder, Van Alstyne & Wash, all rights reserved.
Distribution B r cr B s “Bad” W+ cs 96 © 2006 Loder, Van Alstyne & Wash, all rights reserved.
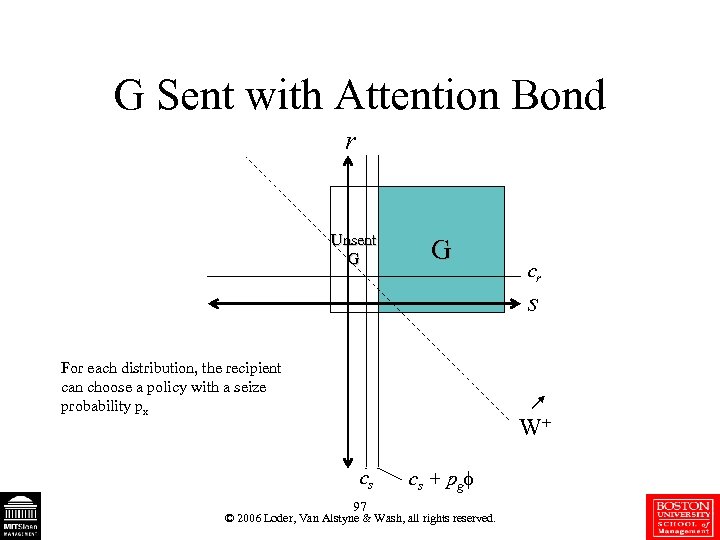 G Sent with Attention Bond r Unsent G G cr s For each distribution, the recipient can choose a policy with a seize probability px W+ cs 97 cs + pg © 2006 Loder, Van Alstyne & Wash, all rights reserved.
G Sent with Attention Bond r Unsent G G cr s For each distribution, the recipient can choose a policy with a seize probability px W+ cs 97 cs + pg © 2006 Loder, Van Alstyne & Wash, all rights reserved.
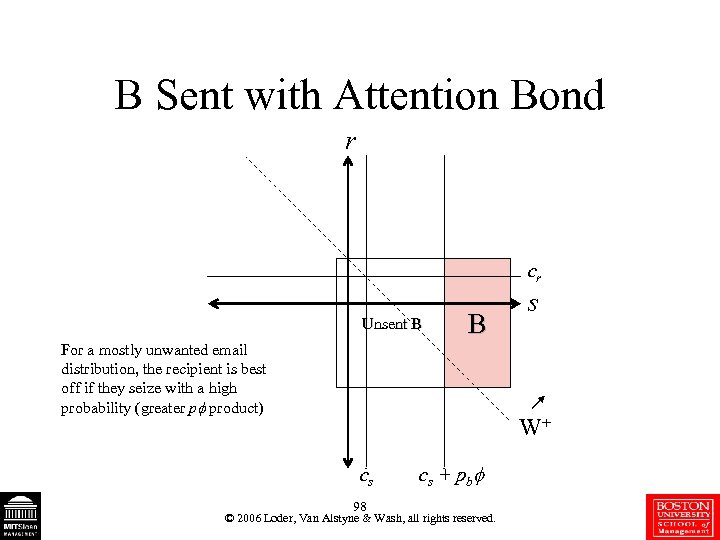 B Sent with Attention Bond r cr Unsent B B For a mostly unwanted email distribution, the recipient is best off if they seize with a high probability (greater p product) s W+ cs 98 cs + pb © 2006 Loder, Van Alstyne & Wash, all rights reserved.
B Sent with Attention Bond r cr Unsent B B For a mostly unwanted email distribution, the recipient is best off if they seize with a high probability (greater p product) s W+ cs 98 cs + pb © 2006 Loder, Van Alstyne & Wash, all rights reserved.
