4e1eb3b82d538e4bfd545b66ce0c274d.ppt
- Количество слайдов: 16
 An Aircraft with 1 NET™ is “ALWAYS CONNECTED” Aircraft Information Technology made STRAIGHTFORWARD and SECURE.
An Aircraft with 1 NET™ is “ALWAYS CONNECTED” Aircraft Information Technology made STRAIGHTFORWARD and SECURE.
 Aircraft is a Node on the Internet • • The aircraft shall require connectivity The aircraft shall require local processing and storage The system shall require access to data by users To achieve the first three items an approved measure of security is required • This presentation will address the existing RTCA requirements, industry activities, and one solution
Aircraft is a Node on the Internet • • The aircraft shall require connectivity The aircraft shall require local processing and storage The system shall require access to data by users To achieve the first three items an approved measure of security is required • This presentation will address the existing RTCA requirements, industry activities, and one solution
 RTCA Aircraft Security Standards exist • DO-326 A - Adds to current guidance for aircraft certification to handle threat of intentional unauthorized electronic interaction to aircraft safety. It adds data requirements and compliance objectives, as organized by generic activities for aircraft safety. • DO-355 - A resource for civil aviation authorities and the aviation industry when the operation and maintenance of aircraft and the effect of information security threats can affect aircraft safety. Operation and maintenance of the aircraft related to information security threats are defined. • DO-356 - This document describes guidelines, methods and tools used in performing an airworthiness security process.
RTCA Aircraft Security Standards exist • DO-326 A - Adds to current guidance for aircraft certification to handle threat of intentional unauthorized electronic interaction to aircraft safety. It adds data requirements and compliance objectives, as organized by generic activities for aircraft safety. • DO-355 - A resource for civil aviation authorities and the aviation industry when the operation and maintenance of aircraft and the effect of information security threats can affect aircraft safety. Operation and maintenance of the aircraft related to information security threats are defined. • DO-356 - This document describes guidelines, methods and tools used in performing an airworthiness security process.
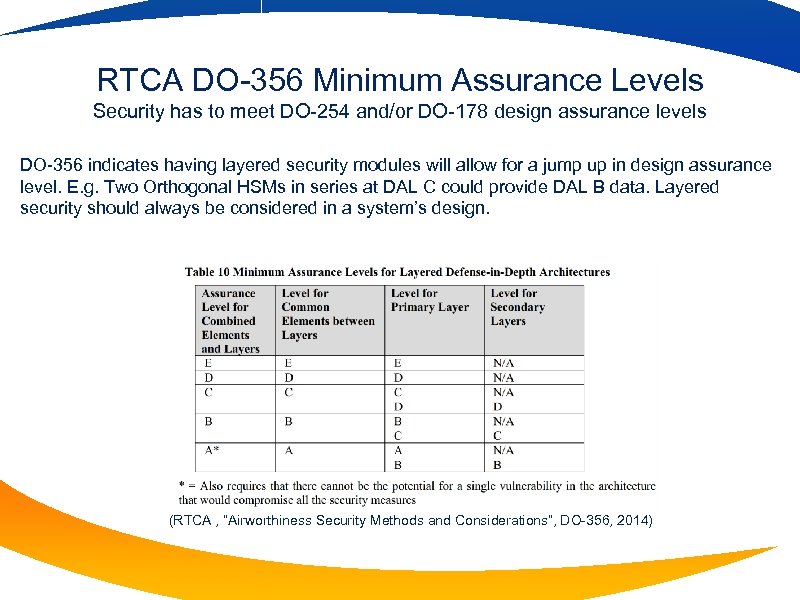 RTCA DO-356 Minimum Assurance Levels Security has to meet DO-254 and/or DO-178 design assurance levels DO-356 indicates having layered security modules will allow for a jump up in design assurance level. E. g. Two Orthogonal HSMs in series at DAL C could provide DAL B data. Layered security should always be considered in a system’s design. (RTCA , “Airworthiness Security Methods and Considerations”, DO-356, 2014)
RTCA DO-356 Minimum Assurance Levels Security has to meet DO-254 and/or DO-178 design assurance levels DO-356 indicates having layered security modules will allow for a jump up in design assurance level. E. g. Two Orthogonal HSMs in series at DAL C could provide DAL B data. Layered security should always be considered in a system’s design. (RTCA , “Airworthiness Security Methods and Considerations”, DO-356, 2014)
