e90d41330318c87ce60102ed6c32902b.ppt
- Количество слайдов: 18
 An Analysis of XMPP Security Team “Vision” Chris Nelson Ashwin Kulkarni Nitin Khatri Taulant Haka Yong Chen CMPE 209 Spring 2009
An Analysis of XMPP Security Team “Vision” Chris Nelson Ashwin Kulkarni Nitin Khatri Taulant Haka Yong Chen CMPE 209 Spring 2009
 Agenda n n n HISTORY OF XMPP INTRODUCTION TO XMPP SECURITY IN XMPP • Use of TLS (Transport Layer Security) • Use of SASL (Simple Authentication and Security Layer) n n SECURITY CONCERNS IN XMPP Conclusion
Agenda n n n HISTORY OF XMPP INTRODUCTION TO XMPP SECURITY IN XMPP • Use of TLS (Transport Layer Security) • Use of SASL (Simple Authentication and Security Layer) n n SECURITY CONCERNS IN XMPP Conclusion
 HISTORY OF XMPP n n n 1998 -Core technology was invented by Jeremie Miller 1999 -Jabber open-source community initially started to developed the protocol 2000 -Instant Messaging and Presence Protocol (IMPP) Working Group published the result 2002 and 2003 -XMPP protocol was formalized by IETF 2004 -The XMPP RFCs were published. 2007 -Jabber Software Foundation was renamed XMPP Standards Foundation
HISTORY OF XMPP n n n 1998 -Core technology was invented by Jeremie Miller 1999 -Jabber open-source community initially started to developed the protocol 2000 -Instant Messaging and Presence Protocol (IMPP) Working Group published the result 2002 and 2003 -XMPP protocol was formalized by IETF 2004 -The XMPP RFCs were published. 2007 -Jabber Software Foundation was renamed XMPP Standards Foundation
 Application using XMPP n n n n n Instant messaging Presence Media session management Shared editing Whiteboarding Collaboration Lightweight middleware Content syndication Generalized XML routing.
Application using XMPP n n n n n Instant messaging Presence Media session management Shared editing Whiteboarding Collaboration Lightweight middleware Content syndication Generalized XML routing.
 The core protocols of Extensible Messaging and Presence Protocol n n n Jabber Client Jabber Server Presence and IM Session Establishment Resource Binding Server Dialback Simple Authentication and Security Layer S/MIME Encryption Stanza Errors Stream Errors Transport Layer Security XML Streams
The core protocols of Extensible Messaging and Presence Protocol n n n Jabber Client Jabber Server Presence and IM Session Establishment Resource Binding Server Dialback Simple Authentication and Security Layer S/MIME Encryption Stanza Errors Stream Errors Transport Layer Security XML Streams
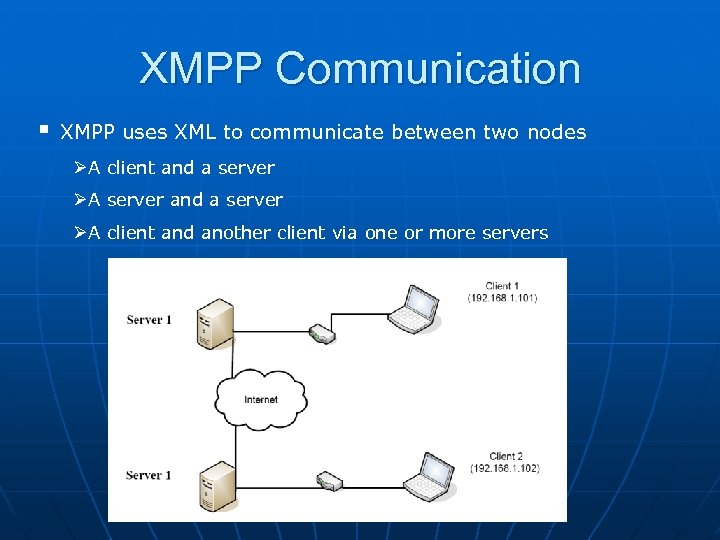 XMPP Communication § XMPP uses XML to communicate between two nodes ØA client and a server ØA server and a server ØA client and another client via one or more servers
XMPP Communication § XMPP uses XML to communicate between two nodes ØA client and a server ØA server and a server ØA client and another client via one or more servers
 XMPP Communication (cont. ) n n simplistic view of one-way communication using XMPP.