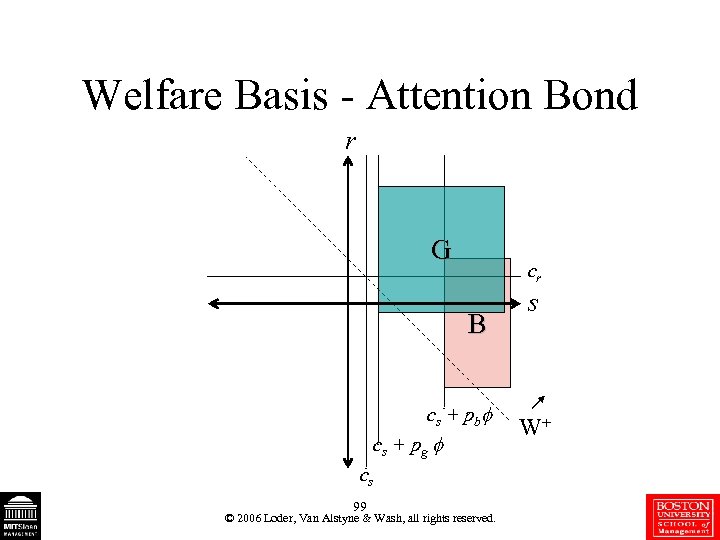 Welfare Basis - Attention Bond r G cr B cs + pb cs + pg cs 99 © 2006 Loder, Van Alstyne & Wash, all rights reserved. s W+
Welfare Basis - Attention Bond r G cr B cs + pb cs + pg cs 99 © 2006 Loder, Van Alstyne & Wash, all rights reserved. s W+
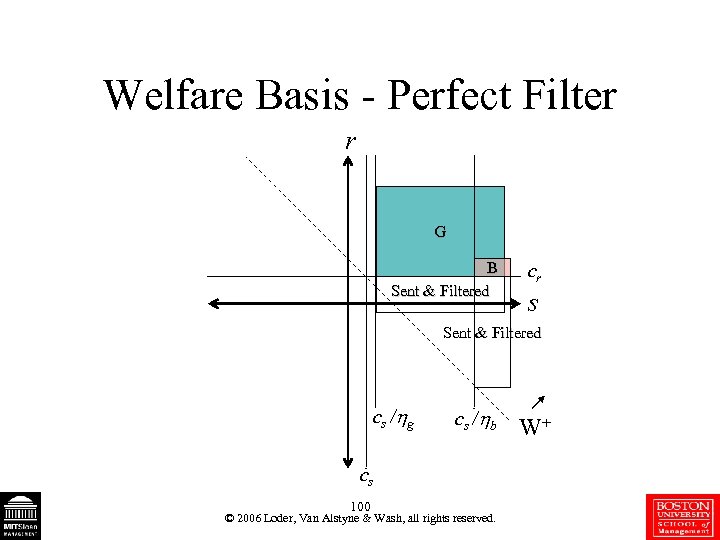 Welfare Basis - Perfect Filter r G B Sent & Filtered cr s Sent & Filtered c s / g c s / b cs 100 © 2006 Loder, Van Alstyne & Wash, all rights reserved. W+
Welfare Basis - Perfect Filter r G B Sent & Filtered cr s Sent & Filtered c s / g c s / b cs 100 © 2006 Loder, Van Alstyne & Wash, all rights reserved. W+
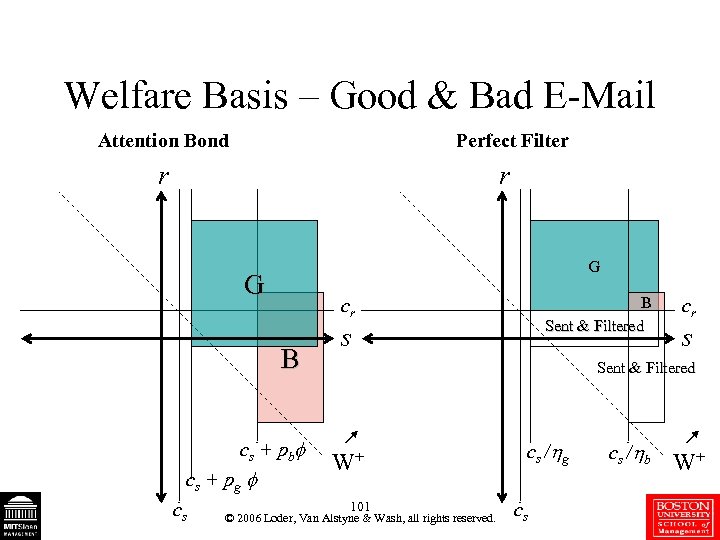 Welfare Basis – Good & Bad E-Mail Attention Bond Perfect Filter r r G G B cs + pb cs + pg cs B Sent & Filtered cr s Sent & Filtered W+ 101 © 2006 Loder, Van Alstyne & Wash, all rights reserved. c s / g cs c s / b W+
Welfare Basis – Good & Bad E-Mail Attention Bond Perfect Filter r r G G B cs + pb cs + pg cs B Sent & Filtered cr s Sent & Filtered W+ 101 © 2006 Loder, Van Alstyne & Wash, all rights reserved. c s / g cs c s / b W+
 How about the perfect Pigouvian tax for heterogenous senders & receivers? © 2006 Loder, Van Alstyne & Wash, all rights reserved.
How about the perfect Pigouvian tax for heterogenous senders & receivers? © 2006 Loder, Van Alstyne & Wash, all rights reserved.