 NIST Algorithms and Security Standards FIPS is a testable US government standard • FIPS PUB 140 -2: Specifies the security requirements for a cryptographic module utilized within a security system protecting sensitive information in computer and telecommunication systems. • FIPS PUB 191: Understanding the necessity to provide security on a LAN and how to decide the appropriate security measures needed. • FIPS PUB 197: Specifies the Advanced Encryption Standard (AES), which is a symmetric block cipher that can process data using cipher keys. • FIPS PUB 186 -4: Specifies a suite of algorithms that can be used to generate a digital signature. Digital signatures are used to detect unauthorized modifications to data and to authenticate the identity of the signatory. In addition, the recipient of the signed data can use a digital signature as evidence in demonstrating to a third party that the signature was, in fact, generated by the claimed signatory.
NIST Algorithms and Security Standards FIPS is a testable US government standard • FIPS PUB 140 -2: Specifies the security requirements for a cryptographic module utilized within a security system protecting sensitive information in computer and telecommunication systems. • FIPS PUB 191: Understanding the necessity to provide security on a LAN and how to decide the appropriate security measures needed. • FIPS PUB 197: Specifies the Advanced Encryption Standard (AES), which is a symmetric block cipher that can process data using cipher keys. • FIPS PUB 186 -4: Specifies a suite of algorithms that can be used to generate a digital signature. Digital signatures are used to detect unauthorized modifications to data and to authenticate the identity of the signatory. In addition, the recipient of the signed data can use a digital signature as evidence in demonstrating to a third party that the signature was, in fact, generated by the claimed signatory.
 Certificate Authority One step in the process • Certificate Authority (CA): is a trusted third party who validates keys for exchange in public domain • Digital Certificates: Are electronic credentials that are used to assert the online identities of individuals and entities. Digital certificates are analogous to a passport or drivers licenses. Organization does due diligence to prove you are who you say you are and then issues you documentation proving it. • Public Key Infrastructure (PKI): Certificates are issued to a specific public key, which is paired to a private key.
Certificate Authority One step in the process • Certificate Authority (CA): is a trusted third party who validates keys for exchange in public domain • Digital Certificates: Are electronic credentials that are used to assert the online identities of individuals and entities. Digital certificates are analogous to a passport or drivers licenses. Organization does due diligence to prove you are who you say you are and then issues you documentation proving it. • Public Key Infrastructure (PKI): Certificates are issued to a specific public key, which is paired to a private key.
 Cryptographic Key Management System • Cryptographic key management system (CKMS): is how all the keys in a system, hierarchal or other, are managed. • NIST SP 800 -130: CKMS consists of policies, procedures, components and devices that used to protect, manage and distribute cryptographic keys and certain specific information, called metadata. • Each vendor can create a CKMS, a standard for certificates similar to X. 509, and everything else needed. Or we can produce a standard method and benefit together.
Cryptographic Key Management System • Cryptographic key management system (CKMS): is how all the keys in a system, hierarchal or other, are managed. • NIST SP 800 -130: CKMS consists of policies, procedures, components and devices that used to protect, manage and distribute cryptographic keys and certain specific information, called metadata. • Each vendor can create a CKMS, a standard for certificates similar to X. 509, and everything else needed. Or we can produce a standard method and benefit together.