XMPP Communication (cont. ) n n simplistic view of one-way communication using XMPP.
 SECURITY IN XMPP n XMPP is built on four layers • TCP as the reliable transport protocol • TLS for encryption of data sent over the TCP connection • SASL for authentication of nodes communicating over TLS and TCP • XMPP as an application communicating over the reliable, authenticated, and encrypted channel
SECURITY IN XMPP n XMPP is built on four layers • TCP as the reliable transport protocol • TLS for encryption of data sent over the TCP connection • SASL for authentication of nodes communicating over TLS and TCP • XMPP as an application communicating over the reliable, authenticated, and encrypted channel
 SECURITY IN XMPP Use of TLS n n n The initiating entity opens a TCP connection including the 'version' attribute The receiving entity responds by opening a TCP connection including the 'version' attribute The receiving entity offers the STARTTLS extension including a
SECURITY IN XMPP Use of TLS n n n The initiating entity opens a TCP connection including the 'version' attribute The receiving entity responds by opening a TCP connection including the 'version' attribute The receiving entity offers the STARTTLS extension including a
 SECURITY IN XMPP Use of TLS (Cont) n n The initiating entity issues the STARTTLS command The receiving entity MUST reply with either a
SECURITY IN XMPP Use of TLS (Cont) n n The initiating entity issues the STARTTLS command The receiving entity MUST reply with either a
 SECURITY IN XMPP Use of SASL n n n The initiating entity requests SASL authentication by including the 'version' The receiving entity advertises a list of available SASL authentication mechanisms The initiating entity selects a mechanism by sending an
SECURITY IN XMPP Use of SASL n n n The initiating entity requests SASL authentication by including the 'version' The receiving entity advertises a list of available SASL authentication mechanisms The initiating entity selects a mechanism by sending an
 SECURITY IN XMPP Use of SASL (cont. ) n If necessary, the receiving entity sends more challenges -- the initiating entity sends more responses until: • The initiating entity aborts the handshake by sending an
SECURITY IN XMPP Use of SASL (cont. ) n If necessary, the receiving entity sends more challenges -- the initiating entity sends more responses until: • The initiating entity aborts the handshake by sending an
 XMPP Extensions n n n Instant Messaging and Presence -- base XMPP extensions for instant messaging, contact lists, presence, and privacy blocking. (RFC 3921) End-to-End Signing and Object Encryption (RFC 3923) XMPP extensions with additional features including XML-RPC and SOAP bindings, inband registration, extended presence, geolocation, and reliable message delivery (XEP series )
XMPP Extensions n n n Instant Messaging and Presence -- base XMPP extensions for instant messaging, contact lists, presence, and privacy blocking. (RFC 3921) End-to-End Signing and Object Encryption (RFC 3923) XMPP extensions with additional features including XML-RPC and SOAP bindings, inband registration, extended presence, geolocation, and reliable message delivery (XEP series )
 XMPP Extensions (XEP series ) n n Service Discovery -- a robust protocol for determining the features supported by other entities on an XMPP network (XEP-0030) Data Forms -- a flexible protocol formshandling via XMPP, mainly used in workflow applications and for dynamic configuration (XEP 0004 ) File Transfer -- a protocol for transferring files from one XMPP entity to another (XEP-0096) HTTP Binding -- a binding of XMPP to HTTP rather than TCP, mainly used for devices that cannot maintain persistent TCP connections to a server (XEP-0124 )