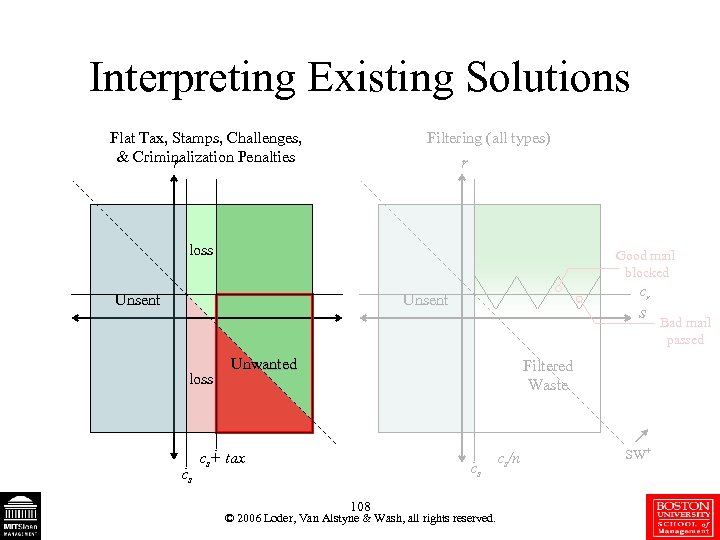 Interpreting Existing Solutions Flat Tax, Stamps, Challenges, & Criminalization Penalties r Filtering (all types) r loss Good mail blocked Unsent cr Unsent loss cs s Unwanted Filtered Waste cs+ tax cs 108 © 2006 Loder, Van Alstyne & Wash, all rights reserved. cs/n SW+ Bad mail passed
Interpreting Existing Solutions Flat Tax, Stamps, Challenges, & Criminalization Penalties r Filtering (all types) r loss Good mail blocked Unsent cr Unsent loss cs s Unwanted Filtered Waste cs+ tax cs 108 © 2006 Loder, Van Alstyne & Wash, all rights reserved. cs/n SW+ Bad mail passed
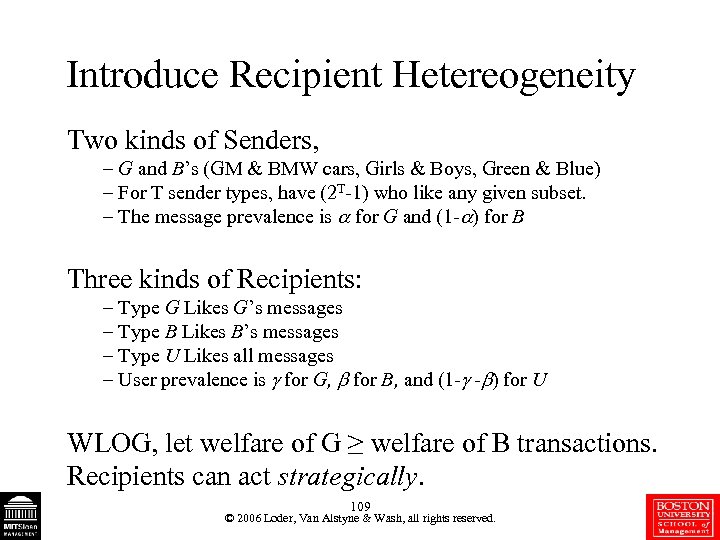 Introduce Recipient Hetereogeneity Two kinds of Senders, – G and B’s (GM & BMW cars, Girls & Boys, Green & Blue) – For T sender types, have (2 T-1) who like any given subset. – The message prevalence is for G and (1 - ) for B Three kinds of Recipients: – Type G Likes G’s messages – Type B Likes B’s messages – Type U Likes all messages – User prevalence is for G, for B, and (1 - - ) for U WLOG, let welfare of G ≥ welfare of B transactions. Recipients can act strategically. 109 © 2006 Loder, Van Alstyne & Wash, all rights reserved.
Introduce Recipient Hetereogeneity Two kinds of Senders, – G and B’s (GM & BMW cars, Girls & Boys, Green & Blue) – For T sender types, have (2 T-1) who like any given subset. – The message prevalence is for G and (1 - ) for B Three kinds of Recipients: – Type G Likes G’s messages – Type B Likes B’s messages – Type U Likes all messages – User prevalence is for G, for B, and (1 - - ) for U WLOG, let welfare of G ≥ welfare of B transactions. Recipients can act strategically. 109 © 2006 Loder, Van Alstyne & Wash, all rights reserved.
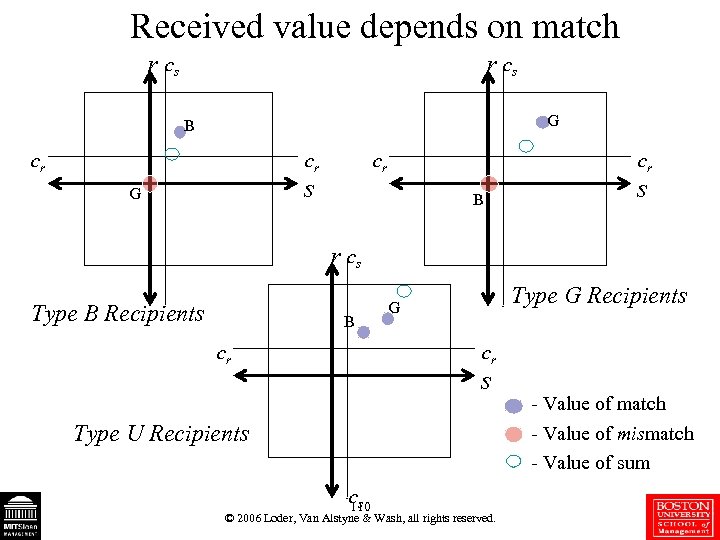 Received value depends on match r cs G B cr cr cr s G cr B s r cs Type B Recipients B cr Type G Recipients G cr s Type U Recipients cs 110 © 2006 Loder, Van Alstyne & Wash, all rights reserved. - Value of match - Value of mismatch - Value of sum
