 An Authentication and Authorization Infrastructure: the PAPI System
An Authentication and Authorization Infrastructure: the PAPI System
 Index • An approximation to the solution • PAPI Architecture • JAVA – JWS • Possible Scenarios • Future works
Index • An approximation to the solution • PAPI Architecture • JAVA – JWS • Possible Scenarios • Future works
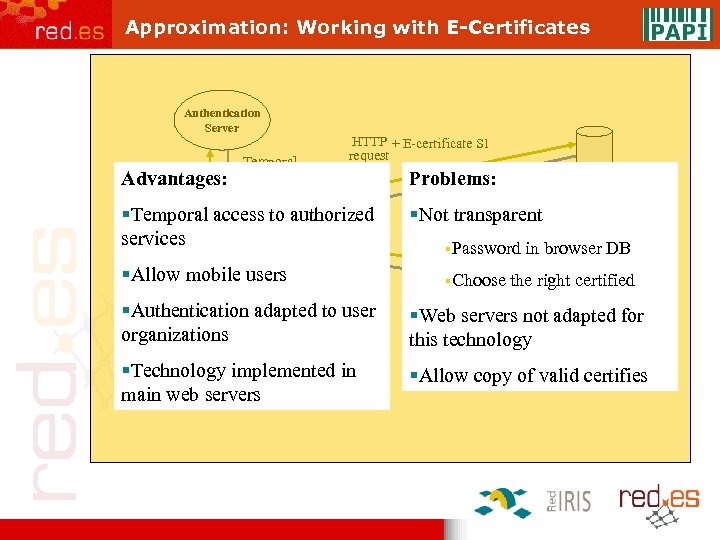 Approximation: Working with E-Certificates Authentication Server Temporal Authentication Advantages: E-certificates data HTTP + E-certificate S 1 request Web §Temporal access to authorized browser services E-certificate S 1 E-certificate users §Allow mobile. S 2 E-certificate S 3 Problems: Web page Web Server S 1 §Not transparent HTTP + E-certificate S 2 request §Password in browser §Choose Web page DB the right certified §Authentication adapted to user organizations Web §Web servers not adapted for Server S 2 this technology §Technology implemented in main web servers §Allow copy of valid certifies
Approximation: Working with E-Certificates Authentication Server Temporal Authentication Advantages: E-certificates data HTTP + E-certificate S 1 request Web §Temporal access to authorized browser services E-certificate S 1 E-certificate users §Allow mobile. S 2 E-certificate S 3 Problems: Web page Web Server S 1 §Not transparent HTTP + E-certificate S 2 request §Password in browser §Choose Web page DB the right certified §Authentication adapted to user organizations Web §Web servers not adapted for Server S 2 this technology §Technology implemented in main web servers §Allow copy of valid certifies
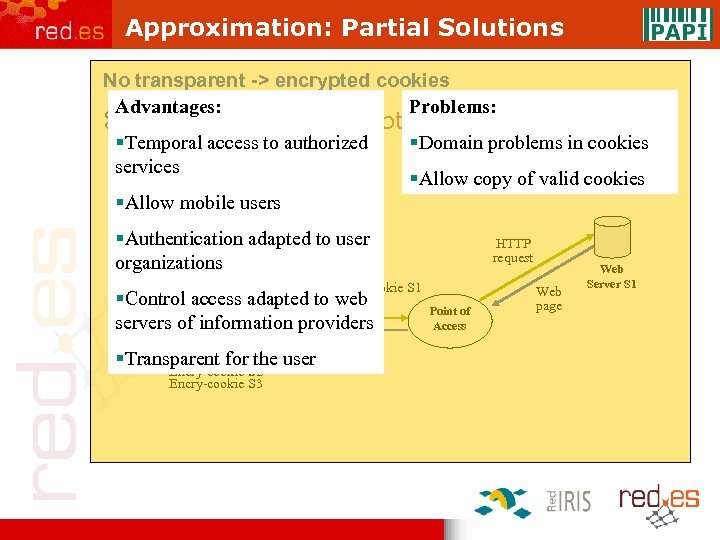 Approximation: Partial Solutions No transparent -> encrypted cookies Problems: Advantages: z Web servers not adapted -> Points of Access §Temporal access to authorized services Authentication Server §Domain problems in cookies §Allow copy of valid cookies §Allow mobile users Temporal §Authentication adapted to user Authentication Encrypt-cookies organizations data HTTP + Encry-cookie S 1 request to web adapted §Control access Web servers of browser information providers Encry-cookie the §Transparent for. S 1 user Encry-cookie S 2 Encry-cookie S 3 Web page HTTP request Point of Access Web page Web Server S 1