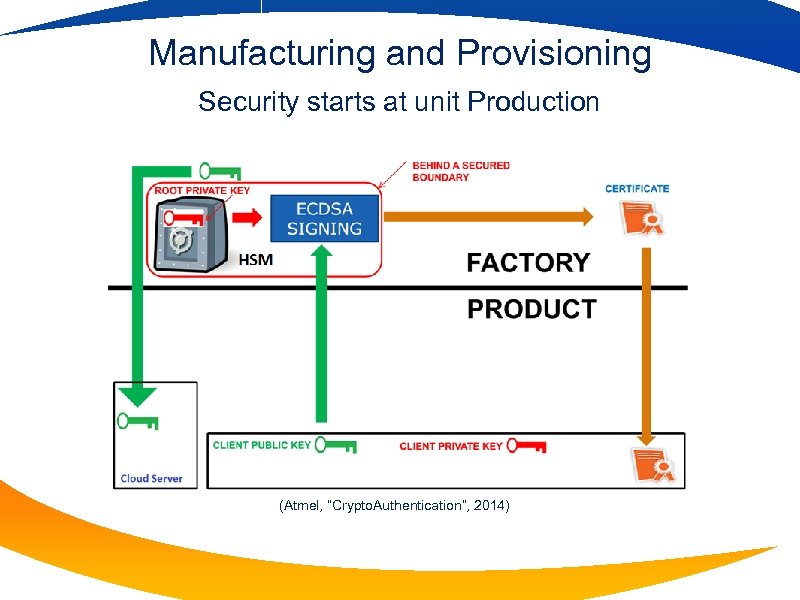 Manufacturing and Provisioning Security starts at unit Production (Atmel, “Crypto. Authentication”, 2014)
Manufacturing and Provisioning Security starts at unit Production (Atmel, “Crypto. Authentication”, 2014)
 Security In Automotive Solutions exist • Automobile industry is already doing this and there are many IC manufacturers supporting them. • Freescale white paper: e. g. of manufacturer meeting the auto industry security requirements. • Industry Standards used: National Institute of Standards and Technology (NIST), Hersteller Initiative Software (HIS) Working Group, Trusted Computing Group (TCG)
Security In Automotive Solutions exist • Automobile industry is already doing this and there are many IC manufacturers supporting them. • Freescale white paper: e. g. of manufacturer meeting the auto industry security requirements. • Industry Standards used: National Institute of Standards and Technology (NIST), Hersteller Initiative Software (HIS) Working Group, Trusted Computing Group (TCG)
 Malware Resistant • Software: Is always changing, therefore, opening itself up to new security vulnerabilities everyday. • Hardware: Never changes! Built to seasoned standards so trial and error is out of the way. • Hardware implementations such as a Trusted Platform Module (TPM) from the TCG standards. • ASICs standing on the back of well established standards like AES, SHA, ECDSA, etc. are the solution found by other industries thus far.
Malware Resistant • Software: Is always changing, therefore, opening itself up to new security vulnerabilities everyday. • Hardware: Never changes! Built to seasoned standards so trial and error is out of the way. • Hardware implementations such as a Trusted Platform Module (TPM) from the TCG standards. • ASICs standing on the back of well established standards like AES, SHA, ECDSA, etc. are the solution found by other industries thus far.