Received value depends on match r cs G B cr cr cr s G cr B s r cs Type B Recipients B cr Type G Recipients G cr s Type U Recipients cs 110 © 2006 Loder, Van Alstyne & Wash, all rights reserved. - Value of match - Value of mismatch - Value of sum
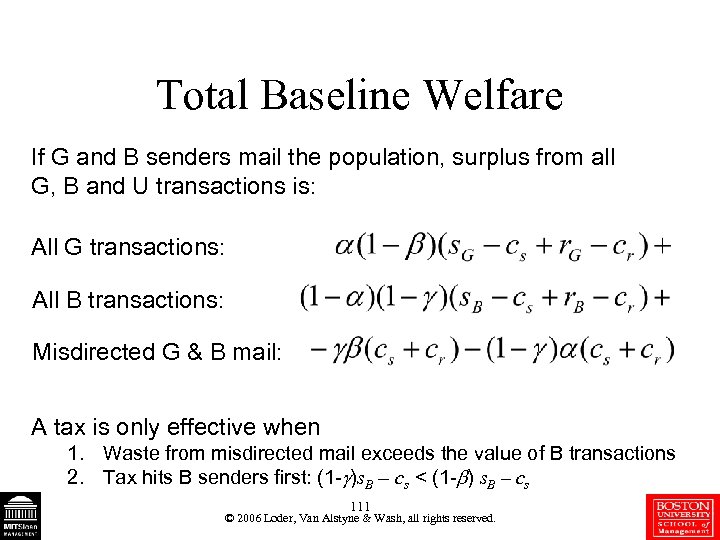 Total Baseline Welfare If G and B senders mail the population, surplus from all G, B and U transactions is: All G transactions: All B transactions: Misdirected G & B mail: A tax is only effective when 1. Waste from misdirected mail exceeds the value of B transactions 2. Tax hits B senders first: (1 - )s. B – cs < (1 - ) s. B – cs 111 © 2006 Loder, Van Alstyne & Wash, all rights reserved.
Total Baseline Welfare If G and B senders mail the population, surplus from all G, B and U transactions is: All G transactions: All B transactions: Misdirected G & B mail: A tax is only effective when 1. Waste from misdirected mail exceeds the value of B transactions 2. Tax hits B senders first: (1 - )s. B – cs < (1 - ) s. B – cs 111 © 2006 Loder, Van Alstyne & Wash, all rights reserved.
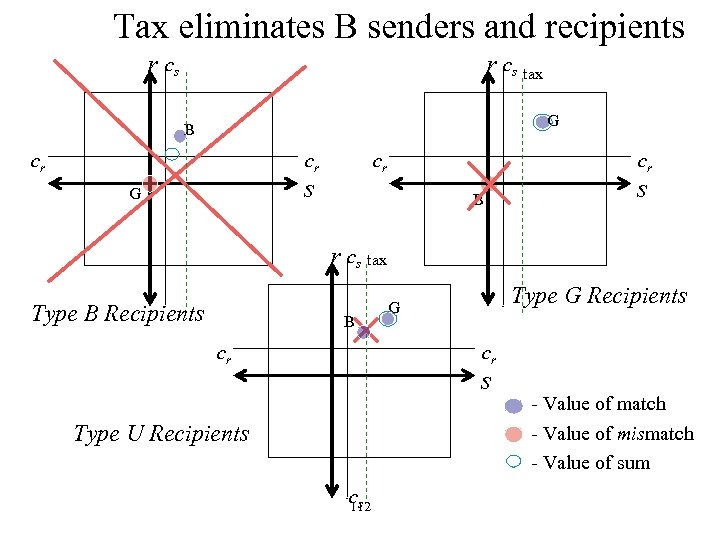 Tax eliminates B senders and recipients r cs tax G B cr cr cr s G cr B s r cs tax Type B Recipients B cr Type G Recipients G cr s Type U Recipients cs 112 - Value of match - Value of mismatch - Value of sum
Tax eliminates B senders and recipients r cs tax G B cr cr cr s G cr B s r cs tax Type B Recipients B cr Type G Recipients G cr s Type U Recipients cs 112 - Value of match - Value of mismatch - Value of sum
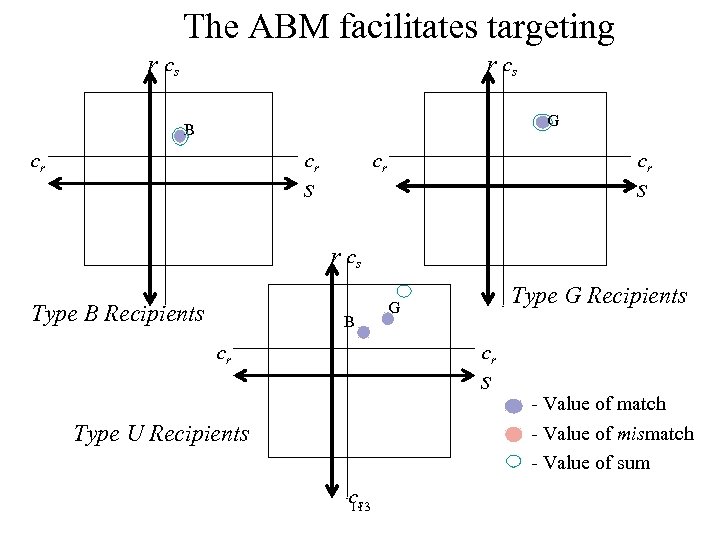 The ABM facilitates targeting r cs G B cr cr cr s r cs Type B Recipients B cr Type G Recipients G cr s Type U Recipients cs 113 - Value of match - Value of mismatch - Value of sum
The ABM facilitates targeting r cs G B cr cr cr s r cs Type B Recipients B cr Type G Recipients G cr s Type U Recipients cs 113 - Value of match - Value of mismatch - Value of sum