Approximation: Partial Solutions No transparent -> encrypted cookies Problems: Advantages: z Web servers not adapted -> Points of Access §Temporal access to authorized services Authentication Server §Domain problems in cookies §Allow copy of valid cookies §Allow mobile users Temporal §Authentication adapted to user Authentication Encrypt-cookies organizations data HTTP + Encry-cookie S 1 request to web adapted §Control access Web servers of browser information providers Encry-cookie the §Transparent for. S 1 user Encry-cookie S 2 Encry-cookie S 3 Web page HTTP request Point of Access Web page Web Server S 1
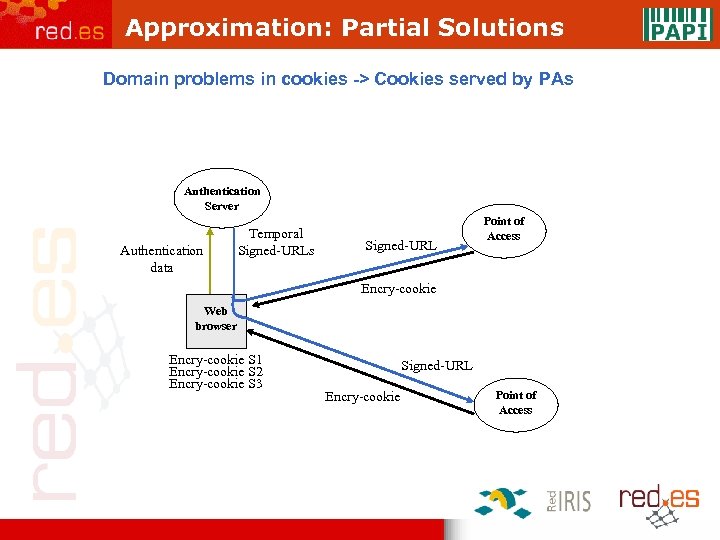 Approximation: Partial Solutions Domain problems in cookies -> Cookies served by PAs Authentication Server Authentication data Temporal Signed-URLs Signed-URL Point of Access Encry-cookie Web browser Encry-cookie S 1 Encry-cookie S 2 Encry-cookie S 3 Signed-URL Encry-cookie Point of Access
Approximation: Partial Solutions Domain problems in cookies -> Cookies served by PAs Authentication Server Authentication data Temporal Signed-URLs Signed-URL Point of Access Encry-cookie Web browser Encry-cookie S 1 Encry-cookie S 2 Encry-cookie S 3 Signed-URL Encry-cookie Point of Access
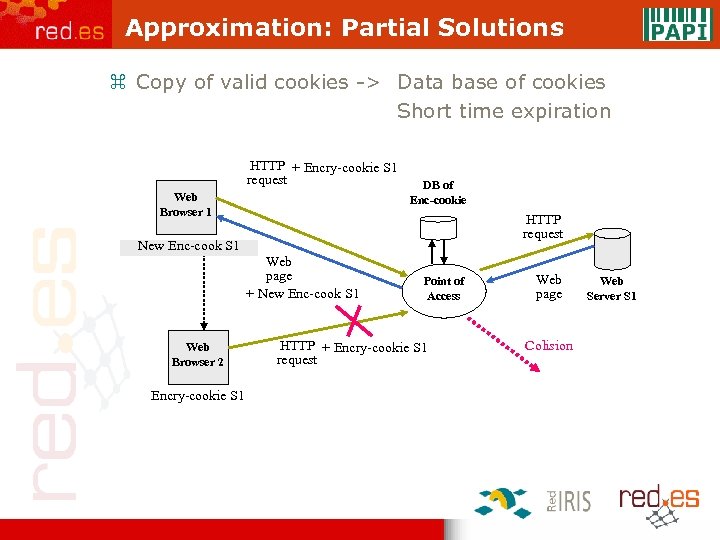 Approximation: Partial Solutions z Copy of valid cookies -> Data base of cookies Short time expiration HTTP + Encry-cookie S 1 request Web Browser 1 DB of Enc-cookie HTTP request New Enc-cook S 1 Encry-cookie S 1 Web page + New Enc-cook S 1 Web Browser 2 Encry-cookie S 1 Point of Access HTTP + Encry-cookie S 1 request Web page Colision Web Server S 1
Approximation: Partial Solutions z Copy of valid cookies -> Data base of cookies Short time expiration HTTP + Encry-cookie S 1 request Web Browser 1 DB of Enc-cookie HTTP request New Enc-cook S 1 Encry-cookie S 1 Web page + New Enc-cook S 1 Web Browser 2 Encry-cookie S 1 Point of Access HTTP + Encry-cookie S 1 request Web page Colision Web Server S 1