XMPP Extensions (XEP series ) n n Service Discovery -- a robust protocol for determining the features supported by other entities on an XMPP network (XEP-0030) Data Forms -- a flexible protocol formshandling via XMPP, mainly used in workflow applications and for dynamic configuration (XEP 0004 ) File Transfer -- a protocol for transferring files from one XMPP entity to another (XEP-0096) HTTP Binding -- a binding of XMPP to HTTP rather than TCP, mainly used for devices that cannot maintain persistent TCP connections to a server (XEP-0124 )
 SECURITY CONCERNS IN XMPP n Security depend on user • User trust a certificate from an unknown source n And/Or implementation • Performing SASL negotiations before securing the channel with TLS • sending message, presence, or iq data before completing the TLS or SASL negotiations
SECURITY CONCERNS IN XMPP n Security depend on user • User trust a certificate from an unknown source n And/Or implementation • Performing SASL negotiations before securing the channel with TLS • sending message, presence, or iq data before completing the TLS or SASL negotiations
 Conclusion n n XMPP was designed with security in mind Its architecture is solid The implementation is secure Susceptible to careless users
Conclusion n n XMPP was designed with security in mind Its architecture is solid The implementation is secure Susceptible to careless users
 References § § § § § Summary of XMPP. (2007, January 16). Retrieved March 8, 2008, from http: //www. xmpp. org/about/summary. shtml Extensible Messaging and Presence Protocol. Retrieved March 8, 2008, from http: //en. wikipedia. org/wiki/Extensible_Messaging_and_Presence_Protocol Extensible Messaging and Presence Protocol (XMPP): Core. (2004, October). Retrieved March 8, 2008, from http: //tools. ietf. org/html/rfc 3920 Extensible Messaging and Presence Protocol (XMPP): Instant Messaging and Presence. (2004, October). Retrieved March 8, 2008, from http: //tools. ietf. org/html/rfc 3921 6 End-to-End Signing and Object Encryption for the Extensible Messaging and Presence Protocol (XMPP). (2004, October). Retrieved March 8, 2008, from http: //tools. ietf. org/html/rfc 3923 The XMPP Federation. Retrieved March 8, 2008 from https: //www. xmpp. net Simple Authentication and Security Layer (SASL). (2006, June). Retrieved March 8, 2008, from http: //tools. ietf. org/html/rfc 4422 Extensible Messaging and Presence Protocol (XMPP): Core. (2004, October). Retrieved March 8, 2008, from http: //tools. ietf. org/html/rfc 3920
References § § § § § Summary of XMPP. (2007, January 16). Retrieved March 8, 2008, from http: //www. xmpp. org/about/summary. shtml Extensible Messaging and Presence Protocol. Retrieved March 8, 2008, from http: //en. wikipedia. org/wiki/Extensible_Messaging_and_Presence_Protocol Extensible Messaging and Presence Protocol (XMPP): Core. (2004, October). Retrieved March 8, 2008, from http: //tools. ietf. org/html/rfc 3920 Extensible Messaging and Presence Protocol (XMPP): Instant Messaging and Presence. (2004, October). Retrieved March 8, 2008, from http: //tools. ietf. org/html/rfc 3921 6 End-to-End Signing and Object Encryption for the Extensible Messaging and Presence Protocol (XMPP). (2004, October). Retrieved March 8, 2008, from http: //tools. ietf. org/html/rfc 3923 The XMPP Federation. Retrieved March 8, 2008 from https: //www. xmpp. net Simple Authentication and Security Layer (SASL). (2006, June). Retrieved March 8, 2008, from http: //tools. ietf. org/html/rfc 4422 Extensible Messaging and Presence Protocol (XMPP): Core. (2004, October). Retrieved March 8, 2008, from http: //tools. ietf. org/html/rfc 3920
 Questions and Answers Thank You!
Questions and Answers Thank You!