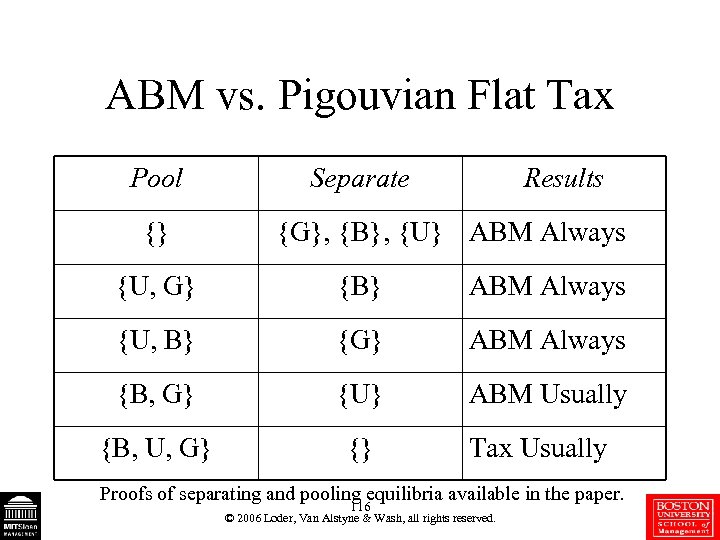 ABM vs. Pigouvian Flat Tax Pool {} Separate Results {G}, {B}, {U} ABM Always {U, G} {B} ABM Always {U, B} {G} ABM Always {B, G} {U} ABM Usually {B, U, G} {} Tax Usually Proofs of separating and pooling equilibria available in the paper. 116 © 2006 Loder, Van Alstyne & Wash, all rights reserved.
ABM vs. Pigouvian Flat Tax Pool {} Separate Results {G}, {B}, {U} ABM Always {U, G} {B} ABM Always {U, B} {G} ABM Always {B, G} {U} ABM Usually {B, U, G} {} Tax Usually Proofs of separating and pooling equilibria available in the paper. 116 © 2006 Loder, Van Alstyne & Wash, all rights reserved.
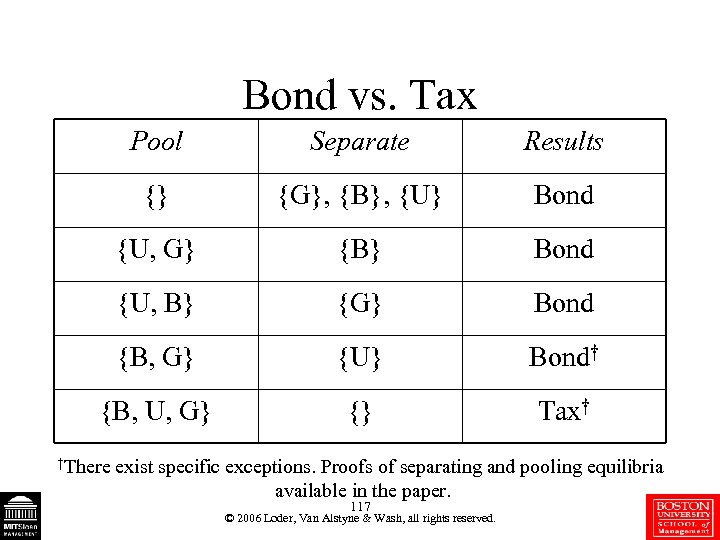 Bond vs. Tax Pool Separate Results {} {G}, {B}, {U} Bond {U, G} {B} Bond {U, B} {G} Bond {B, G} {U} Bond† {B, U, G} {} Tax† †There exist specific exceptions. Proofs of separating and pooling equilibria available in the paper. 117 © 2006 Loder, Van Alstyne & Wash, all rights reserved.
Bond vs. Tax Pool Separate Results {} {G}, {B}, {U} Bond {U, G} {B} Bond {U, B} {G} Bond {B, G} {U} Bond† {B, U, G} {} Tax† †There exist specific exceptions. Proofs of separating and pooling equilibria available in the paper. 117 © 2006 Loder, Van Alstyne & Wash, all rights reserved.
 ABM • Proposition: If recipient types choose distinct bond values, then the ABM results in first-best welfare. • Intuition: No unnecessary costs from mistargetting, all transactions complete, separating equilibrium. • Conditions: When bond values are low relative to message values – (test condition inequalities available) 118 © 2006 Loder, Van Alstyne & Wash, all rights reserved.
ABM • Proposition: If recipient types choose distinct bond values, then the ABM results in first-best welfare. • Intuition: No unnecessary costs from mistargetting, all transactions complete, separating equilibrium. • Conditions: When bond values are low relative to message values – (test condition inequalities available) 118 © 2006 Loder, Van Alstyne & Wash, all rights reserved.