 TM Solution 1 Net Beta tested and available • • System has moved 100 s of millions of secure records 1 Net. TM v 2 was launched to meet FIPS 140 -2 and RTCA requirements • • Solution addresses security and certification issues for aircraft Thompson Aerospace will make patents and/or security modules available to any third parties based on a license agreement
TM Solution 1 Net Beta tested and available • • System has moved 100 s of millions of secure records 1 Net. TM v 2 was launched to meet FIPS 140 -2 and RTCA requirements • • Solution addresses security and certification issues for aircraft Thompson Aerospace will make patents and/or security modules available to any third parties based on a license agreement
 Data Security is the Overriding Requirement for 1 Net™ FIPS 140 -2 Level 3 for Data Validity, Security and Access FIPS 140 -2 Level 3 of security is used by the US government for secret information. FIPS is a verifiable standard and this level of data management will allow uploading and downloading of the most critical type of data. Hardware based Aircraft Trusted Platform Module (TPM) A TPM is the industry standard for creating, storing, and encrypting/decrypting keys. A hardware TPM provides an unhackable means of key management. An ECC trusted module that uses ECDSA (security means) validation for users ECDSA type security provides the best solution for embedded key protection. The application provides a hardware means of user identification to allow access to system data. Users are provided with an ECDSA dongle as a secure means of determining the Access Control List applicability. RTCA (Regulatory Group) DO-326, DO-355 and DO-356 provides the method for certification 1 Net™ complies with RTCA requirements and FIPS 140 -2 Level 3 data requirements. This provides the airline with the capability to meet the security system requirements for ISO 27001: 2013. Security The RTCA requirements define methods to certify information technology for aircraft. Federal Information Protection Standards (FIPS) provide specific requirements to management data. 1 Net™ hardware based data management solution is able to meet both FIPS and RTCA data management while meeting RTCA aircraft certification. Security is Available NOW
Data Security is the Overriding Requirement for 1 Net™ FIPS 140 -2 Level 3 for Data Validity, Security and Access FIPS 140 -2 Level 3 of security is used by the US government for secret information. FIPS is a verifiable standard and this level of data management will allow uploading and downloading of the most critical type of data. Hardware based Aircraft Trusted Platform Module (TPM) A TPM is the industry standard for creating, storing, and encrypting/decrypting keys. A hardware TPM provides an unhackable means of key management. An ECC trusted module that uses ECDSA (security means) validation for users ECDSA type security provides the best solution for embedded key protection. The application provides a hardware means of user identification to allow access to system data. Users are provided with an ECDSA dongle as a secure means of determining the Access Control List applicability. RTCA (Regulatory Group) DO-326, DO-355 