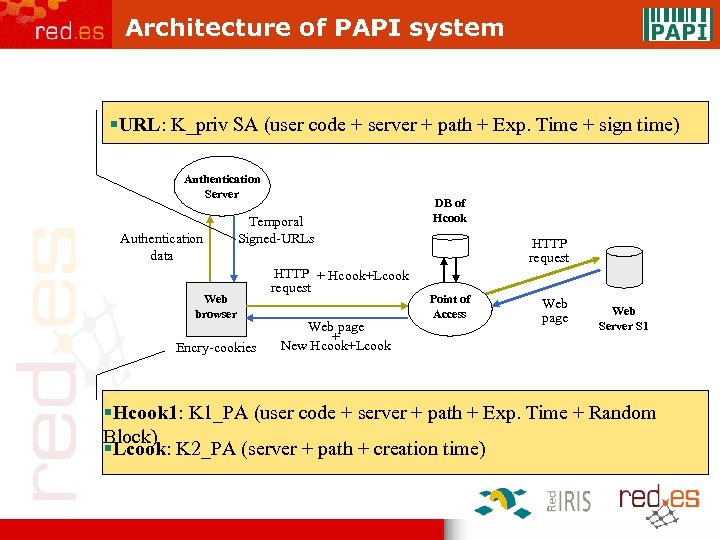 Architecture of PAPI system §URL: K_priv SA (user code + server + path + Exp. Time + sign time) Authentication Server Authentication data Temporal Signed-URLs Web browser Encry-cookies HTTP + Hcook+Lcook request Web page + New Hcook+Lcook DB of Hcook HTTP request Point of Access Web page Web Server S 1 §Hcook 1: K 1_PA (user code + server + path + Exp. Time + Random Block) §Lcook: K 2_PA (server + path + creation time)
Architecture of PAPI system §URL: K_priv SA (user code + server + path + Exp. Time + sign time) Authentication Server Authentication data Temporal Signed-URLs Web browser Encry-cookies HTTP + Hcook+Lcook request Web page + New Hcook+Lcook DB of Hcook HTTP request Point of Access Web page Web Server S 1 §Hcook 1: K 1_PA (user code + server + path + Exp. Time + Random Block) §Lcook: K 2_PA (server + path + creation time)
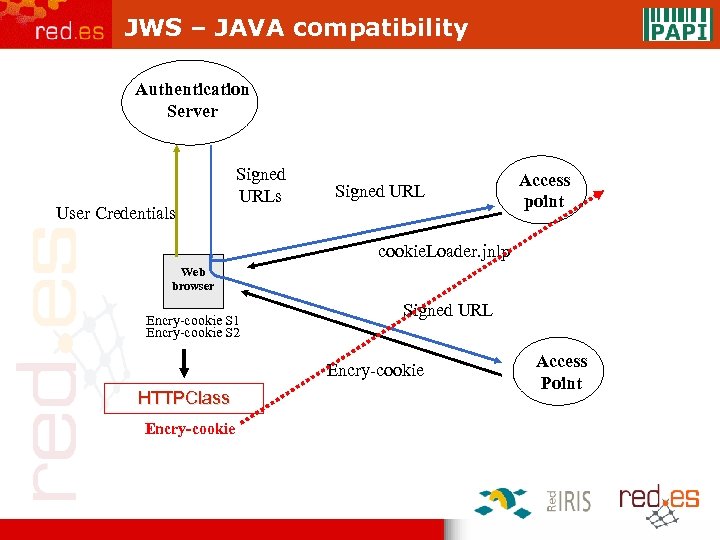 JWS – JAVA compatibility Authentication Server User Credentials Signed URL Access point cookie. Loader. jnlp Web browser Encry-cookie S 1 Encry-cookie S 2 Signed URL Encry-cookie HTTPClass Encry-cookie Access Point
JWS – JAVA compatibility Authentication Server User Credentials Signed URL Access point cookie. Loader. jnlp Web browser Encry-cookie S 1 Encry-cookie S 2 Signed URL Encry-cookie HTTPClass Encry-cookie Access Point
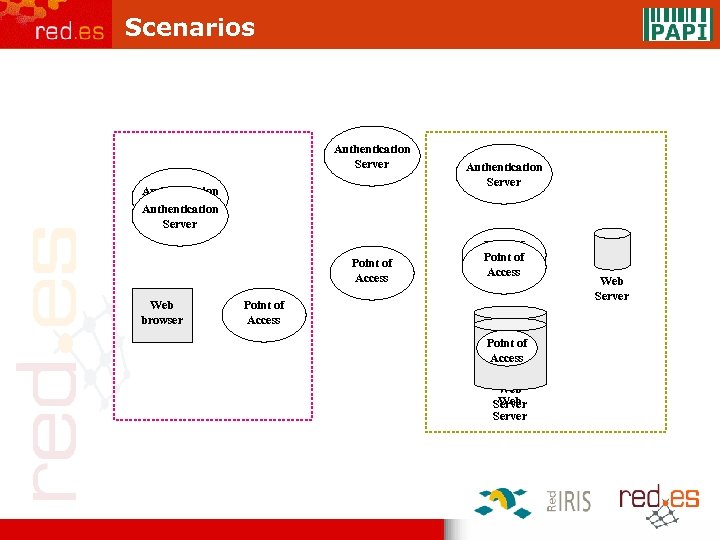 Scenarios Authentication Server Point of Access Web browser Point of Access Authentication Server Point of Access Web Server
Scenarios Authentication Server Point of Access Web browser Point of Access Authentication Server Point of Access Web Server
 Future works • Enhance PAPI compatibility with other technologies q A-Select q Shibboleth q Athens • Include new type of clients q WIFI access q Kerberos q VPNs • Improve the administration tools
Future works • Enhance PAPI compatibility with other technologies q A-Select q Shibboleth q Athens • Include new type of clients q WIFI access q Kerberos q VPNs • Improve the administration tools