 ABM • Proposition: If either b. B or b. G are distinct, then welfare under the ABM dominates that under a flat tax. • Intuition: Choosing to pool internalizes the costs of mistargetting caused by pooling, else you could choose “limit bonds” 119 © 2006 Loder, Van Alstyne & Wash, all rights reserved.
ABM • Proposition: If either b. B or b. G are distinct, then welfare under the ABM dominates that under a flat tax. • Intuition: Choosing to pool internalizes the costs of mistargetting caused by pooling, else you could choose “limit bonds” 119 © 2006 Loder, Van Alstyne & Wash, all rights reserved.
 Welfare Analysis • Proposition: Social welfare under attention bonds exceeds that under a tax, unless type B recipients forgo B messages solely to poach G bonds. • Intuition: If either {B} or {G} separate then targeting improves sufficient to improve welfare. • If {B, G} pool, both must consent. G recipients can always separate by choosing a “limit bond. ” – If B senders mail to a {G, B} pool, B transactions value must exceed the waste. A tax destroys welfare. – If B senders do NOT mail to a {G, B} pool, mail from G to B creates uncompensated waste. A tax improves welfare. 120 © 2006 Loder, Van Alstyne & Wash, all rights reserved.
Welfare Analysis • Proposition: Social welfare under attention bonds exceeds that under a tax, unless type B recipients forgo B messages solely to poach G bonds. • Intuition: If either {B} or {G} separate then targeting improves sufficient to improve welfare. • If {B, G} pool, both must consent. G recipients can always separate by choosing a “limit bond. ” – If B senders mail to a {G, B} pool, B transactions value must exceed the waste. A tax destroys welfare. – If B senders do NOT mail to a {G, B} pool, mail from G to B creates uncompensated waste. A tax improves welfare. 120 © 2006 Loder, Van Alstyne & Wash, all rights reserved.
 Why Not Seize the Bond? • First Contact Moral Hazard • Releasing the bond is also a signal – Credibly distinguish your type in any pooling equilibrium. In computer science vernacular, to separate yourself from a “honeypot. ” – Investment in reputation, Competition, Bi-directional communications, etc. 122 © 2006 Loder, Van Alstyne & Wash, all rights reserved.
Why Not Seize the Bond? • First Contact Moral Hazard • Releasing the bond is also a signal – Credibly distinguish your type in any pooling equilibrium. In computer science vernacular, to separate yourself from a “honeypot. ” – Investment in reputation, Competition, Bi-directional communications, etc. 122 © 2006 Loder, Van Alstyne & Wash, all rights reserved.
 Information Entering the Market • Recipient: bond choice bi serves as a (weak) price signal of recipient type. • Sender: posting bond bi serves as a credible signal of sender belief in a match. • Recipient: For pooling equilibria, refund i =pibi is a credible signal of a match. 123 © 2006 Loder, Van Alstyne & Wash, all rights reserved.
Information Entering the Market • Recipient: bond choice bi serves as a (weak) price signal of recipient type. • Sender: posting bond bi serves as a credible signal of sender belief in a match. • Recipient: For pooling equilibria, refund i =pibi is a credible signal of a match. 123 © 2006 Loder, Van Alstyne & Wash, all rights reserved.
 Adoption, Infrastructure & Policy Issues © 2006 Loder, Van Alstyne & Wash, all rights reserved.
Adoption, Infrastructure & Policy Issues © 2006 Loder, Van Alstyne & Wash, all rights reserved.
 Consider Advantages for Commerce: Direct Marketing • Cheaper than traditional mail channels • Receiver gets the benefit, not printer or mailer, no environmental waste. • More information & preference feedback than TV, Radio, Snail Mail, or Magazines • Lists are self-cleaning 127 © 2006 Loder, Van Alstyne & Wash, all rights reserved.
Consider Advantages for Commerce: Direct Marketing • Cheaper than traditional mail channels • Receiver gets the benefit, not printer or mailer, no environmental waste. • More information & preference feedback than TV, Radio, Snail Mail, or Magazines • Lists are self-cleaning 127 © 2006 Loder, Van Alstyne & Wash, all rights reserved.
 Consider Advantages for Users When someone outside the ABM network 1 st reaches someone inside, they get a challenge saying “adopt this and get”: 1. Your message delivered 2. Your spam eliminated 3. No need to do this again ever for anyone in the network 4. And a free bank account where marketers can drop nickels. 128 © 2006 Loder, Van Alstyne & Wash, all rights reserved.
Consider Advantages for Users When someone outside the ABM network 1 st reaches someone inside, they get a challenge saying “adopt this and get”: 1. Your message delivered 2. Your spam eliminated 3. No need to do this again ever for anyone in the network 4. And a free bank account where marketers can drop nickels. 128 © 2006 Loder, Van Alstyne & Wash, all rights reserved.
 Rebuttals © 2006 Loder, Van Alstyne & Wash, all rights reserved.
Rebuttals © 2006 Loder, Van Alstyne & Wash, all rights reserved.