and DO-356 provides the method for certification 1 Net™ complies with RTCA requirements and FIPS 140 -2 Level 3 data requirements. This provides the airline with the capability to meet the security system requirements for ISO 27001: 2013. Security The RTCA requirements define methods to certify information technology for aircraft. Federal Information Protection Standards (FIPS) provide specific requirements to management data. 1 Net™ hardware based data management solution is able to meet both FIPS and RTCA data management while meeting RTCA aircraft certification. Security is Available NOW
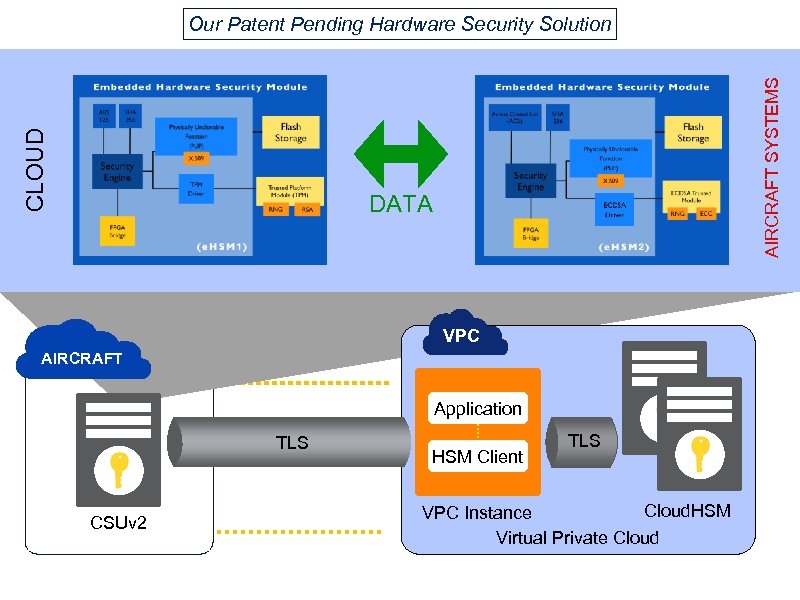 AIRCRAFT SYSTEMS CLOUD Our Patent Pending Hardware Security Solution DATA VPC AIRCRAFT Application TLS CSUv 2 HSM Client TLS Cloud. HSM VPC Instance Virtual Private Cloud
AIRCRAFT SYSTEMS CLOUD Our Patent Pending Hardware Security Solution DATA VPC AIRCRAFT Application TLS CSUv 2 HSM Client TLS Cloud. HSM VPC Instance Virtual Private Cloud
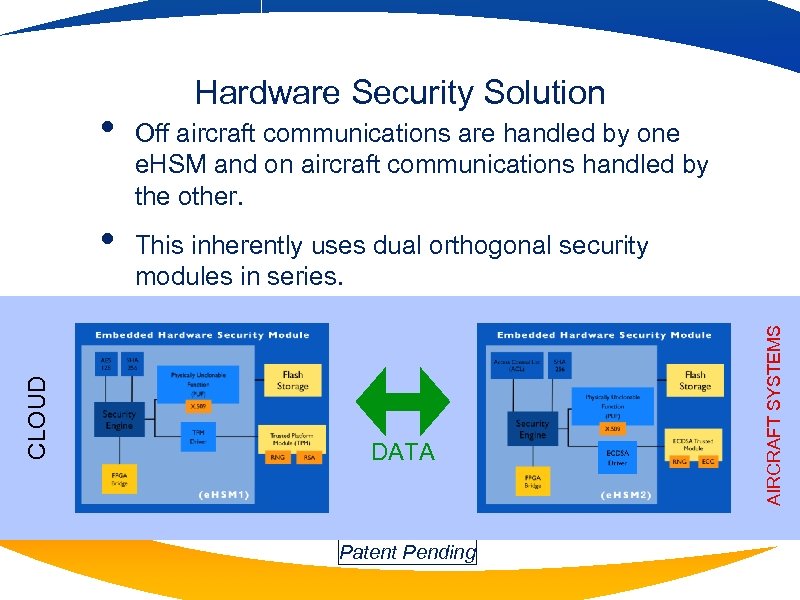 CLOUD • Off aircraft communications are handled by one e. HSM and on aircraft communications handled by the other. This inherently uses dual orthogonal security modules in series. DATA Patent Pending AIRCRAFT SYSTEMS • Hardware Security Solution
CLOUD • Off aircraft communications are handled by one e. HSM and on aircraft communications handled by the other. This inherently uses dual orthogonal security modules in series. DATA Patent Pending AIRCRAFT SYSTEMS • Hardware Security Solution
 Amazon EC 2 and HSM in the Cloud A good partner for aerospace • Amazon Elastic Compute Cloud (Amazon EC 2) allows computing instances in the cloud that can be attached to an HSM via a Virtual Private Network (VPC). • Amazon Web Services (AWS) known for security prowess. • • Helped setup CIA’s private cloud computing network. Extremely convenient, secure, scalable way of setting up infrastructure • Green Hills and Thales e. Security offer solutions
Amazon EC 2 and HSM in the Cloud A good partner for aerospace • Amazon Elastic Compute Cloud (Amazon EC 2) allows computing instances in the cloud that can be attached to an HSM via a Virtual Private Network (VPC). • Amazon Web Services (AWS) known for security prowess. • • Helped setup CIA’s private cloud computing network. Extremely convenient, secure, scalable way of setting up infrastructure • Green Hills and Thales e. Security offer solutions
 ARINC 848 Considerations • • • Authentication using a trusted CA certificate should be considered for units communicating off the aircraft. CKMS implementation shall be required to achieve security Hardware vs software security solutions need to be considered The solution need to be interoperable between suppliers Effective connectivity solutions will not be deployed without security
ARINC 848 Considerations • • • Authentication using a trusted CA certificate should be considered for units communicating off the aircraft. CKMS implementation shall be required to achieve security Hardware vs software security solutions need to be considered The solution need to be interoperable between suppliers Effective connectivity solutions will not be deployed without security