 Obj: Great! I’ll set up a honeypot and retire. Q: As a marketer, what’s your incentive to indiscriminately mail bonds to buyers in the presence of honeypots? A: None. Rather you’ll target bonded messages to prospective buyers with the highest interest. This is exactly what should happen. Forcing marketers to internalize the costs of wasteful messages causes them to produce less waste. 134 © 2006 Loder, Van Alstyne & Wash, all rights reserved.
Obj: Great! I’ll set up a honeypot and retire. Q: As a marketer, what’s your incentive to indiscriminately mail bonds to buyers in the presence of honeypots? A: None. Rather you’ll target bonded messages to prospective buyers with the highest interest. This is exactly what should happen. Forcing marketers to internalize the costs of wasteful messages causes them to produce less waste. 134 © 2006 Loder, Van Alstyne & Wash, all rights reserved.
 Obj: If you can spoof it won’t work; if you can’t spoof you don’t need it. • False on both counts. • If you can spoof, all messages look like 1 st contact. • If you can not spoof, do not confuse (i) verifying an address with (ii) authenticating a user i. Cannot work (see “Social Cost of Cheap Pseudonyms”). ii. Undesirable! You lose Pentagon Papers, Watergate, Enron whistleblowing, Halloween document… any free speech where the sender doesn’t want to be identified! 135 © 2006 Loder, Van Alstyne & Wash, all rights reserved.
Obj: If you can spoof it won’t work; if you can’t spoof you don’t need it. • False on both counts. • If you can spoof, all messages look like 1 st contact. • If you can not spoof, do not confuse (i) verifying an address with (ii) authenticating a user i. Cannot work (see “Social Cost of Cheap Pseudonyms”). ii. Undesirable! You lose Pentagon Papers, Watergate, Enron whistleblowing, Halloween document… any free speech where the sender doesn’t want to be identified! 135 © 2006 Loder, Van Alstyne & Wash, all rights reserved.
 Obj: Doesn’t risk limit free speech? • Free speech is the only criterion on which no intervention beats bonds, filters and taxes. • Perfect Filter: given 74% think political & non-profit speech is spam, much never gets through. • Perfect Tax: always collected ex ante vs. 74% who collect under ABM – and always get through. Would you want Yahoo!, AOL-Time-Warner, or Microsoft determining the content you receive? The ABM is completely decentralized and content neutral; no one person, institution, or policy determines the content you hear. Legitimate senders face lower barriers than under filters or taxes. 136 © 2006 Loder, Van Alstyne & Wash, all rights reserved.
Obj: Doesn’t risk limit free speech? • Free speech is the only criterion on which no intervention beats bonds, filters and taxes. • Perfect Filter: given 74% think political & non-profit speech is spam, much never gets through. • Perfect Tax: always collected ex ante vs. 74% who collect under ABM – and always get through. Would you want Yahoo!, AOL-Time-Warner, or Microsoft determining the content you receive? The ABM is completely decentralized and content neutral; no one person, institution, or policy determines the content you hear. Legitimate senders face lower barriers than under filters or taxes. 136 © 2006 Loder, Van Alstyne & Wash, all rights reserved.
 Obj: If 65% of spam is sent by infected zombies, fraud creates a user nightmare! 137 © 2006 Loder, Van Alstyne & Wash, all rights reserved.
Obj: If 65% of spam is sent by infected zombies, fraud creates a user nightmare! 137 © 2006 Loder, Van Alstyne & Wash, all rights reserved.
 The FTC weighs in 139 © 2006 Loder, Van Alstyne & Wash, all rights reserved.
The FTC weighs in 139 © 2006 Loder, Van Alstyne & Wash, all rights reserved.
 Address the problem before it starts! • In economic terms, this is a moral hazard problem. • Not bearing the costs of the waste their infected machines create, owners are insufficiently motivated (or able) to clean them. • We need fraud protection… Just like credit cards, ISPs can afford to offer say $5 insurance provided ISPs can keep users’ antiviral software up to date. Attacks are detected faster. Virus propagation slows. 140 © 2006 Loder, Van Alstyne & Wash, all rights reserved.
Address the problem before it starts! • In economic terms, this is a moral hazard problem. • Not bearing the costs of the waste their infected machines create, owners are insufficiently motivated (or able) to clean them. • We need fraud protection… Just like credit cards, ISPs can afford to offer say $5 insurance provided ISPs can keep users’ antiviral software up to date. Attacks are detected faster. Virus propagation slows. 140 © 2006 Loder, Van Alstyne & Wash, all rights reserved.
 Obj: If 65% of spam is sent by infected zombies, fraud creates a user nightmare! • In economic terms, this is a moral hazard problem. • Not bearing the costs of the waste their infected machines create, owners are insufficiently motivated (or able) to clean them. • We need fraud protection… Just like credit cards, ISPs can afford to offer say $5 insurance provided ISPs can keep users’ antiviral software up to date. 141 © 2006 Loder, Van Alstyne & Wash, all rights reserved.
Obj: If 65% of spam is sent by infected zombies, fraud creates a user nightmare! • In economic terms, this is a moral hazard problem. • Not bearing the costs of the waste their infected machines create, owners are insufficiently motivated (or able) to clean them. • We need fraud protection… Just like credit cards, ISPs can afford to offer say $5 insurance provided ISPs can keep users’ antiviral software up to date. 141 © 2006 Loder, Van Alstyne & Wash, all rights reserved.
 Policy & Enforcement Issues • Applicable to Do-Not-Call / Do-Not-Spam lists. • Need consumer fraud protection analogous to that for Credit Cards • Severe penalties for spoofing and misuse of 3 rd party IDs • Need escrow account clearing analogous to Automated Clearing House (ACH) for checks • Need pro-competitive open standards • Need for privacy regulation on transactions • Boon to commerce: replace threat of communications veto with option for fruitful exchange 142 © 2006 Loder, Van Alstyne & Wash, all rights reserved.
Policy & Enforcement Issues • Applicable to Do-Not-Call / Do-Not-Spam lists. • Need consumer fraud protection analogous to that for Credit Cards • Severe penalties for spoofing and misuse of 3 rd party IDs • Need escrow account clearing analogous to Automated Clearing House (ACH) for checks • Need pro-competitive open standards • Need for privacy regulation on transactions • Boon to commerce: replace threat of communications veto with option for fruitful exchange 142 © 2006 Loder, Van Alstyne & Wash, all rights reserved.
 Additional Social Benefits • Direct marketing – – • • Cheaper than traditional mail channels Receiver gets the benefit, not printer and mailer Provides information feedback & self-cleaning lists Avoids harmful reputation effects Recipients have reason to publish contact information, not hide it Shifts arms race to crypto. Permits communication otherwise filtered (e. g. political speech) Allows anonymous and whistleblower communication not possible with strong identity systems. Tailors to an individual’s unique preferences. Reclaims the value of your address for you rather than the marketers. Helps you get off any list you don’t want to be on. 143 © 2006 Loder, Van Alstyne & Wash, all rights reserved.
Additional Social Benefits • Direct marketing – – • • Cheaper than traditional mail channels Receiver gets the benefit, not printer and mailer Provides information feedback & self-cleaning lists Avoids harmful reputation effects Recipients have reason to publish contact information, not hide it Shifts arms race to crypto. Permits communication otherwise filtered (e. g. political speech) Allows anonymous and whistleblower communication not possible with strong identity systems. Tailors to an individual’s unique preferences. Reclaims the value of your address for you rather than the marketers. Helps you get off any list you don’t want to be on. 143 © 2006 Loder, Van Alstyne & Wash, all rights reserved.
 Conclusions • Screening action of bond forces senders to reveal their intentions. • Bond size & seizure functions as signal to senders. • Creates possibility of greater trade volume, with both parties wanting to participate -> win-win communication. • Facilitating wealth transfers benefits readers more than unilateral veto. Can beat a Perfect Filter & Perfect Tax. • Shifts the arms-race to crypto • Content neutral and decentralized with respect to free speech. • Returns control of the mailbox to its owner • Can reduce spread of viruses and spam zombies 144 © 2006 Loder, Van Alstyne & Wash, all rights reserved.
Conclusions • Screening action of bond forces senders to reveal their intentions. • Bond size & seizure functions as signal to senders. • Creates possibility of greater trade volume, with both parties wanting to participate -> win-win communication. • Facilitating wealth transfers benefits readers more than unilateral veto. Can beat a Perfect Filter & Perfect Tax. • Shifts the arms-race to crypto • Content neutral and decentralized with respect to free speech. • Returns control of the mailbox to its owner • Can reduce spread of viruses and spam zombies 144 © 2006 Loder, Van Alstyne & Wash, all rights reserved.
 Concluding Remarks • Define “spam” as information pollution. • Property rights then provide price signals and let one side purchase a fraction of the other side’s call externality. • Revealed information can potentially include (i) recipient type (ii) sender type (iii) successful 3 rd party match (not modeled). • Taxes and filters, in contrast, block communication and provide no information to the market. Filters offer no sidepayments. • Side-payments can cause recipients to act strategically. • Combined with a 2 -sided insurance market, can reduce spread of viruses and spam zombies 145 © 2006 Loder, Van Alstyne & Wash, all rights reserved.
Concluding Remarks • Define “spam” as information pollution. • Property rights then provide price signals and let one side purchase a fraction of the other side’s call externality. • Revealed information can potentially include (i) recipient type (ii) sender type (iii) successful 3 rd party match (not modeled). • Taxes and filters, in contrast, block communication and provide no information to the market. Filters offer no sidepayments. • Side-payments can cause recipients to act strategically. • Combined with a 2 -sided insurance market, can reduce spread of viruses and spam zombies 145 © 2006 Loder, Van Alstyne & Wash, all rights reserved.
 Questions? For further info see: 1. “An Economic Response to Unsolicited Communication, ” Loder, Van Alstyne, Wash. http: //bepress. com 2. Popular article – on request. 146 © 2006 Loder, Van Alstyne & Wash, all rights reserved.
Questions? For further info see: 1. “An Economic Response to Unsolicited Communication, ” Loder, Van Alstyne, Wash. http: //bepress. com 2. Popular article – on request. 146 © 2006 Loder, Van Alstyne & Wash, all rights reserved.


